Text
The Top Free Virtual Machine Tools You Should Try Right Now

If you're looking for ways to save money and optimize the efficiency of your office, virtual machine tools are a great place to start. With virtualization technology, you can run multiple operating systems on one physical machine in order to maximize space and resources—allowing for smoother operation and higher output with fewer machines. Not only can it improve performance in terms of game-play, software development, web hosting, or online business transactions; but it also provides cost savings by avoiding the need to purchase expensive hard drives or network components that would otherwise be incurred. In this blog post, we'll explore some of the top free virtual machine tools available right now so you can take full advantage of these amazing benefits without breaking the bank!
Introductory Overview of Virtual Machine Tools
In recent years, the significance of virtual machine tools has grown in leaps and bounds within the realm of information technology. These cutting-edge solutions have deftly become a mainstay for both developers and system administrators alike. Virtual machine tools, by emulating hardware resources, effectively allow multiple operating systems to operate concurrently and independently on a single host machine. As powerful software applications, they facilitate the creation, management, and optimization of virtualized environments for diverse purposes, such as software testing, cybersecurity evaluation, and server consolidation. Moreover, these tools embody a modern, sophisticated approach to managing infrastructure and provide a robust foundation for enhancing productivity, expediting workflows, and fostering innovation for organizations and individuals navigating an increasingly digital landscape.
How to Use VirtualBox for Free
Utilizing VirtualBox for Free delivers a sophisticated and efficient solution to virtualize different operating systems on a single device. VirtualBox, an open-source software, has gained immense popularity among developers and IT professionals owing to its versatility and ease of use. This powerful virtualization tool caters to a wide array of applications, ranging from running legacy software on modern hardware to seamless testing of operating systems and applications without risking the stability of your primary system. The cost-effective nature of this application, coupled with its vast capabilities, makes it an invaluable asset for those seeking to harness the power of virtualization without incurring any financial burden. Integrating VirtualBox into your daily practices paves the way for an innovative and secure environment that fosters creativity and efficiency.
Exploring the Benefits of VMware Player
The advent of virtualization has brought forth numerous benefits, and VMware Player stands as a testament to these advantages. As a reliable, robust, and user-friendly virtualization software, VMware Player excels in offering users an effortless and efficient manner of managing and operating multiple operating systems on a single computer. By employing innovative virtualization methods, VMware Player dramatically enhances productivity, allowing IT professionals and developers to seamlessly test and develop applications on diverse platforms. Moreover, the software's robust security features promise a secure environment that reduces the risk of malicious intrusions and cyber threats. With its unmatched receptiveness for both business and personal use, VMware Player undeniably paves the way for the elevated potential of virtualization in today's dynamic digital landscape.
Making the Most of Parallels Desktop
The ingenious invention, Parallels Desktop, is a state-of-the-art software that enables individuals and businesses to optimize their work processes and improve efficiency. This remarkable tool allows for seamless access to multiple operating systems within a single computer, facilitating effortless interaction between applications and a smooth workflow. By leveraging Parallels Desktop, one eliminates the need for cumbersome hardware, thus conserving resources, while simultaneously promoting synergy between disparate platforms. The result is a unified work environment leading to increased productivity and reduced complexity. Moreover, its compatibility with various devices such as smartphones and tablets, makes it an indispensable and versatile accomplice in today's fast-paced digital landscape.
Examining Microsoft's Hyper-V for Windows 10
In recent years, the significant rise in virtualization technologies has brought forth an array of benefits for both businesses and individual users. One such cutting-edge solution is Microsoft's Hyper-V, a remarkable feature available on Windows 10 operating systems. Hyper-V allows users to create and manage virtual machines (VMs) within a single device, eliminating the need for investing in additional hardware, whilst ensuring efficient utilization of the available resources. Embracing this technology can lead to enhanced productivity and flexibility, as it permits simultaneous deployment of multiple operating systems, streamlines software testing processes, and simplifies disaster recovery procedures. Furthermore, by closely examining the dynamic capabilities of Hyper-V, IT professionals can ascertain novel methods to optimize resources, reduce overhead costs, and bolster their organization's strategic approach to technological advancement.
Unleashing the Power of QEMU with Open-Source Software
The phenomenal potential of QEMU, an open-source machine emulator and virtualizer, becomes increasingly evident when synergized with other open-source software. Such collaborations afford developers and users an integrated platform to optimize the performance, functionality, and flexibility of virtual systems. Streamlining processes, reducing costs, and overcoming challenges posed by proprietary software, these dynamic partnerships continually push the boundaries of what is feasible within the realm of virtualization. As innovation accelerates and open-source software gains traction across various industries, the combination of QEMU and other renowned open-source tools paves the way for groundbreaking advancements, ultimately challenging conventional paradigms and shaping the future of technology.
In conclusion, virtual machine tools offer a cost-effective solution to the demands of modern computing. From the simple yet powerful VirtualBox software to the more advanced VMware Player and Parallels Desktop options, there is something available for everyone's needs. For those looking to explore a Windows 10 experience without investing in a separate license or running numerous installations on their device, Microsoft's Hyper-V can provide a great alternative solution. Finally, open-source solutions such as QEMU can help tech enthusiasts really unleash their creativity as they customize their environment and modify it however they please. Whether for business or pleasure, virtual machines are here to stay and power users everywhere are sure to get plenty of use out of this increasingly powerful technology!
7 notes
·
View notes
Text
Email Marketers' Security Guide: 8 Must-Read Tips

Frankly, email marketing is a minefield with countless moving pieces. One of these essential components that cannot be overlooked is security – it's a must when dealing with customer and vendor data. As emails contain valuable information such as usernames and passwords, when an unsecured message makes its way into the wrong hands or to a botnet address, confidential data can easily get exposed potentially leading to huge financial losses. In order to stay ahead of the loop and ensure your clients' safety, today we uncover 8 crucial strategies for secure email marketing!
Understand the Impact of Data Breaches on Businesses
Data breaches have become an alarming concern for businesses in today's digital age, with potentially disastrous consequences. It is crucial for organizations to comprehend the far-reaching implications of such security incidents. When sensitive information is compromised, not only is there a significant financial burden but there is also lasting damage to an organization's reputation and customer trust. Regrettably, even the strongest security measures may not provide complete protection against cybercriminals who employ increasingly sophisticated techniques to gain unauthorized access. To mitigate risks and maintain a robust defense, businesses must continually assess and update their cybersecurity strategies. By understanding the impact of data breaches, companies can take steps to proactively safeguard their digital infrastructure and assets, subsequently ensuring their long-term resilience against cyber threats.
Utilize and Enable Multi-Factor Authentication
The importance of robust cybersecurity measures in today's digital world cannot be overstated, and one of the most effective means of safeguarding our digital assets is through the utilization of Multi-Factor Authentication (MFA). MFA serves as an additional layer of protection that requires users to verify their identities through multiple methods before granting access to sensitive information, systems, or resources. By incorporating various elements such as knowledge-based authentication (passwords, answers to security questions), possession-based authentication (hardware or software tokens), and inherence-based authentication (biometric data such as fingerprints or facial recognition), MFA bolsters conventional security protocols, significantly reducing the risk of unauthorized access. Enabling MFA not only demonstrates a commitment to proactively protecting one's digital landscape but also helps foster a culture of security awareness and responsibility, ultimately fortifying the virtual frontiers on which we increasingly rely.
Leverage Email Encryption to Protect Sensitive Information
In today's rapidly advancing digital age, safeguarding sensitive information has become a paramount concern for individuals and organizations alike. One effective way to achieve this is by leveraging email encryption. By utilizing encryption techniques, email users can protect their confidential data from unauthorized access during transmission, ensuring that only the intended recipient can decode and read the contents. As cyber threats continue to evolve and become increasingly sophisticated, adopting email encryption not only demonstrates vigilance but also reinforces the importance of cybersecurity in our daily communications. Furthermore, by taking precautionary steps in securing sensitive information, businesses and individuals can preserve their reputations and foster trust among their stakeholders, reaffirming the indispensable role of email encryption in our digitally connected world.
Establish a Comprehensive Policy for Mobile Device Security
In today's rapidly evolving digital landscape, it has become imperative for organizations to establish a comprehensive policy for mobile device security. The surge in mobile device usage and the ease with which sensitive information can be accessed, transmitted, and stored has made it crucial to implement robust security measures. An effective mobile device security policy will not only safeguard the confidentiality, integrity, and availability of critical data, but also help mitigate the risks associated with unauthorized access, malware attacks, and data breaches. By incorporating key elements such as strong access controls, encryption, mobile application management, and employee training, organizations can reap the benefits of technological advancements while maintaining a secure digital ecosystem. Ultimately, a well-crafted and diligently enforced mobile device security policy will contribute to the long-term success and stability of the organization, facilitating business continuity and fostering trust amongst stakeholders.
Utilize Secure File Sharing Systems and Tools
In today's digital age, the need for secure file-sharing systems and tools cannot be understated. With the ever-present risk of data breaches, hacking, and other cyber threats, it is paramount for individuals and organizations alike to establish dependable ways of exchanging sensitive information. Employing secure file-sharing platforms not only safeguards vital data but also maintains confidentiality and sustains trust among collaborators. In this pursuit, utilizing advanced encryption methods, multi-factor authentication, and robust access control features are some of the essential elements that must be incorporated when designing and selecting secure file-sharing tools. By proactively prioritizing data security, we can foster a safer online ecosystem that upholds the integrity and privacy of the digital assets we exchange every day.
Create a Password Management System
In today's digital age, maintaining the security and privacy of our online accounts is of paramount importance. Consequently, the creation of a robust password management system becomes an essential element in safeguarding your confidential information. By implementing a comprehensive password management system, you can ensure that all your passwords are stored securely, accessible only to you, and updated without hassle. Not only does such a system drastically reduce the risk of unauthorized access to your data, but it also alleviates the burden of remembering complex, unique passwords for each platform. The employment of advanced encryption techniques, two-factor authentication, and device-specific syncing capabilities further strengthens the system's security. Thus, a well-designed password management system is a cornerstone to achieving a secure, stress-free online experience.
As digital transformation continues to shape business operations across the globe, cybersecurity is more important than ever. Companies must actively assess their existing security posture and invest in critical tools and policies that can help protect the integrity of their data. Data breaches have created massive financial losses for many companies and continue to be a major threat. Businesses need to understand the complexity of managing cybersecurity, know the potential areas of risk, develop effective mitigation strategies, and invest in appropriate tools such as multi-factor authentication, email encryption, mobile device security policy, secure file sharing systems and tools, and password management systems. Ultimately, organizations should strive to create an environment that enables comprehensive data protection today so they can remain secure in the face of potential challenges tomorrow.
0 notes
Text
The Flexiple Remote Work Handbook

Are you a remote worker looking for ways to maximize your productivity and stay organized while working from home? If so, then this is the perfect guide for you! The Flexiple Remote Work Handbook provides practical tips and advice on how to set yourself up for success as a productive remote employee. In this comprehensive guide, we'll cover everything from the basic principles of telecommuting all the way through time management strategies and important self-care practices that will help keep you productive while enjoying the flexibility that comes with having a virtual office space. Read on to learn more about why having an effective remote work strategy is key to doing well in your role.
The Benefits and Challenges of Working from Home
The evolving landscape of work culture has given rise to an increasing number of professionals enjoying the benefits and navigating the challenges of working from home. This shift in working dynamics offers several perks, such as flexibility in managing personal and professional commitments, reduced commuting time, and enhanced work-life balance. However, it is essential to acknowledge the obstacles that accompany remote work as well. Some of the most prominent challenges include maintaining productivity in a home environment, blurring lines between work and leisure, and the potential for social isolation. To thrive in this contemporary work setting, professionals must strike a delicate balance, cultivating a structured routine that optimizes productivity and ensures personal well-being.
Scheduling Your Time for Maximum Productivity and Efficiency
In today's fast-paced world, it is imperative for individuals to schedule their time in a manner that ensures maximum productivity and efficiency. This begins with the recognition that the manner in which we allocate our time directly impacts our ability to achieve desired outcomes. By carefully prioritizing tasks, setting clear goals, and harnessing the power of innovative technologies and time management methodologies, we can optimize our daily schedule to better serve our personal and professional objectives. Establishing such discipline and structure in our lives can prove to be indispensable in our quest for success and personal fulfillment. Consequently, the art of time management warrants significant attention as it equips us with the ability to lead effective and rewarding lives.
Staying Organized in the New Normal
In the ever-evolving landscape of the new normal, staying organized has become an indispensable skill for individuals and businesses alike. As the boundaries between work and personal life become increasingly blurred, it behooves us to adopt a proactive approach to managing our time, priorities, and resources effectively. Embracing digital productivity tools, refining time-management strategies, and seeking innovative methods for decluttering our physical and digital spaces can vastly improve our overall efficiency, balance, and peace of mind. In a world where adaptability is key, imbuing ourselves with a deep sense of discipline and structure in our personal and professional lives will equip us to better navigate the challenges that the new normal so steadfastly present.
Setting Boundaries - Avoiding Burnout While Working Remotely
In today's fast-paced digital age, achieving a healthy work-life balance has become increasingly challenging, particularly for those working remotely. The ability to set boundaries is crucial in preventing burnout, which can have detrimental effects on both personal and professional affairs. By distinguishing between work and personal spaces, establishing a consistent routine, and communicating expectations with colleagues, remote workers can cultivate an environment conducive to maintaining their mental and emotional well-being. Additionally, incorporating regular intervals for self-care and leisure allows individuals to recharge their batteries, ultimately maximizing their productivity and efficacy in the long run. Investing in one's well-being by setting boundaries not only ensures a sustainable work approach but also fosters a sense of fulfillment and satisfaction in all aspects of life.
The Importance of Staying Connected and Communicating Clearly
In today's fast-paced world, staying connected and communicating clearly have become essential attributes for both personal and professional growth. These factors not only have a significant impact on one's ability to establish authentic relationships but also contribute to streamlining tasks and decisions. Effective communication facilitates a mutual understanding between individuals, allowing them to navigate complexities and prevent misunderstandings. Moreover, staying connected enriches our lives by creating a support network that provides emotional, intellectual, and social sustenance in times of need. As we forge ahead into an increasingly interconnected era, the ever-present importance of clear communication and enduring connections becomes increasingly apparent.
Leveraging Technology to Boost Performance
In today's fiercely competitive business environment, leveraging technology to boost performance has become crucial for organizations to maintain their competitive edge and drive continual growth. The integration of advanced technologies, such as artificial intelligence, machine learning, and data analytics, can significantly enhance operational efficiency, facilitate informed decision-making, and streamline communication across various departments. By embracing innovation and staying abreast of technological advancements, businesses equip themselves with the tools and strategies necessary to optimize resource allocation, reduce costs, and increase customer satisfaction. Ultimately, harnessing the power of technology is instrumental in fostering a culture of continuous improvement and propelling an organization toward long-term success.
Working from home can be an incredibly powerful tool for staying organized and productive, but it’s important to keep in mind the unique challenges that come with remote work. When embraced responsibly, it has the potential to provide greater flexibility and a more balanced work/life schedule. A successful remote career lies in managing your time, maintaining a clean workspace, setting boundaries, communicating effectively, and embracing new technology. Learning how to successfully navigate these simple yet effective strategies is essential for long terms success in the telecommuting world. The ability to overcome obstacles and make the most of our remote working capabilities will ultimately determine whether or not this new normal can be beneficial both professionally and personally.
0 notes
Text
Strategic database security in the background

The security of business data should always remain at the forefront of organizational objectives. Achieving this requires an effective strategy for database security that takes measures to both protect and prevent malicious activities from occurring. With the constantly evolving threat landscape, it is important to not only create proactive defenses but also ensure regular maintenance and updates with a focus on staying ahead of potential threats. In this blog post, we will explore how strategic database security can help safeguard your organization's most valuable assets in the background while ensuring peace of mind.
Overview of Database Security
Database security is of the utmost importance for any organization, as it contains large amounts of vital data. It requires a comprehensive approach in order to protect an organization from various threats. This includes implementing authentication and access procedures that restrict user inputs at multiple levels, selecting reliable encryption techniques to safeguard communications, using firewalls and intrusion detection systems, and monitoring databases for suspicious activities. Additionally, employees should be educated on database handling and provided with regular training sessions to ensure the security remains top-notch. While database security can be complicated to handle and defend against potential breaches, it is essential for preventing valuable information from getting into the wrong hands.
The Risks of Poor Database Security
Poor database security can be incredibly dangerous in today's digital world, as it leaves organizations vulnerable to data theft and other malicious activities. Companies are putting their customers and proprietary information at risk when they opt for inadequate security measures or neglect proper upkeep of existing security protocols. While the immediate repercussions can range from minor inconveniences to significant financial losses, long-term damage is difficult to predict or quantify - allowing someone access to private data could open up additional vulnerabilities that could continue to create issues down the road. Businesses big or small must take proper steps to ensure that the entirety of their network is secure by investing in sophisticated technologies and knowledgeable professionals who are able to protect against risks of all kinds.
Strategies to Bolster Database Security
When it comes to protecting databases from threats, organizations must have the appropriate strategies in place. Relevant measures include monitoring user access on a regular basis, encrypting data fields, and deploying tools to detect and prevent suspicious activity. It is also crucial for companies to develop a comprehensive disaster recovery plan that involves various redundancies and scheduled backups. Further, businesses should examine their infrastructures from time to time to identify any potential loopholes that could be exploited by malicious actors. Finally, while implementing preventive approaches like two-factor authentication can help deter attacks, organizations should also consider responding with routine penetration tests just in case there are vulnerabilities still lurking around. Ultimately, when organizations utilize the right strategies to bolster database security, they can know that their valuable systems are safeguarded against digital dangers.
How Automation Can Help in Ensuring Database Security
Automation is becoming increasingly important in the field of database security. By using automated processes and tools, companies can enhance the efficiency of their security protocols and reduce the amount of human effort required for regular maintenance tasks. Automation also opens up a range of options for data protection, including monitoring user access, traffic analysis and password updates. Furthermore, automation can analyze input from numerous sources to identify any potential threats or vulnerabilities before they become a problem. In this way, automation helps businesses ensure that their database security is robust and resilient against unauthorized access or activities.
Auditing Existing Database Security Measures
Security auditing existing databases involves the evaluation of access rights and permission to determine if any unauthorized changes or modifications have been made. This process is an important part of ensuring that businesses and organizations operate securely, as these changes can have ripple effects on a system's security posture. To conduct this type of audit, trained personnel must be able to recognize different types of threats, such as SQL injection attacks, malware infections, and malicious insiders. Additionally, having a baseline understanding of methods for data storage and encryption is essential when evaluating whether systems are adequately protected against potential adversaries. Ultimately, proper auditing will help the organization proactively reduce the chances of intrusion or attack.
Tips for Businesses to Ensure Adequate Database Protection
In today's digital age, it is essential for businesses to understand the importance of database protection. If a system breach occurs, confidential customer and business data can be accessed and misused. Business leaders must take proactive steps to guarantee that their systems are well-prepared to face any security risks. Database encryption, secure password protocols, firewalls and quality anti-malware products should all be deployed as a baseline protective measure. Regular disk imaging and monitoring can help identify malicious attackers before they cause significant damage. Furthermore, companies should urge their employees to practice comprehensive cyber safety habits while working remotely with company resources. Adequate database protection requires vigilance and periodic maintenance to stay ahead of potential threats.
In conclusion, as businesses grow, so does their need for adequate database security. Poorly managed databases expose businesses to malicious attacks and data breaches that can result in catastrophic damage to their reputation and bottom line. Database security is a process that requires considerable investment of time and resources. Strategies such as proper authentication, encryption, role-based access control, automation technology implementation, vulnerability scanning, patch management and auditing help build an effective defense system which ultimately safeguards valuable corporate assets. By taking the necessary steps now to secure your databases, you can avoid the costly consequences of neglecting this important aspect of business operations.
0 notes
Text
How to Protect a VM in a Cloud Environment
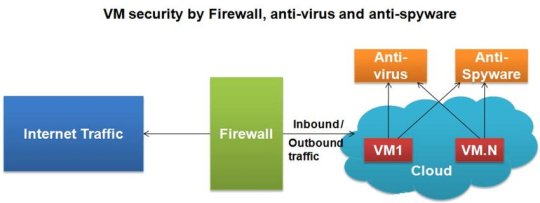
The protection of virtual machines (VMs) in a cloud environment is an increasingly important issue. As organizations move more of their data online and become reliant on cloud platforms for computing, storage, and other services, ensuring that their VMs are secure from malicious actors must be taken seriously. In this blog post, we'll explore the details of protecting your VM in a cloud-based infrastructure, from understanding user authentication to configuring access control measures.
Understanding the Basics of Virtual Machine Security
As the use of virtual machines continues to grow, IT professionals must become more familiar with the security implications that come along with this technology. Virtual machine security involves different safety measures than those used to protect traditional physical systems. Understanding the basics of virtual machine security is important for ensuring that these systems are secure and running optimally. Knowing how to configure settings and options such as role-based access control and least privilege policies are essential skills that IT personnel should possess when protecting virtual machines. Furthermore, applying proven techniques like hardening, patching regularly, and enabling log analysis can help IT professionals stay on top of threats specifically related to their virtual environments.
Establishing Access Control for Cloud VMs
Establishing proper access control for cloud virtual machines (VMs) is critically important. Without access control measures, VMs can become vulnerable to malicious actors or malicious software such as viruses and malware. Companies should implement authentication systems that are username and password based and/or authentication via tokens. Additionally, they should also update the authorization policies regularly to keep up with the evolving security threats. Identity and Access Management solutions serve to ensure that only authenticated users are given appropriate authorizations in accordance with their job roles within the company; anyone else attempting to gain unauthorized access shall be prevented from doing so through robust authentication measures such as multi-factor authentication. Implementing these measures will go a long way in ensuring that data stored on the cloud is secure without compromising functionality and user experience.
Learning about Firewall Rules and Best Practices
Learning about firewall rules and best practices is an important skill for anyone responsible for managing computer networks and keeping them secure. Studying up on the basics, properly configuring your firewalls and regularly monitoring them are essential steps when it comes to maintaining the security of your network’s data and the information it contains. From filtering out bad traffic to offering protection against threats like malware or denial-of-service attacks, effective firewalls play a key role in safeguarding all of your most sensitive and important information. With that in mind, understanding the specific rules and procedures associated with them can help ensure that your network infrastructure remains secure now and in the future.
Best Practices for Monitoring VM Activity
Monitoring virtual machine (VM) activity is essential for ensuring system security, performance, and efficiency. Unfortunately, understanding the best practices for doing this isn't always straightforward. In many cases, the chosen authoritative source of information is what ultimately determines whether or not the monitoring effort is successful. Considerable thought should be put into deciding on the security tools and techniques to use in monitoring VM activity so that all necessary data points are taken into account. Additionally, automated solutions can save time but can also lead to false positives if they are not configured properly. However, once the right approaches have been determined and carried out correctly, organizations will have a much better chance of spotting suspicious VM activity quickly and effectively.
Securing Data in the Cloud with Encryption
Due to the extensive use of cloud storage, security measures are paramount to ensure proprietary information remains safe and secure. Encryption is one of the most effective methods for protecting data stored in the cloud. It scrambles data into a code that can be deciphered with a key, which requires authorization and authentication. An added layer of security involves using multiple keys from different sources which enable each user to gain access independently. In other words, everyone holds individual puzzle pieces of encrypted data and must combine them before making sense out of the final product. Data owners who want to send confidential files can also upload messages without worrying about malicious third-party breaches.
Identifying and Responding to Potential Risks
Successful business operations require collective awareness of potential risks that may compromise the progress and stability of a company. To identify such threats in advance, it is necessary to undertake an assessment process to evaluate the likelihood and impact of such issues. This process should involve bringing together the expertise of colleagues across multiple departments to gain a holistic view of potential sources of risk. Once potential risks have been identified and their severity assessed, appropriate strategies for responding should be developed for each instance. Such strategies might include implementing additional controls or developing new processes or policies to ensure a proactive response to any impending threats. Being proactive in this way will allow companies to get ahead of any issues before they become costly problems in the long term.
Securing a virtual machine in the cloud is an ongoing process and demands close attention and thoughtful security strategies. By understanding the basics of VM security, establishing access control limits, creating firewall rules, adhering to best practices for monitoring VM activity, encrypting sensitive data, and responding to potential threats quickly and efficiently, businesses can ensure their cloud VMs maintain the highest level of security. With careful attention to these aspects of security, organizations can ensure their data remains safe from any vulnerabilities or threats that may arise.
1 note
·
View note
Text
Cybersecurity Handbook for Small Businesses

As a small business owner, it's essential to be knowledgeable about cybersecurity best practices. Cybercrime is on the rise, costing businesses trillions of dollars each year. If you want to keep your data and personal information safe, then having an up-to-date security plan in place is imperative. In this blog post, we discuss the importance of understanding cyber threats and how to protect yourself from them with our ultimate guide to cybersecurity for small businesses. Read on to learn more about what steps you need to take when creating a comprehensive cyber safety strategy.
Why Cybersecurity is Important for Small Businesses
Small businesses are often the targets of cyber security attacks, with an estimated $2 trillion annually stolen or lost due to these breaches. These intrusions can have long-term and expensive repercussions. Not only do they threaten a company's ability to make profits and deliver services, but they also expose confidential customer data which could result in hefty lawsuits and big-time fines. As a result, it is vital for small businesses to take preventive steps such as installing appropriate firewalls on their computers, securing WiFi networks, providing regular employee training on cybersecurity topics, and regularly updating software. Cybersecurity is not just about preventing losses; it is about ensuring the safety and protection of customers and of the organization in the long run.
A Comprehensive Guide to Protecting Your Company Data
As your business develops, so too does its data. Protecting private and confidential company information is essential in today's ever-evolving technological landscape. Employee credentials, customer information, financial records, and other sensitive data must be safeguarded to ensure both the success and longevity of your business. To that end, it is important to establish a comprehensive security strategy that incorporates the most up-to-date measures for safeguarding critical data such as tracking user accounts and activities, encrypting stored data, investing in reliable security software, and utilizing biometric authentication methods. With the right safety protocols in place, your company enjoys increased performance while offering optimal protection from threats such as malicious attacks or natural disasters.
Five Security Strategies for Securing Business Operations
As a business owner, it is important to keep operations secure. To help with this, five key strategies exist that can be employed to help safeguard operational security. These include developing a plan of prevention, leveraging best-in-class technology solutions, implementing multifactor authentication and other access control measures, monitoring activities on the network proactively, and providing ongoing awareness training and education to employees. Each of these strategies offers valuable protection against potential cyber threats while maintaining the productivity of staff throughout their day-to-day operations. If you are looking to maximize your protection against digital intrusions or other malicious activity in your company's environment, consider adopting each of these strategies for success.
Best Practices for Developing Secure Passwords
Secure passwords are an integral part of keeping personal information safe and secure. To ensure strong security, it is important to practice best practices for creating secure passwords. This includes utilizing a mix of uppercase and lowercase letters, numbers, and symbols as well as avoiding dictionary words or phrases. Keeping passwords unique from account to account is also important; recycling the same password across multiple sites can leave all linked accounts vulnerable to attack. Additionally, passwords should be changed periodically, especially if there has been any suspicious activity on the particular account in question. Following these strategies will help keep user accounts secure while providing confidence that personal information is protected.
Steps for Setting Up an Effective Firewall
Firewalls are an essential component of any computer system's security setup as they protect a network from unwanted intrusions. To ensure that a firewall is effective, it is important to take some key steps when setting one up. First, it should be ensured that each user who has access to the system has their own unique login and that the passwords are regularly changed. Secondly, it is advised to set up multiple levels of authentication so that access to different levels of data can be controlled. Additionally, it is important to limit users’ privileges in order to further secure sensitive files, applications, and information like credit card numbers or other financial data. Finally, using an app with security features such as logging who is entering and exiting the system is encouraged. These measures will help to keep a firewall properly configured and secure against malicious actors and possible vulnerabilities.
How to Monitor Access to Sensitive Data and Digital Assets
In the digital age, it is essential to monitor access to sensitive data and digital assets. Organizations should incorporate practices that play an integral role in safeguarding these resources. To start, organizations should continuously analyze their networks for system vulnerabilities, take active measures to patch them, and routinely update authentication requirements to ensure that only legitimate users are granted access. Additionally, monitoring solutions or third-party vendors can be leveraged to detect any changes in network activity or suspicious user roles that seek out privileged data from another user's account. By establishing processes and procedures to track where data is stored, who has access, and when it changes, companies can better protect their sensitive information and digital assets.
Cybersecurity is a vital part of protecting any business, no matter how small. With the ever-evolving landscape of cyber threats, it can be hard to stay ahead of the game and ensure that your company is secure from attacks. By following best practices like staying on top of password security and setting up an effective firewall, you can make sure your sensitive data is kept safe. Additionally, monitoring access to digital assets and training staff on the importance of data security are both important measures businesses need to take in order to remain secure. In a world where digital security threats are likely to continue to grow, having a comprehensive cybersecurity strategy in place is essential for keeping your business safe and operating effectively.
0 notes
Text
Data Backup in Digital Commerce: Its Assessment

For the majority of cyber threats and ransomware attacks, e-commerce companies are the main targets. This is mostly because the information they hold, manage, and use, such as client data and financial transactions, is sensitive.
Compromise of data in the world of digital business can result in severe financial loss, permanent reputational harm, or even a complete halt to operations. In order to secure company continuity by swiftly retrieving data, firms need to have a strong data security plan and make routine backups.
For both big businesses and tiny online shops, this blog illustrates the significance of data backup. Learn more about how to protect your data by reading on to find out about typical dangers, various backup techniques, and platform-specific issues.
Types Of E-Commerce Data
Large volumes of data are collected, managed, stored, and used by e-commerce websites. Also, you need to understand how digital commerce helps the company. The most important data types for company operations must thus be known to store owners and security managers in order for them to be given top priority in backup plans.
Product catalogs: This is all the information related to products, including descriptions, prices, images, quantities, inventory status, and more. Product data is necessary to maintain daily operations, ongoing sales, and customer satisfaction.
Customer information: Personal details about your clients, such as names, phone numbers, email addresses, and physical addresses, in addition to order history, payment information, and preferences. Losing this data can cause serious compliance issues as well as reputational damages.
Sales records: Sales transactions are mainly used to perform accurate financial reporting and inventory management. These records include payment information, customer data, and transaction history.
Website content: The collection of files and folders that make up an e-commerce website, such as images, web page content, and product descriptions. If this data is compromised, your entire website may stop working properly or shut down entirely, which in turn causes downtime and decreases customer satisfaction.
Important Elements In An E-Commerce Website
For your customers to have a smooth buying experience, your online store is made up of a number of components that interact with one another:
Databases: Most of your information is collected in pre-structured databases provided by the e-commerce platform that you are using.
Custom code: You can add custom code to edit your theme or website.
Themes: All e-commerce website builders provide themes you can use and customize to build your online store.
Asset directory: This is the media library in which you keep your images, videos, and other media.
Products and content: Informative website pages such as guides, blogs, and product descriptions help improve your ranking in search engine results.
Accounting and finances: This is the collection of inventory, customer information, and orders used by the accounting department to keep track of your operations.
It is necessary to perform complete backups now and then to ensure business continuity by protecting all of these elements since they are the building blocks of your website. If one of these elements fails, it can jeopardize your entire store and halt your operations.
Common Threats To E-Commerce Data
Knowing the various data kinds and e-commerce components you work with now, you should educate yourself on the dangers that might result in data loss. These threats might be categorized as either internal or external dangers.
Theme Code Editing
In modifying your theme code, mistakes are quite easy to make. Even a minor mistake might significantly harm your business by damaging your user experience or interfering with consumer activity. Before releasing your new code into the production environment, make sure to test it. Also, you must be able to roll back your modifications if necessary, ideally via restoring backed-up data.
Integrating With Third-Party Applications
While creating or modifying an online store, it is typical to install or integrate third-party software. Do not forget that these applications were not developed by the e-commerce platform itself, but rather by other firms. The platform's app store is where you should download them from if you want to be secure. Although it may result in certain undesirable changes, this does not ensure that the program you installed will integrate well with your website.
Human Error
One of the most frequent causes of data loss is this. Important information such as theme components, items, or blogs might occasionally be edited or deleted by employees, which can cause problems throughout the online business. The creation and use of erroneous CSV imports is another error that occurs frequently in digital commerce. Data backup must thus be balanced in priority because it is the best way to undo changes or retrieve lost data.
View the full article here : The Importance of Data Backup in Digital Commerce
0 notes
Text
Employ these 12 software tools to digitize your business.

Businesses must employ software to better digitize their workflows and processes. There is a wide range of software applications available that can help businesses automate tasks, improve communication, and increase productivity. However, with so many options available, it can be difficult to know which tools are right for your business. To help you out, we've compiled a list of 12 software tools that every business should use to digitize their operations. Read on to find out more.
Introduce the 12 software tools that can help digitize your business
If you're looking to unlock the full potential of your business, it is important to consider digitizing your operations. Fortunately, there are 12 reliable software tools you can use to help you achieve this goal. From documentation and back-end bookkeeping to inventory management and customer relationship tracking, there are offerings available to help streamline almost any process or issue. These solutions are designed to make life easier for today's entrepreneurs and small businesses, enabling growth and facilitating organizational optimization. Utilizing such initiatives will open new opportunities while reducing the traditional administrative burden experienced by many companies in their daily operations. The time has come to take your business into the digital world and reap the rewards offered by these powerful software tools.
Describe how each tool can be used to streamline processes and increase efficiency
By utilizing the right tools, processes can be streamlined and efficiency can be increased. For example, certain software programs provide an automated system that can perform tasks that would have been completed manually, meaning processes can be quickened without sacrificing quality. Project management tools provide another avenue to increase efficiency by helping assign tasks and keeping track of their progress in real-time. Additionally, analytics are available to measure productivity and identify any areas of improvement needed. Overall, using the right tools optimizes the workflow process for maximum efficiency and a successful outcome.
Offer tips on how to get started with using each tool
When attempting to master the use of new tools, it can be quite daunting. However, there are a few simple tips that can make the process easier. First, take some time to get familiar with the format, layout, and main functions of your chosen tools. For example, if you plan to use a content management system such as WordPress, learn about its dashboards and various functionalities. Second, if possible seek out online tutorials or guides that can help walk you through these functions in an easy-to-follow format. Thirdly and finally, consider taking advantage of forums where users who have gone before you are able to share any tips and tricks they have learned along the way - chances are somebody out there has faced a similar challenge before. With these steps and guidance from experienced users, your journey into using the new tools should be made much simpler and enjoyable.
Share stories of businesses that have successfully employed these software tools
It is no secret that businesses across the world are utilizing software management tools to streamline their operations. Numerous examples of successful case studies have emerged in the last few years that illustrate how these tools have been effectively employed to help organizations improve their overall efficiency and productivity. For instance, an international research team recently conducted an extensive study featuring dozens of companies which found that utilizing digital task boards led to a 31% decrease in the time spent on project coordination. Similarly, a financial consulting firm achieved drastic reductions in its customer service costs after implementing a cloud-based Knowledge Base platform for its team members. These are but two stories among many which demonstrate the power of software management tools in today's rapidly changing business landscape.
Encourage readers to try out these tools in their own businesses
Successful businesses are a combination of many elements, from having the right resources to motivated employees. Taking advantage of modern technology can be a tremendous help in different aspects of operations. Fortunately, there is an abundance of tools available that could prove beneficial to entrepreneurs and business owners. These include analytics, cloud computing services, customer management applications, data-gathering tools, and many others. Given the potential to achieve higher efficiency and improved productivity, it is highly recommended that entrepreneurs explore these technologies and incorporate them into their businesses if possible. Doing so can lead to significant improvements that have long-term effects on success.
0 notes
Text
4 Methods to Prevent Data Leakage

There are many ways for data to leak out of an organization, and it can be difficult to prevent all of them. However, there are some common methods of data leakage that organizations can guard against. In this blog post, we'll discuss four of these methods and how you can prevent them.
Use data encryption methods to protect your information
With the prevalence of digital information and social networks, protecting the data you store on your devices is becoming increasingly important. Thankfully, using data encryption methods can provide a much-needed layer of security to any device. With these methods, any data can be turned into incomprehensible code in order to protect it from unauthorized access, which helps to ensure that personal files remain secure and private. Most popular operating systems contain built-in encryption options that make it easy to utilize this capability without needing extensive technical knowledge or resources. Data encryption is an effective tool for keeping your information secure, so if you have yet to implement encryption measures, now is definitely the time to do so!
Create access control measures to restrict who can see certain data
In order to ensure the security of data, implementing certain access control measures is an essential step. This will help to restrict who can view certain sensitive information. Access control measures such as designing policies to determine user roles and permissions, installing firewalls to control internet traffic, and establishing encryption techniques that protect stored information can all help secure data. Creating these levels of access protection helps create a more secure environment for data that needs to remain confidential or separate from other sources. Ultimately, with the proper access control measures in place, the risks associated with data leakage are minimized.
Implement activity logging to track user behavior
Activity logging is a proven and effective way to track user behavior. It can provide a digital history to assess user trends, which can be harnessed for marketing purposes. Through activity logging, organizations are able to gain insights into which of their products and services are popular with customers, as well as observe customer preferences and their journeys from discovery through to engagement. Implementing activity logging not only allows businesses to identify patterns in user behavior but also enables better decision-making by having key information stored in one place. Activity logging is thus an invaluable tool for understanding today's customers and maximizing returns on investments.
Educate employees on proper data handling procedures
Educating employees on proper data handling procedures is essential to maintaining organizational security. Without instruction on current industry best practices, employees pose a risk to the organization's confidential information, internally and externally. Knowing how to properly utilize and protect data can help ensure that high standards of security and privacy are upheld in order to prevent malicious actors from accessing it. Having an understanding of acceptable use policies and technical safeguards such as encryption is key in today's digital-driven society. Investing in employee data education will greatly reduce the chances of being targeted by cyber threats.
Data protection is essential in any organization. Without taking the proper precautions, sensitive data can be vulnerable to malicious attackers or careless employees. By following our steps, you can ensure that your information remains secure: encryption, access control measures, activity logging, and educating employees on data handling practices. It is our hope that by implementing these methods you will feel more confident in the security of your data and rest easy knowing that there are safeguards in place to protect it. In this digital age where data privacy has become increasingly important, ensuring that your data is kept safe should be a top priority for any organization or individual.
0 notes
Text
The 3 Best Technology for the Task in Addressing App Fragmentation and Siloed Communication
There are many technologies available in the market that can help organizations with addressing app fragmentation and siloed communications. In this blog post, we will be discussing the three best technology for the task. These technologies are Microsoft App Manager, BlackBerry Application Suite, and good old email marketing. Organizations can use any of these technologies to manage app fragmentation and communicate with their employees more effectively. All these solutions have their own set of features and benefits that make them unique and ideal for addressing app fragmentation and siloed communications respectively. Let us take a look at each of these technologies in detail.
The Three Best Technologies for the Task in Addressing App Fragmentation and Siloed Communication
Although technology can often be complex and difficult to manage, it should also be used to make communication and applications easier to manage. By utilizing the best technologies for addressing app fragmentation and siloed communication, teams can easily collaborate with each other toward a common goal. These three technologies include low-code development platforms, integrative software solutions, and automated testing systems. Low-code development platforms are powerful tools that allow organizations to quickly build custom enterprise software. Integrative software solutions provide a unified environment by connecting different information systems that typically operate in isolation from each other, breaking down communication barriers between different departments or teams. Automated testing systems increase app reliability by running numerous tests on various systems without needing constant manual review. These three technologies help bring together teams in order to break away from the inefficient siloed conversation and instead focus on tackling the task at hand.
How these Technologies Can Help Address App Fragmentation and Siloed Communication
An increasingly complex technological landscape is making it hard for organizations to provide a unified customer experience across all of their apps, as app fragmentation and siloed communication has been on the rise. By utilizing modern technologies such as identity graphs, AI-powered search capabilities, and analytics solutions, companies can create a more unified experience for their customers. With these technologies in place, customers no longer need to switch between multiple apps - instead, they can access all the information they need through one unified platform. This not only helps reduce customer frustration but also reduces costs associated with maintaining different interfaces. All in all, these technologies offer organizations the tools necessary to tackle app fragmentation and siloed communication head-on while providing better experiences for their customers.
What Else You Can Do to Address App Fragmentation and Siloed Communication
App fragmentation and siloed communication continue to be a growing challenge for businesses, but there are additional measures that can be taken to reduce its impact. It is important to create coherent structures of technology and open collaboration across departments. Having processes in place that contribute to the ease of communication can bring teams closer together while reducing app fragmentation. Establishing user journeys and policies such as data reuse principles provide guidance on how different silos can interact in the application development process while also encouraging data sharing. Creating designated tools used by all teams makes it easier to centralize the implementation of new technologies, eliminating unnecessary duplication. Regular review intervals will help manage continual improvements needed as the IT landscape evolves. Employing these methods should empower organizations to gain better control over their apps, minimizing any further impact of app fragmentation and siloed communication.
In conclusion, it is clear that addressing app fragmentation and siloed communication with technology is possible. When implementing such technologies, the benefits are clear - from improved device performance and greater efficiency to improved security and user experience. We can all use the three best technologies - app portability, API calls, and server-side architecture - to address app fragmentation and siloed communication. Furthermore, there are other actions we can take to reduce app fragmentation too. For example, by creating relationships between IT and US personnel, enhanced communication capabilities such as process automation, AI chatbots, or customer relationship management (CRM) software can be deployed. Ultimately, when it comes to addressing app fragmentation and siloed communication - a combination of technology implementation paired with alternative teams will help ensure that companies get the most out of their available resources while boosting efficiency in the workplace.
Reference: App Fragmentation & How To Avoid Siloed Communication: 3 Right Technologies for The Job
0 notes
Text
How Can I Increase My Laptop's Gaming Performance? | Use Our Advice To Speed Things Up!

If you're a PC gamer, there's nothing worse than a laggy laptop. Games can stutter, FPS can drop, and it generally ruins the experience. So what can you do to increase your laptop's gaming performance? Here are a few tips. Use our advice to get your games running smoothly again.
Check for updates to your graphics drivers
Staying up-to-date with the latest graphics drivers is essential for keeping your computer in tip-top shape. Not only can it help improve graphics performance, but having access to the newest features that they offer helps keep you ahead of the game. Taking a few minutes each month to check whether any new updates are available and downloading them could be the difference between getting a superior gaming experience or spending hours trying to troubleshoot problems. For dedicated gamers, checking for these updates can make all the difference in how much enjoyment they get out of their hobby.
Close any unnecessary programs running in the background
Employing modern technology to the fullest extent often requires more than the simple performance of everyday tasks. It is essential to take proactive steps to ensure that your computers and devices are running optimally. One of the best steps you can take is to shut down any unnecessary programs running in the background. These superfluous programs can not only slow down your device but also endanger its security. To protect yourself, make it a habit every time you log on to analyze what programs may be impacting your device’s performance, and then promptly close them in order to keep your computer running efficiently and securely.
Allocate more RAM to your games
When it comes to gaming, there are some instances when allocating more RAM can give you a much better gaming experience. Whether this involves streaming high-definition video or playing complex video games, a greater amount of RAM will be required to carry out these tasks efficiently. Not only does this help when it comes to smoother gameplay and improved graphics, but it can also allow your gaming device to support several titles without the need for further upgrades or purchases. Allocating more RAM for your games isn't just about having fun; it's an investment in your future gaming success and satisfaction.
Adjust your power settings
Optimizing your energy efficiency can save you money and help the environment. By adjusting your computer's power settings, you can regulate its electricity usage to ensure that it does not draw too much energy when in use or when in sleep mode. Additionally, properly configuring your system will protect its hardware from long-term damage due to overheating. Furthermore, by enabling automatic updates and powering down devices when not in use, you can increase the longevity of your computer's components while being mindful of your environmental impact. With small adjustments, you can utilize green practices while running a sustainable and efficient computer.
Clean out your laptop's vents and cooling system
Taking good care of your laptop is essential for maintaining peak performance. This includes regularly cleaning the internal vents and cooling system, as dust and other debris can clog the machinery and affect the laptop's ability to cool itself. To clean out these components, open up the laptop lid (making sure it's powered off) and use a soft brush to rid the interior of dirt or build-up. You can also use compressed air in a canister to blow away excess particles inside the laptop. Taking preventative measures such as this can help ensure that your laptop runs smoothly for years to come.
With the five steps outlined in this blog post, you are now equipped with the knowledge needed to improve your laptop's gaming performance. It can be a daunting task to make sure you've got all of the necessary updates applied and background programs shut down, but by completing these tasks you will be well on your way to boosting your laptop's gaming abilities. Furthermore, don't forget about allocating more RAM, adjusting your power settings, and taking the time to clean out any vents or dust from your laptop's cooling system. By following through with every single step mentioned in this article, you are sure to greatly enhance your computer's gaming potential.
Reference: How to Improve Gaming Performance on Laptop? | Make It Run Faster With Our Tips!
0 notes
Text
The Top 12 Productivity Apps & Software for 2022

Managing projects becomes simple with the greatest productivity software. You can efficiently monitor both in-office and remote teams while assuring superior outcomes.
Task management and collaboration functions are available on the user-friendly interface of the majority of productivity applications. It assists managers in establishing organizational objectives and in updating staff members.
With a little investigation, choosing the best productivity tool may be simple. The simplicity of using unified communication and file sharing tools will be appreciated by you and your team.
By using these top 11 productivity tools in 2022, you can create a seamless working environment. Don't lose out on this chance.
Top 12 productivity software and apps this 2022
It's crucial to reevaluate if this strategy still aligns with your objectives in a society where working hard is the norm. Keep your to-do lists short and cheerful, and stop rushing to complete tasks before deadlines. But how can you establish an effective work cycle without jeopardizing your health?
There are methods to leverage internet tools and programs that are accessible on desktop and mobile devices to boost your productivity at work. You can define goals, coordinate resources, and collaborate productively with the help of these programs.
You can discover the top 11 productivity tools in this post to make your daily job more enjoyable.
1. Google Workspace
Business Starter Plan: $6 /user per month
Business Standard: $12 /user per month
Business Plus: $18 /user per month
Manage multiple teams and projects with Google Workspace.
Formerly known as G Suite, Google Workspace is one of the top productivity software that has all the essential tools needed for individuals and organizations.
Every Google Workspace plan includes project management tools and business apps for individuals and organizations. With core apps like Gmail and Google Meet, you can quickly relay messages and set up meetings on one platform. In addition to swift company updates, this software has excellent productivity tools that enable multiple people to edit any document simultaneously.
Signing up with Google Workspace allows you to share schedules with your team and send reminders for upcoming events. You’ll find that this productivity tool has everything you need whether you’re a solo entrepreneur or own an enterprise.
Pros:
Most enterprises use Google Workspace because it has a built-in office suite ideal for all their project management needs.
Flawless real-time document editing.
It allows up to 300 users in one admin account.
Cons:
Poor file management in Google Drive. When integrating with many members, organizing files can pose a challenge.
It doesn’t include a free plan for team collaboration. The free subscription is only available for single users.
Offline editing is only available on Chrome and advance plans.
2. Trello
Trello is one of the popular free productivity software available.
Trello is a visually stimulating task management software that uses the Kanban board approach. It allows teams to create boards, cards, and lists to organize tasks in a rewarding way. You can customize each panel to fit your working style by moving items to different progress points. For example, you may label a column “In Progress,” “For Validation,” and “Completed Tasks.”
With Trello, team members can discuss projects by adding comments, due dates and casting votes on ideas. If you need to save time, you may use an automation Butler command that moves and archives cards automatically
Pros:
It’s user-friendly and easy to learn without the steep learning curve.
It integrates with over 100+ tools like Google Drive, Slack, and Jira.
Small scale businesses enjoy using Trello because it allows unlimited users on a single board. All you need to do is invite your members via email.
Cons:
It’s only ideal for small projects. You may opt for Teamwork productivity software if you’re managing complex projects.
Limited storage space.
It doesn’t include any reporting and time tracking tools.
3. Zoom
Basic: Free sign-up for meetings up to 40 minutes
Pro: $149.90 per year per user that can host up to 100 participants
Business: $199.90 per year per user that can host up to 300 participants
In today’s hybrid workspace, companies are looking for reliable team communication tools to meet their employees virtually. Zoom brings teams together, providing remote conferencing services through their cloud platform. It features live chat functionality, screen sharing, calendar integration, and international calling. Their high-quality, scalable system ensures that you and your team won’t miss important meetings.
Zoom makes it easy for attendees to watch an event on desktop and mobile without signing up for an account. For that reason, you to live-stream any meeting or webinar on your Facebook page.
Pros:
It’s one of the top-performing video communication platforms for small and large businesses.
Companies find Zoom mobile and desktop app convenient to join meetings on the go.
For people who aren’t tech-savvy, Zoom has an easy-to-use system that allows users to download and install the program with just a few clicks.
Cons:
Although Zoom allows people to message each other in the chat box, it lacks the option for users to control inappropriate comments.
There are some instances where people crash Zoom conference calls.
HD Video doesn’t come with the basic plan. You’ll need to subscribe to higher plans to get HD video quality.
4. Clockify
Freemium Plan is available.
Basic Plan: $3.99 per user/month
Standard Plan: $5.49 per user/month
Pro Plan: $7.99 per user/month
Enterprise Plan: $11.99 per user/month
Tracking attendance for onsite staff and remote teams has never been easier with Clockify. It allows individuals and managers to monitor work hours and projects from any location via GPS.
This time-tracking software lets employees start and stop the clock as they work. Depending on the setting, they can also manually input their hours. Hybrid teams find Clockify useful because it has a calendar that allows individuals to block time for tasks. So you can organize your schedule better, focusing on specific assignments at a time.
Aside from timekeeping, this productivity tool has an intuitive dashboard, making it easy for users to learn. The panel interface includes employee work reports to review your team’s shift, earnings, and activity. Thus, there’s no need to use a different app for invoicing labor; Clockify automates billable hours accurately for you.
Pros:
Users can create automated customizable invoices to help minimize payment delays.
This time management app includes 40+ integrations with other programs like Quickbooks, Trello, Google Calendar, and Asana.
It has a free forever plan that provides sufficient features for growing businesses.
Cons:
The HR management team may have to manually log Paid Time Off (PTO) since Clockify doesn’t include PTO management features.
Users may experience lag on Clockify mobile app.
The screenshot and mouse idle tracking features are only available for paid plans.
Reference : Top 12 Productivity Software and Apps this 2022
0 notes
Text
12 Best Remote Working Tools for Managing Work From Home

You now see why businesses are making such a big deal out of work-from-home or remote working technologies!
Millions of individuals and companies are being impacted by the Covid 19 epidemic on a worldwide scale as a result of lockdowns, market closures, suspension of company activities, and other measures.
The globe is suffering from this pandemic in various ways, including financially and personally. The idea of working remotely or from home has become quite popular among corporations throughout this crisis.
The use of remote working tactics by enterprises as a result of limits and safety precautions has left businesses perplexed as to how to manage their employees' productivity and efficiency.
But there's no need to fret or panic because we have the greatest tools for managing remote work from home and how it will help your company.
Best Remote Working Tools
Here, we offer some of the top work-from-home solutions from many categories so that you may handle remote working and support the expansion of your company during these challenging times.
Work From Home Productivity Tools
Trello
Trello is a well-known collaborative task management application that offers a straightforward interface to assist you in allocating, monitoring, and organizing your daily tasks or projects.
It enables managers and team leaders to delegate tasks to their teams and monitor each person's development. Along with supplying work information and directions, you can also verify the completion time and date. It is among the greatest solutions for managing remote teams.
Google Online Suite
The Google online suite may be thought of as the online equivalent of Microsoft Office, allowing users to create, share, access, rate, modify, and give feedback to other users.
You may use it to do presentations, datasheets, papers, hangout discussions, disk storage, and other things. With this solution for remote teams, team collaboration and sharing are simple and possible in real-time through the Internet.
Microsoft Office 365 Backup
You can easily include automated data backup into your everyday processes with NAKIVO's Microsoft 365 backup. By keeping data backups locally, the NAKIVO solution enables you to prevent the loss of your files, channels, tabs, posts, and other Microsoft Office data. Office 365 data may be quickly recovered and returned to its original place.
Reference : 12 Best Remote Working Tools To Manage Work From Home
0 notes
Text
Microsoft 365 Data Loss Prevention: Exploring its Capabilities and Limitations

Microsoft 365's data loss prevention capabilities are a key selling point for many organizations. However, it is important to understand the limitations of these capabilities in order to make sure that your organization's data is adequately protected. In this blog post, we'll explore Microsoft 365's DLP capabilities and discuss some of the potential limits.
Introduce Microsoft 365 Data Loss Prevention and its capabilities
Microsoft 365 Data Loss Prevention (DLP) is a powerful tool for companies of any size that want to protect their sensitive data from unauthorized access and theft. It helps prevent sensitive information, ranging from credit card numbers to intellectual property, from accidentally being shared with external entities or malicious actors. With DLP, monitored content is instantly filtered, quarantined, and blocked if it matches a defined set of parameters and conditions including keyword, content type, file name, or extension. Additionally, users can receive notifications when they attempt to share confidential information and give them options on how to proceed. By providing detailed analytics on usage patterns and enforcement policies, Microsoft 365 DLP enables businesses to proactively control the lateral flow of sensitive data across their networks much more efficiently and effectively.
Discuss the limitations of Microsoft 365 Data Loss Prevention
Microsoft 365 Data Loss Prevention is an incredibly powerful security solution for businesses looking to protect their sensitive information. However, there are still certain limitations that should be taken into consideration before selecting this software as a security provider. One of the biggest downsides of Microsoft 365 Data Loss Prevention is its lack of customization options. This means that while it can perform automated filtering and control access through certain policies, they cannot be tailored to your exact needs which may not suit all organizations. Furthermore, the pricing structure can be a deterrent for many small businesses that may prefer more affordable solutions due to their tight budget requirements. Despite these potential issues, however, Microsoft 365 Data Loss Prevention does remain an effective security solution for those willing to invest in the program and properly utilize its functions.
Offer tips on how to work around these limitations
When people are presented with limitations in their work or tasks, it can sometimes seem overwhelming or difficult. However, there are various methods that can be employed to overcome these obstacles. Working collaboratively with colleagues and divvying up the different components of a project is one such tactic. This helps to break down potentially daunting features into more manageable chunks and spread the workload out evenly. Additionally, considering the use of technology to aid in time-consuming tasks like administrative or organizational work could help streamline processes and save time over manual solutions. Setting achievable benchmarks to measure progress is also beneficial as it will allow individuals working within their own limits to stay on track and ensure performance standards are met. Finally, regular breaks from the task at hand can both boost morale and generate new ideas for problem-solving.
Conclude with a summary of the pros and cons of using Microsoft 365 Data Loss Prevention
Microsoft 365 Data Loss Prevention provides organizations with substantial benefits, such as accurate information intelligence, risk-based policies, and stable data protection throughout its entire infrastructure. On the other hand, it also has some disadvantages that organizations should consider when deciding if this solution is a good fit for them. Chief among these is the cost involved with setting up and maintaining the system, although enterprises that have considered an investment in protecting sensitive data have found that this solution pays for itself many times over. Microsoft 365 Data Loss Prevention features may also be too comprehensive for smaller companies that do not require all of its features, making customization an additional challenge to employ it. It is essential to weigh your organization's needs thoroughly against the pros and cons of using this platform before making a decision to use it.
In conclusion, Microsoft 365 Data Loss Prevention is an effective way to keep critical information secure. It offers built-in encryption, governance, and visibility controls that can ensure your data is stored securely. While there are some limitations in terms of its usability, especially for users who aren't familiar with Office 365 apps and tools, these can be overcome by providing more resources and training for users. With regular maintenance and preventive measures like password protection and multi-factor authentication enabled, Microsoft 365 Data Loss Prevention can give organizations the confidence that their data is safe from potential threats. Ultimately, while there are positives and negatives associated with using Microsoft 365 Data Loss Prevention, it remains a powerful tool in the effort to protect sensitive information.
0 notes
Text
Securing Your Business During the Second Wave of COVID-19

As the world grapples with the second wave of COVID-19, businesses have to once again find ways to operate safely while maintaining security. Businesses must ensure that they are taking all necessary steps to protect their data and networks from potential threats. Here are some tips to help you secure your business during this uncertain time.
1. Implement a cybersecurity strategy: Businesses should take proactive measures to protect their systems against cyberattacks by having an effective cybersecurity strategy in place. This includes ensuring strong passwords, two-factor authentication, regular software updates, and antivirus protection, as well as monitoring for suspicious activity on your network and backing up important data.
2. Educate employees on cybersecurity best practices: Businesses should educate their employees on best practices for cybersecurity, such as using secure passwords, recognizing phishing scams, and avoiding suspicious links. Businesses should also ensure their employees are aware of the importance of data security and train them to adhere to the company’s cybersecurity policies.
3. Stay informed: Businesses should stay abreast of any new threats or vulnerabilities that may affect their operations by subscribing to cybersecurity alerts from reliable sources. Business owners can also subscribe to industry publications or newsletters to keep up with current trends in cybersecurity.
4. Invest in cybersecurity solutions: Businesses should invest in effective solutions such as firewalls, encryption software, and intrusion detection systems to protect their networks against cybercriminals. Business owners should also consider hiring a reputable IT security firm to help them implement these solutions and stay up-to-date with the latest cybersecurity technologies.
By following these tips, businesses can take proactive steps to secure their networks and protect their data during this uncertain time. Business owners should remain vigilant when it comes to cybersecurity and ensure they are taking all necessary measures to keep their operations safe from potential threats.
Pandemic waves affecting business
operations, data security, and cybersecurity are not going away anytime soon. Businesses must stay ahead of the curve in order to maintain their reputation and protect their valuable assets. By following these tips, businesses can ensure they remain secure during this difficult period.
Decisive strategies in place
businesses can remain secure and protect their reputation during COVID-19 and beyond. Business owners should make sure they understand current cybersecurity trends and have an effective cybersecurity strategy in place to safeguard their networks against potential threats.
With the right security measures in place, business owners can confidently move forward with their operations knowing that their data is protected from any potential cyber threats. Businesses must prioritize security now more than ever before in order to keep themselves safe during this second wave of COVID-19.
Smart change matters
Businesses must make sure to stay up-to-date with the latest changes in cybersecurity and ensure their networks are secure. By taking proactive steps to protect their data and investing in effective security solutions, businesses can confidently move forward with their operations during this uncertain time.
The key is to always be prepared and take all necessary measures to protect your business from potential threats. Business owners should consider these tips when looking for ways to secure their systems during the second wave of COVID-19. With the right strategies in place, businesses can remain secure and continue operating safely in this difficult period.
Consider diverse income sources
Businesses should also consider diversifying their income sources to protect themselves from economic downturns. Business owners can look into other revenue streams, such as online sales, subcontracting services, or virtual events. By having multiple sources of income, businesses can ensure they remain financially secure during these challenging times.
In conclusion, businesses must be proactive in securing their networks and protecting their data during the second wave of COVID-19. Business owners should make sure to stay informed on current cybersecurity trends and invest in effective solutions that will keep their systems safe from potential threats. Businesses should also consider diversifying their income sources to protect themselves from any potential downturns. With the right strategies in place, businesses can remain secure and move forward with confidence during this uncertain time.
0 notes
Text
Top 10 Best Data Recovery Software of 2021: A Complete Overview and Comparison Guide
Data loss is a nightmare for anyone who relies on their computer for work, school, or just everyday life in general. If you're not regularly backing up your data, then you're at risk of losing important files if your computer ever crashes or is otherwise damaged. Thankfully, there are lots of great data recovery software programs out there that can help you get your lost data back. In this blog post, we'll be taking a look at the 10 best data recovery software programs of 2021 and comparing them side-by-side to help you choose the right one for your needs.
INTRODUCTION: Define data recovery software and its purpose.
Data recovery software is a specialized program that can help recover lost or inaccessible files from hard drives, flash drives, and other types of removable media. It is designed to scan for recoverable files and allow users to recover them by offering options for either restoring them or recovering them in their original, unmodified form. With the right data recovery software, users can restore photos, videos, documents, messages, and all other types of digital data that may have been deleted accidentally or become corrupt. Data recovery software gives users the ability to minimize chaotic losses due to events such as system crashes and malware attacks while saving time in the file recovery process.
EaseUS Data Recovery Wizard
When it comes to finding dependable data recovery software, EaseUS Data Recovery Wizard has earned its place among the top 10 best data recovery programs of 2021. Offering comprehensive solutions for lost file recovery, as well as versatile scheduling capabilities, this program offers users both accuracy and reliability. Additionally, EaseUS Data Recovery Wizard includes a wide range of extra features such as support for specific file types, customizable filters based on the time span of the lost files, advanced search capabilities, and even the capability to check files prior to recovery to ensure their accuracy or condition. With customer reviews praising its ease of use and accuracy, this is an excellent choice for all your data recovery needs.
Disk Drill
If you’re looking for reliable data recovery software, then Disk Drill is definitely worth a look. Featuring powerful scanning capabilities, this software easily and quickly finds lost or deleted files without complex workflows. It offers support for hundreds of file types, making it the perfect solution to recover documents, photos, audio and video files, deep scans and previews for results analysis, non-technical user interfaces for easy access and management of multiple drives, etc. In addition to these features, it also provides advanced protection against data loss with its built-in MRE technology as well as backup functionalities allowing you to create an emergency file recovery plan. Therefore with its impressive features list, Disk Drill is undoubtedly one of the best data recovery tools available in the market today.
Recuva
Well known as one of the most reliable and efficient data recovery software, Recuva offers its users a wide range of features and fixes to restore their corrupted or lost files. These features include powerful scanning methods that enable users to find the source of their lost files, deep scan options for locating hard-to-find files, pause/resume support for saving on time, secure overwrite function that destroys all traces of recovered data, support for dozens of file types such as documents, archives, emails, images and more. Furthermore, Recuva is extremely user-friendly with its easy-to-navigate interface and lightweight design. The intuitive wizard helps users in every step from installation to recovering their lost data without any hassle. With Recuva's amazing technology and wide selection of features, anyone has the ability to recover their precious data quickly and safely.
Stellar Data Recovery
Stellar Data Recovery offers an all-in-one data recovery solution, providing you with options ranging from free scanning to paid solutions to recover lost or deleted files. Its powerful scan engine and sleek user interface make it one of the most efficient data recovery software tools around. With this software, users can quickly recover data from a wide range of storage media, including external hard drives, flash storage devices, and even digital cameras. Stellar Data Recovery has been making waves in the industry for its comprehensive support for multiple file systems and intuitive menus for easy navigation. It also comes with an enhanced Preview option so that users can preview recovered files before saving them. All these features certainly put Stellar Data Recovery on the list of best data recovery software solutions in 2021!
MiniTool Power Data Recovery
MiniTool Power Data Recovery is a highly-rated option in the world of data recovery software for 2021. This software has an easy-to-use interface and offers 4 modules to select from, depending on the user's needs. With MiniTool Power Data Recovery, users can recover accidentally deleted files from hard drives, USB drives, CD/DVD disks, memory cards, and more. This software also includes advanced technology to scan deep on almost all devices and can effectively recover data before any damage is caused to it. The support team of this software is accommodating in answering every query promptly and with maximum efficiency. These features make MiniTool Power Data Recovery one of the best options available right now for data recovery solutions.
While we have only scratched the surface, this list provides some of the best data recovery software available on the market today. With varying price points and features, there is surely a solution for everyone's needs. Data loss can be a frightening experience, but with the right tools, it does not have to be permanent. Hopefully, this guide has provided some clarity and ease during what could otherwise be a stressful time.
0 notes
Text
10 Steps to Protect Your Operations from Cyberattacks on Logistics

Cyberattacks can have a devastating impact on logistics operations, disrupting supply chains and leading to sizable financial losses. Protecting your operation from these threats is essential to ensuring continuity of service for your customers. Here are 10 steps you can take to safeguard your business against potential cyberattacks.
1. Understand the types of attacks that can occur.
2. Know your vulnerabilities.
3. Establish strong security policies and procedures.
4. Train employees in cybersecurity best practices.
5. Implement security technology solutions across your operation.
6. Conduct regular risk assessments of your logistics processes.
7 . Monitor activity on all systems and networks 24/7/365.
8. Respond quickly and effectively to any incidents that do occur.
9. Improve your operations regularly through lessons learned.
10. Stay up-to-date on the latest cybersecurity threats and trends.
Educate your employees on cybersecurity threats and how to recognize them
One of the most important steps to ensure operations and logistics remain secure is education on cybersecurity threats. All employees should be informed of the risks that can come with using internet-connected devices, including what a threat looks like and how to respond if one is detected. Investing time in educating employees on these topics will go a long way in deterring cyberattacks. Proactively training employees about policies, procedures, and protocols associated with their work can also assist in identifying suspicious behavior or anomalies to keep the organization safe from cyber attackers. Teaching your team proper password maintenance, emailing etiquette and the importance of doing virus scans can be valuable tools in ensuring operations stay secure.
Implement a data security policy that includes encryption and password protection
It is critical to protect your operations from cyberattacks on logistics by implementing a data security policy. Such a policy should include strong encryption methods to protect sensitive data, along with robust passwords that need to be regularly changed and updated to maintain the highest levels of security. Furthermore, for ultimate protection, consider using a two-factor authentication system, as this greatly reduces the possibility of unauthorized access. Taking proactive steps to secure sensitive information with policies such as these makes it much more difficult for malicious actors to successfully attack your operations.
Conduct regular cyber audits of your systems and networks
To protect your operations from cyberattacks on logistics, it is essential to conduct regular cyber audits of your systems and networks. This thorough review process helps identify vulnerabilities, evaluate the strength of existing defenses, and take precautions against potential threats. Audits enable you to maintain control over data security and access while sensitive information remains secure in real time. Regular cyber audits allow businesses to assess the areas that need updates or improvements, making them an invaluable asset for the proactive management of network security.
Install firewalls and intrusion detection systems
Taking proactive steps to ensure the security of your logistics operations is essential in this digital age. To protect against cyberattacks, installing firewalls and intrusion detection systems should be the first priority. Firewalls help prevent unauthorized access to networks, while intrusion detection systems can detect and alert users to suspicious or malicious activity. With these measures in place, businesses can gain visibility into potential threats and reduce potential disruption from cyber attackers. Taking the time to properly secure operations will lead organizations towards long-term assurance that their data is protected.
Use secure communications protocols
In this digital age, the use of secure communication protocols is essential in protecting your operations from cyberattacks on logistics. According to the 10 Steps to Protect Your Operations from Cyberattacks on Logistics, utilizing secure protocols helps open a direct dialog between your businesses’ IT systems and retailers, customers, shipping providers, or any other party involved in your operations. Additionally, encrypting transmissions further enhances the security of communication networks and exchanges. Establishing protocols that are tailored to your business needs will go a long way to minimizing cybersecurity risks and safeguarding your operations.
Restrict access to sensitive data
In an increasingly digital world, protecting sensitive data is of vital importance. Establishing rules for limiting access to logistical data is a key step toward ensuring the security of operations against cyber-attacks. Restricting access based on the privilege to only those who need it can go a long way in reducing the risk of any unauthorized attempts at accessing this information. It should also be coupled with other control measures such as multifactor authentication and secure guidelines governing access rights and privilege assignments within your organization. By doing so, you can ensure that your operations are well-protected from potential cyber threats.
Taking these steps will help to ensure that your company is protected from cyberattacks. By encrypting data and restricting access to sensitive information, you can make it difficult for hackers to obtain the information they are looking for. Installing firewalls and intrusion detection systems can also help to deter attacks. Educating your employees on how to recognize cybersecurity threats is another important step in protecting your business. Regularly conducting cyber audits of your systems and networks can help you identify vulnerabilities so that you can take action to fix them. By taking these measures, you can help protect your company from costly cyberattacks.
Reference : 10 Steps to Prevent Logistics Cyber Attacks and Protect Your Operations
0 notes