#two-factor authentication
Text
Items Returned
At long last, I have been restored to my property.
Fourteen months ago, my mobile phone, personal computer, and other effects were removed from my home.
What followed was a massive headache as I quickly realized that I could not access the majority of my accounts without the two-factor authenticator (2FA) app on my phone.
My bank, primary email account, and all the financial offers I had done…

View On WordPress
0 notes
Text
Here's a reminder that you shouldn't use SMS text-based two-factor authentication.
App-based 2FA is far more secure, and it's instant too. If you're on a site that supports passkeys, those are even better!
[tumblr] offers both app-based and SMS text-based 2FA. If you're still on SMS, click the edit pencil icon next to "Two-factor authentication" in your Account Settings to switch on "Generate code via authenticator app" and switch off "Send code via SMS." And don't forget to save your backup codes!
If you don't have a smartphone that supports authenticator apps, SMS text-based 2FA is better than nothing, but do make that switch as soon as you can.
1 note
·
View note
Text
LinkedIn Hacker Mayhem
Automated Security Challenges – Photo Credit Gizmodo
Should You Panic or Stay Calm?
It could just be me but I doubt it. I’ve certainly had my share of attempts to attack my accounts including the SIM Jacking I documented (3 Minutes to Financial Ruin). But since the vast majority of these attacks are automated with the perpetrators using tools that essentially automate the tasks of attacking…

View On WordPress
#2FA#account protection#Cybersecurity#data breach#Hacking#Healthcare Security#LinkedIn#login alerts#Password Managers#password security#Passwords#phishing#secure#Security#social media security#two-factor authentication
0 notes
Text
Heads up: Threatening software detected; opening the file is prohibited.
In an era where the digital world is as intrinsic to our lives as the air we breathe, the relevance of cybersecurity can not be overemphasized. Secure mobile apps , every download, and every apparently innocuous online interaction brings with it the possible risk of inviting malicious software right into our digital sanctuaries. This write-up aims to illuminate why downloading and install or opening destructive programs on your computer system is not simply dangerous-- it belongs to unlocking to your electronic home to a host of unwelcome effects.
Malicious software application, or "malware," is a wide term that encompasses numerous kinds of damaging software program, including viruses, trojans, worms, ransomware, and spyware, to name a few. These electronic threats are developed with purposes that vary from benign mischievousness to straight-out malevolent functions, such as stealing individual details, pirating computer resources, or securing documents for ransom money.
Cyber hygiene of downloading or opening a documents that harbors malware can trigger a domino effect of occasions that jeopardize your computer's safety and security and honesty. Here's a failure of why it's perilous:
1. ** Personal Info Theft **: Many types of malware are created to stealthily infiltrate your system and pilfer delicate data such as passwords, financial details, and individual identity details. This information can then be made use of for illegal tasks, marketed on the dark internet, and even bring about identification burglary.
2. ** System Damage **: Certain malware variations can corrupt documents, alter or delete important system data, and in extreme instances, make a computer inoperable. This not only interrupts individual or company operations but can additionally result in the loss of important data.
3. ** Source Hijacking **: Some malicious programs, like cryptojacking malware, clandestinely use your computer system's sources to mine cryptocurrency, considerably decreasing your system and potentially creating lasting damage to elements as a result of overheating or overuse.
4. ** Ransomware **: Probably one of the most nefarious forms of malware, ransomware secures your files, securing you out of your very own data. The wrongdoers then demand a ransom for the decryption trick. Paying the ransom, nonetheless, does not ensure the return of your information and additional funds the cycle of cybercrime.
5. ** Personal privacy Violation **: Spyware and certain kinds of trojans can check your activities, log keystrokes, and even turn on video cameras and microphones without authorization, bring about an extensive intrusion of privacy.
Shielding on your own from these digital threats entails a combination of watchfulness and the usage of cybersecurity tools. Always validate the resource of your downloads, avoid opening email add-ons or links from unidentified senders, and use thorough anti-viruses software application that supplies real-time defense, routine updates, and system scanning capabilities.
Enlightening oneself on the characteristics of phishing attempts and rip-off sites is also important. These commonly function as the distribution devices for malware. Search for HTTPS in web addresses, and watch out for sites that display inadequate design, spelling, and grammar mistakes, or that request unnecessary personal information.
To conclude, Secure coding standards is much better than remedy" has actually never ever been even more applicable than in the context of digital safety. The short-term adventure or benefit of downloading an unknown documents fades in contrast to the possible threats. By exercising safe surfing practices and arming your system with robust protection steps, you can substantially alleviate the risk of malware and guard not just your digital life, however your reality too.
#Secure computing#Phishing scams#Spyware threats#Hacking protection#Cybersecurity tips#Vulnerable software#Email attachment safety#Internet phishing#Digital security#Malicious URLs#Online fraud prevention#Security patches#Firewall protection#Virus scan#Secure passwords#Two-factor authentication#Cybersecurity education#Malicious code#Cyber hygiene#Data encryption#Secure networks#Security vulnerabilities#Malware quarantine#Cyber defense strategies#Suspicious activity monitoring#Identity theft protection#Secure file sharing#Malware signatures#Cyber risk management#Secure online transactions
1 note
·
View note
Text
A Guide to Finding Your Apple ID
A Guide to Finding Your Apple ID. The Apple ID – the key that unlocks the entire Apple ecosystem, from the App Store to iCloud to Face ID. But what happens when that key seems to have vanished deeper than a wormhole in the latest sci-fi movie? Don’t panic, fellow Apple enthusiasts! This guide is your compass for navigating the digital wilderness and finding your Apple ID once again.
Continue…

View On WordPress
#A Guide to Finding Your Apple ID#Apple devices#Apple ecosystem#apple id#Apple ID password#Apple ID website#email recovery#email search#find Apple ID#lost Apple ID#recover Apple ID#security tips#social media#two-factor authentication
0 notes
Text
In the current era, where almost every aspect has transitioned to the digital platform, the issue of digital security is a growing concern. Given the ongoing cyberattacks and phishing attempts, adopting security measures like 2FA has become imperative. However, you might be wondering what it is, how it works, and what the benefits of two-factor authentication are.
0 notes
Text
Can I Invest Bitcoin in Binance
Cryptocurrency is the financial world by storm, with Bitcoin working the way as a most popular investment choice. The potential of investing Bitcoin especially on the Binance platform. Buckle up as we survey the ins and outs of this excite speculation.
Introduction
In the advance technology of cryptocurrency, where fortunes are prepare and lost in the blink of an eye. Bitcoin stands as a beacon…

View On WordPress
#Binance#Bitcoin#Buy Bitcoin on Binance#Can#Can I Invest Bitcoin in Binance#Creating a Binance Account#Depositing Funds#Invest#Key Features#market#Purchasing Bitcoin on the Binance#rsik#strategy#Two-Factor Authentication#withdraw
0 notes
Text
Inactive Gmail Accounts Deletion Next Month December 2023 - Secure Steps to Keep Your Google Account Active
Introduction:
As we navigate the vast digital landscape, keeping our online accounts secure and active is crucial. Google has recently announced an upcoming cleanup initiative that targets inactive Gmail accounts. Scheduled for deletion next month, this proactive measure aims to enhance security and manage data storage efficiently. In this blog post, we’ll guide you through the steps to ensure…

View On WordPress
#Account Access#Account Activity#Account Maintenance#Account Notifications#Account Recovery#Cleanup#Cybersecurity#Data Storage#Deletion#Digital Cleanup#Gmail#Google Account#Google Services#Inactive Accounts#Online Privacy#Online Security#Password Security#Security Measures#Third-Party Apps#Two-Factor Authentication
0 notes
Text
BDRSuite v7.0.0 GA Released New Features
BDRSuite v7.0.0 GA Released New Features #VembuBDRSuitev7.0.0GARelease #BackupandRecoverySoftware #KVMBackup #AzureBackup #AWSBackup #PostgreSQLBackup #FileShareBackup #TwoFactorAuthentication #ImportBackupData #PrePostBackupScripts #FileLevelRecovery
Vembu Technologies has recently unveiled the latest BDRSuite v7.0.0 GA, introducing many new features. This release has many new features and enhancements for comprehensive backup and recovery capabilities. Let’s look at BDRSuite v7.0.0 GA and the new features it contains.
Table of contentsWhat is BDRSuite?Free version for home lab environmentsOverview of the new featuresKVM Backup and…

View On WordPress
#aws backup#azure backup#Backup and Recovery Software#File Level Recovery#File Share Backup#Import Backup Data#KVM Backup#PostgreSQL Backup#PrePost Backup Scripts#two-factor authentication#Vembu BDR Suite v7.0.0 GA Release
0 notes
Text
FIDO Technology: The Future of Secure Online Authentication
The Revolution in Online Authentication: FIDO Technology Explained
Introduction:In today’s digital age, security and convenience are at the forefront of online interactions. Traditional username and password authentication methods have proven to be vulnerable to various cyber threats, leading to a search for more robust alternatives. Enter FIDO, which stands for “Fast Identity Online.” FIDO…

View On WordPress
#Biometrics#Cybersecurity#FIDO Technology#Online Authentication#Passwordless Authentication#Two-Factor Authentication#User Privacy
0 notes
Text
How to set up Two-factor Authentication: The 2023 Identity Management Guide
Safety breaches in the digital era are a common occurrence. Cybercriminals are looking for approaches to access personal facts. One way to help guard against these assaults is by using two-factor authentication (2FA), which adds a further layer of protection to your identity management systems.
EnableX multichannel CPaaS makes it easy to put in force 2FA through various channels such as video, voice, SMS, and WhatsApp for Business API, providing a convenient and secure manner for end users get the right of entry to their accounts.
In this blog, we will explore the following:
Why is 2-factor authentication important
Trends in identity management solutions globally
How to set up 2-FA using SMS OTP, the most widely used channel
How to turn on two factor authentication on various platforms and channels
Explore new trends in 2-factor authentication globally
How EnableX can help you create secure login and transaction workflows using 2FA on new communication channels using Video, WhatsApp and Voice
Original Source
0 notes
Text
Cybersecurity: Follow 7 Best Practices to Protect Personal Data Now
Introduction:Recognizing the Need for Cybersecurity1. PasswordsUse Secure and Original PasswordsLength and ComplexityAvoid Using Personal InformationCreate a Unique Password for Each AccountPassword Manager2FA, or two-factor authentication2. Maintain Up-to-Date Software and EquipmentUpdates to the operating systemUpdates for web browsersAntivirus and security software updates3. Warning: Phishing…

View On WordPress
#best practices#cybersecurity#cybersecurity education#data backups#data privacy#online security#personal data protection#phishing attacks#secure Wi-Fi networks#software updates#strong passwords#two-factor authentication
0 notes
Text
Tech-Up Tuesday: Phishing 101 - How to Recognize and Avoid Email Scams
Welcome to Tech-Up Tuesday! 🎉 Today, we’re diving into the world of phishing and equipping you with the knowledge to recognize and avoid those sneaky email scams. But fear not, we won’t let these cyber tricksters get the best of us. Instead, we’ll tackle the topic with a humorous twist, using analogies and emojis to make it easy for even the most novice readers to understand. So, grab your…
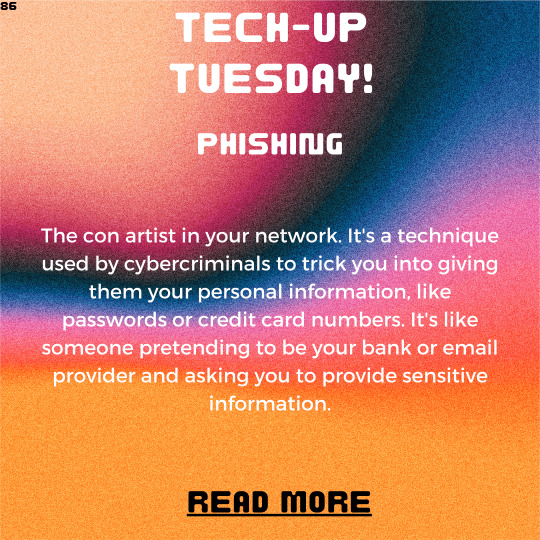
View On WordPress
#avoiding email scams#cyber anglers#email scams#online security#phishing#phishing prevention#recognizing phishing#social engineering#spoofed sender#two-factor authentication
0 notes
Text
#Data Protection Act#Privacy Online#Online Privacy#Personal Data Protection#Data Breaches#Privacy Rights#Online Security#Protecting Personal Information#Secure Browsing#Encryption#VPN#HTTPS#Strong Passwords#Two-Factor Authentication#Privacy Settings#Safe Online Communication
1 note
·
View note
Text
Social Media Security: Essential Tips to Safeguard Your Accounts from Hackers
Explore how to bolster your social media security! From unique passwords to two-factor authentication, learn to defend your digital identity. Check out this detailed guide. #OnlineSecurity #SocialMediaSecurity
The prominence of social media in our daily lives has paved the way for hackers to exploit vulnerabilities. The importance of social media security cannot be overstated in this era where our digital profiles serve as a reflection of our identities. I’d like to take you through some key strategies to safeguard your accounts from malicious cyber-attacks.
The Power of Strong and Unique Passwords
A…

View On WordPress
#Account Activity#Conscious Sharing#Email Security#Online Security#Phishing#social media#Strong Passwords#Third-Party Apps#Two-Factor Authentication
1 note
·
View note
Text
Passwords How Often Do You Change Them?
Passwords How Often Do You Change Them? Once every so often I think that we need simple password reminders. #kravis #security #passwords #midjourney
Passwords How Often Do You Change Them?
Passwords How Often Do You Change Them? Once every so often I think that we need simple password reminders. And, this posting is a gentle reminder of that and also some other ideas you might try if you have the time. The reminder could be for both work and home. 🙂 Because if you have a lot of passwords a good solution needs to be easy to use so you keep up…

View On WordPress
#cyberattacks#password manager#password security#Thoughts & Ideas#two-factor authentication#unique passwords
0 notes