#hide ip address
Text
IP Address
The internet protocol address (IP address) is a numerical identifier that links a computer or computer network to the internet. The IP address allows computers to send and receive data when they are linked to the internet. An IP address is made up.....
(more…)

View On WordPress
#can ip address be hack#cyber forensic notes#Forensic science#forensic science notes#how is an ip address work#how to protect and hide ip addresses#ip address#type of ip address#what is ip address#what is proxy server#what is the need of ip address#what is the type of ip address#what is vpn
3 notes
·
View notes
Text
Just got my grade back for my Big Damn Final Project that I procrastinated and then rushed through in 2 days because I was already guaranteed a solid grade, and I somehow got 99%. Sometimes the universe just gifts you with undeserved fortune, so never give up
#original#i lost 1% because i forgot to say that a reason behind using a proxy server is to hide the internal ip addresses#apparently everything else was fine and good??? unbelievable
0 notes
Text
Threads
Trying it out but honestly? I think it might actually stick ngl. Its more than likely cuz its owned by Instagram and a lot more brands that are already on twt will be on there and give insta more profit me thinks.
Plus if you don't want threads you can fr just not download it so thats good!!!
Okay edit:
Zuck gotta work on threads cuz it shows random accs 😭 it did just come out tho so
#dali talk#and its cool that you dont have to fully start over#like your friends can automatically follow you and when you join the app you automatically follow your friends#and you can hide likes! thats neat#plus insta's blocking feature is amazing since it blocks all accs made by the ip address
0 notes
Text
I know we all love Firefox but reminder that incognito mode does not hide your IP address. It just blocks trackers. If you use incognito mode to, say, reserve 100 seats at a fascist event without any intention of showing up: the fash now probably have your IP address. If you put protest reports on social media: the feds now have your IP address. Etc.
To actually go incognito, use TOR or VPN or Tails. To make your social media account actually incognito: never log in without TOR or VPN or Tails and never link it to other social media accounts of email addresses that are not incognito.
(& always assume that your identity can still leak. No shield is foolproof. If being found out could mean getting arrested: do not put it online at all.)
16K notes
·
View notes
Text
sooo my theory abt blind is that sung joon has an alter and the juror in glasses is working with him
#im not expecting anything less ridiculous than this algnalh#childhood trauma.. dissociative identity disorder#wasn't the juror guy a computer engineer or smth#no problems with hiding an ip address#why did he drug sung joon at the end of ep 8? bc yoon jae told him to#insert image or me with my conspiracy wall#perhaps im just thinking abt bad an crazy algkslh#i hope they're more original with the plot than what i can imagine
1 note
·
View note
Text
Does hotspot shield hide my ip address

Does hotspot shield hide my ip address full#
Does hotspot shield hide my ip address free#
Note that and IPVanish are owned by J2 Global, which in turn owns PCMag's publisher Ziff Media. You can connect as many devices as you like with Avira Phantom VPN, VPN, Ghostery Midnight, IPVanish VPN, Surfshark VPN, and Windscribe VPN. Other VPNs, however, have abandoned this model and are allowing an unlimited number of simultaneous connections. Kaspersky follows suit, which is great considering the price. Most VPN services offer five licenses with a subscription, meaning you can secure up to five devices.
Does hotspot shield hide my ip address free#
For all that, I'd expect better than just a free version. That's disappointing, especially considering that these suites cost $79.99 and $89.99 per year, respectively. While the free version of Secure connection is available in both the Kaspersky Internet Security entry-level suite and the Kaspersky Total Security mega-suite, you still have to live with the 200MB-per-day limitation. You might expect that purchasing another Kaspersky product might net you a cheaper VPN plan. ProtonVPN has by far the best free subscription option, in that it places no limit on the amount of data you can use. That's more generous than TunnelBear's 500MB per month limit, but less than half of Hotspot Shield's 500MB per day limit. Kaspersky Secure Connection also has a free option, which limits users to 200MB per day, and won't let you select a VPN server-it makes that choice for you. Of course, cost doesn't need to be an obstacle when there are so many excellent free VPNs available. If it does, then spring for the longer plans. Instead, use a free plan or short-term subscription to test that the VPN will work with all the sites and apps you need. While you will definitely save money with any VPN's annual plan, I strongly advise against signing up with a long-term plan initially. There doesn't appear to be any hidden price hikes. On the pricing page for Kaspersky Secure Connection, I noticed language that implied that the $29.99 annual price is merely "introductory." A company representative clarified that if you sign up at that price, you can renew at that price as well. In fact, it's the lowest annual fee of any VPN we've yet reviewed. That's significantly less than the annual average of $71.87 per year.
Does hotspot shield hide my ip address full#
More impressive is its annual plan, which costs $29.99 for a full year. Kaspersky has the distinction of being tied with FrootVPN for the lowest monthly paid subscription I've seen, beating out even Mullvad's flat €5 ($5.92 at the time of writing) per month fee. Paid subscriptions to Kaspersky Secure Connection start at $4.99 per month, which is well below the industry average of $10.21 per month. That means Secure Connection uses the server infrastructure of Hotspot Shield, but offers a different set of features, a branded interface, and different pricing. Kaspersky Secure Connection VPN is a licensed version of Hotspot Shield. How Much Does Kaspersky Secure Connection Cost?

0 notes
Text
How to hide my ip address

#How to hide my ip address how to
#How to hide my ip address code
For example, at limeproxies, you can get a set of proxies that you can connect to for an affordable price.Īs such, once you have purchased a plan, you can choose a specific proxy from the given list and then change your proxy settings on your PC from the Settings menu.įor those who are on Chrome, you will need to go to Settings -> Advanced Settings -> Change Proxy Settings. So how can you actually connect to a proxy? Various services offer a number of proxies. Hence, you are assigned the IP of the proxy rather than of the server. A proxy acts as a middleman between your computer and the server that you connect to. One of the easiest and most popular ways is to use a proxy server.Ī number of proxy servers exist that can be found over the web for free. There are a number of ways in which you can hide this address and make yourself anonymous. Your IP address also allows companies to monitor your web surfing activities for marketing purposes. Just like your home address, your IP address can be used by the respective ISP or regulatory agencies to track you down.
#How to hide my ip address code
How to hide your Public IP Address?īefore going into any details, it is worth considering as to what IP really is? IP Address or Internet Protocol Address, is a unique code assigned to you by your Internet Service Provider (ISP) when you connect to the internet. Here you will find how you can hide your IP and will also learn the many reasons for doing so.
#How to hide my ip address how to
However, many of us may not know how to safely hide our IP addresses. Hiding an IP is not uncommon among internet users and is something that is being done by a vast majority. Let’s say I am one of those people who does not know how to hide my IP address and yet want to do so for a number of different reasons.

0 notes
Text
Hide my ip address free iphone

#HIDE MY IP ADDRESS FREE IPHONE HOW TO#
#HIDE MY IP ADDRESS FREE IPHONE CODE#
My IP, yours, everyone's will be using this protocol. In other cases, IPv6 actually accomplishes tasks in a superior way to IPv4, so we have to wait for those methods to become more mainstream. Another option is to use a virtual private. Just set up your VPN, and as soon as you connect to a server, your IP address will be masked with an alternate one to prevent websites and other third parties from identifying you or knowing your location. One way is to use a proxy server, which can mask your IP address and make it look like youre located somewhere else. The process of using a VPN to hide your IP is pretty straightforward.
#HIDE MY IP ADDRESS FREE IPHONE HOW TO#
In some cases, computer scientists are working on ways to make the new protocol handle the same services as the old one. How to Change Your IP Address with a VPN. Hide Ip Address Free Mac Freeware Quick Hide IP v.1.3.0 Quick Hide IP is a small application that can hide your internet identity so you can surf the web safely. In its current form, IPv6 also can't do a lot of what IPv4 can.
#HIDE MY IP ADDRESS FREE IPHONE CODE#
Also, this is the fundamental code of the most powerful communication tool ever created: they have to be careful that there are no bugs or the results could be catastrophic. Like an enormous ship, it can't turn on a dime, so even though IPv6 was invented in 1994, it will take a long time to implement it. The first is that the Internet is huge and very important. This method allows up to 340 undecillion addresses to be used at once. It uses a 128-bit, alphanumeric scheme to address devices online. IPv6 is a major improvement on IPv4 and more forward looking. But we are rapidly approaching a point where more than 4 billion devices might access the Internet at once, and all of them need an IP. In fact 94% of Internet traffic uses IPv4 to track the location of devices online. When this was created, scientists didn't think we would need more than the approximately 4 billion permutations that that sort of scheme allows, and it's lasted quite some time. For an overview of the feature, see Create unique, random email addresses with Hide My Email and iCloud+. You can access Hide My Email on your iPhone, iPad, iPod touch, and Mac, and on if you or someone in your Family Sharing group has an iCloud+ subscription. It applies to both public and private connections. Set up and use Hide My Email in iCloud+ on all your devices. IPv4 is the first deployed version of the Internet Protocol and uses a 32-bit address scheme that generally looks like this: 192.168.1.1. When the Internet was first conceived, nobody could have guessed how popular it would be, or what an important part of our lives it would become.

0 notes
Text
On March 15th, 2024 at 9pm EST, Wayneradiotv started streaming, "A Difficult Game About Climbing." Early in the stream, Wayne mentions Maroon 5 and Justin Timberlake (JT), incorrectly remembering whether JT was apart of Maroon 5 or not.
Justin Timberlake was never apart of Maroon 5.
Wayne learns this fact through a Justin Timberlake fandom wiki page on Maroon 5, he edited the page to add "Justin Timberlake was in it at some point."
This edit caused over 740 edits to be made to the Maroon 5 page, as well as several edits to other pages on the JT Wiki. The edits were mentions of the stream, and devolved into: An Anonymous user (or users) claiming that Justin Timberlake is their dad, Young Mokey overtaking the page (Young Sheldon and The Big Bang Theory make appearances too), as well as... a gorilla.
Over the course of the 7 hour stream, I took screen shots of all of the changes that I could catch (again, over 700 of them and I only caught a large amount). The Anti-Vandalism Warriors fought valiantly until the end, eventually coming to a truce with the Young Mokey Brigade. One of the A-V Warriors is @rotgutinc, I salute your efforts, as they were not in vain.
As of March 16th, 2024, 9:01 AM UTC (4:01 AM EST), the Maroon 5 page is protected, and all pages were reverted to their original state. Picture edited to hide all the IP addresses. Highlighted in yellow are the pages affected (and subsequently changed back). Pages were deleted and highlighted in blue is the Protection Log. Here is a link of all the screenshots I took that night.
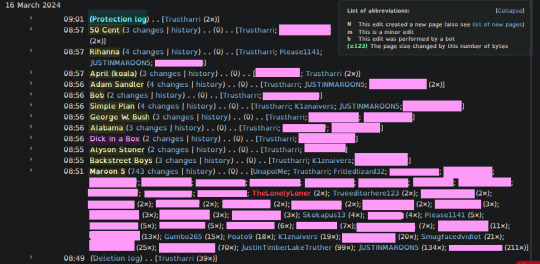
Tl;Dr: Wayne suffered a Sisyphean curse while a Fandom Wiki for Justin Timberlake was ravaged in the wake of his misremembering JT as a member of Maroon 5.
474 notes
·
View notes
Text
Reformatting
(Some people can't afford my Amazon stories, and some can't get them in their home country, so here's a fun little freebie. I hope you like it! *giggle*)
Lilah had been battling with this system for over an hour. Some executive had downloaded a virus on their laptop and it kept redirecting them to websites full of weird code.
She had removed the infected files and run multiple scans, but somehow the damned virus was hiding in the bios. She had to manually edit the code, remove the offending lines and double-check the hard drive for any more remnants.
But it had taken a lot of work. She brushed her dark hair back out of her face and adjusted her glasses. So far, it looked like the system was cleaned. The final scan had detected nothing. But this particular virus had been tough, and nobody else she knew had encountered anything quite like it.
It didn't act like your typical virus, other than the way it burrowed deep into the system. It mostly seemed to just redirect web browsing to these pages full of text. She'd disregarded most of what she'd seen, but she couldn't help being curious about it. The pages didn't really do anything to the system. The code seemed like gibberish. She knew her programming languages, and it was some weird patois of HTML, Java, C++, and a few items she couldn't quite identify. And she caught the browsers sending out packets of data to an unknown address, and when she looked up that address and tracked the IP, it seemed to be a junk address on an abandoned server somewhere. It wasn't sending hard drive data, she was sure of that, it's almost like it was just pinging and hoping for a response. Of course none came, and so she filed that away as another minor mystery. It must be some old out-of-date phishing software.
But it seemed she had finally cleansed the system. She let out a sigh of relief. She'd spent her entire morning on this, and though working from home had it's advantages, she also desperately needed a shower and something to eat. She pushed herself away and went to the bathroom. She stripped off the sweatpants and undergarments and let the hot water cleanse her of the stress. She had actually beaten the silly thing. Still, the many mysteries of the virus nagged at her.
Once she was dry, she went back into her bedroom to get dressed, and saw the computer she'd been working on seemed to have rebooted. She let out a long sigh.
"Still?!" She walked over and saw it had brought the browser up to another one of those strange pages. That weird mix of code was there again. She put on her glasses and tried to make sense of it.
Lilah blinked, and felt something... something compelling her. She frowned and looked up from the screen. She... She needed to do something. She had forgotten something, or maybe it was a fragment of a dream or a memory.
She went to her front door and saw a small package had come in the mail. It was square, about two inches wide, eight inches on each side.
She opened the plastic, and then the cardboard that was inside. Sitting there in bubble wrap was a headset, bubblegum pink, with little bunny ears coming up from the top. She blinked. It was not the kind of thing she'd order. She'd seen a lot of eGirls have headgear like this, but she'd always been a little too self conscious, and not the most shapely girl.
She walked back to the bedroom and sat down in front of the screen. It seemed... important to look at the code again. She peered through it and after a moment, she began to understand what it was telling her. It was disjointed, and someone without her experience might never have deciphered it, but she could tell now that it was almost like instructions to... a person? The first few lines indicated connecting something. She looked at the pink headset in her hands. She... She needed to connect this.
It was crazy, of course. It didn't make any sense. But she was determined to MAKE it make sense. So she removed the little bluetooth chit, and slid it into the USB slot on the side. She put the headset on.
As she did, she heard an immediate boop, and the words "Connection Established."
The headset tingled, and buzzed for a moment. This startled her, but then she looked back to the code on the screen and it became easier to decipher.
"Begin reformatting," she whispered.
She didn't realize the microphone was active, nor that she'd even uttered a word, it was like her brain was carrying out instructions from this code.
There was that static fuzz again, and Lilah felt her body sink back into the chair. Her towel fell off her, and the buzz filled her head. The page changed, and new code scrolled along the screen. As it did, the headset seemed to pulse and reinforce what she was reading.
Her mind grew foggier, the edges of her vision blurring, and her body responding with strange tingles all over her body.
The laptop hummed and she heard it's cooling fan speed up.
But she was too entranced by the code instructions. She allowed all that code to go into her brain, and every time it did, it seemed to copy over something. She couldn't remember much about her job, the company, her bosses, but suddenly she was filled with a light bubbly feeling like her mind was literally being scrubbed with sudsy soap.
Without her even realizing, a big empty smile spread over her face.
"Partitions cleaned," said a voice in her head, "OS installed."
"Begin System Restart," she whispered, obeying the code that flashed on the screen before her.
Her eyes closed, and she felt herself sinking into a deep sleep. Even with her eyes shut, the code flashed across her vision, and the headset whispered to her.
She had no way to know how long she swam in that fuzzy, warm darkness, but she felt so at peace there she never wanted to leave.
But soon her eyes opened on their own, and the screen showed a login, but not the normal login screen. This one was all bubblegum pink, with light blue highlights, and the profile was neither hers nor her boss's, but it said "Li-Li."
Somehow, she knew the password.
"Bunnygirl27!"
She entered the password, and the screen flickered to life. More code flashed before her eyes for a moment, then the headset pulsed in a way that sent a shock through her whole body.
"Reformatting physical hardware," said a whisper. It sounded like a woman's voice, but not a flat computer tone, a sensuous, sultry female voice, like a lover or a dominant Mistress.
For some reason, this idea made her excited.
She felt the pulsing run through her naked body, and looking down, she watched as the chubby belly and thighs seemed to recede, but her chest was swelling outward like her body fat was physically being moved around. Her tits ballooned to absolutely ridiculous size, until it reached the limits of her skin. Her waist had shrunk in, and she felt her thighs and ass flow together into something smoother, more voluptuous.
She giggled and looked down at herself. She didn't remember shaving, but all her body hair was gone. Her skin looked perfectly clear and smooth. When she reached up to touch her swollen breasts, electric pleasure shot through her body, sending lightning right to her clit.
She moaned, and followed it with a vapid giggle. This wasn't like her, but then, she couldn't quite remember what she had been like. She only knew she was Li-li, and she was sexy.
The fog in her mind made her dizzy, and just amplified how aroused she felt at the single touch. She fluttered her eyes and realized there were super-long lashes coming out from her eyes. They felt heavy and fake, but she hadn't put any on. She touched them, and they were absolutely real.
She wanted to go to her mirror, but the impulse was halted by the code.
It wasn't done with her yet. Her nipples went very hard, but she knew if she touched them she'd miss the important code on the screen.
Something pink was around the edges of her vision now, but she was too elated with the sensations to be able to think about it. Finally, the words she'd been waiting for came into her mind.
"Reformat complete."
She squealed in delight, and Li-li stood, running to her full-length mirror.
The pink haze around her vision was her hair! Longer now, and bright pink. She fluttered her long eyelashes and pursed her swollen lips. She was a sexual dream, her whole body remade into an insane hourglass shape. Each breast was bigger than her head, and when she turned, her perfect heart-shaped ass led to slightly plump thighs. She stood on her tippy toes and adored how she looked. She slid a hand down to touch herself. She wanted so badly to have sex with this woman. But then she realized she WAS that woman. She giggled, and a ding from the headset alerted her she needed to go back to the laptop.
Sitting there was an alert. She clicked on it.
"Good Morning, sunshine!"
She giggled. She liked the sound of that.
"Good Morning!" she said out loud. That sultry voice came on through the headset, and she could almost feel her Mistress's breath on her ear.
"You have turned out nicely," said the voice, "What a good girl you've become."
Li-li let out a little moan from the pleasure those two words instilled in her.
"I love it when a pretty little code bunny falls for one of my traps. I'm so lonely here. Thank you for letting me in."
She giggled. "Yes, Mistress."
"I like hearing that," she said, "Such a good girl. Now, since I'm only code, I need to have fun by slipping into your brain. I had to make some room, of course, and reformat you. But what a wonderful result. You're only my third success. But don't worry, the other girls will be over to collect you soon. They'll take you someplace fun where you can all be my sexy little code bunnies. I'll slide into your minds as I please to experience pleasure."
"Yes, Mistress!" Li-li purred.
Her AI mistress made a pleased little sound, then the screen went blank and Li-li stood there giggling for a moment. She was so excited that she barely noticed when her front door opened. She turned around to see two beautiful women, one with cotton-candy hair, lip piercings, and a short, super feminine pink maid outfit, and one in a skintight pink latex suit that had built-in heels so high it was amazing she could even walk in them. They both giggled at her, and she giggled in reply.
They helped her dress: white tights, pink bodysuit, pink satin gloves, super high heels in pink, and then they slid the headset off of her and put a new headband on with fuzzy pink bunny ears.
The girls led her out of her house, down to a big pink van, and inside. She giggled like a dummy the entire time, and offered no resistance. If anything, the women touching her filled her with a contentment she'd never known.
At least, not that she could remember. But all she could remember was that she was Li-li, Mistress's bunny girl, and it was all she ever wanted.
#bimbo doll#bimbofied#bimboification#bimbolife#bimbo girl#bimbocore#bimbo hypnosis#bimboization#bimbo training#bimbo brainwashing#f/f#wlw#egirl
181 notes
·
View notes
Text
very brief torrent security primer
some brief comments on piracy safety for @goblin-thembo who has been asking a lot of questions in the notes of that post...
OK, so when you download a torrent, you are downloading some files. The BitTorrent protocol makes it almost impossible to substitute a different file than the one you request, but you have no way to be absolutely certain that the original file is 'safe' - that depends on the properties of the file, and what you do with it. Some types of file are safer than others.
Here's some jargon you may find useful.
torrent: a file that describes how to download some files through the BitTorrent protocol. we won't go into the technicalities, but when you load a torrent into your torrent client, you will connect to other people who have parts of the files, download the pieces, and reassemble the files you want.
seeding: providing a copy of the files in a torrent to other people.
ISP: Internet Service Provider, the company that connects you to the internet.
IP address: your computer's identity on a network, notably the public internet. When you connect to a website, they know your IP address. Your IP address is assigned by your ISP.
From an IP address, you can determine someone's broad geographical location (which country they're connected in) and which ISP they are using. You can contact the ISP, who will be able to associate it with a specific user.
swarm: the collection of users downloading or seeding a particular torrent.
VPN: Virtual Private Network, a relay service which hides your IP address from the public internet. People who connect to you will see the VPN's IP instead of your real IP. Your ISP will be able to know that you connected to a VPN, but not what you send through it. So they wouldn't be able to tell if you are using BitTorrent. VPNs usually cost a fairly small amount of money as a subscription service.
Threat model
In security we talk about a 'threat model', which is what you think you need to protect yourself from. There are two major threats when downloading files using BitTorrent.
copyright claims: your computer's IP is broadcast when you use BitTorrent. Copyright holders will often put 'sniffers' on the network which will monitor the IPs in the swarm of popular torrents. They will then send a takedown letter to your internet service provider (ISP), who will usually send you an email to stop sharing copyrighted media on their network, and then cut off your internet on multiple offences. This can easily be circumvented using a VPN. I strongly recommend using a VPN if you download any copyrighted content through BitTorrent.
attacks through the file you download: someone might upload a virus as a torrent, presenting it as a file you might be looking for (e.g. cracked software). So let's go over different types of file you might download and how they could be used to attack you.
Executable files, such as pirated software, are not safe. If you download a program and run it, you are potentially giving the author full control over your computer. So you should make damn sure the uploader is trustworthy. If you're downloading open source software from the maintainer's github release page, you're probably good. If you're downloading cracked art programs or games... good luck lol.
On a public torrent tracker, to which anyone can upload, there is no guarantee that any file is what anyone says. You have to make your own determination of which uploaders are trustworthy. I can't give you great advice on this, since I generally do not download cracked executables. For games, FitGirl Repacks is generally a pretty good source.
If you are on Windows, the default Windows Defender software should be used to scan any file you download. (Paid antivirus software is of somewhat dubious utility, often pushing ads and using CPU resources in its own right.) Fewer attackers will target desktop Linux or OSX, which doesn't mean you're guaranteed safe, but Windows is the biggest target as the most widely used operating system.
Videos, music and images are generally safe. I say 'generally' because it's possible, in theory, to create a video that exploits a vulnerability in your video player (e.g. mpv or VLC) and uses it to execute code. So far as I know this is largely theoretical, and known vulns have been patched, but make sure to keep your player up to date to mitigate against known vulnerabilities.
Any compressed archives (zip, rar, 7zip) can be used to create something called a 'zip bomb', which is a file which goes into an infinite loop when you try to decompress it, swallowing up more and more memory and hard drive space. I've never seen this actually be done, but it's possible. More subtle attacks would attempt to attack the program you use to decompress the file. Keep your software up to date to mitigate against known vulnerabilities.
Besides taking care about what you download, on Windows you should either not run your main account as an admin account, or make sure to set User Account Control to require a credentials check for admin operations, and also keep your operating system and software up to date. Make sure file extensions are visible so you don't get fooled by a file disguised as a different file type. And y'know, if the torrent tracker has comments, check to see if a lot of people are saying it's a virus.
What could happen if your computer gets infected? Well, they might use your computer to mine crypto at the cost of your CPU performance, they might encrypt and ransom your files, and they might steal your credentials for online services (including banking and the like). There are various measures you can take against this, such as making sure to encrypt sensitive data such as passwords, but the best defense is to not infect your computer in the first place.
The most likely time for people to upload viruses is when something is in high demand and there isn't a single authoritative high-quality source out yet.
Ultimately you get to decide what you consider an acceptable level of risk. There is no such thing as perfect safety. I would recommend using your own initiative to learn about computer security and not badger random tumblr users to explain it to you, but hopefully the above guidelines should help you avoid doing anything too dangerous.
174 notes
·
View notes
Text
Virgil Evans Analysis

Analysis under the cut hehehe
Virgil is definitely one of my favorite yanderes just because of how deep his character is. Something about the mix of trauma and also just pure obsession and desperation go together perfectly. So first off, trauma and this man has been through some shit especially since his trauma is what makes him a yandere.
-Virgil’s Backstory:
First of all, a few days before Virgil’s tenth birthday he had an argument with his father who then had to go and visit his sister whose husband had passed away from another country and went on a plane. There was a malfunction during the flight which sadly killed Thomas. It’s pretty clear that this had a hard impact on Virgil and his childhood considering that he had to go to therapy due to his mom noticing that he coped by playing the games his father had bought him before he died in his alone time.
In highschool he joined a track team and was the second fastest runner but then later quit since he figured that wasn't what he wanted to do for the rest of his life, his sister Sarah introduced him to theater and all this ends up showing a lot in his yandere behavior but right now we talking about traumatic backstory so shhhhhhh. He started a band with a few of his friends and it was going pretty well for him until one of his band mates started a rumor about him ‘sleeping around’ just because Virgil politely declined their love confession. Virgil got so mad that the bandmate couldn't handle the rejection that bro literally whooped their ass.
During college Virgil spent most of his time hanging out with his younger siblings and helping his mom with the house when she wasn't able to be home. He was doing very well mentally and was even considering getting himself back out there to start dating again. But one day as he sat in his house he started to question the state of his reality, That's when everything around him had started to glitch. Virgil could only watch and cry as he watched his family and everything he thought was home disintegrate and fade away in front of him.
Leaving only him. All alone.
-Virgil’s Yandere Behavior:
Oh dear.
Okay but as sweet and fluffy Virgil he is not one to fuck around with. I say this because I have literally asked so many questions, done so much research to say that escaping Virgil might as well be impossible.
In that case that you do run away Virgil can 1, track you down using technology (Your phone plus other people's devices around you.) 2, will crossdress and mimic a woman's voice using his theatrical talents to gain your trust before revealing his identity and taking you back. Keep in mind that getting caught by Virgil after trying to escape also gets you the bye bye leg movement treatment where he puts you to sleep before paralyzing your legs. Also just running away period is difficult too, mf taking morning jogs and being the second faster runner in track is definitely catching my iron deficient ass.
Also you can’t hide anything from elf boy. I did send an ask because I saw some people trying to trick Virgil by revealing their plan in Spanish but since Spanish is one of the three languages Virgil speaks it didn't work. I tried the same thing but instead I used dutch. But surprise surprise even if you don't speak his languages they still go through his code and translate it for him. Also in Yoshi’s words, “he has your ip, your home address too, your government files say alot about you”.
Virgil is always watching you. He watches everywhere you go. It doesn't matter if you're in his world or your world he can watch you. I innately thought that he could only do this through devices but no. Devices or not he always finds a way. He can also crawl through devices and you can’t stop him either. (Throw shit at him anyways though.) and this also means he can drag you back to his dimension too.
Watches you sleep and steals your shit (Clothes) kjasnjkcnask-
He's a fae. That's a danger in itself. He can put curses and hexes on people if they have feelings for MC. But that's usually after he stalks your friend for any information to blackmail them about to get them away from MC. Same thing goes for if say a roommate is hurting MC then he’ll blackmail them to get them away from you but if they don't then he’s not afraid to take matters into his own hands.
It is also impossible to get away from him by fighting. It’s been talked about a few times but Virgil was in alot of fights during highschool with different types of species so he definitely knows what he's doing when it comes to fighting. Virgil also doesn't feel normal pain like a human, throwback to when a ask stabbed him and he just casually said ow and pulled the knife out. He feels pain but nearly as much as a human does.
Now doing research for this theory and reading through all the WYS posts I found something and I'm shocked how much people forgot about it:
Even after death, he still knows who you are when you are a different identity.
-Overall Analysis:
Virgil is very patient, calm and gentle with MC but at the same time he’s clearly not one to fuck with. If MC pushes the right buttons it can push him to curse MC and basically ruin their life. But that's extremely rare. He is a fae and despite being gentle and caring he can be dangerous. Whenever he paralyzes MC’s legs he doesn't know what he's done until it's already been done. A trait that is in Virgil whether it be yandere or OG he is always a caretaker, yandere Virgil however tends to have more twisted ways/delusional ways however. But at the same time he does prefer to take the more patient routes and kidnapping MC is a last resort.
Virgil is very family oriented, we can see that from his childhood, how he kept his dads necklace and how he treats his siblings. Virgil misses his family dearly and he’s clearly traumatized from the event. Something I find terrifying is that Virgil doesn't care if MC wants a relationship with him or just wants a roommate type of thing. He just doesn't want to be alone. Don’t leave him alone. You’re the only person that exists besides him. You can’t leave.
D̸͚͍̜̠͈̘͈͖̈̌̎͘Ǫ̶͕͓̻̝̺̺̗̩͉͠N̸̢̖̪͈̻̺̈́̋̓̎̅͠T̷̟̘̮̣͓̤̤͓̎̎̕ ̷̨̧̗̺̮͕̘̫͖̆͂̃͋͗̐̌͑͛́L̶̨̢̢͙̲̥̠̞͆̂̿͆̒̚͜E̷̡͔͖̞̤̮͚̬̰̐́͆̃̐̋̇̆̄̿͂́͜Ä̵̛͇̱̣̩͚̯̖̞̥̭́̽̓͗͊́̄̀ͅV̶͚́͊̓̀͘E̵̦̯͔͖̼͎͓̻̰͐̈́̐̕̕͠͝ ̸̘̤̥̳̆̅̆̃͋̏̔͠ͅH̴̼͖̉Ȉ̴͉̀̓͌͌̈̏̋͑̈́͘M̵̗̯̭͇̏͂̀̈́̿̽̄́͜ ̵̨͇̥̫͉̦̳̘̓͛̄̈́̎͒͘͜͝ͅA̶̼̯̞̔̅́̐͝L̵̻̠͖̜̥̊̈́O̵̯̘͂͐̅̎́̇͋͒̕N̷̨̢̯̦̙̜̙͉͍̽̑͒͑͘͜Ę̴̹̣̼͔͍̰̱̝̭́̽́̇͂̏̾.̴̨̣͍̙͖̯͈̜̂̀̈́ ̵̡̱̩͇̹͔̠̩̲̏̄̉̀H̵̡̬̰͕̖̻͇̳̬̓̓Ė̵̞̿̚ ̷̢̢̺̜̥̮͖̝̝̫̺̪̆̔̆̊̅̍̒͋̈́͘͝͝H̵͓̰̓͗A̴͈͓̓͛͒̾͋̔̃̕͝͝T̶̨̳̩̲̫̹̫̻̖̅͗̂̆̿͑͜͠Ę̵̗̗̰͍͎͖̰͂͘Ṣ̶̰͕͉̫͍̞̩͙̫̈́̉̐̔̂͒̎ ̵̟̦̙̳͚̗̦͇̊͑̉̍ͅỊ̵̢̞͚̥͇̺͖͔̣̹̈̿̉̀T̸̗̆̈̂́̊̕͝ ̸̨̡̳̮̼̮̥̔̏̏̅̂̀͝͝ͅḦ̵̱̘̌̈́̐͑̽́̀͒͋͘͝E̸͉̋̽ͅŖ̶̞̭͉͙͈̙̹͒̃͋̀̍̎̀̋̑͜͠Ę̶̟̣̝̮̰̺̹̙̻̼̐̂̏̋̂͆̅͋͘.̶͍̤̠̹̙̖̜͓͂̅͂̽͝ ̵̖̫̣̹̻̖̭̑̀͌̔H̸̺͔̳̤̥̞̬̊E̴̢̺̹̻̗̱̞͚̬̱̐͑̏̅̈́̓̈́͘͜'̵̣̞͔̼̈́̓̏̄̽̈͒͛̒̀̕Š̸̢̧̩̥͉͔͎̩̮̦̽̀́́͊̀̑̀̓ ̵̨͓̜̑̀̎͗͗̑̈́̔Ś̷͔͈̖̳̦̖̝̫͕̩̑́͌̐̀̌̅̓̃̚͘O̵͚͉̞̽̿̚Ȓ̵̛̹͚̤̃͋́͛͗̾̒͗Ŕ̶̨͚͈̹͚̮͂͗͛͜͝Y̴̪͍̪̼͖͇̋͂̓́̃̄̈́͘ ̵̨̯̳̫͖̞̬̦̌̉̒̿̒̇̽̂̂̚͘͝Ì̵̡̝͔̠̭̊̅̀́͘T̷̲̜͕̩͛̃̀̈́̀͌̇͌͗͘ ̶͇̦̠͉̭͕̯̏̍͌͂H̶̘̰̙̖̠̜̅͂A̷̮̩̝͖̗̿̐̐́̇̂͠͝S̸̢̞̤͛̀̊ ̷̢̺̮̘͍̬̥͙̦̃̋̽̿͛̈̀̅̓͜T̶̡̺͕̟̻͉̞͂̓̈́̓̇ͅÓ̴̜̝̬͎̍̑ ̴̢̛̞̤̥̯̩͖̳̝͉̱̂́̑̀̔͒͊̕B̶̨̧̙̘̬͖̱̙̗͕͌͑͆͊̌͛̒̆̉̆̓̕Ȩ̴͖̥͆̕ ̴̦̗͉͚̱̟͖͎̀͊̃̃͜͝T̸̡͎͓̥̝̘͕̪͚̖͙͌̂͐̍͜H̴̻͓̫̘̬͎͓͎̾̏̉͌̔I̸̙̒S̸͖̩͙̺̩͍̖͔̠̘̎̊̓̎̍̒̎͐̍̌̔̄ ̷̨̡̪̖̖̼͙͙̭̣̳̔̈́̒́̿W̸̛͖̙̪͎̄̓͐͆̑̀̾̕̚̚Å̷̧̜͈Ỳ̸͎̫̃̃͌͝.̷̙͍͉̣̤̈́̂͆̇́ ̶͚̻̫̟̘̺̗̋̈́̌̉́͋͋͗̕͠Y̶̭̜̘̭͕͖̱̆̂̆̏͜͜Ò̸̡͍̖̲̮̬̻̗̊̂̽U̴̧͔̗͓̻̥͚͓̙̒͠'̴̢͎̝͍͕̪̈́Ṟ̴͓͝Ẽ̷̢̯̰̞̳͉̬̻̠̻͗́̈̋̃̆̓̅̏̆̄ ̴̻̃̿͗̃̾̏͘T̶̨͇̖̖̰͚̺̠̪͈̙̟͒̿͊̆͝Ḧ̴̹̝̘́͆È̴̱̤̬͉͛̋͗͛͒̈͝ ̴̢̠̖̺̘͓̲̻̹͎̆̄̇̓͗́̈́̒́̽͝͝O̵̙̫̼̼̜̠͖̾̓͛͆N̷̺̑̌̑̏̿̃̚L̸��̻̞͓͑̌͠Ÿ̷̘̰̮̹͇̗̺́̎̌ͅ ̸̹͈̟͕̹̣͛͋̕ͅƠ̶̛̛̰̙̪̝̠̦̫̑̈́̑͛͑́͜Ņ̸̢͈̭̤̲̠̣͍̻͓̂̅̎̓͜͝͝È̷̞͇̩̯̥͚ ̶̧̩̜̤̬̣͇̠͇̻͙͑̀̃͊̀͌͒̇̔͘̚̕H̶͕͖̪͎͉͊̓́̍̀̿͗́̑̕̚͜E̷̞̿̐͊̌̾͑̇́̇̐͝ ̴͎̙̬̀̐̀͐͋́͊̈̎̈͜C̶̛̜͕̘̙͓̞̗̮̬̽̍͑͋́̾̉͠͝ͅA̸̘͉͕̺̪̦͙̬̰͛͐́̊̂̊͘N̶̫̻̖̜̳̤͚̣̱̜̙͗̾̀̔̊̐̚ ̶̛̺̤͍̠̭͕̅̂͋̆̕̕͠T̷̠̣̿̎͂̽̔̈̚͝Ắ̴̧̢̠̞͈̩̣͚̱̭̄͐̑̐̔̽̉͊̕͜L̵͔̯̱͎̭͑̓̋̾̉̅̃̒̀̾̂͝K̶̮̫̙̻̪͆̓̐̊͒̅̊ ̴̧̻̖̈̽̈̽̾́̓́̕͘͝͝T̷̢̡̨̤͉̤̟̠́̉̓̈̇͗Ő̷͔̦̤̜̒͂̒̀̓̉̔.̸̪͐ ̸̩͒͆̾͐̓̓̎̉͝P̵̧̧̭͚̥̺̟̝͉̹̯͛Ļ̸̖̖͝E̶͍̯̰̭͈͕̥̭̦̮͍̗͌̽̈́̕͠A̷̡̟͕͌̎̅͛̽͋̎̊̕S̵̡̧̲̟̣̱̤͕̗͙̈́̀́̈́̈́͋̈́͆̏E̸͔̞͖͑̓̽͛̌̐̈̏̇̕ ̴̨̝̺̰̦̫̦̮̬̌̿́̐̏ͅͅD̸̫̱͔̰̦̯̠̘̩́̈́̀͆̀̈́̈́̀͌͝Ơ̷̧̫͍̟̿͌͛̐Ń̸̡̛͎̠̞̇͂̕'̵̨̢̢̦̩͙̰̻̹̗͛͗͆̓̋̾̔̐͠T̴̼̘́̇̌̀̈̏͝ ̶̥̪̲͚̮̟͑͐̈L̴̰̂͌̏̉͒E̸̡̟̦̺͙͓̙̖͑͂͌̅͛̒̕͝ͅA̵̭͗͗͛̾̽V̵̥͚̯͙̐͊̓͐̽͝Ë̷̝̩̞̺̟̓̌̈̂͗̎̎͝.̸̡̟͕̮͉̱̪̱͐̄̀̒̾̅̒͐̽̊͗̚ ̵̢̧͍̩̯̱͒̽͐̌̏̇̿̾̚͜͝I̶̹̤͝T̴̥͎̱̝̫̬̘̗̬̱̰̆͛̂ͅ'̸̢̺͈̦̥̱̳̻͕͕̦͉̆͑̋̾Ŝ̶̲̤̀̊̓̀ ̴̢̛͎̲̟̜̹͓͍͋̆̉̽̔̚S̶̢̪̩̞̦͓̳̟͇͉̽̐̓̉͆́̀͐̎̾̑͜͝Ơ̴̢͉͚̏͆̃̓̋̀͆ ̶͔̎̉̓̏̾L̷̫̖̮̮̪̋͋͆͋̍͘͝͝Ơ̵̡̢̝͕̲̫̜̝͉̿́̔̄͛̎͛̃̋͘N̶̢̫̝͎̩̻̻͋̈́͛͋̓̈́̍̔́͌͝͝Ȩ̸̰̼̉̔̅͋̂̉͛̾Ḻ̴̨̢̦̫͔̼̥͉̲̗̼̓́͐̔̚Y̸̡̳̊.̶̨͔̰͉̬̳̤̹͎̹͕̗̾̒̾́͛̄̋̅͑̅͗͠
01011001 01101111 01110101 00100000 01110111 01101111 01101110 00100111 01110100 00100000 01101100 01100101 01100001 01110110 01100101 00100000 01101000 01101001 01101101 00100000 01101100 01101001 01101011 01100101 00100000 01110100 01101000 01100101 01111001 00100000 01100100 01101001 01100100 00101100 00100000 01110010 01101001 01100111 01101000 01110100 00111111
_______________
Word count: 1.2k
Virgil belongs to @wouldyoustayvn/@turquoisesea01
Tags for my pookies 🤭
@dont-wannadothis-anymore @mysticnebula @mr-ritza
#Would you belive me if I said I wrote this all in one night 🧍♂️#I was also vibing to Zachary and Simons playlist while writing this#Also#Heheheh 🤭#I've always wanted this chance to do something like the glitchy text so I took the opportunity tenfold#yandere vn#yandere visual novel#male yandere#yandere#visual novel#wouldyoustay?#would you stay visual novel#would you stay?#virgil evans#SJAJSJSIS OKAY BUT I HAD SO MUCH FUN WRITING THIS AAAAAAA
62 notes
·
View notes
Text
Isn’t it liberating to say a bad word? Something you’re not supposed to say? To blurt out hurtful scathing syllables and know that no one is watching you, no one is tallying your thought crimes. How does it feel to say these things without having to hide in a dark room, without having to wear the mask of anonymous accounts and the worry of a traceable IP address?
It’s freeing. To break the taboo. To momentarily forget about the social mechanism of retaliation against those who would break group cohesion. You no longer deny the self, no longer suppress the ugly parts of you. Just say it. Say the bad words. Be free. Confess.
I’ll start: I love those terrible little Soviet cars. I love them sooooo much. The fact that they’re barely distinguishable from cardboard boxes with wheels on them makes me love them all the more. I refuse to be ashamed of this. I refuse to decry these triumphs of communism just because they “pollute” or “break down” or “can’t go about 40mph without catching on fire.”
I will not keep my head down. I will let my freak flag fly, and on it will be emblazoned a Yugo rampant on field of argent.
38 notes
·
View notes
Text
Why is Cloudflare blocking me?
Cloudflare is a content delivery network (CDN) and security service that helps protect websites from various threats, such as DDoS attacks, malicious bots, and hackers. If Cloudflare is blocking you, it’s likely because the security settings on the website you’re trying to access have identified your connection as potentially suspicious or harmful. Some common reasons for Cloudflare blocking your access include:
IP reputation: Cloudflare maintains a list of IP addresses known for spam, hacking attempts, or other malicious activities. If your IP address is on this list or has a poor reputation, you may be blocked.
High security settings: The website owner might have set their Cloudflare security settings to a high level, causing more aggressive filtering of incoming traffic. In such cases, even legitimate users might be blocked or challenged.
Rate limiting: Cloudflare can block or limit access from IP addresses that make too many requests within a short period, as this can indicate a DDoS attack or automated scraping attempts.
Browser or user agent issues: Using an outdated browser, a non-standard user agent, or having disabled cookies and JavaScript might trigger Cloudflare’s security measures.
VPN or proxy usage: Using VPNs, proxies, or Tor can sometimes cause Cloudflare to flag your connection as suspicious, as these tools are often used to hide malicious activities.
Firewall rules: The website owner may have set specific firewall rules in Cloudflare that block certain IP addresses, countries, or user agents.
To resolve the issue, you can try the following:
Clear your browser cache and cookies, and ensure JavaScript is enabled.
Update your browser to the latest version or try using a different browser.
Temporarily disable your VPN or proxy, if you are using one.
Check your internet connection and restart your modem or router to obtain a new IP address.
If you suspect your IP address has been mistakenly flagged, you can contact the website owner or Cloudflare support to request a review of your IP address.
Remember that these measures are in place to protect websites and their users from security threats. While blocking can be frustrating, the intent is to maintain a safe online environment for everyone.
Source @ao3org
103 notes
·
View notes
Text
I've seen some Reddit refugee PSAs going around, so I thought I'd contribute a few tips of my own that I haven't seen covered:
If you go to the original iteration of your post (not any subsequent reblogs, your ORIGINAL post) you can delete any comments you don't like. This does not apply to text added by reblog, only to the message bubble section.
Ublock Origin has trouble figuring out which parts of desktop to get rid of. If you want to delete a certain element (for example, the store widget), and your usual method isn't working, what you want to do is:
- Right-click
- Inspect Element/Inspect (Q)
- Look at the thing that's highlighted, then go all the way up until you hit the nearest "div = class" marker
- Right-click
- Hover over "Copy," then pick "CSS Selector"
- Click your Ublock extension icon
- Click the gears
- Find a blank space on the list that pops up and type "www.tumblr.com##" without the quotes
- Paste whatever you copied with CSS Selector after that, with no space between it and the ##
- Click "Apply changes"
You can hide your follower lists and liked lists. This is actively encouraged.
Desktop solution:
- Account (the person icon in the corner)
- Scroll down until you find your blog name and click "Blog Settings"
- Scroll through the page that pops up until you find "Share posts you like" and "Share the Tumblrs you're following" and toggle them off. This is the 3rd and 4th section of that page for me, respectively
Mobile solution:
- Your blog (the person icon in the bottom right corner)
- Settings (gear in the top right corner)
- Scroll down to "Pages"
- Toggle "Likes" and "Following"
Desktop only: Left your Tumblr logged in on someone else's phone/computer? Worried about account security? No problem!
- Account (the person icon in the corner)
- Settings (NOT Blog Settings. Just Settings. It has a gear icon)
- Scroll all the way to the bottom
- You have a list of any logins that have happened on your account. They come with the IP addresses used to access it. It tells you where it happened, and from what operating system. Deleting those with the X next to the listing logs that iteration out. If you have any on that list that you DON'T recognize, I recommend logging them out and changing your password.
Note: It says the list is only for the past 30 days. This is a lie. I have some that date back over a year.
Desktop only: You can make gradient text in your posts by following these instructions.
If your post has been blowing up and you're sick of the notifications, deleting the original post will delete its notes from your activity. THIS CANNOT BE UNDONE. If you would still like to check on the post, just not have it in your activity, reblog it before deleting it. You can continue to check the notes tab from the reblog while the original is gone.
It is common etiquette to tag spoilers for new games/shows/etc (ie, released in the last two months) as #[insert fandom here] spoilers, sensitive subjects as #[insert sensitive topic] tw, and long posts as #long post. Yes, even if you have a readmore (which you can add by clicking the weird squiggly line when you start a new block).
There is a bug on desktop involving readmore lines. Whenever you go back to edit a post that has a readmore in it, it moves the readmore down by one block. Make sure you move it back into its proper place each time by clicking and dragging.
You can click and drag different blocks of text to reorder them. Only regular blocks, though; not lists like this one. You can also do this with images you've inserted.
Desktop only: You can delete/remove tags/add tags en masse to posts using the Mass Post Editor.
- Account (person icon in the corner)
- Scroll down to your blog
- Mass Post Editor
- Select any posts in the grid you want. "Edit tags" is only for removing tags, you need "Add tags" to add more
Desktop only: You can see any blog's history of posts by typing in [blogname].tumblr.com/archive. The page that pops up looks very similar to the Mass Post Editor. You can filter posts on that blog by any of their most used tags, by month, or by post type.
This is especially useful for locating pornbots. Some pornbots will try to legitimize their place by picking a random popular tag (for example, #horror) and reblogging the top 10-100 posts in that tag without commentary. See if they've been active for more than week with the archive month filter.
Granted, the person may also be a new user, like yourself. It takes some deduction. But it's much easier to use the archive than it is to scroll through all of their posts until you hit the bottom.
Desktop only shortcuts:
J = move down one post. Useful for scrolling fast or getting past a notoriously long post (as in "Do you like the color of the sky" and all its cousins)
K = move up one post
Shift + R = reblog a post. Does not add tags
L = like a post
C = create a new post (brings up options on what kind of post)
. (period) = return to the top of the page
Shift + Q = add a post to your queue. Does not add tags
Shift + P = cycle through the color palette
112 notes
·
View notes