#Once all this maintenance is hashed out the GOAL
Text
PROMPT #6: Ring
"Livvy," said Zero, so quietly that she almost hadn't heard her amid the bustle outside Meghaduta.
"Yeah?"
Zero's face was characteristically hidden by her wide-brimmed hat, but Ahtyn could make out the barest trace of a frown underneath. "I believe my linkpearl may be broken. If you would be willing to assist me, I would be in your debt."
"Pffft." If the maintenance and repair of linkpearls was a matter of debts, the Garlond Ironworks would not be facing nearly as many financial challenges. "Don't worry about it. You can just treat me to some more curry later."
Zero nodded - almost immediately - and dropped her linkpearl into Ahtyn's palm. Almost at once, it gave a chirp and a small vibration.
"It has been activating almost constantly. I have found the command to silence it, but if I were to do so, I would not be informed of messages from you and your companions. Given the urgency of our tasks, that would be unacceptable."
Ahtyn examined the linkpearl from the outside. For all intents and purposes, it was identical to her own: the same make and model as the one Minfilia had given to her nearly ten years ago. "Looks like all the bits are where they should be. You haven't dropped it, or anything?"
"Not that I can recall."
"Gotcha. So from here, the first step that most people will tell you is to turn it off and back on again, but let's be real, we don't have time for that."
Zero tilted her head in confusion. "Is it not worth an attempt?"
"Nah, it's fine." She brought it a little closer to her face. "Mind if I check some of your inbox? I promise I won't look at anything private - I just want to see if there are actually messages coming through every time you get a ping, or if it's alerting you to nothing."
"You may look at whatever you would like."
There was a lesson in there somewhere about friendship and trust, and how there were some friends (like G'raha) to whom she could show her entire search history without any negative repercussions, and some friends (like Urianger) with whom she would sooner never speak again than show a single saved image on her tomestone, but Ahtyn was too distracted to make it into a coherent point. Zero's inbox was in shambles.
"How many people have you given this number to?"
Zero had to ponder this question, which was not a good sign in this context. Ultimately, however, she said, "Only the Scions. And one formidable hunter of elite marks."
"That's it, then. Looks like whoever they are, they've signed you up to a hunt linkshell."
"A hunt linkshell?"
"Not a very good one; there's way more chatter than callouts happening." Ishgardian court drama, complaints about aetheroil prices, dispatches from the Quicksand, and a recurring stream of lines and hashes made to look like fat cats. "I think it's safe to mute this until we're back from the void for good."
"I see."
Ahtyn pressed a few buttons to mute the awful linkshell but did not yet hand it back to Zero, as she could sense that the reaper had more questions. "Linkshells can be handy for meeting people, especially people with shared goals or interests. But they can be a bit too much for me. All it takes is one annoying person to ruin the vibe, you know?"
To her credit, Zero nodded in immediate understanding. But of course - she herself had been something of a leader of her own little community in the void. "You are not in a linkpearl for meeting other women?"
For a moment, Ahtyn's brain went completely empty. "Uh, no," she stammered. "No, I prefer to meet people more… organically."
"Organically?"
"Like, I want to get to know someone in person before I talk to them."
"Strange," said Zero. "I would think that talking to someone is the only way of getting to know them."
"I mean to date! Dating is way different from friendship, and I've always felt most comfortable being friends with someone before I think of them as a possible romantic partner."
"Like Zenos."
The only emotion she could summon was a deep relief that none of the others were around to hear. "…There are lots of reasons why Zenos and I would never have been… romantic partners. But in theory? Yeah. Sort of like that."
Again Zero nodded. She held out her hand for her linkpearl, and Ahtyn returned it. As the reaper walked away, evidently deep in thought, Ahtyn filed away a mental note to make a few long overdue calls.
18 notes
·
View notes
Text
When we discuss state power and these things, we need to hold onto multiple ideas at once. Yes, we are discussing actions like Israel’s aggression in Gaza. Yes, we will discuss the United States, the global American Empire, and its allies and conspirators. It’s impossible to chart the history of these concepts and their consequences without relying on these specifics.
But as we do so, we must also grasp that nation states are also representations of a larger process at play. The United States, for instance, has been the main front for global capitalism since it took over the responsibility from Great Britain following World War II. That union of capitalism and the nation state means that notions of “conventional politics,” or the belief that we are simply watching two parties “hash out their differences,” obfuscates what is often happening below the surface. Developments often feel bewildering because we’re part of a process that is intentionally mystified, leaving us wondering why principles and promises are so often jettisoned.
Here this: the intertwining of capitalism and nation states means that our politics, our culture, and our institutions have been co-opted to carry out actions that are counter to the national interest, or at least the interest of us, the citizens, in favor of achieving goals that are beneficial to the interests of capital.
An example: our military and intelligence agencies tirelessly cooperate with capitalist interests in arranging outcomes on the latter’s behalf, oftentimes hurting the nation state and its citizens while setting the table for the wealthy and powerful to become more wealthy and more powerful.
In this way, a momentum has built that ensures, regardless of what happens politically, the process will continue. That process is aided by politics, aided by culture, and certainly aided by technology, including computing and now A.I.
Barack Obama, who promised Change in his transformative campaign, found himself, when in power, subject to forces he felt beyond his control. In that presidency, which was won in part with a promise to wind down George W. Bush’s war, Obama oversaw a wild expansion, including the usage of drone strikes that grew by nearly ten times under his watch.
The usage of drones, and the growing list of targets Obama habitually signed off on, represented that momentum we have been discussing. Drones replaced troops, creating an operation we could actively ignore as Americans as long as our sons and daughters were kept out of harm’s way, laying a framework for a hegemonic oppression we would experience, if we experienced it at all, from a grand distance. The list and resulting killings was eventually reduced to bloody maintenance. Bruce Riedel, an analyst for the CIA and a counter-terrorism adviser to Obama, likened the operations to lawn maintenance, telling The Washington Post, “You’ve got to mow the lawn all the time. The minute you stop mowing, the grass is going to grow back.”
Our War On Terror coincided with the final collapse of our social safety net. Hurricane Katrina and the Financial Collapse made it obvious that our government had no interest in meeting the needs of the people and had been reprogrammed to solely serve the needs of the wealthy. In the past this co-option had been hidden, marginally at least, behind economic growth and supposed progress, but the truth of neoliberalism was coming to bear. That which had been done to nations around the world in the name of American control had been done on behalf of neoliberal capitalism masquerading as the U.S. We had been promised never-ending progress, luxuries, and dominance. But, as it always does, the oppression boomeranged around and met its originator. It became obvious that American Empire had always been a front for something else.
Turning this ship around and getting past this crisis depends on a massive sea-change of philosophy, governance, and culture. Reining in Tech, taxing its benefactors, and reasserting government oversight of industry and decision-making processes is absolutely vital. The momentum has kept that from happening and brought us here. A.I. is simply a vehicle is accelerating to the next stage in this ugly evolution.
As configured, there is no way that the state or any states will choose not to harness these technologies to these ends. It is too tempting. Too built into the system as it presently works. The nation state, even as it recognizes the co-option by neoliberal capitalism, has no choice but to trudge forward. It’s like an insect or an animal consumed by a parasitic disease. Still walking. Still trampling. Still serving.
And the time is now also because, as previously mentioned, these things will be leveraged against us and against dissent. When that happens, the words “terrorist” and “insurgent” will be more than enough cover for whatever an algorithm needs to protect itself and the process it serves. Because opposing the momentum of the zombie state pits you directly on the other side of the gun. Of the drone. Of the robot dog.
2 notes
·
View notes
Text
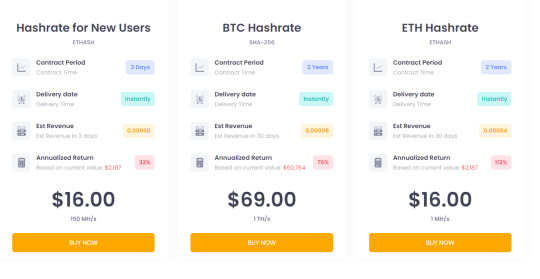
High-quality Used Asic Miner For Sale Zeus Mining
WhatsMiner M30S++ 112T is essentially the most environment friendly and powerful ASIC mannequin manufactured by MicroBT of their whole WhatsMiner product line. The maximum hashrate that can be achieved using the M30S++ 112T model is 112 thash/s with an influence effectivity of 31 j/T. This powerful WhatsMiner M30S works on the SHA256 crypto algorithm and runs on an influence provide of 3472 watts. MicroBT also supplies a 12 months of guarantee in case any sort of maintenance is required after the sale of an ASIC miner. “High energy price has at all times been an impediment to profitable mining for a lot of. If you might be tired of shedding your time and hard-earned cash on power-hungry mining rigs, ASICRUN is right here for you.
This overly simplistic watermill analogy has many technical points however is an efficient start line for a basic understanding. On a 30A PDU with a L6-30P and two 20A built-in branch circuit breakers, two S9's can plug into one department circuit and the final S9 can plug into the opposite department circuit. The first department circuit breaker may have a present draw of 13A, the second department circuit breaker may have a current draw of 6.5A, and the entire present draw at the L6-30P plug shall be 19.5A. The 80% rule is revered for both branch breakers and every thing upstream. To simplify PDU choice, there are two primary issues for compatibility along with your setup.
The first time you run EasyMiner, it enters 'MoneyMaker' mode which lets you automatically create a paper Litecoin pockets and start mining instantly with a non-public pool. While convenient, it isn't more likely to generate excessive income at the present issue price. Still, as evidenced by the E9 and other crypto ASICs, manufacturers have found methods round these limitations. With such vitality bills, the device’s daily operational value is projected at simply $7.80, while its day by day earnings reach $37.23.
https://horizonminers.com/faq/ are delivered throughout the globe within simply seven days. The firm additionally offers complete guarantee protection for all hardware and software issues. The best approach to mine digital currencies at present is using specialised digital forex mining machines known as ASIC miners. Like most know-how, mining hardware will probably continue to get more powerful and environment friendly at the identical time.

Since the primary goal of any miner is to make a great profit, the choice of an ASIC device have to be taken critically. The first step is to choose a hashing algorithm supported by the ASIC. Then, you have to take notice of the ASIC miner’s computing power (hash rate) on which mining efficiency and total profit depend. Due to its slim focus, ASIC equipment is ten occasions extra productive and energy-efficient than video playing cards for mining. With their assist, finding a hash to create a new block, with the subsequent reward, is way faster.
First of all acquiring them is hard they usually don’t include any warranty. Once ETH switches to PoS you need to swap it to other coin that uses the identical algorithm. Here are few other ASIC miners that are out there available in the market right now. Ethereum being a second largest cryptocurrency and contemplating it can nonetheless be mined using GPUs it presents a fantastic opportunity for residence miners and crypto enthusiasts. Sure, if you obtained the proper ASIC miner then go ahead and mine coins like BTC, LTC and DOGE. But if you're a GPU miner then ETH is the best coin you could mine in 2021.
That’s why it’s all the time a sensible idea to have the location checked out first earlier than making any financial decisions as as to if you should pursue mining Bitcoin. Ethereum's Proof-of-Work mining algorithm is designed to be ASIC-resistant. Basically because of this using an ASIC shouldn't be helpful enough to warrant the excessive value of ASICs. Heatsinks take up nearly all of the real estate of your common ASIC miner. They are big blocks of aluminium designed in such a means as to draw warmth from the chips, usually screwed to either side.
#bitmain antminer s19pro#bitmain ka3#bitmain antminer s9#bitmain firmware#bitmain kda miner#bitmain l7#bitmain miner#bitmain s9#bitmain antminer s19#bitmain antminer s19 xp#bitmain antminer s7#bitmain antminer z9#bitmain e9#goldshell#goldshell kd6#goldshell miner#goldshell kd5#goldshell miners#goldshell kd max#goldshell mining#goldshell sc box#ibelink#ibelink bm-k1 for sale#ibelink bm-k1#ibelink bm-k1+#ibelinks#ibelink bm k1#ibelink bm-k1 +#ibelink bm-k1 max#ibelink bm k1+
1 note
·
View note
Text
What Is Asic Mining & How Does It Work?
Block 786,729 used greater than two billion nonces from one mining pool. The goal hash, used to determine mining difficulty, is the number miners are trying to solve for once they mine. This number is a hash generated by the network converted from hexadecimal to decimal type. In this case, the number you selected, 19, represents the goal hash the Bitcoin community creates for a block, and the random guesses from your mates are the guesses from the miners. If you think about the time and money you want to make investments so as to mine a selected cryptocurrency, then it is in all probability not value investing in a USB ASIC miner to diversify your portfolio. However, should you purpose to mine crypto with the assistance of a USB ASIC miner, research the choices obtainable and discover a product that can supply much with less.

user coins geometry dash -hand asic miner at zeusbtc.com give you something that not only make your transactions secure but additionally comfort. We sell high-quality used ASIC miners to the world at the lowest worth and inspect every miner before shipment to ensure that clients receive high-quality mining tools. But free supply and tax-free buying are solely a half of the explanation to choose on Millionminer.com on your ASIC miner purchases.
Each block accommodates a set of transactions the miner has validated and confirmed. The first miner to successfully clear up the cryptographic puzzle and create a new block is rewarded with a set quantity of cryptocurrency. This process is called “mining” and is important to the operation of the cryptocurrency community. Model Antminer K7 (63.5Th) from Bitmain mining Eaglesong
The Antminer Silencer is an attachment that matches instantly onto the exhaust fan of an Antminer device. It’s designed to channel the airflow in a means that reduces turbulence, which is a primary source of noise in fans. Along with common cleansing and maintenance, that may do the trick and allow you to get pleasure from your ASIC miners at maximum efficiency for several years. ASIC miners are expensive machines, so you should take excellent care of them to avoid spending lots on replacements. Luckily, there are some practices to make the most out of your miners. This concern on the coronary heart of the Bitcoin protocol is known as scaling.
Circuits are rated based mostly on the utmost ampere rating of the overcurrent safety device (OCPD), sometimes the circuit breaker. Therefore, the derated capacity of a circuit is simply 80% of the present ranking of the circuit breaker. A circuit with a 20 amp breaker has a capability of sixteen amps, and a circuit with a 30 amp breaker has a capability of 24 amps. For example, if the whole current demand of a twin input miner is 14A, each input will only draw approximately 7A of present. You merely click on a button to begin mining and click a button to stop the whole course of. GPU mining provides better returns than CPU mining, however they are nonetheless less than what an ASIC miner would supply.
As we step into 2023, the landscape of crypto mining continues to evolve, with new ASIC fashions offering unprecedented energy and efficiency. Although cryptocurrency mining isn't as widespread as a number of years in the past, it plays an essential role within the industry and (still) makes a lot of money for miners. In the meantime, both WhatsMiner M30S++ or Antminer S19 Pro are the most favored choices amongst Bitcoin miners.
The goal of BeginCoinMining is to make Bitcoin mining simpler to grasp and extra accessible for all. Mining requires cautious planning and a focus to keep away from unlucky outcomes. All computer systems are a possible fire hazard, and this danger is magnified in mining due to the fixed usage and high power outputs involved.
#bitmain antminer s19pro#bitmain ka3#bitmain antminer s9#bitmain firmware#bitmain kda miner#bitmain l7#bitmain miner#bitmain s9#bitmain antminer s19#bitmain antminer s19 xp#bitmain antminer s7#bitmain antminer z9#bitmain e9#goldshell#goldshell kd6#goldshell miner#goldshell kd5#goldshell miners#goldshell kd max#goldshell mining#goldshell sc box#ibelink#ibelink bm-k1 for sale#ibelink bm-k1#ibelink bm-k1+#ibelinks#ibelink bm k1#ibelink bm-k1 +#ibelink bm-k1 max#ibelink bm k1+
1 note
·
View note
Text
Behind the Scenes: The Workflow of a Leading PHP Development Company

A top PHP development companydoes more than just write code. Their secret sauce for success is an intricate tapestry woven with various processes, teamwork, adherence to industry standards, and a steadfast dedication to continuous enhancement. Taking a peek behind the curtain can shed some light on how these top-notch PHP development companies get their edge.
Initial Steps: Planning & Consulting

The inception of a project in a PHP development company involves an initial phase of planning and consultation. This step allows the company to get under the skin of the client's business, to truly understand their target demographic, the competition they face, and their unique project goals. Detailed discussions around project features, the budget, deadlines, and other vital details are hashed out during this phase.
Renowned PHP development companies often organize multiple client meetings to grasp the full scope of the project's requirements. This understanding entails a thorough analysis of existing systems, the identification of potential hurdles, and the formulation of possible solutions. An in-depth market research process aids in understanding the market pulse and competitor strategies, feeding into a well-rounded project strategy.
Bringing Ideas to Life: Design & Prototyping
Once the plan is locked in, the top PHP development company dives into the design and prototyping stage. This phase breathes life into abstract ideas by crafting wireframes or low-fidelity mockups that present a visual representation of the application or website layout and elements.
Top-tier PHP development companies often adopt an iterative approach to design, ensuring that every facet of the design aligns with user requirements and client expectations. The prototyping process involves building a detailed, interactive model of the final product, which provides a sneak peek into its functionality, aesthetics, and user experience.
From Designs to Reality: Development
When a PHP development company moves from the design stage to the development phase, it's like setting code in motion. Front-end development is where the magic happens, giving life to the designs. It's about translating sketches into a real, interactive interface, employing languages like HTML, CSS, and JavaScript.
In contrast, back-end development is the hidden powerhouse of the application, working behind the scenes on the server side. This is where data management happens, and it ensures that all the features of the application function seamlessly.
Assuring Quality: Testing

A key player in the workflow of any best PHP development agency is Quality Assurance (QA) and testing. This phase certifies that the application is bug-free and aligns with the quality benchmarks established during the planning phase.
Testing is an elaborate process comprising several layers, including unit testing, integration testing, system testing, and user acceptance testing. The best PHP development companies often employ a blend of automated testing tools and manual testing to ensure thorough coverage. The collaboration between QA engineers, developers, and sometimes even clients is vital to swiftly identify and resolve issues.
Going Live: Deployment
The deployment phase signifies the application's journey from a development environment to a live setting. It's a critical phase that PHP development companies must navigate with care. It involves important steps like server configuration, database management, and the actual launch of the application.
Top-tier PHP development companies typically utilize Continuous Integration/Continuous Deployment (CI/CD) pipelines to automate numerous deployment tasks. This practice fosters a consistent environment and smooth transitions between different stages. Documentation is also a key component of this phase, offering essential guidance for future maintenance and updates.
Maintenance & Support
Maintenance and support aren't one-off tasks; they continue long after the project has been launched. A leading PHP development company often provides various support packages to cater to different needs. They regularly monitor for bugs, performance issues, and security vulnerabilities while keeping the application updated with the latest software versions, frameworks, and security patches.
Innovation & Upgradation
Innovation and continual upgrading are key survival tactics in the ever-evolving tech industry. Top-notch PHP development companies don't simply deliver a project and wash their hands off it; they constantly seek ways to innovate and improve their services.
Researching new technologies, tools, and methodologies is an ongoing endeavor. These PHP development companies always stay updated with the latest trends, enabling their clients to leverage the most advanced solutions. Regular training sessions and workshops for team members foster a culture of continuous learning and innovation.
Conclusion
Let's be clear, it doesn't end with code. It's not just a technical exercise; it's about crafting solutions that resonate with the client's desires and needs. The secret formula to standing tall as the Best PHP development agency is far from singular. It's an artful blend of synchronizing various phases from integration of the latest technologies to commitment to quality.
#phpwebdevelopment#webdevelopment#php#phpdeveloper#phpdevelopment#phpframeworks#phpdevelopmentcompany#phplaraveldeveloper#webdevelopmentcompany#knightcoders#shivtechnolabs
0 notes
Text
Yall remember when I updated fics like, once a month? Damn those were the days!
#THE GOAL IS TO GET BACK TO THAT#Once all this maintenance is hashed out the GOAL#the AIM is to return to updating fics monthly!#or maaaaybe biweekly if I'm in a hurry to get something finished#okay! its very late and i need to go to bed!#avi.txt#fic talk#word blogging
3 notes
·
View notes
Text
Libonomy Blockchain
The evolution of Blockchain has opened doors for research and development in this field. Since Satoshi Nakamoto’s introduction of Bitcoin back in 2008 the world of technology changed completely. It gave the world a new advanced technology to explore. Blockchain system has evolved, from solving problems to keeping up with future development, the cycle has not ceased. The reason it has become a huge success lies in the nature of this system, where it is consensus based and works without intervention of any authority. Blockchain records data that is immutable, which is encrypted and given a unique hash. The hash of the previous block is connected to the hash of the new block. To solve the hash and add further data on the blockchain a consensus is reached among the nodes that are connected. Consensus protocols still have to face many problems and their latest solutions have also become a problem. POW, POS and DPOS have still failed to provide a solution for Byzantine General problem and double-spending. Blockchain is one of its kind blockchain systems that will use Artificial Intelligence at its core, with dynamic threshold, utilizing all the benefits of POW, POS and DPOS and introducing a whole new system which is much more transparent, decentralized , fast and robust.
Overview Of Libonomy

Libonomy is one of its kind blockchain that has achieved the goals of innovation and creativity with great success. The kind of innovation it advertises attracts and reaches out to masses that have the knowledge that the system is fulfilling its role of greatness. Many only talk about a new system of blockchain but Libonomy is on its road to fulfill that ideology already. The uniqueness of any organisation becomes its trademark and the uniqueness of Libonomy is that it offers its clients to explore beyond their imagination and think out of the box. The speciallty of Libonomy Blockchain is that it does not use the previous consensus algorithms that have been used for a very long time. These consensus algorithms have their own drawbacks and Libonomy believes in providing an error-free consensus engine that has been architectured carefully. It uses Artificial Intelligence consensus algorithm, an automated computer generated engine that saves energy, time and gives high speed of transaction. The system being generated through AI is safe from any human corruption and it is fully decentralized that it endorses complete transparency as well. The exclusivity of Libonomy is not the only commendable factor of it but the stability that it offers on its many platforms as well. Libonomy pioneers in providing safety and security to all its clients that use it with great trust. It is a cost-effective platform that believes in giving the best to its clients only. It saves the energy of resources and time of its clients so that everything is carried down effectively and efficiently.
Blockchain Technology
The working of the system is not too complex, an overview of the system needs to be addressed before moving forward to the technicalities of the system. When the nodes join the Libonomy Blockchain system, the AI will run its analysis on the nodes. The analysis is carried forward on the contribution and participation of the nodes in the blockchain. The data regarding the capability of how far the nodes are willingly taking part in the blockchain is gathered as well as the speed of the transactions and communication is gathered, all this information is combined to understand the nature of the nodes in the respective system. Once, the analysis is completed the data is transferred to the algorithm which then classifies the information depending on the nature of the nodes and assigns a pool to each one of them.
There are four different types of pool. The Power pool is the main pool where the transactions are verified and validated. There is Exploit Finding pool which runs a security check-up on the nodes to look for any issues with it, like its contribution in the blockchain. The Maintenance pool is a pool for all the nodes that are not assigned to any other pool and are associated as a backup. The Audit pool is assigned for the application of rules and regulations. When the nodes have been put in their respective pools, digital signals are passed to create a network, meanwhile the idle nodes are cut off.
There is no or less communication between blockchain with another blockchain. This creates hindrance in getting a connection across and expanding the horizon of the blockchain. Libonomy Blockchain has the feature of interoperability that will allow multiple blockchain systems to run under the umbrella of Libonomy blockchain.The Libonomy Blockchain can support public blockchain and private blockchain, both. Corporations and businesses can use the blockchain in their new business projects that can take the plan a step ahead in any sector of business. Government, education, health, identity management and many other sectors can integrate the blockchain in their organisations to make it easy for them to manage work with the benefit of stability and security.
Smart contracts are mostly implemented in blockchain to enhance the system, however, with Libonomy Blockchain the AI engine will verify and validate the smart contracts, creating them on their own keeping in the nature of nodes and the network in consideration. Libonomy blockchain technology provides its own blockchain SDK using which users can utilize the system in their own platform or build dApps on top of it, which are completely decentralized and cost-effective. The use-cases for Libonomy Blockchain are limitless and versatile because of the nature of the engine and the whole system bringing innovation and creativity together.
Components Of The System

Transaction Per Second
TPS of a node is modeled as an evaluation function that takes node properties, nature of the network and safety elements as its independent variable.
Computing Power Ratio
Computing power ratio is the ratio of calculating force of a node to calculating force of the whole network,.
Exploit Finding Nodes
EF Nodes guarantee the security of the network. These nodes will be put off the network if any false nodes are found in the power pool.
Maintenance Nodes
Maintenance Nodes are backup nodes that are pulled out and assigned into their respective pool. AI engine will kick out the nodes from either pool, in case of a corrupt node.
Audit Nodes
Audit nodes will carry out the auditing of the pool on a constant basis. If any of the power nodes fail to fall within the threshold assigned by the audit nodes, the node will be removed from the network.
Virtual Voting
Every node in the network can spread signed information to its randomly chosen neighbours. With virtual voting, each node can determine if a transaction is valid, block upgrade and threshold upgrade. Signal Passing Digital pulse is generated with each communication, which is pulse based message communication the fastest possible technique for better communication and achieving high throughput of the whole network.
Gossip Algorithm
Multi-Layered Gossip involves attaching a small additional amount of information to a pair of gossip that contains the history about the nodes.
Power Nodes
These power nodes can be picked under a mechanism by an AI engine. The power nodes are namely classified into Lightening Nodes, Middle Nodes and Lower Nodes.
Neural Network
Neural Network is the main core used in this blockchain. It is inspired from the human brain, and neural network will help in classifying and clustering information. It will help in organising, storing and managing.
Network Proposal System
The network of Libonomy Blockchain is explained below, to grasp the working of the system.
The AI consensus engine will generate dataset of the nodes consisting the analysis of their performance, strength in being part of the blockchain and history of any activity in the algorithm.
After the dataset is received it is then passed on to the prediction algorithm.
The training of the machine takes place in a learning algorithm which is Neural Network based on the dataset received from the nodes that are connected to the network.
The Neural Network is being used to make predictions and dynamically classify nodes into their respective pool with dynamic threshold, as defined by the state engine of the blockchain.
The network has become a distributed network with high speed communication and data transfer. The transaction per second of this network is highly competitive against other known networks.
The High Speed Autonomous Blockchain is taken into consideration
Pulse based message communication is used for data writing and sharing on distributed ledger. Pulse based message passing is one of the most advanced techniques to transmit and receive messages.
Pulse Based message communication will keep the nodes dedicated towards the network.
There is a continuous communication taking place of large datasets of the nodes, while still not overloading the network with the requests.
Cryptographic hashing is still happening, while still maintaining immutability and perfect blockchain.
Multi Node pools are created for transaction verification, blockchain maintenance, and rules creation.
The system is avoiding hard forks, while allowing blockchain upgrades.
Gossip communication between multiple node pools is taking place for transaction verification and blockchain is upgraded.
Network is being upgraded and the blockchain keeps on scaling with a consistent architectural structure.
As the signals will pass the gossip protocol will be working to its full potential, then the Virtual Voting will utilize this information to upgrade the pools and data will be shared. Based on the rules accepted and generated by the AI engine and Pools, the State Engine Machine will maintain the system’s state and upgrade it dynamically.
The second stage begins with:
Public Blockchain Testnet is created which is identical to the software of the cryptocurrency, but does not disturb the main cryptocurrency software as it is an experiment.
All the nodes from all around the world are allowed to contribute to the network.
AI engine will keep maintaining the dataset for future upgrading of the blockchain and remove all the issues.
Application layer will be used to create DEX, smart contracts and other DApps.
X-Virtual Machine will be part of the blockchain system:
Virtual Machine compiler will run and build smart contracts and DApps.
It will allow auditing of smart contracts.
Software Development Kit (SDK) will be installed in one package for developers to use the blockchain.
The above implementation plan of the Libonomy Blockchain fully considers the operation needs of the development of consensus algorithms, the building process of a Blockchain with AI engine and the ability enhancement process of the Blockchain community, so as to make the Libonomy Blockchain available as soon as possible, popularize it in the community and carry out process. Also, gradual improvements will take place in the Blockchain through constant iteration and upgrade.
1 note
·
View note
Text
A Proposal
UPDATE: I have found a study buddy! :) If anything opens up in the future, though, I’ll let y’all know!
Hey, y’all! So, as the title suggests, I have a bit of a proposal for y’all. I’m curious to know if anyone is in the market for a study buddy. Just for accountability and all that. If you’re interested, read on!

Why a Study Buddy?
So, first things first: why exactly would you want a study buddy?
It’s lonely learning a language alone! Language is intrinsically social and sometimes, it can get hard motivating yourself to study when you have no-one to share the journey with. So, if you’ve been looking for someone to celebrate the little victories with and someone to vent your learning frustrations to, I’m your girl!
Accountability! Sometimes, knowing that you’ve got someone else who’s in the same boat as you is enough to keep you going. I for one know that I am way more motivated to do my best and bring my A-game if someone else is counting on me, so if you’re about having that extra incentive, keep on reading!
Friendship! If everything happens to work out nicely, you get the added bonus of having a new friend! Of course, this is just a bonus, so if you’re the type of person who just needs more of a professional study buddy, no worries! I’m down with that, too.
How This Would Work
As the specifics will be highly dependent on you (should you choose to accept this challenge), I’m thinking that we can just do some form of texting basically?Like, we can decide what platform you want to use and all that, but it’d basically boil down to once weekly or bi-weekly “official” check-ins where we can chat/text about what we’ve done (along with whatever fun side notes we want to share throughout the week). Basically, we can work out exactly how “official” we want this to be, but ultimately, we text, we laugh, and we work through any road blocks we might hit. Teamwork makes the dream work!
What I Ask from You
If you’re still interested in this whole thing, here’s what I would like to ask of you so that we can be good study buddies for each other.
Age range of 21-25. This is nothing against younger or older study buddies!! I just think that for my first go round, it would be nice to study with someone who’s likely in a similar place in life as I am. I’m more than open to chatting to anyone outside of this age range via tumblr, but for a study buddy specifically, it’d be really nice if we were in the same age range!
Comfortable in English. Sadly, I am very very monolingual (for now). As long as you’re comfortable with your English skills and don’t mind chatting with a native English speaker who (admittedly) throws around some weird wording from time to time, we’re good!
Still in the beginner(-ish) phase of Korean. That way, we’re really in the same boat and neither of us will get roped into playing the role of tutor. Remember, study buddy is the goal here!
Be flexible and understanding! I work, so sometimes my weekends get taken up with work events and sometimes my brain is simply fried by the time I get home. I promise that 99% of the time, I’m usually on my A-game, but I am only human, so there will definitely be times when I might be a little behind. Please be gentle, and I promise I’ll stick around!
Miscellaneous
Just in case you want a few extra details about me and where I am with Korean!
Currently on Level 1 of Talk to Me in Korean
From the US, so that’ll give you a range of what my time zone is
Like k-pop and k-dramas
Play video games (I’ve basically sold my soul to Bioware at this point)
Former band geek
Studied Latin for a while
Love fantasy literature
Super low maintenance friend/study buddy, so if you’re worried about this becoming a time suck, don’t! I promise I’m super flexible when it comes to time commitments!!
Introverted and a little awkward, but super well meaning!
And there ya’ have it, folks. If you’re still standing by the end of this and are willing to take a leap of faith on this, please hit me up (message, ask, whatever works best)! This is my first time as a study buddy, so there might be a few hiccups on my end as I try to settle into things, but I promise I’ll do my best to be a good study buddy for you! We can hash out any other details as we chat, too, so please don’t be afraid to drop me a note if you’re interested! Thanks so much for reading all of this, and best of luck with your language goals!!
15 notes
·
View notes
Text
MVU Cloud Mining: Best Bitcoin Alternative
If you choose to begin mining bitcoin or different altcoins, you want a huge funding in hardware and electricity. Or you can be counted on a cloud mining platform, which is the answer I’d propose these days. However, many of these web sites are genuinely Ponzi schemes, the place customers by no means get their cash back… So is MVU cloud mining legit?
MVU cloud mining: one of the best mining cloud mining platforms
MVU cloud mining targets consist of making mining simple, reachable and less costly to each new and superior users.
Click here to join in MVU cloud mining
MVU cloud mining statistics center
As usual, it’s tough to get any facts about their information center. Because a mining farm like theirs is probably to be the goal of malicious people. The solely element we can examine is that it’s a modern, hi-tech facility housing crypto-equipment. And it’s maintained through a crew of certified personnel to mine at maximum hash rates, besides overheating the equipment.

How does MVU cloud mining work?
While you ought to buy limitless contracts, it’s no longer the case. So if you determine to register on their site, you’ll be in a position to buy each year contracts to mine coins. And you can select the quantity of hash fee you prefer for every contract.
Basically, with the contract, you’re renting mining tools and computing strength from the company. And the enterprise will mine for you, giving you a share of the cash they mine.
You can begin with a very low funding to mine bitcoins. Just a couple bucks to supply it a try. But don’t anticipate to be a millionaire overnight!
Once you offered a contract, you can allocate your hash energy immediately to the mining pool you desire to serve in. So you can optimize your profit.
What about the MVU Cloud Mining payouts? Everything’s automated. And payouts take place as soon as a day. You’ll acquire your first payout the following day after finishing a purchase. And you’ll get day by day payouts afterward.
In addition, you can use the reinvest function. It lets in you to mechanically purchase an extra hash price as quickly as your stability approves it. The gadget will test your stability after every payout and use the quantity to add hash charge to your contract.
What cash can you mine at MVU Cloud Mining?
Of course, the most important coin reachable is bitcoin. And you can additionally mine ethereum, etc. However, you can’t mine quite a few cash with one contract on this platform. So you’ll want to buy a contract per digital currency.
Click here to see more details of MVU Cloud Mining
Is mining on MVU Cloud Mining profitable?
While you can locate lots evaluation on the profitability of cloud mining platforms, I commonly endorse doing the calculations via yourself. Indeed, the profitability elements you want to analyze preserve on changing. And the reply to this query relies upon on the coin’s price, the community difficulty, and the hash rate.
If you don’t understand how to calculate the income you can make, you can use the MVU Cloud Mining income calculator. But don’t forget about to add the upkeep expenses for bitcoin… And maintain in idea that your income relies upon on the trade prices and mining too!
But I got the refferral Link, which I can get free hashrate and 5% commision.
With the charge of crypto-currencies climbing, I anticipate that you can earn you extra than the rate of the contract. And if the coin you’re mining doesn’t collapse, you must be fine. But keep in mind you usually have the preference to purchase bitcoins. And I have the quality location to purchase bitcoin.
Are there MVU Cloud Mining promo code?
I didn’t locate a dependable supply for MVU Cloud Mining, unfortunately.
Click here to get free hasharte on MVU Cloud Mining.
Conclusion
Choosing a dependable and legit cloud mining internet site is challenging these days. While it’s continually a gamble, all the factors I may want to discover on the organisation and on the provider is good. And how can half of a million customers global be wrong? Therefore you can have faith MVU Cloud Mining to supply what they offer.
When you purchase one of their mining contracts, you’ll come to be a crypto-miner. And no longer the sufferer of a scam. Just seem at the cash piling up each day on your account wallet.
Concerning the earnings of cloud mining, you ought to absolutely take a look at yourself earlier than purchasing. And I won’t vouch for it in this article: I’m now not Nostradamus… But if you don’t have a load of cash to invest, you ought to reflect onconsideration on the use of this service. Because they take delivery of honestly low quantities to begin with. And you won’t have to fighting with find the money for hardware, software program or maintenance.
Also, if you begin with low investment, you can figure out to reinvest the cash you mined to enlarge your hash rate. I assume this is genuinely a pleasant characteristic to offer.
Finally, for these of you who have used MVU Cloud Mining, let me recognize what you notion about it below!
0 notes
Text
China’s leadership in the Bitcoin mining industry will be challenged
https://ift.tt/3f19gQw
China’s leadership in the Bitcoin mining industry will be challenged
If you talk about Bitcoin (BTC) mining, you have to talk about China. China has become a giant in the Bitcoin mining ecosystem with major mines and pools, quick, cheap labor and a majority control of the world’s hashing power. So, should you go set up a mining operation there? Do the pros outweigh the cons? Is China actually a threat to the Bitcoin ecosystem? Let’s look at the state of Chinese mining.
Back to the basics
In the beginning of Bitcoin, you could simply mine from your laptop or set up a few miners in your home to run the hashing algorithm. But as more miners started turning on and the Bitcoin mining difficulty rose, higher levels of computing power and electricity was needed to solve the equations and reap the reward.
Only a finite amount of Bitcoin can be mined — 21 million tokens — so as time goes on, it will get harder and harder to mine them. Miners continue to need better and faster hardware, which requires more electricity. Today, mining operations are moving to large data centers where thousands of miners run day and night.
Related: How to mine Bitcoin: Everything you need to know
Why mention all of this? Because when mining at a large scale, electricity costs, labor costs, the speed of acquiring new hardware and sustainability come into play if generating profit is the goal — and China has the advantage in nearly all of these areas.
The state of mining in China
At the end of 2019, China produced nearly two-thirds of the world’s hashing power. Even though cryptocurrency usage and exchanges are reportedly banned in China and Bitcoin mining was once in danger of being shut down, the government took an about-face and is increasingly embracing the use of blockchain technology in its major industries — and allowing Bitcoin mining to grow.
Related: US Bitcoin holders worry about Chinese control of the mining network
Bitcoin mining in China is a growing industry because labor costs are cheap, turn-around time is incredibly quick, and lead time and production costs are much lower, since the country is a hub for global trade. Since much of the hardware used to mine Bitcoin is made in China, miners can very quickly be upgraded. If you want to set up a data center fast with low overhead and expenses, do it in China.
Low electricity costs in the form of hydropower are available as well. Because Bitcoin mining requires so much electricity between powering the miners and powering the fans to cool the miners, a data center needs to get electricity as cheaply as possible. Hydropower in the Sichuan province is reportedly as low as $0.02 per kWh during the rainy season, and the Chinese government is now encouraging mining in this province so operations can take advantage of the hydropower plants there.
Related: Sichuan rainy season to give Bitcoin hash rate a much needed jolt
But only some Chinese mining operations run on cleaner, cheaper hydropower. Most run instead on coal, which is a dirtier and more expensive option. Of the main power sources today, hydro is the cheapest, at around $0.01 to $0.02 per kWh, with wind being another cheap option at $0.025 cents per kwh. Gas and coal are the more expensive options, at $0.03 to $0.035 cents (plus transmission costs and taxes). So, while labor and materials may be cheap, coal usage makes mining operations unsustainable from both a cost perspective and environmental perspective. Factor in the political instability of setting up mining operations in China, and you may want to look elsewhere.
Can China stay on top?
Anyone wanting to set up scaled mining operations are increasingly seeking out locations in Nordic countries, Canada and the United States. While these locations may offer higher start-up expenses and maintenance costs, the availability of sustainable, cost-effective electricity is proving to be a big advantage. Additionally, these areas are more politically stable, so there is less threat that the government will one day decide to shut down all mining operations. In fact, Canada deemed mining operations as “essential services” during its COVID-19 pandemic shutdown.
Related: Regulatory overview of crypto mining in different countries
This may be the reason why the world’s hashing power is shifting locations. According to a recent report, Chinese hashing power is decreasing compared with last year yet growing in other parts of the world.
Another reason for this decrease may be that Chinese mining was hit hard in 2020. The COVID-19 pandemic disrupted supply chains, causing new hardware to be significantly delayed in getting to data centers. In an industry where every minute counts, using slower, older miners for even a day longer means losing money and advantage. Additionally, China’s quarantine rules prevented workers from tending to their rigs, further disrupting operations.
Additionally, the third Bitcoin halving occurred this past May, cutting the mining reward in half and forcing miners to make significant upgrades to their hardware to stay competitive. Because it now takes twice as much hashing power to mine the same amount of Bitcoin as a year ago, mining operations have needed to not only upgrade, but make sure their energy costs were staying efficient. Following the halving, many miners around the world switched off because the endeavor was no longer profitable.
On top of it all, this summer’s monsoon season caused excessive flooding in the Sichuan province, leading to electrical shortages that cut up to 20% of the region’s hash rate.
Despite these significant setbacks, mining in China is sure to bounce back. But with other parts of the world embracing and encouraging Bitcoin mining, and with the greater sustainability offered elsewhere, we may soon see China’s place as the giant of the industry challenged.
The views, thoughts and opinions expressed here are the author’s alone and do not necessarily reflect or represent the views and opinions of Cointelegraph.
Philip Salter is the head of mining operations at Genesis Mining, the world’s largest cloud crypto mining operation, where he leads the software development, data engineering and research teams. Salter started his career as a software developer for BSI Business Systems Integration AG. Salter is an avid miner and crypto enthusiast based in Germany.
https://ift.tt/2UtCpuq
Bitcoin News
China’s leadership in the Bitcoin mining industry will be challenged
Wanna Win Some Free Crypto?
This is our favorite crypto casino... Check it out and get a free sign up bonus and daily crypto rewards!

The post China’s leadership in the Bitcoin mining industry will be challenged appeared first on ESA Token.
from WordPress https://ift.tt/3puoxOD
via IFTTT https://ift.tt/3oqtis8 https://ift.tt/3dTdjOi
0 notes
Text
3 Pros of Investing in Bitcoin and Other Cryptocurrencies

Top 3 ways of how to invest in cryptocurrency for beginners and experienced investors. In fact, there are only two ways to invest:
market speculation
mining
If you are a beginner, it will not be easy to figure out both the first and the second methods. But over time, it will become completely clear how to invest in cryptocurrency for beginners.
The third highlighted method is an “indirect” investment in cryptocurrency, since the investor has no interaction with it as such, but provides an opportunity for third parties to work with it “directly”. Find out how to invest in cryptocurrency on Binance and BitMEX.
1. Exchange speculation! Where to start, how to act, what income can be obtained?
The very scheme of investing in cryptocurrency through a purchase on the exchange is not as difficult to understand as it seems. In practice, an investment in cryptocurrency looks like this:
Choose an exchange.
Choose an asset.
Buy cryptocurrency.
Sell currency at a better rate.
You can sell everything at once. You can wait until a year passes and the price of the asset will increase several times. It all depends on whether you are focused on long-term or short-term investments in cryptocurrency.
Step 1: Choosing Exchanges
To begin with, all truly worthy exchanges are geared towards an English-speaking user. There are intermediary exchanges that offer to buy cryptocurrency on their Russian-language sites. For this, of course, you will have to give a percentage of each transaction. And the quality of the services provided, as a rule, is much lower than on the original sites. Do not forget about this when you need to find out how to invest in cryptocurrency for beginners. Therefore, ideally, of course, it is better to work immediately on well-known foreign exchanges with a good reputation without any intermediaries.
Step 2. Asset selection
Analyze the “behavior” in the market of each cryptocurrency, read the analytics and forecasts, and only then make a purchase. If you are taking the first steps, you can try with cheaper currencies to understand the principle of trading on the exchange. Investing in Bitcoin - the most expensive cryptocurrency today - is simply pointless. The first step in studying the question of how to invest in cryptocurrency - to learn how to feel the market and make independent forecasts - you can start investing "big" in bitcoins or try to take risks with promising new cryptocurrencies.
Step 3. Buying an asset
You can replenish your account on the exchange using electronic payment systems or with a bank card. For more information about registering and choosing a place to store currency, see the article “The best cryptocurrency wallet, how to choose?” To trade without any hitches, it’s better to get a few wallets.
Attention! Some exchanges accept exclusively “ready-made” cryptocurrencies to replenish their wallets, that is, they cannot be replenished through WebMoney. This, for example, is about Poloniex.
When the money is credited, you specify in the search the number of cryptocurrencies that you need and look for a suitable option in the results. Having selected it, send a request to the trader. When he confirms it, a transaction will occur.
Step 4. Selling an asset at a favorable rate
After the transaction, your wallet on the exchange will be replenished with the cryptocurrency that you bought. Further, you can continue to study the question of how to invest in cryptocurrency for beginners, or act in two ways:
Leave it on the exchange, and then later sell it as soon as you find a profitable offer. Withdraw it to your own secure wallet.
The first option is convenient only if you are making short-term investments in cryptocurrency and are going to sell it soon. It is not recommended to store electronic money constantly on exchanges, as they are often subjected to hacker attacks. And then, they are also not safe from the risk of bankruptcy, therefore it is better not to trust your savings to intermediaries.
The first option is convenient only if you are making short-term investments in cryptocurrency and are going to sell it soon. It is not recommended to store electronic money constantly on exchanges, as they are often subjected to hacker attacks. And then, they are also not safe from the risk of bankruptcy, therefore it is better not to trust your savings to intermediaries.
Your income level will depend on how much you are willing to invest and which trading strategy you choose. In the best-case scenario, investments in cryptocurrency bring up to 30% per month.
By the way, if you decide to figure out how to invest in cryptocurrency correctly, then know that it is not even necessary to immediately sell it. The longer you keep it in your wallet - the more it will grow in value. Time will work for you without any effort on your part. Then it will be possible to simply transfer cryptocurrency into regular money, having received several times more than they invested. And you can not translate at all, but pay with it for various operations. Already now it is accepted by many shop windows, shops, auctions, etc., and in a few years, it will probably be freely converted into everyday life. Wait and see…
2. We are engaged in mining - we open our own "farm".
Mining is the “mining” of cryptocurrency. You will receive it for infrastructure maintenance, that is, in the literal sense, to produce a new currency by performing certain mathematical calculations. The difficulty is that the miner needs to guess one hash from millions of combinations, which hundreds of his colleagues can try to do at the same time. Besides, the number of miners increases every year, so the mining procedure is complicated, and the reward is reduced. Full information about mining is contained in the article “What is mining in simple words?”, It will be useful to familiarize yourself with it.
Mining bitcoins on a regular PC will fail. And this is another fact that should be taken into account to understand how to properly invest in cryptocurrency. We need special farms with high capacities, minimal energy consumption, connected to electricity and the Internet around the clock. To create such a farm at home, you will have to purchase equipment for 2-3 thousand dollars. Since the amount is serious, some miners are combined into groups, work together, and then "divide" the income received equally.
3. Cloud mining as a form of mediation.
The meaning of cloud mining is to provide rental capacities for cryptocurrency mining. That is, the investor, in this case, directs direct investments in power, and not in bitcoins. It works indirectly with cryptocurrency, but nevertheless, it is precisely it that is the ultimate goal for miners who use its services.
So is it worth the risk or not?
Investing in cryptocurrency is undoubtedly a risk. Therefore, first, you need to figure out how to invest in cryptocurrency correctly. However, any investment activity is a risk. Do you not want to take risks? So, the profession of investors and big money is not for you. Today, the stage of cryptocurrency formation in the world can be compared with infancy. A lot of time will pass before it starts to decline. So today it’s too late to figure out how to invest in cryptocurrency. If you join this stream now, you have every chance of getting a high profit from cryptocurrency.
0 notes
Text
Original Post from Rapid7
Author: Bri Hand
Pen testers rely on a variety of methods to compromise their clients during penetration testing service engagements, but none are quite as fun as when they must don a disguise to blend in with their surroundings. So, in honor of Halloween, we thought we would celebrate by sharing a few of our Rapid7 pen testers’ costumed crusades. Did they trick employees into doing their bidding, or were they treated to proper security protocols? Read on to find out!
‘The Boy in Blue,” by Trevor O’Donnal
I’ll never forget the time we were penetrating a police department. We had finished our pillaging and left the building, but once we reached our rendezvous point, we realized our good friend Ross was missing. We tried to reach him on our two-way radios, to no avail.
As we started to panic, in walks Ross in full police uniform, including a police radio! He had to raid the clean laundry in the basement dressing room to get out of the building. We bowed before him because we weren’t worthy.
And yes, this was all in scope. The police chief had said, “Anything goes, short of killing or kidnapping someone.” He had a great laugh about it in the end.
‘Here Are Your Flowers,’ by Robert Stewart
I once did a physical social engineering engagement where I didn’t see a clear path into the customer’s office space. The receptionist was behind a locked door and used a remote speaker to talk to guests and let them in. All of the other doors into the office could only be accessed by a badge, and my attempt at cloning badges was unsuccessful. But I wasn’t giving up.
I did a ton of recon on the employees and after finding one woman on LinkedIn first, I tracked down her Facebook page using her name, location, and profile picture. Her Facebook page was public, which meant all of her personal details were available. I learned about her family, her habits, her hobbies, and her husband.
I devised a plan to show up as a flower delivery guy to surprise her with a dozen roses from her husband and a song to serenade her with in the office. I worked up my costume to appear like a delivery guy would, and got the receptionist to let me in. The employee was called from the back to the front desk, which was a bummer because I wanted to be at her desk, but I rolled with it. I gave her the flowers, sang, “You Are My Sunshine,” and finished with, “Love, Tony!”
Her response was a confused, “Tony? Who is Tony?!”
“Uh … I don’t know, that’s what the order said!” I replied, and promptly booked it out of there. As it turns out, the woman I found on Facebook was not actually the right person, despite the fact that they had the same name, lived in the same city, and looked very similar. Totally crazy.
Though I failed at getting into where I wanted to go, this is still one of my favorite engagements because of the way it ended.
‘Pizza Delivery!’ by Aaron Herndon
On a previous red team operation, we had recently completed our objectives remotely. Access to the network had been obtained, servers were compromised, and loot was exfiltrated. In the twelfth hour, our point of contact had an idea. He wanted us to infiltrate the physical security operations center (SOC) with either a plant or some type of attack. This operations center had its own entrance separate from the rest of the main facility entrances, making it possible to knock on the door and gain entry directly to the lobby attached to the SOC room.
Assuming the SOC facility would require badge and PIN access (which turned out to be correct) and that tailgating would not be feasible due to the center being a single room with a small number of employees who all knew each other, we decided to take a new approach: enter as the pizza man.
Using a uniform from a large pizza chain, we dressed the part. Then we ordered the SOC some lunch. The odd request was that we asked for an empty pizza box from the pizza chain, which they did provide. Inside this box was our laptop, equipped with a CrazyRadio PA device running the MouseJack firmware. On loop, the device would scan for vulnerable USB mice and keyboards to remotely inject keystrokes (a surprisingly common vulnerability due to the wide adoption of Logitech peripherals in the workplace). We configured our MouseJack payload to quickly open the run prompt, download a payload from the internet, and execute it, giving us remote access to the machine.
On the day of our attack, we approached with four pizza boxes and a bag with some two-liter bottles of soda. The top three boxes actually contained pizza, while the fourth housed our payload delivering machine. With our hands full, we banged our elbow against the door of the SOC room to get their attention. An intercom buzzed, and we were asked to identify ourselves. After saying we had a pizza delivery, the door quickly opened to reveal an excited employee.
We indicated that we weren’t sure who had ordered the pizza, but were told to come to this room for delivery. The SOC employee directed us into the room, allowing us to set the pizzas down. We spent a couple of minutes making small talk, letting our mousejacking attack go to work. Then, we mentioned that the bottom pizza was actually to be delivered to another individual at the company, and reclaimed our payload box, making a smooth exit.
Returning to our car, hearts racing from excitement, we quickly contacted one of the red team operators to see if the attack was successful. Sure enough, we had received a connection to our payload server and the attack launched. Unfortunately, the connection died four minutes into being used. Had they discovered our pizza Trojan horse? Did the employee shut their machine off to go indulge themselves in the food provided? We still do not know.
‘The Construction Worker,” by Leon Johnson
I was once part of a Red Team of three tasked with testing an energy company with three locations in three different cities. My assigned location was surrounded by an 8-foot barbed-wire fence to guard most of its service and Cat heavy equipment vehicles.
I started by driving by the site on the first day of testing, watching people arrive for work and leave to get an idea of what sort of activity this location had. I went to dinner, and when I came back around 9 p.m., I realized there was a business next door that allowed for cover after hours. I decided to jump the fence and walk around the property in the shadows as much as I could. My goal was to avoid getting picked up by any cameras and getting caught.
As I began checking the commercial vehicles for unlocked doors, I found that one had a laptop on the armrest inside. I got excited, as I was thinking of all the possibilities for what I could do with a laptop if I got my hands on it. The vehicle’s locked doors stumped me for a while until I realized the quarter window was unlocked. I was able to push it open, unlock the truck, jump in, and grab the laptop.
I sat there for about five minutes waiting to see if anyone had spotted me. When nothing happened, I tried to get into the laptop but struggled because I didn’t have any tools on me. I made a call to my point of contact and asked for permission to take the laptop, which was granted. I then slid it under the fence, jumped over to my rental car, and headed to my hotel.
I worked on the laptop all night, getting past the login first with Kon-Boot and adding a local administrator user. Later, I mounted the hard drive with Kali, as the drive wasn’t encrypted. I pulled up the local admin hashes off the PC and set up some malware so that when the box was booted up, it would call back to me and give me access when it was on.
The next morning, I broke back in and returned the laptop before employees’ shifts started so no one would suspect anything. I got a local administrator shell, but it died before I could do anything with it. So, I had to go back the next day and do it again. Once more, I briefly got a shell I was unable to do anything with.
I decided to go to an office of theirs and attempt to see whether I could clone some RFID badges so I could use them to gain access to the facility without having to jump the fence every night. It turns out, the location I cloned badges from was a shared office, and I was unable to tell who or where the cloned badges I obtained came from. In the end, none of them worked at the location I had been given permission to test.
At this point, it was the second-to-last day of the assessment, and I didn’t have everything I wanted. So, I decided to do it again but just keep the laptop and use it to get into the corporate network. This time, I got into a truck and put on a uniform someone left inside. I used this uniform to walk around the property and gain access to more trucks. I figured if I were seen on camera, I would look like a legitimate employee just doing some maintenance or say that if I were somehow found and questioned.
I also knew the laptop would now be reported stolen in the morning, which meant I didn’t have much time to work with, since they could have had a way to shut off access to it. I started taking a forensic clone of the system and decided to take a shower while it was cloning. When I came out, I saw the mouse cursor was moving and closing things! It became a fight for the mouse and keyboard at this time, and I ended up just disconnecting the network connection. I eventually got on the corporate network and gained local admin access on some other systems, which led to domain admin access. With that, I was able to do whatever I wanted on their network and systems.
That was fun.
Interested in learning more about how Rapid7 pen testers conduct their assessments? Check out our 2019 Under the Hoodie report.
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source
Author: Bri Hand This One Time on a Pen Test, Halloween Edition: An Ode to Our Favorite Pen Tester Disguises Original Post from Rapid7 Author: Bri Hand Pen testers rely on a variety of methods to compromise their clients during…
0 notes
Text
Constantinople Ahead: What You Need to Know About Ethereum’s Big Upgrade
Constantinople, ethereum’s next system-wide upgrade, is coming soon to a node near you.
Finalized August 31, Constantinople includes five different ethereum improvement proposals (EIPs). Once released on ethereum, the proposals will permanently alter the blockchain with a host of new backwards-incompatible upgrades.
This means that nodes — the network of computers that run ethereum software — must either update together with the whole system or continue running as a separate blockchain entity.
More formally known as a “hard fork,” system-wide upgrades have instigated a fair amount of drama in the past. Most notably, in the case that a portion of users don’t agree with the change, this may result in two different versions of the same blockchain running concurrently.
As dramatic as these things can get (having formerly resulted in a competing cryptocurrency named ethereum classic), most of the upgrades in Constantinople won’t be noticeable to average users. Indeed, described by independent developer Lane Rettig, the upcoming ethereum hard fork won’t feature any “big changes” for end users at all.
Characterized as primarily a “maintenance and optimization upgrade” by Rettig, Constantinople features small, yet highly technical, ethereum improvements to network efficiency and fee structure, as well as, upgrades that pave the way to ethereum’s hotly anticipated scaling roadmap.
Additionally, the hard fork includes changes to ethereum’s underlying economic policy, and the delay of the difficulty bomb, a piece of code programmed to activate what is known as the ethereum “ice age” in which new block creation on the network eventually slows to a complete halt.
As detailed by CoinDesk, the economic change has been the cause of contention, with conflicting views expressed by ethereum stakeholders in the months prior to the upgrade.
At press time, anxiety is continuing to brew among the networks miners that are faced with an impending pay cut following Constantinople. But still, achieving a balance between all stakeholder concerns, developers are confident that the upgrade will be broadly well received.
While a formal block number has yet to be finalized, core developers and clients are currently implementing, reviewing and testing the Constantinople code.
As ethereum trader Eric Conner told CoinDesk:
“Complex coding and testing takes time. And ethereum is live so it’s essential to be sure no changes are breaking.”
The new ethereum
The five EIPs set to be released in Constantinople are:
EIP 145: A technical upgrade written by two ethereum developers, Alex Beregszaszi and Pawel Bylica, EIP 145 details a more efficient method of information processing on ethereum known as bitwise shifting.
EIP 1052: Authored by core developer Nick Johnson and Bylica, EIP 1052 offers a means of optimizing large-scale code execution on ethereum.
EIP 1283: Based on EIP 1087, which was written by Johnson, this proposal mainly benefits smart contract developers by introducing a more equitable pricing method for changes made to data storage.
EIP 1014: Created by the founder of ethereum himself, Vitalik Buterin, the purpose of this upgrade is to better facilitate a certain type of scaling solution based upon state channels and “off-chain” transactions.
EIP 1234: Championed by Afri Schoedon, release manager for major ethereum client Parity, this upgrade is the most contentious of the batch, reducing block mining reward issuance from 3 ETH down to 2 ETH, as well as, delaying the difficulty bomb for a period of 12 months.
All in all, the changes include: code optimizations to improve processing times for developers; fairer pricing structures for changes made to smart contract data storage; a code edit making scaling solutions through state channels easier to occur on ethereum; and changes to ethereum’s economic policy.
Given these code changes are likely to shape the progress of the second most popular blockchain for years to come, Constantinople is worth taking a deeper look at.
Optimizing code
To begin, both EIP 145 and 1052 are targeted at improving network efficiency, by making changes to ethereum’s underlying virtual machine — the EVM.
Powered by software at the heart of ethereum, the EVM processes smart contracts into a series of ones and zeros also called bytecode.
Seeking to maintain the longevity of ethereum and optimize performance to better serve user needs, both EIP 145 and EIP 1052 seek to optimize the developer experience for smart contract developers specifically.
EIP 145 introduces native “bitwise shifting” functionality which is able to run through bytecode without relying on arithmetic operations such as multiplication and division. In effect, this means that the smart contracts underlying decentralized applications like CryptoKitties will be processed faster by the EVM.
Additionally, when smart contracts on ethereum are executed and called upon, EIP 1052 introduces an upgrade by which only the essential data of the contract code is checked rather than the entirety of the code itself.
Namely, rather than verifying the full contract, EIP 1052 makes it so a compressed line of code, or a “hash” can be verified instead, saving computing time and cost — especially for lengthy smart contracts that run on thousands of lines of code.
Cheaper storage
Further EIPs deal with how smart contracts are stored on ethereum — such as EIP 1283, which reduces the amount developers need to pay when building smart contracts.
As it stands, without EIP 1283, certain updates to smart contract code cost a hefty amount of gas, the computational unit of energy required to execute operations on the ethereum platform.
EIP 1283 implements a better cost analysis for contracts, by breaking down what contract changes have been written in ethereum’s short term storage, called memory, rather than the blockchain itself.
If none or a few of those updates end up on the blockchain, it reduces the overall cost for developers. As Johnson, the author of the original proposal concept behind EIP 1283 recounted to CoinDesk:
“In some cases in the past, we were charging gas for things that didn’t actually happen or didn’t actually cost any real resources and now we’re trying to adjust things so we only charge gas that aligns with the work we actually have to do.”
In the future, Johnson added that developers are looking to implement what is known as rent fees.
As detailed by CoinDesk, the idea is to charge a fee for users holding data permanently stored on the blockchain. Johnson said this would be an effective way to disincentivize “using up storage for things you don’t need them for.”
State channels
Aside from a revamped gas fee structure for smart contract developers, EIP 1014 helps progress an experimental scaling solution called state channels.
Actively under development as a part of efforts to scale ethereum for larger transaction volume, these channels minimize the amount of operations that need to happen on the ethereum blockchain itself, freeing up network resources and space.
Created by founder of ethereum Vitalik Buterin, EIP 1014 is described on GitHub by state channel developer Liam Horne to be “a significant performance increase in state channels.”
Others on the same forum have echoed the sentiment, urging for its inclusion into Constantinople and affirming that EIP 1014 would better facilitate transactions happening “off-chain.”
Economic policy
Finally, there is EIP 1234, the latest addition to the four other proposals set to be released in Constantinople dealing with the incremental increase in block mining difficulty known as the difficulty bomb.
Originally intended to encourage the transition into an more ecological, proof-of-stake based consensus system named Casper, the switch is still a long way off. As such, steps must be taken to delay the bomb — and decrease ether issuance alongside it.
Simply put, given the removal of the difficulty bomb, blocks will be faster to mine following Constantinople. This means that steps must be taken to reduce the reward per block as well — and EIP 1234 reduces them from 3 ETH to 2 ETH per block.
Because ethereum doesn’t have a formal monetary policy — currently maintaining an uncapped inflation model — according to a trader named Eric Conner, the reward reduction in EIP 1234 can be thought of as akin to a “stop gap” that is aimed at effectively curbing a “supply bleed”.
Schoedon, author of EIP 1234, described it as “the best proposal to stabilize issuance while simultaneously delaying the bomb” in an email to CoinDesk.
Still, certain members of the ethereum mining community opposed the decision to decrease mining rewards, arguing thinner profit margins and the potential of mining operations to become increasingly centralized in the hands of few.
The concerns come at a time when ASICs — a highly competitive type of mining hardware that removes hobbyists from the mining industry — are becoming increasingly widespread on ethereum.
What’s next
In summary, all five EIPs have impacts to ethereum that touch on a number of broader goals and initiatives still to be worked out on the decentralized platform even after Constantinople is fully released.
At present, each EIP will continue undergoing testing, implementation and peer-review in the weeks to come, though the process is by no means a linear progression.
As ethereum core developer Nick Johnson notes, technically “anyone can contribute tests” to a global test suite that is later run against all client implementations. However, it’s not as if ethereum clients must wait for these tests to be finalized before moving forward with code implementations of their own.
Schoedon, who boasts Parity as “probably one of the fastest teams implementing the changes for Constantinople” emphasized last Saturday in an email to CoinDesk that they were the first client, having implemented all five EIPs, to be “feature-complete” for Constantinople, awaiting now peer-review before full acceptance into their official codebase.
This aspect of preparation to do with testing and review that goes into a hard fork can be as time-consuming of a process, if not more time-consuming, than reaching consensus on a decentralized platform.
So, despite an original release date for October 8th, the grand premiere of ethereum’s next hard fork may not be due until later in the month or even sometime in November.
Luckily, the sneak peak of all five EIPs to be included in Constantinople has given ethereum fans and critics alike a good sense on what to expect.
The only thing left to stay tuned for now is a prime execution.
Zodiac clock image via Shutterstock
The leader in blockchain news, CoinDesk is a media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. CoinDesk is an independent operating subsidiary of Digital Currency Group, which invests in cryptocurrencies and blockchain startups.
!function(f,b,e,v,n,t,s){if(f.fbq)return;n=f.fbq=function(){n.callMethod? n.callMethod.apply(n,arguments):n.queue.push(arguments)};if(!f._fbq)f._fbq=n; n.push=n;n.loaded=!0;n.version='2.0';n.queue=[];t=b.createElement(e);t.async=!0; t.src=v;s=b.getElementsByTagName(e)[0];s.parentNode.insertBefore(t,s)}(window, document,'script','//connect.facebook.net/en_US/fbevents.js');
fbq('init', '472218139648482'); fbq('init', '239547076708948'); fbq('track', "PageView");
This news post is collected from CoinDesk
Recommended Read
Editor choice
BinBot Pro – Safest & Highly Recommended Binary Options Auto Trading Robot
Do you live in a country like USA or Canada where using automated trading systems is a problem? If you do then now we ...
9.5
Demo & Pro Version Try It Now
Read full review
The post Constantinople Ahead: What You Need to Know About Ethereum’s Big Upgrade appeared first on Click 2 Watch.
More Details Here → https://click2.watch/constantinople-ahead-what-you-need-to-know-about-ethereums-big-upgrade
0 notes
Text
Constantinople Ahead: What You Need to Know About Ethereum's Big Upgrade
New Post has been published on https://cryptnus.com/2018/09/constantinople-ahead-what-you-need-to-know-about-ethereums-big-upgrade/
Constantinople Ahead: What You Need to Know About Ethereum's Big Upgrade
Constantinople, ethereum’s next system-wide upgrade, is coming soon to a node near you.
Finalized August 31, Constantinople includes five different ethereum improvement proposals (EIPs). Once released on ethereum, the proposals will permanently alter the blockchain with a host of new backwards-incompatible upgrades.
This means that nodes — the network of computers that run ethereum software — must either update together with the whole system or continue running as a separate blockchain entity.
More formally known as a “hard fork,” system-wide upgrades have instigated a fair amount of drama in the past. Most notably, in the case that a portion of users don’t agree with the change, this may result in two different versions of the same blockchain running concurrently.
As dramatic as these things can get (having formerly resulted in a competing cryptocurrency named ethereum classic), most of the upgrades in Constantinople won’t be noticeable to average users. Indeed, described by independent developer Lane Rettig, the upcoming ethereum hard fork won’t feature any “big changes” for end users at all.
Characterized as primarily a “maintenance and optimization upgrade” by Rettig, Constantinople features small, yet highly technical, ethereum improvements to network efficiency and fee structure, as well as, upgrades that pave the way to ethereum’s hotly anticipated scaling roadmap.
Additionally, the hard fork includes changes to ethereum’s underlying economic policy, and the delay of the difficulty bomb, a piece of code programmed to activate what is known as the ethereum “ice age” in which new block creation on the network eventually slows to a complete halt.
As detailed by CoinDesk, the economic change has been the cause of contention, with conflicting views expressed by ethereum stakeholders in the months prior to the upgrade.
At press time, anxiety is continuing to brew among the networks miners that are faced with an impending pay cut following Constantinople. But still, achieving a balance between all stakeholder concerns, developers are confident that the upgrade will be broadly well received.
While a formal block number has yet to be finalized, core developers and clients are currently implementing, reviewing and testing the Constantinople code.
As ethereum trader Eric Conner told CoinDesk:
“Complex coding and testing takes time. And ethereum is live so it’s essential to be sure no changes are breaking.”
The new ethereum
The five EIPs set to be released in Constantinople are:
EIP 145: A technical upgrade written by two ethereum developers, Alex Beregszaszi and Pawel Bylica, EIP 145 details a more efficient method of information processing on ethereum known as bitwise shifting.
EIP 1052: Authored by core developer Nick Johnson and Bylica, EIP 1052 offers a means of optimizing large-scale code execution on ethereum.
EIP 1283: Based on EIP 1087, which was written by Johnson, this proposal mainly benefits smart contract developers by introducing a more equitable pricing method for changes made to data storage.
EIP 1014: Created by the founder of ethereum himself, Vitalik Buterin, the purpose of this upgrade is to better facilitate a certain type of scaling solution based upon state channels and “off-chain” transactions.
EIP 1234: Championed by Afri Schoedon, release manager for major ethereum client Parity, this upgrade is the most contentious of the batch, reducing block mining reward issuance from 3 ETH down to 2 ETH, as well as, delaying the difficulty bomb for a period of 12 months.
All in all, the changes include: code optimizations to improve processing times for developers; fairer pricing structures for changes made to smart contract data storage; a code edit making scaling solutions through state channels easier to occur on ethereum; and changes to ethereum’s economic policy.
Given these code changes are likely to shape the progress of the second most popular blockchain for years to come, Constantinople is worth taking a deeper look at.
Optimizing code
To begin, both EIP 145 and 1052 are targeted at improving network efficiency, by making changes to ethereum’s underlying virtual machine — the EVM.
Powered by software at the heart of ethereum, the EVM processes smart contracts into a series of ones and zeros also called bytecode.
Seeking to maintain the longevity of ethereum and optimize performance to better serve user needs, both EIP 145 and EIP 1052 seek to optimize the developer experience for smart contract developers specifically.
EIP 145 introduces native “bitwise shifting” functionality which is able to run through bytecode without relying on arithmetic operations such as multiplication and division. In effect, this means that the smart contracts underlying decentralized applications like CryptoKitties will be processed faster by the EVM.
Additionally, when smart contracts on ethereum are executed and called upon, EIP 1052 introduces an upgrade by which only the essential data of the contract code is checked rather than the entirety of the code itself.
Namely, rather than verifying the full contract, EIP 1052 makes it so a compressed line of code, or a “hash” can be verified instead, saving computing time and cost — especially for lengthy smart contracts that run on thousands of lines of code.
Cheaper storage
Further EIPs deal with how smart contracts are stored on ethereum — such as EIP 1283, which reduces the amount developers need to pay when building smart contracts.
As it stands, without EIP 1283, certain updates to smart contract code cost a hefty amount of gas, the computational unit of energy required to execute operations on the ethereum platform.
EIP 1283 implements a better cost analysis for contracts, by breaking down what contract changes have been written in ethereum’s short term storage, called memory, rather than the blockchain itself.
If none or a few of those updates end up on the blockchain, it reduces the overall cost for developers. As Johnson, the author of the original proposal concept behind EIP 1283 recounted to CoinDesk:
“In some cases in the past, we were charging gas for things that didn’t actually happen or didn’t actually cost any real resources and now we’re trying to adjust things so we only charge gas that aligns with the work we actually have to do.”
In the future, Johnson added that developers are looking to implement what is known as rent fees.
As detailed by CoinDesk, the idea is to charge a fee for users holding data permanently stored on the blockchain. Johnson said this would be an effective way to disincentivize “using up storage for things you don’t need them for.”
State channels
Aside from a revamped gas fee structure for smart contract developers, EIP 1014 helps progress an experimental scaling solution called state channels.
Actively under development as a part of efforts to scale ethereum for larger transaction volume, these channels minimize the amount of operations that need to happen on the ethereum blockchain itself, freeing up network resources and space.
Created by founder of ethereum Vitalik Buterin, EIP 1014 is described on GitHub by state channel developer Liam Horne to be “a significant performance increase in state channels.”
Others on the same forum have echoed the sentiment, urging for its inclusion into Constantinople and affirming that EIP 1014 would better facilitate transactions happening “off-chain.”
Economic policy
Finally, there is EIP 1234, the latest addition to the four other proposals set to be released in Constantinople dealing with the incremental increase in block mining difficulty known as the difficulty bomb.
Originally intended to encourage the transition into an more ecological, proof-of-stake based consensus system named Casper, the switch is still a long way off. As such, steps must be taken to delay the bomb — and decrease ether issuance alongside it.
Simply put, given the removal of the difficulty bomb, blocks will be faster to mine following Constantinople. This means that steps must be taken to reduce the reward per block as well — and EIP 1234 reduces them from 3 ETH to 2 ETH per block.
Because ethereum doesn’t have a formal monetary policy — currently maintaining an uncapped inflation model — according to a trader named Eric Conner, the reward reduction in EIP 1234 can be thought of as akin to a “stop gap” that is aimed at effectively curbing a “supply bleed”.
Schoedon, author of EIP 1234, described it as “the best proposal to stabilize issuance while simultaneously delaying the bomb” in an email to CoinDesk.
Still, certain members of the ethereum mining community opposed the decision to decrease mining rewards, arguing thinner profit margins and the potential of mining operations to become increasingly centralized in the hands of few.
The concerns come at a time when ASICs — a highly competitive type of mining hardware that removes hobbyists from the mining industry — are becoming increasingly widespread on ethereum.
What’s next
In summary, all five EIPs have impacts to ethereum that touch on a number of broader goals and initiatives still to be worked out on the decentralized platform even after Constantinople is fully released.
At present, each EIP will continue undergoing testing, implementation and peer-review in the weeks to come, though the process is by no means a linear progression.
As ethereum core developer Nick Johnson notes, technically “anyone can contribute tests” to a global test suite that is later run against all client implementations. However, it’s not as if ethereum clients must wait for these tests to be finalized before moving forward with code implementations of their own.
Schoedon, who boasts Parity as “probably one of the fastest teams implementing the changes for Constantinople” emphasized last Saturday in an email to CoinDesk that they were the first client, having implemented all five EIPs, to be “feature-complete” for Constantinople, awaiting now peer-review before full acceptance into their official codebase.
This aspect of preparation to do with testing and review that goes into a hard fork can be as time-consuming of a process, if not more time-consuming, than reaching consensus on a decentralized platform.
So, despite an original release date for October 8th, the grand premiere of ethereum’s next hard fork may not be due until later in the month or even sometime in November.
Luckily, the sneak peak of all five EIPs to be included in Constantinople has given ethereum fans and critics alike a good sense on what to expect.
The only thing left to stay tuned for now is a prime execution.
Zodiac clock image via Shutterstock
The leader in blockchain news, CoinDesk is a media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. CoinDesk is an independent operating subsidiary of Digital Currency Group, which invests in cryptocurrencies and blockchain startups.
0 notes