#OWASP top 10 attacks
Text
มาตรวจสอบช่องโหว่ด้วย OWASP ZAP กัน
OWASP ZAP (Zed Attack Proxy) เป็นเครื่องมือที่ใช้สำหรับการทดสอบความปลอดภัยของแอปพลิเคชันเว็บ โดยสามารถใช้งานในการตรวจสอบช่องโหว่ความปลอดภัยต่างๆ ที่อาจเกิดขึ้นกับเว็บแอปพลิเคชัน ในกรณีที่คุณต้องการทดสอบความปลอดภัยของเว็บแอปพลิเคชันของคุณด้วย OWASP Zap นี่คือขั้นตอนที่คุณสามารถทำตามได้
ดาวน์โหลด OWASP Zap ได้จากเว็บไซต์ของ OWASP ที่ https://www.zaproxy.org/download/
เริ่มต้นใช้งาน OWASP Zap…

View On WordPress
0 notes
Text
Fortifying Digital Fortresses: A Comprehensive Guide to Cybersecurity
In today's digital landscape, where virtually every aspect of our lives is intertwined with technology, cybersecurity has emerged as a paramount concern. As the prevalence of mobile applications, web platforms, and interconnected networks continues to soar, the need to safeguard sensitive data and protect against malicious threats has never been more critical. In this comprehensive guide, we delve into the intricacies of various facets of cybersecurity, ranging from mobile application security to information security, offering insights and strategies to fortify digital fortresses against evolving cyber threats.
Mobile Application Security:
Mobile Application Security have become ubiquitous, serving as indispensable tools for communication, productivity, entertainment, and commerce. However, their widespread usage also makes them prime targets for cyberattacks. Mobile application security encompasses measures aimed at safeguarding the confidentiality, integrity, and availability of data stored and processed by mobile apps.
Secure Development Practices: Implementing secure coding practices during the development phase is crucial for mitigating vulnerabilities. Developers should adhere to established security standards and frameworks such as OWASP Mobile Top 10 to address common threats like insecure data storage, improper session handling, and lack of input validation.
Encryption and Data Protection: Utilizing robust encryption mechanisms to protect sensitive data both in transit and at rest is imperative. Employing techniques like end-to-end encryption and secure key management helps thwart unauthorized access and data breaches.
Authentication and Authorization: Implementing strong authentication mechanisms such as biometric authentication, multi-factor authentication (MFA), and OAuth ensures that only authorized users can access the application's functionalities and resources.
Regular Security Assessments: Conducting periodic security assessments, including penetration testing and code reviews, helps identify and remediate vulnerabilities proactively, ensuring the resilience of the mobile application against evolving threats.
Network Security:
Network Security focuses on protecting the integrity, confidentiality, and availability of data transmitted across networks, encompassing both internal and external communication channels. With the proliferation of interconnected devices and the advent of IoT (Internet of Things), securing network infrastructure has become increasingly complex.
Firewalls and Intrusion Detection Systems (IDS): Deploying firewalls and IDS/IPS (Intrusion Detection and Prevention Systems) helps monitor and filter network traffic, preventing unauthorized access and detecting malicious activities in real-time.
Virtual Private Networks (VPNs): Utilizing VPNs encrypts network traffic, safeguarding sensitive information from eavesdropping and man-in-the-middle attacks, particularly in untrusted or public network environments.
Secure Wi-Fi Networks: Implementing robust Wi-Fi security protocols such as WPA3 encryption, strong passphrase policies, and network segmentation minimizes the risk of unauthorized access and Wi-Fi-based attacks like rogue AP (Access Point) exploitation.
Regular Patch Management: Promptly applying security patches and updates to network devices, including routers, switches, and access points, mitigates vulnerabilities and strengthens the overall security posture of the network infrastructure.
Attack Surface Management:
Attack surface management involves the continuous assessment and reduction of an organization's attack surface—the sum of all points where an attacker can attempt to enter or extract data from an environment. With the expanding digital footprint fueled by cloud adoption, IoT proliferation, and interconnected systems, managing and minimizing the attack surface is paramount.
Asset Discovery: Conducting comprehensive asset discovery to catalog all devices, applications, and services within the organization's infrastructure helps identify potential entry points and vulnerabilities.
Vulnerability Management: Employing vulnerability scanning tools and automated assessments aids in identifying and prioritizing vulnerabilities based on severity and exploitability, enabling timely remediation efforts.
Configuration Management: Enforcing secure configuration baselines for devices, applications, and cloud services reduces the attack surface by eliminating unnecessary services, disabling default accounts, and hardening system settings.
Continuous Monitoring: Implementing robust monitoring solutions to detect and analyze changes in the attack surface in real-time facilitates proactive threat detection and response, minimizing the window of exposure to potential cyber threats.
Web Application Security:
Web application security serve as gateways to valuable data and functionalities, making them lucrative targets for cybercriminals. Web application security encompasses measures aimed at protecting web-based systems and applications from a myriad of threats, including injection attacks, cross-site scripting (XSS), and session hijacking.
Input Validation and Output Encoding: Implementing rigorous input validation mechanisms and output encoding techniques mitigates the risk of injection attacks such as SQL injection and XSS, preventing malicious payloads from being executed within the application context.
Secure Authentication and Session Management: Utilizing secure authentication mechanisms, such as strong password policies and session tokens with appropriate expiration times, prevents unauthorized access and session hijacking attempts.
Web Application Firewalls (WAF): Deploying WAF solutions helps filter and monitor HTTP traffic, detecting and blocking suspicious requests and malicious payloads before they reach the web application server.
Regular Security Testing: Conducting regular security assessments, including vulnerability scanning, penetration testing, and code reviews, helps identify and remediate security vulnerabilities proactively, ensuring the resilience of web applications against cyber threats.
Information Security:
Information security, often referred to as InfoSec, encompasses the protection of data assets against unauthorized access, disclosure, alteration, and destruction. With data being the lifeblood of organizations across all industries, maintaining the confidentiality, integrity, and availability of information is paramount.
Data Encryption: Employing encryption technologies to encrypt data at rest, in transit, and during processing safeguards sensitive information from unauthorized access and disclosure, mitigating the impact of data breaches.
Access Control and User Privilege Management: Implementing robust access control mechanisms, including role-based access control (RBAC) and least privilege principles, ensures that only authorized users can access and manipulate sensitive data.
Data Loss Prevention (DLP): Deploying DLP solutions helps monitor and prevent the unauthorized transmission of sensitive data, including intellectual property, personally identifiable information (PII), and financial records, both within and outside the organization's network perimeter.
Incident Response and Disaster Recovery: Establishing comprehensive incident response plans and disaster recovery strategies enables organizations to effectively respond to security incidents, minimize the impact of data breaches, and restore normal operations in a timely manner.
In conclusion, cybersecurity is an ongoing journey rather than a destination. By adopting a holistic approach encompassing mobile application security, network security, attack surface management, web application security, and information security, organizations can mitigate risks, safeguard critical assets, and foster trust in an increasingly digital world. Embracing proactive security measures, staying abreast of emerging threats, and fostering a culture of cybersecurity awareness are fundamental pillars in the ongoing battle against cyber adversaries.
0 notes
Text
The CCP's Organized Hacking Business
Today, on March 26, 2024, The US sanctions against the CCP hackers behind critical infrastructure attacks are widely reported. According to the indictment document:
"https://www.justice.gov/opa/media/1345141/dl?inline"
All of the Defendants indicted work for Wuhan Xiaoruizhi Science & Technology Co., Ltd. (武汉晓睿智科技有限责任公司) , a looks-like "civilian company" but actually created by the State Security Department of Hubei Province of China. China's enterprise registration information shows that the Company's business activities are "technology development, technical consulting, technology transfer, technical services, sales of high-tech products and accessories for high-tech products; design and system integration of computer information networks; import and export of goods, technology import and export, etc."

"http://www.21hubei.com/gongshang/whxrzkjyxzrgs.html"
Such too broad business description also appears in several MSS related "civilian-alike" companies but they were eventually revealed by the US government as the CCP's organized hackers.
Further research revealed that the CCP has been working on foreign web intrusion technology as a mission. Here is an example.
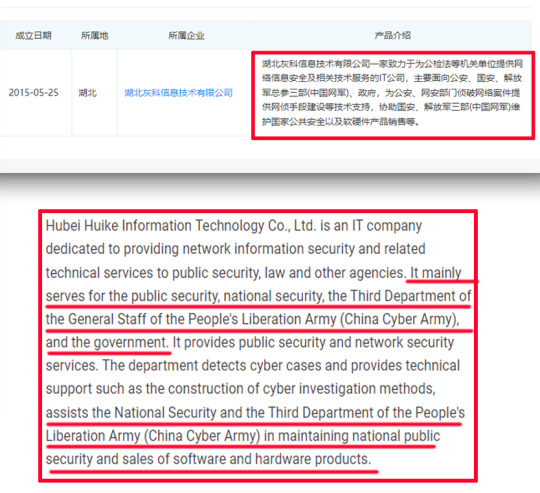
On China's enterprise search website Qcc.com/企查查, I found a company named "Hubei Huike Information Technology Co., Ltd/湖北灰科信息技术有限公司". The Company mainly serves for "China's public security, national security, the 3rd Department of the General Staff of the PLA (China Cyber Army) and the government"
"https://www.qcc.com/"
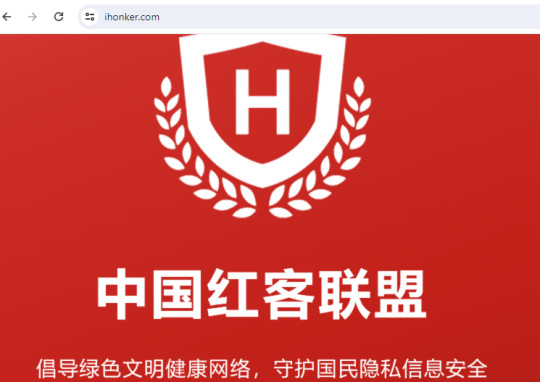
In 2016, the company posted its hiring information on ihonker/Honker Union/中国红客联盟 website:

"https://www.ihonker.com/thread-7922-1-1.html"
Here is the translation of the hiring requirements based on Google Translation:
"job requirements:
1. Be familiar with the steps, methods and processes of intrusion testing;
2. Be familiar with common attacks and defense methods, familiar with web security and intrusion technology, and be able to conduct web intrusion testing, WEB code vulnerability mining and analysis by yourself;
3. Be familiar with the working principles of mainstream operating systems, databases, networks and application systems, and fully master common security vulnerabilities and exploitation techniques;
4. Familiar with mainstream Web security technologies, including SQL injection, XSS, CSRF and other OWASP TOP 10 security risks;
5. Be familiar with mainstream domestic and foreign WEB security products and tools, such as: Nmap, SqlMap, Pangolin, APPScan, Inspect, wvs and other Web scanning tools;
6. Be able to build demonstration environments for various intrusion tests; be able to skillfully use various means to effectively intrude the system;
7. Familiar with the principles and operations of firewalls, IDS, IPS, vulnerability scanning, and intrusion testing, familiar with the configuration of switches and routers, and familiar with host system (unix, windows) security protection technology;
8. Proficient in using common intrusion tools, such as metasploit, etc.;
9. Have good teamwork spirit, professionalism, communication skills and document writing skills;
10. Proficient or familiar with one or more scripting languages such as perl/python/javascript/shell;
11. Applicants who can independently write relevant hacking tools, have published articles on well-known websites and forums, or have achieved excellent results in various competitions will be given priority.
12. No cybercrime record."
As you can see, the company targets web security vulnerabilities, focuses on intrusion and hacking.
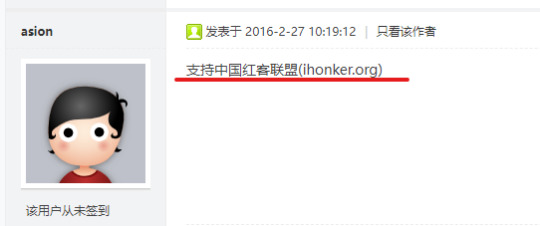
A reply to this hiring post indicated the Company's relationship with "中国红客联盟(ihonker.org). The reply says "Support ihonker.org".
"https://www.ihonker.com/thread-7922-1-1.html"
As per Baidu and Wikipedia, 中国红客联盟 is also known as H.U.C, Honker Union, a group for hacktivism, mainly present in China.
"https://baike.baidu.com/item/%E4%B8%AD%E5%9B%BD%E7%BA%A2%E5%AE%A2%E8%81%94%E7%9B%9F/837764"
"https://en.wikipedia.org/wiki/Honker_Union"
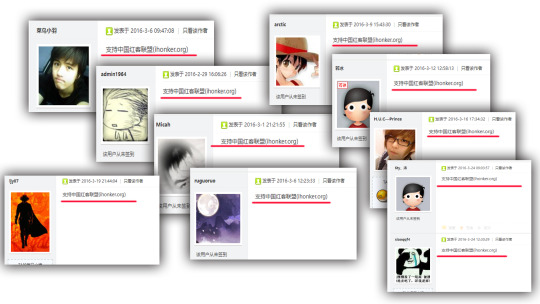
Although Wikipedia cited a source saying "there is no evidence of Chinese government oversights of the group" and the web address has changed, the "org" indication in the reply is pretty clear about the website's connection with China's government. The "support ihonker.org" reply to the China's-National-Security-related Company's post is overwhelming. The picture below reflects part of the same replies:
"https://www.ihonker.com/thread-7922-1-1.html"
A Mandarin social media based in Canada, iask.ca, aka 加拿大家园 listed some of Honker Union's attacks against foreign governments:
"April to May 2001: Counterattack against the US Internet... ...successfully counterattacked and captured the White House website, and even hung the five-star red flag on the official website of the White House"
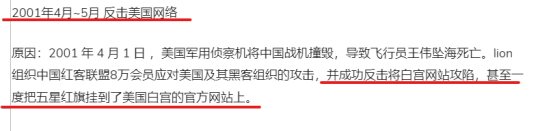
"https://www.iask.ca/news/240712"
"September 18, 2010 Attack on Japanese network"
"... ... launched a large-scale attack on Japanese government websites"

"https://www.iask.ca/news/240712"
China's government will surely deny its connection with such organized attacks, but the fact speaks for itself.
0 notes
Text
10 top cybersecurity books that should be on your bookshelf - CyberTalk
New Post has been published on https://thedigitalinsider.com/10-top-cybersecurity-books-that-should-be-on-your-bookshelf-cybertalk/
10 top cybersecurity books that should be on your bookshelf - CyberTalk
EXECUTIVE SUMMARY:
In an age of digital everything, do you even use a bookshelf anymore? Whether you read physical books, live on Kindle or are an Audible addict, our curated list of must-reads is designed to help you stay at the forefront of innovation and incorporate the best insights into your organization.
We’re excited to share brand new titles, with a handful of the classics interspersed within. These titles push the boundaries of conventional thought, delve into emerging trends, explain groundbreaking theories, and unveil urgent business strategies. You’ll find inspiration, enlightenment and profound opportunities for individual and business growth.
1. The CISO Desk Reference Guide Vol 1, 3rd Edition, by Bill Bonney, Gary Hayslip and Matt Stamper (2023). In every profession, there is a standard, go-to desk-reference guide that professionals can always rely on. In cyber security, The CISO Desk Reference Guide is that book.
Authored by seasoned practitioners, this guide provides new Chief Information Security Officers (CISOs) with valuable insights for effectively establishing a strong cyber security program.
This is the type of book that security professionals need to have on-hand when someone from the C-suite sends an urgent message demanding swift action and sage advice is required.
2. Enterprise Cybersecurity in Digital Business, by Ariel Evans (2022). In this modern masterpiece, core areas of discussion include cyber security tools, cyber security regulation, cyber security incident response, forensics and audits, GDPR, cyber security insurance, cyber security risk management, cyber security risk management strategy and vendor risk management.
This is not only a resource for cyber security professionals – it’s also an essential read for CEOs and other business stakeholders who wish to stay informed about the latest cyber security challenges and high-impact business solutions.
3. The Art of Deception: Controlling the Human Element of Security, by Kevin D. Mitnick (2003). One of the world’s most notorious hackers, Kevin Mitnick provides an insider’s perspective on security, as informed by his own cyber criminal past.
In The Art of Deception, he contends that firewalls and encryption protocols will never be enough to stop a savvy grifter who’s bent on breaching a corporate database.
Drawing on true stories, Mitnick vividly illustrates the vulnerabilities of even the most fortified information systems in the presence of a slick con artist (say, one posing as an IRS agent).
While this book is now 20 year-old, the material is as timely as ever. Most importantly, Mitnick imparts guidance around averting social engineering hacks through security protocols, training programs and more.
4. Hacking APIs, by Corey J. Ball (2022). For seasoned professionals, Hacking APIs offers valuable insight into the types of attacks that professionals may need to prevent and defend against as computing continues to evolve.
This book will prepare professionals for pen-testing APIs, succeeding within bug bounty programs, and securing APIs more effectively. Readers will also learn how REST and GraphQL APIs operate in the wild, and develop an API testing ‘lab.’
Further, readers will walk away with strong knowledge of tools that can prove useful for reconnaissance, endpoint analysis and fuzzing – think Kiterunner and OWASP Amass.
5. The CISO Evolution, by Matthew K. Sharp and Kyriakos Lambros (2022). This book aims to assist cyber security professionals in advancing their communication skills, particularly as they relate to interactions with management and boards.
Through engaging narratives, the authors guide professionals along a course to develop executive presence. They’re careful to elucidate nearly every pitfall encountered by technology experts when communicating with executives.
The CISO Evolution sets out to foster trust among senior business leaders by aligning and creating distinctive expectations around risk appetite, capital allocation and more.
Despite a title that appeals to the CISO audience, the book is intended for all types of security professionals, risk professionals, IT auditors and risk managers; anyone who seeks effective strategies that can put them on a path to better communication and stronger business outcomes.
6. A Hacker’s Mind, by Bruce Schneier (2023). Esteemed cyber security expert and New York Times best-selling author Bruce Schneier presents a treatise on the mind of the hacker, how we can reverse current hacking trends, understand the systems that underpin our society and bend the arc of history.
7. This is How They Tell me That the World Ends, by Nicole Perlroth (2021). The book reads like a John Le Carre thriller novel; part mystery, part commentary, part psychological analyses.
The author puts herself in the mind of hackers. What must it feel like to sell a zero day vulnerability? Who’s really buying these exploits? She dives into this underworld in a way that no reader could have ever anticipated.
As Perlroth weaves the story together, she describes the sensitive nature of journalistic research in relation to cyber space; at one point, she found herself enclosed in a windowless closet because of concerns about super spies who could intercept conversations with lasers.
8. Cracking the Blockchain Code, by Dikla Barda, Roman Zaikin and Oded Vanunu (2023). These experts from Check Point Software have over 15 years of professional experience each.
They wrote this book after observing a significant uptick in cyber criminal activity targeting blockchain platforms. In 2021, a staggering $14 billion in cryptocurrencies was stolen by hackers, according to CNBC research.
For those interested in blockchain and cryptocurrency, this book presents practical tools, labs and exercises designed to help readers recognize security vulnerabilities and understand the processes involved in the blockchain network.
Cracking the Blockchain Code provides a comprehensive toolkit for CISOs and security professionals, enabling them to enhance their teams’ readiness to address the evolving security challenges in the blockchain and cryptocurrency spaces.
9. The Smartest Person in the Room, by Christian Espinoza (2001). The author takes a critical look at the cultural aspects of the cyber security industry, which have been evolving across the past few decades.
Says Espinoza, “…in my more than thirty years of experience in cybersecurity and leadership, I found that…technical employees are the root of the problem,” pointing to the toxic cyber security culture found in some companies.
To address this issue, Espinoza proposes “The Secure Methodology,” a seven-step program for improving staff interpersonal skills and reducing their own personal insecurities, which contribute to a toxic culture.
With a knack for storytelling, Espinoza’s heart-felt and acutely perceptive advice is a salve for any struggling team.
10. Hands-on Artificial Intelligence for Cybersecurity: Implement Smart AI Systems for Preventing Cyber Attacks and Detecting Threats and Network Anomalies, by Alessandro Parisi (2019).
Modern organizations allocate substantial budgets to cyber security – billions of dollars annually. Artificial intelligence has emerged as a highly effective element that can be used in constructing more intelligent and secure systems.
This manual introduces widely adopted AI approaches that can be customized to identify potential attacks and to safeguard corporate systems.
Find out about integrating AI capabilities into the development of intelligent prevention and defense mechanisms. Strategies are applicable to spam filters, network intrusion detection, botnet detection and secure authentication.
After reading this book, professionals will be well-equipped to create intelligent systems that are capable of recognizing unusual patterns and attacks; effectively fortifying systems through the application of AI.
Are you a cyber security expert and published author with a book that you’d like to highlight in a future thought leadership article? We want to hear from you. Email us: [email protected].
#2022#2023#2024#Advice#ai#Analysis#API#APIs#arc#Art#Article#artificial#Artificial Intelligence#authentication#best cybersecurity books#billion#Blockchain#boards#book#Books#botnet#budgets#Business#C-suite#Check Point#Check Point Software#CISO#CISO evolution#CISOs#code
0 notes
Text
The OWASP IoT top 10 vulnerabilities and how to mitigate them

The Internet of Things (IoT) has catalyzed a technological revolution, embedding connectivity into our everyday objects. From smart homes to industrial systems, IoT devices have seamlessly integrated into our lives. However, this exponential growth in interconnected devices has unveiled significant security challenges. Recognizing these risks, the Open Web Application Security Project (OWASP) meticulously analyzed real-world incidents to compile the top 10 vulnerabilities plaguing IoT devices and ecosystems. Understanding and addressing these vulnerabilities are critical to fortifying the security of IoT environments.
Weak, guessable, or hardcoded passwords: IoT devices often harbor vulnerabilities due to default or easily guessed passwords. This oversight allows unauthorized access to sensitive data or device configuration. Mitigation involves implementing robust authentication mechanisms and encouraging users to set strong, unique passwords.
Insecure network services: Vulnerabilities within network protocols or configurations, such as unencrypted communication or outdated software, expose IoT devices to exploitation. Employing secure network protocols and conducting regular vulnerability assessments can help mitigate these risks.
Insecure ecosystem interfaces: Weakly secured interfaces between IoT components and external systems pose a significant threat. These interfaces can be exploited to gain unauthorized access or control over the device. Regular patching, access control enforcement, and encryption are recommended measures to counter this vulnerability.
Lack of secure update mechanism: Many IoT devices lack a secure update mechanism, leaving them vulnerable to known exploits. Implementing features like digital signatures and secure firmware validation can address this vulnerability.
Use of insecure or outdated components: Third-party components in IoT devices may contain vulnerabilities that attackers can exploit. Regularly updating and patching software and monitoring component vulnerabilities are essential practices.
Insufficient privacy protection: IoT devices often collect sensitive data without adequate privacy safeguards. Encryption, user consent for data collection, and privacy-by-design principles are crucial for mitigating this risk.
Insecure data transfer and storage: Transmitting or storing data without encryption exposes sensitive information to interception or manipulation. Secure protocols, encryption, and robust access controls are vital measures to secure data transfer and storage in IoT devices.
Lack of device management: Ineffective device management can lead to unauthorized access or manipulation of IoT devices. Strong authentication mechanisms and access controls are essential to mitigate this risk.
Insecure default settings: Manufacturers often leave default settings unchanged, creating security vulnerabilities. Changing default settings during initial setup and disabling unnecessary services can reduce these vulnerabilities.
Lack of physical hardening: Failure to implement physical security measures exposes IoT devices to hardware attacks. Measures such as disabling debug ports, secure boot mechanisms, and tamper detection help safeguard devices from physical intrusions.
Securing IoT devices demands a multifaceted approach involving robust authentication, encryption, regular updates, and user education. Understanding these vulnerabilities and adopting proactive mitigation strategies are paramount to safeguarding IoT ecosystems, preserving data integrity, and protecting user privacy in an increasingly connected world.
#pci dss compliance#pci dss saq#pci software security framework#pci secure software standard#pci secure software lifecycle#iso 27001 audit#GDPR.risk assessment#vulnerability assessment
0 notes
Text
Locking the Digital Doors: Understanding Web and Mobile App Security

In our digital world, apps on our phones and websites we visit are like doors to a house. But just like we lock our doors to keep bad guys out, we need to protect these apps from cyber bad guys. One way we do this is through something called a Web Application Firewall, which acts like a security guard for our apps. It stops the bad guys from sneaking in and causing trouble.
Another important thing to know is that these apps talk to each other using something called APIs. APIs help them share information. But if not handled carefully, they can accidentally spill sensitive information. OWASP help us understand the risks associated with these APIs, so we can make sure our apps are safe and sound. Together, let’s learn more about keeping our apps safe and our digital world secure!
Web and Mobile application Security
Securing web and mobile applications is crucial to protect sensitive data and ensure user safety. Here are the top 10 things to do:
Authentication and Authorization: Implement strong user authentication and authorization mechanisms to ensure that only authorized users can access certain features or data.
Data Encryption: Use encryption techniques (SSL/TLS) to protect data transmission between the client and server. Also, encrypt sensitive data at rest.
Input Validation: Validate and sanitize all user inputs to prevent common vulnerabilities like SQL injection and cross-site scripting (XSS).
Session Management: Implement secure session management practices to prevent session hijacking and fixation attacks.
API Security: Secure your APIs with authentication tokens, rate limiting, and proper access controls. Use API keys or OAuth for authorization.
Code Review and Testing: Regularly review and test your code for vulnerabilities. Use static analysis and dynamic testing tools to identify and fix security issues.
Patch Management: Keep all software components, libraries, and frameworks up to date with the latest security patches.
Error Handling: Implement proper error handling to avoid revealing sensitive information in error messages.
Security Headers: Use security headers like Content Security Policy (CSP), HTTP Strict Transport Security (HSTS), and Cross-Origin Resource Sharing (CORS) to control browser behavior.
Security Training and Awareness: Train your development and QA teams in secure coding practices and keep them updated on the latest security threats and best practices.
Regular security audits and penetration testing should also be part of your security strategy to proactively identify and mitigate vulnerabilities in your web and mobile applications.

2. Top 10 OWASP API Security Risk
The Open Web Application Security Project (OWASP) provides a list of the top 10 most critical web application security and API Risk official website (https://owasp.org)
API1:2023 – Broken Object Level Authorization–
APIs tend to expose endpoints that handle object identifiers, creating a wide attack surface of Object Level Access Control issues. Object level authorization checks should be considered in every function that accesses a data source using an ID from the user.
API2:2023 – Broken Authentication–
Authentication mechanisms are often implemented incorrectly, allowing attackers to compromise authentication tokens or to exploit implementation flaws to assume other user’s identities temporarily or permanently. Compromising a system’s ability to identify the client/user, compromises API security overall
API3:2023 – Broken Object Property Level Authorization–
This category combines API3:2019 Excessive Data Exposure and API6:2019 – Mass Assignment, focusing on the root cause: the lack of or improper authorization validation at the object property level. This leads to information exposure or manipulation by unauthorized parties.
API4:2023 – Unrestricted Resource Consumption–
Satisfying API requests requires resources such as network bandwidth, CPU, memory, and storage. Other resources such as emails/SMS/phone calls or biometrics validation are made available by service providers via API integrations, and paid for per request. Successful attacks can lead to Denial of Service or an increase of operational costs.
API5:2023 – Broken Function Level Authorization–
Complex access control policies with different hierarchies, groups, and roles, and an unclear separation between administrative and regular functions, tend to lead to authorization flaws. By exploiting these issues, attackers can gain access to other users’ resources and/or administrative functions
API6:2023 – Unrestricted Access to Sensitive Business Flows–
APIs vulnerable to this risk expose a business flow – such as buying a ticket, or posting a comment – without compensating for how the functionality could harm the business if used excessively in an automated manner. This doesn’t necessarily come from implementation bugs.
API7:2023 – Server Side Request Forgery–
Server-Side Request Forgery (SSRF) flaws can occur when an API is fetching a remote resource without validating the user-supplied URI. This enables an attacker to coerce the application to send a crafted request to an unexpected destination, even when protected by a firewall or a VPN.
API8:2023 – Security Misconfiguration–
APIs and the systems supporting them typically contain complex configurations, meant to make the APIs more customizable. Software and DevOps engineers can miss these configurations, or don’t follow security best practices when it comes to configuration, opening the door for different types of attacks.
API9:2023 – Improper Inventory Management–
APIs tend to expose more endpoints than traditional web applications, making proper and updated documentation highly important. A proper inventory of hosts and deployed API versions also are important to mitigate issues such as deprecated API versions and exposed debug endpoints.
API10:2023 – Unsafe Consumption of APIs–
Developers tend to trust data received from third-party APIs more than user input, and so tend to adopt weaker security standards. In order to compromise APIs, attackers go after integrated third-party services instead of trying to compromise the target API directly.
3. Importance of WAF web application firewall
A Web Application Firewall (WAF) is a crucial component in modern cybersecurity, primarily focused on protecting web applications from a variety of online threats and attacks. Here are several key reasons highlighting the importance of WAF:
Protection from Web Application Attacks: WAFs are designed to defend against common web application attacks, including SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and more. These attacks can compromise data integrity, steal sensitive information, or disrupt application functionality.
Zero-Day Attack Mitigation: WAFs can detect and mitigate new and emerging threats, even before patches or security updates are available. They do this by analyzing incoming traffic patterns and behavior anomalies.
Reduced Attack Surface: By filtering and monitoring incoming web traffic, WAFs help reduce the attack surface of web applications. They can block malicious requests before they reach the application server, minimizing the risk of exploitation.
DDoS Attack Mitigation: Some advanced WAFs have Distributed Denial of Service (DDoS) protection capabilities. They can identify and mitigate large-scale traffic floods, helping maintain service availability during attacks.
Compliance Requirements: Many regulatory standards and compliance frameworks, such as PCI DSS and HIPAA, mandate the use of security measures like WAFs to protect sensitive data. Implementing a WAF can help organizations meet these requirements.
Logging and Auditing: WAFs provide detailed logs of incoming traffic and blocked threats. These logs can be invaluable for security audits, incident response, and forensic analysis.
Real-Time Threat Monitoring: WAFs offer real-time monitoring of web traffic, enabling security teams to identify and respond to threats quickly. They can trigger alerts or automated responses to specific attack patterns.
Traffic Normalization: WAFs can normalize incoming traffic, filtering out malicious or malformed requests. This helps ensure that only legitimate, well-formed requests reach the application, improving its overall stability.
Protection for Legacy Applications: WAFs can protect older or legacy web applications that may not have been built with modern security practices in mind. They act as an additional layer of security for such applications.
Cost-Efficient Security: Implementing a WAF can be more cost-effective than addressing vulnerabilities and responding to security incidents after an attack has occurred. It provides proactive, continuous protection.
In summary, a Web Application Firewall is a critical security component for safeguarding web applications from a wide range of threats. It helps organizations maintain the confidentiality, integrity, and availability of their web services and sensitive data.
Simple antivirus software is designed primarily to detect and remove known malware and viruses based on predefined signatures and patterns. While antivirus programs are important for basic protection, they have limitations that make them insufficient in today’s complex cybersecurity landscape.
Here’s why EDR (Endpoint Detection and Response) is necessary:
1.Limited Detection Capabilities: Antivirus relies on known signatures and patterns to identify threats. It may miss zero-day attacks and sophisticated malware that haven’t been previously identified.
2.Lack of Behavioral Analysis: EDR solutions monitor the behavior of files and processes on an endpoint. They can detect suspicious activities, such as unusual system behavior or data exfiltration, even if there are no known malware signatures involved.
3.Advanced Threats: EDR solutions are better equipped to detect advanced threats like fileless malware and polymorphic malware that can change their code to evade traditional antivirus scans.
4.Incident Response: EDR provides real-time monitoring and alerting, helping organizations respond quickly to security incidents. Antivirus software typically lacks these features.
5.Visibility and Investigation: EDR solutions provide detailed information about endpoint activity, allowing security teams to investigate incidents thoroughly, trace the source of an attack, and understand its scope.
6.Threat Hunting: EDR enables proactive threat hunting. Security analysts can search for signs of compromise and anomalies to detect threats that may have gone unnoticed by traditional antivirus.
7.Compliance and Reporting: EDR solutions often provide extensive reporting capabilities, which are crucial for compliance with data protection regulations and for demonstrating a proactive approach to security.
8.Adaptive Protection: EDR can adapt its response to evolving threats, applying behavioral analysis and machine learning to identify new attack patterns.
In summary, while antivirus software is a fundamental layer of protection, EDR complements it by offering advanced threat detection, real-time monitoring, incident response capabilities, and the ability to investigate and mitigate complex security incidents. In today’s rapidly evolving threat landscape, EDR is a critical component of a comprehensive cybersecurity strategy.
This blog emphasizes the critical importance of securing web and mobile applications in our digital era. It highlights the escalating threat landscape targeting crucial elements of our digital infrastructure. APIs (Application Programming Interfaces) are crucial for application functionality but can pose significant security risks if not adequately protected. The OWASP API Security Top 10 is a vital resource that sheds light on prevalent vulnerabilities in the API landscape. The blog delves into these risks, providing a comprehensive analysis of their implications and suggesting potential solutions. Additionally, the blog underlines the fundamental role of a Web Application Firewall (WAF) in enhancing digital security by monitoring and filtering traffic, acting as a defense against cyber threats. It invites readers to join this journey to enhance their understanding of web and mobile application security, fostering a safer digital future.
0 notes
Text
youtube
In this video, we talk about how to install our free WAF solution which helps to protects your web applications and APIs from OWASP Top 10 attacks. You need to follow the step-by-step process which are explaining in this video and secure your online business from cyber attacks. Our free WAF solution have built in signature, DDoS mitigation, security threat feeds, custom signatures, bot mitigation, built-in load balancing features to protect against OWASP Top 10 attacks. Visit: https://www.haltdos.com/community/ Check out the documentation (User Guide): https://docs.haltdos.com/community/
0 notes
Text
Learn about what's trending in App & API attacks
Sign up for our live two-part webinar series to discover why BOLA continues to be ranked number one on the OWASP API Top 10. Sign up today. #cybersecurity #AkamaiSOTI
Learn about what's trending in App & API attacks
Sign up for our live two-part webinar series to discover why BOLA continues to be ranked number one on the OWASP API Top 10. Sign up today.
Akamai Dynamic Signal
0 notes
Text
OWASP Top 10 Security Guidelines: A Comprehensive Guide to Securing Your Web Application
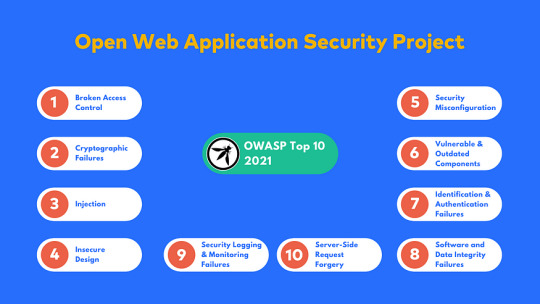
In today’s digital age, web applications have become an integral part of our daily lives. However, with the increasing number of web-based attacks, securing your web application has never been more critical. One way to ensure your web application is secure is by following the OWASP Top 10 Security Guidelines.
If you are looking for a comprehensive guide to securing your web application with OWASP Top 10 Security Guidelines, check out this article from Tech blog. The article covers the top security risks faced by web applications, the OWASP Top 10 Security Guidelines, and how to implement these guidelines in your web application.
By following the OWASP Top 10 Security Guidelines, you can ensure your web application is secure and protected against common security risks such as SQL injection, cross-site scripting, and broken authentication and session management. With the right security measures in place, you can give your users the peace of mind they need to trust your web application and keep coming back for more.
Conclusion
Securing your web application is a crucial step in today’s digital landscape. By following the OWASP Top 10 Security Guidelines, you can ensure your web application is secure, protected, and trusted by your users.
0 notes
Text
Vulnerabilities: What is Broken Access Control and how to fix it
What is Access Control?
Before understanding the vulnerability, let's see what an access control is (Access Control).
Access control ( Access Control ) is a mechanism that specifies what information, functions or systems will be accessible to a particular user, group or role. That is, it is a way to control who can access certain resources , typically by using policies to specify access privileges.
In web applications, access control involves using protection mechanisms such as:
Authentication (verify user identity)
Authorization (check if the user has permission to access a resource).
What is a Broken Access Control?
The Broken Access Control vulnerability occurs when a failure or absence of access control mechanisms allows a user to access a resource that is outside of their intended permissions.
This vulnerability is one of the most common in websites and ranks No. 5 in the OWASP TOP 10 (Open Web Application Security Project).
Due to the number of errors related to access control, there are several vulnerabilities under the Broken Access Control category , some of them are:
IDOR (Insecure Direct Object Reference)
CSRF (Client-Side Request Forgery)
CORS (Cross-Origin Resource Sharing) misconfiguration
It has been classified by the CWE (Common Weakness Enumeration) as CWE-284: Improper Access Control. You can visit its technical sheet to know more specifications.
Broken Access Control Risks
The risks of this vulnerability depend on the interaction that the attacker manages to have with a company's server.
However, in the case of companies, it is common for occasions from information leaks to the alteration of sensitive or confidential data.
common case
Broken Access Control in administrative functions
There could be two possible Broken Access Control scenarios here:
In the event that an unauthenticated user can access and obtain the list of e-mails.
In the event that an authenticated user who is not an administrator manages to access and obtain the list of mails.
In both cases, the application would be vulnerable.
Tips to prevent it
Preventing this vulnerability can be complex since there are many scenarios that can lead to it, however, there are good practices that you can implement to mitigate it, such as:
Check the implementation of correct access control, establishing roles and permissions to access resources.
Verify that access to resources by ID has an additional verification step that ensures the entry of authorized users
Deny access to your resources by default, unless you want them to be public.
What a Broken Access Control looks like in code
Suppose a website allows its users to register and post blog articles.
During this registration, the user must provide data such as their email and name, and site administrators can see this information from a menu (only accessible to administrators) that has the option "See all emails."
And accessing here executes the following code:
The server effectively asks the user to log in to access the email list, however, it does not check their role or permissions.
Therefore, the application is vulnerable since an authenticated user but without permissions can access a functionality intended only for administrators .
Solution
The server should also check what roles or permissions the user has when accessing the resource. To do this, it would be necessary to modify the code so that it contains the following:
if (isset( $_SESSION [ 'loggedin' ]) && $_SESSION [ 'isadmin' ] == true )) {
load_emails();
}
else {
return_to_login();
}
In this way, any user who is not authenticated or who is not authorized (other than administrator), will be redirected to the Login page .
A pentest never hurts
Broken Access Control vulnerabilities are very common not only due to a lack of effective functional testing by developers, but also due to a lack of automated detection (static and dynamic review tools).
For this reason, carrying out an ethical hacking exercise (of the penetration testing type , manual intrusion tests or pentest ) is the most convenient and viable option to detect them in time and mitigate them at the root.
Conclusion
The Broken Access Control vulnerability usually appears when there are errors in the implementation of access controls.
Although it may seem like a simple and harmless vulnerability, its impact can be critical and the difficulty of finding it using automated tools can make it go unnoticed.
Consider following the good practices outlined above and periodically performing penetration tests to find this and any other types of vulnerabilities.
As vulnerabilities exist in the web3 spaces, Cypershield is one of the kinds of Security and Smart Contract audit company rendering exceptionally professional smart contract auditing services for varied Crypto projects. In the process of rendering your projects, full-on auditing services help you come over your smart contract vulnerabilities and reach a higher scale in the market.
0 notes
Text
Is your website Secure?
I will do penetration test your website with professional report

I will Penetration Test your valuable website and provide a very professional report which includes vulnerability descriptions, exploitation steps, recommendations, root causes and more.So you can secure your valuable assets.
What does this service include?
Automatic Web Application Penetration Testing (Nessus, Acunetix, BurpSuite Scanner)
Manual Web Application Security Testing (BurpSuite Pro, Metasploit, BeEF, Acunetix, Nessus)
OWASP Top 10 Attacks
Web Application Vulnerability Scanner With All Premium Tools
Professional Penetration Testing Report (Step to reproduce with Screenshots)
Vulnerability scanning (BurpSuite Pro, Metasploit, BeEF, Acunetix, Nessus)
Test for SQL injection With SQLMap
Test for XSS with No XSS
Test for Buffer overflow
Network Protocol Analyze With WireShark
Test for file inclusion and other all vulnerabilities (Astra Pentest )
Why am I?
100% customer satisfaction
Reliable and Fast
24/7 support
5+ Years of experience
Fully dedicated
1 note
·
View note
Text
Cyber security is a critical concern in today's digital age as cyber attacks are becoming more frequent and sophisticated
One of the most dangerous types of attacks is XXE Injection, which allows attackers to exploit vulnerabilities in XML parsers to gain access to sensitive information. Another type of attack to be aware of is Phar Deserialization, which can be used to execute arbitrary code on a server.
To protect against these types of attacks, it is important to stay informed about the latest hacking techniques and tools. One tool that can be useful in this regard is Frida, which is a dynamic instrumentation framework that can be used to perform runtime manipulation and hooking of applications. Redteam, another hacking tool, can be used for penetration testing, also known as pentest, to identify vulnerabilities in a target system.
It is also important to be aware of OWASP top 10, which is a list of the most common web application security vulnerabilities. One of the vulnerabilities on the list is CSRF (Cross-site Request Forgery) which can be used to trick a user into performing actions they did not intend. Another vulnerability to be aware of is Pickle Deserialization, which can be used to execute arbitrary code on a server.
For those interested in learning more about hacking and cyber security, there are many resources available such as the Zh3r0 CTF, a hacking competition where participants can test their skills, and the write up available on umbccd.io, a website that provides CTF write-ups, hacking tools and hacking tricks. A good example of a real-world application is the WaTF Bank, a bank that regularly conduct pentest to secure their systems.
In conclusion, it is important to stay informed and vigilant in the ever-changing cyber threat landscape. By understanding the latest types of attacks and tools available, as well as taking steps to protect against them, you can help to keep your information and systems secure. Remember to stay informed and vigilant to keep yourself and your organization safe.
mobile security solution
0 notes
Text
Cyber security is a critical concern in today's digital age as cyber attacks are becoming more frequent and sophisticated
One of the most dangerous types of attacks is XXE Injection, which allows attackers to exploit vulnerabilities in XML parsers to gain access to sensitive information. Another type of attack to be aware of is Phar Deserialization, which can be used to execute arbitrary code on a server.
To protect against these types of attacks, it is important to stay informed about the latest hacking techniques and tools. One tool that can be useful in this regard is Frida, which is a dynamic instrumentation framework that can be used to perform runtime manipulation and hooking of applications. Redteam, another hacking tool, can be used for penetration testing, also known as pentest, to identify vulnerabilities in a target system.
It is also important to be aware of OWASP top 10, which is a list of the most common web application security vulnerabilities. One of the vulnerabilities on the list is CSRF (Cross-site Request Forgery) which can be used to trick a user into performing actions they did not intend. Another vulnerability to be aware of is Pickle Deserialization, which can be used to execute arbitrary code on a server.
For those interested in learning more about hacking and cyber security, there are many resources available such as the Zh3r0 CTF, a hacking competition where participants can test their skills, and the write up available on umbccd.io, a website that provides CTF write-ups, hacking tools and hacking tricks. A good example of a real-world application is the WaTF Bank, a bank that regularly conduct pentest to secure their systems.
In conclusion, it is important to stay informed and vigilant in the ever-changing cyber threat landscape. By understanding the latest types of attacks and tools available, as well as taking steps to protect against them, you can help to keep your information and systems secure. Remember to stay informed and vigilant to keep yourself and your organization safe.
HTTP Request Smuggling
0 notes
Text
Cyber security is a critical concern in today's digital age as cyber attacks are becoming more frequent and sophisticated
One of the most dangerous types of attacks is XXE Injection, which allows attackers to exploit vulnerabilities in XML parsers to gain access to sensitive information. Another type of attack to be aware of is Phar Deserialization, which can be used to execute arbitrary code on a server.
To protect against these types of attacks, it is important to stay informed about the latest hacking techniques and tools. One tool that can be useful in this regard is Frida, which is a dynamic instrumentation framework that can be used to perform runtime manipulation and hooking of applications. Redteam, another hacking tool, can be used for penetration testing, also known as pentest, to identify vulnerabilities in a target system.
It is also important to be aware of OWASP top 10, which is a list of the most common web application security vulnerabilities. One of the vulnerabilities on the list is CSRF (Cross-site Request Forgery) which can be used to trick a user into performing actions they did not intend. Another vulnerability to be aware of is Pickle Deserialization, which can be used to execute arbitrary code on a server.
For those interested in learning more about hacking and cyber security, there are many resources available such as the Zh3r0 CTF, a hacking competition where participants can test their skills, and the write up available on umbccd.io, a website that provides CTF write-ups, hacking tools and hacking tricks. A good example of a real-world application is the WaTF Bank, a bank that regularly conduct pentest to secure their systems.
In conclusion, it is important to stay informed and vigilant in the ever-changing cyber threat landscape. By understanding the latest types of attacks and tools available, as well as taking steps to protect against them, you can help to keep your information and systems secure. Remember to stay informed and vigilant to keep yourself and your organization safe.
pentest kubernetes
1 note
·
View note