#IoT safeguard
Text
Unmasking the Invisible: Ethical Hackers and the Art of Vulnerability Hunting

In today's digital age, our reliance on technology has created a vast and interconnected landscape. While this interconnectedness offers undeniable benefits, it also introduces vulnerabilities – chinks in the armor that can be exploited by malicious actors. Imagine a grand castle, its walls seemingly impenetrable. But what if there were hidden weaknesses, unseen passages known only to a select few? This is where ethical hackers, the unsung heroes of cybersecurity, come in. They are the vulnerability hunters, the digital detectives on a relentless quest to identify and expose these weaknesses before they can be used for malicious purposes.
This blog delves into the fascinating world of vulnerability hunting, exploring the role of ethical hackers in safeguarding our digital assets. We'll uncover the techniques they employ, the challenges they face, and the importance of cyber security training Mumbai for fostering a skilled workforce of ethical hackers.
The Invisible Threat: Unveiling Vulnerabilities
Imagine a digital thief attempting to break into a bank vault. They wouldn't simply smash through the front door; they'd meticulously search for weaknesses – a faulty security system, a hidden ventilation shaft. Similarly, vulnerabilities in software, hardware, and network configurations act as those hidden access points for malicious hackers. These vulnerabilities can be:
Software Bugs: Errors in the code that can be exploited to gain unauthorized access or cause unexpected behavior.
Misconfigurations: Improper settings in network devices or software applications that create security gaps.
Zero-Day Attacks: Previously unknown vulnerabilities that attackers exploit before software vendors have a chance to issue a patch.
These vulnerabilities are often invisible to the untrained eye. This is where ethical hackers, also known as white hats, step in. They act as the security guardians, wielding specialized tools and techniques to hunt for these hidden weaknesses.
The Art of the Hunt: Techniques of a Vulnerability Hunter
Ethical hackers employ a diverse arsenal of techniques in their pursuit of vulnerabilities. Here are some of the most common methods which you can learn in cyber security training mumbai :
Network Scanning: Ethical hackers use specialized tools to scan networks and identify devices, open ports, and potential security weaknesses.
Penetration Testing: This involves simulating a cyberattack to identify vulnerabilities that could be exploited by malicious actors. Ethical hackers attempt to gain unauthorized access to systems using various techniques, mimicking the methods black hats might employ.
Social Engineering Testing: This involves testing the organization's security awareness by attempting to trick employees into revealing sensitive information or clicking on malicious links.
Code Review: Ethical hackers meticulously examine the code of software applications to identify potential vulnerabilities and bugs.
These techniques require a deep understanding of cybersecurity principles, programming languages, and hacking methodologies. Cyber security training Mumbai can equip individuals with the necessary skills and knowledge to become proficient vulnerability hunters.
The Challenges of the Hunt: A Constant Cat-and-Mouse Game
The world of vulnerability hunting is a constant cat-and-mouse game. As technology evolves, so do the vulnerabilities that ethical hackers need to identify. Here are some of the key challenges they face:
The Ever-Expanding Attack Surface: With the increasing use of cloud computing, mobile devices, and the Internet of Things (IoT), the attack surface – the potential points of entry for attackers – is constantly expanding. This makes it more challenging for ethical hackers to identify all potential vulnerabilities.
Zero-Day Attacks: The constant threat of zero-day attacks, where attackers exploit previously unknown vulnerabilities, keeps ethical hackers on their toes. They need to be constantly researching and developing new methods to identify these vulnerabilities before they can be used in real-world attacks.
Staying Ahead of Black Hats: Malicious hackers are constantly innovating and developing new attack techniques. Ethical hackers need to stay up-to-date on the latest hacking trends and methodologies to ensure they can identify vulnerabilities before they are exploited.
The Value of the Hunt: Why Vulnerability Hunting Matters
Vulnerability hunting plays a critical role in safeguarding our digital infrastructure. By proactively identifying and patching vulnerabilities, ethical hackers can significantly reduce the risk of successful cyberattacks. Here are some of the key benefits of vulnerability hunting:
Reduced Risk of Cyberattacks: By identifying and patching vulnerabilities, ethical hackers make it more difficult for malicious actors to gain unauthorized access to systems and data.
Improved Security Posture: The process of vulnerability hunting helps organizations identify and address weaknesses in their overall security posture, leading to a more robust defense.
Enhanced Compliance: Many regulations require organizations to conduct regular vulnerability assessments. Ethical hacking helps organizations meet these compliance requirements.
Cyber security training Mumbai can equip individuals with the skills to become ethical hackers, contributing to a safer digital landscape. These courses can provide valuable knowledge on vulnerability hunting methodologies, penetration testing techniques, and ethical hacking best practices.
2 notes
·
View notes
Text
Maximizing ROI: The Cost-Effectiveness of Amazon Web Services (AWS)
In today's digitally driven landscape, cloud computing has become synonymous with innovation and operational efficiency for businesses worldwide. Among the plethora of cloud service providers, Amazon Web Services (AWS) stands tall, offering an extensive suite of tools and solutions to empower organizations on their path to digital transformation. This in-depth exploration navigates through the core features, advantages, and transformative impact that AWS brings to businesses of all sizes.

Introducing Amazon Web Services (AWS)
Amazon Web Services, commonly referred to as AWS, is a cloud computing platform introduced by Amazon.com in 2006. Since its inception, AWS has redefined the accessibility and utilization of computing resources, storage solutions, and an array of IT services. Its distinguishing factors lie in its unmatched scalability, reliability, and diverse service offerings, making it the preferred choice across industries, from startups to enterprise-level corporations and government entities.
Scalability: Harnessing Elasticity for Dynamic Growth
AWS's hallmark feature is its elastic scalability, empowering businesses to seamlessly adjust their computing resources according to fluctuating demands. With AWS, organizations can effortlessly scale their infrastructure up or down, ensuring optimal performance and cost efficiency. Whether handling sudden spikes in website traffic or launching new applications, AWS provides the agility necessary to respond swiftly to evolving business needs.
Reliability: Building Upon a Foundation of Resilience
Reliability is a cornerstone of cloud computing, and AWS excels in this domain. By leveraging multiple data centers distributed across different geographic regions, AWS offers a highly redundant infrastructure, minimizing the risk of downtime and ensuring uninterrupted service availability. Through the strategic distribution of workloads across various availability zones, AWS provides inherent fault tolerance, enabling businesses to achieve exceptional levels of reliability for their critical applications and services.
Cost-effectiveness: Maximizing Value with Flexible Pricing Models
In a competitive market, cost optimization is paramount for businesses. AWS's pay-as-you-go pricing model enables organizations to pay solely for the resources they consume, eliminating the need for upfront investments in hardware or long-term commitments. This flexible pricing structure, coupled with robust cost management tools like AWS Cost Explorer and AWS Budgets, empowers businesses to manage their cloud expenditures effectively and optimize return on investment (ROI).

Security: Fortifying Digital Assets with Comprehensive Protections
Security is a top priority in the cloud, and AWS places great emphasis on it. Through stringent security measures such as encryption, access controls, and network security protocols, AWS provides a secure environment for sensitive data and critical workloads. Additionally, AWS offers compliance certifications tailored to various industry standards, ensuring that businesses can meet regulatory requirements seamlessly. Whether safeguarding customer data or protecting intellectual property, AWS instills confidence through its commitment to best-in-class security practices.
Diverse Service Portfolio: Enabling Innovation Across Industries
AWS boasts a diverse and extensive service portfolio, catering to a myriad of use cases and industry verticals. From foundational services like compute instances (EC2) and storage solutions (S3) to advanced offerings such as machine learning (Amazon SageMaker) and Internet of Things (IoT) platforms, AWS provides the essential tools needed to drive innovation and unlock new opportunities. Whether developing mobile applications, analyzing vast datasets, or deploying global e-commerce platforms, AWS offers the comprehensive suite of services to support diverse business objectives.
Flexibility and Customization: Tailoring Solutions to Unique Needs
A key strength of AWS lies in its flexibility and customization capabilities. With a vibrant ecosystem of third-party integrations and tools, AWS empowers businesses to tailor their cloud environments to align with specific requirements. Whether implementing hybrid cloud architectures, adopting DevOps practices, or integrating seamlessly with existing IT systems, AWS offers the flexibility necessary to adapt and innovate within the dynamic business landscape.
Conclusion: Embracing the Future with AWS
In summary, Amazon Web Services (AWS) transcends the realm of mere cloud computing—it serves as a catalyst for innovation, efficiency, and growth. With its unmatched scalability, reliability, cost-effectiveness, security measures, and diverse service portfolio, AWS empowers businesses to realize their full potential in the digital age. Whether aspiring to disrupt markets as a startup or striving for operational excellence as an enterprise, AWS provides the indispensable tools and services to transform visions into reality. Embrace the future of cloud computing with AWS and embark on a journey of endless possibilities.
2 notes
·
View notes
Text
Crafting Digital Transformation: The Expertise of a dApp Development Company

Digital transformation has become imperative for businesses navigating the ever-evolving technological landscape. Among the myriad tools and strategies, dApp development stands out as a pivotal means of crafting a seamless digital transformation experience. A reputable dApp development company plays a crucial role in guiding businesses through this intricate process.
Understanding dApp Development
Decentralized applications (dApps), a cornerstone of blockchain technology, offer transparency, security, and efficiency. The process involves designing, developing, and deploying these applications, harnessing the power of blockchain for a wide range of functionalities.
Choosing the Right dApp Development Company
Selecting the right partner for your digital transformation journey is paramount. Look for a dApp development company with a proven track record, relevant experience, and a portfolio that aligns with your business goals.
Services Offered by dApp Development Companies
These specialized firms provide a spectrum of services, including ideation, design, development, and deployment. They tailor solutions to the unique needs of each business, ensuring a customized and effective digital transformation.
Case Studies
Real-world case studies exemplify the impact of dApp development on businesses. These success stories illustrate how companies achieved enhanced efficiency, improved customer satisfaction, and significant growth through digital transformation.
Benefits of Investing in dApp Development
Investing in dApp development yields numerous benefits, including increased operational efficiency, streamlined processes, and elevated user experiences. These advantages contribute to a competitive edge in the market.
Challenges in dApp Development
While the benefits are substantial, challenges in dApp development exist. Addressing issues such as scalability, integration, and security is crucial for a successful digital transformation journey.
Future Trends in dApp Development
Staying abreast of emerging trends is essential. Technologies like artificial intelligence, Internet of Things (IoT), and smart contracts are shaping the future of dApp development. Adapting to these trends ensures the sustainability of digital solutions.
Client Testimonials
Client testimonials provide valuable insights into the practical impact of dApp development. Hearing directly from businesses that have undergone digital transformation showcases the tangible benefits of partnering with a reputable dApp development company.
Cost Considerations in dApp Development
Understanding the factors influencing the cost of dApp development helps in making informed decisions. Balancing quality and budget considerations ensures a cost-effective yet impactful digital transformation.
Security in dApp Development
Prioritizing security measures is non-negotiable. Robust security protocols safeguard dApps and the underlying blockchain infrastructure, ensuring data integrity and user trust.
Scalability of dApp Solutions
Planning for scalability is integral to future-proofing digital solutions. A well-designed dApp should seamlessly accommodate growth, adapting to the evolving needs of the business.
Industry-Specific dApp Solutions
Industries have unique requirements, and dApp development can be tailored to meet these specific needs. From healthcare to finance, examples abound of successful industry-focused dApp solutions.
Collaboration and Communication
Effective collaboration between businesses and dApp development teams is paramount. Transparent communication channels foster understanding, ensuring that the final product aligns with the client's vision.
Conclusion
In conclusion, a dApp development company serves as a guiding force in the digital transformation journey. From conceptualization to deployment, their expertise ensures a smooth transition, unlocking the full potential of decentralized applications. Businesses keen on embracing digital transformation should explore the services of reputable dApp development companies, paving the way for a future-ready and competitive enterprise.
FAQs
What is a dApp development company?
A dApp development company specializes in designing and deploying decentralized applications, leveraging blockchain technology for enhanced functionality.
How does digital transformation benefit businesses?
Digital transformation enhances operational efficiency, improves customer experiences, and provides a competitive advantage in the market.
What challenges are associated with dApp development?
Challenges include scalability, integration issues, and security concerns that require careful consideration and strategic solutions.
What industries can benefit from industry-specific dApp solutions?
Virtually any industry can benefit, including healthcare, finance, logistics, and more, with tailored dApp solutions addressing specific industry needs.
How can businesses ensure the security of their dApps?
Businesses can ensure security by implementing robust security protocols, conducting regular audits, and staying informed about the latest cybersecurity trends.
2 notes
·
View notes
Text
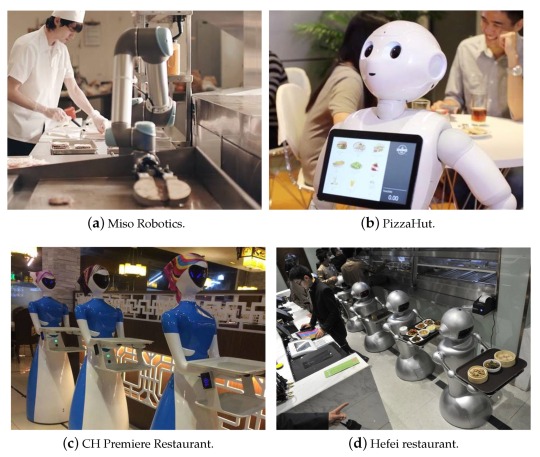
1. The rise of the drive-through window in the quick-service sector has been greatly aided by communication tools like headsets and intercom systems, which allow employees to interact with one another in an effective and efficient manner.
2.Our restaurant employs video surveillance to safeguard both our reputation and the safety of our food and service, as well as the well-being of our staff and patrons.

3. Technology advancements have made it possible to automate a number of HR procedures, including hiring and training, and to give real-time data and analytics for workforce management optimization.
4. In the next five years, hardware advancements particularly in robotics, sensors, and IoT devices will probably have the biggest effect on foodservice operations.
2 notes
·
View notes
Text
Navigating the Digital Revolution: A Comprehensive Guide to Digital Transformation Services
In the fast-paced landscape of today's business world, staying ahead means embracing the digital revolution. Digital transformation has become more than just a buzzword; it's a strategic imperative for businesses aiming to thrive in an increasingly competitive environment. In this comprehensive guide, we'll explore the intricacies of Makclan Digital transformation services and how they can empower your organization to navigate the complexities of the digital era.
Understanding Digital Transformation Services
Digital transformation services encompass a broad spectrum of technologies and strategies designed to leverage digital technologies to reshape organizational processes, culture, and customer experiences. From cloud computing and data analytics to artificial intelligence and the Internet of Things (IoT), Makclan Digital these services aim to drive efficiency, innovation, and growth.
The Drivers of Digital Transformation
The need for digital transformation is often fueled by various factors, including changing customer expectations, evolving market dynamics, and advancements in technology. To stay competitive, businesses must identify their unique drivers and leverage digital transformation services accordingly.
Key Components of Digital Transformation Services
1. *Cloud Computing:* Embracing cloud solutions enable businesses to scale operations, enhance flexibility, and reduce infrastructure costs. The cloud forms the backbone of many Makclan digital transformation initiatives.
2. *Data Analytics:* Harnessing the power of data provides valuable insights for informed decision-making. Analytics tools allow organizations to extract actionable intelligence from vast amounts of data, driving strategic initiatives.
3. *Artificial Intelligence (AI) and Machine Learning (ML):* Integrating AI and ML technologies automate processes, improves efficiency, and enables predictive analysis. These technologies empower businesses to make data-driven decisions and enhance customer experiences.
4. *Cybersecurity:* With increased reliance on digital technologies comes the need for robust cybersecurity measures. Makcaln Digital transformation services include implementing advanced security protocols to safeguard sensitive information.
5. *IoT Integration:* The Internet of Things connects devices and systems, fostering real-time communication and data exchange. This connectivity enhances operational efficiency and facilitates the development of smart, interconnected ecosystems.
Choosing the Right Digital Transformation Service Provider
Selecting the right partner is critical for a successful digital transformation journey. Consider factors such as expertise, track record, scalability, and the ability to tailor solutions to your specific business needs. A reliable service provider acts as a strategic collaborator, guiding you through each phase of the transformation process.
Overcoming Challenges in Digital Transformation
Despite the myriad benefits, digital transformation is not without its challenges. Resistance to change, cultural shifts, and the complexity of integrating new technologies are common obstacles. A comprehensive strategy that addresses these challenges head-on is essential for a smooth and successful transformation.
The Impact on Organizational Culture
Digital transformation extends beyond technology; it's a cultural shift that requires buy-in from all levels of an organization. Fostering a culture of innovation, continuous learning, and adaptability is crucial for sustained success in the digital era.
Realizing the Benefits of Digital Transformation
The benefits of digital transformation are manifold. Improved operational efficiency, enhanced customer experiences, and the ability to respond swiftly to market changes are just a few of the advantages. Successful digital transformation positions your organization as an agile, forward-thinking industry leader.
Conclusion
In conclusion, navigating the digital revolution through comprehensive digital transformation services is not just a choice; it's a necessity for businesses aiming to remain relevant and competitive in the era Of Makclan Digital. By understanding the key components, selecting the right service provider, overcoming challenges, and fostering a culture of innovation, your organization can embark on a transformative journey towards a digitally empowered future. Embrace the opportunities presented by the digital era, and position your business for sustained success in the dynamic landscape of today's business world.
#Digitaltransformation#SeoagencyinPennsylvania#Linkbuildingserviceprovider#contentdevelopment#affiliatemarketing#linkbuilding#leadgeneration#ecommercesolutions#onlineshopping#digitalproducts#ecommercesoftware#highqualityleads#businessgrowth#leadgenerationservices#ebusiness#digitalmarketingcompany#seocompany
3 notes
·
View notes
Text
In today's digitally connected world, cyber security has become a paramount concern. It encompasses the practice of safeguarding systems, networks, and data from digital attacks, unauthorized access, or damage. With the rapid growth in online transactions, social media, and Internet of Things (IoT) devices, vulnerabilities have increased, making cyber security more critical than ever.
Attackers employ a variety of methods, such as malware, ransomware, phishing, and social engineering, to breach defenses. Individuals, businesses, and governments must stay vigilant by keeping software up to date, utilizing strong, unique passwords, and employing multi-factor authentication.
Investing in robust security measures not only protects sensitive information but also maintains trust and integrity in digital relationships. In an era where data breaches can lead to significant financial and reputational losses, cyber security is not just a technological concern but a fundamental aspect of modern life.
4 notes
·
View notes
Text
The Future of Semiconductors: Unveiling a World of Possibilities

**The Future of Semiconductors: Unveiling a World of Possibilities**
As we stand on the brink of a new era, the semiconductor industry finds itself at the heart of a technological revolution. The impact of semiconductors on our lives has been profound, driving advancements across industries and shaping the very fabric of our modern civilization. But what lies ahead for this dynamic and transformative field? Let's delve into the future of semiconductors and the boundless possibilities that await us.
**1. Quantum Leap in Computing:**
The race towards quantum computing is intensifying, and semiconductors will play a pivotal role in unlocking its true potential. Quantum processors, built on novel semiconductor materials, have the power to process vast amounts of data in a fraction of the time it takes traditional computers. The future of computing will transcend current limitations, empowering us to solve complex problems previously deemed insurmountable.
**2. AI and Machine Learning:**
The era of artificial intelligence is upon us, and semiconductors will serve as the backbone of AI and machine learning applications. With the growing demand for AI-driven technologies in autonomous vehicles, robotics, healthcare, and more, the semiconductor industry is set to witness an unprecedented surge in AI-focused chip designs. Neuromorphic computing, inspired by the human brain's architecture, could unlock revolutionary AI capabilities, paving the way for cognitive computing and self-learning systems.
**3. The Internet of Things (IoT) Revolution:**
As IoT proliferates, the demand for energy-efficient and high-performance semiconductor devices will skyrocket. We envision a future where billions of interconnected devices communicate seamlessly, facilitated by advanced semiconductor technologies. Ultra-low-power processors, sensors, and wireless communication chips will define the landscape of the IoT revolution, shaping smart cities, wearables, and an interconnected world.
**4. Green and Sustainable Semiconductors:**
Sustainability will be a driving force in the semiconductor industry's future. Innovations in materials and manufacturing processes will lead to environmentally friendly and energy-efficient semiconductor solutions. From eco-friendly chip packaging to renewable energy-powered fabs, the industry will strive to minimize its carbon footprint, contributing to a greener tomorrow.
**5. Silicon Photonics and Beyond:**
The integration of photonics with silicon promises a new era of ultra-high-speed data transmission and processing. Silicon photonics will revolutionize data centers, enabling faster communication between chips and reducing data bottlenecks. Moreover, emerging technologies like 2D materials and carbon nanotubes offer exciting possibilities for futuristic semiconductor devices that could outperform traditional silicon-based chips.
**6. Security and Privacy:**
With the increasing dependence on connected devices, security and privacy will be paramount. Future semiconductor designs will prioritize hardware-based security features to protect against cyber threats and safeguard sensitive data. Trusted execution environments and secure enclaves will become integral components of semiconductor devices, ensuring user confidence in an interconnected world.
**7. Global Collaboration and Talent Development:**
The future of semiconductors will thrive on global collaboration and talent development. International partnerships will foster innovation, as countries pool their resources and expertise. Companies will invest in nurturing a diverse and skilled workforce, driving advancements and promoting a culture of inclusion and creativity.
The future of semiconductors is bright, brimming with possibilities that have the potential to redefine our world. As innovators, engineers, and visionaries, let's embrace this transformative journey together. Let's harness the power of semiconductors to build a future that empowers, connects, and inspires generations to come.
*The future is here, and it's in the hands of those who dare to dream and innovate with semiconductors as their guiding light.*
2 notes
·
View notes
Text
Accelerating transformation with SAP on Azure
Microsoft continues to expand its presence in the cloud by building more data centers globally, with over 61 Azure regions in 140 countries. They are expanding their reach and capabilities to meet all the customer needs. The transition from a cloudless domain like DRDC to the entire cloud platform is possible within no time, and a serverless future awaits. Microsoft gives the platform to build and innovate at a rapid speed. Microsoft is enhancing new capabilities to meet cloud services' demands and needs, from IaaS to PaaS Data, AI, ML, and IoT. There are over 600 services available on Azure with a cloud adoption framework and enterprise-scale landing zone. Many companies look at Microsoft Azure security compliance as a significant migration driver. Microsoft Azure has an extensive list of compliance certifications across the globe. The Microsoft services have several beneficial characteristics; capabilities are broad, deep, and suited to any industry, along with a global network of skilled professionals and partners. Expertise in the Microsoft portfolio includes both technology integration and digital transformation. Accountability for the long term, addressing complex challenges while mitigating risk. Flexibility to engage in the way that works for you with the global reach to satisfy the target business audience.
SAP and Microsoft Azure
SAP and Microsoft bring together the power of industry-specific best practices, reference architectures, and professional services and support to simplify and safeguard your migration to SAP in the cloud and help manage the ongoing business operations now and in the future. SAP and Microsoft have collaborated to design and deliver a seamless, optimized experience to help manage migration and business operations as you move from on-premises editions of SAP solutions to SAP S/4 HANA on Microsoft Azure. It reduces complexity, minimizes costs, and supports end-to-end SAP migration and operations strategy, platform, and services. As a result, one can safeguard the cloud migration with out-of-box functionality and industry-specific best practices while immaculately handling the risk and optimizing the IT environment. Furthermore, the migration assimilates best-in-class technologies from SAP and Microsoft, packed with a unified business cloud platform.
SAP Deployment Options on Azure
SAP system is deployed on-premises or in Azure. One can deploy different systems into different landscapes either on Azure or on-premises. SAP HANA on Azure large instances intend to host the SAP application layer of SAP systems in Virtual Machines and the related SAP HANA instance on the unit in the 'SAP HANA Azure Large Instance Stamp.' 'A Large Instance Stamp' is a hardware infrastructure stack that is SAP HANA TDI certified and dedicated to running SAP HANA instances within Azure. 'SAP HANA Large Instances' is the official name for the solution in Azure to run HANA instances on SAP HANA TDI certified hardware that gets deployed in ‘Large Instance Stamps’ in different Azure regions. SAP or HANA Large Instances or HLI are physical servers meaning bare metal servers. HLI does not reside in the same data center as Azure services but is in close proximity and connected through high throughput links to satisfy SAP HANA network latency requirements. HLI comes in two flavors- Type 1 and 2. IaaS can install SAP HANA on a virtual machine running on Azure. Running SAP HANA on IaaS supports more Linux versions than HLI. For example, you can install SAP Netweaver on Windows and Linux IaaS Virtual Machines on Azure. SAP HANA can only run on RedHat and SUSE, while NetWeaver can run on windows SQL and Linux.
Azure Virtual Network
Azure Virtual Network or VNET is a core foundation of the infrastructure implementation on Azure. The VNET can be a communication boundary for those resources that need to communicate. You can have multiple VNETs in your subscription. If they weren't connected, we could call them Pierre in Azure wall; there will be no traffic flow in between. They can also share the same IP range. Understanding the requirements and proper setup is essential as changing them later, especially with the running production workloads, could cause downtime. When you provision a VNET, The private blocks must allocate address space. If you plan to connect multiple VNETs, you cannot have an overlapping address space. The IP range should not clash or overlap with the IP addressing in Azure while connecting on-premise to Azure via express route or site-site VPN. Configuring VNET to the IP address space becomes a DHP service. You can configure VNET with the DNS server's IP addresses to resolve services on-premise.VNETS can be split into different subnets and communicate freely with each other. Network security groups or NSGs are the control planes we use to filter traffic. NSGs are stateful but simple firewall rules based on the source and destination IP and ports.
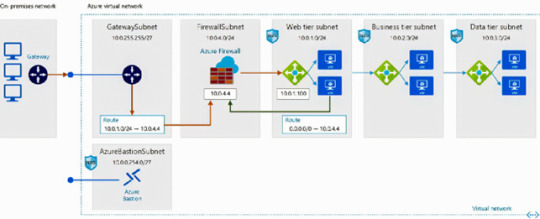
Azure Virtual Gateway
For extensive connectivity, you must create a virtual gateway subnet. When you create a virtual gateway, you will get prompted for two options: VPN or Express Route Gateway; with VPN, you cannot connect to the Express Route Circuit. If you choose the Express Route Virtual Gateway, you can combine both.
There are two types of VPN;
1) The point-to-site VPN is used for testing and gives the lowest throughput.
2) The site-site VPN connection can offer better benefits by bridging networks.
This VPN offers zero support for SLA and uses this connection as a backup for the recommended connection on Azure, called the express route. Express route is a dedicated circuit using hardware installed on your data center, with a constant link to ‘Microsoft Azure Edge’ devices. Express route is inevitable for maintaining the communication between application VNET running in Azure and on-premise systems to HLI servers. The express route is safer and more resilient than VPN as it provides a connection through a single circuit and facilitates second redundancy; this helps route traffic between SAP application servers inside Azure and enables low latency. Furthermore, the fast path allows routine traffic between SAP application servers inside Azure VNET and HLI through an optimized route that bypasses the virtual network gateway and directly hops through edge routers to HLA servers. Therefore, an ultra-performance express route gateway must have a Fast Path feature.
SAP HANA Architecture (VM)
This design gets centered on the SAP HANA backend on the Linux Suse or RedHat distributions. Even though the Linux OS implementation is the same, the vendor licensing differs. It incorporates always-on replication and utilizes synchronous and asynchronous replication to meet the HANA DB requirements. We have also introduced NetApp file share for DFS volumes used by each SAP component using Azure site recovery and building a DR plan for App ASCs and the web dispatches servers. Azure Active directory is used in synchronization with on-premises active directory, as SAP application user authenticates from on-premises to SAP landscape on Azure with Single Sign-On credentials. Azure high-speed express route gateway securely connects on-premises networks to Azure virtual machines and other resources. The request flows into highly available SAP central, SAP ABAP services ASCS and through SAP application servers running on Azure virtual machines. The on-demand request moves from the SAP App server to the SAP HANA server running on a high-performance Azure VM. Primary active and secondary standby servers run on SAP-certified virtual machines with a cluster availability of 99.95 at the OS level. Data replication is handled through HSR in synchronous mode from primary to secondary enabling zero recovery point objective. SAP HANA data is replicated through a disaster recovery VM in another Azure region through the Azure high-speed backbone network and using HSR in asynchronous mode. The disaster recovery VM can be smaller than the production VM to save costs.
SAP systems are network sensitive, so the network system must factor the design decisions into segmenting the VNETs and NSGs. To ensure network reliability, we must use low latency cross-connections with sufficient bandwidth and no packet loss. SAP is very sensitive to these metrics, and you could experience significant issues if traffic suffers latency or packet loss between the application and the SAP system. We can use proximity placement groups called PGS to force the grouping of different VM types into a single Azure data center to optimize the network latency between the different VM types to the best possible.
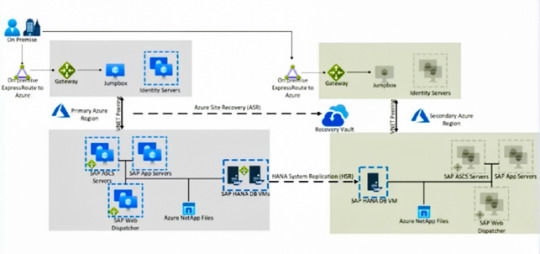
Security Considerations
Security is another core pillar of any design. Role-based Access control (RBAC) gets accessed through the Azure management bay. RBAC is backed up through AD using cloud-only synchronized identities. Azure AD can back up the RBAC through cloud-only or synchronized identities. RBAC will tie in those cloud or sync identities to Azure tenants, where you can give personal access to Azure for operational purposes. Network security groups are vital for securing the network traffic both within and outside the network environment. The NSGs are stateful firewalls that preserve session information. You can have a single NSG per subnet, and multiple subnets can share the same energy. Application security group or ASG handles functions such as web servers, application servers, or backend database servers combined to perform a meaningful service. Resource encryption brings the best of security with encryption in transit. SAP recommends using encryption at rest, so for the Azure storage account, we can use storage service encryption, which would use either Microsoft or customer-managed keys to manage encryption. Azure storage also adds encryption in transit, with SSL using HTTPS traffic. You can use Azure Disk Encryption (ADE) for OS and DBA encryption for SQL.
Migration of SAP Workloads to Azure
The most critical part of the migration is understanding what you are planning to migrate and accounting for dependencies, limitations, or even blockers that might stop your migration. Following an appropriate inventory process will ensure that your migration completes successfully. You can use in-hand tools to understand the current SAP landscape in the migration scope. For example, looking at your service now or CMDB catalog might reveal some of the data that expresses your SAP system. Then take that information to start drawing out your sizing in Azure. It is essential to ensure that we have a record of the current environment configuration, such as the number of servers and their names, server roles, and data about CPU and memory. It is essential to pick up the disk sizes, configuration, and throughput to ensure that your design delivers a better experience in Azure. It is also necessary to understand database replication and throughput requirements around replicas. When performing a migration, the sizing for large HANA instances is no different from sizing for HANA in general. For existing and deployment systems you want to move from other RDBMS to HANA, SAP provides several reports that run on your existing SAP systems. If migrating the database to HANA, these reports need to check the data and calculate memory requirements for the HANA instances.
When evaluating high availability and disaster recovery requirements, it is essential to consider the implications of choosing between two-tier and three-tier architectures. To avoid network contention in a two-tier arrangement, install database and Netweaver components on the same Azure VM. The database and application components get installed in three-tier configurations on separate Azure Virtual Machines. This choice has other implications regarding sizing since two-tier, and three-tier SAP ratings for a given VM differs. The high availability option is not mandatory for the SAP application servers.
You can achieve high availability by employing redundancy. To implement it, you can install individual application servers on separate Azure VMs. For example, you can achieve high availability for ASCS and SCS servers running on windows using windows failover clustering with SIOS data keeper. We can also achieve high availability with Linux clustering using Azure NetApp files. For DBMS servers, you should use DB replication technology using redundant nodes. Azure offers high availability through redundancy of its infrastructure and capabilities, such as Azure VM restarts, which play an essential role in a single VM deployment. In addition, Azure offers different SLAs depending on your configuration. For example, SAP landscapes organize SABC servers into different tiers; there are three diverse landscapes: deployment, quality assurance, and production.
Migration Strategies:- SAP landscapes to Azure
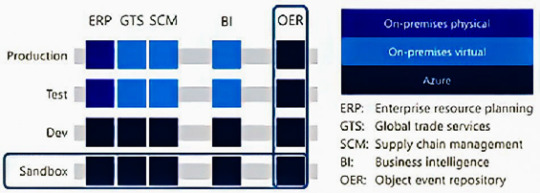
Enterprises have SAP systems for business functions like Enterprise Resource Planning(ERP), global trade, business intelligence(BI), and others. Within those systems, there are different environments like sandbox developments, tests, and production. Each horizontal row is an environment, and each vertical dimension is the SAP system for a business function. The layers at the bottom are lower-risk environments and are less critical. Those towards the top are in high-risk environments and are more critical. As you move up the stack, there is more risk in the migration process. Production is the more critical environment. The use of test environments for business continuity is of concern. The systems at the bottom are smaller and have fewer computing resources, lower availability, size requirements, and less throughput. They have the same amount of storage as the production database with a horizontal migration strategy. To gain experience with production systems on Azure, you can use a vertical approach with low-risk factors in parallel to the horizontal design.
Horizontal Migration Strategy
To limit risk, start with low-impact sandboxes or training systems. Then, if something goes wrong, there is little danger associated with users or mission-critical business functions. After gaining experience in hosting, running, and administering SAP systems in Azure, apply to the next layer of systems up the stack. Then, estimate costs, limiting expenditures, performance, and optimization potential for each layer and adjust if needed.
Vertical Migration Strategy
The cost must be on guard along with legal requirements. Move systems from the sandbox to production with the lowest risk. First, the governance, risk, compliance system, and the object Event Repository gets driven towards production. Then the higher risk elements like BI and DRP. When you have a new system, it's better to start in Azure default mode rather than putting it on-premises and moving it later. The last system you move is the highest risk, mission-critical system, usually the ERP production system. Having the most performance virtual machines, SQL, and extensive storage would be best. Consider the earliest migration of standalone systems. If you have different SAP systems, always look for upstream and downstream dependencies from one SAP system to another.
Journey to SAP on Azure
Consider two main factors for the migration of SAP HANA to the cloud. The first is the end-of-life first-generation HANA appliance, causing customers to reevaluate their platform. The second is the desire to take advantage of the early value proposition of SAP business warehouse BW on HANA in a flexible DDA model over traditional databases and later BW for HANA. As a result, numerous initial migrations of SAP HANA to Microsoft Azure have focused on SAP BW to take advantage of SAP HANA's in-memory capability for the BW workloads. In addition, using the SAP database migration option DMO with the System Migration option of SUM facilitates single-step migration from the source system on-premises to the target system residing in Azure. As a result, it minimizes the overall downtime. In general, when initiating a project to deploy SAP workloads to Azure, you should divide it into the following phases. Project preparation and planning, pilot, non-production, production preparation, go-live, and post-production.

Use Cases for SAP Implementation in Microsoft Azure
Use cases
How does Microsoft Azure help?
How do organizations benefit?
Deliver automated disaster recovery with low RPO and RTO
Azure recovery services replicate on-premises virtual machines to Azure and orchestrate failover and failback
RPO and RTO get reduced, and the cost of ownership of disaster recovery (DR) infrastructure diminishes. While the DR systems replicate, the only cost incurred is storage
Make timely changes to SAP workloads by development teams
200-300 times faster infrastructure provisioning and rollout compared to on-premises, more rapid changes by SAP application teams
Increased agility and the ability to provision instances within 20 minutes
Fund intermittently used development and test infrastructure for SAP workloads
Supports the potential to stop development and test systems at the end of business day
Savings as much as 40-75 percent in hosting costs by exercising the ability to control instances when not in use
Increase data center capacity to serve updated SAP project requests
Frees on-premises data center capacity by moving development and test for SAP workloads to Microsoft Azure without upfront investments
Flexibility to shift from capital to operational expenditures
Provide consistent training environments based on templates
Ability to store and use pre-defined images of the training environment for updated virtual machines
Cost savings by provisioning only the instances needed for training and then deleting them when the event is complete
Archive historical systems for auditing and governance
Supports migration of physical machines to virtual machines that get activated when needed
Savings of as much as 60 percent due to cheaper storage and the ability to quickly spin up systems based on need.
References
n.d. Microsoft Azure: Cloud Computing Services. Accessed June 13, 2022. http://azure.microsoft.com.
n.d. All Blog Posts. Accessed June 13, 2022. https://blogs.sap.com.
n.d. Cloud4C: Managed Cloud Services for Enterprises. Accessed June 13, 2022. https://www.cloud4c.com.
n.d. NetApp Cloud Solutions | Optimized Storage In Any Cloud. Accessed June 13, 2022. http://cloud.netapp.com.
4 notes
·
View notes
Text
Potential Use Cases of Blockchain Technology for Cybersecurity By Azgari Lipshy
By Azgari Lipshy
The potential use cases of blockchain technology for cybersecurity are numerous and varied. From providing a secure and decentralized way to store data to create an immutable record of transactions, blockchain has the potential to revolutionize the way we think about cybersecurity. This article will explore some potential use cases of blockchain technology for cybersecurity.
Cryptocurrencies are one of the most famous use cases of blockchain technology. They have been widely discussed in many articles, so we will not discuss them here. Instead, we will look at some of the lesser-known ways that blockchain technology can be used to enhance cybersecurity.
One of blockchain technology's most important use cases in today's data-driven market is providing a secure and decentralized way to store data. Businesses and organizations are increasingly dependent on data to make critical business decisions. The need to store data has also increased exponentially with the Internet of Things (IoT) proliferation. As a result, we have seen explosive growth in the amount of data being created every day. This data is increasing the risk of cyber-attacks and breaches. The security of such data is extremely important for businesses, governments, and individuals. As we have seen from recent data breaches, the consequences of losing sensitive information can be severe. Therefore, the need to secure data has never been greater.
In recent years, the frequency of cyberattacks has increased exponentially. Over the past few years, a staggering increase in data breaches has resulted in major financial losses and damaged business reputation. Blockchain is beginning to emerge as a viable cybersecurity attack mitigation solution in this situation. This is where Blockchain technology comes into play. It provides a tamper-proof and transparent method of storing and managing data. It is also decentralized,
Blockchain consists of data blocks that are linked together and secured using cryptography. In short, a blockchain is a digital ledger that cannot be tampered with or changed. Each block contains a timestamp so that it can be traced to its creation. Since the data is decentralized, it has no single point of failure and is extremely difficult to hack or manipulate. Decentralization also means no centralized authority governing the information and assets stored on the blockchain.
Below are some of the ways blockchain impacts the worldwide cyber security landscape:
A Decentralized Storage Solution
Data is unquestionably the new oil for business growth. Businesses need solutions to store and manage sensitive data intelligently and safely as they accumulate large amounts of it from many sources. Most organizations still keep their data in centralized locations nowadays, which is quite advantageous for hackers. Files and information are typically divided by decentralized storage services and distributed around other network nodes. Therefore, enterprises can safeguard their digital assets and information by utilizing blockchain-based storage solutions that offer decentralized storage capabilities.
Decentralized Instant Messaging
As more providers crowd the instant messaging industry, secure messaging has become a source of increasing controversy. Like any technology tool, it has advantages for the general public. It also presents the potential for malicious actors to undermine security and for people to abuse it to carry out unlawful or misleading activities. The recent influx of new messaging systems based on blockchain technology poses regulatory risks to enterprises and threatens to reinvent what "secure" in messaging implies.
While several private messaging systems have used blockchain and cryptocurrency technologies, the emphasis has been on boosting features’ anonymity. Blockchain technology is being pushed as a foundation for decentralized communications that offer users ultimate privacy and anonymity.
DDoS Attack Mitigation
A distributed denial-of-service (DDoS) attack is a malicious attempt to stop a network or server's regular activity by overloading the target or its infrastructure with an influx of Internet traffic. It has been noted that these attacks can use connected devices like routers, webcams, phones, televisions, etc., to launch attacks. The Hide and Seek virus is only one of several new DDoS attack types constantly emerging. It continues to function even after a system reboot.
However, an immutable and cryptographically secure blockchain can be a successful defense against such attacks. Several blockchain service providers claim that their solutions can defend against DDoS assaults by enabling users to join decentralized networks.
DNS Security Improvement
The internet's operational framework is the Domain Name System (DNS). It serves as a public directory connected to resources on the internet (like IP addresses) through domain names. Because of this, DNS is susceptible to attack from hackers who could bring down the website by using the link between their IP address and domain name. Numerous businesses and organizations have seen how such attacks prompted temporary shutdowns that cost them their most devoted clients and business partnerships.
By decentralizing the DNS records, blockchain can provide a prophylactic method to combat this nature of cyberattacks. A user's domain information can be immutably recorded on a distributed ledger, and immutable smart contracts can enable the connection. With this, it is clear that blockchain is becoming a workable option for protecting crucial business data and digital assets from threats.
Multi-Signature Authentication Model
One of the most critical threats to many businesses, employees, and individuals is tampering with usernames and passwords. Once a hacker has access to the main domain that contains the login information for numerous users, they have a virtual safe with a wealth of personal data. With blockchain technology, users can authenticate other users by validating their access to various devices without using usernames and passwords. This can already be seen in Multi-signature crypto wallets.
Conclusion
In conclusion, blockchain technology has great potential for improving cybersecurity. By decentralizing data and using cryptographic algorithms, blockchain can make it more difficult for hackers to access sensitive information. Additionally, smart contracts can help to automate security processes and make it easier to track compliance. With so many potential applications, it is clear that blockchain has the potential to play a major role in improving cybersecurity.
About The Author
Azgari Lipshy writes about technology, yoga and her solo travels around the world. She is a degreed quota-carrying technology industry sales and account management professional with progressive territory growth for enterprise and channel sales. She is an annual achiever that has worked as both an individual contributor key account manager and sales organization team leader.
4 notes
·
View notes
Text
The Insubordinate
“The IOT was never going to be just another magical order: we are the cats you cannot herd. So how do we keep things organised while safeguarding our personal autonomy within our Pact? Or, as it’s mostly asked, how does a Chaos Order work?One of the answers is the Insubordinate. This role is a mainstay of the Pact’s anti-authoritarian way of doing things but is by definition pretty alien to the majority of occulture.
[..]
These five roles of the Insubordinate consist of the following tasks.
Ensure that all explanations, speeches and teachings are clear to everyone and criticize those, which are not, and demand their clarification. Thus, the Fool’s task is to simulate ignorance where others pretend understanding.
Convey criticism with a certain easiness and impertinence. Thus the duty of the Jester is to take something appear ridiculous which others would like to diplomatically overlook.
Point out personal weaknesses and blind spots. Thus it is the responsibility of the Chaplain to handle personal issues in an impartial manner.
Receive reports on personal magical development without commenting on them. Thus it is the task of the Confessor to offer protection from laziness and self-satisfaction.
Hold the right to veto any instruction and to inform a Magus, the Section Head or the Council of the Magi about its exercise. Thus it is the Inquisitor’s duty to prevent the abuse of position.”
1 note
·
View note
Text
Exploring Technology Integration and Privacy Concerns in Shared Office Spaces in Ernakulam
Introduction
Shared office spaces have emerged as a popular choice for professionals seeking flexible and collaborative work environments in Ernakulam. These spaces offer a range of amenities and services, including advanced technology integration, to enhance productivity and connectivity. However, along with the benefits come privacy concerns that must be addressed to ensure a secure and comfortable working environment.
Technology Integration in Shared Office Spaces
Advanced Connectivity: Shared office spaces in Ernakulam are equipped with high-speed internet connectivity and Wi-Fi infrastructure to support the needs of modern businesses. Seamless connectivity enables professionals to work efficiently and collaborate with remote teams.
Smart Office Solutions: Many shared office spaces integrate smart office solutions such as IoT devices and automation systems to optimize space utilization and enhance operational efficiency. These technologies streamline tasks like room booking, temperature control, and access management.
Collaborative Tools: Shared office spaces offer a suite of collaborative tools and software platforms to facilitate communication and project management among tenants. Video conferencing, instant messaging, and cloud-based document sharing platforms enable seamless collaboration irrespective of physical location.
Security Measures: Technology integration also extends to security measures such as surveillance cameras, access control systems, and cybersecurity protocols to safeguard sensitive data and ensure the safety of occupants and their belongings.
Privacy Concerns in Shared Office Spaces
Confidentiality Risks: The open layout of shared office spaces may raise concerns about confidentiality, especially for businesses handling sensitive information. Discussions, phone calls, and confidential meetings can be overheard, potentially compromising privacy and confidentiality.
Data Security: Shared networks and communal devices pose risks to data security, as cyber threats and unauthorized access could lead to data breaches and loss of sensitive information. Businesses must implement robust cybersecurity measures to mitigate these risks.
Personal Space: Shared office spaces often lack dedicated personal space, which can impact privacy and comfort levels for individuals. Noise levels, distractions, and lack of privacy partitions may hinder concentration and productivity.
Compliance Issues: Businesses operating in shared office spaces must ensure compliance with data protection regulations and privacy laws. Failure to address privacy concerns could lead to legal implications and reputational damage.
Addressing Privacy Concerns through Technology
Privacy Enhancing Technologies (PETs): Shared office spaces can leverage PETs such as encryption, anonymization, and data minimization techniques to enhance privacy protection and minimize data exposure.
Privacy-By-Design Approach: Implementing privacy-by-design principles ensures that privacy considerations are integrated into the design and development of shared office space infrastructure and technology solutions from the outset.
User Education and Awareness: Educating tenants about privacy risks and best practices for safeguarding sensitive information fosters a privacy-conscious culture within shared office spaces. Regular training sessions and awareness programs can help mitigate privacy concerns.
Transparency and Consent: Shared office space operators should be transparent about data collection practices, usage policies, and security measures implemented within the premises. Obtaining explicit consent from tenants for data processing activities enhances trust and accountability.
Conclusion
Technology integration in shared office spaces offers numerous benefits for professionals in Ernakulam, ranging from enhanced connectivity and productivity to streamlined operations. However, privacy concerns must be addressed effectively to maintain a secure and comfortable working environment. By implementing appropriate technology solutions, privacy-enhancing measures, and fostering a culture of privacy awareness, shared office spaces can mitigate privacy risks and uphold the confidentiality and security of tenants' information.
0 notes
Text
The evolution of healthcare ransomware attacks - CyberTalk
New Post has been published on https://thedigitalinsider.com/the-evolution-of-healthcare-ransomware-attacks-cybertalk/
The evolution of healthcare ransomware attacks - CyberTalk


By Zac Amos, Features Editor, Rehack.com.
In recent years, ransomware has emerged as a critical threat to the healthcare industry, with attacks growing in frequency, sophistication and impact. These cyber assaults disrupt hospital operations, compromise patient safety and undermine data integrity.
Understanding how ransomware tactics have evolved — from basic phishing schemes to complex, multi-faceted attacks — enables healthcare organizations to develop more robust defenses. Staying informed about the latest trends and techniques that cyber criminals use allows healthcare providers to safeguard their systems and ensure the continuity of care.
Initial ransomware attacks
Early ransomware tactics in healthcare were relatively rudimentary but still impactful. The first known ransomware attack — the PC Cyborg or AIDS Trojan — occurred in 1989 and targeted roughly 20,000 researchers and medical institutions. This attack involved distributing infected floppy disks that encrypted file names and paying a ransom to unlock them.
Although primitive by today’s standards, this attack highlighted the vulnerability of healthcare systems. Hospitals faced significant disruptions, affecting patient care and operations. This early incident underscored the potential havoc that ransomware could wreak on the healthcare sector. It set the stage for more sophisticated future threats.
Evolution of attack vectors
The evolution of ransomware in healthcare has seen a significant shift; from simple phishing attacks to sophisticated social engineering techniques. Initially, attackers used basic phishing emails to trick individuals into downloading malicious software.
However, as defenses improved, cyber criminals adapted by using more advanced social engineering tactics. These methods involve conducting detailed research on targets, the creation of personalized messages and placing phone calls, as to gain trust and infiltrate systems.
Alongside this, Remote Desktop Protocol (RDP) exploits have surged. These exploits allow attackers to access healthcare networks remotely by exploiting weak passwords and unpatched systems.
The healthcare sector has also seen a rise in exploited vulnerabilities in medical devices and the IoT. Cyber criminals have increasingly targeted these interconnected systems — which often lack robust security measures — to launch attacks.
This trend was particularly evident in the fourth quarter of 2023. The healthcare industry accounted for 16% of all ransomware attacks, making it the second-most targeted sector during this period. Exploitation of vulnerabilities can disrupt medical services and poses significant risks to patient safety. In turn, this highlights the urgent need for enhanced cyber security measures in healthcare.
Advanced encryption and evasion techniques
As ransomware has evolved, attackers have developed more complex encryption methods to secure healthcare data more effectively. One notable tactic is double extortion, where cyber criminals encrypt data and threaten to release sensitive information if the victim doesn’t meet their demands. This dual threat has increased the pressure on targeted organizations.
Further, 74% of Chief Information Security Officers believe that AI-powered cyber threats, including advanced ransomware, significantly impact their organizations. Attackers are also implementing polymorphic malware, which constantly changes its code to avoid detection by traditional security systems. Techniques like this make it challenging to combat sophisticated threats.
Targeting larger and more critical institutions
Ransomware attackers have shifted from targeting small clinics to targeting large hospitals and extensive healthcare networks, resulting in more significant disruptions and higher ransom demands than previously. Larger institutions have substantial financial resources, which makes them attractive targets for cyber criminals seeking substantial payouts.
The financial impact of the attacks on larger healthcare organizations is profound. In 2023, experts reported data breaches costing an average of $10.93 million each. This cost increase underscores ransomware’s severe financial strain on healthcare providers. It affects their ability to deliver essential services and invest in further security measures.
Ransomware-as-a-service
The rise of Ransomware-as-a-Service (RaaS) platforms has contributed to the proliferation of ransomware attacks in the healthcare sector. These RaaS groups operate on various business models, including monthly subscriptions, one-time license fees, affiliate programs or pure profit-sharing arrangements.
Offering user-friendly interfaces and comprehensive support, RaaS has lowered the barrier to entry for cyber criminals. It even enables those with zero technical expertise to launch sophisticated attacks. This democratization of ransomware has led to an increase in the frequency and diversity of attacks. It poses a more significant threat to healthcare organizations that must now defend against an extremely broad range of adversaries.
Collaboration and sophistication of cyber criminals
The formation of ransomware syndicates and partnerships has further expanded the threat landscape in healthcare. Cyber criminal groups now share resources and intelligence, enhancing their capabilities and effectiveness. In fact, some RaaS operators provide ongoing technical support and grant access to private forums where hackers exchange tips and information, fostering a collaborative environment.
This collective effort allows more sophisticated attacks, as cyber criminals leverage advanced threat intelligence and surveillance to identify vulnerabilities and tailor their strategies. Consequently, healthcare organizations face increasingly coordinated and informed adversaries, making securing their systems even more challenging.
Countermeasures and mitigation strategies
In response to the evolution of advanced ransomware, healthcare organizations have had to enhance their defensive measures. Adopting multi-layered security approaches — involving a combination of firewalls, intrusion detection systems, regular software updates and employee training — has become paramount.
Additionally, AI and machine learning are crucial in detecting and preventing attacks. These technologies can analyze vast amounts of data in real time and identify unusual patterns more accurately than traditional methods. Leveraging AI-driven tools lets healthcare providers anticipate and mitigate ransomware attacks more effectively than otherwise. It also helps bolster their overall cyber security posture.
Adapting to an evolving threat
The need for continuous adaptation in cyber security strategies is critical as ransomware threats evolve and become more sophisticated. The future landscape of ransomware in healthcare will likely see more advanced tactics. This makes it essential for healthcare organizations to stay vigilant and proactive in their defense measures.
For more insights from Rehack Features Editor, Zac Amos, click here. Lastly, to receive practical cyber insights, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#000#2023#adversaries#affiliate#ai#AI-powered#analyses#attackers#barrier#Business#CNI#code#Collaboration#collaborative#Collective#comprehensive#compromise#continuous#critical infrastructure#cyber#cyber criminals#cyber security#Cyber Threats#cybersecurity#data#Data Breaches#data integrity#defense#defenses#democratization
0 notes
Text
Industrial Packaging Market: A Comprehensive Overview
Introduction
Effective industrial packaging plays a crucial role in protecting manufactured goods during transportation and storage. With the complexity of modern supply chains that involve multiple touch points, choosing the right packaging solutions becomes all the more important to prevent product damage. This article explores some key considerations for packaging and highlights how incorporating the right practices can boost efficiency.
Packaging Materials
One of the first steps in industrial packaging market is selecting appropriate materials. Common materials used for packaging include cardboard, plastics like polyethylene (PE), polypropylene (PP), polystyrene (PS), and corrugated fiberboard. Each of these has their strengths - cardboard is cost-effective while plastics provide moisture and impact resistance. It is important to choose materials based on the product type, intended transport and storage conditions. For example, electronics may need anti-static plastics to prevent damage from static electricity. Temperature and humidity sensitive goods require moisture barrier packaging. Fragile items need extra cushioning and protection.
Designing for Product Safety
Effective packaging design is essential to safeguard products from damage during transportation and warehousing. Packaging needs to be robust yet sustainable. Cushioning needs to absorb impacts without being too bulky. Secure closure and sealing methods prevent items from shifting during transit. Correct labelling with handling instructions ensures careful treatment. Integrated designs for stacking/nesting optimize space. Considerations for unit load capabilities allow consolidation into shipping containers or pallets. Traceability features like barcodes facilitate inventory management. Compliance with regional/global regulations is also important.
Streamlining Processes
Industrial packaging processes should focus on efficiency and waste reduction. Standardized packaging components allow automating assembly lines. Optimized box/container sizes reduce excess material. Reusable/returnable packaging like IBCs and plastic crates lower total costs. Pull-style kanban or push-style CONWIP systems match demand. Bulk packaging for identical parts improves load consolidation. Robotics automate repetitive tasks. RFID and real-time monitoring enhances visibility. Analytics provide packaging optimization insights. Such streamlining yields cost savings, sustainability gains and scalability for growth.
Ensuring Supply Chain Compliance
Modern supply chains involve intricate networks encompassing multiple countries, partners, and modes of transport. Non-compliance with packaging, labeling or shipping regulations can disrupt operations. Packaging needs to be designed keeping applicable international regulations in mind whether by air, sea, road or rail. Mandatory information like hazardous material labels, orientation arrows, stacking limits should be clearly displayed. Harmonized System (HS) codes facilitate customs clearance. Certifications prove quality/sustainability. Real-time monitoring maintains temperature/shock control. Compliance minimizes delays, damage claims and builds trust with customers and regulators.
Adopting New Technologies
Emerging technologies offer huge potential to transform industrial packaging market processes. Internet of Things (IoT) sensors allow real-time monitoring of package conditions, location tracking and predictive maintenance of transport equipment. Blockchain provides tamper-proof provenance information increasing transparency. Augmented/virtual reality aids training and remote troubleshooting. 3D printing customizes designs on demand. Robotics and autonomous vehicles automate material handling and fleet operations. Artificial intelligence recognizes patterns to optimize packaging selection, design defect prediction and demand forecasting. Adopters gain competitive advantages through increased visibility, efficiency and sustainability.
#Industrial Packaging Market Growth#Industrial Packaging Market Size#Industrial Packaging Market Share
0 notes
Text
The Future of Transportation: A Deep Dive into EV Services, Autonomous Vehicles, and the Connected Car with V2Soft

The transportation landscape is undergoing a seismic shift. Electric vehicles (EVs) are rapidly gaining traction, autonomous vehicles (AVs) are inching closer to reality, and the Internet of Things (IoT) is transforming cars into rolling data centres. This technological confluence presents both challenges and opportunities, and V2Soft is at the forefront of developing solutions to navigate this exciting new era.
The Rise of Electric Vehicles and the Need for EV Services Solutions
EVs are no longer a niche market; they are becoming mainstream. Consumers are drawn to their environmental benefits, lower running costs, and superior driving experience. However, the widespread adoption of EVs necessitates a robust infrastructure for charging and maintenance. V2Soft recognizes these needs and offers a comprehensive suite of EV services solutions, including:
Charging station management: V2Soft can design, develop, and implement software solutions for managing EV charging networks. These solutions can track energy usage, optimize charging schedules, and facilitate seamless user experiences.
Battery health monitoring: Maintaining optimal battery health is crucial for EV performance and longevity. V2Soft offers solutions that monitor battery health in real-time, predict potential issues, and schedule preventative maintenance.
Fleet management solutions: Businesses with electric fleets require specialized management tools. V2Soft develops solutions that track vehicle location, optimize routes for efficiency, and ensure timely charging for uninterrupted operations.
EV diagnostic tools: V2Soft can design tools for technicians to diagnose and troubleshoot issues specific to EVs. These tools can streamline maintenance processes and improve service quality.
By providing these EV services solutions, V2Soft empowers businesses and individuals to embrace the EV revolution with confidence.
The Coming Age of Autonomous Vehicles and V2Soft's Role
While fully autonomous vehicle services are not yet commonplace, significant advancements are being made in this field. AVs hold immense potential to revolutionize transportation, offering increased safety, reduced traffic congestion, and improved accessibility. V2Soft understands the complexities of AV development and offers its expertise in various areas:
Sensor integration: AVs rely on a multitude of sensors, including LiDAR, cameras, and radar, to perceive their surroundings. V2Soft can design solutions that integrate these sensors seamlessly, ensuring accurate data collection.
Data processing and analysis: AVs generate massive amounts of data from their sensors. V2Soft offers solutions for real-time data processing and analysis, enabling AVs to make informed decisions in dynamic environments.
Simulation and testing: Before hitting the roads, AVs need rigorous testing in simulated environments. V2Soft develops simulation platforms that replicate real-world scenarios, allowing for safe and efficient testing of AV software and hardware.
Cybersecurity solutions: AVs are vulnerable to cyberattacks, which could have catastrophic consequences. V2Soft develops robust cybersecurity solutions to safeguard AV systems from malicious actors.
V2Soft's contribution to AV development paves the way for a future where autonomous cars are a safe and reliable reality.
The Connected Car Revolution and the Power of the Internet of Things
The Internet of Things cars is transforming traditional cars into connected vehicles brimming with functionalities. These vehicles can collect data on vehicle performance, driver behavior, and the surrounding environment. V2Soft leverages the power of IoT to provide innovative solutions for the connected car:
Vehicle health monitoring: IoT sensors can track engine performance, tire pressure, and other vital aspects of a car's health. V2Soft offers solutions that analyze this data, alerting drivers to potential problems and facilitating preventative maintenance.
Usage-based insurance: With data on driving habits, usage-based insurance programs can be developed. V2Soft can design platforms that collect safe driving data, enabling insurers to offer personalized and fair premiums.
In-vehicle infotainment: Connected cars can become entertainment hubs. V2Soft can develop solutions that integrate navigation, streaming services, and other infotainment features, enhancing the driving experience.
Advanced driver-assistance systems (ADAS): IoT data can be used to improve ADAS features like automatic emergency braking and lane departure warning. V2Soft can design solutions that analyze real-time data to trigger these safety features proactively.
By harnessing the power of IoT, V2Soft is helping create connected cars that are not just vehicles but intelligent transportation systems.
V2Soft: A Partner in Building the Future of Transportation
Deep industry expertise (continued): V2Soft understands the challenges and opportunities presented by emerging technologies. This expertise allows them to develop solutions tailored to the specific needs of the evolving transportation landscape.
Focus on innovation: V2Soft is constantly pushing boundaries and exploring new ways to improve transportation. Their commitment to research and development ensures they remain at the cutting edge of technology.
Scalable solutions: V2Soft's solutions are designed to be scalable, adapting to the diverse needs of businesses and individuals. Whether managing a small fleet of EVs or developing a complex AV system, V2Soft has the solution.
Commitment to partnerships: V2Soft embraces collaboration and actively seeks partnerships with leading players in the automotive industry. These partnerships foster knowledge sharing and accelerate innovation.
A global perspective: V2Soft recognizes the global nature of the transportation industry. They develop solutions with a global perspective, ensuring their applicability across diverse markets and regulatory environments.
The Road Ahead: Embracing a Sustainable and Efficient Future
The convergence of EV services, autonomous vehicles, and connected cars promises a future of sustainable, efficient, and safe transportation. V2Soft is committed to playing a pivotal role in this transformation. By developing innovative solutions and fostering industry partnerships, V2Soft aims to empower businesses and individuals to embrace this exciting new era.
Here are some additional points to consider for the conclusion of your blog:
Briefly discuss potential challenges and how V2Soft is working to address them (e.g., ethical considerations for AVs, data privacy in connected cars).
End on a positive and optimistic note, reiterating V2Soft's commitment to building a better future of transportation for all.
Include a call to action, encouraging readers to learn more about V2Soft's solutions or even collaborate with them on future projects.
By incorporating these elements, you can create a compelling and informative blog that positions V2Soft as a leader in shaping the future of transportation.
0 notes
Text
Harnessing Data Science for Personalized Healthcare

Data Science's Impact on Personalized Healthcare
Delving into the realm of personalized healthcare, Data Science emerges as a transformative force, revolutionizing traditional healthcare paradigms. By harnessing vast troves of patient data, Data Science enables tailored treatment plans, predictive interventions, and real-time monitoring, fostering improved patient outcomes and healthcare efficacy. The concept of personalized healthcare encompasses individualized treatment strategies tailored to each patient's unique genetic makeup, medical history, and lifestyle factors. Through Data Science, healthcare providers can unlock insights into disease patterns, treatment responses, and prognostic indicators, paving the way for precision medicine approaches.
From predicting disease risks to optimizing treatment regimens, Data Science empowers healthcare practitioners to deliver targeted, proactive care that addresses patients' specific needs and maximizes therapeutic efficacy. Thus, the integration of Data Science in healthcare into personalized healthcare heralds a new era of patient-centered medicine, where treatments are not only evidence-based but also deeply personalized to enhance health and wellness outcomes.
Data Science's Integral Role and Ongoing Challenges in Personalized Healthcare
Embarking on the journey of personalized healthcare, Data Science emerges as both a guiding light and a compass, steering the course of patient-centered medicine. At its core, Data Science harnesses the power of analytics to construct intricate patient profiles, delving deep into medical histories, genetic predispositions, and lifestyle patterns. Through data-driven insights, healthcare practitioners can craft personalized treatment plans tailored to each individual's unique needs and circumstances. Predictive modeling further enhances this approach, enabling the anticipation of disease trajectories and the proactive adjustment of interventions to optimize outcomes.
Simultaneously, real-time monitoring facilitated by IoT devices empowers continuous feedback loops, allowing for dynamic adjustments to treatment regimens based on evolving patient conditions. However, amidst this landscape of innovation, formidable challenges loom on the horizon. Ethical considerations demand careful navigation, ensuring that personalized healthcare respects patient autonomy, privacy, and confidentiality. Data privacy and security concerns necessitate robust safeguards to protect sensitive health information from breaches and unauthorized access.
Moreover, regulatory frameworks must evolve to keep pace with the rapid advancements in personalized healthcare, balancing innovation with patient safety and compliance. As Data Science continues to shape the landscape of personalized healthcare, addressing these challenges remains paramount to realizing its full potential in revolutionizing healthcare delivery. Thus, as we forge ahead into this brave new world, it is imperative to navigate the complexities with diligence, foresight, and an unwavering commitment to advancing patient care.
Future Vistas of Data Science in Personalized Healthcare
As we peer into the horizon of personalized healthcare, the future beckons with a tapestry of emerging trends and advancements propelled by Data Science. Rapid strides in machine learning, artificial intelligence, and big data analytics promise to usher in an era of unprecedented precision and efficacy in healthcare delivery. From predictive analytics forecasting disease onset to advanced algorithms optimizing treatment regimens, the potential for innovation knows no bounds.
The ripple effects of these advancements extend far beyond the confines of the clinic, promising to reshape the very landscape of patient outcomes and healthcare delivery. With personalized treatment plans tailored to individual needs, patients can anticipate improved health outcomes, reduced hospitalizations, and enhanced quality of life. Moreover, the shift towards proactive, preventive care facilitated by Data Science holds the promise of alleviating healthcare burdens and reducing healthcare costs in the long term.
Amidst this wave of innovation, opportunities abound for collaboration and innovation across diverse sectors of the healthcare ecosystem. Cross-disciplinary partnerships between healthcare providers, technology firms, researchers, and policymakers hold the key to unlocking the full potential of Data Science in personalized healthcare. Together, they can harness collective expertise and resources to tackle complex healthcare challenges, drive innovation, and accelerate the translation of cutting-edge research into real-world solutions.
It is imperative to embrace these opportunities with open arms and a shared commitment to advancing patient-centered care. By harnessing the power of Data Science and fostering collaborative partnerships, we can chart a course towards a future where healthcare is not only personalized but also predictive, proactive, and profoundly impactful.
Embrace Data Science with Pattem Digital for Healthcare
The pivotal role of Data Science in enabling personalized healthcare cannot be overstated. As we reflect on our exploration, it becomes evident that Data Science holds the key to unlocking the full potential of personalized healthcare, revolutionizing patient care and healthcare delivery. Key takeaways underscore the transformative impact of Data Science in tailoring treatment plans, predicting disease trajectories, and enhancing patient outcomes. By embracing Data Science, healthcare stakeholders can harness its power to drive innovation, improve efficiencies, and ultimately, elevate the standard of patient care.
At Pattem Digital, we offer unparalleled expertise in Data Science services tailored to the unique needs of the healthcare industry. Our team of seasoned professionals combines technical proficiency with domain knowledge to deliver cutting-edge solutions that drive tangible results. With a proven track record of success and a commitment to excellence, choosing Pattem Digital means partnering with a trusted ally dedicated to shaping the future of healthcare through Data Science.
0 notes
Text
Electronic Filters Market Size, Trends, Growth and Analysis Forecast 2024 - 2031
The "Electronic Filters Market" is a dynamic and rapidly evolving sector, with significant advancements and growth anticipated by 2031. Comprehensive market research reveals a detailed analysis of market size, share, and trends, providing valuable insights into its expansion. This report delves into segmentation and definition, offering a clear understanding of market components and drivers. Employing SWOT and PESTEL analyses, the study evaluates the market's strengths, weaknesses, opportunities, and threats, alongside political, economic, social, technological, environmental, and legal factors. Expert opinions and recent developments highlight the geographical distribution and forecast the market's trajectory, ensuring a robust foundation for strategic planning and investment.
What is the projected market size & growth rate of the Electronic Filters Market?
Market Analysis and Insights :
Global Electronic Filters Market
Electronic filters market size is valued at USD 40,776.4 million by 2028 is expected to grow at a compound annual growth rate of 15.50% in the forecast period of 2021 to 2028. Data Bridge Market Research report on electronic filters provides analysis and insights regarding the various factors expected to be prevalent throughout the forecasted period while providing their impacts on the market’s growth.
Electronic filters are basically the four-terminal, signal processing filter in the form of electrical circuits, used to remove some avoidable features or components from a signal. They help protect the wireless connectivity used in sectors such as traffic, health, weather & environmental monitoring by blocking signals of frequencies outside the band. They can be passive or active on the basis of type. It is also majorly used in hospitals to eliminate disruptions in hospital networks.
The surging penetration of smartphones and connected devices and the heightened demand for reliable filters to safeguard telecommunications & military electronics across the globe are the major significant factors responsible for driving the growth of market over the forecast period of 2021 to 2028. Moreover, the factors such as the adoption of advanced technologies such as IoT, cloud computing and virtual reality, high penetration of LTE and VoLTE networks and growing customer demand for digital content fuels the growth of the electronic filters market. However, the factors such as high initial cost and dearth of technically skilled expertise ultimately hamper growth of electronic filters market. On the other hand, the advent of innovative products and 5G deployments across the globe are expected to create various new opportunities that will lead to the growth of the electronic filters market in the above mentioned forecasted period. The limited signal bandwidth of electronic filters is estimated to pose as a major challenge hindering the growth of the electronic filters market.
This electronic filters market report provides details of new recent developments, trade regulations, import export analysis, production analysis, value chain optimization, market share, impact of domestic and localized market players, analyses opportunities in terms of emerging revenue pockets, changes in market regulations, strategic market growth analysis, market size, category market growths, application niches and dominance, product approvals, product launches, geographic expansions, technological innovations in the market. To gain more info on electronic filters market contact Data Bridge Market Research for an Analyst Brief, our team will help you take an informed market decision to achieve market growth.
Browse Detailed TOC, Tables and Figures with Charts which is spread across 350 Pages that provides exclusive data, information, vital statistics, trends, and competitive landscape details in this niche sector.
This research report is the result of an extensive primary and secondary research effort into the Electronic Filters market. It provides a thorough overview of the market's current and future objectives, along with a competitive analysis of the industry, broken down by application, type and regional trends. It also provides a dashboard overview of the past and present performance of leading companies. A variety of methodologies and analyses are used in the research to ensure accurate and comprehensive information about the Electronic Filters Market.
Get a Sample PDF of Report - https://www.databridgemarketresearch.com/request-a-sample/?dbmr=global-electronic-filters-market
Which are the driving factors of the Electronic Filters market?
The driving factors of the Electronic Filters market include technological advancements that enhance product efficiency and user experience, increasing consumer demand driven by changing lifestyle preferences, and favorable government regulations and policies that support market growth. Additionally, rising investment in research and development and the expanding application scope of Electronic Filters across various industries further propel market expansion.
Electronic Filters Market - Competitive and Segmentation Analysis:
Global Electronic filters Market, By Type (Low Pass Filter, High Pass Filter, Bandpass Filter, Band Reject Filter, All-Pass Filter), Application (Power Supplies, Audio Electronics, Radio Communications, Analog to digital Communication), Country (U.S., Canada, Mexico, Brazil, Argentina, Rest of South America, Germany, Italy, U.K., France, Spain, Netherlands, Belgium, Switzerland, Turkey, Russia, Rest of Europe, Japan, China, India, South Korea, Australia, Singapore, Malaysia, Thailand, Indonesia, Philippines, Rest of Asia-Pacific, Saudi Arabia, U.A.E, South Africa, Egypt, Israel, Rest of Middle East and Africa) Industry Trends and Forecast to 2031.
How do you determine the list of the key players included in the report?
With the aim of clearly revealing the competitive situation of the industry, we concretely analyze not only the leading enterprises that have a voice on a global scale, but also the regional small and medium-sized companies that play key roles and have plenty of potential growth.
Which are the top companies operating in the Electronic Filters market?
The major players covered in the electronic filters market report are ABB, AVX Corporation, BLOCK Transformatoren-Elektronik GmbH, Captor Corporation, CD Automation UK Ltd, Circutor, Cosel Europe GmbH, Mini-Circuits, Schneider Electric, Iridian Spectral Technologies Ltd, Murata Manufacturing Co., Ltd, Microwave Filter Company Inc., Pole/Zero Corporation, Altecnic Ltd, Midwest Optical Systems, Inc., Nanjing XingHuo Technology Co. Ltd, EMI Solutions, Anatech Electronics Inc., Beltran Technologies Inc., Marian, Inc., among other domestic and global players.
Short Description About Electronic Filters Market:
The Global Electronic Filters market is anticipated to rise at a considerable rate during the forecast period, between 2024 and 2031. In 2023, the market is growing at a steady rate and with the rising adoption of strategies by key players, the market is expected to rise over the projected horizon.
North America, especially The United States, will still play an important role which can not be ignored. Any changes from United States might affect the development trend of Electronic Filters. The market in North America is expected to grow considerably during the forecast period. The high adoption of advanced technology and the presence of large players in this region are likely to create ample growth opportunities for the market.
Europe also play important roles in global market, with a magnificent growth in CAGR During the Forecast period 2024-2031.
Electronic Filters Market size is projected to reach Multimillion USD by 2031, In comparison to 2024, at unexpected CAGR during 2024-2031.
Despite the presence of intense competition, due to the global recovery trend is clear, investors are still optimistic about this area, and it will still be more new investments entering the field in the future.
This report focuses on the Electronic Filters in global market, especially in North America, Europe and Asia-Pacific, South America, Middle East and Africa. This report categorizes the market based on manufacturers, regions, type and application.
Get a Sample Copy of the Electronic Filters Report 2024
What are your main data sources?
Both Primary and Secondary data sources are being used while compiling the report. Primary sources include extensive interviews of key opinion leaders and industry experts (such as experienced front-line staff, directors, CEOs, and marketing executives), downstream distributors, as well as end-users. Secondary sources include the research of the annual and financial reports of the top companies, public files, new journals, etc. We also cooperate with some third-party databases.
Geographically, the detailed analysis of consumption, revenue, market share and growth rate, historical data and forecast (2024-2031) of the following regions are covered in Chapters
What are the key regions in the global Electronic Filters market?
North America (United States, Canada and Mexico)
Europe (Germany, UK, France, Italy, Russia and Turkey etc.)
Asia-Pacific (China, Japan, Korea, India, Australia, Indonesia, Thailand, Philippines, Malaysia and Vietnam)
South America (Brazil, Argentina, Columbia etc.)
Middle East and Africa (Saudi Arabia, UAE, Egypt, Nigeria and South Africa)
This Electronic Filters Market Research/Analysis Report Contains Answers to your following Questions
What are the global trends in the Electronic Filters market?
Would the market witness an increase or decline in the demand in the coming years?
What is the estimated demand for different types of products in Electronic Filters?
What are the upcoming industry applications and trends for Electronic Filters market?
What Are Projections of Global Electronic Filters Industry Considering Capacity, Production and Production Value? What Will Be the Estimation of Cost and Profit? What Will Be Market Share, Supply and Consumption? What about Import and Export?
Where will the strategic developments take the industry in the mid to long-term?
What are the factors contributing to the final price of Electronic Filters?
What are the raw materials used for Electronic Filters manufacturing?
How big is the opportunity for the Electronic Filters market?
How will the increasing adoption of Electronic Filters for mining impact the growth rate of the overall market?
How much is the global Electronic Filters market worth? What was the value of the market In 2020?
Who are the major players operating in the Electronic Filters market? Which companies are the front runners?
Which are the recent industry trends that can be implemented to generate additional revenue streams?
What Should Be Entry Strategies, Countermeasures to Economic Impact, and Marketing Channels for Electronic Filters Industry?
Customization of the Report
Can I modify the scope of the report and customize it to suit my requirements? Yes. Customized requirements of multi-dimensional, deep-level and high-quality can help our customers precisely grasp market opportunities, effortlessly confront market challenges, properly formulate market strategies and act promptly, thus to win them sufficient time and space for market competition.
Inquire more and share questions if any before the purchase on this report at - https://www.databridgemarketresearch.com/inquire-before-buying/?dbmr=global-electronic-filters-market
Detailed TOC of Global Electronic Filters Market Insights and Forecast to 2031
Introduction
Market Segmentation
Executive Summary
Premium Insights
Market Overview
Electronic Filters Market By Type
Electronic Filters Market By Function
Electronic Filters Market By Material
Electronic Filters Market By End User
Electronic Filters Market By Region
Electronic Filters Market: Company Landscape
SWOT Analysis
Company Profiles
Continued...
Purchase this report – https://www.databridgemarketresearch.com/checkout/buy/singleuser/global-electronic-filters-market
Data Bridge Market Research:
Today's trends are a great way to predict future events!
Data Bridge Market Research is a market research and consulting company that stands out for its innovative and distinctive approach, as well as its unmatched resilience and integrated methods. We are dedicated to identifying the best market opportunities, and providing insightful information that will help your business thrive in the marketplace. Data Bridge offers tailored solutions to complex business challenges. This facilitates a smooth decision-making process. Data Bridge was founded in Pune in 2015. It is the product of deep wisdom and experience.
Contact Us:
Data Bridge Market Research
US: +1 614 591 3140
UK: +44 845 154 9652
APAC: +653 1251 975
Email:- [email protected]
Browse More Reports:
Global Biofoam Packaging Market – Industry Trends and Forecast to 2029
Global Electronic Filters Market – Industry Trends and Forecast to 2028
Global Aerospace Insulation Coatings Market - Industry Trends and Forecast to 2029
Global Congestive Renal Failure (CRF) Market – Industry Trends and Forecast to 2029
Global Aircraft Seat Actuation Systems Market – Industry Trends and Forecast to 2028
#Electronic Filters Market#Electronic Filters Market Size#Electronic Filters Market Share#Electronic Filters Market Trends#Electronic Filters Market Growth#Electronic Filters Market Analysis#Electronic Filters Market Scope & Opportunity#Electronic Filters Market Challenges#Electronic Filters Market Dynamics & Opportunities
0 notes