#kua compatibility
Text
😉TALES & TRIVIA: Same Zodiac Couple ~"Match made in Heaven"?
In terms of Chinese Astrology, same Zodiac Couples are either the same age, or one Zodiac Cycle apart with a large age-gap of 12 years. It is commonly believed that people of the same Zodiac Sign are most compatible as they share the same characteristics and world view.
Indeed, people of the same Chinese Zodiac Sign are considered “Allies or Best Friends” but is this enough for a lasting, romantic relationship of the live-happily-grow-old-together kind?
To find out, here’s a quick CHECKLIST:
⚀ Are you in the same Life Star/KUA GROUP?
▪️EAST GROUP: 1, 3, 4, 9.
▪️WEST GROUP: 2, 5, 6, 7, 8.
⚁ Do your Life Stars/Kua No. form a “HO TU” combination?
▪️1/6, 2/7, 3/8, 4/9.
⚂ Do your Life Stars/Kua No. add up to 10?
▪️1+9 / 2+8 / 3+7/ 4+6/ 5+5.
[Life Star/KUA No. Formula:-
If born before February 4th, subtract 1 year from date of birth.
FOR MEN: Add last 2 digits of Year of Birth and reduce to single no. Deduct this no. from 10. If answer is 5, then take 2 as the Kua No.
(NOTE: For Boys born in year 2000 and after, deduct from 9 instead of 10).
FOR WOMEN: Add last 2 digits of Birth Year and reduce to single no. Add 5 to this no. If answer is 5, take 8 as Kua No.
(NOTE: For Girls born in year 2000 and after, add 6 instead of 5)].
SUMMARY
🔸Same Age Couples.
‘83🐷Boar/ ‘84🐀Rat: ❤️❤️
‘85🐂Ox/‘86🐯Tiger/‘87🐰Rabbit: ❤️
‘88🐉Dragon / ‘79🐑SHEEP: ❤️❤️
‘80🐒Monkey/‘89🐍Snake/‘90🐴Horse❤️
‘81🐓Rooster/ ‘82🐶Dog: ❤️
🔸Older Male with Younger Female.
Rat:▫️'72🐀 +‘84🐀 = ❤️❤️❤️
Ox: ▫️'73🐂 +‘85🐂 = ❤️❤️❤️
Tiger: ‘74🐯 +‘86🐯 = ❤️
Rabbit: ‘75🐰+‘87🐰= ❤️❤️❤️
Dragon: ‘76🐉+‘88🐉= ❤️
Snake: ‘77🐍+‘89🐍 = ❤️
Horse: ‘78🐴+‘90🐴 = ❤️
SHEEP: ‘79🐏+‘91🐑 = ❤️
Monkey: ‘80🐒+‘92🐒= ❤️❤️❤️
Rooster: ‘81🐓+‘93🐔= ❤️
Dog:▫️ ‘82🐶+‘94🐶 = ❤️
Boar:▫️'83🐷+‘95🐷 = ❤️
~~~~~
[Rating System:
▪️Same Zodiac only: ❤️
▪️Same Zodiac + Same Group: ❤️❤️
▪️Same Zodiac+Same Group+Ho-Tu or Sum-of-Ten: ❤️❤️❤️]
How to add more “Hearts” :
🔸WESTERN ZODIAC:
An additional ❤️ if you and your partner are highly compatible.
🔸 BAZI or Four PILLARS BIRTHCHART:
More hearts ❤️ if you both “appear” in the “Spouse Palace” of the other’s Chart, and if your respective Self-Elements/Daymasters are in positive relationship to each other with the Timing just right. (NOTE: This would require some skills to interpret).
LAST WORDS
In the final analysis, Same Zodiac Couples understand each other intimately because both share common character traits and temperament. In fact, they are so alike there is a tendency to shut out alternative interests and viewpoints, and it is this lack of diversity and challenge that could stiffle and stagnate a long-term relationship. Falling under the influence of the same set of Stars every year also means both would go through bad patches the same time together, with neither having the mental energy and strength to help the other person pull through. Nonetheless, who am I to say what’s right or wrong in matters of the heart. Like they say, LOVE can conquer all, so for Same Zodiac Couples, if he/she is truly THE ONE & ONLY, then so be it and f*** off to everyone!!
#chinese astrology#chinese zodiac#love compatibility#kua compatibility#kua numbers#lucky in love#bazi destiny analysis#match made in heaven#same zodiac couples#tales & trivia
5 notes
·
View notes
Text
Amharic Keyboard

Amharic Keyboard Download
Click or type it.. Copy it.. And paste it.. Done!
Free online Ethiopian Amharic keyboard compatible with all Mobile and Desktop devices. Write in Geez letters online without installing any apps. This online keyboard comes with word suggestion feature, this feature makes your Amharic typing experience much easier. Virtual Amharic keyboard to type Amharic, Easily type all Amharic characters, Amharic letters online. Use anywhere, on any device, without any software.
Typing with this Amharic keyboard is the fastest way to type - you don't need any other Amharic input tools.
Amharic language keyboard is designed in a new way of simple English and Amharic typing. Are you bothered from mobile keyboard typing and want to a new and fast Amharic keyboard?
This Amharic Keyboard enables you to easily type Amharic online without installing Amharic keyboard. You can use your computer keyboard or mouse to type Amharic letters with this online keyboard.
Pressing on the Amharic keyboard layout will toggle the mouse input between virtual QWERTY keyboard and virtual Amharic keyboard. The key will also turn on/off your keyboard input conversion. Minecraft football stadium. Pressing on your keyboard has the same function.
Instructions for using the HBN Keyboard
When you click one of the root characters, all the variations will show up on the keyboard. You can then type the variation you want. Press or either + or for additional Amharic letters that are not visible on the keyboard.
Instructions for using the Phonetic Keyboard
To enter አማርኛ type amarNa a(አ) ma(ማ) r(ር) Na(ኛ). To enter አዲስ አበባ type adis abeba a(አ) di(ዲ) s(ስ) a(አ) be(በ) ba(ባ). To enter ገብርኤል type gebr'El ge(ገ) b(ብ) r(ር) 'E(ኤ) l(ል). Note that rE yields ሬ while r'E yields ርኤ.
euiaEoWልለሉሊላሌሎሏቍቈቊቋቌ
Instructions for using Transliteration
Transliteration works more or less the same way as the phonetic input with minor differences. Examples are a(አ), u(ኡ), i(ኢ), aa(ኣ), ee(ኤ), e(እ), o(ኦ), ua(ኧ), he(ሀ), hu(ሁ), hi(ሂ), ha(ሃ), hee(ሄ), h(ህ), ho(ሆ), hh(ሕ), sz(ሥ), sh(ሽ), qw(ቍ), qh(ቕ) , qhw(ቝ), eh(ዕ), ch(ች), x(ኅ), xw(ኍ), ny/gn(ኝ), kh(ኽ), khw(ዅ), zh(ዥ), dh(ዽ), gw(ጕ), gh(ጝ), th(ጥ), c(ጭ), ts(ጽ), tz(ፅ), ph(ጵ), bua(ቧ), kua(ኳ), hoa(ሇ), koa(ኯ), .(።), '.(.), ,(፣), ',(,), :(፤), ;(፥), :-(፦), <(«), >(»), ::(፡), +x(፠), |x(፨), `1(፩), ~1(፲).
Single quote(') can be used as a partition so that what is one the left and what is on the right are transliterated separately. For example s'ehl will produce ስዕል instead of ሰህል.
Font download for iPhone and iPad users
To download Amharic font for iPhone and iPad click signed.mobileconfig.
Font download for Mac users
To download Amharic font for Mac click AbyssinicaSIL1.200.zip and copy the font file, AbyssinicaSIL-R.ttf, to the Fonts folder in the Library folder on your hard drive.
Downloading and Installing for Windows
To download the HBN keyboard software to your computer click ethiopic.zip and view this YouTube video. The video shows how to download and install the keyboard on Windows Vista.
On some versions of Vista an error may occur during installation. In that case, right-click on setup.exe and run as administrator.
Marvel vs capcom 2. People also search for.
After downloading and installing your keyboard, view one of the video instructions here.
Amharic Keyboard Download
For mobile phones and tablets, touch and hold inside the text area to copy the text. You can then paste the text in any app such as Facebook, Twitter, email, or search app.

0 notes
Text
"Best HSM for Aadhaar card Authentication - Aadhar API Supported"
Unique Identity Authority of India (UIDAI) is created to provide unique identity to all residents of India. UIDA has enrolled the citizens to provide online authentication using demographic and biometric data. The UID (also known as Aadhar) number that uniquely identifies a resident, allows them to establish their identity to various agencies in India. Aadhar is a permanent non-revocable identity. Citizens can prove their identity using their Aadhar credentials. In order to bring transparency in the whole Aadhar Authentication system, an Hardware Security Module (HSM) plays a vital role.
What Is Adhar Authentication?
Aadhar authentication is a process of submitting the personal identity data to Central Identities Data Repository (CIDR) maintained by UIDAI. UIDAI confirms the proof of identity after matching the submitted identity data with the data at CIDR. UIDAI defined a framework called Aadhar Authentication Framework to provide the details of the authentication types offered. Currently, Aadhar Authentication supports Demographic Matching, Biometric Matching, and additional features such as One-Time-Password (OTP). In India, various institutions use Aadhar authentication to establish their customers’ identity, confirming beneficiary, even attendance tracking in offices. It can be used for demographic data verification too.
For providing efficient authentication mechanism, UIDAI defined a structure with the service providers viz., Authentication User Agency (AUA), e-KYC agency (KUA) Sub-AUA (SA), Authentication Service Agency (ASA). AUA/SA/ AUA, KUA & SA are known as authentication user agencies
AUA – It is an entity using Aadhar authentication to provide services to their customers.
SA – It is an entity having business relationship with AUA offering specific services in a domain.
ASA – It is an entity that directly connects UIDAI through private secure connection for transmitting authentication requests from various AUAs.
Terminal Devices – Biometric capture devices, attached with terminals are used by SAs/AUAs in the Aadhar authentication process. These authentication devices must comply with specifications provided by UIDAI to protect all the biometric and demographic information. Moreover, authentication devices initiate the authentication request, create PID block, and forward to user authentication agency server for creating auth XML. To ensure integrity and non-repudiation, the XML must be digitally signed by the AUA/KUA and/or ASA. In e-KYC service e-KYC response data is encrypted. UIDAI mandates the use of FIPS 140-2 Level 3 certified Hardware Security Module (HSM) for digital signing auth XML and decryption of e-KYC data.
Kryptoagile provides FIPS 140-2 Level 3 compliant Hardware Security Modules to fully comply UIDAI directives.
Here are some of the advantages of hardware security modules offered by Kryptoagile:
Best suited for general purpose data processing
Digital document signing
PDF signing
GST signing
E-invoice signing
Extremely popular in financial data processing
Payment processing,
NEFT transactions,
RTGS transactions
Electronic fund transfer management
Powered with world's most advanced data encryption mechanism
Compatible with cross industry applications
#aadharauthentication#Aadhaar card authentication#aadhaar authentication solutions#Itsecurity#it security services
0 notes
Text
Final Project
View live link here
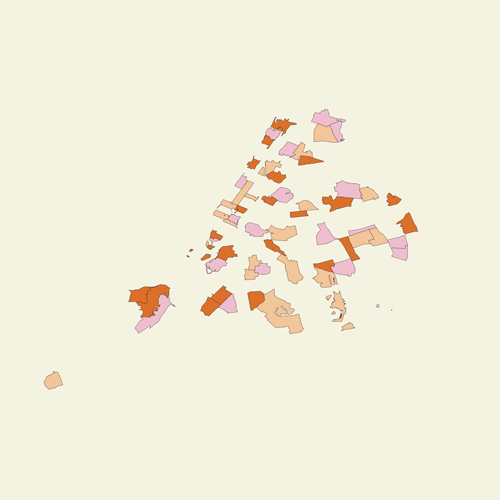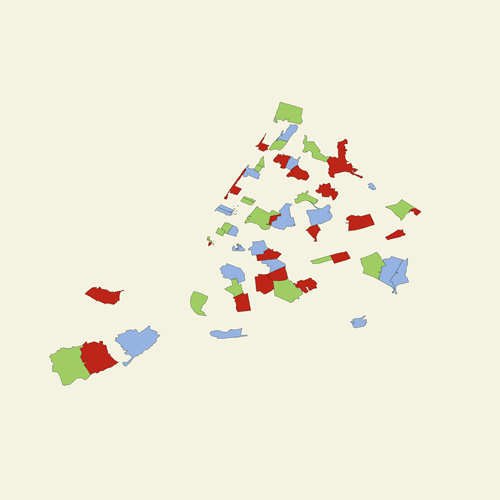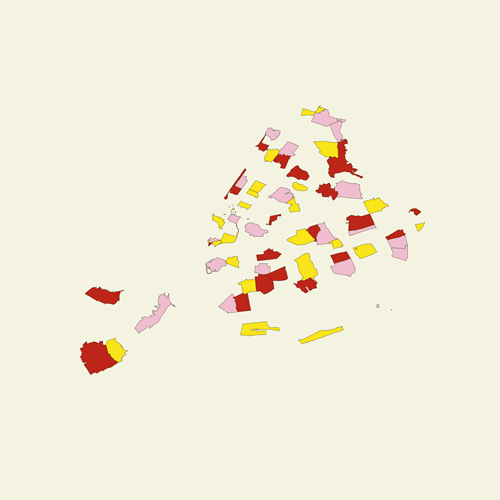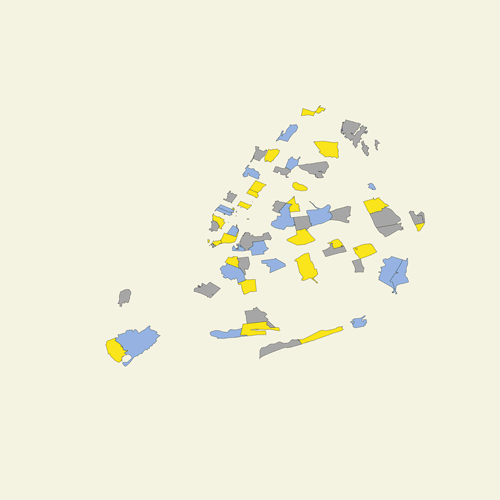
Project Statement
Pungsujiri Map of New York is designed to guide you to your luck zones. It will activate specific luck areas in your life, bringing you peace and prosperity.
Process
Developing (speculative) data set
Traditional Pungsujiri evaluation factors include various geographical factors, direction, seasons etc. Obviously, New York’s topographic traits are vastly different from Asia’s mountainous regions and do not fit into traditional pungsu jiri readings. So, to develop pungsujiri data set, Im using one of widely used theory, the Eight Trigrams. It claims to use energy forces to harmonize individuals with their surrounding environment. Geomancy involves interpreting a series of 16 figures formed by a randomized process that involves recursion, followed by analyzing them, often augmented with astrological interpretations.

[Image Description: Image of multiple numbers surrounding a house. Abstract image for describing house numerology idea.]
Similar to House numerology methodology, I used eight trigram math recursion to label each zip code area with specific eight trigram zone and energy.
To better pair with each individual users, I ask each user upon entering the site to provide their name + birth year to provide a personalized map. This was an attempt to take a similar approach of hyper-personalized services that make you feel like the whole experience is centered around ‘me’. I took a lot of inspiration from the Co-star app and other astrology services for this idea.

[Image Description: Image of NYC zipcode geojson data]
Generated simple json data to store zipcode information + pungsujiri readings. Which is used to visualize and provide personal readings accordingly.

[Image Description: Screenshot of json data]
Developing Map
I initially planned on using leaflet.js + mapbox.gl but as I was developing this project, I felt like the scope of visualization Im trying to achieve in my project is really simple and those tools are unnecessary for now. Im using svg shapes from NYC zip code boundaries to draw out the map.
Documentation images
View live link here

[Image Description: Image of website with text input asking users for Name and birth year]

[Image Description: Image of website loading with a text “Reading your Pungsujiri zone”]
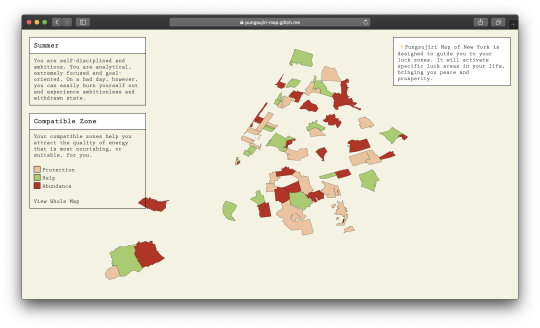
[Image Description: Image of website showing personalized NYC energy map in the center. On the left side of the page shows user’s name with personalized reading and explanation of compatible NYC zone. Right side of the page shows short description of the project ]

[Image Description: Image of website showing personalized NYC energy map in the center. On the left side of the page shows user’s name with personalized reading and explanation of compatible NYC zone. Right side of the page shows short description of the project. ]
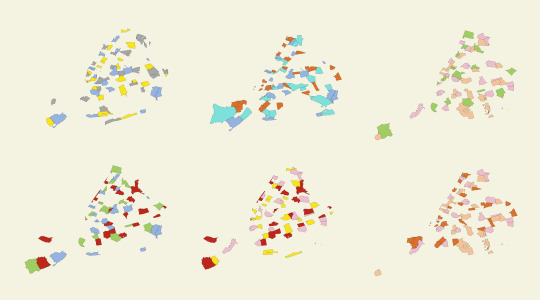
[Image Description: Image of NYC map in different colors]
Sources
https://jk-lee.com/geography-of-hidden-faces
The Ryukyu Islands Feng Shui Village Landscape, 2008
Diagrams of Power: Visualizing, Mapping, and Performing Resistance, Make Money, Not Art
Woman and NatureBook, Susan Griffin
We are the Land: Native American Views of Nature
https://www.nytimes.com/2005/04/25/business/worldbusiness/disney-bows-to-feng-shui.html
https://yalantis.com/blog/predictive-algorithm-for-house-price/
https://www.investopedia.com/articles/realestate/12/real-estate-valuation.asp
https://www1.nyc.gov/assets/em/html/know-your-zone/knowyourzone.html
All my mood board resources are here: Are.na
https://www.thespruce.com/your-feng-shui-kua-number-calculator-1274670
https://pages.ucsd.edu/~dkjordan/chin/Baguah.html
https://medium.com/@michaelyardney/what-your-house-number-means-property-numerology-ea182f79c8d4
0 notes
Text
DOWNLOAD AOPEN AX4PER-GN SES DRIVER
File Version: 415111878
Operating Systems: Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X
Uploader: Teddy
Download Type: http
File Size: 23 Mb
Date Added: 05 December, 2019
Downloads: 3217
Price: Free
File Format: exe
File Name: aopen ax4per-gn ses driver

Change log:
- Bug - [System Log] Fixed a bug where backup logs were not displayed on Settings.
- Fixed Help page don't need "BigPond(aopen ax4per-gn ses driver "BigPond) Connection" description.
- Fixed turn on virtual server with schedule will cause internet access failure.
- Fixed a bug where some settings were not copied during(aopen ax4per-gn ses driver during) failover.
- Fixed the issue that always showed motion alert on mydlink live view page when enable motion detection.
- Fixed(aopen ax4per-gn ses driver Fixed) failure of resuming from S4 under Win 98SE.# Fixed incompatibility with ATI MAXX VGA card.
- Fixed the issue where HD-WLU3/R1 or HD-WHU3/R1 was not recognized after rebooting the Mac device the drive was connected to.
- Fixed the error that(aopen ax4per-gn ses driver that) bookmark and favorite lists were disappeared occasionally when MicroSD card was inserted in the device.
- Network]: Fixed a bug where some IP addresses and subnet masks could not be configured.
- Issues Fixed- Fixed(aopen ax4per-gn ses driver Fixed) an issue where the camera would go out of focus after reboot.
Users content:
Corrected the unattended install command option from "-SILENT" to "/s". Due to OS limitation, when installing total memory of 4GB capacity or more, Windows 32-bit operation system may only recognize less than 3GB. - Updated the description in WPS page. Kindle Unlimited Recommendations: Try Kindle Unlimited for free and see recommended Kindle Unlimited titles after choosing your favorite genres. Music player- Improved process information of resume. Add United Kingdom ISP, Plusnet - Fibre broadband. Updated CPU Code. The Division may hang when using Quad AMD Crossfire technology. The Install dialog will appear. Gaming durability: ASUS SafeSlot and premium components for maximum endurance. DOWNLOAD SONY VGN-SR26GN DRIVER
Supported OS:
Microsoft Windows 8 Enterprise (64-bit)
Microsoft Windows 8.1 (32-bit)
Microsoft Windows 8.1 Pro (64-bit)
Windows XP 32-bit
Microsoft Windows 8.1 Enterprise (64-bit)
Windows 2000
Windows Server 2003 64-bit
Microsoft Windows 10 (32-bit)
Windows Server 2016
Windows Vista 32-bit
Windows 10
Microsoft Windows 8 Enterprise (32-bit)
Windows 8
Microsoft Windows 8.1 (64-bit)
Notebook 8.1/8/7 64-bit
Windows Server 2012
Microsoft Windows 8 (64-bit)
Windows Server 2003 32-bit
Windows 7 32-bit
Windows Server 2008 R2
Microsoft Windows 8.1 Pro (32-bit)
Microsoft Windows 8 Pro (64-bit)
Windows XP 64-bit
Windows Vista 64-bit
Microsoft Windows 10 (64-bit)
Windows Server 2008
Microsoft Windows 8 Pro (32-bit)
Microsoft Windows 8 (32-bit)
Windows 8.1/8/7/Vista 64-bit
Notebook 8.1/8/7 32-bit
Microsoft Windows 8.1 Enterprise (32-bit)
Windows Server 2012 R2
Windows 8.1
Windows 7
Windows 7 64-bit
Windows 8.1/8/7/Vista 32-bit
Searches:
aopen ax4per-gn ses Yku863-kua; aopen ax4per-gn ses YWIDR8639; aopen ax4per-gn ses driver for Microsoft Windows 8 Pro (64-bit); aopen ax4per-gn ses YW8639; aopen ax4per-gn ses driver for Windows Server 2016; aopen ses ax4per-gn driver; aopen ax4per-gn ses driver for Windows XP 32-bit; aopen ax4per-gn ses Y YW863-8; aopen ax4per-gn ses driver for Microsoft Windows 8.1 (32-bit); aopen ax4per-gn ses Y86k; aopen ax4per-gn ses driver for Microsoft Windows 8 Pro (32-bit)
Compatible Devices:
USB Hubs; Wifi adapter; Gadget; Usb Cables; Ipad; Iphone
To ensure the integrity of your download, please verify the checksum value.
MD5: b7f53aa5cedb18dd2246bedc9be506d6
SHA1: 6898518bff48439a4ea935ebaae7972f7b18e171
SHA-256: 357ac7454ec5adf5a430f47fda737aec96f3881947deee866fcacf0e30103fd6
0 notes
Link
*Amazon Brand - Solimo Non Stick Tawa (26cm, Induction and Gas Stove Compatible)*
~mrp - 800~
price - 375
link - https://amzn.clnk.in/kUA
more - https://amzn.clnk.in/kUB
0 notes
Text
Kua Number Calculator Pro
Kua Number Calculator Pro
By: Ramesh Batra
[sc name=”ads1″]
Category: Utilities
Release Date: 2019-04-23
Current Version: 1.0
Adult Rating: 4+
File Size: 527.00 kB
Compatibility: Requires iOS 12.2 or later.
Copyright: Ramesh Batra
Price: $0.99
Description:
According to Feng Sui every Individual have a different energy level. On which the Feng Sui an Ancient Art has paid a lot of attention for harnessing that energy…
View On WordPress
0 notes
Photo

Second attempt join @latihanpegangkuas challenge #lpk_fashion, and this another my #hootd with @koolastuffa outfit, Kertas; HVS 70gsm (ga compatible buat water colour tp sering pake (´ー`)) Kuas : lyra Watercolour : mix titi dan merk satunya lupa + marries gouache, .cat poster merk sakura untuk warna silver, Sketch pake lineart warna no 008 #latihanpegangkuas
0 notes
Text
How I Spent the Remainder of My Education Budget This Year.
I had an education budget that needed burning.
I'm a huge believer in conferences for networking, not at all for learning. People with something truly meaningful to say write it down. If it's something that's cutting edge they publish it in a journal. If it's something that's a little more ossified or lengthy, they write a book. If I want to learn something I read about it.
So what did I want to invest in? Well, there's a couple of areas that I've been eyeing for quite awhile and, as it turns out, these kinds of books are expensive, so I had no trouble whatsoever using the remainder of the extremely generous education budget my company provides (which just invites me to say, you should come work with me!).
Programming Languages
I've long bemoaned how little I understand programming languages at the meta level. I chalk this up to the fact that I've only professionally used 3 of note (Java, Python, and Clojure if you're interested) and I really wouldn't say I've given Python a fair shake.
Clojure and Java are pretty diametrically opposed languages but they also have a weird relationship because Clojure is hosted by Java and so Java things are easily within reach. I enjoyed Java while I was writing it but when Moore's law failed and I read JCIP I needed to head for hills.
Python's strange because lots of people I respect like it quite a bit but when I write it I feel like I'm doing everything wrong. I don't yet know if that's because of me or because of it. I suspect the former.
That said, I believe that studying programming languages, especially languages with vastly different takes on what Turing Completeness means, makes you a fundamentally better programmer in whatever language you happen to be using at your day job. I also believe that the days of of the monoglot programmer are thoroughly at an end. Even if you do managed to land a stable gig somewhere you're still most likely going to be writing software in several different languages. At my current employer we have a healthy mix of Clojure, Python, SQL, Chef (if you'll allow it), Terraform (again), Elisp (my baby), and Bash. Not to mention the various services we install and maintain. I simply can't afford to specialize in any of those if I want to stay productive.
So that's what I chose to really dig deep on with the remainder of this years education budget.
Essentials of Programming Languages by Friedman and Wand
What I'm most excited for in this book is a truly thorough examination of programming languages as languages. I'm hoping that this gives me a bunch of vocabulary and terms with which to explore languages as I learn them.
Seven Languages in Seven Weeks: A Pragmatic Guide to Learning Programming Languages by Tate
I chose this book because it's literally a guide to doing what I'm hoping to be doing for 7 languages. It's possible to teach yourself anything but it's often easier with a teacher.
The 7 languages covered are Clojure, Haskell, Io, Prolog, Scala, Erlang, and Ruby.
I'm covering some of the same ground here as I will in future books but, like I said, the main point of this book is learning how to quickly grok a language, not what any of the specific languages have to offer.
The Go Programming Language by Donovan and Kernighan
I'm primarily interested in Go because Rob Pike has been trying to get the world to accept CSP as the way to organize systems for 30 years and he seems finally to have done it here.
Learn You a Haskell for Great Good!: A Beginner's Guide by Miran
I want to learn Haskell because I want to truly grok laziness. No other language of any degree of use is fully lazy. I want to know what falls out of that.
Learn You Some Erlang for Great Good!: A Beginner's Guide by Hébert
I want to learn Erlang because people tell me that nothing teaches you about parallelism better than Erlang. I'm also interested in it's QuickCheck implementation although that may be proprietary.
The Little Schemer by Friedman and Felleisen
I'm mostly interested in Scheme because it was the language used by SICP, a book of nearly mythical importance, and because of Continuations. Ever since Kyle Burton tried to explain them to me I've been interested in them.
The Reasoned Schemer by Friedman, Byrd, and Kiselyov
I hope to pick up logic programming from this book.
Real World OCaml by Minsky, Madhavapeddy, and Hickey
Technomancy recommends OCaml. So does Yegge. Lisp with a strong typing system? I guess that sounds pretty cool. Maybe I'll learn to love type systems from this. :)
Let Over Lambda by Hoyte
This cringe-inducingly introduced book claims to be about macros. Clojure's never taught me much about those. I'd love to learn more.
Elements of Clojure by Tellman
Everything I've ever seen or heard from Zach Tellman is worth listening to. If he wrote a guiding philosophy book about how to use Clojure I want in.
Applications/Services
I think you need to learn about what you have in production. It's OK to be quick and dirty when you're rushing to ship but eventually you've gotta hunker down and actually understand what's going on. At least someone does. And I'm willing to be that someone.
Effective Python: 59 Specific Ways to Write Better Python by Slatkin
As I mentioned, even though I did Python professionally for almost 18 months I never felt like I gave it a fair shot. And I still feel like I'm fighting it all the time. It feels like a toy. I'd like a no-nonsense guide on how to do it right. You could argue that this book belongs in the languages section but, and I'm sorry if this sounds snobbish, I don't think Python's going to teach me anything interesting about languages or programming. Some of the most critical components of my employer's systems are written in Python. I want to know how to make them sing.
Kafka: The Definitive Guide: Real-Time Data and Stream Processing at Scale by Narkhede
Kafka is an important component of our data ingestion architecture which is basically one half of what my company does. We don't push it that hard though, and we still see some consistent, shady behavior from it. I want to stop that.
Kubernetes: Up and Running: Dive into the Future of Infrastructure by Hightower and Docker in Action by Nickoloff
My company recently took the dive into the containerization buzzcraze. I do not think very highly of that. I believe there's a ton of complexity introduced by it that people ignore because it sounds cool.
That said, it's the world I live in and I want to know how to be good at it. K8s: Up and Running is the book recommended to me.
Java Concurrency in Practice by Goetz
It used to be said that there were basically two vectors into the Clojure ecosystem: Ruby developers sick of performance woes and piss-poor compatibility stories and Java developers who had finally gotten around to reading JCIP, were scared out of their mind (👋), and had bad memories of C++ (I'm looking at you, Scala).
These days, though, I actually know a lot more Clojure developers (at least at my company) with little to no prior Java experience. This is a shame because Effective Java is very nearly required reading for writing truly Effective (or at least, Performant) Clojure. In fact, there's been a bunch of discussion lately among the engineers at my company about wrapper libraries like clj-time that are misused because the wrapped library was misunderstood.
Clojure's concurrency primitives are really interesting but they're hosted on the JVM and so thoroughly understanding Java Concurrency actually is important if you want to actually grok them.
I've read JCIP before but had to leave it behind at a former employer. I wanted this one for my shelf.
Building Evolutionary Architectures: Support Constant Change by Ford, Parsons, and Kua
I heard about this book from Fowler. I generally think Fowler is always worth listening to. I'm hoping to continue to learn about architecture from this book.
The Terraform Book by Turnbull
We use Terraform to manage the vast majority of our infrastructure. It's always been something I've poked at until it works and then moved on from. That needs to stop.
Problem Solving
I have always felt like a very weak problem solver. I feel trapped by Cognitive Biases and don't really understand how to overcome them. I fear failure and it shuts my thinking down. I latch on to solutions that I see rather than thinking broadly. I want to be better here.
Thinking, Fast and Slow by Kahneman
I'm interested in this because of the recent national conversations around Cognitive Biases. I distrust myself deeply, but I want to be smart about it. I'm hoping to learn more about my cognition here and to learn strategies for overcoming my biases.
Thinking Forth by Brodie
This could go in the languages section. The reason I put it here is because, on the tin, it reports to be about how to think about applying programming languages to the problems you face.
The Little Prover by Friedman and Eastlund
I believe that my revulsion to proofs in Math has made me a weaker software developer. Ever since watching through the SICP course I was blown away by the power of wishful thinking and it only occurred to me much later that the thing that annoyed me most about proofs was essentially an educated wishful though, just like I apply every day at my job. I want to be better at proofs.
How to Solve It: A New Aspect of Mathematical Method by Polya
I heard about this book from Rich Hickey. Rich Hickey's another person that you should just always listen to. Hammock Driven Development is a talk every single developer in the world should listen to.
One key assertion in that talk is the problem solving is not about innate intelligence or something that some people are good at and everyone else is bad at. Instead, it's a skill that we can practice. This is the book he recommended to practice it.
Leadership
The Manager's Path: A Guide for Tech Leaders Navigating Growth and Change by Fournier
I've heard nothing but good things about this book. At my stage of life I need to manage better or I'm going to sink. I don't have enough personal time to leverage to accomplish all the things I want or need to accomplish. I've been on a long-ish course of study on this topic and I want to continue.
DevOps
So why aren't there any books here? Primarily because I already used some of my education budget to get books in this vein and I haven't gotten to consume them yet. I'm especially excited to dig into The DevOps Handbook after having read through The Phoenix Project, a book I can't recommend more that was given to me by Connor McArthur. It's also arguable that some of the other books I've picked up like the Kafka and k8s resources would fit in this category. But, I ran out of money and felt that the rest of the books on this list were more important.
One technology I really should be better at than I am is Chef. A big reason that I didn't buy a Chef book though is that there apparently aren't really any good ones. Oh well, I'll stick with the docs.
If I haven't said so publicly before: The Interlibrary Loan system is a National Treasure. So why didn't I get all these books from there? Well, for some of them, I did. I'm currently reading a copy of ZooKeeper by Reed and Junqueira and Building Evolutionary Architectures and I have several more on order. Sadly, these sorts of technical books can sometimes take a while to find. I had the budget, I figured it was worth spending. If any of the books don't prove to be worth it, I'm planning on donating them to the library.
Finally, what didn't make the cut just yet? In the interest of time I'm not going to be explicit about what interests me about every one of these.
Making Work Visible by Degrandis
Effective DevOps by Davis
Release It! by Nygard
Effective Java (3rd Edition) by Bloch
SICP by Abelson and Sussman
How to Design Computer Programs by Felleisen
Bootstrapping by Bardini
The Creative Computer by Michie
The Linux Programming Interface by Kerrisk
The Rust Programming Language by Klabnik
Compilers by Lam and Aho
Enterprise Integration Patterns by Hohpe
Infrastructure as Code by Morris
Paradigms of Artificial Intelligence Programming by Norvig
ANSI Common Lisp by Graham
Practical Common Lisp by Siebel
The Art of the Metaobject Protocol by Kiczales
The Scheme Programming Language by Dybvig
The Practice of Programming by Kernighan
Lisp in Small Pieces by Queinnecc
Clean Code by Martin
The Seasoned Schemer by Friedman
Purely Functional Data Structures by Okasaki
The Little MLer by Felleisen
The Clean Coder by Martin
The Unix Programming Interface by Kernighan
Thanks to everyone who recommend books to me and chatted with me on Twitter. I got help from #erlang, #haskell, and #go-nuts on freenode. Special thanks to fogus for putting together a really interesting list of books that I can't wait to dig through.
#clojure#reading#languages#haskell#erlang#forth#python#java#kubernetes#DevOps#zookeeper#ocaml#docker#cognitive biases#golang#kafka#scheme#continuations#csp
0 notes
Text
"Best HSM for Aadhaar card Authentication - Aadhar API Supported "
Unique Identity Authority of India (UIDAI) is created to provide unique identity to all residents of India. UIDA has enrolled the citizens to provide online authentication using demographic and biometric data. The UID (also known as Aadhar) number that uniquely identifies a resident, allows them to establish their identity to various agencies in India. Aadhar is a permanent non-revocable identity. Citizens can prove their identity using their Aadhar credentials. In order to bring transparency in the whole Aadhar Authentication system, an Hardware Security Module (HSM) plays a vital role.
What Is Adhar Authentication?
Aadhar authentication is a process of submitting the personal identity data to Central Identities Data Repository (CIDR) maintained by UIDAI. UIDAI confirms the proof of identity after matching the submitted identity data with the data at CIDR. UIDAI defined a framework called Aadhar Authentication Framework to provide the details of the authentication types offered. Currently, Aadhar Authentication supports Demographic Matching, Biometric Matching, and additional features such as One-Time-Password (OTP). In India, various institutions use Aadhar authentication to establish their customers’ identity, confirming beneficiary, even attendance tracking in offices. It can be used for demographic data verification too.
For providing efficient authentication mechanism, UIDAI defined a structure with the service providers viz., Authentication User Agency (AUA), e-KYC agency (KUA) Sub-AUA (SA), Authentication Service Agency (ASA). AUA/SA/ AUA, KUA & SA are known as authentication user agencies
AUA – It is an entity using Aadhar authentication to provide services to their customers.
SA – It is an entity having business relationship with AUA offering specific services in a domain.
ASA – It is an entity that directly connects UIDAI through private secure connection for transmitting authentication requests from various AUAs.
Terminal Devices – Biometric capture devices, attached with terminals are used by SAs/AUAs in the Aadhar authentication process. These authentication devices must comply with specifications provided by UIDAI to protect all the biometric and demographic information. Moreover, authentication devices initiate the authentication request, create PID block, and forward to user authentication agency server for creating auth XML. To ensure integrity and non-repudiation, the XML must be digitally signed by the AUA/KUA and/or ASA. In e-KYC service e-KYC response data is encrypted. UIDAI mandates the use of FIPS 140-2 Level 3 certified Hardware Security Module (HSM) for digital signing auth XML and decryption of e-KYC data.
Kryptoagile provides FIPS 140-2 Level 3 compliant Hardware Security Modules to fully comply UIDAI directives.
Here are some of the advantages of hardware security modules offered by Kryptoagile:
Best suited for general purpose data processing
Digital document signing
PDF signing
GST signing
E-invoice signing
Extremely popular in financial data processing
Payment processing,
NEFT transactions,
RTGS transactions
Electronic fund transfer management
Powered with world's most advanced data encryption mechanism
Compatible with cross industry applications
0 notes
Text
AADHAR AUTHENTICATION VIA HARDWARE SECURITY MODULE
Unique Identity Authority of India (UIDAI) is created to provide unique identity to all residents of India. UIDA has enrolled the citizens to provide online authentication using demographic and biometric data. The UID (also known as Aadhar) number that uniquely identifies a resident, allows them to establish their identity to various agencies in India. Aadhar is a permanent non-revocable identity. Citizens can prove their identity using their Aadhar credentials. In order to bring transparency in the whole Aadhar Authentication system, an Hardware Security Module (HSM) plays a vital role.
What Is Adhar Authentication?
Aadhar authentication is a process of submitting the personal identity data to Central Identities Data Repository (CIDR) maintained by UIDAI. UIDAI confirms the proof of identity after matching the submitted identity data with the data at CIDR. UIDAI defined a framework called Aadhar Authentication Framework to provide the details of the authentication types offered. Currently, Aadhar Authentication supports Demographic Matching, Biometric Matching, and additional features such as One-Time-Password (OTP). In India, various institutions use Aadhar authentication to establish their customers’ identity, confirming beneficiary, even attendance tracking in offices. It can be used for demographic data verification too.
For providing efficient authentication mechanism, UIDAI defined a structure with the service providers viz., Authentication User Agency (AUA), e-KYC agency (KUA) Sub-AUA (SA), Authentication Service Agency (ASA). AUA/SA/ AUA, KUA & SA are known as authentication user agencies
AUA – It is an entity using Aadhar authentication to provide services to their customers.
SA – It is an entity having business relationship with AUA offering specific services in a domain.
ASA – It is an entity that directly connects UIDAI through private secure connection for transmitting authentication requests from various AUAs.
Terminal Devices – Biometric capture devices, attached with terminals are used by SAs/AUAs in the Aadhar authentication process. These authentication devices must comply with specifications provided by UIDAI to protect all the biometric and demographic information. Moreover, authentication devices initiate the authentication request, create PID block, and forward to user authentication agency server for creating auth XML. To ensure integrity and non-repudiation, the XML must be digitally signed by the AUA/KUA and/or ASA. In e-KYC service e-KYC response data is encrypted. UIDAI mandates the use of FIPS 140-2 Level 3 certified Hardware Security Module (HSM) for digital signing auth XML and decryption of e-KYC data.
Kryptoagile provides FIPS 140-2 Level 3 compliant Hardware Security Modules to fully comply UIDAI directives.
Here are some of the advantages of hardware security modules offered by Kryptoagile:
Best suited for general purpose data processing
Digital document signing
PDF signing
GST signing
E-invoice signing
Extremely popular in financial data processing
Payment processing,
NEFT transactions,
RTGS transactions
Electronic fund transfer management
Powered with world's most advanced data encryption mechanism
Compatible with cross industry applications
#aadhaar authentication solutions#aadhaar authentication solutions in delhi#HSM provider in India#HSM in Delhi/NCR#hardware security module provider in Delhi#hardware security module provider in India#E signing solution in delhi
0 notes
Photo

What Is Adhar Authentication?
Aadhar authentication is a process of submitting the personal identity data to Central Identities Data Repository (CIDR) maintained by UIDAI. UIDAI confirms the proof of identity after matching the submitted identity data with the data at CIDR. UIDAI defined a framework called Aadhar Authentication Framework to provide the details of the authentication types offered. Currently, Aadhar Authentication supports Demographic Matching, Biometric Matching, and additional features such as One-Time-Password (OTP). In India, various institutions use Aadhar authentication to establish their customers’ identity, confirming beneficiary, even attendance tracking in offices. It can be used for demographic data verification too.
For providing efficient authentication mechanism, UIDAI defined a structure with the service providers viz., Authentication User Agency (AUA), e-KYC agency (KUA) Sub-AUA (SA), Authentication Service Agency (ASA). AUA/SA/ AUA, KUA & SA are known as authentication user agencies
AUA – It is an entity using Aadhar authentication to provide services to their customers.
SA – It is an entity having business relationship with AUA offering specific services in a domain.
ASA – It is an entity that directly connects UIDAI through private secure connection for transmitting authentication requests from various AUAs.
Terminal Devices – Biometric capture devices, attached with terminals are used by SAs/AUAs in the Aadhar authentication process. These authentication devices must comply with specifications provided by UIDAI to protect all the biometric and demographic information. Moreover, authentication devices initiate the authentication request, create PID block, and forward to user authentication agency server for creating auth XML. To ensure integrity and non-repudiation, the XML must be digitally signed by the AUA/KUA and/or ASA. In e-KYC service e-KYC response data is encrypted. UIDAI mandates the use of FIPS 140-2 Level 3 certified Hardware Security Module (HSM) for digital signing auth XML and decryption of e-KYC data.
Kryptoagile provides FIPS 140-2 Level 3 compliant Hardware Security Modules to fully comply UIDAI directives.
Here are some of the advantages of hardware security modules offered by Kryptoagile:
Best suited for general purpose data processing
Digital document signing
PDF signing
GST signing
E-invoice signing
Extremely popular in financial data processing
Payment processing,
NEFT transactions,
RTGS transactions
Electronic fund transfer management
Powered with world's most advanced data encryption mechanism
Compatible with cross industry applications
https://www.kryptoagile.com/aadhar-authentication-hsm-solutions-delhi.html
#aadhaar authentication solutions#aadhaar authentication solutions in delhi#Entrust partners in Delhi#document signing solutions in delhi#HSM provider in India#HSM in Delhi/NCR#hardware security module provider in Delhi#hardware security module provider in India#E signing solution in delhi#Digital Signing Solutions in Delhi#pki solutions in delhi#two factor authentication solutions providers in delhi
0 notes
Text
"Best HSM for Aadhaar card Authentication - Aadhar API Supported"
Aadhar authentication is a process of submitting the personal identity data to Central Identities Data Repository (CIDR) maintained by UIDAI. UIDAI confirms the proof of identity after matching the submitted identity data with the data at CIDR. UIDAI defined a framework called Aadhar Authentication Framework to provide the details of the authentication types offered. Currently, Aadhar Authentication supports Demographic Matching, Biometric Matching, and additional features such as One-Time-Password (OTP). In India, various institutions use Aadhar authentication to establish their customers’ identity, confirming beneficiary, even attendance tracking in offices. It can be used for demographic data verification too.
For providing efficient authentication mechanism, UIDAI defined a structure with the service providers viz., Authentication User Agency (AUA), e-KYC agency (KUA) Sub-AUA (SA), Authentication Service Agency (ASA). AUA/SA/ AUA, KUA & SA are known as authentication user agencies
AUA – It is an entity using Aadhar authentication to provide services to their customers.
SA – It is an entity having business relationship with AUA offering specific services in a domain.
ASA – It is an entity that directly connects UIDAI through private secure connection for transmitting authentication requests from various AUAs.
Terminal Devices – Biometric capture devices, attached with terminals are used by SAs/AUAs in the Aadhar authentication process. These authentication devices must comply with specifications provided by UIDAI to protect all the biometric and demographic information. Moreover, authentication devices initiate the authentication request, create PID block, and forward to user authentication agency server for creating auth XML. To ensure integrity and non-repudiation, the XML must be digitally signed by the AUA/KUA and/or ASA. In e-KYC service e-KYC response data is encrypted. UIDAI mandates the use of FIPS 140-2 Level 3 certified Hardware Security Module (HSM) for digital signing auth XML and decryption of e-KYC data.
Kryptoagile provides FIPS 140-2 Level 3 compliant Hardware Security Modules to fully comply UIDAI directives.
Here are some of the advantages of hardware security modules offered by Kryptoagile:
Best suited for general purpose data processing
Digital document signing
PDF signing
GST signing
E-invoice signing
Extremely popular in financial data processing
Payment processing,
NEFT transactions,
RTGS transactions
Electronic fund transfer management
Powered with world's most advanced data encryption mechanism
Compatible with cross industry applications
https://www.kryptoagile.com/contact.html
#aadhaar authentication solutions#aadhaar authentication solutions in delhi#document signing solutions in delhi#Entrust partners in Delhi#digital signature certificate online#two factor authentication#Digital Signing Solutions
0 notes
Text
AADHAR AUTHENTICATION VIA HARDWARE SECURITY MODULE
Unique Identity Authority of India (UIDAI) is created to provide unique identity to all residents of India. UIDA has enrolled the citizens to provide online authentication using demographic and biometric data. The UID (also known as Aadhar) number that uniquely identifies a resident, allows them to establish their identity to various agencies in India. Aadhar is a permanent non-revocable identity. Citizens can prove their identity using their Aadhar credentials. In order to bring transparency in the whole Aadhar Authentication system, an Hardware Security Module (HSM) plays a vital role.
What Is Adhar Authentication?
Aadhar authentication is a process of submitting the personal identity data to Central Identities Data Repository (CIDR) maintained by UIDAI. UIDAI confirms the proof of identity after matching the submitted identity data with the data at CIDR. UIDAI defined a framework called Aadhar Authentication Framework to provide the details of the authentication types offered. Currently, Aadhar Authentication supports Demographic Matching, Biometric Matching, and additional features such as One-Time-Password (OTP). In India, various institutions use Aadhar authentication to establish their customers’ identity, confirming beneficiary, even attendance tracking in offices. It can be used for demographic data verification too.
For providing efficient authentication mechanism, UIDAI defined a structure with the service providers viz., Authentication User Agency (AUA), e-KYC agency (KUA) Sub-AUA (SA), Authentication Service Agency (ASA). AUA/SA/ AUA, KUA & SA are known as authentication user agencies
AUA – It is an entity using Aadhar authentication to provide services to their customers.
SA – It is an entity having business relationship with AUA offering specific services in a domain.
ASA – It is an entity that directly connects UIDAI through private secure connection for transmitting authentication requests from various AUAs.
Terminal Devices – Biometric capture devices, attached with terminals are used by SAs/AUAs in the Aadhar authentication process. These authentication devices must comply with specifications provided by UIDAI to protect all the biometric and demographic information. Moreover, authentication devices initiate the authentication request, create PID block, and forward to user authentication agency server for creating auth XML. To ensure integrity and non-repudiation, the XML must be digitally signed by the AUA/KUA and/or ASA. In e-KYC service e-KYC response data is encrypted. UIDAI mandates the use of FIPS 140-2 Level 3 certified Hardware Security Module (HSM) for digital signing auth XML and decryption of e-KYC data.
Kryptoagile provides FIPS 140-2 Level 3 compliant Hardware Security Modules to fully comply UIDAI directives.
Here are some of the advantages of hardware security modules offered by Kryptoagile:
Best suited for general purpose data processing
Digital document signing
PDF signing
GST signing
E-invoice signing
Extremely popular in financial data processing
Payment processing,
NEFT transactions,
RTGS transactions
Electronic fund transfer management
Powered with world's most advanced data encryption mechanism
Compatible with cross industry applications
https://www.kryptoagile.com/aadhar-authentication-hsm-solutions-delhi.html
#aadhaar authentication solutions#aadhaar authentication solutions in delhi#Entrust partners in Delhi#HSM in Delhi/NCR#HSM provider in India
0 notes
Photo

KUA Payload Drop System vtol release system for remote rescue and emergence delivery Brand Name: JUANTEC Compatible Drone Brand: ZEROTECH Size: 50x20x15.5cm Weight: 720g Model Number: KUA Lite PAYLOAD Compatible Drone Model: Any brand of drones can be fixed Package: Yes
0 notes