#nonidentify
Text
i hope that anyone here who is going the widespread protests that are happening later today have a safe travel, stay masked up (for covid and safety/identity reasons), and make sure to know what to do if you have to deal with police or get arrested/detained. pls wear nonidentifying clothing, leave your phone at home and get a burner phone if you can, and research for more tips for protests, and be safe 👍🏾🇵🇸
#it’s late here so idk anyone going will see this but good luck to y’all 💗💗💗#also pls don’t listen to ppl that are saying to not use your masks they are definitely the feds#🪐 speaking
140 notes
·
View notes
Text
someone in the tags of my tumblr post told me they like nonidentifiable centricide content so heres a treat for you
23 notes
·
View notes
Note
Do you have any advice for people wanting to help anonymously?
It depends on how anonymously you'd like to help! Some things like social media archiving is relatively anonymous and can be done privately in your home without others seeing.
To a certain extent, sharing content on social media can be anonymous if you have vpns and tor browsers and if your account is not associated with your real life persona.
Though if you're talking about in person help, I'd recommend wearing a mask that covers the features of your face (something like a KN95 for both covid reasons and privacy reasons), sunglasses that cover your eyes, and a Kuffiyeh or other type of head+neck wrap. Of course you'd also need to wear nonidentifiable clothing and leave your phone at home. People who are security experts might have more to talk about electronics and their use in anonymous work like this though.
You might also be a connector of sorts — like you know a guy who knows a guy who is directly in touch with the president of your organization and they've yet to make a statement. You could connect someone (like an activist in your area) and ask them to talk to this specific person that you kinda know.
Other than that, I'm not sure what else. If anyone else has any ideas or experience, feel free to let us know! Thanks for sending this in.
21 notes
·
View notes
Text
damn dis last chat got me
It wasn't even a suicide chat, it was someone that--well I gotta be vague as all hell for nonidentifying, but a guy with a family that wanted help with an addiction, and I truly feel like I made a difference tonight for the first time. One two hour chat later. Some of his reasons for motivations just. Good guy, bad situation, I think he'll be okay, he was on the verbal phone with a therapist with an assigned support person before our chat was done, even if I had to sort of point his nose at the number a few times.
Now I can take my first break.

8 notes
·
View notes
Note
hello i have no idea how to say this without feeling like im coming off incredibly conceited (so im on anon for now) but. a while ago i wrote a fic that i think you would maybe probably enjoy? its a psychological torture-y body horror-y semi-character-study longfic thats essentially just jay getting physically and emotionally more fucked up in kind of a villain arc way but not really a Villain? lots of violence etc and some of your jay whump drawings were kind of a big insp while i was writing it ahaha!! so i thought maybe youd be interested - that said tho feel free to ignore this ask!!!! i realise promoing myself in your inbox is a bit cheeky i just genuinely thought the themes were up your alley so if you are interested lmk i can link you but no worries if not B) also love your work!! the way you write (and draw) whump is incredibly tasty it scrambles my brain ok bye
hmhmm i would say i am interested in such elements. but i have to be upfront and honest here. i am VERY VERY critical about fanfiction. i love fanfiction but bc i love fanfiction i am also very. picky. i developed a refined taste over the years. not that im saying that i assume your fic isnt good, its just that. are you okay with running the risk of me not liking it by sharing it with me? are you open to (honest but fair) criticism? i dont want you to have expectations for my reaction. and also i dont want to give unwarranted criticism either, i dont want to be mean or hurtful. i just. cant lie about fic. so if i dont have high praise for a fic i keep it mostly to myself. well i do vague a lot about fanfic on twitter. but i try to keep it nonidentifying if it isnt positive.
anyways thats not the point. if i havent inadvertently scared you off and you are emotionally prepared for any reaction (or even no reaction), you may send it to me. i can only promise that i will judge it fairly. if you okay with constructive criticism i can give it too. but i get it if you dont want that. if you just want me to read it just for the sake of reading it i can do that too
#and also. to be 100% honestly anon. i may know what fic it is. i went on a deep dive through jays tag and opened a lot of fics. a lot.#like i read a LOT of ninjago fics but theres more i havent read yet im certain i have 200 ninjago fics open on my phone. still.#i have a low attention span#sorry for the long answer i just wanted to like.... set expectations. or rather get rid of any expectation you have of me#......... i love fanfiction.... but like. watch out.#asks#anonymous
8 notes
·
View notes
Text
A Thunderhead High-Altitude Balloon System, launched by U.S. Army Pacific Soldiers, takes flight during Balikatan 22 on Fort Magsaysay, Nueva Ecija, Philippines, in April. Balikatan is an annual exercise between the Armed Forces of the Philippines and U.S. military designed to strengthen bilateral interoperability, capabilities, trust, and cooperation built over decades of shared experiences. Credit: Spc. Darbi Colson/DVIDS

Blockchain-backed, open standard-based decentralized identity (aka self-sovereign identity) technologies can provide warfighters with combat identification (CID) of the networked digital forces that comprise the modern military’s multidomain sensor-to-shooter kill chains.
High confidence in the digital identity and capabilities of every networked kill-chain participant (i.e., digital CID) is required before military decision-makers will trust collapsing information stovepipes, automating high-value decision making and separating command from control to the degree needed to significantly accelerate the “sense, make sense and act” command and control (C2) functions needed to act inside an adversary’s decision cycle.
The problem: uncertainty in the identity and capabilities of each entity communicating from behind its networked Internet Protocol (IP) address hinders information sharing and automation in the “sense, make sense and act” C2 functions.
Per the March 2022 U.S. Department of Defense Summary of the Joint All-Domain Command and Control (JADC2) Strategy, warfighting is becoming more and more digitalized to “use increasing volumes of data, employ automation and AI [artificial intelligence], rely upon a secure and resilient infrastructure, and act inside an adversary’s decision cycle.” The JADC2 vision for joint warfighting is an Internet of Things connecting digitalized sensors-to-shooters “to sense, make sense, and act at all levels and phases of war, across all domains, and with partners, to deliver information advantage at the speed of relevance.” These digitalized sensors, shooters and their directing C2 work together in coordinated kill chains to put weapons on target with maximal effect and minimal collateral damage. Because the targeting information they originate and exchange results in literal life-or-death outcomes, every participant in the kill chain and their information must be trustworthy and reliable to a high degree of certainty.
Identification is the root of all trust because it provides accountability. Unidentified, misidentified or compromised digital forces participating in a kill chain jeopardize the trustworthiness of the targeting information and the reliability of execution. Online digital identification and authentication in the battlespace is a form of CID, which is generally recognized as the “process of attaining an accurate characterization of detected objects throughout the operational environment sufficient to support engagement decisions.” CID traditionally applies to positive identification of targets and nearby friendlies and neutrals to avoid fratricide and minimize total casualties. But in digitalized kill chains, positive identification and verification of the identity, capabilities and information provided by the digital participants are needed to prevent or detect inadvertent or purposeful targeting misinformation and execution mishandling that could result in unintended outcomes.
But trustworthy network digital identification has historically been difficult, especially at scale, because online entities communicate from behind nonidentifying IP addresses. And herein lies the problem for JADC2. Battlespace commanders, planners and operating forces communicating electronically with each other in a contested battlespace environment feel too uncertain in the digital identities and capabilities of in-area networked forces (people, organizations and things) to trust them with the degree of independent decision making, ad hoc information exchanges and artificial intelligence-based automation that would significantly shorten the kill chain.
They rightly question the trustworthiness of digital identities because networked devices and their hosted applications:
Are not largely public key enabled at the application layer and instead rely on the encrypted transport layer for security.
Rely heavily on third-party identity providers, directories and boundary security enforcement points outside the control of the device owner and its applications.
Communicate with each other via complex network routes spanning multiple connection points and protocols. The application layer payloads exchanged are typically not encrypted end-to-end across all these route segments, thus making them vulnerable to man-in-the-middle attacks and manipulation.
Exchange no cryptographically verifiable identifying and nonidentifying claims/credentials issued by trusted authorities that assert identifying attributes and capabilities.
Trustworthy CID of networked forces will only get harder as the number and type of digital forces explode due to the ongoing military digitalization of traditional forces and the growing deployment of autonomous vehicles and other types of attritable Internet of Things devices. These small, low-cost, attritable devices and other types of digital forces require a commensurately small, low-cost, assured identity solution that is open, standards-based, interoperable, de-centrally implemented and administered to affordably secure the internet-scale networked battlespace.
The blockchain-enabled CID solution
Distributed ledger technology (aka blockchain) solves the digital identity problem by providing a scalable, decentralized, low-cost, highly secure way to cryptographically bind an entity’s identifier to its private and public key pair while also distributing it widely and securely. In a blockchain-based digital identity solution, the immutable hash of the chained blocks of transactions stored on the ledger immutably binds a new kind of globally unique, unchanging digital identifier (W3C decentralized identifiers or DIDs) to its public key. The blockchain consensus mechanism ensures that each distributed ledger in the blockchain network independently writes the bound identifier/public keys on its ledger. Therefore, an entity’s DID and cryptographically bound public key are automatically and immutably distributed across all physically disparate and independently operated nodes of a distributed blockchain network. To verify an identity’s digital signature, a relying party looks up the subject’s DID on a local blockchain ledger node and retrieves the immutably bound public key.
After this seminal use-case for blockchain technology was recognized, several open-source organizations emerged to develop an overall Trust over IP architecture framework and the supporting open standards and implementations. The resultant highly secure digital identity solution became known as self-sovereign identity, decentralized identity and decentralized public key infrastructure.
In deployment, these standards and technologies take the form of small footprint software agents and secure digital wallets installed on each participating networked device. Software agents and secure digital wallets use standardized protocols and cryptography to automate assured CID. The agents of any communicating digital forces automatically establish a secure channel (exchange pair-wise public keys) and then use the encrypted channel to exchange cryptographically verifiable claims about their identities, capabilities and data via small, lightweight, machine-readable, schema-defined, digitally signed verifiable credentials. The verifiable credentials are issued to digital forces (representing people, organization and thing entities) by recognized authoritative trustworthy issuers registered on a blockchain ledger. Verifiers of a verifiable credential look up the issuer’s DID on the blockchain, retrieve the associated public key and confirm the issuer’s digital signature on the verifiable credential.
CID is performed by the agents when they validate the signatures of exchanged verifiable credentials and use the attributes to perform mutual identification, authentication and authorization. Once trusted CID is complete, the devices use the established trusted relationship to perform various use cases.
For example, a sensor device passes collected images to its controller over some complex multi-hop route. Because the sensor and its controller hold each other’s relationship-specific identifier bound to its public key, the sensor data and the controller’s acknowledgments are all digitally signed and encrypted end-to-end between the devices, independent of any transport-layer encryption. The receiving controller has high assurance that the image data came from the trusted sensor and hadn’t been tampered with. The sensor has high assurance that the trusted controller really received it.
The sensor could also hold in its wallet nonidentifying types of verifiable credentials asserting various claims about the sensor itself—the manufacturer-certified resolution of a camera, for example. In this way, the controller could make better decisions about how best to employ that sensor. For example, if the camera only took wide-angle images, the controller wouldn’t try to assign it a collection task requiring a zoom capability.
2 notes
·
View notes
Text
Test Gauge with UL498 Figure 111.1
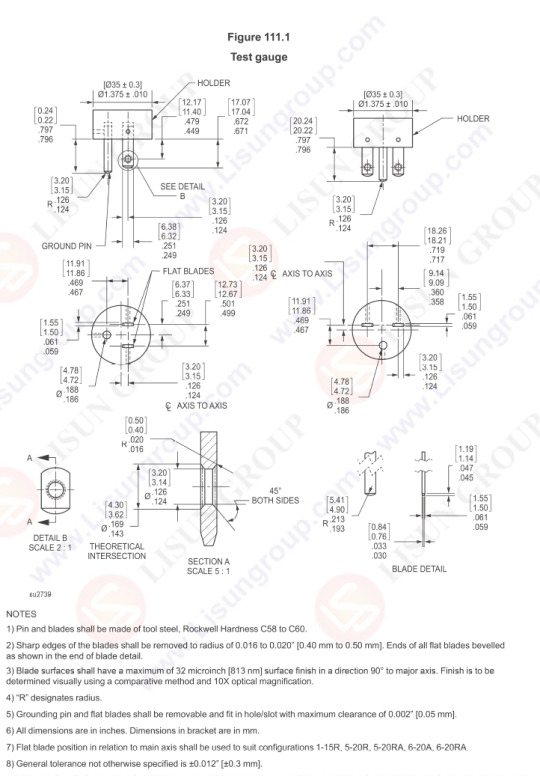
Retention of Blades Test
A flush or self-contained receptacle having a 5-15R,5-20R,6-15R, or 6-20R configuration shall be subjected to the retention of blades test described in this Section.
Exception: A receptacle having a 1-15R,5-15R,5-20R,6-15R, or 6-20R configuration and not of the flush or self-contained type may instead be subjected to the Retention of Plugs Test, Section 116.
Receptacles having the break-off tab, when provided, removed from one nonidentified terminal are to be subjected to ten conditioning cycles of manual insertion and withdrawal of a standard test gauge, see Figure 111.1. Each of six devices is to be tested. The gauge is to be configured as outlined in Table 111.1. The force applied to insert the gauge for any of the conditioning cycles is not to exceed 40 lbf (178 N). The gauge is to have the dimensions indicated in Figure 111.1 but is not to have holes in the outer ends of the blades.
Test Gauge with UL498 Figure 111.1
The standard test gauge is to be configured as shown in Table 111.2 using the line blades without holes and with the grounding blade removed. The gauge is then to be inserted in the receptacle and a static 3 lbf (13.3 N) (including the weight of the gauge), which tends to remove the gauge from the receptacle, is to be applied for a period of 1 minute in a direction normal to the plane of the face of the receptacle. There shall not be more than 0.079 inch (2 mm) displacement of the gauge.
The standard gauge is to be configured as shown in Table 111.3 using the line blades with holes in the end and with the grounding blade in place. The test is to be conducted using the apparatus as described in Figure111.1A. The test gauge is attached to the apparatus as shown. The apparatus consists of a principal mass, and a supplementary mass. The supplementary mass is 1.5 lbs (6.7 N). The principal mass, together with the supplementary mass, the Gage and any hardware equals 15 lbs (67 N) total. The gage is inserted fully into the device.
The principal mass and associated hardware is hung on the gage without jolting. The gage shall not remain in the receptacle. If the gage does not withdraw the supplementary mass is raised and allowed to fall from a height of 2 in (51 mm) onto the principal mass one time. The gage shall not remain in the receptacle. A test apparatus that does not incorporate a supplementary mass and equals the 15 lbs (67 N) total is permitted if agreeable to all parties.
Lisun Instruments Limited was found by LISUN GROUP in 2003. LISUN quality system has been strictly certified by ISO9001:2015. As a CIE Membership, LISUN products are designed based on CIE, IEC and other international or national standards. All products passed CE certificate and authenticated by the third party lab.
Our main products are Goniophotometer, Integrating Sphere, Spectroradiometer, Surge Generator, ESD Simulator Guns, EMI Receiver, EMC Test Equipment, Electrical Safety Tester, Environmental Chamber, Temperature Chamber, Climate Chamber, Thermal Chamber, Salt Spray Test, Dust Test Chamber, Waterproof Test, RoHS Test (EDXRF), Glow Wire Test and Needle Flame Test.
Please feel free to contact us if you need any support.
Tech Dep: [email protected], Cell/WhatsApp:+8615317907381
Sales Dep: [email protected], Cell/WhatsApp:+8618117273997
Read the full article
0 notes
Note
I used to have an imagine reference sheet for just about every character that I wanted to play, but I deleted them all once rules started to get stricter and actually enforced. To my knowledge I don't believe any of them were too bad, but I've been so afraid that one of them might break a rule and get me banned that I just don't bother with them at all.
bad take, anon. the rules are pretty straightforward. let me break them down for you.
no underage images (self explanatory, no loli or shota)
no real people (this is any image of a real person at all, including nonidentifying photos like you'd use for an aesthetic/mood board or public figures)
the only exception to the real people rule is that if no part of the real person is distinguishable (a power ranger suit, deadpool, spiderman suit)
if the images in your reference photos are nsfw in any way, you have to be in nsfw
hope this helps!
0 notes
Text
USA: 32 transgender people have been murdered in 2022
USA: 32 transgender people have been murdered in 2022
FILE – A protester holds up a sign at a march for the rights of transgender people in Lisbon on March 31, 2022. (AP Photo/Armando Franca)
PA
At least 32 transgender and gender-nonidentifying people have been killed in the United States so far in 2022, the Human Rights Campaign announced Wednesday in its annual report.
Non-white transgender people account for 81% of known victims this year and…
View On WordPress
0 notes
Note
absolutely not, i have standards. i'm just wondering how you made your way from corinthian to an arts and crafts project. a ball of yarn
if you wanna get technical. i’d say he falls under venom category bc it’s a man dressed up in a nonidentifiable sort of suit. so.
1 note
·
View note
Text

The RAIN acronym is an ancient Buddhist mindfulness tool to cope with hardship. When life throws you a curve ball -- a weighty life decision, a problem at work or even a moment of anxiety that you can't put your finger on -- how do you react?
RECOGNIZE
ALLOW
INVESTIGATE
NON-IDENTIFY
R stands for recognizing what is happening in this moment. Someone just walked too close to you on the sidewalk or didn’t give you what you feel is your “right of way,” and boom, you’re angry. The “R” is simply to notice what is happening, to be present enough to know that something is happening. This is not a small thing. Many people are immediately reactive—and worse, they blame the other person for causing their reaction. The point is to be awake, to pay attention.
A stands for accepting. This does not mean that you wanted what just happened to happen. It simply means that you acknowledge that it did. You name it: for example, “anger is here.” The idea is that although you are not going to indulge the emotion or thought with further thinking or righteousness or another emotion, neither do you resist or avert or distract yourself from what’s happening. You simply acknowledge and name what is happening. You are willing to be open to whatever it is.
I stands for investigating the sensations in the body. This step is primarily a physical noticing. What does anger feel like? The heart beats faster, there can be a flush of energy and heat and a tightening of certain muscles. These physical events are what we label as “anger.” This energetic emotional component has to be willingly and thoroughly felt until the body returns to open relaxation. You breathe and wait and breathe and feel the body, at first tight and then slowly changing, relaxing and opening, letting go. If this is not thoroughly done, then we haven’t really felt the emotion that was triggered by the initial thought, and that energy gets stuck in the body and adds to the conditioned structure that was triggered in the first place. This openness to the physical event is what integrates the energy, dissipates it, and—if it is practiced over and over— eventually dissolves that particular egoic structure, which has no concrete core. The realization that the egoic system will eventually dissolve if we don’t add more thought or energy to it is a wonderful one when first experienced, and a real taste of the potential freedom to come if we continue with practice.
N stands for not identifying. There’s no need to identify a “me’” in what just happened. It was just a passing mental and emotional event, like watching a scene in a movie or the clouds as they move through the sky. We don’t have to build and rebuild a “me” on the passing content of the body-mind. Instead, we can stand as the observer. This not-identifying is tricky, but when the first change of identity shifts from the content of mind to the observer, we can see that the content is not who we are. This is the first real shift of freedom. Eventually identification as “the observer” drops away as well, but to simply make the shift is a good place to start.
#Buddhism#mindfulness#rain acronym#life#mind#thoughts#emotjins#western Buddhist#the middle way#the path#rain#recognize#allow#investigate#nurture#nonidentify
252 notes
·
View notes
Photo


Praying the quality isn’t too damaged -
#Ravio#Link#Nintendo#Fan Art#RavioLi#3rd times a charm hopefully#Art#Ravio x Link#Nonidentified Link or Ravio
22 notes
·
View notes
Note
Im in love with Your blog
Thanks. You’re sweet.
1 note
·
View note
Note
What?! Everyone is giving love to Lan, without me?!?! This is an unacceptable condition!!🍋!!!🍋! To Lan: 💕💞💟🧡❣️💛❣️💛💛💜❤️🖤❤️💝💓💘💋💙💓💜❤️💜💞💙💓❣️💘💛💌💙💋💙💛💜💛💜❤️🖤❣️❤️💝💋❣️💋💙💙💞💟💛💌💋💟💟🧡💟❤️💙💓❣️💞❣️💟💓💟💓💙💜💓💜💓

*NONIDENTIFIABLE NOISES* SVBJKBWKFHWEUGKJCSJ twank you… ;w;
12 notes
·
View notes
Note
(bf/gf person again) really tho like... i just want u to know that u definitely arent alone in the whole 'what even is gender lmao but also help???' thing, and that for sure it can work out super well relationship wise so long as u nd ur partner communicate about it. in the end gender is something super personal nd only u can define how u view yourself in relation to the gender binary, whether ur fluid, nonidentifying, or anything else. nobody else can make that decision for u. good luck love!!
yeah, i feel like it doesnt matter, but also it does matter?? anyway i hate my brain im annoyed. thank you so much darling!!
3 notes
·
View notes
Text
How To Fix ?m=1 In Blogger Mobile version Url
In Mobile version of Blogger ?m=1 Is a Official Sub Domain and It Is A Identification system To Verify Blogger Domain or Not. We Can't Remove ?m=1 from url Because it is a Defalt from Blogger.But we can redirect this ?m=1 into only domain. To make Your website Url nonidentifyed Follow our Steps.
DOWNLOAD CODE
INSTALL WITH FULL TOTURIAL
CONTINUE READING
#blogging #solution #blogging problems
0 notes