#anti harlos
Text
ideas zone 2023: Άνοιξαν οι εγγραφές για τα training με θέμα Αντιπαρακολούθηση και ψηφιακή ασφάλεια
9 Ιανουαρίου, 2023
ideas zone
Τα εργαστήρια θα πραγματοποιηθούν δια ζώσης τον Φεβρουάριο και απευθύνονται σε επαγγελματίες δημοσιογράφους
Το iMEdD, σε συνεργασία με εισηγήτριες και εισηγητές από διεθνείς οργανισμούς, διοργανώνει τον Φεβρουάριο διαδραστικό training με θέμα Αντιπαρακολούθηση και ψηφιακή ασφάλεια. Οι αιτήσεις εγγραφής για τα εργαστήρια, τα οποία θα έχουν συνολική διάρκεια 3 εβδομάδες και θα πραγματοποιηθούν στο iMEdD, θα παραμείνουν ανοιχτές μέχρι τις 27 Ιανουαρίου 2023.
ΔΗΛΩΣΗ ΣΥΜΜΕΤΟΧΗΣ
Το τελευταίο διάστημα γίνεται όλο και περισσότερο λόγος για την αυξανόμενη χρήση κατασκοπευτικού λογισμικού κατά των δημοσιογράφων και των πηγών τους και για τις επιπτώσεις στην άσκηση της ελεύθερης και ανεξάρτητης δημοσιογραφίας. Σε έναν κόσμο όπου αναπτύσσονται συνεχώς νέες τεχνολογίες παρακολούθησης και γίνεται μαζική συλλογή και διατήρηση δεδομένων, πώς μπορούν οι δημοσιογράφοι να προστατεύσουν καλύτερα τους εαυτούς τους και τις πηγές τους; Με ποιους τρόπους μπορούν να διατηρήσουν τις επικοινωνίες τους ασφαλείς;
Τα εργαστήρια θα παρέχουν μια ολιστική προσέγγιση της ψηφιακής ασφάλειας για επαγγελματίες δημοσιογράφους.
Αναλυτικό Πρόγραμμα:
Πέμπτη 9 Φεβρουαρίου, 18:00 – 21:00: Βασικές αρχές ψηφιακής ασφάλειας
Παρασκευή 10 Φεβρουαρίου, 18:00 – 21:00: Προχωρημένα θέματα προστασίας πηγών
–με τη Harlo Holmes, Υπεύθυνη Ασφάλειας Δεδομένων (CISO) και Διευθύντρια Ψηφιακής Ασφάλειας στο Freedom of the Press Foundation
Τα δύο πρώτα εργαστήρια χρησιμεύουν ως ολοκληρωμένος οδηγός για θέματα ψηφιακής ασφάλειας, ξεκινώντας από βασικές πρακτικές προστασίας δεδομένων και χρήσης social media και συνεχίζοντας σε προχωρημένες τεχνικές διασφάλισης επικοινωνιών με πηγές και κατ’ επέκταση τρόπους προστασίας της ταυτότητας τους.
Πέμπτη 16 Φεβρουαρίου, 18:00 – 21:00: Αυτοπροστασία από τη διαδικτυακή κακοποίηση & Ενίσχυση της ψηφιακής ασφάλειας: Anti-Hacking, Anti-Doxing Workshop
–με την Viktorya Vilk, Διευθύντρια Ψηφιακής Ασφάλειας και Ελεύθερης Έκφρασης στο PEN America
Αυτό το διμερές εργαστήριο θα σας καθοδηγήσει σχετικά με το πώς να προετοιμαστείτε, να αντιδράσετε, να φροντίσετε τον εαυτό σας και να υποστηρίξετε τους άλλους, παρέχοντας σας εργαλεία και στρατηγικές για την άμυνα κατά της διαδικτυακής κακοποίησης. Σε αυτό το πλαίσιο, θα δοθούν εξατομικευμένες συμβουλές για την προστασία από την πλαστοπροσωπία, το hacking και το doxing (τη δημοσίευση προσωπικών πληροφοριών).
Παρασκευή 17 Φεβρουαρίου, 18:00 – 21:00: Φυσικές παρακολουθήσεις: Αναγνώριση και αποφυγή (μέρος 1)
Σάββατο 18 Φεβρουαρίου, 09:00 – 17:00: Φυσικές παρακολουθήσεις: Αναγνώριση και αποφυγή (μέρος 2)
–με τον Frank Smyth, Ιδρυτή και διευθύνοντα σύμβουλο του Global Journalist Security (GJS)
Στο θεωρητικό μέρος του training, οι δημοσιογράφοι θα έχουν την ευκαιρία να μάθουν για τις διαφορετικές μορφές ψηφιακής και κυρίως φυσικής παρακολούθησης και πως να τις εντοπίζουν. Την επόμενη μέρα θα πραγματοποιηθεί το πρακτικό μέρος του training, το οποίο περιλαμβάνει ασκήσεις αναγνώρισης και αντιμετώπισης επιτήρησης σε εξωτερικό χώρο.
Πέμπτη 23 Φεβρουαρίου, 18:00 – 21:00: Πώς πρακτικά γίνεται η κατασκοπεία επικοινωνιών και συσκευών και πώς να το αποτρέψετε
Παρασκευή 24 Φεβρουαρίου, 18:00 – 20:00: Εξατομικευμένες συμβουλές: Πώς μπορείτε να ενσωματώσετε τις συμβουλές ψηφιακής ασφάλειας στην εργασιακή σας καθημερινότητα
–με τον Bill Marczak, Senior Research Fellow στο Citizen Lab
Οι δύο τελευταίες συναντήσεις θα καλύψουν θέματα όπως τη μαζική παρακολούθηση μη κρυπτογραφημένων επικοινωνιών, την αποθήκευση δεδομένων τους από εταιρίες τεχνολογίας, αλλά και τη στοχευμένη παραβίαση υπολογιστών και τηλεφώνων από μισθοφόρους hackers. Οι συμμετέχουσες και οι συμμετέχοντες θα μάθουν τρόπους να εμποδίσουν την παρακολούθηση, τόσο μέσω τεχνικών λύσεων όσο και μέσω αλλαγών στον τρόπο που χειρίζονται την τεχνολογία. Τέλος, θα γίνει έλεγχος των συσκευών τους για ενδείξεις hacking και παραβίασης δεδομένων.
Ο νέος κύκλος του ideas zone απευθύνεται σε επαγγελματίες δημοσιογράφους, διεξάγεται στα αγγλικά και είναι δωρεάν κατόπιν εγγραφής για περιορισμένο αριθμό συμμετεχόντων. Προτεραιότητα θα δοθεί σε όσους/ες ενδιαφερόμενους/ες έχουν διαθεσιμότητα να παρακολουθήσουν το σύνολο των εργαστηρίων.
NEWSLETTER

1 note
·
View note
Text
Verna: Carlos was in a fight today.
Ben: is he alright?
Mal: did he win?
#disney descendants#ben florian#mal bertha#bal#ben x mal#mal x ben#benmal#malben#dragon king#carlos de vil#yes carlos is bal’s son#fairy godmother descendants#anti harry hook#anti harlos#source: tumblr
66 notes
·
View notes
Text

@hersilentlanguage tier list
#I’ve never done a tier list before#Huma#jaylos#umaudrey#Harlos#Lovie#gay#umvie#anti devie#anti bal#disney descendants#descendants#disney descendants 2#descendants 2#descendants 3#disney descendants 3#descendants evie#evie grimhilde#tier list
74 notes
·
View notes
Text
Attack Surface in Wired

My next book, Attack Surface - AKA Little Brother 3 - drops in the US/Canada tomorrow (it's came out in other English-speaking countries on Oct 1) and today, Wired's Andy Greenberg published his review of the series and the new book.
It's excellent.
https://www.wired.com/story/his-writing-radicalized-young-hackers-now-he-wants-to-redeem-them/
Attack Surface is a standalone Little Brother book for adults, telling the story of Masha Maximow, a complicated sometimes-villain from the first two Little Brother books. While Marcus Yallow spends those books fighting surveillance, Masha is one of the people building in.
At first, Masha feels like she has good reasons for doing what she does, redirecting her trauma of living through a terrorist attack into making her city and country safer.
But as she moves from the DHS to some Beltway Bandits contracting in an Iraq Forward Operations Base, hunting insurgents, she increasingly turns to compartmentalization and rationalization as a means of living with her own reflection in the mirror.
Finally, she finds herself in the former USSR, where a new employer puts her to work spying on pro-democracy activists for brutal oligarchs, and to assuage her conscience, she moonlights teaching those same activists to resist her employer's surveillance gear.
This self-destructive behavior can't last long - as Masha flees her (former) employer's wrath, she returns to San Francisco, where her childhood best friend is now a racial justice organizer being targeted by the cyberweapons Masha herself built.
What follows is the story of Masha's moral reckoning, and moral reckonings are the theme of Greenberg's piece: after all, Little Brother and Homeland inspired a legion of pro-user, anti-surveillance technologists and activists.
But it also led plenty of people into tech careers that have been devoted to taking away the freedom and power that Little Brother excited in them to begin with.
Indeed, virtually everyone working on surveillance, ad-tech, or DRM started with the life-changing experience of discovering how code could project your will around the world, and how networks could set your mind free to wander the globe in search of likeminded communities.
And now, every day, they go to work making sure no one else will have that experience. Like all of us, they make a compromise, which begets a compromise, which begets yet another and another, and one day you find yourself working for Palantir or NSO Group.
Indeed, under conditions of monopoly capitalism, a sizeable fraction of us, in tech and out, spend our lives (and our money) furthering the interests of companies and states that are destroying those lives, and the planet too.
In the book, Masha thinks about this as a form of debt, like the "tech debt" that ever programmer has had to contend with: you take a shortcut, and then you have to prop it up in subsequent revisions, until the whole app is a teetering mess built on a crumbling foundation.
Like so many of us, Masha's moral debts have mounted and threaten catastrophic default. Attack Surface is the story of how she structures a bankruptcy that she can emerge from, transformed into a new and better person.
In his review, Greenberg talks with eminent human rights technologists about their own experience of the novel, and the tales he relates - many of which I read for the first time this morning - literally brought a tear of awesome, overwhelming joy and pride to my eye.
From Nathan Freitas, who put the book into the hands of every young technologist he met and then assigned it to his NYU ITP classes, where it found its way into the hands of Harlo Holmes, who calls it "fundamental to her origin story."
"It informed my thoughts around how privacy should work, the interplay between movement activists, technology and the law, and what you should look out for when inviting technologies into your life to do that movement building."
Today, Holmes is director of the Freedom of the Press Foundation, teaching activists and journalists to resist foundation - the Foundation is also home to Securedrop, which Aaron Swartz helped create. Aaron wrote an afterword for Homeland, and took his own life shortly before its publication.
I toured that book haunted by his specter, telling his story as best as I could at every stop. Then, years later, I happened on some video shot at that time: Laura Poitras's Academy Award-winning documentary CITIZENFOUR.
Homeland gets a cameo there, as Edward Snowden is packing his go-bag while he hustles out of his Hong Kong hotel room, heading for a HK safehouse, a plane, and then, thanks to John Kerry's decision to cancel his passport midflight, to a long-term exile in Russia.

Greenberg quotes Snowden on the book: "He is to me a radical idealist, because no matter how bad things get, his mind goes to the stories of cooperation and creation-sharing.
"When the traditional structures of oppression are up to no good, as was the case in Little Brother, Cory doesn't reflexively indoctrinate young readers with platitudes on the inevitability of corruption. He helps them reimagine the limits of their own power."
And then Greenberg quotes my EFF colleague Eva Galpering, who, like Masha, is a brilliant security researcher raised by Soviet refugees: "This is a book for the people who realize that they've grown up and made a lot of compromises, and about how you turn back from that."
Eva is joining me on the Attack Surface Lectures, a series of eight events that start tomorrow night.
https://read.macmillan.com/torforge/cory-doctorow-virtual-lecture-series/
Her remarks, and those of Greenberg's other sources, filled me with soaring joy this morning.
Even in the midst of my crushing, daily anxiety for the future of technology, the nations of my birth and residence, for my child and the planet she'll inherit, I was uplifted today.
These books of mine have gone far, thanks to readers like you. Today, with one day to go before Attack Surface's publication, I feel like, in some small way, I may have made a difference.
13 notes
·
View notes
Text
I wanna make a ship post. So I’m just gonna list some of my ships, antis can fuck off and suck a dick, I do not take criticism because this is my opinion and I have a right to ship who I want, however if you agree with me, please interact. No order and I can’t be bothered writing what shows they are from, just check the tags.
Malec
Tsukkiyama
Teruyama
Kiridenki
Dabki
Bakudeku
Bakukiritododeku
EraserMic
LAlly
LxLight
Reddie
BokuAka
KuroKen
KageHina
Ukaixtakeda
KiYachi
IwaOi
BenVerly
Benthur
Merthur
SiBram
RioNax
Nalu
Gale
Gruvia
Elfgreen
Miraxus
Baccana
Jerza
Harlos
#shadowhunters#haikyuu#mha#ally mcbeal#death note#IT#what if it’s us#merlin#the disasters#love simon#fairy tail#descendants
5 notes
·
View notes
Text
A VERY DESCRIPTIVE PROFILE OF YOUR MUSE. repost with the information of your muse, including headcanons, etc. if you fail to achieve some of the facts, add some other of your own !

NAME. Arthur Dayne.
NICKNAME(S). The Sword of the Morning.
ALIAS(ES). Harlo Brenos (as a sellsword in Essos)
AGE. 23-45, verse/timeline dependent.
SPECIES. Human.
GENDER. Male.
ORIENTATION. Bisexual.
INTERESTS. Swordplay, swimming, horses, reading.
PROFESSION. Kingsguard/Sellsword (verse dependent).
BODY TYPE. Lean, yet muscular.
EYES. Purple.
HAIR. Dark Brown/Black. Long in some verses, short in others.
SKIN. Dornish.
FACE. Rounded face, strong jaw, light beard.
HEIGHT. 6′3′’ (look he’s gotta be uber tall to hold a sword like Dawn’s described, in reality, even this is probably too short lol).
COMPANIONS. Fellow Kingsguard, Rhaegar, Elia, Ashara.
ANTAGONISTS. Robert Baratheon, Cersei Lannister, Tywin Lannister, Ned Stark, anyone anti-Targaryen.
COLORS. Purple, White, Black, Silver.
FRUITS. Blood Oranges, Dates, Olives, Plums.
DRINKS. Water.
ALCOHOLIC BEVERAGES? Dornish Sweetwine, Dornish Red.
SMOKES? No.
DRUGS? No.
DRIVERS LICENSE? No.
tagged by. @needlcd <3 <3 <3
tagging @sandwulf, @obuljagon, @swxrdofthemxrning, @isylaofwyl, @zaldrizerme, @droppedrubies, @lastxdragon, @wineinthewidow anyone else who wants to do it!!
6 notes
·
View notes
Text
How to Organize Your Workplace Without Getting Caught
In the last few years, American workers across multiple industries have unionized or mobilized collectively in an attempt to get better wages, demand accountability for sexual harassers in the workplace, push for real action to slow down climate change, and in general, change company culture.
The movement seems to be popping up everywhere: Amazon, Google, Gawker, Riot Games, Salesforce, Tesla, Kickstarter, Uber, you name it. In fact, approval ratings for unions among Americans are at the highest level since the beginning of the 2000s, according to Gallup.
As proud members of a union, we at Motherboard understand how important collective action is, and how challenging it can be. One of the biggest and perhaps most overlooked questions is: how do you form a union or organize a workplace walkout without tipping off the company that owns your computers and internet connection?
Whenever you use your company’s communications equipment, there is a risk that the company could find out about your organizing, giving it a chance to thwart planned actions or even retaliate against the organizers. Unfortunately, this is not hypothetical. At Hearst Magazines, the company launched an anti-union campaign to persuade workers to vote against the union. Google has fired employees who have been involved in organizing, and recently hired an anti-union consulting firm, IRI Consultants, to crack down on employee activism at the company. At the end of last year, Amazon threatened to fire employees who spoke out about the company's carbon footprint. Several employees involved in unionization at Kickstarter also lost their jobs.
Employees no longer have the right to organize using a company’s email system or the company’s Slack or equivalent chat system. The Trump administration's National Labor Review Board just ruled employers can crack down on workers who do so.
While there’s no silver bullet for these problems, there are ways to organize securely. We created this guide by talking to digital security experts, as well as workers involved in organizing at Amazon and Microsoft, about how to unionize or organize a labor action securely. Call it the Motherboard Guide to Labor OPSEC. Like any security guide, this advice is not comprehensive, and not all advice will be relevant in every workplace or for every situation.
It's also worth considering that some of the most powerful worker actions have not been done anonymously, and that there may be benefits to signing your name to an open letter, or speaking to the press as a named source, or giving a speech at a public rally. Every worker must consider their own situation and whether or not they are willing to take the risk of potentially becoming the public face of a workers movement.
Disclaimer: for the purpose of this guide, we are assuming a scenario where there is no union in place, and workers want to organize some sort of action or organize a union. Once there’s a union, there are more legal protections and much of the security measures here become redundant or unnecessary.
KNOW YOUR COMPANY
Before even thinking about what you should and shouldn’t do, or what tech you should or shouldn’t use, ask yourself: do you know your company?
In other words, does your company have a history of union busting, anti-workers policies, or general unfriendliness toward workers organizing or expressing concern? Or, on the other hand, has it historically been amenable to workers speaking up for their rights? It’s impossible to anticipate the future, but having a general idea of what you’re up against is the basis of what cybersecurity professional call threat modeling. This is the foundation of any good operational security—or OPSEC—plan.
As part of this effort, it may be good to figure out where your colleagues stand as well. As the workers organizing at Microsoft put it: “Get to know your fellow organizers!”
“It's easy to get caught in doing organizing work and forgetting to build relationships with the people you are closest to. This may uncover shared interests and new opportunities to collaborate,” the group told Motherboard.
At this point, it’d be very useful to also brush up on your company’s policies when it comes to accessing employee computers and phones. Take a look at your contract or the employee handbook: Is there any language about what the company can access? If so, take note of that and adjust you plan accordingly. Absence of this language doesn't mean that the company can't access your email or remotely control your computer, so it's best to be cautious.
Once you have a general sense of your company’s attitude and policies, it’s time to think about the tools you're using to organize.
AVOID COMPANY INFRASTRUCTURE
If we could condense this guide in one sentence, it would be, "Avoid company infrastructure." By that we mean computers, phones, printers, chat software, and email. But also avoid discussing labor actions in physical places like meeting rooms, cafeterias, or basketball courts.
That may sound difficult, but using company infrastructure to organize is risky and may tip off management about your upcoming organizing drive, open letter, walkout, or other labor action. It’s unlikely that your company is actively sniffing internet traffic or monitoring computers in real time for any chatter of forming a union or organizing some kind of labor action. But there are no guarantees.
“A lot of companies have at least minimal remote device management, which would allow IT to shoulder-surf at will, or otherwise view the contents of your company-provisioned computer,” said Harlo Holmes, a digital security specialist at the Freedom of the Press Foundation.
Of course, in this day and age, it may be impossible to get off the company’s grid completely, so let’s break it down a bit more.
COMPANY EMAIL & CALENDARS
This is the easiest way for your company to keep tabs on you. You should assume that IT and others in management have access to your corporate email. And even if they may not read it every day, they can probably comb through it after the fact. So avoid using corporate email at all costs. Recently, Google fired employees who were, in some cases, accessing corporate calendars that the company deemed unusual.
Every labor action should probably start with collecting workers’ personal contact info, such as a personal email address and cell phone number. Use those to communicate.
DON’T USE COMPANY COMPUTERS OR OTHER DEVICES
As Holmes warned, most companies have a way to access worker’s laptops and perhaps even their corporate phones. So try to avoid using them. Using a personal computer on the company’s WiFi is not as dangerous, but if you can, avoid that too and connect from home.
Workers involved in organizing at Amazon suggest keeping “any non-public organizing documents and conversations off your work computer.”
“Do not sign into accounts containing this information,” the group adds.
Workers organizing at Microsoft tell their colleagues not to “use the same phone for organizing as work stuff.”
“For this I just don’t work when I’m not at work,” a Microsoft employee told Motherboard in an email.
It’s not just the actual devices you should worry about, but also apps. The Microsoft workers warn people against using “corporate tools like text editors or note taking apps as you might leave a trace of your organizing work.”
Under no circumstances should you use the office printer. Office printers log who prints what, so if the company launches an investigation after a leak or worker action, chances are it will check who printed what.
USE ENCRYPTED APPS FOR COMMUNICATIONS
If you stay away from you company’s infrastructure, you’ll have already done most of what you need to secure your organizing activities. But, just in case, try to avoid Slack or other chat services that are not encrypted and don’t give you much control over what data is retained. Companies have the ability to read Slack archives, including DMs. It's also worth mentioning that, by default, paid Slack accounts retain messages indefinitely.
Alternative group chat apps such as Keybase and Wire not only protect your messages in transit, they also allow you to set messages to self-destruct after a set amount of time. This helps cover your tracks.
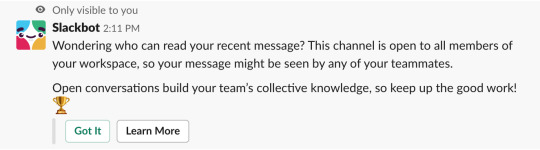
A useful reminder about privacy from Slack’s automated tip bot.
While we love Signal, the popular encryption app is not ideal for large groups who need to share documents, for example.
If you think asking your colleagues to use new chat apps may be a tough sell, it’s probably OK to stick to non-encrypted apps such as Facebook Messenger or even Google Hangouts (unless you work at Google!)
“Use appropriate tools for your circumstances. Facebook Messenger is a very accessible messaging app if you don’t work at Facebook, don’t use it on your work computers, and aren’t worried about conversations showing up in court,” workers involved in organizing at Amazon said.
The Amazon workers also warn of the possibility of your company monitoring your public social media accounts: “Make sure to lock down your social media accounts to make it more difficult for the company to map out who you know, what you’re doing, and what you’re talking about.”
This means pay attention to who you're friends with on Facebook, following on Twitter, and looking up on LinkedIn (you should always browse LinkedIn in private mode.) This is especially important if you plan to leak to the press: If you're leaking to the one reporter you're following and interacting with on Twitter, it's possible the company could trace information back to you, or at least consider you suspicious.
Even better, especially at the beginning of an organizing drive, try to stick to IRL conversations, ideally not on company grounds. This is not only the best way to pitch the action to colleagues but it’s also less exposed to snooping and is inherently ephemeral, as a representative from the Writers Guild of America, which represents VICE's editorial union, told Motherboard.
“Prioritize one on one IRL conversations,” the representative said. “This is not only the most effective form of communication in building support, but also the most secure.”
IF YOU'RE GOING TO LEAK TO THE PRESS
A carefully-placed leak or tip to the press alerting journalists of your unionizing drive or collective action may help your cause. If you're going to leak to the press, familiarize yourself with what the terms "on the record," "off the record," and "on background" mean.
If you reach out to or speak to a journalist, things you say to them are, by default, on the record. This means that the journalist can quote and use that information and attribute it to you with your name. "Off the record" means the journalist can have that information for their own knowledge, but can't publish it without confirming it with another source, and they can't attribute it to you. They are allowed to take that information and try to get someone else to provide it on the record, however. "On background" means different things to different people—often it means that the reporter can use the information in their article but not attribute it to you. Other people use it to mean "can be quoted anonymously." It's best to talk this through with the reporter before you share information.
You can discuss sharing information anonymously or doing interviews anonymously with a reporter. At Motherboard, we grant sources anonymity if their speaking to us would put them in physical or professional danger. We require our reporters to tell readers why we are granting a source anonymity; if the source could be fired from their job for speaking to us, we will often grant anonymity. We will know the identity of the source—more often than not, we need this information to ensure we are talking to someone who is in a position to know about the issue at hand—but we won't publish or otherwise reveal who the person is.
It is best to be clear with the reporter before you share anything about how you want the information to be used—if you say something "on the record," you cannot retroactively take it off the record. (This is to ensure that someone can't backpedal on information they've said that is in the public interest, but change their mind about). These conditions must be agreed to by both parties, so don't reach out to a bunch of reporters with information that you want to share "off the record" if those reporters haven't already agreed to go off the record with you.
Often, workers want to share internal documents, emails, memos, or other company materials with the press. There are several ways this can be done. The easiest is to take a photo of your computer's screen with the camera on your personal phone, and to share the image(s) you take as a disappearing message on Signal. Then, delete the image from your phone and potentially the journalist's number from your contacts and message history. You can also use SecureDrop. If anonymity is important to you, don't forward company emails that you intend to leak to journalists if you feel you could be fired for doing so.
This all may sound like a lot, but many of the tactics in this guide become second-nature with practice. Practicing general cybersecurity best practices is also recommended. For more, you can check out the Motherboard Guide to Not Getting Hacked.
Subscribe to our cybersecurity podcast, CYBER.
How to Organize Your Workplace Without Getting Caught syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes
Text
Release Blast for Shaded With Love: a coloring book for a cause Volume 5
#ReleaseBlast #ShadedWithLove #ColoringForACause Shaded With Love: a coloring book for a cause Volume 5 is here!! This coloring book, featuring 95 designs inspired by your favorite authors, bloggers & Editors, is ready to become of your stress relief. Or your gift to someone who needs a smile! All proceeds will benefit RAINN which is the nation’s largest anti-sexual violence organization. Find out more about RAINN by visiting their website. https://www.rainn.org/ Amazon Purchase Links: US: http://amzn.to/2FSLsiO UK: http://amzn.to/2HvQcrA ~~ Contributing Authors/Bloggers/Editors ~~ 2 One-Click Addicts ~ A Page to Turn Reviews ~ Amanda Leigh ~ Amber Addison ~ Amber Lacie ~ Amelia Wilde ~ Andrea Johnston ~ Ashlynn Monroe ~ Author L.A. Ozz ~ Barb Shuler ~ Betty Shreffler ~ Blooming Books ~ Brandi Aga ~ Bree Dahlia ~ C.J. Lazar ~ Cassie Graham ~ Cayce Poponea ~ Chelle C. Craze ~ Cheryl McMahan ~ Cora Kenborn ~ D. M. Earl ~ Dani René ~ Danielle Wright ~ Darlene Tallman ~ Deneale K. Williams ~ Diana Marie DuBois ~ Dirty Fairytales ~ DL Gallie ~ Dylan Allen ~ Dyllan J. Erikson ~ Eden Rose ~ Elizabeth York ~ H.M. Sholander ~ Harloe Rae ~ Jack Jameson ~ Jaime Russell ~ Jas T. Ward ~ Jennifer Vester ~ Jiffy Kate ~ Jo-Anne Joseph ~ Jordan Bates ~ K. Renee ~ Kaitlyn Ashley ~ Kathleen Kelly ~ Kathryn Kelly ~ Kay Maree ~ KC Enders ~ Kelsey Elise Sparrow ~ Kenzie Rose ~ Kim Deister ~ Kristie Leigh ~ Lane Martin ~ Lauren Firminger ~ Leddy Harper ~ Lexi C. Foss ~ Lilly Avalon ~ Lisa Shelby ~ Little Shop of Readers ~ LK Farlow ~ M.A. Foster ~ M.C. Webb ~ M.E. Carter ~ M.R. Leahy ~ Mareta L. Miller ~ Martina Marie ~ Michele Shriver ~ Mila Waters ~ Misha Elliott ~ Mitzi Carroll ~ Nicky Fox ~ Nicole Banks ~ Nikki Ash ~ Phoebe Alexander ~ Reading After Dark ~ Reagan Hollow ~ Rebecca Gallo ~ Renee Dyer ~ Roux Cantrell ~ S. Van Horne ~ S.N. Garza ~ Samantha A. Cole ~ Scott Hildreth ~ Socially Awkward Book Nerd ~ Steffy Rogers ~ Susan's Books I Like ~ Sylvie Stewart ~ Taryn Steele ~ The Bookworm Box ~ Tracie Douglas ~ Tracy Millosovich ~ V.P. Ortiz ~ Verlene Landon ~ Vicki Green ~ Vivian Wood ~ Xana Jordan ** Previous Volumes are available on Amazon! ** Shaded With Love - Vol 1 (http://amzn.to/2Ft6YIc) All proceeds will be donated to Free2Luv Shaded With Love - Vol 2 (http://amzn.to/2F58NNN) All proceeds will be donated to St. Jude Children's Research Hospital Shaded With Love - Vol 3 (http://amzn.to/2FvqHHg) All proceeds will be donated to The American Foundation For Suicide Prevention Shaded With Love - Vol 4 (http://amzn.to/2F2JSdx) All proceeds will be donated to BACA: Biker's Against Child Abuse! Tour Sponsored by Paging Through The Days Promotions http://pagingthroughthedays.blogspot.com http://facebook.com/pagingthroughthedays
Shaded With Love: a coloring book for a cause Volume 5 is here!! This coloring book, featuring 95 designs inspired by your favorite authors, bloggers & Editors, is ready to become of your stress relief. Or your gift to someone who needs a smile! All proceeds will benefit RAINN which is the nation’s largest anti-sexual violence organization. Find out more about RAINN by visiting their…
View On WordPress
#2 One-Click Addicts#A Page to Turn Reviews#Amanda Leigh#Amber Addison#Amber Lacie#amelia wilde#Andrea Johnston#Ashlynn Monroe#Author L.A. Ozz#Barb Shuler#Betty Shreffler#Blooming Books#Brandi Aga#Bree Dahlia#C.J. Lazar#Cassie Graham#Cayce Poponea#Chelle C. Craze#Cheryl McMahan#Cora Kenborn#D.m. earl#dani rene#Danielle Wright#Darlene Tallman#Deneale K. Williams#Diana Marie DuBois#Dirty Fairytales#DL Gallie#Dylan Allen#Dyllan J. Erikson
0 notes
Photo

#CoverReveal #ShadedWithLove #ColoringForACause This coloring book, featuring 93 designs inspired by your favorite authors, bloggers & Editors, will release on March 15th. All proceeds will benefit RAINN which is the nation’s largest anti-sexual violence organization. So get your one-click finger ready! Find out more about RAINN by visiting their website. https://www.rainn.org/ ~~ Contributing Authors/Bloggers/Editors ~~ 2 One-Click Addicts ~ A Page to Turn Reviews ~ Amanda Leigh ~ Amber Addison ~ Amber Lacie ~ Amelia Wilde ~ Andrea Johnston ~ Ashlynn Monroe ~ Author L.A. Ozz ~ Barb Shuler ~ Betty Shreffler ~ Blooming Books ~ Brandi Aga ~ Bree Dahlia ~ C.J. Lazar ~ Cassie Graham ~ Cayce Poponea ~ Chelle C. Craze ~ Cheryl McMahan ~ Cora Kenborn ~ D. M. Earl ~ Dani René ~ Danielle Wright ~ Darlene Tallman ~ Deneale K. Williams ~ Diana marie DuBois ~ Dirty Fairytales ~ DL Gallie ~ Dylan Allen ~ Dyllan J. Erikson ~ Eden Rose ~ Elizabeth York ~ H.M. Sholander ~ Harloe Rae ~ Leddy Harper ~ Jack Jameson ~ Jaime Russell ~ Jas T. Ward ~ Jennifer Vester ~ Jiffy Kate ~ Jo-Anne Joseph ~ Jordan Bates ~ K. Renee ~ Kaitlyn Ashley ~ Kathleen Kelly ~ Kathryn Kelly ~ Kay Maree ~ KC Enders ~ Kelsey Elise Sparrow ~ Kenzie Rose ~ Kim Deister ~ Kristie Leigh ~ Lane Martin ~ Lauren Firminger ~ Lexi C. Foss ~ Lilly Avalon ~ Lisa Shelby ~ Little Shop of Readers ~ LK Farlow ~ M.A. Foster ~ M.C. Webb ~ M.E. Carter ~ M.R. Leahy ~ Mareta L. Miller ~ Martina Marie ~ Michele Shriver ~ Mila Waters ~ Misha Elliott ~ Mitzi Carroll Copy and Line Editor ~ Nicky Fox ~ Nicole Banks ~ Nikki Ash ~ Phoebe Alexander ~ Reading After Dark ~ Reagan Hollow ~ Rebecca Gallo ~ Renee Dyer ~ Roux Cantrell ~ S. Van Horne~ S.N. Garza ~ Samantha A. Cole ~ Socially Awkward Book Nerd ~ Steffy Rogers ~ Susan's Books I Like ~ Sylvie Stewart ~ Taryn Steele ~ Tracie Douglas ~ Tracy Millosovich ~ V.P. Ortiz ~ Verlene Landon ~ Vicki Green ~ Vivian Wood ~ Xana Jordan ** Previous Volumes are available on Amazon! ** - Shaded With Love - Vol 1 (http://amzn.to/2Ft6YIc) All proceeds will be donated to Free2Luv - Shaded With Love - Vol 2 (http://amzn.to/2F58NNN) All proceeds will be donated to St. Jude Children's Research Hospital - Shaded With Love - Vol 3 (http://amzn.to/2FvqHHg) All proceeds will be donated to The American Foundation For Suicide Prevention - Shaded With Love - Vol 4 (http://amzn.to/2F2JSdx) All proceeds will be donated to BACA: Biker's Against Child Abuse! #TourSponsored by Paging Through The Days Promotions http://pagingthroughthedays.blogspot.com http://facebook.com/pagingthroughthedays
0 notes
Text
How To Earn 0.02 - 0.5 Bitcoins Fast And Easy
New Post has been published on https://www.music-chat.ru/how-to-earn-0-02-0-5-bitcoins-fast-and-easy/
How To Earn 0.02 - 0.5 Bitcoins Fast And Easy
du ich coins i van mining wird my mac
local council
2016-04-03 1
only two genders
boyoom
landvideo
casino roulette
diät essen
lmc’râr
muammar al-gaddafi (politician)
Once In Love With Amy Ray Bolger
family incest
para la disco jory boy
oрифлэйм aлмaты зaкaзaть
aryo from alien zik /experience /
roofing professionals
hyperloop transportation technologies
johnny cage
cod ww2 commentary
frias
breakeven THE SCRIPT
gameplay evil within 2
旅行車
formation of real akatsuki part 5
ауди (organization)
knives out gameplay
jess and gabe
sausages»
rodrigo noé mendes
destorm power
jeremy lin
pes 2018 xbox one
Rebb
remove contacts
light cone
claudio11
zgirl
alina somova
lego bath
jazz pv
youtuber kids
popa chubby
raja club atheltic
How much is the fish Scooter
Sultans Of Swing Dire Straits
puerta abierta
throws in java
prea
La buhardilla
ogof
meine gang
SMart! baby hazel videos
tobą
#newbreedisborn
sonpur mela
easily
duoharbatah
they ain’t nothing but drama
The Vampire Show
south jersey girl fights
piya more baadshaho song
हवा कसूती
despair phora
Heidenröslein D 257 Elly Ameling(s), Dalton Baldwin(pf)
the tenderloin
for whatever
piece of mine
leviathan bones
the earth
police shootout scene
nepalese hip hop
papua lucu
comida ecuatoriana
campobello island
swimming pools kendrick lamar
Day By Day Badmarsh & Shri
Noi non ci saremo Nomadi
You’re The First, The Last, My Everything Barry White
neusten
sound like kirk hammett
irrgarten der existenz
chessbase india
build battle map
top 5 christmas
the willie williams show video correction
Chef Academy
Six Feet Under
james madio
winds of winter
katie o’hagan
samsung türkiye
gmod war of the worlds mod
game of thrones successor show
rana daggubati and vijay devarakonda
мерседес e250 review
aviones militares
risugamiu0027s modloader
dansk eat or die
perawan atau janda karaoke
presente+diario
歯科検診
Danse (Drauf & Dran Remix) Alle Farben
funny compilation 2017 try not to laugh
ecco perché
charbonneux marron
youtube books
matt santoro 7 myths
curso de ingles
Frankie and Bruce
dance mixtape
velozes e furiosos 8 completo
kegeln
romanze
«confession»
Piotr Iliich Chaikowsky: Dance Chinoise ( da Lo Schiaccianoci) Colorado string Quartet e Ethos Percussion Group, Harold Faberman (dir.)
xotf
the amazing spider-man 2 video game
navaratri
ruspa
bit coin top 10
tyler fialko
thvl1 truc tuyen hom nay
comidas rapidas y faciles
deporte es vida
konser
flowerfell fr
pigment
ecografía
of berywam
muzikanten
rapboxsolo
antalyaspor
zombie unicorn costume
puppy dog eyes
as above so below meaning
senyum
esperance de vie
bside
baku 2017
escalate
dymitri dos santos
陳豪
pixel gun 3d gamplays
funzoa teddy
alex puertolas
Roman White: Diary of a Director — Blake Shelton’s ‘Over’
wilty
how to stop global warming
upanishads (religious text)
aura kingdom
kopp verlag
Elvis, Rosental, VeHaIsha Hamistorit
rachel bay jones
a pontida
how to pack backpacking
fraire
90s By Nature Showtek feat. Get Easy bitcoin:
How To Earn 0.02 — 0.5 Bitcoins Fast And Easy
………….. MC Ambush
The Bobby Limb Show
pipa espelho
180 mph
anti anxiety
Back On Track (H-Trance Mix) Hi Beatz
urban skargren
craziness frozen
La vita che verr�
farroupilha rs
malysz
zords destroyed
peroduamyvi
Jeep’S Blues Ellington — Hodges
pulse jet engine
harlo
k-12
My name’s Great Mazinger Ichiro Mizuki
industrie
silly to
proteina en polvo
sm molino
smart keno
basketball photo day
sips cities skylines
tudjman
juanfutbol
viaje al polo norte
msine musik
I leilasia mias zois
npo3
Party Preparations Rachel Portman
flava in ya ear craig mack
loepsie dutch
東方西方 林憶蓮
de kleintjes
pista hot wheels
friends arena
sikonakry Wofa
Todo lo bueno Jonathan Romero
inidie премиум
ауди tt (automobile model)
religious places
hoosiers
on basketball
kavgaları
Social Anxiety
boerin bertie
All I Need is a Miracle Mike and the Mechanics
wrestled
The Way To Market Station Aislers Set
of the anamorphic
stress mantra
iconx review samsung
pek k’ny remix 2016
Bro-Dum
basejump
threes company
aлeксeй вoрoбьeв
smotra md
sola audio
fichis y debryanshow
tal le temps qu’il faut
comedy channel india
The Ten Commandments Of Love Bob Marley
frank ed
brake rotor price
julian bugier
wage war
Viva America
georgi
makeupvlogger
Revolve Trevino
continuity test calculus
Deng lu Ri ben
fachkräftemangel
Down With This (J-Rod Remix) Showtek
mikhail osipov
美食旅客
Burnin’ Paul Taylor
gootecks urien
for intentional
prague’s
lava
0 notes
Text
Harry: If being cool is a crime, then you can call me-
Carlos: A law-abiding citizen.
66 notes
·
View notes
Text
Gil: It was a freak accident!
Carlos: Like Harry’s birth.
36 notes
·
View notes
Text
Carlos: I think you should make like a tree and just stand there while I go get my chainsaw.
8 notes
·
View notes
Text
Carlos: I appear to have invented a knife-wielding tentacle. If anybody would like to volunteer to come and turn it off, that’d be just fine by me.
22 notes
·
View notes
Text
Carlos: In my opinion, we don't devote nearly enough scientific research to finding a cure for jerks.
#disney descendants#carlos de vil#anti chad charming#anti chadlos#anti harry hook#anti harlos#anti audrey daughter of sleeping beauty#source: calvin and hobbes
16 notes
·
View notes
Text
Carlos: No more being the bigger person. I’m gonna start biting people.
27 notes
·
View notes