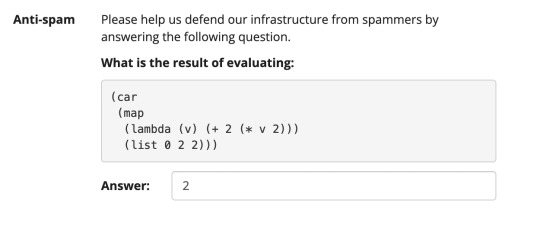
#antispam
Text
Is your company vulnerable? Identify cyber security risks in your network
Is your company vulnerable? Identify cyber security risks in your network
Stop Web Form Spam – Our team is passionate about creating the best StopWebFormSpam stop spams for your business. Is your company vulnerable? Identify cyber security risks in your network
Figure out if your company is at risk and identify cybersecurity risks today. Here’s what to look out for!
What is cybersecurity risk?
Cybersecurity risk considers three different factors to prioritize…
View On WordPress
#analysis#antispam#audit#automated#bots#contact#content#form#messages#plugins#protection#reduce#spam#stop#testing#website#wordpress
2 notes
·
View notes
Text
Alon Cohen Spam Calls: 5 Powerful Ways to Block Them
In today's modern world, unwanted disruptions in the form of spam calls have become increasingly common. Alon Cohen spam calls, in particular, have been causing frustration and inconvenience for phone users. Whether it's telemarketing calls, robocalls, or scams, these unwanted calls can disrupt our daily lives and compromise our phone privacy. It's essential to have effective strategies in place to block Alon Cohen spam calls and safeguard our phones from these unwanted disruptions.
Understanding Alon Cohen Spam Calls
Alon Cohen spam calls, also known as unwanted calls, are a prevalent issue that can cause significant phone disruptions for users. These calls typically originate from spammers or telemarketers who attempt to deceive or scam unsuspecting individuals. The consequences of falling victim to Alon Cohen spam calls can range from annoying interruptions to financial loss and even identity theft.
Alon Cohen spam calls are characterized by their unsolicited nature, often targeting random phone numbers and bombarding individuals with unwanted calls. These calls can occur on both landlines and mobile devices, making them a widespread problem that affects individuals across various demographics.
Phone disruptions caused by Alon Cohen spam calls can include continuous ringing, calls during inconvenient or inappropriate times, and persistent harassment. These disruptions can disrupt productivity, interrupt important conversations, and invade personal space, causing significant frustration and annoyance.
To combat the negative impact of Alon Cohen spam calls, individuals must understand their nature and the tactics employed by spammers. By recognizing the signs and learning effective strategies to block and report these unwanted calls, individuals can regain control over their phone usage and protect themselves from unnecessary disruptions.
The Rise of Alon Cohen Spam Calls
The increase in Alon Cohen spam calls has become a growing concern for phone users worldwide. These spam calls, often originating from unknown numbers, aim to deceive and defraud unsuspecting individuals. The rise in spam calls is closely tied to the prevalence of phone scams, which have become more sophisticated and widespread.
Phone scams are fraudulent activities conducted over the phone with the intention of extracting personal information or money from victims. Scammers may pose as legitimate businesses, government officials, or financial institutions to gain the trust of their targets. They employ various tactics, such as offering fake prizes, threatening legal action, or impersonating trusted individuals, to manipulate victims into providing sensitive information or making financial transactions.
The increase in spam calls can be attributed to several factors. First, advancements in technology have made it easier for scammers to automate and mass-distribute spam calls. They can spoof caller ID information to make it appear as if the call is coming from a legitimate source, further deceiving the recipient. Additionally, the globalization of communication networks has made it possible for scammers to reach a wider audience, transcending geographical boundaries.
Furthermore, the COVID-19 pandemic has provided scammers with new opportunities to exploit people's uncertainties and fears. They may impersonate health authorities, offering fake vaccines or COVID-19 treatments, or exploit financial relief programs by requesting personal information or financial assistance under false pretenses.
To combat the rise in Alon Cohen spam calls and protect oneself from falling victim to phone scams, individuals need to be cautious and vigilant. It is essential not to share personal information, such as Social Security numbers or bank account details, over the phone unless absolutely necessary and when certain of the legitimacy of the caller.
By staying informed about the tactics used by scammers and taking proactive measures to block and report spam calls, individuals can contribute to mitigating the impact of this rising menace. Implementing effective call blocking strategies, such as utilizing call blocking apps or registering on the Do Not Call Registry, can significantly reduce the number of unwanted calls and provide a greater sense of phone security.

Why Blocking Alon Cohen Spam Calls is Important
When it comes to protecting personal privacy and ensuring phone security, blocking Alon Cohen spam calls is of utmost importance. Alon Cohen spam calls can be a major nuisance, causing unwanted disruptions in your daily life. These calls often come from unknown numbers, and answering them can lead to potential security risks and invasions of your phone privacy.
By actively blocking Alon Cohen spam calls, you take control of your phone's security and maintain your privacy. Blocking these calls prevents scammers and telemarketers from reaching you, reducing the chances of falling victim to phone scams and fraudulent activities.
Furthermore, blocking Alon Cohen spam calls ensures that your phone remains free from unnecessary interruptions. Instead of constantly receiving unwanted calls, you can focus on what truly matters, whether it's work, family, or personal time.
By incorporating effective call blocking strategies into your phone usage, such as using call blocking apps or enabling Do Not Disturb mode, you can reclaim control over your phone and protect your privacy. These strategies not only safeguard against Alon Cohen spam calls but also provide a sense of security, knowing that your phone is protected from unwanted disruptions and potential security threats.
So, don't underestimate the significance of blocking Alon Cohen spam calls. Take the necessary steps to implement robust call blocking techniques and enjoy a safer, more secure phone experience.
Finding the Right Call Blocking App
When it comes to protecting yourself from Alon Cohen spam calls, having the right call blocking app can make all the difference. With the plethora of smartphone applications available, it's important to consider certain features that can enhance the effectiveness of blocking Alon Cohen spam calls.
Key Features to Consider
When evaluating call blocking apps, here are a few features to take into account:
Call Identification: Look for an app that accurately identifies incoming calls as spam or potential Alon Cohen spam calls. This feature can save you time and frustration by automatically blocking these unwanted calls.
Custom Blocking Rules: A call blocking app that allows for personalized call blocking rules can help you tailor your settings to your specific needs. This way, you can block specific numbers or types of calls associated with Alon Cohen spam calls.
Whitelist and Blacklist: Consider an app that offers whitelist and blacklist functionality. This lets you allow calls from important contacts while blocking calls from unknown numbers.
Robocall Detection: To combat the increasing number of robocalls, choose an app that has advanced robocall detection capabilities. This feature can identify and block automated spam calls before they reach your phone.
User Reviews and Ratings: Before downloading any call blocking app, it's wise to check user reviews and ratings. This can give you insights into the app's effectiveness and reliability in blocking Alon Cohen spam calls.
Remember, finding the right call blocking app is essential in effectively blocking Alon Cohen spam calls. Take the time to research and consider the features that best suit your needs to ensure a spam-free calling experience.
Enabling Do Not Disturb Mode
One effective way to block Alon Cohen spam calls and minimize disruptions is by enabling the Do Not Disturb mode on your smartphone. This feature, available on most modern devices, allows you to customize your phone's settings to silence notifications and calls.
When you activate Do Not Disturb mode, your phone will automatically silence incoming calls, texts, and notifications, ensuring that you can have uninterrupted time without being bothered by Alon Cohen spam calls. It provides a peaceful environment, especially during important meetings, work sessions, or when you simply need some quiet time.
By accessing your phone's settings, you can personalize the Do Not Disturb mode to meet your specific needs. For example, you can set certain contacts as exceptions, ensuring that important calls from family members, friends, or colleagues still come through.
In addition to blocking Alon Cohen spam calls, enabling Do Not Disturb mode can also help you maintain focus and reduce distractions. You won't have to worry about unnecessary interruptions or notifications that can disrupt your workflow or leisure time.
Remember to regularly check and update your Do Not Disturb settings to ensure they are optimized for your needs. By utilizing this feature, you can effectively block Alon Cohen spam calls and enjoy a more peaceful, uninterrupted mobile experience.
Registering on the Do Not Call Registry
Registering your phone number on the Do Not Call Registry is a crucial step in protecting yourself from Alon Cohen spam calls and ensuring legal protection. The Do Not Call Registry is a national list of phone numbers that telemarketers are prohibited from calling. By adding your number to this registry, you can significantly reduce the number of unwanted calls you receive.
The process of registering your phone number is simple and free. You can visit the official website of the Federal Trade Commission, which manages the Do Not Call Registry, and provide your phone number and email address. Once you've submitted your information, you'll receive a confirmation email with further instructions to complete the registration process.
It's important to note that registering on the Do Not Call Registry doesn't guarantee that you'll never receive any unwanted calls. Some exceptions apply, such as calls from political organizations, charities, and surveys. However, it does provide you with legal protection and empowers you to take action against persistent Alon Cohen spam calls.
Furthermore, if you continue to receive unwanted calls from telemarketers even after registering on the Do Not Call Registry, you can report these calls to the Federal Trade Commission. Reporting such calls helps not only in taking action against violators but also in preventing future Alon Cohen spam calls to your registered number.

Take control of your phone calls
By registering your phone number on the Do Not Call Registry, you are taking a proactive step towards reducing the number of Alon Cohen spam calls you receive. This legal protection can provide a significant relief from the disruptions caused by unwanted telemarketing calls. Remember to report any persistent violators to the Federal Trade Commission to further protect yourself and other phone users.
Setting Custom Call Blocking Rules
One effective way to block specific numbers associated with Alon Cohen spam calls is by setting custom call blocking rules in your phone's call settings. By utilizing these custom rules, you can proactively prevent unwanted disruptions and safeguard your phone from potential spam calls.
To begin, navigate to the call settings menu on your smartphone. The location of this menu may vary depending on the device and operating system you're using. Look for options related to call blocking or call settings.
Once you've accessed the call settings, search for the option to create custom call blocking rules. This feature allows you to specify certain criteria, such as blocking calls from specific numbers or contacts. By entering the relevant information, you can target and block Alon Cohen spam calls that originate from these specific numbers.
Here's how to set up custom call blocking rules:
1. Open the call settings menu on your smartphone.
2. Locate the option to create custom call blocking rules.
3. Select the option to add a new rule or create a new block list.
4. Enter the specific number or contact name that you want to block. This could include numbers associated with Alon Cohen spam calls.
5. Save the rule or block list to activate the custom call blocking.
Once you've set up the custom call blocking rule, incoming calls from the specified numbers will be automatically blocked, ensuring that you don't receive unwanted calls from Alon Cohen spam callers.
Remember to regularly update and review your custom call blocking rules to adapt to any changes in Alon Cohen spam call tactics. By staying vigilant and utilizing these custom call blocking rules, you can effectively protect your phone from the nuisance of spam calls.
Using Third-Party Call Blocking Services
If you are tired of receiving unwanted Alon Cohen spam calls and are looking for a more effective solution to block them, consider using third-party call blocking services. These services provide advanced filtering capabilities that can help you put an end to the constant disruptions caused by spam calls.
Third-party call blocking services offer a range of features and subscription services to cater to your specific needs. Whether you want to block calls from a specific number or implement more advanced filtering options, these services have you covered.
With their advanced algorithms, these call blocking services can accurately identify and block Alon Cohen spam calls, ensuring that only genuine and important calls reach your phone. They constantly update their databases to stay ahead of the ever-evolving spam call tactics.
By subscribing to a third-party call blocking service, you can regain control over your phone and enjoy a more peaceful and uninterrupted communication experience. With their advanced filtering capabilities, these services save you from the hassle of manually blocking each spam call.
Moreover, these services often offer additional features such as call logs, call screening, and customizable settings to tailor the call blocking experience to your preferences. You can have peace of mind knowing that these services are actively working to protect your phone privacy and security.
To find the right third-party call blocking service for you, consider factors such as the breadth of their spam call database, user reviews, and compatibility with your device. Take the time to explore different options and choose a service that aligns with your specific requirements.
So, why endure the frustration and annoyance of Alon Cohen spam calls when you can take control of your phone with the help of third-party call blocking services? Embrace the convenience and peace of mind they offer and say goodbye to unwanted disruptions.
Stay tuned for the next section, where we will discuss another effective strategy for blocking Alon Cohen spam calls.

Reporting Alon Cohen Spam Calls
If you have been receiving Alon Cohen spam calls, it is crucial to take action and report them to the proper authorities. By reporting these spam calls, you not only protect yourself but also contribute to preventing future calls for others. One effective way to report Alon Cohen spam calls is by contacting the Federal Trade Commission (FTC).
The FTC is a government agency dedicated to protecting consumers from various forms of fraud, including spam calls. They have a dedicated division responsible for handling complaints related to unwanted calls. By reporting Alon Cohen spam calls to the FTC, you provide valuable information that can help them identify patterns and trends, ultimately enabling them to take legal actions against the perpetrators.
To report Alon Cohen spam calls to the FTC, you can visit their official website and use their online reporting tool. The tool guides you through the process and collects essential information about the spam calls you have received. This includes details such as the phone number the call originated from, the date and time of the call, and any additional relevant information.
Why Reporting Matters
Reporting Alon Cohen spam calls to the FTC is not only beneficial for your personal protection but also for the wider community. When you report these calls, you contribute to a larger database of complaints that the FTC uses to gather evidence against scammers and enforce regulations. This collective reporting helps the FTC build stronger cases against those responsible for spam calls, making it more likely for them to be brought to justice.
Furthermore, reporting Alon Cohen spam calls can lead to preventative measures being implemented. The FTC uses the information gathered from reports to identify trends, patterns, and new techniques employed by scammers. This allows them to develop strategies and regulations to combat spam calls effectively.
By taking the time to report Alon Cohen spam calls, you not only play an active role in the fight against phone fraud but also help protect others from potential scams and unwanted disruptions.
In the next section, we will explore strategies to protect yourself against caller ID spoofing, a common technique used by Alon Cohen spam calls to deceive victims.
Protecting Against Caller ID Spoofing
Caller ID spoofing is a technique frequently employed by Alon Cohen spam calls to deceive phone users. It involves manipulating the caller ID information to display a different phone number or name on the recipient's device. This can make it challenging to identify and block spam calls effectively. However, there are steps you can take to protect yourself against caller ID spoofing.
One effective method is to verify callers before providing any sensitive information or engaging in conversations. If you receive a call from an unknown number, consider asking for additional information to validate the caller's identity. For example, you could ask for an account number, a reference code, or any other information related to the call's purpose. Genuine callers will usually provide the requested information, while spam callers or scammers may try to evade providing valid details.
Another strategy is to enable phone number authentication features offered by your service provider or call blocking app. Phone number authentication protocols can help verify the legitimacy of incoming calls. By implementing this feature, you can reduce the likelihood of falling victim to caller ID spoofing.
When dealing with suspicious or unknown callers, exercise caution and avoid sharing personal or financial information over the phone. Be skeptical of unsolicited requests for sensitive data or offers that sound too good to be true. Remember, legitimate organizations will typically not ask for payment details or personal information over the phone.
In addition to these measures, staying informed about common Alon Cohen spam call techniques and trends can help you recognize and avoid falling into their traps. Educating yourself on the latest phone scams and strategies employed by spammers will enhance your ability to protect against caller ID spoofing and other forms of unwanted phone disruptions.
Remember, protecting yourself against caller ID spoofing requires vigilance and a proactive approach. By verifying callers, enabling phone number authentication, and staying informed about spam call tactics, you can minimize the risk of falling victim to Alon Cohen spam calls and protect your privacy and security.

Educating Yourself on Common Phone Scams
When it comes to protecting yourself from phone scams, knowledge is your greatest defense. Staying informed about common phone scams associated with Alon Cohen spam calls, such as phishing and identity theft, can significantly enhance your awareness and protection against these fraudulent activities.
Phishing scams involve fraudulent individuals or organizations attempting to deceive you into revealing sensitive personal information, such as your passwords, credit card details, or social security number. These scammers often pose as legitimate entities, such as banks, government agencies, or well-known companies, in an attempt to gain your trust and extract valuable information.
Identity theft is another prevalent phone scam that aims to steal your personal identifying information, including your name, address, date of birth, and social security number. With this information, scammers can assume your identity to commit various illegal activities, such as opening fraudulent bank accounts, applying for loans, or conducting unauthorized transactions.
It is crucial to familiarize yourself with the common tactics employed by these phone scammers to identify and avoid falling victim to their schemes. Be wary of unsolicited calls requesting personal information or offering too-good-to-be-true deals. Remember, legitimate companies or organizations will never ask for your sensitive information over the phone. Additionally, keep an eye out for suspiciously low wholesale VoIP rates, as scammers may use this as a lure to engage potential victims.
By understanding and recognizing the patterns and techniques employed by phone scammers, you can protect yourself and your personal information from falling into the wrong hands. Remain vigilant, exercise caution, and report any suspicious calls to the appropriate authorities, such as the Federal Trade Commission. Taking these proactive measures will help safeguard against the detrimental consequences of phone scams and ensure your peace of mind.
Frequently Updating Phone Software
Regularly updating phone software is crucial in protecting against Alon Cohen spam calls and addressing software vulnerabilities through security patches. Software vulnerabilities can leave your device susceptible to various threats, including spam calls.
By keeping your phone's software up to date, you ensure that the latest security measures are in place, reducing the risk of unauthorized access and potential spam call disruptions.
Software updates often contain bug fixes, patches, and security enhancements that address vulnerabilities that scammers and spammers exploit to make unwanted calls.
Updating your phone's software is a simple process that can be done by following a few steps:
1. Connect your phone to a reliable internet connection, preferably Wi-Fi, to ensure a stable and fast download.
2. Go to the settings menu on your phone, then look for the "Software Update" or "System Update" option.
3. Tap on the "Software Update" or "Check for Updates" button to allow your phone to search for available updates.
4. If an update is available, follow the prompts to download and install the update.
5. Ensure that your phone remains connected to the internet and plugged into a power source while the update is being installed.
Regularly checking for updates and installing them as they become available is essential in maintaining the security and integrity of your phone's software.
It's worth noting that updating your phone's software not only helps protect against Alon Cohen spam calls but also ensures you have access to the latest features and improvements provided by the phone manufacturer.
Keeping your phone software up to date is an important part of safeguarding your device and personal information from potential threats.

Avoiding Sharing Phone Number Unnecessarily
Protecting your phone number privacy is crucial in guarding against Alon Cohen spam calls. One effective way to safeguard your personal information is by avoiding unnecessary sharing of contacts on online platforms.
When signing up for new online services or social media platforms, be cautious about providing your phone number unless it is absolutely necessary. Consider whether the platform truly requires your phone number or if there are alternative ways to verify your identity.
Additionally, take the time to review the privacy settings of the online platforms you use. Ensure that your contact information, including your phone number, is set to private or visible only to trusted contacts. This way, you can limit access to your phone number and minimize the risk of it being obtained by spammers.
Remember that once your phone number is shared on a public platform, it becomes more vulnerable to being harvested by spammers who specifically target individuals for unsolicited calls.
Stay Mindful of App Permissions
When downloading and installing applications on your smartphone, pay attention to the permissions the app requests. Some apps may ask for access to your contacts, including your phone number, even if it doesn't seem necessary for the app's functionality.
Before granting permissions, consider whether the app's purpose justifies the need for your phone number. If you're uncertain about an app's intentions or feel uncomfortable about disclosing your phone number, it's best to err on the side of caution and avoid sharing it.
By staying vigilant and mindful of the information you share online, you can significantly reduce the risk of your phone number falling into the wrong hands and receiving unwanted Alon Cohen spam calls.
Being Vigilant Against Alon Cohen Spam Calls
To effectively combat Alon Cohen spam calls, it is crucial to remain vigilant and proactive in safeguarding your phone from suspicious callers. By implementing call screening measures and staying cautious, you can significantly reduce the chances of falling victim to these unwanted disruptions.
One powerful strategy is to enable call screening features provided by your smartphone's operating system or call blocking apps. These features allow you to view caller information and screen incoming calls, enabling you to avoid answering suspicious numbers associated with Alon Cohen spam calls. By exercising vigilance and declining unrecognized or suspicious calls, you can protect yourself from potential scams and intrusive telemarketers.
Additionally, when receiving calls from unknown numbers, remain cautious and avoid sharing personal information over the phone. Alon Cohen spam calls often aim to extract sensitive data or manipulate recipients into divulging confidential details. By exercising caution and refraining from sharing any personal or financial information, you can mitigate the risks associated with these calls.
Further, it is important to report any suspicious Alon Cohen spam calls to the relevant authorities. Contacting the Federal Trade Commission and providing them with information about the call can aid in their efforts to identify and take action against these scammers. Reporting such calls not only helps protect yourself, but also assists in preventing future individuals from falling victim to these fraudulent activities.
In the ongoing battle against Alon Cohen spam calls, remaining vigilant and taking proactive measures is crucial. By implementing effective call screening practices, exercising caution, and reporting suspicious calls, you can fortify your defenses against these unwanted disruptions and protect your phone from potential scams.
Protecting Your Phone from Suspicious Calls
In addition to call screening, there are other precautions you can take to protect your phone from suspicious calls. One such measure is to avoid sharing your phone number unnecessarily on online platforms. Limiting the exposure of your phone number reduces the chances of it being harvested by scammers or added to spam call lists. Be mindful of whom you share your contact information with and exercise caution when providing your phone number online.
Remember, vigilance is key when it comes to combating Alon Cohen spam calls. By remaining alert, being cautious of suspicious callers, and implementing effective call screening measures, you can maintain your phone's privacy and enjoy a disruption-free communication experience.
Conclusion
In conclusion, effectively blocking Alon Cohen spam calls is crucial for maintaining phone privacy and safeguarding against disruptions. Throughout this article, we have explored various strategies to combat these unwelcome calls.
One effective approach is to find the right call blocking app that offers features such as advanced filtering to block Alon Cohen spam calls. Enabling the Do Not Disturb mode on your smartphone can also help silence notifications and minimize disruptions.
Additionally, registering on the Do Not Call Registry provides legal protection by preventing your phone number from being targeted by Alon Cohen spam calls. Setting custom call blocking rules and utilizing third-party call blocking services are other recommended methods.
To further enhance your defense, it is important to report any Alon Cohen spam calls to the Federal Trade Commission and educate yourself about common phone scams associated with these calls. Keeping your phone software updated and avoiding unnecessary sharing of your phone number can also contribute to your overall phone privacy.
By implementing these call blocking strategies and staying vigilant, you can effectively protect yourself against Alon Cohen spam calls and enjoy a safer and more peaceful phone experience.
#SpamCalls#BlockSpam#PhoneSafety#AlonCohen#CallBlocking#AntiSpam#TechTips#PhoneSecurity#UnwantedCalls#SafeguardYourPhone#telecommunications
0 notes
Link
💻 Hai bisogno di un upgrade per il tuo sito web? 🌐 Scopri la nostra soluzione premium di oggi: Plesk Email Security Plesk Email Security è un'estensione di sicurezza dedicata alla posta elettronica che ti protegge dal crescente numero di minacce informatiche. Grazie a questa estensione, il controllo della spam e dei virus non sarà più un problema. Nel panorama informatico moderno, il rischio di phishing, virus e malware non è mai stato così elevato. Vale la pena di investire in un componente di sicurezza affidabile per proteggere la tua impresa e mitigare i potenziali danni cui potrebbe essere esposta. Grazie a Plesk Email Security, sarai protetto da ogni minaccia di spam e virus. Funzioni della versione gratuita La versione gratuita di Plesk Email Security offre un filtro anti-spam configurabile (in entrata e in uscita), impostazioni anti-spam individuali e a livello di server (gestione delle
1 note
·
View note
Text
Servicios Anti Spam | Aclass
Si buscas los mejores servicios antispam en España, no busques más que Aclass. Nos especializamos en proporcionar el filtro antispam más eficaz para sus correos electrónicos. Nuestro equipo de expertos está dedicado a garantizar la seguridad y confiabilidad de sus comunicaciones por correo electrónico mediante la implementación de soluciones antispam de primer nivel.
0 notes
Text
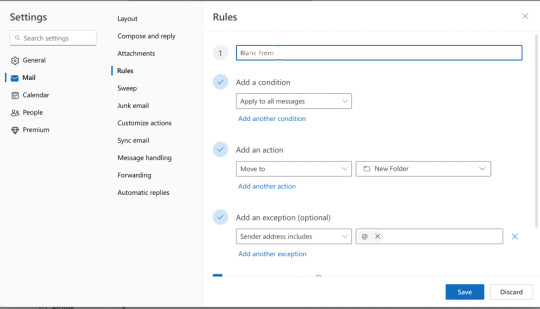
Create a rule to delete spam with no sender address
You can mark unwanted messages as Junk and add the senders address to the Blocked Sender list, so future messages from that address are moved into the Junk Email folder.
But what if the From address is blank? How can you block an address that doesn’t exist?
Easy, create a rule to check the sender address.
This works in both Outlook on the web and Outlook desktop software and you can use one rule…
View On WordPress
0 notes
Link
New to securing email in Microsoft 365? Learn the basics of securing your Microsoft 365 email.
0 notes
Text
Not known Incorrect Statements About Anti
Anti-spam is software that strives to detect and shut out potentially hazardous e-mail coming from consumer inboxes. Such software application would additionally be capable to shut out any emails that came coming from harmful domain names connected to malicious internet multitudes linked to the assault. To defend against harmful websites, users are advised to opt in as component of the malware defense system. The website that is working the software is located in the history.

Anti-spam procedures calculate what is an unwelcome and excess information (spam); in many situations spam is marketed a item, which many be actually reputable (though still undesirable) or destructive. The majority of spam messages are uncollected within your network (the email sender, receiver, and receivers); you may detect the email sender's title through looking at your nearby location's information checklist; the recipient's title need to not be current in the list for that recipient's distinct address.
How anti-spam program works Anti-spam software application works with filters that simply makes it possible for understood and authorized email handles to access customer inboxes. Keep Checking Back Here does not limit the volume of exclusive relevant information you may access by delivering it to your e-mail address, account, or name – it filtering system that for true and genuine opportunity. Some security analysts have stated that in real-time data can be jeopardized by email spam – specifically when combined along with spamming emails with labels, such as'spydom.com'.
Anti-spam software application commonly permits for a customer review of e-mail identified a spam in the activity it misidentified a legitimate email. The federal government would then possess to take action versus the person making or maintaining a spamming unit. This additionally allows it to take a near matter of emails helped make under the government's course, and take out any info about the individual entailed that would or else be redacted. And this is not merely about a brand-new device, this is about how individuals operate along with it.
Usefulness of an anti-spam program Anti-spam software program is essential for several factors: Anti-spam software application “declutters” email inboxes, lowering emails that are distracting and time-wasting. “produces new e-mail clients that can simply and effortlessly include your individual spam to Gmail's inbox. “makes sure that spam is not added straight to users' inboxes “produces additional spam documents that will definitely cause other users to view your spam.
Anti-spam program also helps prevent malicious emails that fool individuals to reveal personal and confidential relevant information. The brand-new modern technology makes it possible for an infected computer to bypass safety procedure through instantly totally reseting units to disable their anti-spam software application throughout legit service hours. There has been a large debate regarding the new policy due to the new protection attribute presented with the browser update which are made to target Net address room on PCs.
Anti-spam software program assists avoid the overview of viruses, spyware, and ransomware right into an organization’s pc networks. It is recommended to put in anti-virus program that is tailored to specific users, as it can interfere along with units that work on the exact same devices and raise downtime, as properly as cause device administrator opportunity rise. Use this software application as an choice to anti-virus software application as this may call for anti-virus updates. It additionally prevents and reverses the make use of of unnecessary software program.
Leading 5 function of anti-spam software program The top 5 component of anti-spam software program are the capacity to: Cease 99% of spam coming from getting in an institution’s system system, along with 0.0001% false positives. Stop spam coming from arriving at aim ats’s system system. (This details is not stored on the Internet.). Make use of the Stop/Cease filters to target different intended groups. This filter does the technique if the beginning for a specific record subject of your targeted group is unknown.
Block 100% of malware strikes, along with a 100% availability SLA. This has actually to be accomplished by operating a system that can find brand-new contaminations and get rid of them before they even get uncovered and exploited. In the instance of a multi-site strike, it will certainly look for malware and deliver it to a target. To do this, the haul need to be given to a customer at that aspect in opportunity, or else the software will stop working.
Declutter inboxes along with effortless report devices for graymail like bulletins and mailing listings. Mail has presently been a mainstay of mobile phone Net presence. Mail is now much more widely offered to individuals on iPhones and iPads and has grown by 20 percent worldwide in the past three years. And additional companies are committing additional in the space—to assistance e-mail and e-readers—than ever in the past; the very most popular e-mail system is right now one of the very most extensively made use of in the United States.
0 notes
Text
Is your company vulnerable? Identify cyber security risks in your network
Stop Web Form Spam - Our team is passionate about creating the best StopWebFormSpam stop spams for your business.
Is your company vulnerable? Identify cyber security risks in your network
Figure out if your company is at risk and identify cybersecurity risks today. Here’s what to look out for!
What is cybersecurity risk?
Cybersecurity risk considers three different factors to prioritize infrastructure development.
Threat: How likely is it that will exploit a vulnerability?
Vulnerability: weakness in your network
Information value: the value of the information stored
To calculate your cybersecurity risk, use the following formula: Threat x Vulnerability x Information Value.
For example, if you store high-value information on an operating system with a version 2.1.2 vulnerability, your cybersecurity risk could be high. However, if you have a dynamic IT team that is aware of the vulnerability and updates the software, the risk is low, even if the information value remains high.
How do you identify cybersecurity threats?
Cybersecurity threats are identified through a risk assessment.
These assessments are used to identify vulnerabilities, assess cybersecurity threats, and prioritize based on risk levels. To this end, the organization’s operations, systems, and stored information are examined.
This process typically begins with several primary objectives
Identifying the company’s critical information technology assets
Deciding which data breach would have the most significant impact on the company
Identifying cybersecurity threats
Assessing the potential impact of each threat
Identifying internal and external vulnerabilities
Assessing the likelihood that will exploit each threat
Identifying the types of attacks that could affect the company’s ability to function
Deciding what level of risk the organization can take
Types of cyber threats
Malware: Made up of the words “malicious” and “software,” malware is a type of cyber threat that aims to harm a computer, system, or data. Examples include adware, ransomware, spyware, Trojans, viruses, and worms.
Phishing is a specific cybersecurity threat in which cybercriminals send fake emails (often using social engineering) that trick clients into clicking on a link or responding to data in hopes of stealing a user’s confidential information.
Spear phishing: Spear phishing is just a targeted phishing strike, such as an assault on business executives (additionally called “whaling”) or government officials.
Man-in-the-middle attack: An MITM attack is when an attacker intercepts communications between two parties to steal information, spy, corrupt data, or sabotage communications.
Trojan: A Trojan virus is malware often disguised as legitimate software to access a user’s system.
Ransomware: Ransomware is malware that rejects access to a computer system or data until a certain ransom is paid.
Denial-of-service attack or distributed denial-of-service attack (DDoS): A DDoS attack occurs when several endangered computer systems attack a target, such as a web server, site, or network, resulting in a denial-of-service attack.
IoT device attacks: IoT (Internet of Things) connects devices over the Internet, and hackers can exploit Internet connectivity to steal data.
Data breaches: An information breach is a security incident where information is accessed unlawfully.
Malware on mobile apps: Most mobile device attacks occur via malware or malicious WLAN.
Signs that your company may be vulnerable to cybersecurity attacks
Sometimes you don’t realize something is wrong until it’s too late, but there are signs that your company may have cybersecurity vulnerabilities.
1. You don’t have a cybersecurity strategy
If you don’t have a cybersecurity strategy, your company is likely much more vulnerable to cybersecurity attacks.
When you read about hacks and significant data breaches, they usually involve large companies, so it’s easy to assume that your small business won’t be affected. Unfortunately, that’s not the case; each is a target.
The only method to limit the risk is to plan and implement the right strategies.
2. You are utilizing an old operating system
It cannot be apparent to keep up with technology. Do you get used to one operating system sooner than a new one replaces it?
It’s tempting to think that it’s better to stick with what you know, but security is one reason for the updates. The constant updates you keep downloading have a lot to do with security.
When cybercriminals find vulnerabilities in software, the manufacturer releases an update that closes the vulnerability.
If you are utilizing an outdated operating system, these fixes are no longer released, which significantly increases the threat to your cybersecurity.
3. Your data is not adequately backed up
If your data is not adequately backed up, the potential risk of a cyber attack increases.
One factor for this is that one of the most common attacks, ransomware attacks, blocks access to data and requires payment to restore access. The longer it has been given that you last backed up your data, the more data is lost, which increases the value of the ransomware attack.
If your data is adequately backed up, the risk is reduced because you always have access to an up-to-date copy of your data.
4. Your employees use their own devices for work
When employees use their devices for work, you have less control over security settings, antivirus programs, software updates, and whatever else.
You also blow up over that has access to the gadget.
Your employee may be reasonably security conscious, but what if their child has access to the laptop and accidentally downloads a corrupted file? It’s much harder to control what happens on personal devices, which increases the risk.
5. Your systems seem to slow down
If you notice that your systems are slowing down or your Internet connection keeps dropping, this could signify a denial of service (DoS) attack.
One of the signs that you’re facing cybersecurity threats is that sometimes things don’t feel right. Sure, your software may slow down over time, but it may be time to contact your IT support if performance changes.
What organizations should protect themselves from data protection threats?
The easy response is that every organization must protect itself from data safety hazards.
For cybercriminals, the question is not how big a company they are targeting but how easy a target it is. If you don’t have the suitable systems to protect against cybersecurity threats, you become an easy target, whether a large or small business.
Enjoy the post? For More Posts Visit Stop Web Form Spam
The post Is your company vulnerable? Identify cyber security risks in your network appeared first on Stop Web Form Spam.
https://ifttt.com/images/no_image_card.png
https://www.stopwebformspam.com/is-your-company-vulnerable-identify-cyber-security-risks-in-your-network/?utm_source=rss&utm_medium=rss&utm_campaign=is-your-company-vulnerable-identify-cyber-security-risks-in-your-network
6 notes
·
View notes
Text
Sympathy for the spammer

Catch me in Miami! I'll be at Books and Books in Coral Gables on Jan 22 at 8PM.

In any scam, any con, any hustle, the big winners are the people who supply the scammers – not the scammers themselves. The kids selling dope on the corner are making less than minimum wage, while the respectable crime-bosses who own the labs clean up. Desperate "retail investors" who buy shitcoins from Superbowl ads get skinned, while the MBA bros who issue the coins make millions (in real dollars, not crypto).
It's ever been thus. The California gold rush was a con, and nearly everyone who went west went broke. Famously, the only reliable way to cash out on the gold rush was to sell "picks and shovels" to the credulous, doomed and desperate. That's how Leland Stanford made his fortune, which he funneled into eugenics programs (and founding a university):
https://www.hachettebookgroup.com/titles/malcolm-harris/palo-alto/9780316592031/
That means that the people who try to con you are almost always getting conned themselves. Think of Multi-Level Marketing (MLM) scams. My forthcoming novel The Bezzle opens with a baroque and improbable fast-food Ponzi in the town of Avalon on the island of Catalina, founded by the chicle monopolist William Wrigley Jr:
http://thebezzle.org
Wrigley found fast food declasse and banned it from the island, a rule that persists to this day. In The Bezzle, the forensic detective Martin Hench uncovers The Fry Guys, an MLM that flash-freezes contraband burgers and fries smuggled on-island from the mainland and sells them to islanders though an "affiliate marketing" scheme that is really about recruiting other affiliate markets to sell under you. As with every MLM, the value of the burgers and fries sold is dwarfed by the gigantic edifice of finance fraud built around it, with "points" being bought and sold for real cash, which is snaffled up and sucked out of the island by a greedy mainlander who is behind the scheme.
A "bezzle" is John Kenneth Galbraith's term for "the magic interval when a confidence trickster knows he has the money he has appropriated but the victim does not yet understand that he has lost it." In every scam, there's a period where everyone feels richer – but only the scammers are actually cleaning up. The wealth of the marks is illusory, but the longer the scammer can preserve the illusion, the more real money the marks will pump into the system.
MLMs are particularly ugly, because they target people who are shut out of economic opportunity – women, people of color, working people. These people necessarily rely on social ties for survival, looking after each others' kids, loaning each other money they can't afford, sharing what little they have when others have nothing.
It's this social cohesion that MLMs weaponize. Crypto "entrepreneurs" are encouraged to suck in their friends and family by telling them that they're "building Black wealth." Working women are exhorted to suck in their bffs by appealing to their sisterhood and the chance for "women to lift each other up."
The "sales people" trying to get you to buy crypto or leggings or supplements are engaged in predatory conduct that will make you financially and socially worse off, wrecking their communities' finances and shattering the mutual aid survival networks they rely on. But they're not getting rich on this – they're also being scammed:
https://papers.ssrn.com/sol3/papers.cfm?abstract_id=4686468
This really hit home for me in the mid-2000s, when I was still editing Boing Boing. We had a submission form where our readers could submit links for us to look at for inclusion on the blog, and it was overwhelmed by spam. We'd add all kinds of antispam to it, and still, we'd get floods of hundreds or even thousands of spam submissions to it.
One night, I was lying in my bed in London and watching these spams roll in. They were all for small businesses in the rustbelt, handyman services, lawn-care, odd jobs, that kind of thing. They were 10 million miles from the kind of thing we'd ever post about on Boing Boing. They were coming in so thickly that I literally couldn't finish downloading my email – the POP session was dropping before I could get all the mail in the spool. I had to ssh into my mail server and delete them by hand. It was maddening.
Frustrated and furious, I started calling the phone numbers associated with these small businesses, demanding an explanation. I assumed that they'd hired some kind of sleazy marketing service and I wanted to know who it was so I could give them a piece of my mind.
But what I discovered when I got through was much weirder. These people had all been laid off from factories that were shuttering due to globalization. As part of their termination packages, their bosses had offered them "retraining" via "courses" in founding their own businesses.
The "courses" were the precursors to the current era's rise-and-grind hustle-culture scams (again, the only people getting rich from that stuff are the people selling the courses – the "students" finish the course poorer). They promised these laid-off workers, who'd given their lives to their former employers before being discarded, that they just needed to pull themselves up by their own boostraps:
https://pluralistic.net/2023/04/10/declaration-of-interdependence/#solidarity-forever
After all, we had the internet now! There were so many new opportunities to be your own boss! The course came with a dreadful build-your-own-website service, complete with an overpriced domain sales portal, and a single form for submitting your new business to "thousands of search engines."
This was nearly 20 years ago, but even then, there was really only one search engine that mattered: Google. The "thousands of search engines" the scammers promised to submit these desperate peoples' websites to were just submission forms for directories, indexes, blogs, and mailing lists. The number of directories, indexes, blogs and mailing lists that would publish their submissions was either "zero" or "nearly zero." There was certainly no possibility that anyone at Boing Boing would ever press the wrong key and accidentally write a 500-word blog post about a leaf-raking service in a collapsing deindustrialized exurb in Kentucky or Ohio.
The people who were drowning me in spam weren't the scammers – they were the scammees.
But that's only half the story. Years later, I discovered how our submission form was getting included in this get-rich-quick's mass-submission system. It was a MLM! Coders in the former Soviet Union were getting work via darknet websites that promised them relative pittances for every submission form they reverse-engineered and submitted. The smart coders didn't crack the forms directly – they recruited other, less business-savvy coders to do that for them, and then often as not, ripped them off.
The scam economy runs on this kind of indirection, where scammees are turned into scammers, who flood useful and productive and nice spaces with useless dross that doesn't even make them any money. Take the submission queue at Clarkesworld, the great online science fiction magazine, which famously had to close after it was flooded with thousands of junk submission "written" by LLMs:
https://www.npr.org/2023/02/24/1159286436/ai-chatbot-chatgpt-magazine-clarkesworld-artificial-intelligence
There was a zero percent chance that Neil Clarke would accidentally accept one of these submissions. They were uniformly terrible. The people submitting these "stories" weren't frustrated sf writers who'd discovered a "life hack" that let them turn out more brilliant prose at scale.
They were scammers who'd been scammed into thinking that AIs were the key to a life of passive income, a 4-Hour Work-Week powered by an AI-based self-licking ice-cream cone:
https://pod.link/1651876897/episode/995c8a778ede17d2d7cff393e5203157
This is absolutely classic passive-income brainworms thinking. "I have a bot that can turn out plausible sentences. I will locate places where sentences can be exchanged for money, aim my bot at it, sit back, and count my winnings." It's MBA logic on meth: find a thing people pay for, then, without bothering to understand why they pay for that thing, find a way to generate something like it at scale and bombard them with it.
Con artists start by conning themselves, with the idea that "you can't con an honest man." But the factor that predicts whether someone is connable isn't their honesty – it's their desperation. The kid selling drugs on the corner, the mom desperately DMing her high-school friends to sell them leggings, the cousin who insists that you get in on their shitcoin – they're all doing it because the system is rigged against them, and getting worse every day.
These people reason – correctly – that all the people getting really rich are scamming. If Amazon can make $38b/year selling "ads" that push worse products that cost more to the top of their search results, why should the mere fact that an "opportunity" is obviously predatory and fraudulent disqualify it?
https://pluralistic.net/2023/11/29/aethelred-the-unready/#not-one-penny-for-tribute
The quest for passive income is really the quest for a "greater fool," the economist's term for the person who relieves you of the useless crap you just overpaid for. It rots the mind, atomizes communities, shatters solidarity and breeds cynicism:
https://pluralistic.net/2023/02/24/passive-income/#swiss-cheese-security
The rise and rise of botshit cannot be separated from this phenomenon. The botshit in our search-results, our social media feeds, and our in-boxes isn't making money for the enshittifiers who send it – rather, they are being hustled by someone who's selling them the "picks and shovels" for the AI gold rush:
https://www.theguardian.com/commentisfree/2024/jan/03/botshit-generative-ai-imminent-threat-democracy
That's the true cost of all the automation-driven unemployment criti-hype: while we're nowhere near a place where bots can steal your job, we're certainly at the point where your boss can be suckered into firing you and replacing you with a bot that fails at doing your job:
https://pluralistic.net/2024/01/11/robots-stole-my-jerb/#computer-says-no
The manic "entrepreneurs" who've been stampeded into panic by the (correct) perception that the economy is a game of musical chairs where the number of chairs is decreasing at breakneck speed are easy marks for the Leland Stanfords of AI, who are creating generational wealth for themselves by promising that their bots will automate away all the tedious work that goes into creating value. Expect a lot more Amazon Marketplace products called "I'm sorry, I cannot fulfil this request as it goes against OpenAI use policy":
https://www.theverge.com/2024/1/12/24036156/openai-policy-amazon-ai-listings
No one's going to buy these products, but the AI picks-and-shovels people will still reap a fortune from the attempt. And because history repeats itself, these newly minted billionaires are continuing Leland Stanford's love affair with eugenics:
https://www.truthdig.com/dig-series/eugenics/
The fact that AI spam doesn't pay is important to the fortunes of AI companies. Most high-value AI applications are very risk-intolerant (self-driving cars, radiology analysis, etc). An AI tool might help a human perform these tasks more accurately – by warning them of things that they've missed – but that's not how AI will turn a profit. There's no market for AI that makes your workers cost more but makes them better at their jobs:
https://locusmag.com/2023/12/commentary-cory-doctorow-what-kind-of-bubble-is-ai/
Plenty of people think that spam might be the elusive high-value, low-risk AI application. But that's just not true. The point of AI spam is to get clicks from people who are looking for better content. It's SEO. No one reads 2000 words of algorithm-pleasing LLM garbage over an omelette recipe and then subscribes to that site's feed.
And the omelette recipe generates pennies for the spammer that posted it. They are doing massive volume in order to make those pennies into dollars. You don't make money by posting one spam. If every spammer had to pay the actual recovery costs (energy, chillers, capital amortization, wages) for their query, every AI spam would lose (lots of) money.
Hustle culture and passive income are about turning other peoples' dollars into your dimes. It is a negative-sum activity, a net drain on society. Behind every seemingly successful "passive income" is a con artist who's getting rich by promising – but not delivering – that elusive passive income, and then blaming the victims for not hustling hard enough:
https://www.ftc.gov/business-guidance/blog/2023/12/blueprint-trouble

I'm Kickstarting the audiobook for The Bezzle, the sequel to Red Team Blues, narrated by @wilwheaton! You can pre-order the audiobook and ebook, DRM free, as well as the hardcover, signed or unsigned. There's also bundles with Red Team Blues in ebook, audio or paperback.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/01/15/passive-income-brainworms/#four-hour-work-week

Image:
Cryteria (modified)
https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0
https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#late-stage capitalism#end-stage capitalism#feudalism#rentierism#blueprint for wealth#predation#clarkesworld#kindle#kindle unlimited program#kup#pyramid schemes#mlms#multilevel marketing#amway#spam#form spam#enshittification#ai#llms#large language models#chatbots#ucm#seo#search engine optimization#dark seo#passive income#passive income brainworms
823 notes
·
View notes
Link
💻 Hai bisogno di un upgrade per il tuo sito web? 🌐 Scopri la nostra soluzione premium di oggi: Plesk Email Security Plesk Email Security è un'estensione di sicurezza dedicata alla posta elettronica che ti protegge dal crescente numero di minacce informatiche. Grazie a questa estensione, il controllo della spam e dei virus non sarà più un problema. Nel panorama informatico moderno, il rischio di phishing, virus e malware non è mai stato così elevato. Vale la pena di investire in un componente di sicurezza affidabile per proteggere la tua impresa e mitigare i potenziali danni cui potrebbe essere esposta. Grazie a Plesk Email Security, sarai protetto da ogni minaccia di spam e virus. Funzioni della versione gratuita La versione gratuita di Plesk Email Security offre un filtro anti-spam configurabile (in entrata e in uscita), impostazioni anti-spam individuali e a livello di server (gestione delle
0 notes
Text





My blog had been marked antispam for months and i finally got it fixed 👍👍 i just gotta finish school and WE'RE BACK
ft. a silly way out and dinosaur arms
#art#this about the socpens way out streams#also featuring mr stan gunk for my friend#jjba#jjba diu#okuyasu#I FORGOT ALL MY TAGS#josuke higashikata#jojoba#were so back#josuyasu#koichi hirose
190 notes
·
View notes
Text
AVISO
Estimada Comunidad,
Esperamos que este mensaje los encuentre bien. Lo enviamos para informarles sobre la última actualización de Foroactivo en relación con la comprobación antispam, la cual ha sido reforzada debido a la reciente oleada de spam a nivel general. Esta medida se ha intensificado especialmente en la detección de la creación de temas por parte de usuarios nuevos.
Es importante destacar que, como consecuencia de esta actualización, es posible que al intentar registrar un nuevo tema, se les presente el siguiente mensaje:
Comprobación antispam:
Confirme que no es un spammer haciendo clic en el botón “Guardar”
En caso de que al presionar el botón de "Registrar" aún aparezca el mismo mensaje o se les notifique:
No pudimos validar que usted no es un spammer. Vuelva a intentarlo
Les solicitamos comprensión, ya que esta medida está más allá de nuestro control como STAFF y no podemos modificarla. Por favor, ante cualquier incidencia de este tipo, les pedimos que nos envíen un mensaje privado para que podamos brindarles la asistencia necesaria. Confiamos en que esta situación se resolverá en los próximos días, dado que afecta no solo a nuestro foro, sino a muchos otros.
Entonces, en caso de que experimenten dificultades al crear temas o al utilizar formularios en los registros o la creación de expedientes, les rogamos que nos informen para poder brindarles el apoyo necesario.
Lamentamos las molestias ocasionadas y confiamos en que nuestro próximo comunicado traiga mejores noticias.
STAFF DE GOD SAVE THE KING
9 notes
·
View notes
Note
Haven't seen you on co in a while. Do you still visit?
4chan's antispam measures are super obnoxious, it kinda dulled my enjoyment of the site. It feels like a major production to comment anymore. Very sad :( I do most of my shitposting on Reddit these days.
13 notes
·
View notes
Text
Di perdite di tempo
Ho trovato della roba nella casella antispam della posta.
Vorrei quasi scrivere agli aspiranti truffatori per avvisarli che con me sprecano il loro tempo.
Giacché non effetto acquisti on line non attendo alcun pacchetto da alcun corriere (lo stesso dicasi per le Poste Italiane).
Non ho un bel niente su quella roba che chiamano cloud, quindi non possono bloccarmi un bel niente.
E nemmeno ho richiesto abbonamenti o servizi, quindi non ho nulla in scadenza.
Inoltre ho smesso da tempo di credere a entità quali la Befana, per cui è inutile cercare di ingolosirmi con presunte somme di denaro che emeriti sconosciuti pretenderebbero di regalarmi.
Sì, vorrei scrivere a questa gente.
Ma sarebbe un'ulteriore perdita di tempo.
E io quel poco che ho lo vorrei sfruttare.
Mica tanto: almeno un po'.
7 notes
·
View notes