#enc collections
Text
jesus
Just
Enduring
Sacrifice
Unyielding
Savior
3 notes
·
View notes
Text
Minthara Beanre x Reader
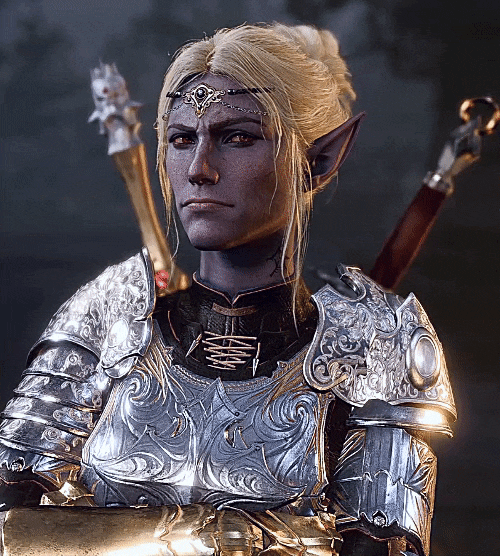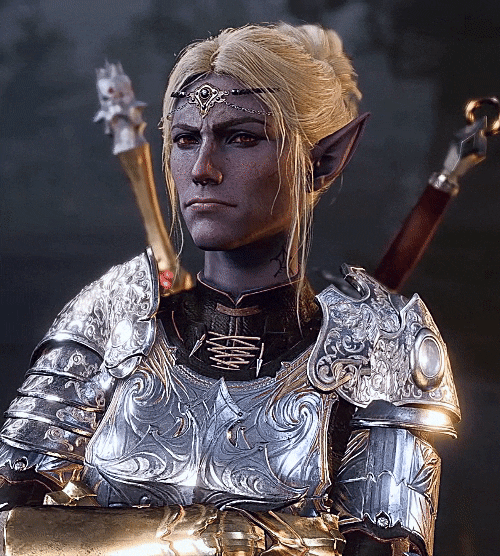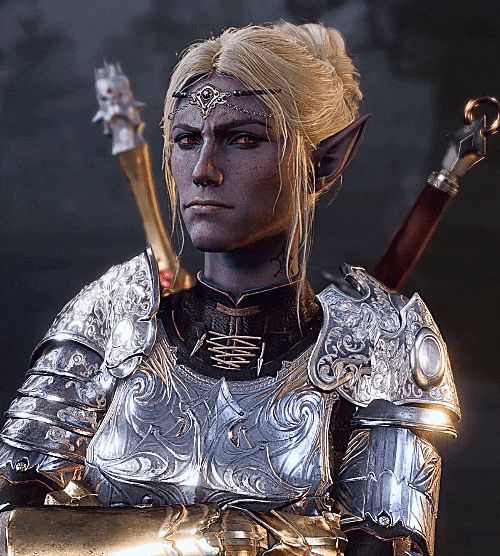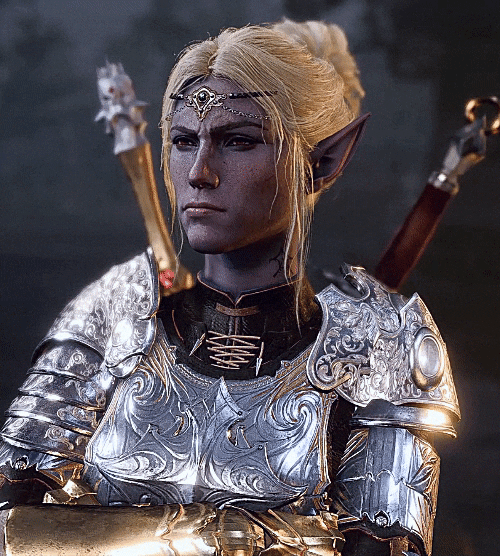
TWs/Tags: Dom!Minthara, Sub!reader/Tav, horny telepathy stuff, size difference (if you squint), mild bondage, begging, extremely minor (non-sexual) reference to gore, AFAB reader but gender-neutral terms are used
As requested by @superanonymousthethird
I hope you like it :3
Sent to siege their leaders, you and your cohorts walked through the damp, goblin-infested halls of the former temple. After passing the guard’s inspection, you wandered the unfamiliar building with them in mind— the cleric, the hobgoblin, and the Drow. You entered an open room with a war table. And leaning above it was her, the Drow. She looked up from the map to gaze at you intensely, a scorching-hot carmine stare to make your stomach drop. With a gulp, you could feel her presence suppress your former sense of confidence.
As she turns to you, her thoughts mingle with yours. With your security shook, your tadpoles connect telepathically.
“Another True Soul?” Her eyebrows pinch together curiously. “You will join me. I’ve been tasked by the Absolute to exterminate these vermin non-believers.”
You nod in response, eager to follow her command to your partymembers’ concern. You learn the Drow’s name to be Minthara as she further presses you for information on the whereabouts of the tiefling colony.
“It appears we are organized to commence the onslaught.” She grins venomously. “I thank you for your cooperation, True Soul. We will leave at dawn to fight. But I am afraid I will not be finished with you by then.” With that comment, she leaves you until the morning.
The day begins with you fastening your armor undisturbed. Suddenly, a presence perturbs your thoughts. You don’t need her to be there physically to know that Minthara is communing with you.
“I will see you on the battlefield, yes?” Her shrill, commanding voice rings through your mind. Images of you and her flash in front of your eyes— her body over yours in ascendency, binding your wrists. You gasp from the shocking sight, your face flushed as her devious chuckle plays through your mind via tadpole. “I hope that’s not too ardent for my True Soul.” The cocky comment echoes before she severs the connection.
You return from the battle drenched in blood and viscera. Forgoing the celebration, you clean your body and armor of the remnants of the battle. Occupying your mind unrelentingly was not the dozens of lives you claimed just hours ago, but Nightwarden Minthara. This, she could sense. Restraining herself from teasing you with more projections of yourselves together, she instead approaches you outside the matters of the mind.
“Not concerned with the celebration, True Soul?” Minthara looks down at you as you sit on a stool beside the flowing river. Unlike the others, she adorns her full armor; augmenting her prowess. You feel underdressed in comparison, wearing only your undershirt and pants.
She stares at you as she kneels down to your level. “You fought excellently against those blasphemers.” She reaches to unbutton your shirt. You’re paralyzed as she dotes on your shirt, pulling it off of you. She stands back, expecting you to stand up. When you don’t respond as such, she gently grabs your wrists to lead you to the nearby partially collapsed structure. Sandwiching your body between hers and the wall, she aggressively puts her lips on yours. She licks your bottom lip; your jaw drops for her.
“So obedient.” She says as her hand holds your chin, angling it so your gaze matches hers.
“Now, will we be executing those trussed-up fantasies you’ve been having? I want you nice and secure when I take you tonight.”
You nod vehemently in agreement.
“It is decided,” she chuckles at your enthusiasm. “Tonight, you are mine.”
She pushes you down to sit beneath her. Piquing your curiosity, she reaches for something in a concealed pocket. As she takes it out, you can see a collection of leather straps, completely unused.
“As you can see, I’ve anticipated this encounter with you. The Absolute operates is mysterious ways, would you say?” She remarks rhetorically as she wraps them around your wrists, binding them together above your head. She stands back, looming above you as if admiring an artwork of her creation.
Leaning back down to your level, she angles her arm above your head, holding both of your bound hands in her singular, larger one. She bows down for another kiss, holding your cheek with her free hand. That free hand soon travels down your abdomen and into your trousers. At a single touch of your cunt, you moan into the kiss.
“Hmm, sensitive are we?” She whispers sadistically, clearly deriving amusement from your whimpers. She continues by dipping a pair of fingers into your heat. A loud gasp escapes your mouth in response. When was the last time you did this again?
Minthara pushes her fingers in, diving deeper against the inside of you while still sucking at your lips. You struggle against her as she senses the tension building in your core. The tension rises and gets tighter until she suddenly removes herself from you. Deprived, you look up to her with a confused expression.
“Don’t worry, little one. I’ll allow you finish.” She moves down lower, pulling down your pants farther. “But I have to know you want it.”
Your face grows red at her words. She wants you to beg for release.
“Please. Please, Minthara,” you begun, unsure of what to say.
“Is that all you have for me, little warrior?” She stares at you, unimpressed, as she teased a thumb against your clit.
“Please, Minthara, I need your mouth, your tongue. I need you. I’m yours,”
“That was just perfect, little one.” She smirks with endearment before yanking the trousers off your legs, leaning down to tongue your clit. You cry out in pleasure again, gripping her hair gently as she goes down on you. She holds your torso in place, pulling you closer when needed. She licks and laps at your cunt, eating you out ravenously.
That familiar tension builds and knots in your stomach again. This time, Minthara intends to see your completion the whole way through. Your jaw drops once more and your eyes roll into the back of your skull as she licks a final stripe up your lips.
As you ride out the high, she makes her way up your body to kiss you again. This time, it’s slow and tired, but all-the-same genuine. She unties you before laying down next to you. You hold onto her form tightly, legs still shaking. Not having the heart to move you from her, she takes your weakened body in her arms and you doze off together.
#Minthara X reader#minthara X tav#Bg3#bg3 X reader#bg3 fanfiction#size difference#Dom!minthara#Dommy mommy#The drussy got me writing fanfic again#baldurs gate 3#Writing request#Possible sequel???#BG3 smut#minthara baenre
105 notes
·
View notes
Text









✨️Starry night themed age regression mood board✨️
☆Links after cut☆
Hat-
https://www.etsy.com/listing/1460608453/celestial-moon-stars-crystal-ball
Bear- https://www.ebay.com/itm/145096185667?chn=ps&_trkparms=ispr%3D1&amdata=enc%3A1H5KrtPxNQAWP4zFrSR40qw3&norover=1&mkevt=1&mkrid=711-117182-37290-0&mkcid=2&mkscid=101&itemid=145096185667&targetid=1529493963262&device=m&mktype=pla&googleloc=9010492&poi=&campaignid=20382379140&mkgroupid=151098995266&rlsatarget=pla-1529493963262&abcId=9316959&merchantid=6296724&gclid=Cj0KCQjw3JanBhCPARIsAJpXTx7yMzKZlyxqffNMIq32U_LN7ZWByMgAkKx4EL8wUTRnryo50lpSOnQaAld1EALw_wcB
Plugs- https://a.co/d/doOTxKN
Paci clip- https://www.etsy.com/listing/1199577131/starry-night-painting-inspired
Paci- https://www.etsy.com/listing/1544829565/starry-night-van-gogh-agere-pacifier
Shirt- https://envygreenmanor.com/collections/the-art-gallery/products/starry-rugby-shirt
Socks- https://www.tiemart.com/products/navy-blue-and-white-striped-socks?variant=31094061203540&gclid=Cj0KCQjw3JanBhCPARIsAJpXTx4l47VBwjkhdRiThoksuQeLawnSm9tgk1IQod7SYKo26JoKYMJhJzAaAgqJEALw_wcB
Shoes- https://galartsy.com/products/van-gogh-starry-night-inspired-sneakers
#age regression#age regressor#sfw#agere#mine#sfw agere#babycore#boyregressor#boyreg#agere boy#boyre#van gogh#starry night#moodboard#agere moodboard
107 notes
·
View notes
Text
Worm Bin Tutorial

Disclaimer: the information I’m giving is based on my own personal experience and research. Some of the things that work for me may not work in a different setup. If you’re interested in learning more, I’d highly recommend the book “Worms Eat My Garbage” by Mary Appelhof.
Why have a worm bin?
It’s a great way to dispose of organic matter while minimizing methane emissions! Landfills aren’t set up for aerobic decomposition, so food scraps in landfills often give off a ton of methane emissions when decomposing, which is a pretty potent greenhouse gas! Also, worm castings are an excellent fertilizer/mulch/soil amendment.
A worm bin is super low-maintenance once you figure out what you are doing. It doesn’t smell bad and can be kept indoors—I keep mine by my desk in the winter! And I think it’s pretty fun. Also, your trash won’t smell as bad when it isn’t full of rotting food!
Making the Worm Bin
Really what you need here are two containers. One of them you put a bunch of holes in, and that sits inside the other container. The holes are important because they allow for drainage of water (which is then caught by the external container) and diffusion of oxygen. I used some kitty litter buckets for this, and they work great! The lid is really useful.

Pro-tip: you don’t need a drill to make the holes. If you have a knife or razor blade, you can press it into the plastic and rotate it, which makes nice, round holes.
The bin with holes in it sits inside the other bin, but there should be space for water drainage/collection and air permeation.
Worms
The worms you want in general are “red wrigglers” or Eisenia fetida. These are sometimes sold as bait worms, but in my experience the “red worms” are actually European Nightcrawlers (labeled “ENC”). Those can also work, but they prefer different conditions from red wigglers (I believe they live deeper in the soil) so they might not be as successful. You also need a lot of worms to start out with, like a pound of worms. I had the best success going to a local vermiculture business and getting a pound of mixed worms (red wigglers, European night crawlers, and Indian blues). I think the mix is useful since having a couple different species makes the bin more resilient.
Note: buying local is really beneficial here. When worms are sold online and shipped, the sellers “dehydrate” them a bit to help lower weight and prevent overheating. The worms will be perfectly healthy after you give them moist bedding again, but you’re going to miss out on bacteria and other beneficial critters that could come with the worms if they are fresh.
Setting up the Bin
An important thing I have learned from experience: you can’t just put food and worms in a bin and expect things to work. You also need bedding. Bedding is filler material, like newspaper or coconut coir. I mostly use newspaper I buy from a local vermiculture business. I tried ripping my own paper and once it got wet it turned into a solid layer, whereas the pre-ripped newspaper I buy has a fluffy consistency.

I’ve also tried using peat moss as bedding, but that didn’t work so well—I got a huge spike in the more population (maybe from acidic conditions?). Peat moss also isn’t great for the environment in general.
The bedding is important because worms shouldn’t eat too much food or too much of their own poop (castings) as both are bad for them. Bedding should be topped off when possible. When you add food to the bin, use a shovel to bury it in the bedding. This helps things rot properly, prevents mold and bad smells, and keeps away critters like fruit flies.
Other Critters
Your worm bin can and should have other critters in it! Some in my bin include mites and springtails, who both help the worms break down organic matter. However, there should be a balance between other critters and the worms. If something appears to be taking over, you might have a problem. I’ve also had fruit flies in my bin—this didn’t end up being a huge problem as long as I only opened the lid of the bin outdoors.
Worm Bin Maintenance
Once you get going, the worm bin doesn’t require much maintenance. I keep a freezer bag in my freezer and fill it up with food scraps, and once it seems the worms are mostly finished with the last feeding, I’ll thaw the bag and feed them again. (Freezing is helpful because it’s a convenient way to preserve the scraps, but it also helps to kickstart breaking down, since freezing damages things.) Be careful not to over-feed the worms, as this can lead to a sour bin and/or string-of-pearls (which is a pretty disturbing worm ailment).
Also be careful of what you feed the worms. You can look up lists of dos and donts online, but in general, stick to plant matter, and don’t feed them aromatic herbs or citrus. Also make sure to feed the worms plenty of crushed eggshells, as this provides grit and halos to regulate the pH of the worm bin.
The worms should be kept in a location with temperatures that are comfortable to humans. They don’t do well if conditions are too cold or too warm.
Make sure to dump out any water that accumulates and add bedding when it’s needed. I use this to water plants, and I haven’t had any negative effects, but some people will say you shouldn’t do that.
Once the bin starts to get full, you can remove worm castings. There are fancy ways to do this, but I just dig through the bin and scoop out any areas that are nearly all worm castings and then remove any worms/eggs that are in the castings by hand. The castings can be mixed in with potting soil or used on top like a mulch. (Although be careful: Ive heard worms are an invasive species in some areas so check before you potentially introduce them to the ground.)
Conclusions
So that’s it! If you want more information, I encourage you to do your own research. Although try to seek out multiple sources—not all the information out on the internet (or even in books) has been properly vetted. I can also try my best to answer questions based on my own experience, but I’m still relatively new at this.
47 notes
·
View notes
Text
If I had the money, talent, and connections with the right people or whatever, I’d revive G3 and bring back all the unique collectible characters from the earlier era from like 2003-2007 and I would give it a show, but the show would be like My Little Pony Tales from the 90s, only with G3 ponies and better 2D animation.
I feel like G3 had untapped potential with a show or a full-length movie like G1 did. G1 was brilliant cause it had like 2 shows, but instead of focusing all their toys on just 6-7 main characters, they had a few main characters but a CRAP TON of different characters in the form of collectible toys.
G3 really shot itself in the hoof when they decided to start the whole “let’s just make 6-7 ponies and make 10,000 slightly different variations of them” thing that started with the Core 7 all the way to the current Mane 5 with G5.
I’d make a G3 show with no modern technology (no smartphones, tablets, social media or infl*enc*rs, but like a few old-school computers, TVs, and telephones, like in MLP Tales) and with a main group of friends, but the physical toys would be as vast and unique as the G1 toys were.
And I would also add BOY PONIES to my new G3 era. In my headcanon, boy ponies do exist in the G3 world, they’re just never around. With my new G3 show, I’d 100% add them and there would be toys based off of them, and some would be toy-exclusive.
I’m just so tired of Starlight Glimmer-idolizing neckbeard bronies taking fat dumps all over G3 for being “stupid and babyish” when they have no idea what G3 was actually like for its target audience or that MLP even existed before G4.
Anyway, I just had to air that out cause I needed to. #BringBackG3

#mlp#my little pony#if it were me#i would do it like this#mlp g3#maybe in another life#mlp rant#i need to make a mlp podcast for this kinda stuff#my little pony g3
66 notes
·
View notes
Text
sukuna is mara

"
I made this thread because I was trying to search more and more about Sukuna as a character and, simultaneously, as a myth as well, trying to learn more about him. And I didn't only search for his connections and metaphors with "Yama " in myths, but also another Demon King that+
I thought would be more precise as a reflection of Sukuna's character in JJK. And that would be the Celestial Demon King Maara. (Sukuna and Maara bellow) Maara is also known as "Hajun ", a name very associated with demons that fight Buddha or some figure that represents him+
in fiction as general. Maara is known as "The Destroyer ", "The Lord of Death " and has a strange and indispensable sovereignty over Samsara itself! In this thread, I will try to relate Maara to Sukuna as much as I can. (Demons of Maara bellow)

Sh
Maara can also be called and known as: Kleśa-māra (Embodiment of unskillful emotions; greed, hate and delusion); Mṛtyu-māra (Maara as embodiment of Death) and most importantly known as+
Devaputra-māra (Deva of Sensuous Realm; the one who appeared to Gautama, Buddha, the night he achieved Nirvana).
In Jujutsu Kaisen, strenght has, even if it is little, a relation and connection with enlightenment. The strongest (Sukuna and Gojo, respectively) are called Honored Ones, the Enlightened Ones. hose who wisdom, genius abilities, powers and names traverse the history of the world+


Shaksasha
@monkeysking88
·
Oct 1
as the best of the best, without a doubt! In a way, we can, in this line of thought, relate that those who want to become stronger are bodhisattvas (those who follow the Buddha way; who look for true enlightenment). Why I'm pointing this out? Because in the Golden Era of Jujutsu+
Shaksasha
@monkeysking88
·
Oct 1
when the Jujutsu Sorcery was in it's most absolute peak collectively, the most powerful of the most powerful reunited to defeat and kill the King of Curses. The most powerful, following the bodhisattva line of thought, are those following the Way of Enlightenment.
Shaksasha
@monkeysking88
·
Oct 1
But… how does this connects with Maara and Sukuna again?
Maara in myths are known for being the most vile demon. The concentration of all forms of evil, depravity and tempting concepts as they come. e being responsible of DESTROYING those who follow the way of Buddha+
Shaksasha
@monkeysking88
·
Oct 1
responsible for killing and corrupting the souls and Ways of those called bodhisattvas, destroying their Illumination. Maara and Sukuna are the same. While in buddhism, Maara defeats and exterminate bodhisattvas, in Jujutsu Kaisen, if strengths does mean that one is closer to+
Shaksasha
@monkeysking88
·
Oct 1
Enlightenment than other, Sukuna defeating overwhelmingly the strongest of the strongest does connect them as he destroyed JJK's "bodhisattvas ", the strongest of the strongest.

Shaksasha
@monkeysking88
·
Oct 1
Sukuna is called The King of Curses, he who posesses the most concentration and brute form of CE, he who surpasses every one of other cursed users. In myths, Maara, as I said earlier, is the utmost form of evil. Of evil methods, of the abstraction of vile things…+
Shaksasha
@monkeysking88
·
Oct 1
Ringing a bell again, here? Both are concentration of evil, in some way.
Shaksasha
@monkeysking88
·
Oct 1
There is, no kidding here, SO MANY WAYS there we can relate the King of Curses and The Destroyer Maara that it's not even funny.
But, lets head to the apex of this thread. Maara's relation to Buddha and how does this reach Sukuna vs Gojo.
Shaksasha
@monkeysking88
·
Oct 1
It's not strange to relate Gojo to Buddha (his name, "Satoru ", literally means, in his rooted form in buddhism, "Enlightenment ), his quote after reaching the skies and calling himself to be the Honored One ("Tenjo tenge yuiga dokuson ", as he says himself)+
Shaksasha
@monkeysking88
·
Oct 1
And, once connecting Sukuna to Hajun (Maara's another name) we begin to cook something here.
You see, Maara is the most evil enemy Buddha has ever faced. The encarnation of evil and depravity, using any way to destroy Buddha and make him part ways with Enlightenment, trying to+
Shaksasha
@monkeysking88
·
Oct 1
tempt him to destroy him, as, those that are CONTAINED in Samsara should, if he chooses too, be helpless once Maara can use any method to destroy us.
(Ironically, I just noticed that in this art, Maara hold the Vajra and Trishula like Sukuna lol)


Maara's most powerful ability in myths is the "Power of Doubt/Illusion". With it, he tries to make Buddha doubt himself and his teachings, his ways, trying to make him doubt that he achieved Nirvana. But, the wise Gautama, the Buddha we know+
Shaksasha
@monkeysking88
·
Oct 1
said that the Earth should be his witness as he doesn't need ESSENTIALY anyone to believe him. They believe if they want to, he doesn't need to doubt his achievement.
Shaksasha
@monkeysking88
·
Oct 1
Ironically, how does this "duel " connects with Gojo and Sukuna? In chapter 230 of JJK, Sukuna calls out Gojo as "painfully ordinary "as he isn't enlightened, he is just as any other sorcerer around, nothing special.
This does hurt, but the most interesting thing here is that Sukuna uses a kanji that calls as "bonpu ". This literally means "those who don't achieved/failed to achieve Enlightenment ", truly ordinary. That's why Gojo's look was so... disappointed. Maybe even with himself.

In buddhism, not doubting his achievement, Buddha defeats Maara and save his students.
But we know that this time, when the most evil being fought the Honored One… this representation of Buddha we call "Satoru Gojo ", didn't come to win against the Celestial Demon King…
Shaksasha
@monkeysking88
·
Oct 1
Just to finish here… I noticed that Maara's representations truly upscales him to the "transcendence level " of myths. He holds the Vajra, the most powerful and unbeatable weapon. He holds the Trishula, being the encarnation of his titles: "The Destroyer "+
Shaksasha
@monkeysking88
·
Oct 1
Reinforcing one theory that said that "power " and strength, isnt the way to defeat Sukuna, comparing Ryomen Sukuna to Maara here, of course. And even, ironically, both Maara and Sukuna have a "special " eye(s) themselves+
Shaksasha
@monkeysking88
·
Oct 1
Sukuna can literally sense the metaphysical manifestation of the CT on a jujutsu sorcerer. Combining with the Third Eye of the Demon King Hajun (Maara) that sees all, to no one EVER escape his evil, in any plane that one founds himself…
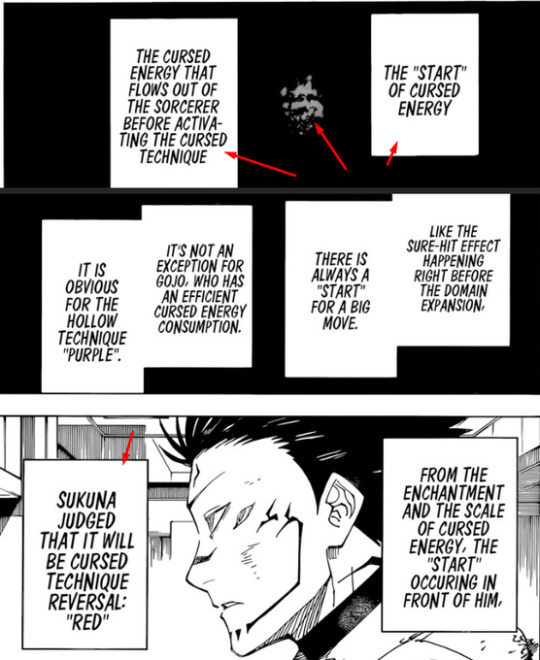
"
7 notes
·
View notes
Note
You mentioned couple of pages ago that "[D&D is] a dungeon crawling combat sim (that doesn’t even really do or encourage dungeon crawls that well anymore, but that’s another post) " What do you mean by 'dungeon crawl' in this context? My impression, as a non-gamer, is that it's just 'go into a dungeon, then fight monsters and get rewards'. Does D&D not do that? And what are examples of a good dungeon crawling RPG? Thank you.
So there's a few reasons for this. And understand that, while I might come off as negative about various editions of D&D in this post, I don't mean to be bashing them. This is just a thing where the culture has changed and the mechanics of the game don't act like they used to.
So. The dungeon crawl. At it's basic, it's simple. There is a dungeon (and a dungeon can be a castle, a labyrinth, a wizard's tower, a tomb, or just a hole in a ground that leads to ADVENTURE). There are obstacles in the dungeon. And there is treasure. And an adventurer wants to go to the dungeon, overcome the obstacles, and get the treasure.
It's that simple. And D&D, as it is now, no longer encourages it. Why can I say that? Well...
TL;DR, because this post got REALLY LONG: The way character progression works in modern D&D has made dungeon crawls obsolete as a method of character advancement.
In WotC's Dungeons and Dragons editions, there's two ways for characters to earn experience. The main way is combat. You kill a monster, you get a chunk of experience points for it. The other way, and it's more of a suggestion in 3.x, but I think 4E and I know 5E make it more prominent, is story milestones. You complete a story, or make it a good ways in there, and you get a good amount of XP for advancing the plot. Westley and Princess Buttercup make it out of the fire swamp only to meet Prince Humperdink and Count Rugen, the six-fingered man, on the other side. Buttercup goes with Humperdink and Rugen knocks out Westley to take him to the Pit of Despair. Break 'til next week's game, you did great, I had a blast, thanks for playing, everyone collect two thousand experience points.
But in the TSR era (because WotC bought TSR about twenty-three years ago, you see. TSR invented D&D, but due to years of terrible business decisions they were basically dying. They would not have survived.) it was a little different. It changed depending on the game/edition (There was Original Dungeons & Dragons in the little brown books, the multi-editioned and sadly often forgotten Basic/BECMI Dungeons & Dragons, the much ballyhooed Advanced Dungeons & Dragons, and the far-spanning 2nd Edition Advanced Dungeons & Dragons), some of them allowed for story progression, others rewarded players for roleplay or exceptional play (like coming up with a plan to save the party or something), others encouraged 'proper' playing of classes by giving experience points for appropriate ability use...
But the experience for all of these was pretty small. Oh, sure, you could get hundreds of experience points for killing a monster, but...
Basic:
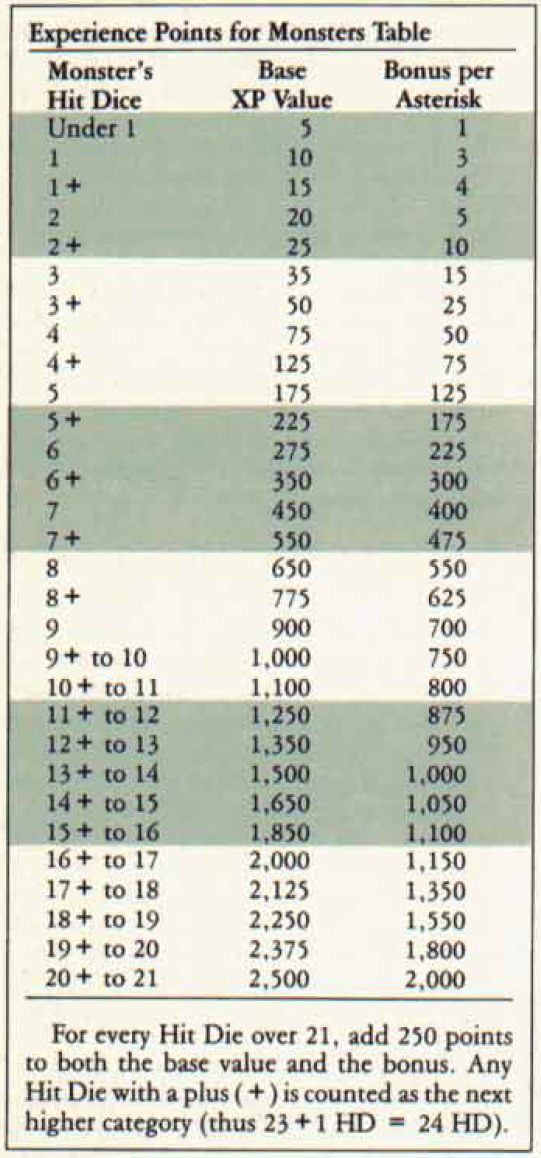
First Edition

2nd Edition

Seems a little easy, yeah? Here's a 2E wizard's experience point chart. He needs the listed amount of experience points to gain a level and get more power/ability.

So if he's fighting a bunch of level 1 monsters at the start of his career, he'd have to kill 166 of them to get to level 2. This isn't likely to happen. And, normally, a wizard wouldn't be doing this alone, so he'd have to split all of that XP into equal portions with each member of his party.
(For reference, in Fifth Edition, an orc, a 1 hit die monster worth 10~15 XP in earlier editions, is worth 100 XP if you kill one. You need 300 XP to reach level 2, 900 to reach level 3, and 2,700 to reach level 4. Though, of course, the party XP split still applies.)
So, how did the main XP gain happen?
GATHERING TREASURE!
Every gold piece of treasure you gathered equaled one experience point. So, five silver pieces? One XP. A ring worth 50 gp? 50 xp. A gem-encrusted set of enchanted plate mail possessing orichalcum inlays worth 100,000 gold pieces? 100,000 experience points (assuming you up and sold it).
All of the TSR editions did this. This was the main way your characters got stronger. Risky fights were stupid, you could get killed that way. It was often better to find ways to avoid them, whether through stealth, diplomacy, trickery, or fear tactics. Story was fine, but that could be wonky at times. (Dare you enter my magical realm?) But gold? Gold was as good as experience.
And under TSR, a lot of people had this concept of, like. A mega-dungeon. Massive, sprawling adventure areas, ten, fifteen, twenty layers deep, each level having possibly dozens of rooms, growing more mysterious and deadly the deeper you go, but with greater rewards as well. You'd have adventurers go down for a week or two, then come back half-dead, but carting enough gold to build a castle from. Then, three months later, when they'd rested and recovered, they'd go right back down, seeking out new caverns and probing deeper depths.
(This is, btw, why silver and copper pieces exist. It's not to simulate an economy. They're traps. Coins have weight, in OD&D and 1E, 10 coins were a pound of weight. In Basic and 2E, 50 coins were a pound. Either way, if you filled your pockets with copper and silver, you might leave the dungeon before you got any gold because you suddenly had too much to carry.)
...So, backtracking a bit:
WotC editions don't do this. They instead increase the XP value of monsters so that combat is the main way to gain experience points, and they also go "But story also matters. Progress the plot of your campaign and you'll get stronger." Which, y'know, valid.
But if your XP is based on story milestones or overcoming enemies, then diving into a deep dungeon that you've got to regularly leave just feels... counterintuitive. In a newer edition, if you leave, the monsters might repopulate, set more traps, risk killing you. It's better to kill them all while you're fresh, refusing to leave until every last monster has been purged. Having to worry about finding a place to long rest mid-dungeon, keeping track of resources like torches, rations, etc., that's not fun for some people. They tend towards single visits.
But big dungeons weren't made for that style of play in mind. If you want that style of play, dungeons need to be short, to the point. A few rooms, maybe three levels, and then you're up and out with a level up jingle playing. Sometimes you might even get campaigns without any dungeons, because why need them if you're just going to use milestones? What's the point of going into the Danger Hole if you're focusing on Political Intrigue? Yeah, the mines might be really interesting to explore if you can dodge the boss fight, and there's tons of loot, but you've really got to make it to Lothlorien.
The biggest dungeons evolve. They might change layout while the party is gone. They'll repopulate, sometimes with different kinds of monsters. The rewards will refresh themselves, but why bother with chicken feed when there's a king's feast five levels down and you've found a short cut?
They're made for repeat visits.
But that's not the modern play style. It's not rewarded by the system. Players would rather not deal with it, because it feels riskier and more dangerous.
And that's what it boils down to.
If you're interested in dungeon crawling games... Well, there's a lot of options. Older editions of D&D still exist. Various OSR (Old School Renaissance, essentially retroclones of early D&D with attempts at better editing and polish) games, like Old School Essentials, Dungeon Crawl Classics, and OSRIC are options. If you want alternatives that aren't quite so D&D, Sword World (Record of Lodoss War's RPG. Originally they tried to sell the setting of Lodoss to TSR, but TSR wasn't interested, so they made their own tabletop game.) has a lot of passionate fans that are doing translations of it. I've heard good things about GURPS' Dungeon Fantasy. And where there's a mention of GURPS, the HERO System is soon to follow with Fantasy HERO deserving a mention.
For science fiction takes, Shadowrun can often take this form (I'd suggest third or fourth edition), Traveller often takes teams in to exploring abandoned moon bases or derelict space ships, and Space Hulk is Warhammer 40k's take on this with a hefty dose of Alien to inform things. Finally, there's a ton of superhero games out there, and what superhero game is complete without a raid on a dungeonmad scientist's lair?
(Note: I haven't played all of those games, but I know all of them by reputation at the very least, and I've spoken to folks who've played each one.)
7 notes
·
View notes
Text
Origins (part 1)
Okay, While not as detailed as a full on written fanfic, this is how i imagine Sissi joining the Lyoko warriors, i'll continue the story next time, don't have enough juice to write it fully now.
This happens on the relative begginings of the story, around the first third of season 1.
It's friday and festive in the Kadic Academy, which means students have three full days of freedom. Of being able to rest and let loose. Yumi's parents and brother have gone on a trip, leaving the girl on charge of the house. And since they trust in her, Yumi has permission to invite her friends to her house. Sadly, both Ulrich and Odd had already made plans and cannot go since they will be out of town throughout the whole weekend, though this doesn't stop her from going ahead, even if there will only be Jeremie and Her. Besides, this means that even if Xana attacks she will be ready to fight.
Meanwhile, Sissi's home is in turnmoil. She thought she would be able to pass this weekend with her mom, but alas she cancelled in the last moment. Jean-Pierre, the director and Sissi's father, tried to calm her down and tell her that her mother loves her still, that she is a really occupied woman and probably some emergency happened.
Sissi doesn't buy it, since her mother left her dad she has had this gnawing feeling that it was somehow her fault. That she wasn't enough. Normally she can silence it but now... It feels like a flame eating her inside. And so she goes to the park besides Kadic, to be alone, to calm down... to let the time pass.
On her way home, Yumi goes through a shortcut through the park, since it has started raining and is possible that in a bit it will be too much, and she didn't have an umbrella right now. But on her way, she notices something. Under a tree there is someone. Not exactly hugging her knees, but noticeable cowered. Yumi also noticed that Sissi's make up what somewhat ruined, even if the rain was still a drizzle...
She recognized what happened. She still didn't know why, But something bad had happened to her. Something painful, not just banter or sarcasm and light insults from classmates, Sissi never reacted to them this way. The director's daughter didn't seem to have noticed her yet since she was too absorted on her own thoughts... probably she could keep walking without trouble, letting this be just a weird enc-
''Hey, it's starting to rain. Did you bring anything to cover from the rain?''
Yumi started the conversation, even if sometimes she was a pain. Seeing Sissi like this felt wrong...Perhaps she would regret it but at this point she kept going with the inertia.
''Look, my family is on a trip for the weekend and they left me the house free and told me i could invite some people over. There was going to be only Jeremie and me, since the others are out of town so i have still some room left. Want to come over and pass the night, even if it's just to cover yourself from the rain?''
Sissi looked at Yumi. Her head still fuzzy and full of bees. Her eyes itchy and blurry. Yeah, Yumi was annoying and the nerd a bit weird... well probably not that different from Herb so whatever. But it felt weird, Sissi thought Yumi didn't liked her, that they were rivals for Ulrich attention. All this interaction felt awkward, It would have been easier if she just had ignored her, at least she didn't noticed the marks of her crying, thanks to the starting rain probably.
Sissi was about to tell her that thanks but no thanks. That she had a home herself to return to...
But her throat went dry. She... she didn't want to go back home... not yet at least. She collected herself and got up. Cleaned the dust from her clothes and looked at Yumi.
''Alright, i'll go. Just... Nevermind. Besides, i'm sure the place will get brighter just with me being there. Guide the way''
And with a sigh, Yumi guided Sissi to her home. Partly regretting having invited her and preparing herself for what would probably be an uncomfortable and not that great of an experience...
Next
2
2 notes
·
View notes
Note
Happy STS, Lee! For Hospital food (sksksk), how does the parasite system (???) work? And despite how harmful it seems, are there any benefits to it? Sending good 🌌 vibes 🌌 and good luck to ya! 🍀🍀🍀 - ✨️ Enc
I am so sorry you may have accidentally opened a can of worms (haha-) with this one
SO the parasites
They're all like worms from space basically but there's a lot of different types and can be defined by how they interact with their hosts
(ALSO THIS MIGHT GET A LITTLE SQUEAMISH IF YOU DON'T LIKE BUG THINGS SORRYYY)
Here are some of the general questions that get asked:
How does the parasite get into the host (human)'s body? Ingested through the mouth, pierces through skin, enters through wounds?
What does it consume? General nutrients that the host eats, blood, hormones?
How does it affect the host? Changing their hormone levels, causing unusual or uncharacteristic actions, burrowing into organs and causing problems?
How much control can it have? Does it fully control the host's actions, partially influence it, or has no notable impact at all?
How intelligent is it? Can it adapt to different situations and scenarios?
What is its weakness? How can it be stopped and treated?
Everything kind of leads to that last question, since a lot of parasites have very diverse weaknesses, so identifying them correctly to apply the correct treatment is key to solving the problem before things get dire.
So with the main character Ward, she knows that the parasite she has came from an infected water source, causes pain, bruising, and damage to external body parts, creates a sensitivity to heat and light and an attraction to water, and grants some protection from (other) infections. She suspects that it can execute some kind of control over her actions, but doesn't know how much, nor knows its intelligence levels or weaknesses.
It's a bit elaborate, so that's why diagnosis and eliminating the issues are the work of a whole time in universe haha
If you've ever seen those medical shows like House or Chicago Med I feel like that's kind of what the day to day lives are working at the treatment ward; strange case, having to collect all they can on the symptoms to try a diagnosis and treatment, seeing if it works, rinse and repeat
#I had this sitting for like 5 days because halfway through I decided I wanted to research parasites even more to get more details LOL#ah. worms.#hospital food#thank you SOOO much for asking!!#qna
3 notes
·
View notes
Note
Same funko anon, here’s one that’s $65 (apologies for the egregious link length 😅) ✨
https://www.ebay.com/itm/265908548799?epid=16032136626&hash=item3de96274bf:g:Dp8AAOSwtM5jNL6a&amdata=enc%3AAQAHAAAA8KTdlSYAmKnnJCMeL4mrrvUPT7elje6brNsIsm7G1zb65mJuJa5b%2BjSvDdvYUjTZqjaYUWFUhH3jVzqP0%2B01AwZxXFfpaPwW7IIAYixZ29u41ycH7B57rO13HtdmLREcJqarf1UoMTJn%2F5tTcP19%2FbVfLSccKDydL93cACKDq0XRfN04e2aJG8d24VQcDCnZCqambDfAHirrSlQfbuzUrDe9phcE7d55kqLBxHHBVk2nVumGVSbap9w%2FmVwutBM5sXBdySajyvtJBbyk%2FtiO6ehQSWFLWRz0CpYvlKvP8BBJ4Hzmz8r1TiTOr0kO870sIw%3D%3D%7Ctkp%3ABk9SR5SEm7r2YA
Oh yeah that's a great price, especially because it's specifically an exclusive collectible. Idk what the shipping is like in the US but for me it's a lot so I'm trying to bid on the only one that's under 80 near me lmao. Great find though!!
9 notes
·
View notes
Note
FOR MY BABYGIRL LAVORNA: 9, 11, 28, 47, 61, 65
9) when in their life were they most scared?
when mummy died :(( and it was my fault 🙈🙈🙈
11) if they have a pet or animal companion, how do they spend time with them? if they don’t have one, what sort of animal would they be interested in raising, if any?
She spends all day every day with her pal cersei :) they never go anywhere apart. she was a rescue tho so she didnt raise her lol thatd be weird
28) do they collect anything?
Oh girl she has so many collections she collects so much shit. but she also chronically misplaces everything so she has like. a single rock. one button. one creature tooth. TWO pieces of weird moss. but she keeps losing everything so quickly and also carries pretty light so yea <3 she collects but she doesnt have collections
47) what could they talk about for hours on end?
OH GIRL all the drama that happens with her friends back home like. first off she has so many friends. and all of those friends have so much happening to them all the time. and lavorna LOVES to gossip but like only when the things she says cant really effect antyhing thats happening. unless shes drunk then she is Sloppy
61) is there an in-game moment of theirs you think about and just laugh?
HER falling off the barstool during the celebration after the grotto race GIRL she is so funny. just keeps talking to cersei while shes laying on the floor of the very busy tavern. AND ELLE JUST STEPPING OVER HER girl its so funny. i love her so much
65) what would their go-to karaoke song be?
an incomprehensible love ballad from 350 years ago that no one knew existed but she SWEARS was like in the top 10 for several decades and is DEVESTATED when no one knows what shes talking abt but she pours her heart and soul into the performance anyway. and the encore. and the second encore. and the third enc-
2 notes
·
View notes
Text
youtube
enjoy an episode of Yuzuki Family.
1 note
·
View note
Text
which is better tor or vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
which is better tor or vpn
Tor vs VPN comparison
In the realm of online security and privacy, both Tor and VPNs (Virtual Private Networks) are popular tools used by individuals looking to protect their anonymity and safeguard their data. However, there are distinct differences between the two that users should consider when choosing the most suitable option for their needs.
Tor, short for The Onion Router, is a free and open-source software that aims to enhance online privacy by routing your internet traffic through a network of servers operated by volunteers worldwide. This process encrypts your data multiple times, making it extremely difficult for anyone to trace your online activities back to you. Tor is known for providing high levels of anonymity, making it a valuable tool for activists, journalists, and individuals living under oppressive regimes.
On the other hand, VPNs work by creating a secure and encrypted connection to the internet through a remote server. By masking your IP address and encrypting your data, VPNs protect your online identity and data from prying eyes, including hackers, ISPs, and government agencies. VPNs are commonly used to bypass geo-restrictions, access region-locked content, and enhance online security while browsing on public Wi-Fi networks.
When comparing Tor vs VPN, it's essential to consider your specific needs and threat model. Tor offers a higher level of anonymity but can be slower due to the multiple encryption layers and the volunteer-operated network. VPNs, on the other hand, provide faster speeds and are more suitable for activities requiring secure connections, such as online banking or streaming. Ultimately, the choice between Tor and VPN depends on your priorities regarding privacy, security, and speed.
Tor network advantages
The Tor network, short for The Onion Router, is a powerful tool that offers several advantages to its users seeking online privacy and security. One of the key benefits of using the Tor network is anonymity. By routing internet traffic through a worldwide network of volunteer relays, Tor conceals the user's IP address and browsing habits from prying eyes, including internet service providers, advertisers, and even government surveillance agencies.
Another advantage of using the Tor network is circumventing censorship and accessing blocked content. In regions where certain websites are restricted or online activities are monitored, Tor provides a way for users to bypass these restrictions and communicate freely. This can be especially important for journalists, activists, and individuals living in authoritarian regimes who rely on unrestricted access to information.
Furthermore, the Tor network enhances security by encrypting data as it passes through each relay, making it significantly harder for hackers to intercept sensitive information such as login credentials or financial details. This encryption is especially crucial when using public Wi-Fi networks, where cyber threats are more prevalent.
Additionally, Tor promotes online privacy by preventing websites from tracking users and collecting data for targeted advertising. By masking the user's true location and identity, Tor helps to preserve anonymity and protect personal information from being harvested without consent.
In conclusion, the Tor network offers a range of advantages including anonymity, bypassing censorship, enhancing security, and promoting online privacy. By utilizing this powerful tool, users can navigate the digital world with greater peace of mind and confidence in their online activities.
VPN benefits and drawbacks
VPN (Virtual Private Network) services are increasingly popular among internet users, offering a range of benefits and drawbacks for those seeking enhanced security and privacy online.
One of the main benefits of using a VPN is increased data security. By encrypting your internet connection, a VPN ensures that sensitive information such as passwords, credit card details, and personal files are protected from potential hackers or cybercriminals. This is particularly important when using public Wi-Fi networks in places like cafes, airports, and hotels, where your data could be vulnerable to interception.
Another advantage of VPNs is the ability to bypass geo-restrictions. By connecting to servers in different countries, users can access region-locked content such as streaming services, websites, and online games that may not be available in their current location. This can be especially useful for travelers or expats looking to access content from their home country.
However, there are also some drawbacks to using a VPN. One common issue is slower internet speeds, as the encryption and rerouting of data through VPN servers can cause a decrease in connection speed. This can be particularly noticeable when streaming high-quality video content or downloading large files.
Furthermore, not all VPN services are created equal, with some free or low-cost options potentially logging user data or lacking strong encryption protocols. It is essential to choose a reputable VPN provider that prioritizes user privacy and security.
In conclusion, while VPNs offer valuable benefits such as enhanced security, privacy, and access to restricted content, users should be aware of potential drawbacks such as slower speeds and the importance of selecting a reliable service provider. By weighing these factors carefully, individuals can make an informed decision about whether a VPN is the right choice for their internet browsing needs.
Tor anonymity levels
Title: Understanding Tor Anonymity Levels: A Comprehensive Guide
Tor, short for The Onion Router, is a powerful tool designed to provide anonymity and privacy to its users. It achieves this by routing internet traffic through a series of volunteer-operated servers, encrypting it at each step, and thereby obscuring the user's IP address. However, not all levels of anonymity within the Tor network are created equal. Understanding these levels is crucial for users seeking varying degrees of privacy and security.
Entry Nodes:
These are the first servers your data passes through when using Tor. They know your real IP address but not your final destination. Therefore, they can see that you are using Tor but cannot determine what you are doing online.
Middle Nodes:
These servers relay your data between the entry and exit nodes. They don't know your IP address or your final destination. Their role is to add another layer of encryption and further obfuscate your online activity.
Exit Nodes:
These servers are the final point before your data reaches its destination on the regular internet. They know the final destination of your data but not your IP address or its origin within the Tor network. However, they can potentially monitor unencrypted traffic, so it's crucial to use HTTPS connections whenever possible.
Hidden Services:
These are websites or services that are only accessible through the Tor network. They use a different routing system, making them even more anonymous than regular Tor connections. Users accessing hidden services remain completely anonymous, as the service itself doesn't know their IP address.
Understanding these Tor anonymity levels empowers users to make informed decisions about their online privacy. By leveraging the appropriate level of anonymity, users can protect their digital identities and maintain privacy in an increasingly surveilled online landscape.
VPN encryption strength
VPN encryption strength is a critical factor to consider when selecting a Virtual Private Network (VPN) service. Encryption plays a vital role in safeguarding your online activities and data from prying eyes, such as hackers, government surveillance, or internet service providers (ISPs). Essentially, VPN encryption involves encoding your internet traffic, making it unreadable to anyone without the decryption key.
The strength of VPN encryption is typically measured by the length of the encryption keys and the encryption protocols used. Common encryption protocols include OpenVPN, L2TP/IPsec, IKEv2/IPsec, and SSTP, each with varying levels of security.
The most secure VPN protocols often utilize AES (Advanced Encryption Standard) encryption, with key lengths of 128-bit, 192-bit, or 256-bit. Among these, AES-256 is considered the strongest and most secure, as it provides a high level of protection against brute-force attacks and other cryptographic vulnerabilities.
In addition to encryption protocols and key lengths, other factors can influence VPN encryption strength, such as the integrity of the VPN provider's infrastructure and the implementation of security measures like Perfect Forward Secrecy (PFS). PFS ensures that even if one encryption key is compromised, past communications remain secure.
When choosing a VPN service, it's crucial to opt for providers that prioritize strong encryption standards and regularly update their encryption protocols to defend against emerging threats. Reading reviews and conducting thorough research can help ensure you select a VPN service with robust encryption measures to safeguard your online privacy and security. Remember, the strength of your VPN encryption directly impacts the confidentiality and integrity of your internet communications, so it's worth investing in a reputable provider with a proven track record in cybersecurity.
0 notes
Text
how a vpn protects your finances
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
how a vpn protects your finances
VPN encryption for banking
Using a VPN for banking activities adds an extra layer of security to protect your sensitive data from cyber threats. VPN encryption technology ensures that the information you send and receive online is securely scrambled, making it extremely difficult for hackers to intercept and decipher your data. This is especially important when conducting financial transactions or accessing personal accounts that contain confidential information.
When you connect to a VPN server, your internet traffic is encrypted, creating a secure tunnel that shields your online activities from prying eyes. This encryption process safeguards your sensitive banking details, such as account numbers, passwords, and financial transactions, from potential cyber intruders looking to steal your information for malicious purposes.
Using a VPN for banking can also help you maintain your privacy and anonymity while online. By masking your real IP address and location with that of the VPN server, you can prevent third parties from tracking your online activities and collecting data about your browsing habits. This added layer of anonymity is crucial for safeguarding your personal and financial information from cybercriminals and data snoopers.
In conclusion, incorporating VPN encryption into your banking routine can significantly enhance your online security and privacy. By encrypting your internet connection and data transmissions, a VPN provides a secure digital environment for carrying out banking transactions and accessing financial services without compromising your sensitive information. Stay safe online by taking advantage of VPN technology to protect your financial assets and personal data from potential cyber threats.
Secure online transactions VPN
Virtual Private Networks (VPNs) play a crucial role in ensuring secure online transactions. As cyber threats continue to evolve, the need for safeguarding sensitive financial information during online transactions has become more important than ever. VPNs provide a secure encrypted connection between the user's device and the internet, protecting their data from prying eyes.
When it comes to making online transactions, whether it's online shopping, banking, or accessing sensitive information, using a VPN adds an extra layer of security. By masking the user's IP address and encrypting their internet traffic, VPNs help prevent hackers and malicious actors from intercepting their data. This is especially important when using public Wi-Fi networks, where the risk of data theft is higher.
Additionally, VPNs can help bypass geographic restrictions that some websites or services may have in place. This is helpful for users who travel frequently and need to access their financial accounts or make transactions from different locations around the world.
However, not all VPNs are created equal, and it's important to choose a reputable VPN service provider that prioritizes user privacy and security. Look for VPNs with strong encryption protocols, a no-logs policy, and a kill switch feature to ensure your online transactions are kept confidential.
In conclusion, utilizing a VPN for secure online transactions is a proactive step towards safeguarding your sensitive information in today's digital age. With the right VPN in place, you can have peace of mind knowing that your online transactions are protected from potential threats and cyber attacks. Stay secure, stay private with a reliable VPN service.
VPN financial data protection
VPN services play a crucial role in safeguarding financial data and ensuring data protection for individuals and businesses alike. In today's digital age, the security of financial information is of paramount importance, with cyber threats becoming increasingly sophisticated.
Using a VPN (Virtual Private Network) encrypts data transmitted over the internet, making it difficult for hackers or any unauthorized parties to intercept and access sensitive financial data. This encryption creates a secure tunnel for data to pass through, preventing potential breaches and ensuring that financial information remains confidential.
For businesses, VPNs are essential in protecting financial data when employees work remotely or access sensitive information on public networks. By using a VPN, companies can establish a secure connection to their servers, reducing the risk of data leaks or breaches that could compromise financial information.
Individuals can also benefit from using VPNs to protect their financial data when conducting online transactions, accessing online banking accounts, or simply browsing the internet. VPNs provide an added layer of security, masking IP addresses and encrypting data to prevent unauthorized access to personal financial information.
In conclusion, VPN services are instrumental in ensuring the protection of financial data in an increasingly digitized world. By encrypting data transmissions and establishing secure connections, VPNs help mitigate the risk of cyber threats and provide peace of mind for both individuals and businesses when handling sensitive financial information.
Anonymity for financial details with VPN
In today's digitally-driven world, safeguarding one's financial information is paramount. With cyber threats and identity theft on the rise, individuals are increasingly turning to Virtual Private Networks (VPNs) to enhance their online security and protect their anonymity, particularly when it comes to financial transactions.
VPNs create a secure and encrypted connection between your device and the internet, masking your IP address and encrypting your data. This means that when you use a VPN, your online activity becomes virtually untraceable, adding an extra layer of protection for your sensitive financial details.
One of the key benefits of using a VPN for financial transactions is the anonymity it provides. By masking your IP address, VPNs prevent third parties, such as hackers or advertisers, from tracking your online activities and collecting your personal data. This makes it significantly more difficult for cybercriminals to intercept your financial information or launch targeted attacks against you.
Moreover, VPNs also help bypass geographic restrictions that some financial institutions may impose. For example, certain banks or payment platforms may limit access to their services based on your location. By connecting to a VPN server in a different location, you can bypass these restrictions and access financial services from anywhere in the world.
However, it's essential to choose a reputable VPN provider that prioritizes user privacy and security. Look for VPNs that offer strong encryption protocols, a strict no-logs policy, and a wide range of server locations to ensure reliable and secure connections.
In conclusion, leveraging a VPN for your financial transactions can significantly enhance your online security and protect your anonymity. By encrypting your data and masking your IP address, VPNs offer a robust defense against cyber threats, allowing you to conduct financial transactions with peace of mind.
VPN fraud prevention finance
Cybersecurity threats continue to evolve, and one area where VPN technology plays a crucial role is in preventing fraud in the finance industry. VPNs, or Virtual Private Networks, provide a secure and encrypted connection for users, allowing them to access the internet anonymously. This anonymity is especially important when handling sensitive financial information online, such as banking transactions or investment activities.
Fraudsters are constantly looking for ways to exploit vulnerabilities in online systems to steal personal and financial data. By using VPNs, individuals and financial institutions can protect themselves against these threats by ensuring that their online activities are encrypted and secure. VPNs help in masking the user's IP address, making it difficult for hackers to track their online actions and steal sensitive financial information.
Financial institutions can also benefit from using VPNs to protect their online platforms from potential fraudsters. By establishing secure connections through VPN technology, banks and other financial organizations can safeguard their customers' data and prevent unauthorized access to sensitive information.
In addition to preventing fraud, VPNs can also help with regulatory compliance in the finance industry. Many regulations require financial institutions to secure customer data and transactions, and using VPNs is a proactive step towards meeting these compliance standards.
Overall, VPN technology plays a vital role in preventing fraud in the finance industry by providing secure and encrypted connections for individuals and institutions alike. By embracing VPNs as part of their cybersecurity strategy, financial organizations can mitigate risks and protect sensitive financial information from falling into the wrong hands.
0 notes
Text
Theme 3 Blog Post - Critical Literacy in Accessing Internet Reference Resources
Real-world examples that catch students' attention are a great way to model Critical Literacy. eg: In 2018 the B.C. Government was still publishing the "Zombie Apocolypse Preparedness Guide" in video and in print. I asked a class of Grade 3's if they thought this was real.
I led them through the survival steps and asked if those might also work for earthquakes, etc. (We also brainstormed other ideas. Some of them were fun.) At the end, I asked them why the B.C. Government might publish such a guide. We concluded that their purpose was to grab peoples' attention, to read an emergency plan because the usual one may have been practical but too boring for some readers.
Teachers Pay Teachers offers Critical Thinking/Literacy units in Advertising, News Media for current, outrageous "fake news" stories, even ChatGPT Reading. The latter's statistics may sometimes be out of date because of its training datasets. It can also present biased information because it can't evaluate data or be skeptical enough yet.
When using Google Chrome, AI now often offers a short paragraph at the top. Beneath it is the URL/link to the source article. However, if one checks this source, one may find the website doesn't even exist or is unreliable.
"AI will make it easier to do everything - the good and the bad..."."2024 is the year AI goes mainstream."*
https://gluusociety.org/ai-guide/

Introducing critical literacy in your library learning commons (LLC) requires collaboration between the classroom teacher and the teacher librarian. Here's a plan on how to do it effectively:
Collaborative Planning:
Initiate a meeting between the classroom teacher and the teacher librarian to discuss the integration of critical literacy into the curriculum.
Identify key learning objectives and standards related to critical literacy that align with the subject being taught.
Curriculum Integration:
Identify opportunities within the curriculum where critical literacy skills can be integrated. This could include analyzing texts, media, or current events from multiple perspectives, questioning power dynamics, or examining bias and stereotypes.
Design lesson plans and activities that incorporate critical literacy principles. For example, students could analyze different versions of a historical event from various cultural perspectives or critically evaluate advertisements for underlying messages.
Resource Selection and Curation:
Collaborate to select resources such as books, articles, videos, and online tools that support critical literacy objectives. Ensure that the resources represent diverse voices and perspectives.
Curate a collection of resources in the LLC that promote critical thinking and inquiry skills. This could include thematic displays, book lists, and multimedia resources that encourage students to question and engage critically with information.
Instruction and Guided Inquiry:
Co-teach lessons that introduce critical literacy concepts and strategies. Provide opportunities for students to engage in guided inquiry, where they explore topics of interest and critically evaluate information sources.
Foster discussions that encourage students to analyze, question, and challenge assumptions. Model critical thinking processes and provide scaffolding as needed.
Assessment and Reflection:
Develop assessment strategies that allow students to demonstrate their understanding of critical literacy concepts. This could include collaborative, small-group projects.
Reflect on the effectiveness of the critical literacy instruction and make adjustments as needed. Solicit feedback from students and colleagues for future planning and implementation.
Promotion and Advocacy:
Share success stories and examples of student work that demonstrate the impact of critical literacy instruction.
Promote the LC as a hub for critical inquiry and information literacy. Host workshops, author talks, or book clubs that encourage students to explore diverse perspectives and engage critically with information.
Create a Learning Commons Tab on the school website with reliable online sources.
By providing opportunities for guided inquiry, you can create a dynamic learning environment that empowers students to think critically, communicate effectively, and become informed and engaged citizens.
FAVCUS, Linda, "AI and YOU: Understanding Artificial Intelligence", PostScript: The Magazine for Retired Educators, pages 15-19.
Teacherspayteachers.com
https://chat.openai.com/
https://gluusociety.org/ai-guide/
0 notes
Text
Laravel Development Trends: What's Evolving in Web Development for 2024

Laravel stands out as a leading PHP framework in 2024, widely embraced for its elegant syntax, user-friendly nature, and rich library ecosystem. Its popularity continues to surge among developers globally, with projections indicating further growth throughout the year.
What is Laravel?
Laravel, an open-source PHP framework, equips developers with an extensive set of tools to craft bespoke web applications efficiently. While initially leveraging Symfony, another PHP framework, Laravel has since developed its own identity, empowering developers to construct full-stack applications with optimal productivity.
The main objective of Laravel development is to improve the accessibility of web applications. This is accomplished through its expressive and refined syntax, enabling developers to produce clean, testable, and maintainable code efficiently.
Laravel owes its success to its meticulously crafted design patterns, adherence to best practices, and strict coding standards.
Orbitwebtech provides an array of development solutions that render it a compelling option for businesses and organizations. Its Laravel development services encompass a spectrum of offerings, spanning from bespoke application development to seamless API integration, alongside comprehensive maintenance and support provisions.
Laravel stands out as a versatile option for developers due to its seamless integration with various PHP libraries and robust data binding capabilities. These features empower developers to seamlessly incorporate a variety of tools and technologies into their projects. As a result of these advantages, Laravel has risen to prominence as one of the leading PHP frameworks available today.
Moreover, Laravel presents numerous advantages. These include prioritizing convention over configuration, facilitating swift development, offering robust routing and validation capabilities, seamless integration with various PHP libraries, and efficient data binding. These features collectively contribute to making Laravel one of the most desirable PHP frameworks available.
In this article, we'll delve into the most recent trends shaping Laravel in 2024 and discuss effective web development strategies to elevate your Laravel-powered websites and applications.
Here's a list of the latest trends in Laravel development for 2024
1) Microservices Architecture
2) Serverless Architecture
3) Real-time Applications
4) Cloud-Native Applications
5) Laravel Headless CMS
6) GraphQL API
7) Artificial Intelligence and Machine Learning
Why is Laravel development in demand?
Laravel development has experienced a surge in popularity in recent years, attributable to several factors.
Elegance and Simplicity:
Laravel boasts a sophisticated yet straightforward syntax, facilitating an accessible learning curve and seamless utilization. Additionally, it offers a plethora of pre-developed functionalities and tools, empowering developers to construct web applications swiftly and effectively.
Strong Community Support:
The Laravel framework benefits from a vibrant community of developers who actively contribute to its growth, provide assistance, and develop numerous open-source packages for integration into Laravel projects. This collaborative ecosystem fosters continuous innovation and enhancement within the Laravel community, driving its evolution and improvement over time.
Security:
Laravel incorporates numerous native security measures, including password hashing, encryption, and CSRF protection, which collectively enhance the security of web applications developed on the platform.
Business proprietors choose to enlist dedicated Laravel developers to capitalize on the Laravel framework's functionalities in enhancing data protection, privacy, and security for their web applications.
The framework incorporates various security measures, including but not limited to password management, user authentication, data encryption, and additional protective features.
Scalability:
Laravel's architecture is tailored to accommodate expansive applications, rendering it a prime selection for enterprises with enduring expansion strategies.
Modular Structure:
Laravel adopts a modular architecture, which facilitates developers in efficiently organizing and managing their codebase. This design enables straightforward customization and expansion of the framework.
Testing Capabilities:
Laravel offers integrated testing functionalities empowering developers to craft and execute tests for their applications, guaranteeing functionality and bug-free operation.
What is Laravel Volt?
Laravel Volt stands out as a fresh front-end template debut in the Laravel 8.x ecosystem. It represents a contemporary, nimble, and adaptable option, offering a polished and sophisticated user interface tailored for Laravel applications.
Volt utilizes cutting-edge web development technologies like Tailwind CSS, Alpine.js, and Blade templates. It incorporates a variety of pre-designed UI components, including forms, buttons, modals, and tables, which can be effortlessly tailored to fit the requirements of any Laravel project.
Volt is specifically crafted to seamlessly integrate with Laravel's authentication system, facilitating the effortless incorporation of user authentication and authorization within Laravel applications. Additionally, it offers a range of pre-designed pages, including login, register, forgot password, and email verification pages, which can be tailored to align with the branding of any Laravel application.
Volt stands out for its simplicity and user-friendly interface. Its clean and modern design, customizable through Laravel's Blade templating engine, is a key advantage. With Volt, developers can efficiently create responsive web applications without the need to start from scratch in UI design.
Laravel vs Volt | What are the differences?
Laravel, a popular PHP framework, and Volt, a compiled language, serve distinct purposes in web development. While Laravel advocates convention over configuration, offering streamlined development processes, Volt provides developers with explicit control over configuration details. The decision between the two ultimately hinges on project requirements and the preferences of the development team.
What is Laravel Folio?
Laravel Folio offers a package or library that delivers page-based routing functionality tailored for Laravel, mirroring the capabilities of Next.js in React applications Laravel Folio, recently introduced by Taylor Otwell, empowers developers with the ability to outline pages using a file-based format. This innovative package streamlines the process by automatically generating routes corresponding to the defined page structure.
Laravel Folio seems to offer valuable functionality for developers interested in creating page-based applications using Laravel. It could be particularly beneficial for individuals familiar with frameworks like Next.js.
The Best Laravel Development Trends in 2024
1) Microservices Architecture
In 2024, the microservices architecture is anticipated to maintain its upward trajectory in popularity. This architectural approach enables developers to craft applications that are both scalable and resilient by decomposing them into smaller, more manageable components.
Microservices architecture is a methodology for constructing software systems composed of independently functioning and loosely coupled services. Laravel, a popular PHP framework, offers a diverse array of features and tools conducive to implementing a microservices architecture.
Below are key considerations to bear in mind when implementing a microservices architecture with Laravel.
Break Down the Application into Smaller Services
To initiate a microservices architecture, the initial action involves decomposing the application into smaller services, each tasked with a distinct business function or capability. Laravel offers a range of functionalities like routing, controllers, and middleware, which can be leveraged to craft these services.
Use APIs for Communication
Microservices interact with one another via APIs. Laravel provides several utilities like the Guzzle HTTP client for crafting and accessing APIs. Leveraging APIs enables each service to be developed and deployed autonomously, without dependencies on others.
Use a Service Registry
In a microservices architecture, services must be capable of discovering one another. This is typically achieved through a service registry, which maintains a record of the available services and their respective endpoints. Laravel offers native support for service discovery with integrations for popular service registries like Consul and Eureka.
Use a Message Broker for Asynchronous Communication
In certain scenarios, there arises a necessity for services to interact with one another asynchronously. To facilitate this, a message broker like RabbitMQ or Apache Kafka can be employed. Laravel offers seamless integrations with both RabbitMQ and Kafka for this purpose.
Use a Containerization Platform
Containerization platforms like Docker or Kubernetes are commonly employed for deploying and managing microservices. Laravel offers seamless integrations with both Docker and Kubernetes for streamlined deployment and management processes.
2) Laravel Serverless Architecture
In 2024, serverless architecture remains a prominent topic, poised to maintain its trendiness. Developers working with Laravel can capitalize on serverless technology to streamline application deployment and upkeep, resulting in significant time and cost savings.
Serverless architecture revolutionizes application development by eliminating the reliance on traditional servers. It allows developers to build and deploy applications without managing server infrastructure. Laravel, a popular PHP framework, can be leveraged to create serverless applications using cloud services such as AWS Lambda or Google Cloud Functions.
Ensure to consider these vital aspects when integrating a serverless architecture into Laravel:
Use a Function-as-a-Service Provider
To initiate the adoption of a serverless architecture, the primary task is selecting a function-as-a-service provider. Alternatives such as AWS Lambda, Google Cloud Functions, and Azure Functions Laravel offers integrations with these providers among others.
Break down the Application into Functions
In a serverless architecture, applications are decomposed into smaller functions, with each function assigned to a specific business function or capability. Laravel offers a range of functionalities, including routing and controllers, which can be leveraged to develop these functions from scratch.
Use Event-Driven Architecture
In a serverless architecture, functions are initiated by events. Laravel offers robust integration capabilities with various event-driven services, including AWS S3 and Google Cloud Pub/Sub, facilitating seamless interactions within applications. This facilitates the activation of functions through these services seamlessly.
Use a Database-as-a-Service Provider
In a serverless architecture, databases are commonly overseen by database-as-a-service (DBaaS) providers like AWS DynamoDB or Google Cloud Firestore. Laravel seamlessly integrates with various providers, including Azure Cosmos DB, enabling you to work with them effortlessly.
Use a Monitoring Tool
Monitoring the health and performance of serverless applications is crucial, just like any other application. Utilizing a monitoring tool like AWS CloudWatch or Google Cloud Monitoring allows tracking of function invocations, errors, and various metrics. Laravel offers integrations with these monitoring tools along with others like New Relic and Datadog.
Laravel Serverless Deployment Platform – Laravel Vapor
Laravel Vapor is a deployment platform designed specifically for hosting serverless Laravel applications.With Vapor, developers can effortlessly deploy their applications to AWS Lambda and efficiently manage infrastructure and scaling needs through a unified dashboard/
3) Real-time Applications
In 2024, the prominence of real-time applications is expected to rise, with Laravel's integration of websockets and event broadcasting offering developers the capability to craft interactive and dynamic real-time applications.
Real-time applications demand instantaneous updates to be readily visible to users. Laravel, a widely used PHP framework, offers numerous features and tools that can be harnessed to develop such applications.
Consider the following crucial factors when creating real-time applications in Laravel.
Use a Real-Time Communication Protocol
To begin developing real-time applications, the initial step involves selecting a suitable real-time communication protocol, such as WebSockets or Server-Sent Events (SSE). Laravel offers seamless integrations with various protocols including Pusher and Socket.io, alongside WebSockets and SSE.
Use a Real-Time Message Broker
Real-time applications facilitate the exchange of messages between clients and servers instantaneously. To manage these messages, real-time message brokers like Redis or RabbitMQ are often employed. Laravel offers seamless integrations with various message brokers, including Redis, RabbitMQ, and Kafka, allowing developers to efficiently handle real-time communication within their applications.
Use a Real-Time Event Broadcasting System
A real-time application sends events to clients instantly. Laravel offers an event broadcasting system to broadcast events to clients through WebSockets or SSE.
Use a Real-Time Notification System
In a real-time application, notifications are dispatched to clients in real-time. Laravel offers a notification system which can be utilized to send notifications to clients via WebSockets or (SSE).
Use a Real-Time Monitoring Tool
Monitoring the health and performance of real-time applications is crucial, much like any other application. Utilizing a real-time monitoring tool such as Laravel Horizon or Telescope enables the tracking of real-time events and metrics effectively.
4) Cloud-Native Applications
Cloud-native applications are anticipated to emerge as a significant trend in 2024. Developers working with Laravel have the opportunity to utilize cloud services provided by major platforms like AWS, Azure, and Google Cloud to create applications that are exceptionally scalable and resilient.
Cloud-native applications are specifically engineered to leverage the capabilities of cloud infrastructure, including scalability, flexibility, and reliability. Laravel, a popular PHP framework, is adept at crafting applications tailored for diverse cloud platforms, harnessing their inherent advantages.
Consider the following key elements when developing cloud-native applications with Laravel:
Use a Containerization Platform
When developing cloud-native applications, the initial stage involves utilizing a containerization platform, like Docker or Kubernetes. Laravel offers support for integration with these platforms, along with others such as Rancher.
Use a Cloud Platform
In a cloud-native application, the software operates within a cloud environment provided by platforms like Amazon Web Services (AWS), Google Cloud Platform (GCP), or Microsoft Azure. Laravel, a PHP framework, offers seamless integration with these leading cloud platforms, along with others like DigitalOcean, facilitating efficient deployment and management of applications.
Use a Cloud Database
In cloud-native applications, the database is commonly overseen by cloud-based database services like AWS RDS, GCP Cloud SQL, or Azure SQL. Laravel provides integrations with various services, including DigitalOcean Managed Databases, among others.
Use a Cloud Storage Service
Cloud-native applications typically rely on cloud storage services like AWS S3, GCP Cloud Storage, or Azure Blob Storage for managing storage. Laravel offers integrations with these services, along with others like DigitalOcean Spaces.
Use a Serverless Computing Service
Cloud-native applications leverage serverless computing services like AWS Lambda or GCP Cloud Functions to execute application code in a scalable and cost-efficient manner. Laravel offers integrations with these serverless platforms along with others like Azure Functions.
5) Laravel headless CMS Open-source
The rise of Laravel's Headless CMS architecture is increasingly recognized for its ability to decouple content management from presentation, offering developers enhanced flexibility and agility in application development.
Laravel offers a range of headless CMS solutions, including Strapi, Directus, and Contentful. These platforms empower developers to build dynamic and adaptable applications with ease.
Laravel Headless Ecommerce
As ecommerce continues to grow in popularity, developers proficient in Laravel are seeking headless CMS Ecommerce solutions that allow for the management of product catalogs and customer data without imposing restrictions on the front-end experience.
Laravel Forge provides developers with a smooth deployment process tailored for headless ecommerce content management systems (CMS), streamlining setup and facilitating rapid development.
Below is a list of popular open-source headless CMS options compatible with Laravel:
Strapi: The Best Headless CMS for Laravel
Strapi stands out as a robust open-source headless CMS, providing both a user-friendly interface and the flexibility to customize API endpoints.
Strapi enables developers to structure and manage content efficiently, providing APIs for content delivery. This feature makes it particularly attractive for Laravel developers seeking seamless content management. Moreover, Strapi offers a dedicated integration for Laravel, simplifying the process of incorporating Strapi into Laravel projects.
Strapi offers extensive customization capabilities, allowing users to incorporate custom code and plugins tailored to their project requirements.
Directus
Directus is an adaptable open-source headless CMS that empowers developers to design bespoke database schemas and API endpoints. With its intuitive interface, it facilitates seamless integration with various tools and platforms.
Cockpit
Cockpit stands out as a lightweight and open-source headless CMS, boasting a user-friendly interface that simplifies content management. With its support for custom fields, user roles, and permissions, Cockpit proves to be an ideal choice for efficiently managing content, particularly suited for smaller-scale projects.
Flamelink.io – A headless Firebase CMS
Flamelink is a cloud-based headless CMS renowned for its intuitive visual interface designed for content management. It seamlessly integrates with leading front-end frameworks such as React, Vue, and Angular. Boasting a comprehensive array of content management functionalities, Flamelink facilitates tasks such as localization and version control with ease.
Hygraph: The Next Generation GraphQL Content Platform
Hygraph is a cloud-based headless CMS offering a GraphQL API for content management and delivery. With features including schema validation and content localization, it provides seamless integrations with leading front-end frameworks such as React and Angular.
Various open-source headless CMS options offer Laravel developers a diverse range of choices for crafting bespoke front-end experiences without the limitations associated with conventional CMS platforms.
6) GraphQL API
GraphQL is a powerful query language designed for APIs, enabling developers to efficiently retrieve only the necessary data, thus minimizing network overhead and enhancing application performance. Laravel developers can take advantage of GraphQL to create APIs that are both efficient and flexible.
GraphQL is a query language for APIs known for its flexibility, efficiency, and power in data querying. It has gained significant traction within the developer community for its ability to efficiently handle complex queries and mutations. Laravel, a well-known PHP framework, offers developers the capability to construct GraphQL APIs proficient in managing intricate operations.
When integrating a GraphQL API into Laravel, it is crucial to consider the following key aspects:
Use a GraphQL Schema
To begin setting up a GraphQL API in Laravel, the initial task involves outlining a GraphQL schema to delineate the data types the API will deliver. Laravel boasts a convenient package known as GraphQL, facilitating the seamless definition and administration of a GraphQL schema.
Use a Resolver
In a GraphQL API, a resolver serves as a crucial component responsible for handling the resolution of queries or mutations to specific values. Laravel offers a user-friendly resolver system, empowering developers to define resolvers for individual fields within their GraphQL schema seamlessly.
Use a Data Source
In a GraphQL API, information is commonly sourced from various repositories, such as databases or external interfaces. Laravel facilitates connections with diverse data sources, including MySQL, MongoDB, and external APIs.
Use a Caching Mechanism
In a GraphQL API, caching serves to enhance performance by minimizing requests to the data source. Laravel provides seamless integrations with caching mechanisms such as Redis and Memcached. Leveraging these integrations can significantly enhance the efficiency of data caching within a GraphQL API.
Use a Security Mechanism
In a GraphQL API, ensuring security is paramount to safeguard against potential attacks and unauthorized access. Laravel offers seamless integrations with various security mechanisms, including JWT and OAuth, which can be effectively employed to fortify the security of a GraphQL API.
7) Artificial Intelligence and Machine Learning
Laravel developers have the chance to harness the power of AI and machine learning technologies to create smart applications capable of adapting to user behavior and preferences through learning mechanisms.
AI and Machine Learning are rapidly evolving disciplines that are transforming business operations. Utilizing Laravel, a popular PHP framework, offers avenues for developing AI and ML applications facilitating data analysis, predictive modeling, and task automation.
When integrating AI and ML capabilities into Laravel, it's vital to keep the following key considerations in mind:
Use a Data Pipeline
To initiate AI and ML integration within Laravel, the primary step involves establishing a data pipeline capable of gathering, refining, and analyzing data. Laravel facilitates seamless integration with various databases such as MySQL and PostgreSQL, alongside other tools for data processing like Apache Spark and Kafka.
Use a Machine Learning Library
In a machine learning application, a machine learning library is typically employed to construct and train models. Laravel offers integrations with various machine learning libraries, including TensorFlow and Scikit-learn, enabling developers to build and train models seamlessly within Laravel applications.
Use a Prediction System
In a machine learning application, a prediction system is employed to generate forecasts using a trained model. Laravel provides a user-friendly prediction system that allows for making predictions utilizing the trained model.
Use an Automation System
In an AI application, an automation system is utilized to streamline tasks through data analysis. Laravel offers a straightforward automation system, facilitating the automation of tasks based on analyzed data.
Use a Natural Language Processing (NLP) Library
In an AI application, text data analysis and processing rely on NLP (Natural Language Processing) libraries. Laravel facilitates integration with various NLP libraries, including SpaCy and NLTK, enabling developers to analyze and process text efficiently.
Use a Computer Vision Library
In an AI application, a computer vision library is employed to analyze and process image and video data. Laravel offers integrations with various computer vision libraries, including OpenCV and TensorFlow, enabling developers to leverage these tools for image and video data analysis and processing.
Conclusion
Laravel has gained widespread popularity among developers for web application development due to its combination of features. Its user-friendly nature, robust security measures, scalability, and vibrant community support have solidified its reputation as a dependable framework for crafting bespoke web applications.
0 notes