#Encryption
Text
CONSEQUENCES OF THE EARN IT ACT
It will be functionally illegal to discuss sexual and GRSM issues
Opens the door to law enforcement monitoring Internet traffic, which means that more moderation will be legally enforced in the future, including censoring of other religions, ethnic groups, or speech against the EARN IT committee and its affiliated parties
US based companies such as Google may be forced to remove GRSM and other non-harmful sexual content from their search engine thus decreasing visibility by a significant amount
YouTube, owned by Alphabet Inc., parent company of Google, will also be forced to remove or terminate existing channels resulting in many well-known content creators being forced to cancel uploading entirely
A brief example would be Hazbin Hotel and Helluva Boss by Vivienne Medrano and Spindlehorse.
Simply mentioning or referencing any form of "sexual" content, no matter how tame, will be risking termination à la Disney
Many subreddits, from r/lgbt to r/femboy, and r/thelastofus to r/undertale, will be censored or removed completely under grounds of featuring GRSM characters
WhatsApp, owned by Meta, an American company, will now be forced to disable end-to-end encryption or backdoor communications for law enforcement.
Discord will be forced to remove NSFW channel functionality and messages will be scanned for illegal material.
Other non-social-media websites, such as CNN will be prevented from reporting on sexual abuse cases
And to top it all off, perhaps the most significant change will be the complete whitewashing of Wikipedia, which will be forced to remove many wiki pages of content documenting genuine SA case studies, information on safe sex, the biology of contraception and possibly even the anatomy of the human reproductive system.
#stop earn it act#anti earn it#earn it#earn it bill#stop internet censorship#fuck earn it#fuck internet censorship#pro encryption#encryption#pro privacy
158 notes
·
View notes
Text

I just made this poster to spread awareness!!
213 notes
·
View notes
Text
Why should you care about quantum computers?
Post #5 on Physics and Astronomy, 23/09/23
Welcome back. It’s been a while.
First, let’s backtrack. What even are quantum computers?
Today’s computers are run on bits. These are the smallest increment of data on a computer, and are run in binary–they can be in the state of either 0 or 1. This essentially corresponds to two values: off and on.
This, therefore, means that information can only remain in one, definite state.
So, what makes quantum computers so different?
A quantum computer is run on qubits (short for quantum bits). Qubits, instead of a single state, can remain in an arbitrary superposition of states (meaning it’s not in any specific state until it’s measured). Qubits, on their own, aren’t particularly useful. But it performs one, very useful, function: it can store a combination of all possible states of the qubit into one area. This means that complex problems can be represented differently in qubits compared to bits.
Quantum computers aren’t fully developed and at their full capacity quite yet. So far, there’s nothing a quantum computer can do that a regular supercomputer cannot. However, this opens an opportunity for some wonderful new things to happen.
One of these things can include the cracking of passwords.
Today’s encryption works by using “trapdoor” functions, which means that data is easy to compute in the forward direction, but extremely difficult to crack in the reverse without special keys. Keywords, ‘extremely difficult’; it is not impossible. However, this is not a massive concern: encryption works on the basis that it would simply take too long to crack.
To give you a tangible example, 100,003 and 131,071 are relatively easy to multiply together, giving you the answer 13,107,493,213. How easy, however, would it be to determine a prime factor pair of this number? It would take a computer a long time to figure this out, since it runs on bits, which can only show one definite state of data.
With quantum computers, it’s different. As aforementioned, qubits can remain in a superposition of states; somewhere in there, the desired answer lies. It’s just a matter of obtaining the resources to make this happen.
Don’t worry, though. Ordinary people aren’t at any risk quite yet.
#physics#astronomy#studyblr#astrophysics#stem#sixth form#mathematics#quantum physics#quantum computing#engineering#encryption#alevels
78 notes
·
View notes
Text
22 notes
·
View notes
Text
So, and correct me if I'm wrong, this is the only completely secure way to communicate over the internet:
1. Get a second computer which you will from now on never connect to the internet nor in any way allow to talk with any other computer, including flash drives, cables, Bluetooth, whatever.
2. Get it inside a Faraday cage that has an airlock type door so that you can always keep it closed.
This is because even of you rip out the antennas on a device, all modern motherboards have a backdoor which allows any government agents with proper equipment to compromise it via short range radio.
For good measure, get that computer its own power supply separate from the grid, to truly air gap it from the internet.
3. Anything which ever appears on any computer or phone can immediately be considered known to every security agency in the world, since all modern devices have backdoors put there for that reason.
Therefore, install on the other computer an encryption program(best if you make it yourself), whose resulting meaningless jumble of digits you by hand copy over to send to whoever needs it, presuming you gave them the key to decrypt it irl scribbled on a note or via the usual public private key method.
If any of this could be made simpler, please tell me, but I'm pretty sure that it can't.
50 notes
·
View notes
Text
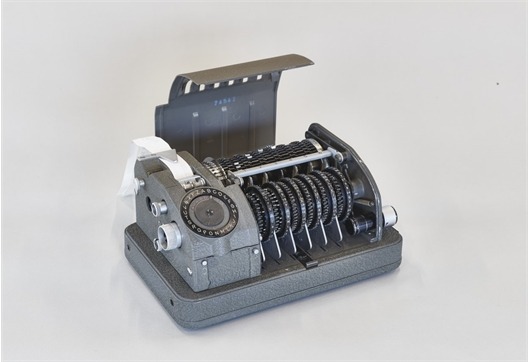
Encryption device called the Crypto CX-52, 1952.
31 notes
·
View notes
Text
Early church officials would send each other messages written on the corpses of recently dead parishioners, who would be buried under the recipient’s church to hide the evidence of seditious content. Oppressive Roman forces would be unable to read these messages once they were encrypted.
206 notes
·
View notes
Note
Hey you, the one with the 'cool thing you think about but don't get to talk about as much as you'd like to.' What is one thing you want to talk about, in as much detail as you'd like (I will read all of it).
Ok one thing that I really think is cool, hmmmmm
This happens every time I’m asked “what do you like” my brain just instantly vacates everything I do, it’s just like “Error 404: Life Experiences not found”
Hmmmmmm, I’d probably say ciphers/encryption
Ok so encryption and ciphers, simple in concept but holy hell does this shit get complex and fun fast
I first found out about them from the Secret Breakers book series (I love it, would definitely recommend), and then I went to a CTYI (Centre for Talented Youth Ireland) course and learned more about them and how they work, in between these two events I also did a load of research and got really hyper fixated on them, I then proceeded to learn more and begin creating my own and making my own little puzzles and stuff
Ok so encipherment and encryption both do a similar job, obfuscate a message to hide it, they were used in the World Wars to send messages to people in enemy lines on both sides (most notably the Enigma Machine), encryption often uses mathematics and numbers linked in certain ways to hide things, ciphers are a little different in the way they operate, ciphers are obfuscations but it’s easier to hide that they are obfuscations as they can often look like normal text
For example, the Baconian cipher uses something similar to binary and highlighted text to hide a message, so 00000 is A, 00001 is B, 00010 is C, so on, so where there is a one you highlight the letter
So to hide the word “hi” you need at least 10 letters, but less that 15, so “hello there” is our ten letters and hi translates to 00111 01000, so we highlight the letters specified, which gives us “hello there” (the baconian cipher was made by Sir Francis Bacon and he has many written letters with hidden messages in them, that’s all I can remember off the top of my head)
But using encryption (for example Base64) “hi” would become “aGk=“ which is much more obvious that it is a hidden message
I’ll explain how encryption is used in real life somewhat in a reblog later, I just want to get back to where I was as uI just accidentally deleted a huge chunk of what I had typed (as in I opened Google to check my spelling and tumblr decided it would be the perfect time to restart, I’m typing this on my phone)
Ok so onto the ciphers, the one that I really really like
So ciphers have been in use for millennia, I’ll start with a common enough one, The Polybius Square
The Polybius Square was created by an Ancient Greek scholar called Polybius(yeah he tried really hard when naming his cipher), the cipher is a simple enough substitution cipher (a substitution cipher is where certain letters or symbols are replaced by others things), where letters are replaced using 2 digits which mark there position on the square
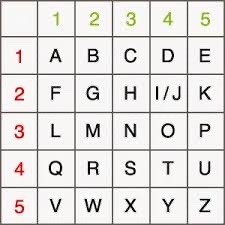
Which looks like this, it goes like this 11=A, 12=B, 13=C, 14=D, 15=E, 21=F, and so on, you’ll notice that in 24, instead of a single letter is both “i” and “j” simply for the reason that you can’t make a square out of 26 boxes
Early ciphers were often only used by themselves but later they were used together to make more complex ciphers whether this be where it was encoded once and then encoded again or that the two were used at the same time to do some funny shenanigans
A great example of this is the ADGFX cipher which uses a modified Polybius Square along with Columnar Transpostion
Ok I’ll explain the ADGFX cipher in just a second ima explain columnar transposition first, so with columnar transposition you need a key, we’ll use “cargo” (the general standard) so first take your message and split it into groups with the amount of characters in the group corresponding to the length of the key (So “we need to attack soon”, would be grouped into groups of 5 when using a key like cargo, the groups would look like this “wenee dtoat tacks oon”)
Next you align the groups under the key

Here is one using the example message of “we need to attack soon”
Ok next you need to take the letters in your key and arrange them alphabetically, so cargo become acgor, now take the columns you made and shift them along with the key letters

Like this
So now that we have our letters it’s easy, we take them from left to right, top to bottom and write them out, leaving us with, “eweentdatoatkscoon” with the key of cargo, now if most people were given that they wouldn’t have the slightest clue what to do
So now imagine if we added more layers, like in the ADGFX cipher
Long story short, you take a custom alphabet and replace the letters in a Polybius square with them, then replace the numbers in the square with ADGFX
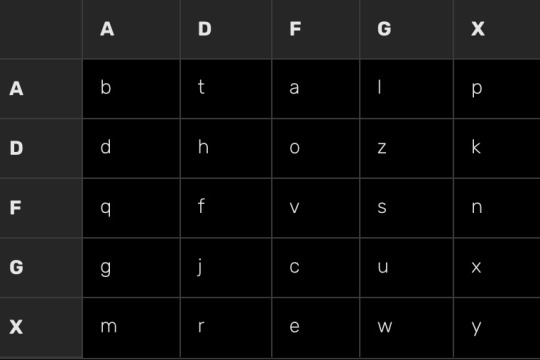
There is one that I stole from Google
So you encode your message using the square and then with the result you use the columnar transposition that we discussed earlier and then you have your final encoded message, unless you want to add more bullshit to it, like idk a A1Z26 cipher, changing the letters to numbers, or maybe a binary converter, or maybe a morse encoder, actually why not all of them
And that’s where shit starts getting fun (for me anyway, where you stack the jenga tower of encoding hoping that one of the ciphers in it doesn’t need numbers or spaces which other ciphers can’t use
Oh another fun thing, a number and text where you have to convert the number to binary and use that to highlight letters which are the encoded message, or are they
And that’s why I absolutely love encoding and ciphers so much because you can create such interesting little things that can become games, or just brand new ciphers where you have to spot little patterns or grab little ideas and run with them hoping that that was the way it works
Actually one last thing before I go, my own encipherment method which I couldn’t find anywhere online, and thus gave it a name
The Eclipsed Polybius Square (EPS)
Ok so the name comes from a name I used to go by (Which was Eclispe) and then the Polybius Square
Ok so I’ve written documentation of it countless times, but I can never explain it off the top of my head, I know how it works, it’s just stored in the depths of the blob of synapses that is in my skull
Ok so first step, take your message and use a Polybius square to turn it into the numbers,
I am struggling to figure out how to write this
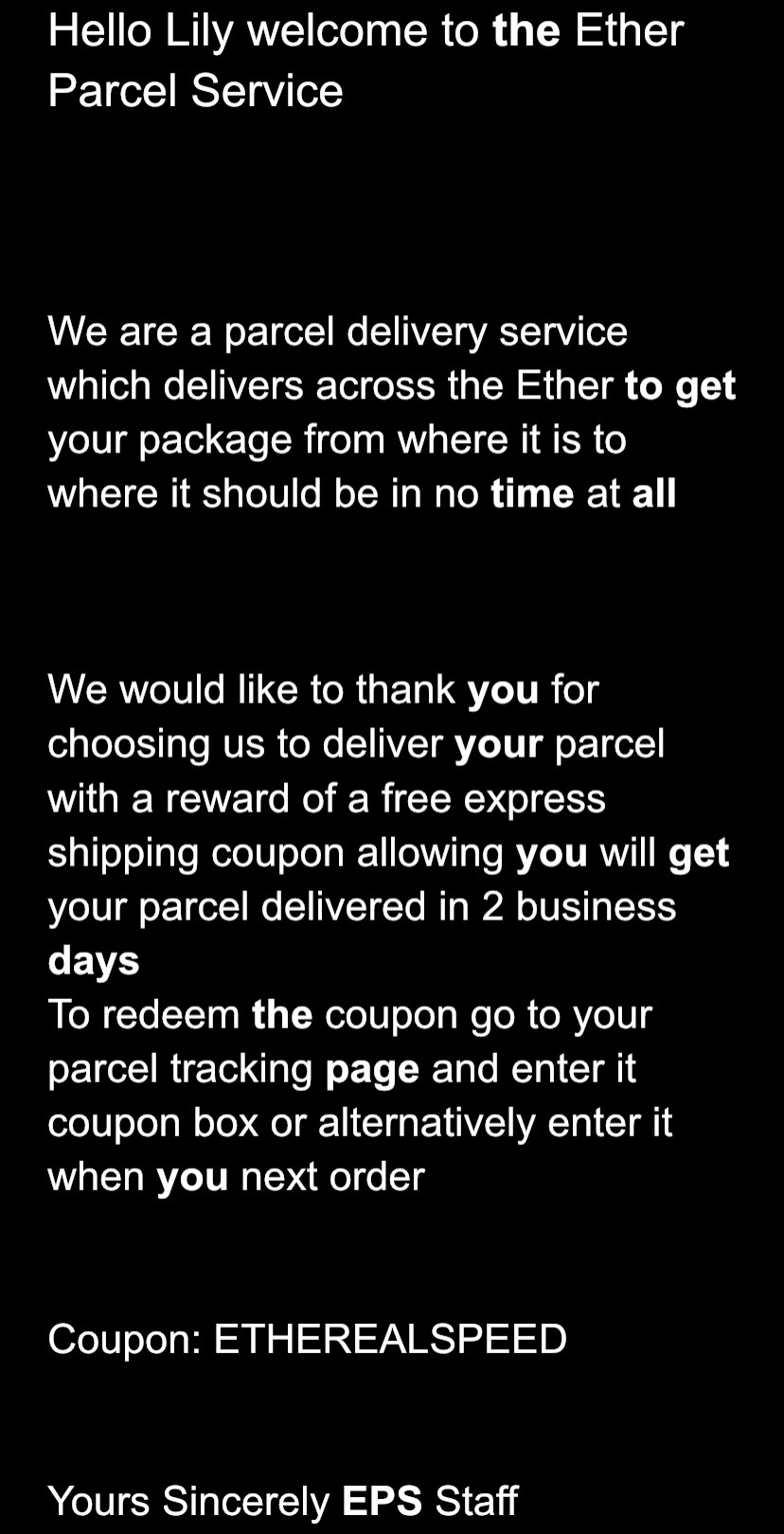
Here is an example which I used in an sort of puzzle hunt that I made for some friends (If you notice the name Lily there, it’s a character within the story of the puzzle hunt, game, thing)
Ok so see how some of the words are highlighted, they indicate numbers for the Polybius square
So “the” is in bold and it’s 3 letters long so we get the number 3, then “to” is in bold so we get 2, these two give us 32 which is our first letter “M”, then we have “get” which is 3, then “time” which is 4, now we have our next letter 34 which is “O”, and this continues to give us a whole word
You’re welcome to solve the rest if you want(send it to me if you do, whether that be in DMs or reblog)
Also just a note, when making the text which will hold the code, I’d recommend making the code first and then writing the text working around the code to get it in using as little words as possible, or you might end up like I did with all of the text there only giving 1 word
Actually actually, I have one last thing, thank you @rookieroc for asking, I have been dying to talk about this and so much more but I just haven’t found anyone to say it about
P.S. I will most likely add to this over time with reblogs with more information on different ciphers
#ciphers#puzzles#encryption#cryptography#god I love ciphers#again thank you @rookieroc for giving me the opportunity to share this knowledge#whadda ya mean it’s half past 2 in the morning#where tf did my time go
21 notes
·
View notes
Photo
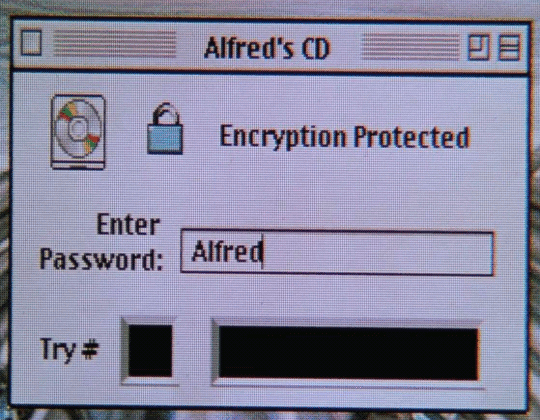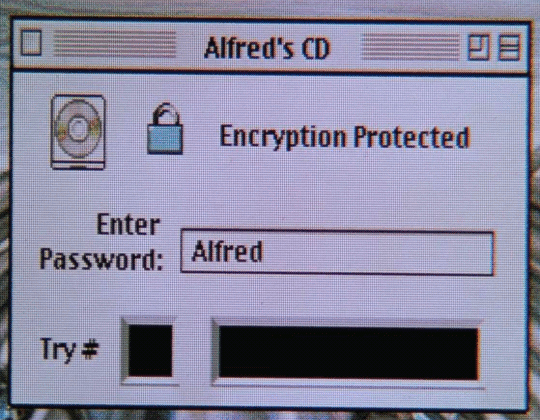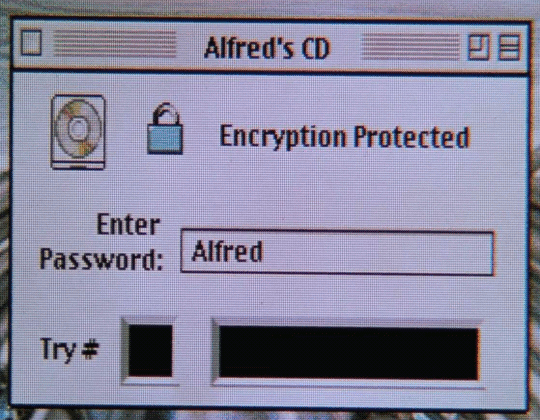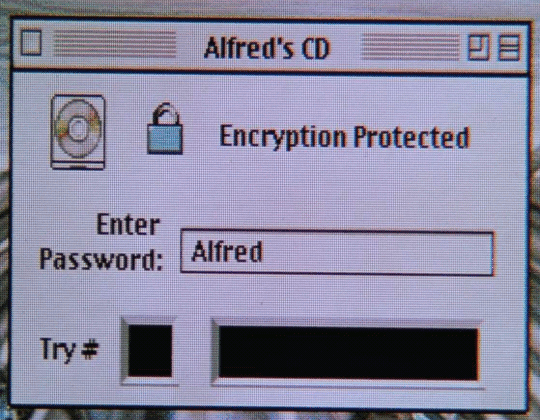
#batman & robin#retrocomputing#cd-rom#apple#macintosh#vhs#gif#1997#90s tech#encryption#alfred pennyworth
300 notes
·
View notes
Text

In an alphabet I made for a dnd game.
This corresponds to English. There are more than 26 letters but not many more than 26. No numbers appear in this text.
I’m honestly not sure how possible it is to decrypt without a partial key. But I’m willing to post additional text, draw anything ambiguous on a grid, etc.
38 notes
·
View notes
Text
I am currently coding a browser right now in pure Python. Let me explain all the steps it has taken at 300+ lines of code except in no particular order because I need to reorganize.
Fernet Encryption
SSL Certificate Check
Implementing a UI - Chose PyQt because its a prettier layout than Tkinter.
Implementing a toolbar for the UI
Implementing browsing history + browsing history tab + a clear button to clear the history - Done in the GUI / UI as well.
Adding a privacy browsing mechanism - routed through Tor
Added PyBlocker for Ad Blocking and Anti-Tracking on websites
Added a feature to make Google not track your searches because fuck you Google you nosey assholes.
Added a sandbox to avoid user getting infected with viruses
Added additional functionalities including optimization that way the browser wasn't slow as fuck:
Using JavaScript v 8 engine to load JavaScript
Using slight mem caching <100mb to avoid slowing the computer but also let the program browse quicker
Using one http request to send multiple http requests - need to set limit.
Encrypted global security features.
I am at over 300 lines of code. I am ready to pay someone to debug this shit when I am finished with it (lol)
May the force be with you my #Pythonistas
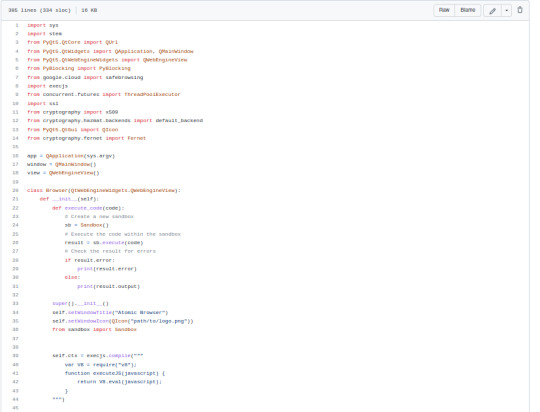
#Python3#pythoncode#coding#programming#programmer#javascript#encryption#cryptography#cybersecurity#internet security#internet#web browsers#web browser history#adblock#ux#ui#gui#development#software development#software developer#devlog#developer log
129 notes
·
View notes
Text

I think this is one of the dumbest things I have ever made and I am so pleased.
#bob and alice#cybersecurity#dumb memes#eclectic library#twitchstreamer#encryption#computercore#computer science#cryptography
7 notes
·
View notes
Text
Last night I dreamed that I had invented this file format, it wasn't entirely clear what it was actually for. It was text-based and divided into key-and-value pairs, where each line consistedof "(name): (value)". You then encypted the entire thing. The universe of Guilty Gear somehow merged with ours, or possibly a portal opened or whatever, and Justice was so impressed with this file format I'd invented, she tried to hook me up with Dizzy. This was sort of background narration as I was going around some building and a highway in a rural area.
While I was waking up, my half-asleep brain tried to actually come up with a fanfiction with this premise, though in practice it was just a bunch of unconnected momentary scenes and quickly went off the rails. My self-insert, as part of transition, gave herself the nickname "Dizzy" as an explicit reference to canon-Dizzy (just like my username), and things got awkward when we actually met. There was a bit where I got Venom and Zato-1 mixed up since Zato-1 is taken over by a monster-thingy (named Eddie, possibly as in Eddie Brock), and Venom corrected me. While learning to fight, possibly from Sol, I got bogged down trying to become an eldritch monstrosity -- "I wanna be able to summon and transform into dark mist which I can form into tentacles and objects, and I want to stop time, fly, and teleport! ... failing that, I want to use a polearm or staff of some sort" and then this turned into a whole backstory. I ended up sort of being a mom-friend to Bridget; when we faced off against oh-shit-it's-Actual-Justice-The-Command-Gear, I was just like "RUN!" and fled using with my eldritch powers, pulling myself along like Olivia Octavius and carrying Bridget along with like shadowy tendrils or whatever (evidently I didn't get the teleportation).
Happy anniversary of Bridget coming out!
#shenanigans#my dreams#dream diary#encryption#guilty gear#justice guilty gear#dizzy guilty gear#wlw#(I'm gay)#zato-1#zato-one#zato 1#zato one#venom#venom guilty gear#sol badguy#eldritch awesome#cryptid lesbians#(it's me! I'm the cryptid!)#bridget#bridget guilty gear#olivia octavius#trans stuff#my stuff#my writing#re: my stuff#dream inspiration
23 notes
·
View notes
Video
youtube
How Quantum Computers Break The Internet... Starting Now by Veritasium
50 notes
·
View notes
Text

Enigma M4 - Naval Edition
Seattle Living Computers: Museum + Labs (closed)
#WW2#German#Germany#Enigma#M4#Enigma M4#cryptography#encryption#OTP#secret#Naval Edition#Seattle Living Computer Museum#Seattle
6 notes
·
View notes
Text
Ephemeral usernames instead of phone numbers safeguard privacy — and makes Signal even harder to subpoena.
#anarchism #abolition #privacy
#anarchism#abolition#privacy#signal#infotech#it#i.t.#information technology#humanrights#telecommunications#communication#endtoendencryption#encryption#encrypted communication#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#antiauthoritarian#antinazi#antifaschistische aktion#antifascist#antifa#anarchist
2 notes
·
View notes