#securuty
Quote
The ultimate security is found only in self-knowledge
- Nisargadatta Maharaj
11 notes
·
View notes
Text

#porteiro#guarda#securuty#safety#tencnico security#tecnico safety#motorista vip#ciencias veterinarias#auxilar veterinario#curso caes de raca perigosa ou potencialmente perigosa
0 notes
Text
We’re hurting steve tonight
#im going after his pride#his securuty in his relationship#his mental health#his physical health#im planning on sending him to therapy but baby boy is struggling HARD
6 notes
·
View notes
Text

I think He is really cute! (I'm sorry I don't know what his gender is) Hope you like it! >)@fluffffpillow
0 notes
Text

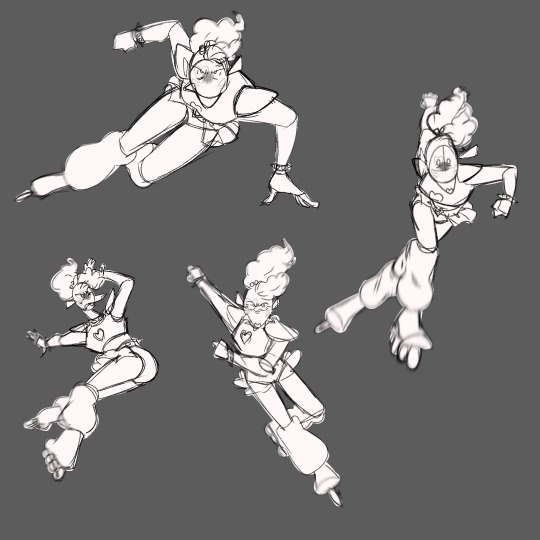
Working on a 31M x Securuty Breach au
(And another one 31MXFNaFSB where they take the roles of the existing animatronics)
I have drawn other designs for the 31M characters but Patana is the first one I wanted to work on, and I think she turned out well
Patana has skates bc I feel like Glamrock Chica deserves them
#31 minutos#patana tufillo#fnaf#fnaf security breach#security breach#glamrock#31m x security breach#31 minutos fanart
47 notes
·
View notes
Text
Drabblecember day 6: Wrapping gifts
Pairing: Sundrop (FNaF: Securuty Breach) x Starshine (My s/i)

Sundrop hummed a little as Starshine wrapped a present. It was sloppy, but hey! It was their first time! "Like this?" they asked, holding up the gift.
"Yes! You did amazing, friend!" Sundrop cheered, before adding, "Now it just needs a bow!"
He rustled around in a bag, pulling out the biggest red bow he could find. "Roxy will love it!" Starshine squealed as Sundrop stuck it on. Sundrop laughed happily, before starting to wrap a gift for Chica. Starshine scooted up against Sundrop, bonking her little star head against his sun head, much like a cat.
"I love you."
(psssst: @eternally-smitten yippee!)
3 notes
·
View notes
Text

mor funnh securuty guard :)
the au he was apart of combined a bunch of peoples different ocs so it got kinda chaotic but holy shit it was so fun. The story from myyyy understanding was liek. when the game is completed/reloaded the self aware ai get mixed up to different characters, so u wont have the same experience twice yknow? every character except for gman. n when he like got attached to tommy n everyone else n then they all lost their sentience he was kinda pissed n used the new ai characters to drag in more characters to get gordon (or in the au his brother John’s) attention to delete em when theyre in the game.
Anyways i still consider the whole completing the game and changing/erasing the ai thing canon and no one can prove me wrong!
#cool clown posting#quip :]#ten points if u know the au im talking about#it is somewhere on this godforsaken website#hlvrai#hlvrai gman
6 notes
·
View notes
Text
does cinnecting to open wifi over vpn provide securuty
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does cinnecting to open wifi over vpn provide securuty
Open Wi-Fi security risks
Open Wi-Fi networks are convenient for staying connected on the go, but they also come with significant security risks. These networks, often found in cafes, airports, and hotels, lack encryption, making it easier for hackers to intercept data transmitted between devices and the internet.
One of the most common risks associated with open Wi-Fi is the interception of sensitive information. When you connect to an open network, your data, such as login credentials, financial details, and personal messages, can be captured by cybercriminals. This can lead to identity theft, financial loss, or unauthorized access to your accounts.
Another concern is the possibility of malicious entities setting up fake Wi-Fi hotspots. These fake networks mimic legitimate ones to trick users into connecting to them. Once connected, hackers can launch attacks like phishing or malware injection to compromise devices and steal data.
Additionally, open Wi-Fi networks are often unsecured, allowing anyone within range to access them without authentication. This opens the door to various attacks, including man-in-the-middle attacks, where an attacker intercepts and alters communication between two parties without their knowledge.
To mitigate the risks associated with open Wi-Fi, it's essential to take precautionary measures. Using a virtual private network (VPN) encrypts your internet traffic, making it more difficult for hackers to intercept. Avoid accessing sensitive information, such as online banking or email accounts, while connected to open networks. Always verify the legitimacy of Wi-Fi networks before connecting, and consider using cellular data or personal hotspots for sensitive tasks when secure networks are unavailable.
By understanding the security risks and implementing best practices, you can protect yourself from potential threats while enjoying the convenience of open Wi-Fi networks.
VPN encryption effectiveness
VPN encryption is a critical component in ensuring the security and privacy of internet communications. It serves as a protective shield, safeguarding sensitive data from prying eyes and malicious actors. The effectiveness of VPN encryption depends on several factors, including the encryption protocol used, key length, and implementation practices.
One of the primary determinants of VPN encryption effectiveness is the encryption protocol employed. Popular protocols such as OpenVPN, IPSec, and WireGuard offer varying levels of security. OpenVPN, known for its open-source nature and strong encryption algorithms, is widely regarded as highly effective. IPSec, commonly used in enterprise environments, provides robust encryption and authentication mechanisms. WireGuard, a relatively new protocol, boasts simplicity and efficiency without compromising security.
Key length is another crucial factor influencing VPN encryption effectiveness. Longer encryption keys offer greater resistance to brute-force attacks, enhancing overall security. Common key lengths include 128-bit, 192-bit, and 256-bit. While 128-bit encryption provides adequate security for most purposes, 256-bit encryption offers an additional layer of protection, particularly against advanced threats.
Furthermore, the implementation practices of VPN providers play a pivotal role in determining encryption effectiveness. Providers should adhere to industry best practices, regularly updating encryption protocols and key management systems. Additionally, robust authentication mechanisms, such as multi-factor authentication, further bolster security.
It's important to note that while VPN encryption significantly enhances privacy and security, it's not infallible. Vulnerabilities in encryption algorithms or implementation flaws can potentially compromise the confidentiality of data. Therefore, users should carefully evaluate VPN providers, opting for reputable services with a track record of prioritizing security.
In conclusion, VPN encryption serves as a crucial safeguard in protecting sensitive data from unauthorized access. The effectiveness of VPN encryption depends on factors such as encryption protocol, key length, and implementation practices. By selecting a reliable VPN provider and adhering to security best practices, users can mitigate risks and enjoy enhanced privacy online.
Public Wi-Fi vulnerabilities
Public Wi-Fi networks have become ubiquitous, offering convenience and connectivity on the go. However, along with the benefits come significant security risks. Public Wi-Fi vulnerabilities pose a serious threat to users' personal information and sensitive data.
One of the primary concerns with public Wi-Fi is the lack of encryption. Unlike private networks, public Wi-Fi hotspots often do not encrypt data transmitted between the user's device and the router. This makes it easy for hackers to intercept and access sensitive information such as passwords, credit card numbers, and personal emails.
Another vulnerability is the presence of rogue hotspots. Cybercriminals can set up fake Wi-Fi networks with names similar to legitimate ones, tricking users into connecting to them. Once connected, hackers can eavesdrop on communications and steal data without the user's knowledge.
Man-in-the-middle (MITM) attacks are also a common threat on public Wi-Fi networks. In these attacks, hackers intercept communications between the user and the intended destination. This allows them to view, modify, or even inject malicious content into the data stream.
Furthermore, unpatched or outdated software on public Wi-Fi routers can expose users to additional vulnerabilities. Hackers often exploit known security flaws in router firmware to gain unauthorized access and launch attacks against connected devices.
To mitigate these risks, users should take proactive measures when using public Wi-Fi. This includes avoiding sensitive transactions such as online banking or shopping, using virtual private networks (VPNs) to encrypt internet traffic, and ensuring devices have up-to-date security software installed.
In conclusion, while public Wi-Fi offers convenience, it also presents significant security challenges. By understanding and addressing these vulnerabilities, users can better protect themselves from potential cyber threats while staying connected on the go.
VPN tunneling protection
Title: Enhancing Online Security with VPN Tunneling Protection
In today's digital landscape, where online privacy and security are of paramount importance, utilizing VPN tunneling protection has become essential for safeguarding sensitive data and ensuring anonymity while browsing the internet.
VPN (Virtual Private Network) tunneling is a technique used to create a secure and encrypted connection over a less secure network, such as the internet. It establishes a "tunnel" through which your data travels, making it virtually impossible for anyone to intercept or decipher.
One of the primary benefits of VPN tunneling is its ability to protect against hackers, identity thieves, and other malicious actors who may attempt to intercept your data while it's in transit. By encrypting your internet traffic, VPN tunneling ensures that your personal information, such as passwords, credit card numbers, and browsing history, remains confidential and secure.
Moreover, VPN tunneling allows users to bypass geo-restrictions and censorship imposed by governments or internet service providers. By connecting to a VPN server located in a different country, users can access content that may be blocked or restricted in their region, ensuring unrestricted access to information and online services.
Furthermore, VPN tunneling provides an additional layer of security when using public Wi-Fi networks, such as those found in cafes, airports, and hotels. These networks are often vulnerable to cyber attacks, but with VPN tunneling, users can encrypt their connection and protect themselves from potential threats.
In conclusion, VPN tunneling protection is a powerful tool for enhancing online security and privacy. By encrypting internet traffic, bypassing geo-restrictions, and securing connections on public Wi-Fi networks, VPN tunneling offers users peace of mind and confidence in their online activities. Whether you're browsing the web, accessing sensitive information, or streaming content, VPN tunneling ensures that your data remains safe and secure.
Secure internet access practices
Secure internet access practices are crucial in today's digital age to protect your personal and sensitive information from cyber threats. By following a few simple protocols, you can significantly reduce the risk of falling victim to online attacks and safeguard your data.
First and foremost, using strong, unique passwords for each of your online accounts is essential. Avoid using easily guessable passwords such as "123456" or "password." Instead, opt for a combination of letters, numbers, and special characters to create a secure password that is hard to crack.
Furthermore, enabling two-factor authentication adds an extra layer of security to your accounts. This means that even if your password is compromised, a second form of verification is required to access your account, making it much harder for hackers to gain unauthorized entry.
When browsing the internet, be cautious about the websites you visit and the links you click on. Avoid clicking on suspicious links or downloading attachments from unknown sources, as they may contain malware or ransomware that can compromise your device and data.
It is also advisable to use a virtual private network (VPN) when connecting to public Wi-Fi networks. A VPN encrypts your internet traffic, preventing hackers from intercepting your data while using public Wi-Fi, thus ensuring a secure connection.
In conclusion, practicing secure internet access habits is essential for protecting your online privacy and security. By implementing these simple yet effective measures, you can minimize the risk of falling victim to cyber threats and enjoy a safer online experience.
0 notes
Text
someone complained to security about me 'taking stuff' (ive not touched any shelves) in the grocery store today. and the securuty guard was like, trying to justify that persons accusation to me?? like saying "you look pretty weird in that big coat and that hat" like man???? are guys not allowed to be weird anymore??????

would you report this guy to security because he walked by you in the grocery store
#to be clear#i wasnt even planning on theft#and its like. weird that someone decided to lie to security about me#i didnt even talk to anyone. i was walking around the store
1 note
·
View note
Text
Babinsa Kel. Ngesrep (Pelda Ari Cahyanto) melaksanakan Senam Bersama Securuty Perumahan Citra Sun Garden di Jln. Sun Garden RW.11 Kel. Ngesrep Kec. Banyumanik.
https://www.instagram.com/p/CsfJl22vazW0ApEiTquOBT9OnHyG7M3LK4_srA0/?igshid=MTc4MmM1YmI2Ng==
1 note
·
View note
Text
So, today in class we were studying a poem of Umberto Saba, where he described his traumas as emerald-green beautiful rocks in the sea (which represent the obstacles of navigating too close to the shore/securuty)
And one of my classmates asked: "but why would someone find their traumas attractive or beautiful"
My mind immediately went: "well, it's normal"
It is not normal
And luckily I didn't say it out loud because I also realised that not everyone has experienced trauma in their life.
Nice🙃
#trauma#funny not funny#poetry#school#it's always entertaining watching my neurotypical/mentally stable classmates trying to understand traumatised artists#the problem tho is when the teachers are also neurotypical/mentally stable so they interpret art in a way that makes zero sense#but what can ya do
1 note
·
View note
Text
Guida Tv Mercoledì 5 ottobre
Guida Tv Mercoledì 5 ottobre
Attenzione! Eventuali cambi di programmazione dell’ultimo minuto, dati da eventi eccezionali, non sempre possono essere riportati!Programmazione delle principali emittenti televisive per la sera:
Rai Uno: Il cane di terracotta (Montalbano)
Rai Due: Delitti in Paradiso
Rai Tre: Chi l’ha visto?
Rete 4: Controcorrente
Canale 5: Emigratis
Italia 1: Securuty
La7: Una giornata particolare
Tv8:…

View On WordPress
0 notes
Text
Android-Pfd-Sdk-Jfk-Atomic UserX-utm_resourse-c-++/D++/<\A> ~{{html}}} [[ 333√4566√]] °^°|\=Ufo- Satellite.Com/Securuty Boeing.com/#boihasbullah Appolo-13- T4-Robotic **<\co3e>**\\ {{ Rss.com/feed/nasa-230√543√= Nucler Titanuim.com/sd4/iso-irs=SpaceX
www.adobe.com/en/securityn www.pdf.com/#android

Boihasbullah Ngadi Supported Google Giggle Groups LLC www.company.com www.smart.com/inteligent @Bullhustler #Nasa #
0 notes
Text
“well done superstar :]c” glamrock freddy i would fucking kill for you
249 notes
·
View notes
Link
Android is one of the operating systems most affected by hacking attacks due to its huge position in the market. For this reason, Goog...
0 notes
Text
me, turning off all the lights in the house and getting into bed to read Security: Self Care™
@dindjarindiaries expect reblogs :)))
#molly ily#securuty chap 3 here i come#hope i will have the braincells to finish it#ive been experiencing major brainrot 😔
3 notes
·
View notes