#yubikey supported
Text
Yubikey.Support for 2-Factor Verification | Yubikey Support
Check out YubiKey's strong support for 2-factor verification. Use hardware-based authentication to increase your online security. YubiKey Support offers dependable setup and troubleshooting support. Your route to better online safety.
With YubiKey's capability for 2-factor verification, security is enhanced. Use this reliable hardware-based solution to protect your internet presence. Get timely support for installation and troubleshooting to guarantee a secure digital experience. Your ideal ally in security.
#yubico support#yubikey support#yubikey supported#yubikey supported services#yubico customer service
0 notes
Text

Xác thực 2 yếu tố là phương pháp cho phép các dịch vụ máy tính và người dùng sử dụng nhiều phương pháp xác thực đề định danh cũng như bảo vệ tài khoản
Yubikey là một loại khoá bảo mật được cung cấp bởi công ty Yubico. Đây là loại khoá bảo mật vật lý phổ biến bậc nhất của thị trường, thường được sử dụng để xác thực hai yếu tố (2FA) và xác minh không cần mật khẩu, giúp người dùng đăng nhập tài khoản thuận tiện hơn mà vẫn đảm bảo tính bảo mật.
0 notes
Text
How To Wipe Out All The Data On An YubiKey In One Gesture

What happens when I touch my YubiKey?
When you touch your YubiKey, it sends a very weak 5v signal to your computer. The signal is only strong enough to trigger a response from the YubiKey. You can think of this like an electric doorbell: A doorbell sends out a short burst of high-voltage AC power when it's pressed; when the low-voltage AC voltage hits the contacts of the receiver (which may be an electromagnet), it causes them to momentarily close and send out DC power that pushes through wires back to your house's main circuit breaker box which then turns on an LED lamp as part of an interlock system that prevents any power from coming through unless someone presses the doorbell button first.
Does YubiKey work without the Internet?
Yes, YubiKey Support can be used without any internet connection. The YubiKey has all the data that you need to be stored on the device in an encrypted manner. Only when you want to login into a site or service will it ask for the data from your key and then it decrypts it using a password or PIN which you entered earlier.
What is the difference between YubiKey and the security key?
YubiKey does not use public-key cryptography. Instead, it creates a challenge-response code that is unique to the device and thus cannot be spoofed. YubiKey is more effective than standard passwords and PINs at mitigating phishing, man-in-the-middle attacks, replay attacks, and other situations where a thief can intercept or steal your credentials.
How many passwords can YubiKey hold?
Yubico's YubiKey can hold up to 32 unique credentials, in addition to a single PIN. If you use Yubico apps and services that require more than 32 credentials, your master password can be used as an override to let you switch between them.
How do I use YubiKey for personal use?
YubiKey for personal use is designed for the everyday user that wants to protect and secure their online accounts. YubiKey can be used to replace passwords, 2FA codes, or other secrets to help prevent unauthorized access.
YubiKey is a security key that protects you against phishing and hijacking. With FIDO standards-based strong authentication, it can be used to securely login to your favorite websites, computers, and applications.
#yubico support#yubikey support#how does yubikey work#yubico customer service#yubikey supported services
0 notes
Text
1. How to setup 2FA on your accounts
As some of you may know, my friend @why-its-kai's Discord account was taken over this morning by a scammer.
The scam they used was this one, or close enough; but anyway, the exact specifics don't matter.
What matters is, it can happen to you. It can happen to anyone.
The good news is, you can learn how to protect yourself. Making some small changes can already improve your online security by leaps and bounds.
I made a series of 3 posts covering the basics:
How to setup 2FA on your accounts (you are here!)
How to spot a scam
How to set up a password manager.
Protect yourself with 2FA
Two-factor authentication, or 2FA, isn't a silver bullet -- but it exponentially increases your online safety by adding an extra step to the login process that a hacker/scammer does not have access to.
Every account that you care about (and even those you don't) should have some form of 2FA enabled.
Especially email -- should your email become compromised, this can become a catastrophe.
(For websites that don't support 2FA, use a burner email!)
What 2FA should I use?
2FA can take many forms, from the highly convenient (SMS, email) to the highly secure (security keys), but one thing is certain:
Any form of 2FA is better than nothing.
The simplest forms of 2FA are phone number or email. While these are very easy to use, they are unfortunately not very secure.
Still, I repeat: despite their flaws, these forms of 2FA are absolutely, 100% better than not having any 2FA at all.
On the other end of the spectrum, security keys (like for example a Yubikey) are extremely secure, but they cost money and are a bit of a hassle at time. I use them, but for most people, it's overkill.
What you want is an authenticator app.
Important
A note, before we go on…
If you enable multiple forms of 2FA, how secure your account is will depend on your weakest link.
For example, if you enable SMS authentication AND register a security key, your account will only be as safe as the SMS authentication. The security key is essentially useless.
In other words, the least secure form of 2FA you add determines the overall security of your account.
Sometimes, less is more!
Authenticator Apps
First, choose a free, reputable authenticator. Google Authenticator is a good choice. So are Aegis Authenticator or Microsoft Authenticator.
For simplicity, we'll go with Google Authenticator; the process is rather similar for most authenticators.
First, download the app from your app store and install it on your phone.
Enrolling Gmail into GA
Securing your email should be your number 1 priority, so let's enroll a Google account to Google Authenticator.
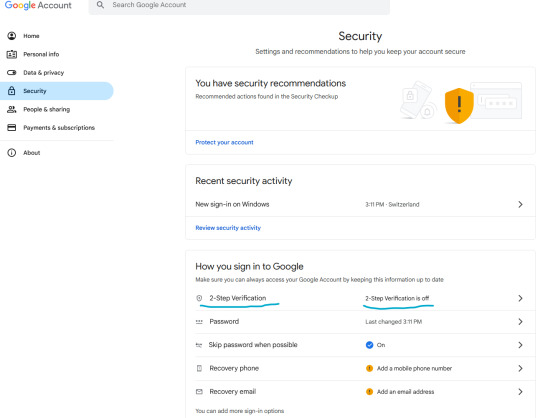
Let's enable two-step verification first.
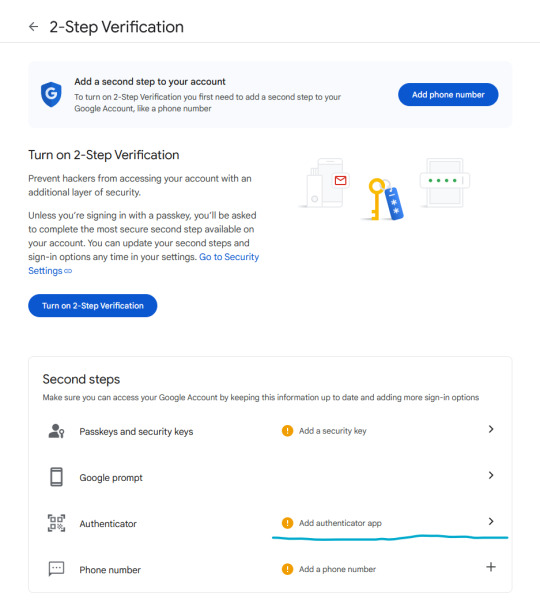
Phone number is better than nothing, but not very safe (SMS verification can be spoofed), so let's click on "Add authenticator app".
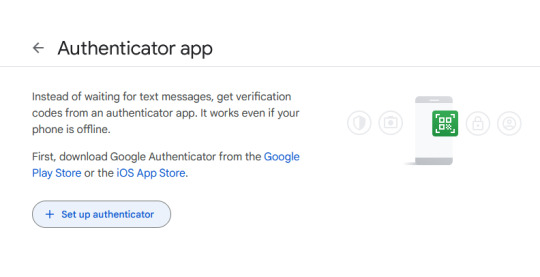
Click on "Set up authenticator". Google will generate a QR-code.
Next, go back to your phone and click on the little multicolored cross. It will bring up a menu; click on "scan a QR code".
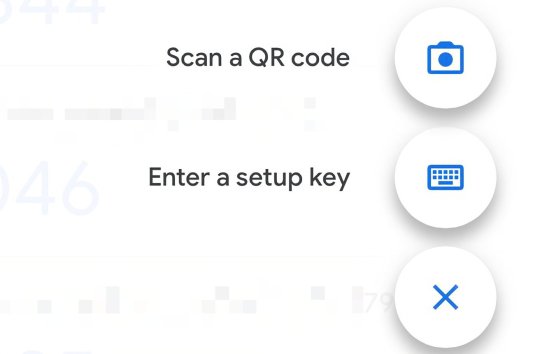
Go ahead and scan the QR code.
Congratulations, you have enrolled your Google account!
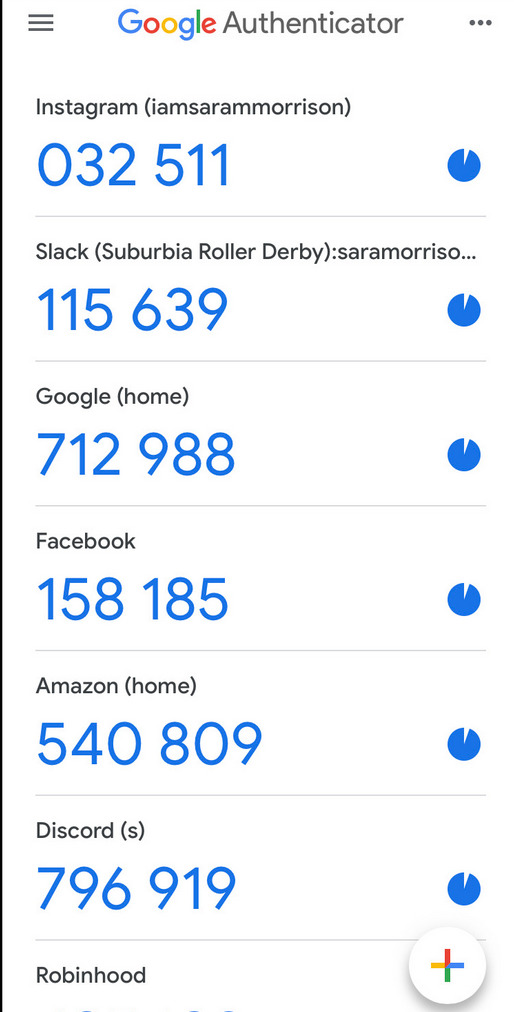
Now, whenever you are asked for a 2FA code, just open the app and copy/paste it.
Note: the codes are stored locally on your phone.
Enabling 2FA on Discord
The process is fairly similar. Go to Settings > My Account:
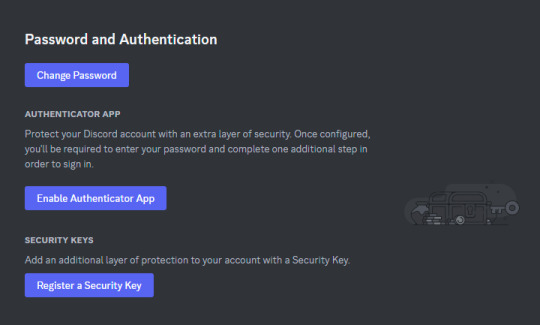
Click on "Enable Authenticator App". You will be prompted for your password. Enter it.
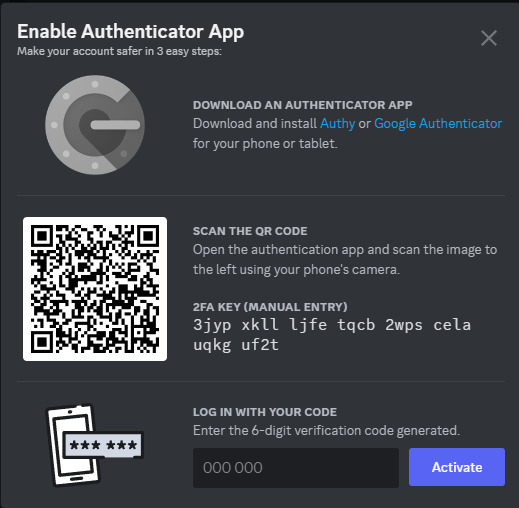
Download Google Authenticator if you haven't already. Scan the QR code as described above.
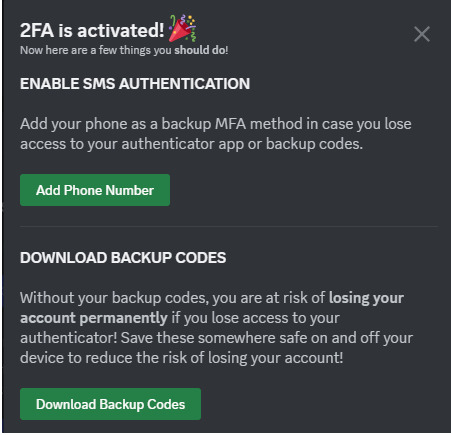
Do take the time to download your backup codes as well!
As explained above, I personally do not recommend setting up SMS authentication here, since authenticator apps are supported, as this weakens the overall security of your account for little benefit.
Stay tuned for parts 2 and 3!
If you have any questions, feel free to PM me.
15 notes
·
View notes
Text
6 notes
·
View notes
Text
Setup Yubikey 2FA on Debian 11
So you want to harden security by enabling two-factor authentication using Yubikey.
WARNING: VERY REAL RISK OF LOCKING YOURSELF OUT! MAKE SURE YOU KNOW WHAT YOU'RE DOING AND HAVE BACKUPS!
This guide will set up the so-called Challenge Response OTP mode. The online mode which require access to internet + Yubikey registration is out of scope.
Read the whole guide and then proceed step by step.
In a separate terminal get root console and keep it open in case you need to rollback changes (don't do anything in it):
$ sudo -s
Install Yubikey personalization package:
$ sudo apt install yubikey-personalization
Install "libpam-yubico" package:
$ sudo apt install libpam-yubico
Configuration of the Yubico PAM module will be requested. Enter this (do not enable anything!):
mode=challenge-response
Check installed package contents (will be useful later):
$ dpkg -L libpam-yubico
The main document of interest is
/usr/share/doc/libpam-yubico/Authentication_Using_Challenge-Response.adoc.gz
Read it as this guide is heavily inspired on it.
Plug in your Yubikey now.
Setup the slot #2 of the Yubikey for the OTP challenge-response mode:
$ ykpersonalize -2 -ochal-resp -ochal-hmac -ohmac-lt62 -oserial-api-visible
This should generate a challenge-<digits> file in ~/.yubico/ directory.
This file is critical and should be protected.
$ chmod 600 ~/.yubico/challenge-<digits>
Return to libpam-yubico configuration and enable Yubikey support (first choice):
$ sudo dpkg-reconfigure libpam-yubico
Make sure the mode string is entered as shown above, asterisk is set next to Yubikey support and hit <Ok>.
Check PAM configuration:
$ cat /etc/pam.d/common-auth
You should see a line:
auth required pam_yubico.so mode=challenge-response
Now run the PAM update utility (read the man page):
$ sudo pam-auth-update
Open a new terminal and try running a sudo command:
$ sudo echo "It works!"
Enter your user password and notice green LED on the Yubikey lighting up. Remove the Yubikey, open another terminal and try to log in - it should fail.
You now have hardened system which requires two-factor authentication!
To troubleshoot issues, use the following mode line:
mode=challenge-response debug
Follow the same steps of the guide. Each sudo call will get a verbose log written to the console.
To uninstall, edit "/etc/pam.d/common-auth" to its previous state. Run pam-auth-update. Check log in works without a Yubikey.
2 notes
·
View notes
Text

Enhance Your Security Architecture with YubiKey 5C Nano—Find It at Otcer.ph!
For Php 6,665.00, the YubiKey 5C Nano transforms your security architecture with its advanced, compact design. Designed to support critical security protocols seamlessly, it ensures your enterprise remains agile and secure against emerging threats. Perfect for businesses that prioritize efficiency and robust defense mechanisms. Start securing your future today at https://otcer.ph or via Viber/WhatsApp: +63 919 839 9123.
#AdvancedSecurityArchitecture #CompactEfficiency #AgileProtection
0 notes
Text
Securing Your Token with Hardware Devices
Hardware tokens, also known as security keys, are physical devices used to gain access to secure networks or systems. They serve as a form of two-factor authentication (2FA), requiring both a token and a password or PIN for access. Common types of hardware tokens include USB devices, key fobs, and smart cards.
The benefits of using hardware tokens are substantial. They are immune to phishing attacks since the authentication information they provide cannot be easily retrieved by malicious actors. Additionally, they do not rely on codes sent via text or email, which can be intercepted or delayed. Users can authenticate their identity swiftly and securely with a simple press of a button or a touch.
When choosing a hardware token, consider factors such as compatibility with your systems, supported connection types (USB-A, USB-C, Bluetooth, or NFC), and adherence to security protocols and authentication standards like FIDO U2F. For instance, the Yubico YubiKey 5 NFC is a widely recognized security key that offers a balance of durability, portability, and ease of use.
For both businesses and individuals, implementing hardware tokens can significantly enhance security. They provide a reliable and efficient way to protect devices and sensitive information from unauthorized access.
In cybersecurity, physical security measures like hardware tokens are just as important as digital precautions. Stay safe and secure!
0 notes
Text
KeePassXC Debian package situation
gemini://namno.duckdns.org/blog/2024-05-15.gmi
On 23rd of April 2023 Julian Andres Klode, Debian maintainer of keepassxc package have removed all networking and IPC features, including support for YubiKeys, from that package, following a very slow-flowing bugreport thread that complained that additional features may increase attack surface. Additionally, keepassxc-full package was created, that retained all these features.
I consider this move to be misguided and harmful for following reasons:
Everyone expects full KeePassXC by default
In one of the threads created following this decision Julian have said that he would expect complains for a year because no one reads NEWS file. He is correct that no one reads NEWS file (or knows about it in general) but he is wrong in his estimate of complains. Complains will not stop after a year, they will continue until keepassxc package stops giving people cut-down version of KeepPassXC, like it does on all other distros.
KeePassXC is advertised with all these features, they are the main reason to choose this package manager over any other. Even Debian package description mentions them:
>In contrast to KeePassX (package keepassx), KeePassXC is actively developed and has more features, e.g., connectivity to a Web Browser plugin (package webext-keepassxc-browser).
https://packages.debian.org/testing/keepassxc [HTTPS]
If someone needed "more secure" option, they could have picked one of the many alternatives that support same database format, but without features that are unnecessary for them. So the only useres that this "benefit" are those who don't know difference between different package managers and just install what's popular, in which case they probably are even more confused as to why their version of program doesn't work like it does for other people.
These are not plugins
Many other people defended this decision by saying that many other Debian packages do not include plugins by default. First of all, there is plenty of packages that have (1st party) plugins included in their package, or as a dependency.
Second of all. they are not plugins. They are #ifdef-ed pieces of code, that only tested with all of them enabled. Option to disable all of the options (as is the current debian situation) is tested only for its ability to compile and no further. This leads to my third point.
Disabling everything decreases safety
Many features disabled by Julian are necessary for keeping the security. From physical USB keys, to browser plugin, that among other things helps distinguishing between real and phishing sites, they activly increase security. Disabling these features leads to users opting into less secure options, like transfering password using clipboard.
Conclusion
I hope that Julian eventually reevaluates his decision and if not reenables these features in main keepassxc package with optional keepasssc-core/minimal/whatever package that you could opt in, at least enables some of the features that actually provide security, like browser integration or secret provider. I also hope that Debain stops thinking that they are center of the universe and stops breaking packages for no good reason.
0 notes
Text

Yubikey.Support for 2-Factor Verification | Yubikey Support
Experience heightened security with YubiKey's 2-factor verification support. Safeguard your online presence using this robust hardware-based solution. Receive prompt assistance for setup and troubleshooting, ensuring a secure digital journey. Your ultimate security companion.
Discover the power of YubiKey support for seamless 2-factor verification. Enhance your online security with this hardware-based authentication solution. Get quick and reliable assistance for setup and troubleshooting. Your key to a safer digital experience.
#yubikey support#yubikey support Service#yubikey supported#yubikey supported services#yubico customer service
0 notes
Text
I was just checking a text file with my notes about which of my several yubikeys I had used for what purposes, when I came across the following:
" FTX - USB-A key (only allows one key)"
I wonder if they ever got around to supporting registering multiple yubikeys before they collapsed.
1 note
·
View note
Text
[Media] YubiKey
YubiKey
The Yubico Security Key is a heavy-duty, tamper-resistant USB and NFC security key designed to protect online accounts against unauthorized access.
It supports FIDO2, FIDO U2F, and other protocols, works with a wide range of online services, and is water and shock-resistant.
With touch-based authentication, it provides an easy and secure way to protect your online accounts from phishing and account takeovers.
Buy online:
🛒 https://amzn.to/3L0xdJL
🛒 https://ali.ski/qAF720
#security #key #usb

0 notes
Text
Multi-factor authentication (MFA)
Multi-factor authentication (MFA) must be enabled on each University member's account.
An additional layer of security for online accounts is multi-factor authentication (MFA).
Also Read:Click here
MFA aids in safeguarding your financial and personal data. Using MFA lowers the chance that someone will access your account even if they learn your login and password, for instance through a scam or cyberattack.
According to Microsoft research, MFA can cut down on these assaults by up to 99.9%.
MFA is a requirement of the rules you accepted when you signed your student agreement (if you are a student) or your work contract, generally speaking (staff).
Set up MFA using an authenticator app (recommended)
We advise you to utilise the Microsoft Authenticator app for the best results. Even if you transfer SIM cards or do not have data roaming enabled, you can use the Microsoft Authenticator app when travelling.
You are free to use another authenticator software if you'd prefer, but be aware that IT Services might not be able to support it.
You will need:
Your smartphone (connected to a strong data signal, wifi, or eduoram if you're on campus), a computer or tablet with internet access. You must use the laptop or computer provided by the university if you are a staff member or postgraduate research student.
A single smartphone with a wifi or data connection can be used to set up MFA if you are an undergraduate or postgraduate taught student.
Set up MFA without a smartphone
computer or tablet.
Please log out first if your Microsoft account with the university is not your default account.
Make sure to link it to your university username and password on your Microsoft account at the University of Bristol.
Use the syntax [email protected] to access your University of Bristol account.
your password, too.
The security information page for "my sign ins" will now appear.
After logging in, select "add method."
Pick "phone" from the drop-down menu, then click "add."
Enter your phone number after choosing your country code. Choose either "call me" or "text me a code."
Please don't input your phone number with the beginning "0" (for example, enter 7912345678 for a UK number).
To confirm your MFA setup, enter the code that was texted to your phone number.
You can then choose to make a phone call or send a text as the default authentication method on the security page (SMS).
You will now be required to validate your login across a number of University services during the next 24 hours. During this time, you ought should still be able to sign in.
You may see an example of MS MFA enrollment in action in this Microsoft video: Video: Configure Microsoft's multi-factor authentication with a mobile device
Set up MFA without a mobile phone
A USB security key can be used to configure MFA and authenticate if you are unable to do so using a mobile device (YubiKey).
The Arts and Social Sciences Library's IT Services Counter is where students can pick up their USB security keys. From Monday through Friday, from 9 am to 11.30 am and 2 pm to 3.30 pm, the counter is open. To obtain a security key, you must present your student identification card. If you require a security key after these hours and are unable to access your university account, please call IT Services at (available 24 hours a day at) 0117 428 2100 or submit a ticket through the IT self-service site (requires log-in).
You can also purchase a USB security key on your own. This FIDO2 YubiKey security key must be blue.
Employees can request a security key by getting in touch with IT Services.
Note:We suggest you to set up a backup authentication mechanism in case you misplace your security key if you use one as your primary login method.
By doing this, you'll be able to keep working while a new key is being ordered.
Set up a second MFA method
Some University services could be temporarily unavailable to you if you:
Never use your MFA phone or device again.
You misplace or damage your phone or other gadget.
Purchase a new phone (or other device) and improperly configure MFA on the new device
Have SMS or phone call authentication configured as your primary authentication method before leaving the UK. Text messages are often unreliable, especially when you're on the go.
Never use your MFA phone or device again.
You misplace or damage your phone or other gadget.
Purchase a new phone (or other device) and improperly configure MFA on the new device
Have SMS or phone call authentication configured as your primary authentication method before leaving the UK. Text messages are often unreliable, especially when you're on the go.
If you have more than one device
We advise you to install the Microsoft Authenticator software on your second device if you have more than one (for instance, a smartphone and a tablet or laptop). To set up the second device, log into the Microsoft Security Information page on your primary device, click "Add sign-in method," and then follow the on-screen instructions.
If you do not have a second device
We advise adding a second authentication method even if you don't have a second device. Click "Add sign-in method" after logging in to the Microsoft Security Information page, then follow the on-screen instructions.
If you need to travel
Please utilise an authenticator app as your default sign-in method if you need to access University services while travelling. Make sure the authenticator app is selected as the "Default sign-in method" when accessing the Microsoft Security Information page.
You can get a one-time code in the app if you don't have data while travelling. To view the one-time code, simply open the app and select "University of Bristol."
Help and support
Multi-factor authentication (MFA) tips are available, including how to sign in with MFA and set up MFA on a new phone.
Please call IT Services at 0117 428 2100 (available 24 hours a day), or submit a ticket through the IT self-service site, if you require additional assistance (requires log-in).
On weekdays from 8 am to 5 pm, more technical questions, such as how to reset MFA if you've misplaced your phone or authentication device, can be addressed (apart from on University closure days).
Please use the IT self-service website to raise a ticket if it occurs after business hours.
1 note
·
View note
Text
239 - Use Security Key to Unlock Your iPhone With Guest Guy Serle and Ben Roethig
The latest In Touch With iOS with Dave.He is joined by guests Guy Serle and Ben Roethig. iOS16.3 was released to the public this week notably Apple added Security Keys providing enhanced security using a Yubikey. The Mac Mini M2 256GB SSD is slower than the previous model. Tips include how to report spam texts and bonus sending the report to your carrier. Apple still provides security updates to older devices and there are Apple web based user guides for your devices.
The show notes are at InTouchwithiOS.com
Direct Link to Audio
Links to our Show
Click this link Buy me a Coffee to support the show we would really appreciate it. intouchwithios.com/coffee
Another way to support the show is to become a Patreon member patreon.com/intouchwithios
Website: In Touch With iOS
YouTube Channel
In Touch with iOS Magazine on Flipboard
Facebook Page
Twitter
Instagram
News
Apple gives some older iPhones OS updates, going back to iPhone 5s
iPadOS 15 drops support for newer iPads in 15.7.3 security update
If you own an older iPhone, you need to install this update ASAP to patch a dangerous flaw
Tweetbot Developer Tapbots Launches 'Ivory' App for Mastodon
Apple Preparing to Re-Release Revamped HomeKit Architecture That Was Removed From iOS 16.2
Gurman: Apple Not Working on New HomePod Mini
Apple Adjusts Trade-In Values for iPhones, Macs, and More
Apple Begins Selling Refurbished iPhone 13 Lineup in Europe, U.S. to Follow Soon
Apple pauses in-house Wi-Fi chip development
Topics
Beta this week. iOS16.3 has been released to the public this week. We will cover the new features and more.
Apple Releases iOS 16.3 With Security Keys for Apple ID, New HomePod Support, Bug Fixes and More
Security Keys in iOS16.3 Apple Explains iOS 16.3's New Security Keys Feature and Support article from Apple: About Security Keys for Apple ID
iOS 16.3 and macOS Ventura 13.2 add hardware security key support
iOS 16.3 Features: Everything New in iOS 16.3 - MacRumors
Apple Releases watchOS 9.3 With New Watch Face, Bug Fixes
Apple Releases HomePod 16.3 Software With Humidity and Temperature Sensing, Find My Improvements, Audio Tuning, and More
How to Use the Temperature and Humidity Sensors on HomePod and HomePod Mini
Apple Releases tvOS 16.3
iOS 16.3 fixes pesky CarPlay bug that broke Find My support in Siri
iOS 16.3 change review: Hardware security keys, HomePod feature updates, and more
In Touch with Mac topics
New 256GB Mac Mini and 512GB MacBook Pro Have Slower SSD Speeds Than Previous Models
Apple Releases macOS VNew 256GB Mac Mini and 512GB MacBook Pro Have Slower SSD Speeds Than Previous Models
This Mac app lets you link different Dock settings to different display setups
Apple's Mac security is so good, it's sending used M1 MacBooks to the scrap heap
CarPlay in EV’s. These are the best CarPlay apps for EV owners
How to fix HomePod and Home app repeatedly asking for your Apple ID password and failing to authenticate
Tips
Do you know Apple provides updated user guides for iPhone, iPad, Apple Watch, Apple TV?
Books
iPhone User Guide on Apple Books
iPad User Guide on Apple Books
Web Guides are always updated - You can add these to the home screen on your iPhone.
iPhone User Guide
iPad User Guide - Apple Support
Apple Watch User Guide
Apple TV User Guide
How to Copy & Paste between iPhone Apps Using Live Text. Some apps will not let you tap and copy text to paste it into another app. Here is how you get around that.
Take a Screenshot of this app screen
Go into photos and open the screenshot you just created. Tap onto the text and you will be able to copy that text. Then paste it into the app of your choice. Notes is usually a good place.
Report spam texts on iPhone. You can report them 3 ways
Use report spam here by tapping the link in the message
Swipe left to delete the message and select Delete and report Junk to Apple.
You also can report the message directly to your carrier. Tap and copy the message and paste it into a new message. In the To box enter 7726 and send the message. You will get a response from the carrier like this
Our Host
Dave Ginsburg is an IT professional supporting Mac, iOS and Windows users and shares his wealth of knowledge of iPhone, iPad, Apple Watch, Apple TV and related technologies. Visit the YouTube channel https://youtube.com/intouchwithios follow him on Mastadon @daveg65,
Twitter @daveg65.and the show @intouchwithios
Our Regular Contributor
Jeff Gamet is a podcaster, technology blogger, artist, and author. Previously, he was The Mac Observer’s managing editor, and Smile’s TextExpander Evangelist. You can find him on Mastadon @jgamet as well as Twitter and Instagram as @jgamet His YouTube channel https://youtube.com/jgamet
About our Guests
Guy Serle Is the host of the MyMac Podcast email [email protected] @MacParrot and @VertShark on Twitter Vertshark.com, Vertshark on YouTube, Skype +1 703-436-9501
Ben Roethig Former Associate Editor of GeekBeat.TV and host of the Tech Hangout and Deconstruct with Patrice Mac user since the mid 90s. Tech support specialist. Twitter @benroethig https://roethigtech.blogspot.com
Here is our latest Episode!
0 notes