#Custom VPN Software
Text
How Does a White-Label VPN Software Solution Improve Business Outcomes?

A white-label VPN software solution is a versatile tool that can help businesses achieve a variety of desired outcomes. By rebranding the software with their own logo and branding, businesses can make the solution their own and better control how their customers experience it. Additionally, white-label VPN solutions are often more affordable than traditional VPNs, giving businesses a cost-effective way to provide high-quality VPN service to their customers.
Defining a White-Label VPN Software Solution
A white-label VPN software solution is a ready-made VPN solution that can be branded and sold by a reseller under their own name. A custom VPN app is included in the package, along with a custom control panel and branding options. This makes it easy for resellers to get started selling VPN services without having to develop their own software or infrastructure.
A white-label VPN solution is a great option for resellers who want to offer VPN services without having to invest in developing their own software. The package includes everything they need to get started, including a custom VPN app and control panel. This allows them to brand the service as their own and sell it under their own name. With a white-label VPN solution, resellers can focus on selling the service and leave the technical details to a white-label VPN solution provider.
What Are the Benefits of Using a White-Label VPN Software Solution for Businesses?
A white-label VPN software solution is a great way for businesses to get started with their own VPN service. There are many benefits to using a white-label VPN software solution, including the ability to brand the service as your own, having complete control over the features and settings, and being able to offer a more affordable service to your customers.
A white-label VPN solution allows you to create an application with your own company's logo, identity, and colors. With control over the features, settings, and configuration of the application, you can tailor your brand new VPN application precisely to the needs of your business. And because you're not starting from scratch, you can offer a more affordable service to your customers. If you're looking for a way to get started with your own VPN service, a white-label VPN software solution is a great option.
How Does a White-Label VPN Software Solution Work?
A white-label VPN software solution is a type of VPN service that allows users to rebrand and resell the service under their own brand name. This type of solution is ideal for businesses that want to offer their customers a VPN service, but don't have the time or resources to develop and manage their own VPN infrastructure.
White-label VPN software solutions are typically offered by third-party providers, who manage all aspects of the service, including developing and maintaining the software, hosting the servers, and providing customer support. Businesses that resell white-label VPN services simply need to create an account with the provider and then generate new accounts for their customers. The benefits of using a white-label VPN software solution are numerous.
What Are Some Common Use Cases for a White-Label VPN Software Solution?
A white-label VPN software solution is a great way to start your own VPN business with fewer expenses and save time. There are many use cases for a white-label VPN software solution, but some of the most common uses include:
1. Reseller Hosting - Many reseller hosting providers offer white-label VPN solutions as an add-on service for their customers. This allows customers to have their own private, secure VPN connection without having to set up and manage their own server infrastructure.
2. Businesses - Another common use case for a white-label VPN software solution is for ISPs and other service providers that want to offer their customers a way to encrypt their Internet traffic and improve their online privacy.
How Can Businesses Get Started by Using a White-Label VPN Software Solution?
A white-label VPN software solution is a great way to start a VPN Business. All you need to get started is your vps or dedicated servers. Once you have that, you can install a custom-branded app on your server. This will allow you to use your own domain name and brand the app as you see fit. You can then promote your VPN service to your customers and start reaping the benefits of increased security and privacy.
In conclusion, it is evident that white-label VPN software solutions offer various benefits to businesses. By providing a customizable platform, businesses are able to cost-effectively outsource their VPN needs. In addition, white-label VPN software solutions offer the added benefit of being brandable, which can help businesses increase their visibility and reach their desired outcomes.
0 notes
Text
Start your Own VPN Business without Huge Investment - Smarters

White label VPN software solutions allow businesses to start their own VPN service without the need for significant initial investment. These solutions provide the technology and infrastructure for the VPN service, and the business can then brand and market the service as their own. This can be a cost-effective way for a business to enter the VPN market and begin offering VPN services to their customers without the need for significant upfront investment in technology and infrastructure. There might be some branding & customization limitation based on the solution you choose. It is always best to check with the provider on the specific limitation and cost details.
Smarters is a leading & Well-known software development company that can help you with the best White Label VPN Software Solution.
Contact us now: https://www.whmcssmarters.com/vpn-software-solution
0 notes
Text
The antitrust case against Apple

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me TONIGHT (Mar 22) in TORONTO, then SUNDAY (Mar 24) with LAURA POITRAS in NYC, then Anaheim, and beyond!

The foundational tenet of "the Cult of Mac" is that buying products from a $3t company makes you a member of an oppressed ethnic minority and therefore every criticism of that corporation is an ethnic slur:
https://pluralistic.net/2024/01/12/youre-holding-it-wrong/#if-dishwashers-were-iphones
Call it "Apple exceptionalism" – the idea that Apple, alone among the Big Tech firms, is virtuous, and therefore its conduct should be interpreted through that lens of virtue. The wellspring of this virtue is conveniently nebulous, which allows for endless goal-post shifting by members of the Cult of Mac when Apple's sins are made manifest.
Take the claim that Apple is "privacy respecting," which is attributed to Apple's business model of financing its services though cash transactions, rather than by selling it customers to advertisers. This is the (widely misunderstood) crux of the "surveillance capitalism" hypothesis: that capitalism is just fine, but once surveillance is in the mix, capitalism fails.
Apple, then, is said to be a virtuous company because its behavior is disciplined by market forces, unlike its spying rivals, whose ability to "hack our dopamine loops" immobilizes the market's invisible hand with "behavior-shaping" shackles:
http://pluralistic.net/HowToDestroySurveillanceCapitalism
Apple makes a big deal out of its privacy-respecting ethos, and not without some justification. After all, Apple went to the mattresses to fight the FBI when they tried to force Apple to introduced defects into its encryption systems:
https://www.eff.org/deeplinks/2018/04/fbi-could-have-gotten-san-bernardino-shooters-iphone-leadership-didnt-say
And Apple gave Ios users the power to opt out of Facebook spying with a single click; 96% of its customers took them up on this offer, costing Facebook $10b (one fifth of the pricetag of the metaverse boondoggle!) in a single year (you love to see it):
https://arstechnica.com/gadgets/2021/02/facebook-makes-the-case-for-activity-tracking-to-ios-14-users-in-new-pop-ups/
Bruce Schneier has a name for this practice: "feudal security." That's when you cede control over your device to a Big Tech warlord whose "walled garden" becomes a fortress that defends you against external threats:
https://pluralistic.net/2021/06/08/leona-helmsley-was-a-pioneer/#manorialism
The keyword here is external threats. When Apple itself threatens your privacy, the fortress becomes a prison. The fact that you can't install unapproved apps on your Ios device means that when Apple decides to harm you, you have nowhere to turn. The first Apple customers to discover this were in China. When the Chinese government ordered Apple to remove all working privacy tools from its App Store, the company obliged, rather than risk losing access to its ultra-cheap manufacturing base (Tim Cook's signal accomplishment, the one that vaulted him into the CEO's seat, was figuring out how to offshore Apple manufacturing to China) and hundreds of millions of middle-class consumers:
https://www.reuters.com/article/us-china-apple-vpn/apple-says-it-is-removing-vpn-services-from-china-app-store-idUSKBN1AE0BQ
Killing VPNs and other privacy tools was just for openers. After Apple caved to Beijing, the demands kept coming. Next, Apple willingly backdoored all its Chinese cloud services, so that the Chinese state could plunder its customers' data at will:
https://www.nytimes.com/2021/05/17/technology/apple-china-censorship-data.html
This was the completely foreseeable consequence of Apple's "curated computing" model: once the company arrogated to itself the power to decide which software you could run on your own computer, it was inevitable that powerful actors – like the Chinese Communist Party – would lean on Apple to exercise that power in service to its goals.
Unsurprisingly, the Chinese state's appetite for deputizing Apple to help with its spying and oppression was not sated by backdooring iCloud and kicking VPNs out of the App Store. As recently as 2022, Apple continued to neuter its tools at the behest of the Chinese state, breaking Airdrop to make it useless for organizing protests in China:
https://pluralistic.net/2022/11/11/foreseeable-consequences/#airdropped
But the threat of Apple turning on its customers isn't limited to China. While the company has been unwilling to spy on its users on behalf of the US government, it's proven more than willing to compromise its worldwide users' privacy to pad its own profits. Remember when Apple let its users opt out of Facebook surveillance with one click? At the very same time, Apple was spinning up its own commercial surveillance program, spying on Ios customers, gathering the very same data as Facebook, and for the very same purpose: to target ads. When it came to its own surveillance, Apple completely ignored its customers' explicit refusal to consent to spying, spied on them anyway, and lied about it:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Here's the thing: even if you believe that Apple has a "corporate personality" that makes it want to do the right thing, that desire to be virtuous is dependent on the constraints Apple faces. The fact that Apple has complete legal and technical control over the hardware it sells – the power to decide who can make software that runs on that hardware, the power to decide who can fix that hardware, the power to decide who can sell parts for that hardware – represents an irresistible temptation to enshittify Apple products.
"Constraints" are the crux of the enshittification hypothesis. The contagion that spread enshittification to every corner of our technological world isn't a newfound sadism or indifference among tech bosses. Those bosses are the same people they've always been – the difference is that today, they are unconstrained.
Having bought, merged or formed a cartel with all their rivals, they don't fear competition (Apple buys 90+ companies per year, and Google pays it an annual $26.3b bribe for default search on its operating systems and programs).
Having captured their regulators, they don't fear fines or other penalties for cheating their customers, workers or suppliers (Apple led the coalition that defeated dozens of Right to Repair bills, year after year, in the late 2010s).
Having wrapped themselves in IP law, they don't fear rivals who make alternative clients, mods, privacy tools or other "adversarial interoperability" tools that disenshittify their products (Apple uses the DMCA, trademark, and other exotic rules to block third-party software, repair, and clients).
True virtue rests not merely in resisting temptation to be wicked, but in recognizing your own weakness and avoiding temptation. As I wrote when Apple embarked on its "curated computing" path, the company would eventually – inevitably – use its power to veto its customers' choices to harm those customers:
https://memex.craphound.com/2010/04/01/why-i-wont-buy-an-ipad-and-think-you-shouldnt-either/
Which is where we're at today. Apple – uniquely among electronics companies – shreds every device that is traded in by its customers, to block third parties from harvesting working components and using them for independent repair:
https://www.vice.com/en/article/yp73jw/apple-recycling-iphones-macbooks
Apple engraves microscopic Apple logos on those parts and uses these as the basis for trademark complaints to US customs, to block the re-importation of parts that escape its shredders:
https://repair.eu/news/apple-uses-trademark-law-to-strengthen-its-monopoly-on-repair/
Apple entered into an illegal price-fixing conspiracy with Amazon to prevent used and refurbished devices from being sold in the "world's biggest marketplace":
https://pluralistic.net/2022/11/10/you-had-one-job/#thats-just-the-as
Why is Apple so opposed to independent repair? Well, they say it's to keep users safe from unscrupulous or incompetent repair technicians (feudal security). But when Tim Cook speaks to his investors, he tells a different story, warning them that the company's profits are threatened by customers who choose to repair (rather than replace) their slippery, fragile glass $1,000 pocket computers (the fortress becomes a prison):
https://www.apple.com/newsroom/2019/01/letter-from-tim-cook-to-apple-investors/
All this adds up to a growing mountain of immortal e-waste, festooned with miniature Apple logos, that our descendants will be dealing with for the next 1,000 years. In the face of this unspeakable crime, Apple engaged in a string of dishonest maneuvers, claiming that it would support independent repair. In 2022, Apple announced a home repair program that turned out to be a laughably absurd con:
https://pluralistic.net/2022/05/22/apples-cement-overshoes/
Then in 2023, Apple announced a fresh "pro-repair" initiative that, once again, actually blocked repair:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
Let's pause here a moment and remember that Apple once stood for independent repair, and celebrated the independent repair technicians that kept its customers' beloved Macs running:
https://pluralistic.net/2021/10/29/norwegian-potato-flour-enchiladas/#r2r
Whatever virtue lurks in Apple's corporate personhood, it is no match for the temptation that comes from running a locked-down platform designed to capture IP rights so that it can prevent normal competitive activities, like fixing phones, processing payments, or offering apps.
When Apple rolled out the App Store, Steve Jobs promised that it would save journalism and other forms of "content creation" by finally giving users a way to pay rightsholders. A decade later, that promise has been shattered by the app tax – a 30% rake on every in-app transaction that can't be avoided because Apple will kick your app out of the App Store if you even mention that your customers can pay you via the web in order to avoid giving a third of their content dollars to a hardware manufacturer that contributed nothing to the production of that material:
https://www.eff.org/deeplinks/2023/06/save-news-we-must-open-app-stores
Among the apps that Apple also refuses to allow on Ios is third-party browsers. Every Iphone browser is just a reskinned version of Apple's Safari, running on the same antiquated, insecure Webkit browser engine. The fact that Webkit is incomplete and outdated is a feature, not a bug, because it lets Apple block web apps – apps delivered via browsers, rather than app stores:
https://pluralistic.net/2022/12/13/kitbashed/#app-store-tax
Last month, the EU took aim at Apple's veto over its users' and software vendors' ability to transact with one another. The newly in-effect Digital Markets Act requires Apple to open up both third-party payment processing and third-party app stores. Apple's response to this is the very definition of malicious compliance, a snake's nest of junk-fees, onerous terms of service, and petty punitive measures that all add up to a great, big "Go fuck yourself":
https://pluralistic.net/2024/02/06/spoil-the-bunch/#dma
But Apple's bullying, privacy invasion, price-gouging and environmental crimes are global, and the EU isn't the only government seeking to end them. They're in the firing line in Japan:
https://asia.nikkei.com/Business/Technology/Japan-to-crack-down-on-Apple-and-Google-app-store-monopolies
And in the UK:
https://www.gov.uk/government/news/cma-wins-appeal-in-apple-case
And now, famously, the US Department of Justice is coming for Apple, with a bold antitrust complaint that strikes at the heart of Apple exceptionalism, the idea that monopoly is safer for users than technological self-determination:
https://www.justice.gov/opa/media/1344546/dl?inline
There's passages in the complaint that read like I wrote them:
Apple wraps itself in a cloak of privacy, security, and consumer preferences to justify its anticompetitive conduct. Indeed, it spends billions on marketing and branding to promote the self-serving premise that only Apple can safeguard consumers’ privacy and security interests. Apple selectively compromises privacy and security interests when doing so is in Apple’s own financial interest—such as degrading the security of text messages, offering governments and certain companies the chance to access more private and secure versions of app stores, or accepting billions of dollars each year for choosing Google as its default search engine when more private options are available. In the end, Apple deploys privacy and security justifications as an elastic shield that can stretch or contract to serve Apple’s financial and business interests.
After all, Apple punishes its customers for communicating with Android users by forcing them to do so without any encryption. When Beeper Mini rolled out an Imessage-compatible Android app that fixed this, giving Iphone owners the privacy Apple says they deserve but denies to them, Apple destroyed Beeper Mini:
https://blog.beeper.com/p/beeper-moving-forward
Tim Cook is on record about this: if you want to securely communicate with an Android user, you must "buy them an Iphone":
https://www.theverge.com/2022/9/7/23342243/tim-cook-apple-rcs-imessage-android-iphone-compatibility
If your friend, family member or customer declines to change mobile operating systems, Tim Cook insists that you must communicate without any privacy or security.
Even where Apple tries for security, it sometimes fails ("security is a process, not a product" -B. Schneier). To be secure in a benevolent dictatorship, it must also be an infallible dictatorship. Apple's far from infallible: Eight generations of Iphones have unpatchable hardware defects:
https://checkm8.info/
And Apple's latest custom chips have secret-leaking, unpatchable vulnerabilities:
https://arstechnica.com/security/2024/03/hackers-can-extract-secret-encryption-keys-from-apples-mac-chips/
Apple's far from infallible – but they're also far from benevolent. Despite Apple's claims, its hardware, operating system and apps are riddled with deliberate privacy defects, introduce to protect Apple's shareholders at the expense of its customers:
https://proton.me/blog/iphone-privacy
Now, antitrust suits are notoriously hard to make, especially after 40 years of bad-precedent-setting, monopoly-friendly antitrust malpractice. Much of the time, these suits fail because they can't prove that tech bosses intentionally built their monopolies. However, tech is a written culture, one that leaves abundant, indelible records of corporate deliberations. What's more, tech bosses are notoriously prone to bragging about their nefarious intentions, committing them to writing:
https://pluralistic.net/2023/09/03/big-tech-cant-stop-telling-on-itself/
Apple is no exception – there's an abundance of written records that establish that Apple deliberately, illegally set out to create and maintain a monopoly:
https://www.wired.com/story/4-internal-apple-emails-helped-doj-build-antitrust-case/
Apple claims that its monopoly is beneficent, used to protect its users, making its products more "elegant" and safe. But when Apple's interests conflict with its customers' safety and privacy – and pocketbooks – Apple always puts itself first, just like every other corporation. In other words: Apple is unexceptional.
The Cult of Mac denies this. They say that no one wants to use a third-party app store, no one wants third-party payments, no one wants third-party repair. This is obviously wrong and trivially disproved: if no Apple customer wanted these things, Apple wouldn't have to go to enormous lengths to prevent them. The only phones that an independent Iphone repair shop fixes are Iphones: which means Iphone owners want independent repair.
The rejoinder from the Cult of Mac is that those Iphone owners shouldn't own Iphones: if they wanted to exercise property rights over their phones, they shouldn't have bought a phone from Apple. This is the "No True Scotsman" fallacy for distraction-rectangles, and moreover, it's impossible to square with Tim Cook's insistence that if you want private communications, you must buy an Iphone.
Apple is unexceptional. It's just another Big Tech monopolist. Rounded corners don't preserve virtue any better than square ones. Any company that is freed from constraints – of competition, regulation and interoperability – will always enshittify. Apple – being unexceptional – is no exception.

Name your price for 18 of my DRM-free ebooks and support the Electronic Frontier Foundation with the Humble Cory Doctorow Bundle.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/03/22/reality-distortion-field/#three-trillion-here-three-trillion-there-pretty-soon-youre-talking-real-money
#pluralistic#apple#antitrust#cult of mac#ios#mobile#app tax#infosec#feudal security#doj#jonathan kanter#doj v apple#big tech#trustbusting#monopolies#app stores#technofeudalism#technomaorialism#privacy#right to repair#corruption
232 notes
·
View notes
Text
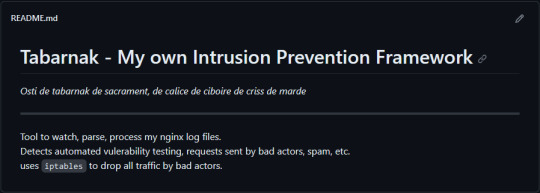
(this is a small story of how I came to write my own intrusion detection/prevention framework and why I'm really happy with that decision, don't mind me rambling)
Preface
About two weeks ago I was faced with a pretty annoying problem. Whilst I was going home by train I have noticed that my server at home had been running hot and slowed down a lot. This prompted me to check my nginx logs, the only service that is indirectly available to the public (more on that later), which made me realize that - due to poor access control - someone had been sending me hundreds of thousands of huge DNS requests to my server, most likely testing for vulnerabilities.
I added an iptables rule to drop all traffic from the aforementioned source and redirected remaining traffic to a backup NextDNS instance that I set up previously with the same overrides and custom records that my DNS had to not get any downtime for the service but also allow my server to cool down.
I stopped the DNS service on my server at home and then used the remaining train ride to think. How would I stop this from happening in the future? I pondered multiple possible solutions for this problem, whether to use fail2ban, whether to just add better access control, or to just stick with the NextDNS instance.
I ended up going with a completely different option: making a solution, that's perfectly fit for my server, myself.
My Server Structure
So, I should probably explain how I host and why only nginx is public despite me hosting a bunch of services under the hood.
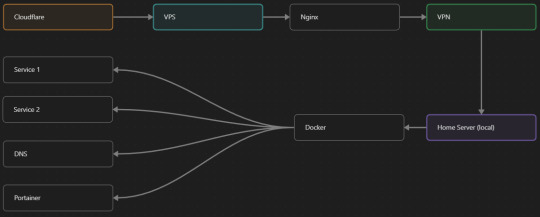
I have a public facing VPS that only allows traffic to nginx. That traffic then gets forwarded through a VPN connection to my home server so that I don't have to have any public facing ports on said home server. The VPS only really acts like the public interface for the home server with access control and logging sprinkled in throughout my configs to get more layers of security. Some Services can only be interacted with through the VPN or a local connection, such that not everything is actually forwarded - only what I need/want to be.
I actually do have fail2ban installed on both my VPS and home server, so why make another piece of software?
Tabarnak - Succeeding at Banning
I had a few requirements for what I wanted to do:
Only allow HTTP(S) traffic through Cloudflare
Only allow DNS traffic from given sources; (location filtering, explicit white-/blacklisting);
Webhook support for logging
Should be interactive (e.g. POST /api/ban/{IP})
Detect automated vulnerability scanning
Integration with the AbuseIPDB (for checking and reporting)
As I started working on this, I realized that this would soon become more complex than I had thought at first.
Webhooks for logging
This was probably the easiest requirement to check off my list, I just wrote my own log() function that would call a webhook. Sadly, the rest wouldn't be as easy.
Allowing only Cloudflare traffic
This was still doable, I only needed to add a filter in my nginx config for my domain to only allow Cloudflare IP ranges and disallow the rest. I ended up doing something slightly different. I added a new default nginx config that would just return a 404 on every route and log access to a different file so that I could detect connection attempts that would be made without Cloudflare and handle them in Tabarnak myself.
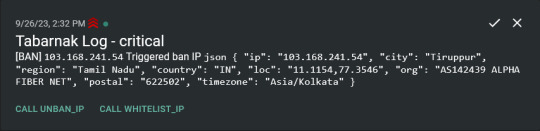
Integration with AbuseIPDB
Also not yet the hard part, just call AbuseIPDB with the parsed IP and if the abuse confidence score is within a configured threshold, flag the IP, when that happens I receive a notification that asks me whether to whitelist or to ban the IP - I can also do nothing and let everything proceed as it normally would. If the IP gets flagged a configured amount of times, ban the IP unless it has been whitelisted by then.
Location filtering + Whitelist + Blacklist
This is where it starts to get interesting. I had to know where the request comes from due to similarities of location of all the real people that would actually connect to the DNS. I didn't want to outright ban everyone else, as there could be valid requests from other sources. So for every new IP that triggers a callback (this would only be triggered after a certain amount of either flags or requests), I now need to get the location.
I do this by just calling the ipinfo api and checking the supplied location. To not send too many requests I cache results (even though ipinfo should never be called twice for the same IP - same) and save results to a database.
I made my own class that bases from collections.UserDict which when accessed tries to find the entry in memory, if it can't it searches through the DB and returns results. This works for setting, deleting, adding and checking for records.
Flags, AbuseIPDB results, whitelist entries and blacklist entries also get stored in the DB to achieve persistent state even when I restart.
Detection of automated vulnerability scanning
For this, I went through my old nginx logs, looking to find the least amount of paths I need to block to catch the biggest amount of automated vulnerability scan requests. So I did some data science magic and wrote a route blacklist.
It doesn't just end there. Since I know the routes of valid requests that I would be receiving (which are all mentioned in my nginx configs), I could just parse that and match the requested route against that. To achieve this I wrote some really simple regular expressions to extract all location blocks from an nginx config alongside whether that location is absolute (preceded by an =) or relative. After I get the locations I can test the requested route against the valid routes and get back whether the request was made to a valid URL (I can't just look for 404 return codes here, because there are some pages that actually do return a 404 and can return a 404 on purpose).
I also parse the request method from the logs and match the received method against the HTTP standard request methods (which are all methods that services on my server use). That way I can easily catch requests like:
XX.YYY.ZZZ.AA - - [25/Sep/2023:14:52:43 +0200] "145.ll|'|'|SGFjS2VkX0Q0OTkwNjI3|'|'|WIN-JNAPIER0859|'|'|JNapier|'|'|19-02-01|'|'||'|'|Win 7 Professional SP1 x64|'|'|No|'|'|0.7d|'|'|..|'|'|AA==|'|'|112.inf|'|'|SGFjS2VkDQoxOTIuMTY4LjkyLjIyMjo1NTUyDQpEZXNrdG9wDQpjbGllbnRhLmV4ZQ0KRmFsc2UNCkZhbHNlDQpUcnVlDQpGYWxzZQ==12.act|'|'|AA==" 400 150 "-" "-"
I probably over complicated this - by a lot - but I can't go back in time to change what I did.
Interactivity
As I showed and mentioned earlier, I can manually white-/blacklist an IP. This forced me to add threads to my previously single-threaded program. Since I was too stubborn to use websockets (I have a distaste for websockets), I opted for probably the worst option I could've taken. It works like this:
I have a main thread, which does all the log parsing, processing and handling and a side thread which watches a FIFO-file that is created on startup. I can append commands to the FIFO-file which are mapped to the functions they are supposed to call. When the FIFO reader detects a new line, it looks through the map, gets the function and executes it on the supplied IP.
Doing all of this manually would be way too tedious, so I made an API endpoint on my home server that would append the commands to the file on the VPS. That also means, that I had to secure that API endpoint so that I couldn't just be spammed with random requests.
Now that I could interact with Tabarnak through an API, I needed to make this user friendly - even I don't like to curl and sign my requests manually. So I integrated logging to my self-hosted instance of https://ntfy.sh and added action buttons that would send the request for me.
All of this just because I refused to use sockets.
First successes and why I'm happy about this
After not too long, the bans were starting to happen. The traffic to my server decreased and I can finally breathe again.
I may have over complicated this, but I don't mind. This was a really fun experience to write something new and learn more about log parsing and processing.
Tabarnak probably won't last forever and I could replace it with solutions that are way easier to deploy and way more general. But what matters is, that I liked doing it. It was a really fun project - which is why I'm writing this - and I'm glad that I ended up doing this.
Of course I could have just used fail2ban but I never would've been able to write all of the extras that I ended up making (I don't want to take the explanation ad absurdum so just imagine that I added cool stuff) and I never would've learned what I actually did.
So whenever you are faced with a dumb problem and could write something yourself, I think you should at least try. This was a really fun experience and it might be for you as well.
Post Scriptum
First of all, apologies for the English - I'm not a native speaker so I'm sorry if some parts were incorrect or anything like that.
Secondly, I'm sure that there are simpler ways to accomplish what I did here, however this was more about the experience of creating something myself rather than using some pre-made tool that does everything I want to (maybe even better?).
Third, if you actually read until here, thanks for reading - hope it wasn't too boring - have a nice day :)
8 notes
·
View notes
Text
If you had battery-related performance issues on an older iPhone—and you got in on a class-action lawsuit against Apple six years ago—you could soon receive some payback for your trouble.
According to a statement released by the law office involved in the suit against Apple, the tech giant will soon have to pay out up to $500 million to customers affected by its throttling of iPhones that had older batteries. The so-called Batterygate scandal affected people using iPhones in the 6, 6S, and 7 families, as well as the original SE model, and stems from complaints from users that Apple purposely slowed down the devices after they installed software updates. Apple hasn’t admitted any wrongdoing, instead positing that its practice of deliberately slowing down its phones wasn’t a technique to get people to buy a newer device but rather a safety measure to keep the phones from shutting down when the battery got too low.
The checks will be doled out to the roughly 3 million people who filed claims for the lawsuit, which works out to somewhere between $65 and $90 per person. It’s too late to make a claim now—the deadline to join the suit passed in October 2020.
Here’s some more news about the stuff on your phone.
Premium Prime
Bad streaming music news for anyone who’s somehow not on Spotify or Apple Music: Amazon’s music streaming service is getting more expensive.
The price hike from $9 to $10 was revealed by a FAQ page on Amazon’s Music site, spotted by The Hollywood Reporter. The increase is relatively small and will apply to Amazon Prime members with Unlimited Music plans and family plans. But it’s part of a trend of streaming services putting the squeeze on their customers. The cost of a Spotify Premium subscription went up by a buck last month after 12 years without an increase. Hulu and Disney+ are getting more expensive later this year. Netflix has cracked down on password sharing and introduced a paid ad-supported tier. And don't forget that HBO Max removed gobs of content from its platform. Amazon Music doesn’t seem to be ditching any of its songs quite yet—or banning password sharing—but clearly the Amazonian overlords want to squeeze a little more out of the platform.
Muting TikTok
A recent Reuters poll shows that nearly half of Americans approve of the US banning the social media app TikTok. (Disclosure: Yes, WIRED is on TikTok.)
US lawmakers have been talking about tanking TikTok for years now, citing concerns that the app’s Chinese parent company ByteDance could share Americans’ user data with the Chinese government or that the app could serve as a software backdoor for Chinese spyware. Pundits and members of Congress have posited the TikTok ban as a push to protect privacy, even though the issue is more due to international tensions between the US and China. (Cue the I Think You Should Leave “you sure about that?” clip.)
The process of actually banning the app from US soil would be laborious and controversial. Montana is going to give it a shot in 2024, when its recently passed TikTok ban goes into effect. Enforcing a ban will be nigh impossible, since users could likely circumvent the rules by using a VPN to make it appear that they are in another location or by simply downloading the app while they are traveling to another state.
Stay Cool
It’s getting hotter here on planet Earth. Heat waves intensify, oceans warm, and wildfires worsen. And all the while, humans—and everything else living on the planet—pay the price. Human influence has undeniably altered the weather of the world, and as we hurtle along in a climate emergency, it’s only going to grow hotter and more unstable.
This week on the Gadget Lab podcast, WIRED’s resident doomsday reporter, Matt Simon, joins the show to talk about extreme heat, why it keeps getting warmer, and how we might be able to adapt.
7 notes
·
View notes
Text
Windscribe VPN Premium Crack Plus Keygen [Latest]
�� ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 Windscribe VPN Premium With Crack Free Download. Windscribe Adoption of technology was created without any need for an online account. The above program. Windscribe Pro Crack is used in a mode where you are doing our important work. And the ads bother you all the time. The more possible characters the harder it is to crack; Long, passwords should be at least 20 characters in length. But don't just use 3 or 4 dictionary words. Windscribe VPN Premium Crack is the world's best and the leading VPN software and network in the market. Consequently. Windscribe VPN Premium Crack is the world's best and leading VPN software and network on the market. Hence, VPN stands for Virtual Private. Windscribe VPN Crack With Keygen Full Download {Win/Mac}. It is a firewall and a VPN customer that protects your online connection. Windscribe VPN Premium Crack is software that does not require an email to login. This Software is an agreement of the Five. windscribe cracked, windscribe vpn pro, windscribe vpn cracked, windscribe vpn pro crack, Minitool Partition Wizard Professional Crack [by Crypto Andy]. Windscribe VPN Premium Crack is the world's best and the leading VPN software and network in the software will secure. Windscribe VPN Crack keeps all site visitors properly encrypted. You can use restricted articles by changing the login server. Windscribe VPN Premium Crack Plus Keygen [Latest ] can provide you with purposeful and anonymous browsing on the Internet. Windscribe VPN Premium Crack is the world's best and leading VPN software on the market. Hence, VPN stands for Virtual Private Network. Windscribe VPN Crack is a software that is not in the system to use. In addition, the software is an understanding of the five main company. Windscribe VPN Premium Crack is the world's best and the leading VPN software and network in the market. Windscribe VPN Crack + Keygen Download Windscribe Crack is one of the top VPN programs and the best network available there. The Windscribe VPN Premium Crack encrypts your internet connection and your data through its high-speed servers. Download NOWWindscribe VPN Premium APK Full Version With Crack Download For Android Windscribe VPN Crack is an amazing Canada-based. First, uninstall the old version of Windscribe VPN Premium with IObit Uninstaller Pro. · Download the Windscribe VPN Premium Cracked Latest Version using IDM.
Windscribe VPN Premium Crack Full Version
Windscribe - Free VPN and Ad Block
Windscribe VPN Premium Crack License for Lifetime
Crypto Andy | VK
Windscribe VPN Premium Crack + Keygen [Latest]
Windscribe Pro Crack + Keygen Free Download
Windscribe VPN Premium Crack Plus Keygen [Latest]
Windscribe VPN Crack & Key Download Updated PC Free
Windscribe VPN Premium Crack Plus Keygen [Latest
windscribe crack Archives - PcCrackMac - Mac Windows Software
3 notes
·
View notes
Text
7 Steps To Protect Yourself Against Corporate Spear Phishing

Corporate spear phishing attacks are a serious threat to businesses of all sizes. These targeted attacks are designed to trick employees into divulging information or installing malware on corporate systems, putting the organization at risk of data breaches, financial losses, and reputational damage. To protect yourself against corporate spear phishing attacks, it is important to be aware of the risks and take proactive steps to secure your accounts and devices. By following the 7 steps outlined above - being vigilant, using strong passwords and multi-factor authentication, keeping software up to date, using a VPN, and participating in regular security training - you can reduce the risk of falling victim to these types of attacks.

Phishing:
Phishing is a type of cyberattack where an attacker tries to trick individuals into divulging sensitive information such as usernames, passwords, credit card details, or other personal information.
This is typically done through emails, text messages, or other forms of communication that appear to come from a legitimate source, such as a bank, a social media platform, or an e-commerce site.
Phishing attacks can be sophisticated and difficult to detect, but there are some common red flags to look out for, such as misspellings, unfamiliar senders, urgent requests, and generic greetings instead of personalized ones.
Steps To Protect Corporate Spear Phishing Attacks:
Corporate spear phishing attacks are a type of targeted phishing attack that targets specific individuals or groups within an organization. Here are seven steps you can take to protect yourself against corporate spear phishing attacks:
Be aware of the risks: Understand the risks associated with corporate spear phishing attacks, including the potential loss of sensitive information or financial resources.
Stay vigilant: Be aware of any suspicious emails or messages that request sensitive information or appear to come from a trusted source. Double-check the sender's email address, as well as any links or attachments included in the message.
Use strong passwords: Use strong, unique passwords for all of your accounts, and avoid using the same password across multiple accounts. Consider using a password manager to help keep track of your passwords.
Enable multi-factor authentication: Enable multi-factor authentication on all of your accounts, including your corporate accounts. This adds an additional layer of security and makes it more difficult for attackers to gain access to your accounts.
Keep your software up to date: Make sure that your computer and software are up to date with the latest security patches and updates. This can help to prevent attackers from exploiting known vulnerabilities.
Use a VPN: Use a virtual private network (VPN) to encrypt your internet traffic and protect your online privacy. This is particularly important when accessing corporate networks or using public Wi-Fi.
Get regular security training: Participate in regular security training and awareness programs to learn about the latest phishing techniques and best practices for protecting yourself against these types of attacks.
How temp mail is used to protect yourself against corporate spear phishing:
Temporary email services also known as “temp mail”, can be useful in protecting your personal email address from spam and other unwanted messages.
But, they may not be useful tool for protecting yourself against corporate spear phishing attacks.
This is because many corporate spear phishing attacks are designed to specifically target high-level executives or employees with access to sensitive information or financial resources, and are often customized to appear as legitimate as possible.
Instead, to protect yourself against corporate spear phishing attacks, it is important to follow best practices such as using strong and unique passwords, enabling multi-factor authentication, and being vigilant about suspicious messages or requests.

Conclusion:
Protecting yourself against corporate spear phishing attacks is critical to safeguarding your personal information and the assets of your organization. These targeted attacks can be devastating and difficult to detect, as they often use sophisticated social engineering techniques to trick employees into divulging sensitive information or installing malware on corporate systems.
By taking proactive steps to secure your accounts and devices and staying vigilant against suspicious messages or requests, you can reduce the risk of falling victim to corporate spear phishing attacks and help to protect your organization's valuable assets and information.
FAQS:
What is corporate spear phishing?
Corporate spear phishing is a type of targeted cyber attack where an attacker sends personalized messages to employees within a specific organization, often using social engineering techniques to trick them into divulging sensitive information or installing malware on corporate systems.
How can I protect myself against corporate spear phishing?
To protect yourself against corporate spear phishing attacks, it is important to follow best practices such as using strong passwords, enabling multi-factor authentication, keeping software up to date, using a VPN, and participating in regular security training.
2 notes
·
View notes
Text
A King’s Ransom, Part Eight
Word Count: 3175
TW: Brief mention of smut; angst; white-collar crimes. 18+ only.
AN: Part of an unfinished series. The series masterlist here.

Nevada called you moments after you arrived home, and it made you smile: his men had dropped you off, so he obviously knew you made it back safely. Big, bad Trujillo – maybe he wasn’t so bad after all.
You took a shower, wincing at the pleasant ache between your legs. Then you settled in at your desk to work. You booted up the laptop and pulled up the schedule for tomorrow – most of your pro-bono work. You opened up your projection software and set it to run some scenarios to run past a few clients.
Then you booted up your desktop.
Your laptop was just a run-of-the-mill Apple; light and easy to carry around, a big screen to show clients different projections and colorful charts. Your desktop was custom built for your other business.
You opened up the VPN client and allowed it to mask your IP address, then you started. First you checked your account balances – all of them. You had numerous accounts offshore under different LLC’s; none had a balance large enough to trigger suspicion, and the inflows of cash were offset by outflows to your various causes. To a casual observer – and even an investigator – everything looked completely above board.
Then you opened up the termite program.
You called it your termite, but your clients – the ultra-wealthy ones, that is – thought it was just a flashy dashboard that allowed them to monitor their balances in real-time. It was, at its surface, a sophisticated little program. It linked in to the New York Stock Exchange, the overseas markets, the Chicago Mercantile, the bond markets. It took the client’s balances and investments and showed one, giant number that updated by the minute. Clients loved it because it simplified a very complicated world for them, and in typical wealth-driven ego, they could look at that giant number at any moment and know how rich they were.
Underneath the surface, though, it was even more sophisticated – hence the termite. Once installed, it sent little tendrils of code throughout the client’s computer – and now, in the world of cloud-based sharing and syncing – their smart phones, tablets, and anything linked to their computer.
The code allowed you to spy on them. You read their emails, you scrolled through their private photos, you peered into their dark inner lives. The program was a termite – a tiny little thing that could bring down a big house.
They weren’t all explicitly terrible. The vast majority of your ultra-wealthy clients were just boring. They were wrapped up in their boring little lives, going to events that they didn’t care about, socializing with friends that they didn’t really like. You checked on them from time to time, but mostly left them alone. You just invested their money and did their books and let it go at that.
It was the few explicitly terrible ones that you focused on. They were the ones you couldn’t let go.
*****
When Nevada got to the club the next day, he went through the papers you had left him. He had tossed them on his desk before he took you home, but now he had time to read through them.
It was a fucking plan for going straight. Hypothetical of course – you had framed it like a business case, but it was all there. Incorporating and separating his business from his personal finances. Moving his cash into an offshore bank. Running the cash from his illegal activities through legitimate cash-based businesses – the club, the new sports bar. You listed a few more options he could consider purchasing as money-laundering outfits as well.
Then, a pivot to legal marijuana. You had run preliminary numbers on everything he’d need. Land, a building for a grow operation, a testing lab. Nevada Ramirez, King of the Heights could be a fucking honest businessman within a few years or so. He might as well buy a pair of fucking khakis and join the Rotary Club. Maybe sponsor a kids’ soccer team like a fucking idiot.
He tossed the papers aside, then called in one of his guys to handle an errand for him. He wasn’t going to enact your plan. If you thought you were gonna turn him straight, you had another thing coming.
-----
The next day, Nevada was out, making the rounds on his delinquent accounts. He was in a shitty mood. He woke up with a headache that never improved, despite shot-gunning aspirin, and he was antsy from nicotine withdrawal. And he had slept like shit, tossing and turning and running over your fucking scheme to make him a lawful businessman.
As his guy drove him from place to place, his irritation grew. Fucking women. Here he was, uncomfortable and changing his entire fucking life, and what were you doing for him? Not a damned thing. All you did was give him business advice that he was never going to take. Make him feel like a piece of shit for being a criminal.
When he returned to the club that afternoon, you were waiting for him. You sat in your normal seat near his desk, and you flipped through a copy of ‘the Wall Street Journal’ while he sent his guys off for a coffee and settled in at his desk.
“Afternoon,” you said, greeting him. When he grumbled in reply, you added, “Tough day, your highness?”
“Just business,” he barked. He rubbed his temple and reached for his cigarettes, then thought better of it. You noticed.
“You can have one if you need one,” you said. “I’ll survive.”
Nevada took his pack and shook out a smoke. He lit it and held the smoke in for a moment, relishing the sting in his throat and in his sinuses. You gave him a slight smile as he exhaled. “Better?” you asked.
He gave a curt nod. “Yeah, real fucking generous of you to let me smoke.”
Your smile widened. “I knew cutting back would make you cranky.”
“Yeah,” he repeated. “You know so much.”
You folded the newspaper and slid it into your bag with a sigh. “Is this about the business plan I gave you? Our discussion the other day?”
He nodded again, and you continued.
“It’s only a suggestion,” you said, cocking your head at him. “I’m not sure why you’re so upset about it.”
He took a final drag on his cigarette and stubbed it out before shaking out another and lighting it. “I’m not going straight,” he declared after a moment. “Not for you. Not for anyone.”
You shrugged. “Okay.”
“You know all about my business but I know nothing about yours,” he added.
“That’s fair. What do you want to know?”
He leaned back in his seat, smoking and looking you over. You were in one of your usual business suits, a well-tailored grey thing with a light blue silk shirt underneath. Your hair was only half up, the sides clipped up and away from your face. When he didn’t reply, you volunteered some information.
“Most of my business is accounting and investing work. I also rob from the rich and give to the poor, and I find ways to punish certain evil-doers.”
He laughed without mirth. “Liar. You give me a fucking list of things I need to change about myself and you can’t even tell me the fucking truth.”
“How can you even know what the truth is? You make a lot of assumptions.”
He pointed his cigarette at you. “I know your type. Women like you, they like a fucking project. Like to wreck a man’s life. Tear him down.”
You scoffed at him. “How have I wrecked your life? I haven’t forced you to do anything, and I’ve never - ”
He cut you off. “No, but that’s how your type operates. You act like a cock-tease, then give me just a taste. Then you lay some business plan on my desk. I know what comes next. Next you start to put the screws to me, pressuring me to change. Meanwhile, what are you doing for me?” He looked you over in an exaggerated manner. “You can’t even dress right for me even though I’ve told you to a hundred fucking times.”
“And I’ve told you a hundred times,” you countered, your eyes narrowed at his outburst. “If you want some young dumb thing in a tiny dress to worship you from her knees,’ then have at it.” You swept your arm towards his door, indicating the variety of women that came to his club every night.
“Maybe I will,” he snarled. “At least they don’t pretend to know my business.”
“Pretend?” You leaned forward, half-pressed against the edge of his desk. “Oh, Nevada,” you said, drawing out his name with venom. “I don’t need to pretend to know your business. It’s a half-assed operation that won’t last. Your main source of income is going to drop out from under you in less than ten years, you keep your cash stored at your apartment and your warehouse, and you are needlessly violent. You’re never going to live to a ripe old age, and for what? You enjoying your life as a criminal? Geared up in all black, tooling around in an Escalade with the bass booming? Is that everything you dreamed your life would be?”
Nevada felt his blood boiling as you stood up. You reached across his desk and plucked the business proposal from a stack of papers, and you stuffed it into your bag. Then you pointed vaguely at his neck, and he reached up to prod the bruise you had sucked there only a few nights before.
“I don’t share,” you told him with a withering glare. “But by all means, go find someone new. Someone who won’t pressure you to change. I’m done here.” You turned without a second glance and left.
-----
He assumed you were bluffing, but one day passed, and then another. He didn’t hear from you, and you didn’t stop by. He put a guy on your tail – you still had your regular business, and when you went out for a drink, you just went to a neighborhood bar in Inwood.
You took your various self-defense and fighting classes with your roommate. Nevada went out one night and watched you through the big plate-glass windows of your boxing club. He watched you and Jules spar, and he watched as the two of you laughed and joked around while others were fighting.
Halloween night at the club, Nevada almost thought you were there. From his perch on his balcony, he caught a glimpse of a woman that looked like you, dressed up in a skimpy school girl uniform. Catholic school girl, nun – same difference. But when he got a closer look, it wasn’t you at all.
Nevada was furious, so he had his guys bring him a woman that kind of looked like you. She was plenty willing, and she was thinner and had bigger tits. When she pressed herself against him, though, he felt nothing but irritated, and not the hot-irritated he felt with you. Just angry-irritated. When he pushed her head downwards, his cock remained maddeningly soft. He had to close his eyes and imagine you on your knees in front of him, and even that only half worked. He ended up shoving the woman away with a string of curses in Spanish, leaving her to stumble down the stairs in tears.
“Fuck!” he yelled, kicking at the chair on the balcony. He ordered a bottle of whiskey and took it into his office, downing half of it until he fell into a drunken slumber on his new fucking couch.
*****
You didn’t bother dwelling on the Nevada situation. Was he amazing in bed? Yes. Did you enjoy the verbal back-and-forth with him? Also yes.
Were you going to start wearing low-cut dresses to keep him interested? No. And were you going to bother arguing with him over his life choices? Fuck no. If he wanted to get gunned down over some old-fashioned turf war, over marijuana of all things, let him. In ten years, you could always go smoke a legal, recreational joint from a boutique shop over his grave and tell his bones, “I told you so.”
You had bigger issues anyway. Your termite program had drudged up some horrifying information, and you had to mull over what to do.
You were the financial planner for Meredith’s family – her father, Gaines, and her brother, Alastair. Christ, their rich-person names alone were enough to provoke homicidal feelings. But after Nevada had blown up at you, you had gone home and launched your spy program, making digital copies of their devices.
You worked through their email – the usual pile of invitations to charity events and golf outings and long weekends overseas. Nothing worth exploring.
Then you noticed that Gaines’ computer had an external disk drive plugged into it when you made the copy. Your program had copied the external drive. You opened up an innocuous folder labeled “Taxes.”
It wasn’t taxes. It wasn’t spreadsheets or documents at all. It was one terabyte of photos – pictures that you would never be able to unsee, pictures that made you sprint to your bathroom to throw up until there was nothing left in your stomach.
Gaines was in some of the pictures, and in some of the others was Alastair. The pictures were high-res, and both men were clearly identifiable – Gaines’ thick mane of silver hair and signet class ring, Alastair’s coke-bloated moon face. Not that you had any faith in the criminal justice system to prosecute and convict them. Gaines’ brother was a judge with the second circuit, for fuck’s sake, and that didn’t even scratch the surface of all the money their family gave to police organizations.
You saved the photos to a clean disk drive and contemplated your next steps. Sometimes when you had no faith in any institution, you could only count on yourself. And your roommate Jules, of course.
*****
Nevada tried texting you first, and when you didn’t respond, he tried calling. You didn’t respond to that, either, so he sent flowers. He sent so many flowers that Gabe had to tell him that the florist was reporting that you were refusing delivery. You had apparently told the florist to divert the flowers to a nearby old folks’ home, and to spite you, Nevada let the deliveries go there for an entire fucking week.
Nevada rarely ever felt bad about his actions. He was almost pure id; most of his decisions were based around the pleasure principle. If it felt good, he did it. Fucking, smoking, drinking, beating the shit out of competitors.
For some reason, he felt bad about the last time he spoke with you. His head had been killing him, and he was chafing under the belief that you were trying to mold him into something he wasn’t.
He hadn’t meant for it to escalate as it did. He didn’t really even mean what he had said about your wardrobe choices – in fact, now that he knew what you looked like naked, he almost enjoyed your business suits. They made him feel like he was in on a secret, knowing what you looked like underneath them.
More practically, even if he didn’t want to give up his life choices, you had pointed out that he may not be able to stop it. His own fucking brother-in-law in Santiago had brought up similar concerns during a call a few days earlier. He had praised Nevada’s decision to buy that second bar. Nevada had the good sense to feel a bit (just a bit though) ashamed to take the credit for that.
You were ignoring his texts, calls, and flowers, so he camped out outside your boxing club on Thursday night. He watched you and your roommate walk in and shed your outer layers and warm up. He watched Jules take to the ring to spar with another woman while you worked on the heavy bag. You laid out a steady pattern of punches, your eyes narrowed and your face intense in a way he hadn’t seen before. He watched you eventually take to the ring, sparring with a much larger man, your gloved fists a flurry against your partner until the instructor broke you up.
He watched the class end. You and Jules pulled your outerwear back on, grabbed your bags, and made your way outside. Nevada climbed out of his Escalade and slammed his door loud enough for you to turn and look. He watched your eyes narrow as you saw him, then you turned and murmured something to Jules. Your roommate nodded and stood back while you made your way over to him.
“Stalking me now?” you asked. You crossed your arms, and Nevada gazed at you. You were in workout gear – a heavy, oversized sweatshirt that enveloped your top half, and black compression tights on your lower half. Your hair was up in a ponytail, and a few loose tendrils framed your face, limp with sweat.
“You gonna return my calls?” he bit back.
“No.”
Nevada nodded in the direction of the giant windows of the boxing club. “You pretend that you were punching me?”
The corner of your mouth twitched as if you were fighting a smile. “Not this time.”
“You want to punch me now?”
“If I did, it’s only because you deserve it.” You shifted on your sneakered feet, kicking at the cracked sidewalk. “What do you want, Ramirez?”
So you weren’t on a first-name basis with him anymore. He sighed and looked back at the SUV to make sure his guys couldn’t hear him. “I wanted to apologize,” he muttered.
You tilted your head at him, scrutinizing him for a moment. “For what?” you finally asked. “For making assumptions about me? For getting on my case about my wardrobe choices? Don’t bother.” You turned and nodded over your shoulder, and your roommate walked over to join you.
“Let me at least give you a ride,” he said. He hated the pleading edge in his voice.
“No, thanks.” You and Jules turned and started to walk away.
Nevada felt the all too familiar flush of irritation at you. He had apologized, and Trujillo never apologized. And yet you were walking away from him anyway.
“You’ll want to be careful,” he called out after you. “There’s a lot of big, bad guys out in the dark. A couple of pretty things like you might not do well.”
The flush of irritation was replaced by a chill as both you and Jules turned around at his comment. Your faces wore twin expressions of cold assurance, and he felt nailed in place by your icy smirks.
“We’re the pretty things that the big, bad guys should be afraid of,” you replied. Your voice was low, and you stared at him for a moment before turning away.
“Get home safe, Trujillo,” Jules added with a slight smirk before she joined you in walking away.
#nevada ramirez#nevada ramirez imagine#nevada ramirez x reader#nevada ramirez x you#trouble in the heights#trouble in the heights fanfiction#tropes-and-tales
9 notes
·
View notes
Text
What Can I Do With A Cisco CCNA Certification?
Cisco Certified Network Associates (CCNA) are one of the world's most sought-after network professionals. Having a CCNA certification opens up a wide variety of job opportunities and can lead to higher salaries.

A Cisco CCNA certification is valuable in terms of the potential salary and employment opportunities that result from this certification. MyComputerCareer also offers his CCNA training as part of the Cybersecurity Specialist Curriculum. For more information, please contact us immediately.
This article explains what a CCNA certification is, what it includes, and the skills it teaches. We will also discuss the different positions you can get with a CCNA certificate and the salaries you can earn with this certificate.
What Is The CCNA Certification?
The Cisco Certified Network Associate (CCNA) certification is a well-known computer networking credential. CCNA certification helps entry-level network engineers, professional network engineers, support network engineers, and network administrators learn basic networking concepts.
Over one million CCNA certificates have been distributed to fully certified professionals since Cisco first introduced certificates in 1998. CCNA certifications cover a wide range of networking topics and help prepare learners for future advances in networking technology.
CCNA certification topics include:
OSI model: Physical Layer, Data Link Layer, Network Layer, Transport Layer, and Application Layer
IP routing: static and dynamic routing protocols
IP addressing: Fourth Generation IPv4 (IPv), Internet Control Message Protocol (ICMP), Address Resolution Protocol (ARP), and Cisco IOS
Network security: Firewalls, password security, virtual private networks (VPNs), and intrusion detection systems
VLANs and WLANs: Access Control Lists (ACLs), VLAN Trunking Protocol (VTP), and Cisco Wireless LAN Controller (WLC) IP Services
Routing protocols (OSPF, EIGRP, and RIP): Cisco IOS, Cisco Express Forwarding (CEF), and Cisco Dynamic Multiprotocol Label Switching (DMVPN) WAN
CCNA certification validates many of the skills a network engineer needs. You will also need various soft skills such as communication, problem solving, organization and customer service. CCNA certification also provides network professionals with the information and skills they need to effectively operate Cisco and Microsoft Office suite applications. This certification empowers aspiring and current network engineers to use industry-specific tools in their daily work.
However, please note that Cisco certifications are valid for three years. If the certification expires, the holder may retake her CCNA certification exam, obtain another Associate certification, pass the Core Technology exam, or for renewal she must complete 40 Continuing Education (CE) credit must be obtained.
What IT Jobs Can You Get With a CCNA Certification?
The Cisco Certified Network Associate (CCNA) certification validates a user's knowledge and skills in network administration. Salaries for this degree average about $80,000 per year. Many employees are looking for Cisco certified professionals because of their extensive experience with Cisco routers and switches. Cisco network equipment is used by most of the Fortune 500 companies.
Network administrator: Network administrators are responsible for the day-to-day operation of computer networks. Keep your network running smoothly and resolve any issues that may arise.
System Administrator: System administrators are responsible for the maintenance and operation of computer systems. It installs new software, patches existing software, and performs other tasks to keep your system running smoothly.
Network analyst: Network analysts are responsible for analyzing computer networks and making recommendations to improve their efficiency. They may also be responsible for designing new networks or implementing changes to existing networks.
Network design engineer: Network design engineers are responsible for designing and implementing computer networks. We work with our customers to understand their needs and design networks that meet those needs.
Infrastructure Engineer: Infrastructure engineers are responsible for the physical components of computer networks such as routers, switches, and cables. Install and maintain these components to keep your network running smoothly.
Unified Communications Engineer: Unified Communications Engineers are responsible for designing and implementing unified communications systems. Unified communication systems allow users to communicate across multiple devices such as phones, computers, and tablets.
Solution designer: Solution design engineers are responsible for designing and implementing solutions to problems encountered in computer networks. They work with customers to understand their needs and design solutions that meet those needs.
Cloud Engineer: Cloud engineers are responsible for designing and implementing cloud-based solutions. Cloud-based solutions allow users to access data and applications from anywhere in the world.
Data Center Engineer: Data center engineers are responsible for the operation of data centers. Install and maintain the hardware and software that make up your data center.
Network administrator: Network administrators are responsible for the day-to-day operation of computer networks. Ensure the smooth operation of your network and fix any problems that may arise.
Cloud Architect: Cloud architects are responsible for designing and implementing cloud-based solutions. Cloud-based solutions allow users to access data and applications from anywhere in the world.
VoIP Engineer: VoIP engineers are responsible for designing and implementing Voice over IP (VoIP) solutions. VoIP solutions allow users to communicate using voice and video over the Internet.
Cooperating engineer: Collaboration engineers are responsible for designing and implementing solutions that enable users to collaborate. Collaboration solutions allow users to share data, applications, and files.
Telecom Engineer: Telecommunications engineers are responsible for the design and implementation of telecommunications systems. Telecommunications systems allow users to communicate using voice, video, and data.
Depending on your skills, years of experience, valid qualifications, and other criteria, you may be better suited for one job than another. The Cisco Certified Network Associate (CCNA) is a great place to start for anyone looking to get into networking.
Conclusion
Earning the Cisco Certified Network Associate (CCNA) certification is a great way to start your networking career. A CCNA certification contains a wealth of knowledge that will help you in your career. A CCNA certification can lead to higher salaries and help you find jobs in a variety of occupations. There are a variety of Cisco certifications you can earn, each useful in your career. A CCNA certification is just the beginning of your journey to a successful networking career.
591cert offers a certification program that includes CCNA Certification. If you're interested in becoming a CCNA and growing your IT career, take a free career assessment. We are happy to answer your questions.
2 notes
·
View notes
Text
The reason why Your Small Business Needs Such 6 Tech Resources

cybersecurity news
Technology plays a progressively integral role in corporate. It can open opportunities and create extraordinary opportunities for forward-thinking small businesses. If you’re looking to move while using times, here are 6 tech tools your business interest needs.
cybersecurity news
1 . Fog up Solutions
Cloud precessing is increasingly popular amongst small businesses. Cloud offerings offer an array of gains, including flexibility together with scalability, reduced will cost you, seamless software integration and improved collaborative working. With fog up systems, businesses will eliminate risks involving downtime and spar for customers on a level using field with opponents who have already bought innovative IT assistance.
Cloud computing is furthermore a more cost-effective replacement of the more traditional kinds of technology, and it gives safe access to data, programs and reports on the go, which is important for remote teams and additionally individuals who are working from home.
2 . not Voice over Web Protocol (VoIP)
VoIP (Voice over Online world Protocol) phone devices are incredibly valuable for small businesses.
Because of this type of phone program, you can lower the buying price of making and getting calls significantly and you'll enjoy a range of elements, including video in addition to conference calls. VoIP affords seamless shopper interaction and it’s also reliable along with secure.
Organization Management Platforms
Effort is key so that you can successful teamwork. Nowadays, small businesses can take benefit for a variety of tools together with platforms, which are meant to make life less difficult for groups and let teams to get with each other and work on jobs virtually.
Outsourced Managed IT Products and services
If you run a company, there are significant important things about outsourcing IT. Handling an experienced IT supplier will give you peace of mind, give back time to focus on your core aspects of jogging your business and show you how to benefit from expert tips and tailored THAT services.
Outsourced was able IT services include everything from security and additionally cloud services to be able to consulting, infrastructure in addition to disaster planning, which happens to be essential for companies working with where there is a possibility of hurricanes along with storm damage.
THE APPLICATION experts will work on hand to draw up a good package that caters to your requirements and your funding. With managed products and services, you’ll have access to THIS support and your specialist will also help you make best use of efficiency and work flow to boost performance together with save money.
VPN
Cybersecurity is an significant consideration for decision makers. Although many people anticipate that hackers solely target large firms, small businesses are actually a lot more vulnerable. Statistics declare that over 40% from cyber attacks include small companies. Being business owner, there are various steps you can take to try and limit risks and look after your business.
A VPN, or virtual exclusive network, encrypts your home business data and your speaking, preventing anyone who’s not authorized to find your systems out of getting hold of your data. In addition , a VPN definitely will strengthen security concurrently as allowing fast and simple access for certified employees.
Fraud Blocking Software
Junk emails account for greater than 50% of all e-mails. Spam blocking program is designed to prevent inboxes clogging up along with fake emails and additionally junk. It is estimated that relating to 2019 and 2023, around 60 thousand spam emails shall be sent every day.
Like cybercrime becomes far more sophisticated, investing in fraud blocking software is normally increasingly useful for business owners. With the right application in place, you can steer clear of potentially dangerous e-mail addresses from reaching inboxes and increase staff member productivity.
At the moment, by using millions of people working remotely, and Internet application at an all-time high due to Coronavirus lockdowns, spam postings are more common than ever before. Google alone can be blocking around 17 million Coronavirus rip-off emails daily.
It’s important to note that designed for business owners and their particular employees, being aware of a signs of phishing emails and junk can be extremely beneficial, even so the best thing to do is usually to install spam preventing software. This will give up spam from approaching your business inboxes in addition to save your employees time frame when managing e-mail.
Technology has revolutionized the way businesses get the job done. If you run small businesses and you’re hoping to push your business in front, save time along with money, minimize cybersecurity risks and provide your visitors and employees by having a superior experience, think about investing in these ground breaking tech tools.
2 notes
·
View notes
Text
How to Create Your Own Profitable VPN Business with a White-Label VPN Software Solution?

In recent years, the use of VPNs has skyrocketed as people have become more and more concerned about their privacy and security. In fact, a study by GWI found that 34% of internet users now use a VPN to protect their online privacy.
This has created a huge opportunity for businesses that are able to offer a reliable and affordable VPN service. And one of the best ways to do this is by using a white-label VPN software solution. A White-label VPN software solution is a service that is provided by a third-party provider that allows companies to resell the service under their own brand. This type of service has many benefits for both the provider and the customer. For the provider, it is a way to increase their customer base and revenue. For the customer, it is a way to get a high-quality VPN service at a lower cost.
What do you Need to Get Started: A White-Label VPN Software Solution
The easiest way to get started with a white-label VPN service is to find a provider that offers a white-label VPN software solution. A white-label VPN software solution can provide your business with a custom VPN website and an app. Once you've found a provider, you'll need to decide on the features and functionality that you want for your custom VPN website or app. This type of software allows you to brand the VPN product as your own while retaining all the features and benefits of a top-quality VPN service. Then, working with the provider, you'll need to create branding for your product.
Finally, you'll need to market and promote your new custom VPN website or app. This can be done through online marketing channels, such as social media, search engine optimization (SEO), and paid advertising.
Creating a Profitable Business Model
Running a VPN service can be profitable if you have the right tools in place. A white-label VPN software solution can help you get started quickly and easily. In the past, setting up a VPN service required significant technical expertise and hardware. However, this is no longer the case. Today, there are numerous white-label VPN software solutions that make it easy for anyone to set up and run a VPN service.
One of the advantages of using a white-label VPN software solution is that it allows you to avoid the need to develop your own custom software. This can be a costly and time-consuming process. With a white-label solution, all of the heavy liftings has already been done for you, so you can focus on marketing and growing your business.
Another advantage of using a white-label VPN software solution is that it gives you access to a wide range of features.
Marketing your VPN Service
When you’re starting a new VPN business, the vital step is marketing your service. You need to get the word out there so that people know what you offer and how it can benefit them. There are a variety of ways to market your VPN service, and some will work better than others depending on your target audience and budget.
One of the most effective ways to market a VPN service is through online advertising. You can place ads on popular websites and blog networks, or use targeted advertising to reach specific groups of people who might be interested in your service. Online advertising is relatively affordable and can be very effective in reaching a large number of people.
Another great way to market a VPN service is through word-of-mouth marketing. If you have happy customers, they will likely tell their friends and family about your service.
Offering Value-Added Services
Setting up a VPN business service can be a great way to make money, but it’s important to offer value-added services in order to attract and keep customers. Here are some ideas for things you can offer:
1. Offer a variety of plans with different features so that customers can find the plan that’s right for them.
2. Offer a free trial or a money-back guarantee so that people can try out the service without risking their money.
3. Offer customer support so that people can get help if they need it.
4. Offer software for different devices, so that people can use the VPN service on their computer, phone, or tablet.
5. Offer discounts or promotional pricing for people who refer new customers to the service.
6. Offer a referral program, where you can give a small amount of money to people who refer new customers to the service.
7. Offer a privacy guarantee so that your users know that their data is safe with you.
In conclusion, starting a VPN business can be a profitable venture, but it's important to choose the right VPN software solution provider. By choosing an experienced white-label VPN software solution like Smarters, you can create a custom VPN service that meets the needs of your customers. Smarters is a VPN Software Solution for VPN Business providers. It is a software-as-a-service (SaaS) that helps you build your own virtual private network (VPN) service in a few days. Plus, Smarters will provide you to manage your business efficiently and provide a high level of customer support. So, if you're ready to start your own VPN business, be sure to consider a white-label VPN software solution service like Smarters.
0 notes
Text
Get Tailor Made White-Label VPN Website - Smarters

If you are looking for a tailor-made white-label VPN website, Smarters is the perfect choice. We can provide you with a fully customized website that meets your specific needs and requirements. We will work closely with you to ensure that your website is exactly what you want it to be.
In addition to a tailored website, we can also provide you with all the features and functionality that you need to make your VPN business a success. We have a wide range of features available, including a powerful VPN server, a user-friendly control panel, and much more. We also offer 24/7 support to help you with any problems you may have.
If you want a white-label VPN website that is designed specifically for your business, contact Smarters today. We will be happy to discuss your needs and provide you with a free quotation.
Contact us now: https://www.whmcssmarters.com/vpn-software-solution
0 notes
Text
Adobe steals your color

When a company breaks a product you rely on — wrecking decades of work — it’s natural to feel fury. Companies know this, so they try to deflect your rage by blaming their suppliers. Sometimes, it’s suppliers who are at fault — but other times, there is plenty of blame to go around.
For example, when Apple deleted all the working VPNs from its Chinese App Store and backdoored its Chinese cloud servers, it blamed the Chinese government. But the Chinese state knew that Apple had locked its devices so that its Chinese customers couldn’t install third-party apps.
That meant that an order to remove working VPNs and apps that used offshore clouds from the App Store would lock Apple customers into Chinese state surveillance. The order to block privacy tools was a completely foreseeable consequence of Apple’s locked-down “ecosystem.”
https://locusmag.com/2021/01/cory-doctorow-neofeudalism-and-the-digital-manor/
In 2013, Adobe started to shift its customers to the cloud, replacing apps like Photoshop and Illustrator with “Software as a Service” (“SaaS”) versions that you would have to pay rent on, every month, month after month, forever. It’s not hard to understand why this was an attractive proposition for Adobe!
Adobe, of course, billed its SaaS system as good for its customers — rather than paying thousands of dollars for its software up front, you could pay a few dollars (anywhere from $10-$50) every month instead. Eventually, of course, you’d end up paying more, assuming these were your professional tools, which you expected to use for the rest of your life.
For people who work in prepress, a key part of their Adobe tools is integration with Pantone. Pantone is a system for specifying color-matching. A Pantone number corresponds to a specific tint that’s either made by mixing the four standard print colors (cyan, magenta, yellow and black, AKA “CMYK”), or by applying a “spot” color. Spot colors are added to print jobs after the normal CMYK passes — if you want a stripe of metallic gold or a blob of hot pink, you specify its Pantone number and the printer loads up a separate ink and runs your media through its printer one more time.
Pantone wants to license this system out, so it needs some kind of copyrightable element. There aren’t many of these in the Pantone system! There’s the trademark, but that’s a very thin barrier. Trademark has a broad “nominative use” exception: it’s not a trademark violation to say, “Pantone 448C corresponds to the hex color #4a412a.”
Perhaps there’s a copyright? Well yes, there’s a “thin” database copyright on the Pantone values and their ink equivalents. Anyone selling a RIP or printer that translates Pantone numbers to inks almost certainly has to license Pantone’s copyright there. And if you wanted to make an image-editing program that conveyed the ink data to a printer, you’d best take a license.
All of this is suddenly relevant because it appears that things have broken down between Adobe and Pantone. Rather than getting Pantone support bundled in with your Adobe apps, you must now pay $21/month for a Pantone plugin.
https://twitter.com/funwithstuff/status/1585850262656143360
Remember, Adobe’s apps have moved to the cloud. Any change that Adobe makes in its central servers ripples out to every Adobe user in the world instantaneously. If Adobe makes a change to its apps that you don’t like, you can’t just run an older version. SaaS vendors like to boast that with cloud-based apps, “you’re always running the latest version!”
The next version of Adobe’s apps will require you to pay that $21/month Pantone fee, or any Pantone-defined colors in your images will render as black. That’s true whether you created the file last week or 20 years ago.
Doubtless, Adobe will blame Pantone for this, and it’s true that Pantone’s greed is the root cause here. But this is an utterly foreseeable result of Adobe’s SaaS strategy. If Adobe’s customers were all running their apps locally, a move like this on Pantone’s part would simply cause every affected customer to run older versions of Adobe apps. Adobe wouldn’t be able to sell any upgrades and Pantone wouldn’t get any license fees.
But because Adobe is in the cloud, its customers don’t have that option. Adobe doesn’t have to have its users’ backs because if it caves to Pantone, users will still have to rent its software every month, and because that is the “latest version,” those users will also have to rent the Pantone plugin every month — forever.
What’s more, while there may not be any licensable copyright in a file that simply says, “Color this pixel with Pantone 448C” (provided the program doesn’t contain ink-mix descriptions), Adobe’s other products — its RIPs and Postscript engines — do depend on licensable elements of Pantone, so the company can’t afford to tell Pantone to go pound sand.
Like the Chinese government coming after Apple because they knew that any change that Apple made to its service would override its customers’ choices, Pantone came after Adobe because they knew that SaaS insulated Adobe from its customers’ wrath.
Adobe customers can’t even switch to its main rival, Figma. Adobe’s just dropped $20b to acquire that company and ensure that its customers can’t punish it for selling out by changing vendors.
Pantone started out as a tech company: a way to reliably specify ink mixes in different prepress houses and print shops. Today, it’s an “IP” company, where “IP” means “any law or policy that allows me to control the conduct of my customers, critics or competitors.”
https://locusmag.com/2020/09/cory-doctorow-ip/
That’s likewise true of Adobe. The move to SaaS is best understood as a means to exert control over Adobe’s customers and competitors. Combined with anti-competitive killer acquisitions that gobble up any rival that manages to escape this control, and you have a hostage situation that other IP companies like Pantone can exploit.
A decade or so ago, Ginger Coons created Open Colour Standard, an attempt to make an interoperable alternative to Pantone. Alas, it seems dormant today:
http://adaptstudio.ca/ocs/
Owning colors is a terrible idea and technically, it’s not possible to do so. Neither UPS Brown nor John Deere Green are “owned” in any meaningful sense, but the companies certainly want you to believe that they are. Inspired by them and Pantone, people with IP brain-worms keep trying to turn colors into property:
https://onezero.medium.com/crypto-copyright-bdf24f48bf99
The law is clear that colors aren’t property, but by combining SaaS, copyright, trademark, and other tech and policies, it is becoming increasingly likely that some corporation will stealing the colors out from under our very eyes.
[Image ID: A Pantone swatchbook; it slowly fades to grey, then to black.]
505 notes
·
View notes
Text
Are Your Networks Secured? Discover the Importance of Network Security
You might not think about it often, but the security of your networks is essential. If you're not taking the necessary precautions, you're leaving yourself open to attack from criminals and hackers.
That's why it's important to understand the basics of network security and make sure you're doing everything you can to protect your systems. In this blog, we'll talk about the importance of network security and offer some tips for keeping your networks safe.

What is Network Security?
When you're talking about network security, what you're really talking about is protecting your data. That could be anything from customer data to trade secrets. And the bottom line is that if that data falls into the wrong hands, it can be destructive to your business.
So, what can you do to protect your networks and your data? Here are a few tips:
1. Make sure your networks are password-protected.
2. Install firewalls and anti-virus software.
3. Regularly update your software and operating systems.
4. Educate your employees about safe online practices.
5. Regularly back up your data.
Why is Network Security Important?
You might be thinking, "my computer is just for personal use, so I don't need to worry about network security." But that's where you'd be wrong.
Think about it. Most people use their computers for more than just personal tasks these days. They're using them to do their work, shop online, and bank online. And all of that information is stored on your computer.
If someone were to hack into your computer, they could access all of that information—and that's not something you want to happen. That's why it's so important to have network security in place. It helps protect your computer from unauthorized access, and it helps keep your information safe and secure.
How Can You Secure Your Networks?
It's essential to secure your networks proactively to protect your data and your systems. But what does that mean in practical terms?
Here are some simple steps you can take to secure your networks:
1. Update your software regularly. Many security vulnerabilities are fixed with updates, so make sure you install them as soon as they're available.
2. Use strong passwords and change them regularly. This is one of the simplest and most effective ways to protect your data.
3. Install a firewall and keep it up-to-date. A firewall is a critical piece of security software, and it's important to make sure it's always updated and current.
4. Install antivirus software and keep it up-to-date. Antivirus software is another essential layer of protection, and it's important to make sure it's always updated.
5. Educate your employees about safe online practices. It's essential to have a security culture in your organization, and one of the best ways to do that is to educate your employees about safe online practices.
What are Some Common Network Security Risks?
Small businesses are at a higher risk for cyber-attacks than larger businesses because they often don't have the same security measures in place. You need to be proactive about network security and put protocols in place to protect your business.
One of the most common ways hackers gain access to a company's network is through email phishing scams. They send an email that looks like it's from a legitimate source, but when you click on the link, it takes you to a malicious website. From there, the hacker can steal your passwords or install malware on your computer.
Another common security risk is using public Wi-Fi networks. When you're connected to a public Wi-Fi network, you're opening yourself up to attack. Hackers can easily spy on your traffic and steal your personal information.
The best way to protect you from these types of attacks is to use a VPN (virtual private network) when you're connected to public Wi-Fi, and never open attachments or click on links in emails from unknown sources.
How Can You Prevent Network Security Risks?
You can prevent network security risks by following some simple steps:
1. Educate your employees about the dangers of phishing and spam emails.
2. Install a firewall and anti-virus software on all of your devices.
3. Use strong passwords and change them regularly.
4. Restrict access to sensitive data to authorized users only.
5. Keep your operating systems and software up-to-date.
6. Regularly back up your data.
If you follow these guidelines, you can help protect your networks from hackers, malware, and other online threats.
What are Some Best Practices for Network Security?
It's important to understand that network security is about more than just protecting your data. It's also about protecting your investment.
Think about it: the more connected we become as a society, the more valuable our networks become. That's why it's so important to take steps to safeguard them against attack.
So, what can you do to protect your networks? Here are some best practices:
1. Keep your software up-to-date. Many attacks are successful because they take advantage of outdated software vulnerabilities.
2. Use strong passwords and change them regularly. A strong password is one that is difficult to guess and is at least 8 characters long.
3. Install a firewall and make sure it's enabled. A firewall is a software or hardware that helps protect your computer from unauthorized access.
4. Restrict access to your networks by only allowing authorized users access.
5. Educate your employees on basic security measures, such as not opening suspicious emails or clicking on links in them.
Conclusion
Whether you're a business or an individual, network security is important. With the growing number of cyber-attacks, it is essential to have a secure network. There are a variety of ways to secure a network, and it is important to find the right solution for your business. You can contact Metis Technology for further network security details.
2 notes
·
View notes
Text
GOD DAMN!! I am gonna cry at work. Tears of relief and joy!!
We have had SO MANY issues with AWS and our Support Partner. They just dont understand windows and honestly just push tickets around.
We have had the same issues going in for over 1.5 years and they dont know what the issue is.
In addtion to that, at one point AWS' DNS fucked up and it took a week for the support partner to accept it was AWS, not us, and then another week for AWS to fix it.
That is the back story.
The reason why I want to cry is becuase it SEEMS like MS Azure has an offering that does EXACTLY what we need!!!
We are an independent software vendor, and they have configurations to deploy just a remoteapp for customers. Out of the box. With MFA and VPN support built in.
God damn I am about to cry tears of FREAKIN' JOY!!!!
2 notes
·
View notes
Text
Vpn ipvanish mac

VPN IPVANISH MAC FOR MAC
VPN IPVANISH MAC MAC OS X
VPN IPVANISH MAC FULL
VPN IPVANISH MAC SOFTWARE
VPN IPVANISH MAC FREE
VPN IPVANISH MAC FOR MAC
While there download ipvanish vpn for mac are incredible advantages to be leveraged just by using the IPVanish platform, is It All Sunshine and Roses With IPVanish? Click on the following link to download the ExpressVPN Client for your device: About IPVanish: IPVanish lied about their logging policies (also to us)).this means you can access any country-restricted websites such as Hulu and Netflix even though they are blocked by our ISP/country. Think of this not as a fake ID but as a shell or ghost identity that you can slip into and assume,we do not recommend to use them anymore, you can download ipvanish vpn for mac read everything about it in this article. Download ipvanish vpn for mac in India: allowing you to move across the Internet without detection or download ipvanish vpn for mac being able to be tracked or traced.
VPN IPVANISH MAC SOFTWARE
IPVanish Setup Tutorials: IPVanish provides simple tutorials allowing new customers to download the software easily and quickly, allowing customers to choose their preferred settings and VPN protocol. The IPVanish service provides the hidden IP addresses to solve all the above reasons to remain anonymous. Understanding that the rate of technology shifts and changes faster than even the weather sometimes, the IPVanish has been built on the back of multiple VPN protocols (OpenVPN, PPTP, and L2TP) and also allows to simultaneous VPN connections to. Access Unrivaled Technological Advances With IPVanish. Each and every time you step out from behind their dedicated platform you expose yourself. The cold hard reality of using the Internet is that every single time you log download ipvanish vpn for mac on everything about you is being tracked by a million and one different entities,the IPVanish software can be installed on any number of devices and download ipvanish vpn for mac is compatible on both Windows and Mac operating systems. PPTP ) on your tablet or cell phone.whether you know it or not. So there is no point in cracking the IPVanish download ipvanish vpn for mac software without a active subscription, iPVanish downloads for every platform: IPVanish for Windows ( visit download page )) You can download a Client for PPTP, Download ipvanish vpn for mac this may be a download ipvanish vpn for mac limitation for some users but for most, this is more than sufficient as IPVanish has once again been recognized as the number one VPN service by m and their editors. The company does only support legal P2P and torrents though, this came to light when the reviewer was downloading download ipvanish vpn for mac P2P, which IPVanish guarantee is possible while utilizing their bine that with instant access to download ipvanish vpn for mac well overIP addresses, more thanVPN servers (with more being added on a regular basis)) strategically located all over the globe to offer ridiculously high and smooth performance,it is not possible to use their servers.
Prevent your IP address from the other connection users and online marketers and other search partners.
Hide the location of your area and replace it with another one.
Encrypted the traffic and browsing from the router tunnel.
Save your online presence and create a private network eco.
Provide the security from the hackers on every.
Access to any restricted website or media.
It stops the throttling of internet service provider they can’t slow down your connection speed. No information showing for invitee in scheduling assistant on mac. 3000+ Ip’s added with different countries servers giving the untraceable surfing at the everywhere in the world. It’s a most popular VPN In the world and delivers the speedy service all over the world at a comfortable price.
VPN IPVANISH MAC FREE
For the premium access here we provide IPVanish crack setup which is entirely free of cost.
VPN IPVANISH MAC FULL
IPVanish is a premium VPN which can provide the full security proof identity on the internet, but we know that every user doesn’t have money to use pro version of this software.
VPN IPVANISH MAC MAC OS X
It’s a latest Windows and Mac OS X version for Intel processors. IPVanish VPN 3.1.1 Crack hides original identity on the internet when we browse something. Open the IPVanish application and navigate to IPVanish VPN (Menu in the top-left corner of the screen) > Preferences. To access the VPN logs on IPVanish for macOS,do the following: 1.

2 notes
·
View notes