#are html ids case sensitive
Text
HTML
New Post has been published on https://hazirbilgi.com/what-is-html-when-and-by-whom-was-html-created/
HTML
What is HTML? When and by whom was HTML created?
HTML is a markup language that defines the structure of web pages. HTML is one of the basic building blocks of every website . For this reason, it is among the first details that web developers will want to learn.
While HTML is an important building block, it is not enough to make a web page look good. It must be supported by CSS and JavaScript . HTML is essentially code and is used to structure the content of a web page.
The content on the web page can consist of a number of different paragraphs, images and tables. It is possible to format them with HTML. In this way, the web browser knows how to configure the web page that a person visits and displays it in the direction desired by the developer.
What is HTML and when was it invented?
HTML or hypertext markup language is a markup language developed for displaying materials or data on the internet. Each material has a known buyer location, called a web page . Web pages contain hypertext links that allow the fetching of related pages.
HTML is the markup language used to code web pages. HTML was designed by British scientist Sir Tim Berners-Lee in 1980 . HTML markup tags contain document elements such as headings, paragraphs, and tables. Once formatted, they can be viewed by programs or applications known as web browsers.
When viewing a web page, web browsers interpret it according to permitted technology. Thus, items such as headings, paragraphs, and tables are presented adapted to the screen size and font used. HTML documents also contain anchor links, called links to other web pages.
What is Semantic HTML?
Semantic HTML is the conveying of literal meanings for the uses of HTML tags. Semantic HTML was used effectively throughout most of the 90’s and became an important part of the standard HTML structure . Since the late 90’s, CSS has become more important in web pages when it has been used effectively .
Semantic HTML
It consists of tags such as , ,,, and . One of the most important reasons to use semantic HTML tags is that web crawlers can easily index the web page. In this direction, it is possible to improve the web page in terms of SEO . Also, semantic HTML is important for accessing web pages from screen readers.
What are HTML Versions?
After HTML was designed, it has developed in many different forms over the years. For this reason, the HTML versions that are used effectively have changed from time to time. There are five different versions of HTML that are used effectively. Each of them made extra contributions to the HTML structure, making it easier for the developers to use it.
HTML 1.0: It is the first version developed for HTML. It was published in 1991 and was used effectively until 1995.
HTML 2.0: Version released in 1995. It has been accepted as the standard version in web design. Added support for features such as text boxes and buttons.
HTML 3.2: Published by the W3C in 1997. It provided extra support in terms of table creation and form elements. It is considered the official standard since 1997.
HTML 4.01: Released in 1999. It is the stable language for the HTML language and is considered the official standard. It has added CSS support to the HTML language.
HTML5: It is the newest version of the HTML language and was announced in 2008. This version is developed by W3C and WHATWG .
What’s the Difference Between HTML Tags, Elements, and Attributes?
HTML tags , HTML elements, and HTML attributes are often confused and used interchangeably when defining. However, there are differences between these three elements. Each HTML tag has its own unique meaning. HTML elements are used to describe content. HTML attributes provide additional information for existing HTML elements.
What are HTML Tags?
HTML defines the formatting of a particular web page. For this reason, the text, images and other content on the page should be displayed in a shaped way. For example, you may want some text to be uppercase, lowercase, bold, or italic. To do this, you need to use HTML tags .
HTML tags are like keywords that define how the web browser will display the content. When a web browser reads a document containing HTML, it reads it from top to bottom and from left to right. Thanks to HTML tags, a web browser can distinguish between HTML content and simple content. Each HTML tag can have different properties.
What are HTML Elements?
HTML consists of three elements , opening tag, content and closing tag . Some elements are used as empty. HTML elements are often confused with HTML tags. However, an element consists of a combination of three different elements. All HTML files are made up of elements. These elements are responsible for creating web pages. They also describe the content on the web page.
Theoretically, the opening tag, content, and closing tag should go together. Some elements may not have content and closing tags. Such elements are called empty elements or self- closing elements . For example, a line spacer
and a straight long line.
elements in this structure.
What are HTML Attributes?
HTML attributes are placed in the opening tag, and they range from the “style” to the “id” description. HTML attributes help convey more information about an element. In addition, these attributes ensure that needs such as styling elements on the web page with JavaScript are met.
While HTML attributes provide additional information about elements, they are modifiers of the HTML element. Each element defines the behavior of the element to which it is attached. HTML attributes must always be applied with the start tag. Although the names to be given to HTML attributes are case sensitive, standard usage consists of lowercase letters.
html,are html tags case sensitive,are html and css programming languages,are html and css the same,are html files safe,are html attachments safe,are html and javascript the same,are html tables still used,are html ids case sensitive,are html sites reliable,are html attributes case sensitive,create an html file,create an html page,can html files be dangerous,create an html table,create an html form,can html id have spaces,create an html element in javascript,create an html link,convert an html to pdf,
#are html and css programming languages#are html and css the same#are html and javascript the same#are html attachments safe#are html attributes case sensitive#are html files safe#are html ids case sensitive#are html sites reliable#are html tables still used#are html tags case sensitive#can html files be dangerous#can html id have spaces#convert an html to pdf#create an html element in javascript#create an html file#create an html form#create an html link#create an html page#create an html table#html
0 notes
Text
Dicas e Recomendações p/ iniciantes em Programação
Tenho me deparado constantemente com os questionamento, de colegas e amigos, sobre: como começar a programar ou para alguns, "codar" ?
Apesar de não ser a minha especialização e muito longe área de interesse, pensei em uma maneira de construir um fluxograma de processo e recomendação de conteúdo para estudar e aprender a programar.
Mas de antemão, deixarei um adendo e recorte de um comentário que li num vídeo do YouTube, tratando justamente sobre o assunto, de Waldeck Vieira.
"Sou desenvolvedor com anos de experiência e vou dar as minhas dicas, principalmente com tantas promessas absurdas que tem hoje de cursos que fazem você virar desenvolvedor em um mês!
Curso é importante sim, mas não vai te fazer virar um desenvolvedor bom em poucos meses!
Estudar é importante sim, mas o que vai fazer você ficar bom, é o treino! Treinar, treinar e treinar muito todos os itens que vou destacar abaixo. É igual aprender a tocar um piano bem, vc nunca vai ser um bom pianista em poucos meses e só estudando teoria, o que vai fazer vc ficar bom é o treino diário!
Não se preocupe em decorar nada, o importante é treinar e entender! Decorar só serve para fazer prova de colégio ou prova de emprego. Mas não mede sua capacidade! Os comandos vc decora praticando!
Já vi muito youtuber bom dizendo que precisa decorar as coisas! Isso é um absurdo, ainda mais hoje que tudo muda toda hora! E cada linguagem vc tem uma forma de escrever os comandos(sintaxe), então não precisa decorar tudo! Ninguém, nem o melhor dev do mundo sabe tudo decorado! O que ele sabe é resolver e entende muita coisa, quando esquece a sintaxe de algo, ele simplesmente consulta na documentação ou na net!
Você só começa a ser um bom desenvolvedor a partir de pelo menos, no mínimo, uns 6 meses de muita prática! Agora ser um dos melhores só fazendo projetos reais e tendo um emprego! Então, mesmo que vc pense em trabalhar com a programação, tenha um emprego, por pelo menos 1 ano! Vc vai ver como vc vai evoluir!
Não precisa começar a estudar só no caderno, escolha uma linguagem, como Python ou JavaScript e pratique nela todos os conceitos!
Itens mais importante para começar e eu iria nessa sequencia. Pratique por pelo menos duas semanas cada item, e tente entender muito bem, e já use uma linguagem, tipo Python ou JavaScript:
Variáveis e seus tipos, case sensitive, constantes, identação do código, condicionais (o famoso if), loops (os famosos for e while), procedures, funções, algoritmos para tratamento de strings, arrays, estrutura de dados aplicada na linguagem escolhida(Essa realmente é uma parte muito importante), conceitos de orientação a objeto. Esse para mim é o básico.
Treine pelo menos uns 5 meses tudo isso! Depois você precisa estudar e praticar, HTML, CSS combinado com JavaScript, mesmo que vc não vá desenvolver para a web, mas vc pode precisar criar um serviço na web para um sistema que vc desenvolveu! Depois estude linguagem SQL para banco de dados, usando uma IDE de desenvolvimento para banco (SQL Server ou MySQL), eu indico!
E uma dica, banco de dados é um mundo a parte, e vc precisa dominar muito a linguagem SQL, dos bancos relacionais (SQL Server, MySQL, Oracle e etc), que é comum em todos os bancos de dados, pois é com ela que vc manipulas os dados, e corrige erros, aumenta a performance de uma consulta e etc!
Então depois de pelo menos mais de 6 meses a 1 ano, estudando e praticando muito tudo isso que coloquei. Desenvolva projetos reais, usando uma linguagem e um banco de dados. E a partir dai, se possível arrume um emprego, e sempre estude e pratique muito em qualquer linguagem e nas novidades do mercado! É isso!".
Portanto, repassado todos os alertas que já venho feito, passarei indicações de conteúdo e ferramentas.
Começaremos pela IDE, mas o que é isso? é um Ambiente de Desenvolvimento no qual utilizamos para programar ou codificar.
Vale ressaltar que a IDE pode variar de linguagem para linguagem no qual ira programar. Citarei alguns a seguir, gratuitos:
JavaScript, recomendo o Visual Studio Code. Pois o VS Code, é uma ferramenta simples, esta sendo constantemente tendo correção de bugs, disponível em diversos idiomas, inclusive PT-Br, compatível com os sistemas: Windows, Linux e Mac. E é possível compilar nas mais diversas linguagens de programação, além de muitas outras funcionalidades, que deixarei vocês conhecerem por si mesmos;
Python, indico o PyCharm e Jupyter Notebook. O VS Code também é uma boa, porém um pouco mais trabalhoso para desenvolver. Mas porque, o python se utiliza de uma IDE especifica ? Por causa, da necessidade de invocar Bibliotecas (coleção de subprogramas usados no desenvolvimento de softwares). Quando trabalhamos com o VS Code por exemplo, toda biblioteca que for utilizar, ira ter que realizar a instalação através do Prompt de comando, ou Terminal, se seu sistema for Linux. Já se vc utilizar IDEs como: Pycharm e Jupyter Notebook, não terá a dor de cabeça de pensar nesse aspecto. E o fato de que não tem a necessidade de criar ou ajustar um venv e outros;
SQL, destaco o MySQL Workbench, Oracle SQL e SQL Server Management Studio (SSMS). O SQL, é uma linguagem que geralmente se organiza em planilha ou tabelas de larga escala, que para quem deseja programar nesta linguagem se faz necessário uma ferramenta que trabalhe especificamente com isso e proporcione uma visualização clara e precisa dos dados, para assim poder fazer a estruturação.
Por se tratar de guia para programadores iniciantes, ficaremos apenas nesses linguagens.
Acrescento que ao contrário do que muitos pensam, HTML e CSS, NÃO SÃO LINGUAGENS DE PROGRAMAÇÃO!
São apenas Linguagens de Marcação e Formatação de Texto e Estilo.
HTML: linguagem de marcação utilizada para estruturar os elementos da página, como parágrafos, links, títulos, tabelas, imagens e até vídeos.
CSS: linguagem de estilos utilizada para definir cores, fontes, tamanhos, posicionamento e qualquer outro valor estético para os elementos da página.
JavaScript: linguagem de programação utilizada para deixar a página com mais movimento, podendo atualizar elementos dinamicamente e lidar melhor com dados enviados e recebidos na página.
Exemplo dessa combinação:
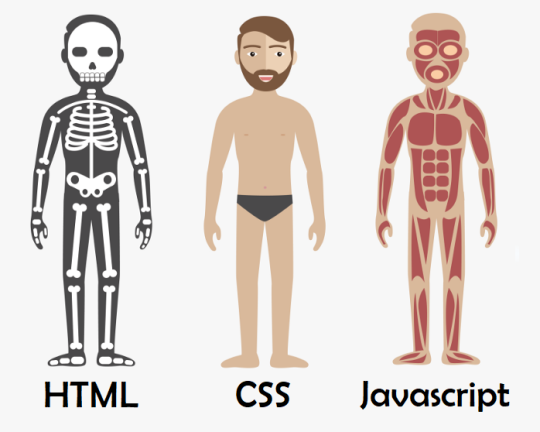
Explicação simples e didática que emprestei da Alura.
Já recomendado IDEs, esclarecido algumas confusões que ocorrem, darei prosseguimento para a indicação de conteúdos para estudo.
Eu particularmente, comecei a ter noção de lógica de programação e a saber a programar jogando os APPs, que foram desenvolvidos especificamente para isso:
Grasshopper, é o aplicativo desenvolvido pela Google, que tem o objetivo de ensinar a linguagem JavaScript, Recursos: quebra-cabeças visuais desenvolvem suas habilidades de resolução de problemas e solidificam os conceitos de programação; feedback em tempo real te orienta como um professor; coleciona conquistas à medida que aprende novas habilidades e ganha certificado.
O aplicativo está disponível para Android e iOS.
Mimo, o aplicativo te instruí a desenvolver em: HTML, JavaScript, CSS, Python e SQL. Além do que já destaquei no app anterior e a possibilidade de dialogar e competir com outra pessoas que também o utilizam para aprender a programar.
O aplicativo está disponível para Android e iOS.
Meoweb: Jogo de programação, a ideia do jogo é que você precisa ajudar Agatha a resgatar os gatinhos perdidos. Você precisa resolver os quebra-cabeças que estão nas plataformas para ajudá-la. Você receberá diferentes desafios que precisa resolver para chegar ao próximo nível. Que consiste em comandos em CSS, é muito fofo e divertido.
Disponível apenas para Android.
Code Combat, é jogo apenas na versão web, onde vocês podem aprender a desenvolver em Python, JavaScript, CoffeeScript e Lua. A curva de aprendizado é bastante suave, começando com comandos básicos de lógica em um universo agradável e colorido. Tudo isso é possível graças à ação de colaboradores do mundo todo, em um projeto aberto, com página no Github.
Disponível em diversos idiomas, incluindo português.
E a vídeos aulas:
Canal Curso em Vídeo :
Algoritmos e Lógica de Programação;
Banco de Dados com MySQL;
HTML5 + CSS3 + JavaScript;
HTML + CSS (módulo 1);
HTML + CSS (módulo 2);
HTML + CSS (módulo 3);
HTML + CSS (módulo 4);
JavaScript e ECMAScript;
Python 1 (princípios básicos);
Python 2 (Estrutura de Controle);
Python 3 (Estrutura Composta).
Vale ressaltar que uma coisa importantíssima é tornar disponível e visível os seus trabalhos, e uma ótima plataforma para isso, com uma ampla comunidade é o GitHub.
Mas o que é o GitHub ?
É uma plataforma de hospedagem de código-fonte e arquivos com controle de versão usando o Git. Ele permite que programadores, utilitários ou qualquer usuário cadastrado na plataforma contribuam em projetos privados e/ou Open Source de qualquer lugar do mundo. - Wikipédia.
Por ser uma plataforma que será importante para o desenvolvimento de seus projetos e trabalhos, e portfólio futuro, deixarei vídeos que te auxiliaram a adquirir o conhecimento pleno das funcionalidades da plataforma.
Curso de Git e GitHub.
Como personalizar o seu perfil no GitHub.
Ademais, acredito que isso é tudo pessoal, o vídeo que me inspirou em escrever esse post na tentativa de auxiliar, desfazer desentendidos e indica conteúdo, foi o casal do canal Código Fonte TV: O MÍNIMO QUE VOCÊ PRECISA SABER ANTES DE PROGRAMAR!.
No qual desmitifica e apoia toda a argumentação e pontos que destaquei até aqui e é claro recomenda mais conteúdo teórico, além do que já escrevi.
Espero ter ajudado em alguma coisa ou mesmo tirado a dúvida de vocês, sintam-se a vontade de curtir, compartilhar e comentar nestes post e outros.
Desde já agradeço pelo seu tempo e atenção, e até um próximo post.
Referências Bibliográficas do que foi abordado:
HTML, CSS e Javascript, quais as diferenças? ;
IDE PARA PYTHON: O QUE É, COMO ESCOLHER E LISTA DAS MELHORES;
Link das IDEs:
Jupyter Notebook;
MySQL Workbench;
Oracle SQL;
PyCharm;
SQL Server Management Studio (SSMS);
Visual Studio Code.
Vídeo Aulas recomendadas:
Algoritmos e Lógica de Programação;
Banco de Dados com MySQL;
Curso de Git e GitHub.
Como personalizar o seu perfil no GitHub.
HTML5 + CSS3 + JavaScript;
HTML + CSS (módulo 1);
HTML + CSS (módulo 2);
HTML + CSS (módulo 3);
HTML + CSS (módulo 4);
JavaScript e ECMAScript;
Python 1 (princípios básicos);
Python 2 (Estrutura de Controle);
Python 3 (Estrutura Composta).
O MÍNIMO QUE VOCÊ PRECISA SABER ANTES DE PROGRAMAR!
Aplicativos recomendados:
Code Combat;
Grasshopper;
Meoweb: Jogo de programação;
Mimo.
10 notes
·
View notes
Text
Hiding Assets in CSS Profiles: What You Need to Know

Introduction
Welcome to the world of CSS, where the art of web design meets the science of presentation. In this blog post, we delve into a fascinating aspect of CSS—hiding assets in profiles. While CSS is primarily known for styling and layout, its capability to conceal assets brings an additional layer of versatility to web development. Join us on a journey through the fundamentals, techniques, and best practices of hiding assets in CSS, unraveling the power and potential this feature holds for web designers and developers alike.
The Basics of CSS

Cascading Style Sheets, or CSS, form the backbone of web design by allowing developers to control the appearance and layout of HTML elements. Understanding the basics of CSS is essential for anyone venturing into the world of web development. Let's explore the key concepts:
- Selectors: CSS uses selectors to target HTML elements and apply styles. Selectors can be based on element types, classes, IDs, or other attributes.
- Properties and Values: CSS styles are defined through properties and values. For example, the color property sets the text color, and the value can be a specific color name or code.
- Box Model: The box model conceptualizes HTML elements as boxes with content, padding, borders, and margins. Understanding how these components interact is crucial for precise layout control.
- Layout: CSS provides various layout options, including Flexbox and Grid, to arrange and align elements on the webpage. These layouts contribute to responsive and visually appealing designs.
- Transitions and Animations: CSS enables the creation of smooth transitions and animations, enhancing user experience. This includes effects like fading, sliding, and rotating elements.
For a quick reference, here's a simple table summarizing some essential CSS properties:
PropertyDescriptioncolorSets the text colorfont-sizeSpecifies the font sizemarginDefines the margin space around an elementpaddingSpecifies the padding space inside an elementdisplayDetermines how an element is displayed
Mastering these fundamental aspects of CSS lays the groundwork for more advanced styling and, in the context of this blog post, for understanding how to manipulate CSS for asset hiding purposes.
Why Hide Assets in CSS?
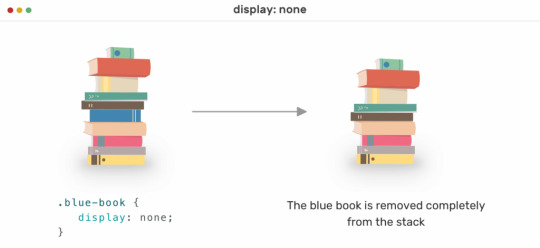
Concealing assets in CSS introduces a layer of complexity that can serve various practical purposes in web development. Let's explore the motivations behind hiding assets and the benefits it brings:
- Security: Hiding sensitive assets, such as API keys or authentication tokens, in CSS can enhance the security of a web application. This makes it more challenging for malicious actors to access and exploit these critical elements.
- Design Optimization: Concealing background images, icons, or other decorative elements in CSS can optimize the design by reducing the number of HTTP requests. This, in turn, enhances page loading speed and contributes to a smoother user experience.
- Code Organization: Placing assets in CSS allows for better organization of code. By consolidating styles and assets in one place, developers can streamline the maintenance process and make the codebase more modular and understandable.
- Responsive Design: Hiding certain assets based on screen size or device type is a common practice in responsive design. This ensures that the web page adapts gracefully to different devices, providing a consistent and visually appealing experience.
- Brand Protection: Concealing proprietary design elements or brand assets in CSS helps protect intellectual property. This is particularly important for businesses that want to safeguard their unique visual identity from unauthorized use or duplication.
Understanding the specific use case for hiding assets in CSS is crucial for implementing this technique effectively. Whether it's enhancing security, optimizing performance, or maintaining a consistent brand image, the decision to hide assets should align with the overall goals and requirements of the web development project.
Common Techniques
When it comes to hiding assets in CSS, developers have several techniques at their disposal. Each method serves a specific purpose, offering flexibility in implementation. Let's explore some common techniques employed for hiding assets:
- Display Property: Setting the display property to none is a straightforward way to hide an element. However, keep in mind that this completely removes the element from the layout, affecting the document flow.
- Opacity: Using the opacity property allows for creating transparent elements. While the element remains in the layout, it becomes visually hidden. Adjusting the opacity value from 0 to 1 controls the degree of transparency.
- Visibility Property: The visibility property offers options like visible and hidden. Similar to the display property, it hides the element but still occupies space in the layout.
- Text Indentation: For hiding text content, applying a negative text indentation can push the text off-screen without affecting its container's layout. This is effective for screen readers and SEO optimization.
- Background Image: Placing assets in the background, especially using CSS pseudo-elements like ::before and ::after, provides a method for hiding decorative elements while maintaining accessibility and document flow.
Here's a quick reference table summarizing these common techniques:
TechniqueDescriptionDisplay PropertySets the element's display type to hide it from the layout.OpacityMakes the element visually transparent without removing it from the layout.Visibility PropertyHides the element while still occupying space in the layout.Text IndentationPushes text content off-screen, rendering it effectively hidden.Background ImageUses background properties to hide decorative assets.
Choosing the right technique depends on the specific requirements of the project and the desired behavior for hidden assets.
Best Practices
While hiding assets in CSS can be a powerful tool, it's essential to adhere to best practices to ensure effective implementation and maintainability. Here are some recommended practices to consider:
- Semantic HTML: Always use semantic HTML to structure your content. Proper HTML markup ensures that your document remains accessible and adheres to web standards.
- Progressive Enhancement: Implement hiding techniques as a form of progressive enhancement. Ensure that essential content and functionality remain accessible even if CSS is disabled or not fully supported.
- Avoid Important Rule: Minimize the use of the !important rule, as it can lead to specificity issues and make the code harder to maintain. Instead, prioritize well-structured and specific selectors.
- Responsive Considerations: Test the visibility of hidden assets across different devices and screen sizes to ensure a consistent and user-friendly experience. Responsive design principles should apply to both visible and hidden elements.
- Document the Code: Provide clear documentation for any hidden assets and the associated CSS. This makes it easier for collaborators to understand the purpose of hidden elements and how they contribute to the overall design.
Here's a concise table summarizing these best practices:
PracticeDescriptionSemantic HTMLUse proper HTML markup for semantic structure and accessibility.Progressive EnhancementImplement hiding techniques as a progressive enhancement, ensuring core content accessibility.Avoid Important RuleMinimize the use of the !important rule for maintainable and specific styles.Responsive ConsiderationsTest visibility across devices to maintain a consistent user experience.Document the CodeProvide clear documentation for hidden assets and associated CSS for better collaboration.
By following these best practices, developers can ensure a robust and maintainable approach to hiding assets in CSS, contributing to a positive and efficient development process.
Case Studies
Exploring real-world examples of hiding assets in CSS provides valuable insights into the practical applications and benefits of this technique. Let's delve into a couple of case studies that showcase the effectiveness of concealing assets:
- Securing API Keys: In a web application that interacts with external APIs, it's common to use API keys for authentication. However, exposing these keys in client-side code poses a security risk. By hiding the API keys in CSS, developers can add an extra layer of security, making it more challenging for malicious actors to access and misuse the keys.
- Optimizing Image Loading: Consider a scenario where a website has multiple versions of an image for different screen sizes. Rather than loading all versions and relying on responsive design to display the appropriate one, developers can hide the unnecessary versions in CSS. This reduces the number of HTTP requests, leading to faster page loading times and improved performance.
Let's break down the second case study further with a table:
ScenarioImplementationOutcomeOptimizing Image LoadingHide additional image versions using CSS based on media queries and screen sizes.Faster page loading times, reduced bandwidth usage, and improved overall website performance.
These case studies demonstrate the versatility of hiding assets in CSS for both security and performance optimization. By adapting these techniques to specific project requirements, developers can create more robust and efficient web applications.
FAQ
Here are answers to some frequently asked questions about hiding assets in CSS:
Q: Why would I want to hide assets in CSS?
A: Hiding assets in CSS can serve various purposes, including enhancing security by concealing sensitive information, optimizing design for better performance, and organizing code for improved maintainability.
Q: Is it always secure to hide assets in CSS for sensitive information?
A: While hiding assets adds a layer of security, it's important to note that it's not foolproof. Critical security measures, such as server-side validation and encryption, should also be implemented to ensure comprehensive protection.
Q: How does hiding assets affect SEO?
A: Hiding assets using techniques like text indentation doesn't negatively impact SEO, as search engines prioritize visible content. However, using techniques that involve hiding entire elements could potentially affect SEO, so it's crucial to consider the specific method used.
Q: What is the role of responsive design in hiding assets?
A: Responsive design and hiding assets often go hand in hand. By strategically hiding certain elements based on screen sizes or device types, developers can ensure a consistent and optimized user experience across various devices.
Q: Are there any accessibility considerations when hiding assets?
A: Yes, accessibility is crucial. Developers should ensure that hidden assets do not compromise the accessibility of the website, especially for users relying on screen readers. Using proper semantic HTML and testing with accessibility tools is essential.
Conclusion
In conclusion, the practice of hiding assets in CSS offers a versatile set of tools for web developers to enhance security, optimize design, and organize code efficiently. Throughout this blog post, we've explored the basics of CSS, the motivations behind hiding assets, common techniques, best practices, and real-world case studies. Let's recap the key takeaways:
- Understanding CSS Basics: A solid grasp of CSS fundamentals, including selectors, properties, and layouts, lays the foundation for effective asset hiding.
- Motivations for Asset Hiding: Whether for security, design optimization, or code organization, hiding assets in CSS addresses various needs in web development.
- Common Techniques: Techniques such as using the display property, opacity, and background images provide flexible options for hiding assets based on specific requirements.
- Best Practices: Following best practices, including semantic HTML, progressive enhancement, and responsive considerations, ensures a reliable and maintainable approach to hiding assets.
- Case Studies: Real-world examples illustrate how hiding assets can contribute to improved security and performance in different scenarios.
- FAQ: Addressing common questions provides clarity on the considerations and implications of hiding assets in CSS.
By incorporating these insights into your web development workflow, you can harness the power of CSS to not only style and layout but also to strategically hide assets for a more secure, efficient, and user-friendly online experience.
Read the full article
0 notes
Text
How to do programming in PHP
PHP, short for Hypertext Preprocessor, is a popular web programming language. Simplicity, adaptability, and dynamic and interactive online applications are its hallmarks. This is the spot to learn PHP programming for beginners. This guide will teach you PHP fundamentals step-by-step.
Prerequisites
Basic HTML and CSS expertise is helpful before learning PHP. Understanding these languages simplifies PHP code integration into web sites.
Setting Up Your Environment
PHP programming requires a development environment. The essential setup stages are:
Web Server: XAMPP, WAMP, or MAMP, which include PHP, Apache, MySQL, and other technologies, can be used. Use a cloud-based development environment instead.
Text editor or IDE: Use Visual Studio Code, Sublime Text, or PhpStorm, which supports PHP.
PHP Installation: Without XAMPP, you must install PHP individually. The official PHP website (php.net) offers the newest version.
Writing Your First PHP Script
Start with a simple "Hello, World!" example to learn PHP:
```php �?php echo "Hello, World!"; ?>
Save the code as a .php file (e.g., hello.php) and store it in your web server's document root folder.
To run the script, navigate to http://localhost/hello.php in your browser. The page should say "Hello, World!"
The PHP syntax
PHP code is contained in <?php and ?> tags. The server interprets PHP code within these tags.
These syntactic components are important:
Statements terminate with a semicolon (;).
Variables begin with a $ symbol (e.g., $variable_name).
Comments can be single-line (//) or multi-line (/* */).
Web page content is produced using echo commands. Variables, data types
PHP supports integers, floats, texts, booleans, arrays, and objects. The variables must begin with a $ and are case-sensitive. Example of variable usage:$name = "John"; $age = 25; $isStudent = true; The Control Structure PHP offers standard control structures such as `if`, `else`, `while`, `for`, and `switch`. These enable code choices and loops.
php if ($age < 18) { echo "You are a minor."; } otherwise { echo "You are an adult."; }
Functions
PHP functions encapsulate reusable code. How to define and invoke a function:
PHP function greet($name) { echo "Hello, $name!"; }
Say hello to "Alice"
Working with Forms
PHP processes HTML form data. To retrieve form data, use the $_POST or $_GET superglobal arrays. Simple form example:
```html Also in `process_form.php`: PHP <?php $username = $_POST["username"]; echo "Welcome, $username!"; ?>
This guide laid the groundwork for PHP programming. As you master the basics, you may learn about databases, user authentication, and dynamic web applications. PHP's large community and copious documentation make it a superb web development language, and there are many online resources to help you learn PHP. Get coding and develop PHP web applications!
#dissertation#essay writing#research paper#thesis#case study help#homework help#report#reportwriting#php#phpdevelopment#php script#php programming
0 notes
Text
Price: [price_with_discount]
(as of [price_update_date] - Details)
[ad_1]
Are you fed up with storage warning on your Mobile Phone? Are you still worried about the inner storage of your new mobile phone which cannot be enough? - Gulloe is a creative USB 3.0 Flash Drive which has double connectors, can be transferred the documents for all series products of mobile phone.Plug and Play - Just plug in Gulloe USB flash drive to start moving photos and videos off your mobile phone.- Use the in-app camera to save photos and videos directly to Gulloe memory stick flash drive, so you can free up your phone's memory for other things. -Transfer files between your mobile phone and laptop.High Transfer Speed USB 3.0 - Read up to 80 MB/s, Write up to 30 MB/s Moblie phone port- Read up to 30 MB/s, Write up to 10 MB/sData EncryptionGulloe usb memory stick also includes encryption software to password protect files, so you can share content while keeping sensitive files secure.Media Formats SupportedMusic:M4A / AIFF / CAF / MP3 / WAVImage:GIF / JPG / PNG / JPEGVideo: AVI / FLV / M4V / MKV / MOV / MP4 / RMVBDocument: DOC / PPT / XLS / XLSX / PDF / HTML / TXDevice Support Support almost all Mobile Phone models including Windows 2000/7/8/8.1/10/Vista/XP/2000/ME, Linux and MacOs 10.3 and above.Please Note IF NECESSARY, PLEASE REMOVE PHONE CASE FIRST.Phone Devices: Need to download the free APP "Y-DISK" from APP Store.Android Devices: Only Android Smart Phone/Tablet with OTG Micro USB/Type-C connector can working with USB flash drive.
【High Speed and One Click Backup】 Experience up to 80 MB/s reading and 40 MB/s writing speed, and photos, videos, documents can be backup to the 1tb flash drive with one click. The iphone memory stick provides a simple and quick way to transfer photos and videos. Allows you to free up the memory on your mobile device without using a data cable or iCloud. With this iphone photo stick, you don’t have to worry about Phone storage anymore! Make file transfer easier.
【Thumb Drive Access Security】Use the iphone thumb drive to easily share data with family, friends and colleagues, making entertainment and work more interesting. The Password & Touch ID can encrypt file information in APP to protect your private files, you can choose to encrypt the entire usb flash drive, or you can choose to encrypt a specific file. All encrypted files stored in this iphone flash drive are invisible on the computer. No worry that others steal your files.
【Watch Video Directly and Share to Social Media】Plug and play, you can watch the movie/play music directly on the iphone flash drive 1tb. When you take beautiful photos on the go, you can store the photos or videos directly on the Phone flash drive without occupying your device memory. Also you can share document/photo to the social media directly from a iphone storage device. (Facebook, Twitter, etc.)
【Photo Stick Storage】USB storage drive is made of frosted aluminum metal. With slidable design. Flash drive has 1tb of memory, you can record your life as you wish to the usb stick. USB storage has dedicated email customer support. You can contact us after 18:00 PDT and we will answer your questions as soon as possible.
[ad_2]
0 notes
Text
Research and Planning For Trailers: Part 20- Symbolism/Details
After learning about how to incorporate hidden details and symbolic meanings in films, I decided that I wanted to do the same thing for our trailers. As the director I wanted the character’s Halloween costumes to have a symbolic meaning. So Jiya and I after a lot of research and analysing of our characters found the perfect costumes for them.
In the film Suhana and Varun were supposed to go as Barbie and Ken. But Suha then dresses up as Tinkerbell when she finds out that that Naisha and her boyfriend are going as Wendy and Peter Pan. In Peter Pan we all know that Tinkerbell likes Peter Pan and is jealous of Wendy. This makes the perfect love triangle. Suhana is Tinkerbell as she wants to be with Naisha’s boyfriend who is Peter Pan and she hates Naisha who is dressed up as Wendy. It also symbolises that Suhana cheated with Rahul (Naisha’s boyfriend). Varun we decided to dress up as Ken as he is supposed to be the perfect, charming and handsome boyfriend and Suhana was supposed to dress up as Barbie as she is the perfect, popular and pretty girl on the outside. But none of this is true and it symbolises how their ‘perfect’ relationship is only a facade.
Inspiration for Barbie and Ken outfit-



Inspiration for Wendy and Tinkerbell outfit-


source of images:
https://in.pinterest.com/pin/5629568263208052/
https://in.pinterest.com/pin/473370610818077685/
We told Sandesh (Varun) to wear a blue suit that he had to look like Ken. Naysa (Naisha) had to wear a blue dress with white stockings that she had to look like Wendy. But for Sakshi we could not find a green dress that suited her to look like Tinkerbell. So to solve this problem Jiya and I decided to make her wear pink dress and pink fairy wings with a white halo hairband on her head to make her look like her own version of Tinkerbell. Suhana’s character always wears pink as it is the colour that symbolises her character. It show cases her perfect and pretty personality from outside when in reality she is the opposite. This way we break the conventions by assigning pink- a colour that is usually used when the person is delicate or sweet. However on the final day before shooting we realised that the wings looked to childish on Sakshi so we did not use them and only used the white halo hairband.
Image of the final Halloween costume for Varun-

Image of the final Halloween costume for Naisha-

Sakshi trying on the wings-

Image of the final Halloween costume for Suhana-

For Isha’s Halloween costume we decided to go with Maleficent. Maleficent as a character looks brave, bold and scary from the outside but she is actually a gentle, vulnerable and caring person. Isha is the same. Her outward appearance is more bold, brave and confident whereas she is actually a very sensitive and caring person but she does not show it to others. I wanted to show that what people think of her and what she truly is are different.
Inspiration for Maleficent costumes-


source of images:
https://www.desertcart.in/products/103639864-disguise-womens-maleficent-deluxe-adult-costume
https://www.partycity.com/adult-maleficent-costume---maleficent-P591016.html
We made Ichcha wear a black long dress with high heeled black boots to show that she was Maleficent. We could not find horns for the head so instead we used a witch hat.
Final Halloween costume for Isha-

For Sushant we originally planned to dress him up as the devil as he is one from the inside. His character id horrible as he sexually assaults a young girl at a party. However, from the outside he looks studious, shy and quiet. We ended up not having a specific costume for him as I wanted to show that his character did not care about these useless things.
Inspiration for Devil costumes-

source of image:
https://www.smiffys.com/collections/mens-devil-costumes
We made Jaden (Sushant) wear a black shirt with black pants for the Halloween party scene. The black colour represents his true nature.
Image of final Halloween costume for Sushant-

0 notes
Text
How to Encrypt Emails in Outlook

A study of IT leaders across the US and UK revealed that 95% of leaders believe data is most at risk when using emails. Additionally, 83% of organizations have experienced email data breaches, out of which human error accounted for 24%.
Another report says that nearly two-thirds of organizations that fell victim to a data breach hadn’t encrypted their data. With email continuing to be the dominant form of business communication, the case for email encryption can’t be stronger!
Most businesses use Microsoft Outlook to share emails often containing sensitive information like personally identifiable information (PII), credit information, meeting agendas, budget documents, IT tickets, client information, etc. With so much confidential information being exchanged, it’s critical to secure emails in Outlook, considering rising cyber threats to businesses.
Furthermore, stringent data privacy regulations like HIPAA and GDPR, among others, regulate how PII should be treated. Incorrect handling of client data can cause companies to incur fines of up to €20 million!
As Microsoft Outlook continues to be one of the most widely used email clients, let’s explore how you can encrypt your emails in Outlook.
How to Send Encrypted Emails in Outlook
There are two primary encryption Office 365 Message Encryption options to secure and send encrypted emails in Outlook.
Option 1: Office 365 Message Encryption
You can use this option only if you have Office 365 email account or 365 subscriptions. (The encryption option is not available in Outlook 2013 and 2016 versions, or Microsoft Office one-time license purchases.) Plus, you can send an encrypted email to any email client – on Outlook servers or other email networks, such as Gmail.
Office 365 Message Encryption is a four-step process:
Compose a new email like you normally do.
Click on “Options” in the message bar and select “Encrypt” from the dropdown.
Apply the relevant settings.
Send encrypted message.
Your recipients will receive an HTML message, which they can download and open in a web browser or mobile app. However, there are no restrictions on attachments when it comes to protection – meaning, the recipient can choose to download them on their local machines, print, or forward them to others.
Option 2: Certificate-Based Encryption or S/MIME
This encryption technique is a bit complex than the Office 365 Message Encryption and involves exchange of public and private security keys to encrypt and decrypt emails. You need to purchase a security certificate from a certified provider and add it to your Outlook by following the guided instructions. Here’s how you can install the certificates:
Click the File option in the top left of your Outlook window and select Options.
Click Trust Center in the new window and choose “Email Security” from the settings.
Click on Import/Export located under “Digital IDs”.
Once you finish all these steps, you can share the signed certificate with your recipient. Your recipients also must install the certificate and send you an email. When both of you exchange emails, you receive both public keys and private keys from each other that can be used to encrypt and decrypt emails.
How to Open Encrypted Emails in Outlook
Your email recipients will see a lock icon next to your email message, indicating the encryption. They will be asked to verify themselves. Once they do that, they can read the message like a normal email. However, there are a couple of limitations.
Limitations of Outlook Encryption Methods
Outlook offers simple methods to encrypt your emails but there are a few limitations:
The maximum message size you can send using Office 365 Message Encryption, including attachments, is 20 MB. This causes a serious inconvenience to businesses as they would either have to break file attachments to reduce the size to comply with the size limits (if the attachment size is over 20 MB), or look for easy file transfer options like cloud storage services. While the former method is time-consuming and practically infeasible, the latter option is fraught with security challenges.
There are some email usage restrictions with Office 365 Message Encryption mode, meaning unless you buy additional Microsoft add-ons - Information Rights Management (IRM) or Azure Information Protection (AIP), your recipient can easily forward, print, or download the attachments. This poses a serious risk to your confidential information, unless you are willing to shell out extra bucks, which again might not be a foolproof solution either.
When it comes to S/MIME, both sender and recipient need to install public certificates and buy them online from certified providers, making this process a bit expensive and hassling.
With S/MIME technique, if anyone gets hold of the private keys, then your data is at risk. Any tampering with public keys also messes up things. Plus, a recipient can read the email only on the device, which has the matching certificate. This makes the whole process really inconvenient for field professionals like sales.
There is a simple, yet effective way to get past these limitations by opting for an email solution that not only gives you superior encryption capabilities but also tops it up with additional features to make it even more user-friendly. RMail, an email security solution from RPost, is just what the doctor ordered!
RMail for Outlook
This is probably the easiest and the most powerful way to encrypt your emails in Outlook. Your recipients don’t need to install or set up anything on their device, sign up for an account, or purchase anything from any service provider.
And you can send encrypted messages to pretty much any email service like Hotmail or Gmail. All you need to do is install our RMail for Outlook app in Microsoft Outlook, restart your Outlook application, and start composing your email. As simple as that!
The encryption experience is as simple for your recipients as it is for you.
For more information: https://rmail.com/learn/how-to-encrypt-emails-in-outlook
0 notes
Link
In this page all uses and syntax of class in HTML is descirbed. The class attribute is used to classifies elements into conceptual groups; Unlike the id attribute, multiple elements may share a class name.(about the id attribute, A complete detail is given in next page) By making elements part of the same class, you can apply styles to all of the labeled elements at once with a single style rule or manipulate them all with a script. In this first example, I’ve added class attributes to classify each div as a “listing” and to classified paragraphs as “descriptions.” Keep in mind that the class attribute can be used on any HTML element. But the class name is case sensitive! So use it carefully.
1 note
·
View note
Text
java script from a beginners point of view-part 1
I started learning java script this month but it was difficult for me to learn ,may be its easy for some of you but i struggled a lot hence i decided why not to explain java script from my point of view.

more then a tutorial this is simply my way of telling myself how i learned/a account of my first hand experience.
the prerequisite for this is definitely html and css (basic knowledge).
1.What is java script?
✨java script is a high level language.
✨ languages are of 2 type
high level(machine independent) and
low level(machine dependent)
✨ interpreted programming language
✨ object oriented capabilities
✨ HTML : gives content
✨ CSS : gives design
✨ JAVA SCRIPT : gives functionality/interactivity
✨ it is a client side scripting language
✨ java script is case sensitive
✨ there are two ways to use java script >>internal and external
2.Lets start.....
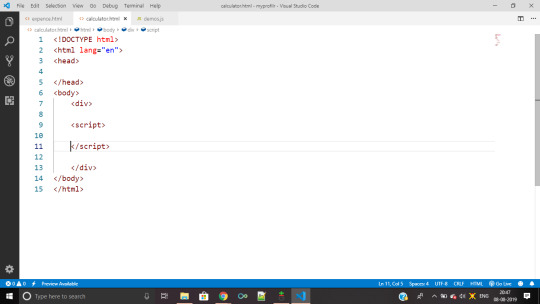
for writing java script you have to write them inside script tag
<script type="text/javascript">
</script>
this is a way to create a internal way
3. My first command
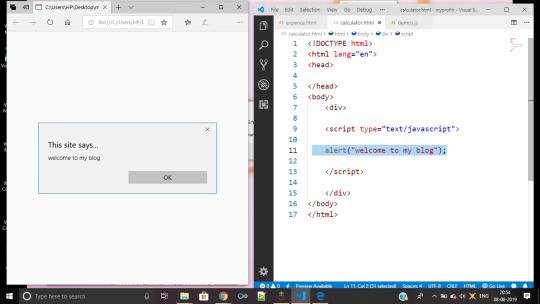
just type the highlighted command on the above image and booom😍😍
your first java command just ran
Window alert() Method
The alert() method displays an alert box with a specified message and an OK button.
Syntax
alert(message);
this message is a String
4. what is window ??? what is write???? what is this????😲
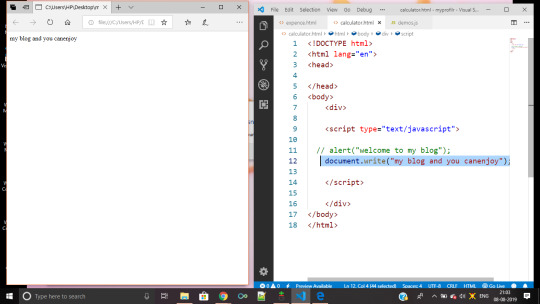
here my message “my blog and you can enjoy” got printed on my web page page.
via document.write();
so basically document is a object
document object represents your web page.
If you want to access any element in an HTML page, you always start with accessing the document object.
how document object is used??
HTML DOM document object is the owner of all other objects in your web page.
in short its don of your web-page😎
some examples of how you can use the document object to access and manipulate HTML.
(dont worry for now you can ignore all the things written after documen object)
Finding HTML Elements
document.getElementById(id) ;
document.getElementsByTagName(name) ;
document.getElementsByClassName(name) ;
Adding and Deleting Elements
document.createElement(element)
document.removeChild(element)
document.write(text) <this was the example >
there are more uses to it which you can search<<thats a link
4.1 .JavaScript can "display" data in different ways:
these are the ways and for now i am going to use and explain document .write()
Writing into the HTML output using document.write().
Writing into an alert box, using window.alert().
Writing into the browser console, using console.log().
Writing into an HTML element, using innerHTML .
Using document.write() after an HTML document is loaded, will delete all existing HTML
1 note
·
View note
Text
Lecture 6
I just remembered that professionalism was part of the portfolio marking criteria so I’ll try to keep it PG in these posts. Meaning that I’m allowed to drop one and only one F-bomb somewhere.
Avalanching
Recall that the Merkle-Damgard hash construction looked like this:
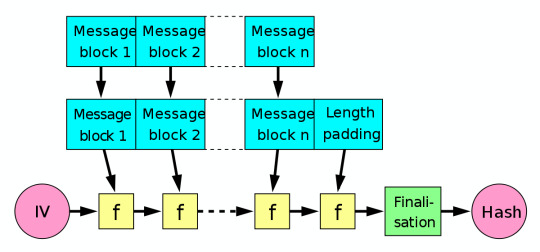
The reason the hash function is segmented into the various f’s you see above, is to allow avalanching to occur; the property that causes good cryptographic hashes to be drastically different from one another, even if the edit distance of the inputs if minimal.
This allows for the semantic meaning of relatively similar inputs to be obfuscated, as one would otherwise be able to perhaps glean information pertaining to the information that had been hashed, through observation of the structure of the hash string and comparison with other similar hashes e.g. if hashing 12345 and 12346 produced hashes of 0xaa0geb212r3r3142q and 0xaa0geb212r3r3131w, then an attacker could probably guess the structure of the input at the very least and perhaps interpolate the inputs by generating other hashes.
Passwords Part II
From the exam, we might have found that the # of bits of security that we get from a random password using the Elephant Apple Golfing principle (or some shit I don’t remember the stupid name) isn’t as many as we would like. It’s naive to say that a password has as many bits as it is long, unless those bits are truly random and the full complement of ASCII characters are actually utilised, such as \0.
Indeed most passwords aren’t that many bits, given that they’re based largely on quotes, names, birthdays etc. etc. and it’s only a matter of time before increases in computing power renders them obsolete.
So yeah, the answer to that question pertaining to the Homophobic Dog Shagger principle is 40-49 bits i.e. the smallest choice. Congratulations if you got it right.
This kind of segues into why WEP keys are terrible:
They’re consisted of a shared 40 bit key, that everyone connected to a network knows, and a 24 bit initialisation vector that was randomly generated locally by the receiver that were combined to form a ‘64′ bit key and this key was used to encrypt every frame.
The obvious issue with this is that it’s trivial to brute force 24 bits, and it’s probably trivial to brute force 40 bits, and it wasn’t too difficult combining all the brute forced combinations to obtain the purported 64 bit key.
Mixing Control and Data - Smashing the Stack for Fun and Profit
http://phrack.org/issues/49/14.html
Mixing control and data is bad, don’t do it.
C lets us do it and although most modern compilers such as gcc and clang have several countermeasures for stack smashing, it remains a useful case study and a common issue in modern software.
Buffer overflows can occur when someone writes shit code and rather than fixing declaring a fixed array size in their loop iteration, they end the array loop once the program hits NULL, allowing a third-party to use a function such as strcpy() - that doesn’t check buffer size - to stuff more in the buffer than has been allocated to memory. There are other methods too but this is the most intuitive to understand.
The Stack and Return Addresses:
Computers switch context lots of times a second to allow them to deal with interrupts from a multitude of sources. When something interrupts them, such as a keyboard entry perhaps, the computer will execute the interrupt and then return to whatever task it was completing before.
How it knows where to return in the code, is by adding the address of that particular point where it stopped - the return address - as well as the miscellaneous parameters that the code needed to execute, onto a LIFO structure known as the stack. These miscellaneous parameters, such as our array, are stored before the pointer and as such, by overflowing the array, we are able to overwrite whatever return address was in stored at the pointer(’s address) which paves the way for all sorts of shenanigans.
Most common of these shenanigans:
- Actually writing code into an overflowed buffer and addressing the pointer to the location of this code
- Getting a shell open
Overflowing the array is most commonly done with a NOP Sled, which is simply consisted of a bunch of NOPs (no operation commands) that serve to pad the buffer up to the memory/stack address containing the return address and your payload which can be either a memory address pointing to your code or pointing to whatever would open up a shell.
This requires us to know the # of NOPs to place into our sled, which can be done in a variety of methods that the course doesn’t require us to know.
*will add more to this section as I read more on it*
NIST and the History of Ciphers
Even after WWII, ciphers were not particularly powerful and for a while there was a ‘crypto black hole’ where no new cryptographic methods were being devised and nobody was aware of any principles one should follow.
This changed with the advent of computers and eventually, groups concerned about security put out a standard known as NIST.
Except noone knew what to put into the standard and so a competition was held which noone except IBM entered into and they won by default.
And so IBM’s DES was adopted and had at the time, only 56 bits.
Then the NSA comes along, looks at DES, breaks it in two seconds using their differential cryptographic methods and says ‘yeah it’s okay keep using it XD’.
Except everyone was like HANG ON, and eventually a successor AES was built. AES was predicated, much like DES, on performing many permutations, transposing and other obfuscating measures, which created an encryption method that was difficult to break feasibly, but had significantly more bits than AES.
XSS (Cross Site Scripting) or why Javascript is awful
Cross Site Scripting
Involved placing Javascript on a webpage, for example in a poorly secured forum, where you know unassuming people would visit. The Javascript will execute upon that page opening and whatever was in the JS will proceed to wreak havoc.
Common attacks include stealing your cookies to impersonate you.
SQL & Command Injections
Webpages that require you to enter your username and password into fields will typically take the characters you entered as your username and password, stick them in an SQL query and execute said query to check your username and password against a preexisting username and password database.
Instead of entering our usernames and passwords, we can enter actual SQL code which will actually execute, due to the nature of PHP converting your input into code. This wouldn’t work in any other language. For example:
Here’s an example query taken off https://www.acunetix.com/websitesecurity/sql-injection/
# Define POST variables uname = request.POST['username'] passwd = request.POST['password'] # SQL query vulnerable to SQLi sql = “SELECT id FROM users WHERE username=’” + uname + “’ AND password=’” + passwd + “’” # Execute the SQL statement database.execute(sql)
Now, we could easily input as the password:
password' OR 1=1
which would cause:
SELECT id FROM users WHERE username='username' AND password='password' OR 1=1'
SELECT id FROM users WHERE username=‘username’ AND password=‘password OR 1=1′
to execute, which would return the first ID of the first user in the database table due to that 1=1 is always true and the query is made complete by the ‘ appended to the word password.
We could easily modify this query to print out the entire table if we wanted to write more code.
Command injections rely on the same concept of writing code into input boxes, but instead we write shell code and grep our way to sensitive data.
Cryptocurrency
Wasn’t really paying attention to this part, I’ll fill it in later
Block Modes
How we combine individually ciphered blocks of a ciphertext, like we did in the Merkle-Damgard hash (recall that the input was split into blocks), to get a whole ciphertext:
- Can concatenate them like in WEP
- Or more commonly, we can use CBC which is really convoluted: here’s some reading if you’re interested, but basically each unciphered block is XOR’d with the previous block.
https://en.wikipedia.org/wiki/Block_cipher_mode_of_operation#Cipher_Block_Chaining_(CBC)
Authentication - WIP
How? What decisions?
Humans are bad at looking at faces
No point in confidentiality, if there is no authentication
Defence in depth
Something you know
Have: let's send someone an SMS when they type their PW WOW.
2FA worked well initially, however, SMS is easy to intercept.
Have single point of weakness, in your phone
Are:
Requires secrets to be confidential, keyloggers, shoulder surfing etc.
Naïve but easy to implement
1 note
·
View note
Text
Learn Google Analytics

Explore Google Analytics: Google analytics is the tool provided by google to Analyze your website as well as user/customer behavior in depth. This will help you in working with SEO ranking your website on the first page of the Search Engine Result Page (SERP). I'll guide you the step by step procedure to start with Google Analytics .
So, let's start with creating an account
1) Sign up for a Google Account (Skip if you already have one)
If you don’t have a Google Account you need to get one now to have access to all the free Google tools that are out there.
2) Get your unique tracking code.
You will the get the unique tracking code you have to upload that link into head part of your website that will track your website report.
a. If it’s your first time logging into Google Analytics read below. If not, skip to Step 2b
If it’s your first time using Google Analytics then before you get your nifty tracking script you will need to answer a couple of questions and accept Google’s terms of service.
The first page will ask for your Website URL as seen below:
Enter in your Website’s URL in the “www.yourdomain.com” format (*NOTE* If you have a secure site, https, make sure to update it accordingly). For Account Name enter in whatever you want to call your website or project. And finally select the correct Time Zone that you are in. When you’re done, click continue.
You will be then be asked to enter in your contact information and accept Google Analytics’s user agreement.
After you agree to Google’s terms of service you finally see your nifty tracking code for the specific website URL you previously entered.
b. If it’s your NOT your first time logging into Google Analytics.
If it’s not your first time logging into Google Analytics simply click on the “Add Website Profile” link at the bottom left of your overview report.
On the next page, keep the selection on “Add a Profile for a new domain) and enter in the domain you want to start tracking (*NOTE* If you have a secure site, https, make sure to update it accordingly). and choose your time zone then click finish.
Google Analytics will then create a custom tracking code snippet for your site.
Copy your code snippet and click finish. Read step 3 on how to install it on your website.
3) Installing Your Tracking Code Snippet
Now that you have your code snippet we will need to install it on your webpage.
In step 2) I instructed you to copy over the code snippet but if you forgot or just didn’t feel like copying it, follow these steps to get your tracking code.
a) Go to the Overview page and click on “edit” in the last column of your website profile report:
b) Click on the check status link in the top right corner:
c) Get your code snippet:
Now that you have your code snippet (again), let’s install it!
All you need to do now is place your code snippet in every single one of your pages in your website. The most common mistake is to place the tracking in only your main index.html/php page.
Home Page: “http://www.xyz.com/index.html”
Our Services Page: “http://www.xyz.com/service.html”
About Us Page: “http://www.xyz.com/about.html”
Contact Us Page: “http://www.xyz.com/contact.html”
Thank You Page: “http://www.xyz.com/thankscont.html”
So we need to install our tracking script. Open your favorite html editor or just open your html/php with notepad and add your tracking script right BEFORE the </body> tag.
The </body> tag is usually at the end of your html code. Do a simple search for “</body>” it in your html editor or notepad to find it. Then simply place your code before the </body> tag as shown below:
Now repeat this process for all of your webpages. In our instance I placed the code in index.html, service.html, about.html, contact.html, and thankscont.html.
After you are done Google Analytics needs some time to go crawl through your webpage to confirm that the scripts are installed. All you need to do now is wait about 12-24 hours for Google Analytics to Update.
Here is what your site’s status will look like when your site isn’t verified:
And here is what your site’s status will look like once it’s been crawled through and confirmed to be installed correctly:
Once your site is confirmed by Google Analytics your site is now being properly tracked by Google Analytics. If after 48 hours your site still has not been confirmed. Please read through Step 3 again and make sure that your code is correctly placed.
4) Adding Goals to Track Conversion.
Now that you have the basic tracking installed in your page you now need to set up Google Analytics so you can start tracking conversions.
With goals you can figure out how many people did a specific action. IE. Bought an item, signed up for a newsletter, read a specific page, etc. For now (as of 03.20.08) Google has a max of 4 goals assigned to each website profile. You can have more than 4 but that is outside of the scope of this beginner guide.
To properly use goals you will need a link to your “goal” page. A “goal” page can be any page where you want your user to go to. It can be a thank you page after a user signs up for your newsletter or it can be the receipt page after someone orders a product from your site.
To get started with setting up a goal, first go into your Analytics home page and click on “edit”.
In the profile settings page two boxes down you should see the “Conversion Goals and Funnel” box. Click edit on an empty Goal. If you are new, just click edit on the G1 row:
You should now see the Goal Settings Page. Let’s go over the “Enter Goal Information” section first:
Active Goal: This activates/deactives your goals. So to start turn this goal on by choosing the “On” button.
Match Type: There are 3 types of match types.
Head Match: Use this type if your webpage uses dynamic URLs. For example, let’s say your goal page is an order receipt page and the links look something like this: “www.example.com/checkout.cgi?page=1&id=9982251615” where the &id=XXXXX changes dyamically.
Exact Match: Use this type if your thank you page is a static page such as: “www.domain.com/1/thanks.html”.
Regular Expression Match: This option uses regular expressions to match your URLs. For many eCommerce website the “thank you” or “receipt” page is a dynamic URL with different pages with OrderID or CustomerID variables and you will need to use this match to track the URL instead of a static domain page. Using regular expressions with wildcards are out of the scope for this beginner tutorial. We will write a post specifically tackling the Regular Expresion Match soon.
So choose the correct match depending on your “goal page”
Goal URL: Enter the directory and file of your goal page. DO NOT input your entire http:// link. Simply just write the directory and file name from your root perspective. IE. “http://www.mysite.com/thankyou.html” enter “/thankyou.html” or “http://www.mysite.com/newpage/thankyou.html” enter “/newpage/thankyou.html”.
Goal Name: This is for your use. Name the goal to whatever you want.
Case Sensitive: Check this if URLs entered above must exactly match the capitalization of visited URLs.
Goal Value: Input what each conversion is worth. Let’s say each newsletter email is worth $0.70 then input that into the goal value. If there is no static monetary value then you can just leave it as zero.
So here is how we filled this out in our example:
The next section is the “Define Funnel”. A funnel is a series of pages that leads up to the goal. If you have a eCommerce site it may consist of 3-5 steps “checkout –> information input –> CC Page –> Review –> Submit” etc. You can define these pages in the funnel section to know exactly how your traffic is reaching your goal page and in which steps they are leaving.
Seeing the funnel is extremely helpful is realizing how your users traverse through your pages to do the action item. Make sure to always use this even though it may be only a 1 step process as the funnel system allows you to easily see your true conversions.
In our example, we want to know how many people sign up from our contact.html page. So our Funnel is:
contact.html –[If user signs up]–> thankscont.html.
So we define the funnel like this:
Like the goal URL in the “Enter Goal Information” section make sure not to include the entire link, just the directory and file.
Make sure to check the “required steps” if you want to track your real conversions. When this is checked goals are ONLY counted when the user goals to our contact.html first. This is important as I’m sure many of our users will go directly to our thank you page in this step by step guide and we don’t want to count those as conversions.
Once that’s done, simply click the “Save Changes” button. Congratulations! You’re now correctly tracking your conversions!

5) Understanding Google Analytics Report.
Now that your site is correctly being tracked, it’s time to see all the cool reports that Google Analytics can show you!
(Pretty, isn’t it?)
Everything is pretty self explanatory and intuitive so I won’t go through every single reporting link. The one item that I do want to talk about is the funnel report in the Goals section as it is the most important part in your conversion tracking.
First click on the goals tab then the Funnel Visualization link:
Once there you will see this:
The above example is a pro bono optimization we’re doing for a charity. We are specifically optimizing their membership page. The funnel is simply, “Membership Page” –> “Membership Buy Thank You Page”
On this day you’ll see that they had 625 visitors go to the membership page and 47 people who bought a membership to this charity organization for a conversion rate of 7.52% which is our true conversion rate.
This is the most important page to understand what is going on with your traffic and find out how you can best monetize it as well as find “conversion leaks” if you have multiple pages in your funnel.
Now what if we didn’t use the optional funnel and wanted to know our conversions? This is what we would have seen from this client:
We would see a .18% conversion for these days…
Why? Because Google Analytics determines the conversion rate as [Goal Visits / Total Visits to the Website].
This charity organization gets TONS of traffic from all over the place to different pages on their site. Most people don’t even view the membership page. So the conversion rate above is incorrect in letting you know how your specific page is converting and you should not rely on this. The only way this report would be correct is if you have just a simple landing page and buy page.
1 note
·
View note
Link
At least 10 politically active students at King’s College London (KCL) were barred from accessing the university campus on March 19, as part of security arrangements for a visit by the queen and Duchess of Cambridge. The activists’ names were also passed along by the university administration to London’s Metropolitan Police.
This deliberate intimidation of left-wing students is a grievous attack on democratic rights and the freedom of association. There was never even an indication that the students had any intention of protesting against the queen’s visit, which they would have been entitled to do in any case. The university and the police have given themselves the power to exclude individuals from campus solely based on their political beliefs.
All the students in question are involved with KCL’s Action for Palestine and Justice4Cleaners protest groups. Action for Palestine is a registered society at the university and campaigns “to end our own institution’s complicity in the illegal occupation of Palestine, serve as a platform for students to learn about social justice, and to educate the wider community about the situation in Palestine.”
Justice4Cleaners has carried out a years-long campaign to end the university’s use of heavily exploited, outsourced labour for their cleaning staff.
The first the 10 knew of the ban was when their university ID cards failed to grant them entry to classes, the library, work shifts and exams. One barred student was told by a KCL staff member, “We were under instructions from the Metropolitan police to refuse access to Bush House due to the event that was taking place. That is all I can say to you.” Others were informed, “There are a number of protesters who have been visible at a number of protests over the last year, two years. You’re identifiable because you were on CCTV.”
This statement suggests the illegal use of video surveillance for political purposes.
Over 400 current and former students and professors have since signed an open letter protesting the university’s despicable actions. The letter explains, “This constitutes an alarming securitization of campus and an act of profiling of students based not on any evidence that they are guilty of wrongdoing, but rather a suspicion that they might potentially commit harmful acts at some point in the future. None of the students subject to this exclusion have any record of university misconduct. Such profiling of students is based on the political viewpoints and racial and national identities of students, and violates the commitment of KCL to providing a safe and inclusive academic community and campus for all…
“This spurious use of ‘security’ encourages a culture of fear, suspicion, mistrust, and functions as a blanket reason for all kinds of repressive measures.”
The signatories demand “an explanation of the process by which this decision was taken, an apology from the KCL administration to these students, and a commitment not to engage in such acts of unjustified profiling and exclusion again.”
KCL refuses to even acknowledge that specific students were targeted. A spokesman commented, “We had an event which demanded the highest level of security and we had to minimise movement through buildings for security reasons. At times some of our buildings were not accessible.”
The university administration laughably offered to carry out a “full and independent review” into how its own decisions were made.
These events must be placed in the context of an ongoing assault on progressive politics being carried out by the government, through the Office for Students (OfS) and Prevent scheme, and the right-wing media. They have sought to use accusations of left-wing “authoritarianism” and “extremism,” coupled with the attempt to brand anti-Zionism as a form of anti-Semitism, to outlaw socialist thought and to suppress popular protest against the reactionary figures who are ever more frequently invited onto university campuses. The barring of the KCL students is only the latest stage in this campaign.
Last November, an essay by academic Norman Geras on the “ethics of revolution”, listed as recommended reading in a course on “Justice and Injustice” at Reading University, was flagged as dangerous by the government’s counter-terrorism Prevent scheme. Students were required to submit a form explaining why they were accessing the Geras article, warned not to access it on personal devices, told to read it in a secure setting and not leave it somewhere it might be seen “inadvertently or otherwise, by those who are not prepared to view it.”
This was on the basis, as their lecturer explained, that “The University understands its responsibility to require it to control access to security-sensitive material, which includes but is not limited to material which might be thought to encourage the commission, preparation or instigation of acts of terrorism; material which would be useful in the commission of acts of terrorism; and material which glorifies acts of terrorism.”
Now students themselves are being labeled as security threats, reported directly to the police and denied access to their own university.
It is especially significant that the barred individuals were active protestors against the Israeli state’s vicious treatment of the Palestinians. A massive campaign of slander is being carried out by the British ruling elite to criminalise political opposition to Zionism and to brand Labour leader Jeremy Corbyn and the political left as anti-Semites. This found sharp expression on the campuses late last year, when now suspended Labour MP Chris Williamson had a public meeting at Sheffield University cancelled by Sheffield Labour Students. The decision was prompted by the Metropolitan Police’s announcement of an investigation into allegations of anti-Semitism in the Labour Party. Williamson had been a vocal critic of this Blairite-led witch hunt.
The WSWS wrote, “The ban is profoundly anti-democratic and has serious consequences for freedom of speech.” Meetings “can now be ‘indefinitely postponed’ on university campuses—and beyond—until Scotland Yard gives the go ahead!”
That warning has been confirmed. Students who protest in defence of the Palestinians are now targets for censorship and police controls. The pretext in this case was a visit by the queen, but there is nothing to stop the same argument being employed in the case of any member of government, army general or right-wing ideologue.
The Socialist Equality Party (SEP) and International Youth and Students for Social Equality (IYSSE) strongly support the fight against KCL’s anti-democratic actions.
The political policing of UK campuses is escalating rapidly. Universities are crucial centres of ruling class strategy and propaganda, and KCL itself is a prime example. The institution hosts a 2,000-student strong “War Studies” department, the front page of its Policy Institute’s website features a report titled “How Russian State Media Weaponises News” and 19 of its alumni currently sit in the House of Commons. With British imperialism facing an unprecedented crisis of rule, these functions of the universities become ever-more vital. At the same time, the ruling class feel seriously threatened by growing anti-capitalist sentiment among young people and its solution is a crackdown on left-wing ideas and action.
Not a single instance of political censorship on campus can be seriously fought without an understanding of these deeper causes. By coming to grips with these issues, students must recognise that their basic democratic rights can only be defended based on a socialist struggle against capitalism.
#SEP#wsws#left wing ban#anti-semitism#queen elizabeth#duchess of cambridge#guillotine bait#jeremy corbyn#king's college london#blairite scum
1 note
·
View note
Text
The Future of #Continuous #Renal #Replacement #Therapy (#CRRT) Market
Growing clinical advantage of CRRT over intermittent blood purification are factors likely to boost the growth of the market. Moreover, presence of well-established key players focusing on developing and commercializing technologically advanced and initiatives undertaken by government to increase the awareness about CRRT are likely to propel the market growth during the forecast period.
According to the International Society of Nephrology (INR), an estimated 13.3 million cases of AKI are registered annually worldwide. This is anticipated to boost the adoption of continuous renal replacement therapy at a rapid rate. With the rapid growth in the geriatric population globally, the prevalence of kidney-related diseases is expected to increase significantly.
As the population in emerging nations is price-sensitive, they prefer lower-priced products. Although the cost of CRRT in developing countries is high which makes these procedures are still unaffordable for a large portion of the population due to the low purchasing power.
For More Info, Download PDF Brochure @ https://www.marketsandmarkets.com/pdfdownloadNew.asp?id=246917088
Emerging markets such as China, India, Brazil, and Mexico are expected to offer significant growth opportunities for players in the CRRT market. According to an article published by the Journal of Clinical and Diagnostic Research (JCDR) 2018, in a prospective observational study conducted in 100 critically ill patients In India, AKI was observed in 17.3 cases/1,000 persons.
Additionally, regulatory policies in the Asia Pacific region are more adaptive and business friendly due to the less-stringent data requirements. This, along with the increasing competition in the mature markets (Europe, Japan, and Australia), will further encourage CRRT product manufacturers to focus on the emerging markets.
The high growth rate of the CVVHDF segment can be attributed to its flexibility as compared to other CRRT modalities. The CVVHDF modality also combines the benefits of convection and diffusion for the removal of solutes, which is another major factor supporting its growth.
The increasing demand for invisible braces among adults due to large adult population base with AKI, increase in the hospitalization among adult population, and the large availability of continuous renal replacement therapy (CRRT) market system and disposables for adults undergoing CRRT procedure.
Moreover, strong foothold of major key players in the region, rising approval of CRRT products for multiple application across many European countries, and initiatives by government to increase the awareness about the advancements in renal therapy.
Read Full Article @ https://www.prnewswire.com/news-releases/continuous-renal-replacement-therapy-crrt-market-worth-1-7-billion-by-2026--exclusive-report-by-marketsandmarkets-301317111.html
1 note
·
View note
Text
Price: [price_with_discount]
(as of [price_update_date] - Details)
[ad_1]
Are you fed up with storage warning on your Mobile Phone? Are you still worried about the inner storage of your new mobile phone which cannot be enough? - Gulloe is a creative USB 3.0 Flash Drive which has double connectors, can be transferred the documents for all series products of mobile phone.Plug and Play - Just plug in Gulloe USB flash drive to start moving photos and videos off your mobile phone.- Use the in-app camera to save photos and videos directly to Gulloe memory stick flash drive, so you can free up your phone's memory for other things. -Transfer files between your mobile phone and laptop.High Transfer Speed USB 3.0 - Read up to 80 MB/s, Write up to 30 MB/s Moblie phone port- Read up to 30 MB/s, Write up to 10 MB/sData EncryptionGulloe usb memory stick also includes encryption software to password protect files, so you can share content while keeping sensitive files secure.Media Formats SupportedMusic:M4A / AIFF / CAF / MP3 / WAVImage:GIF / JPG / PNG / JPEGVideo: AVI / FLV / M4V / MKV / MOV / MP4 / RMVBDocument: DOC / PPT / XLS / XLSX / PDF / HTML / TXDevice Support Support almost all Mobile Phone models including Windows 2000/7/8/8.1/10/Vista/XP/2000/ME, Linux and MacOs 10.3 and above.Please Note IF NECESSARY, PLEASE REMOVE PHONE CASE FIRST.Phone Devices: Need to download the free APP "Y-DISK" from APP Store.Android Devices: Only Android Smart Phone/Tablet with OTG Micro USB/Type-C connector can working with USB flash drive.
【High Speed and One Click Backup】 Experience up to 80 MB/s reading and 40 MB/s writing speed, and photos, videos, documents can be backup to the 64gb flash drive with one click. The iphone memory stick provides a simple and quick way to transfer photos and videos. Allows you to free up the memory on your mobile device without using a data cable or iCloud. With this iphone photo stick, you don’t have to worry about Phone storage anymore! Make file transfer easier.
【Thumb Drive Access Security】Use the iphone thumb drive to easily share data with family, friends and colleagues, making entertainment and work more interesting. The Password & Touch ID can encrypt file information in APP to protect your private files, you can choose to encrypt the entire usb flash drive, or you can choose to encrypt a specific file. All encrypted files stored in this iphone flash drive are invisible on the computer. No worry that others steal your files.
【Watch Video Directly and Share to Social Media】Plug and play, you can watch the movie/play music directly on the iphone flash drive 64gb. When you take beautiful photos on the go, you can store the photos or videos directly on the Phone flash drive without occupying your device memory. Also you can share document/photo to the social media directly from a iphone storage device. (Facebook, Twitter, etc.)
【Photo Stick Storage】USB storage drive is made of frosted aluminum metal. With slidable design. Flash drive has 64gb of memory, you can record your life as you wish to the usb stick. USB storage has dedicated email customer support. You can contact us after 18:00 PDT and we will answer your questions as soon as possible.
[ad_2]
0 notes
Text
Eliminate Your Fear And Pick Up Web Design Today.
The basics of HTML
HTML is a standard markup language for web documents. Other technology, such as JavaScript, can support HyperText Markup language. It is used to create web-based documents. HTML is easy to modify and read using Cascading Style Sheets and other scripting languages. These are HTML-based websites. Both websites are based upon XHTML. For more information, click the links below. Learn more about HTML and Cascading Style Sheets.
HTML is a programming language which describes the content structure. A web browser can view the resultant document. The HTML tags allow you to navigate the Internet in many ways. The b tags are used to highlight and bold text. This language was developed using ISO/IEC JTC1/SC34, or "Document descriptions and processing languages". HTML 1.0 is the simplest syntax.
HTML is a powerful tool for creating amazing creations. It is the most widely used markup language for websites and is always changing. It is easy to learn and has a high level of functionality. The World Wide Web Consortium (W3C) is responsible for HTML's development and maintenance. HTML is an easy language to learn, but it's becoming more powerful. It is important to master the language. This article will help you to master HTML basics.
HTML was an original format used for documents. It was popular in the 1990s, but it was not standardized until 2014. It has changed significantly over the years. It is used in a variety of academic documents. It's used to create interactive programs and websites. It is compatible with many operating systems, including Apple OS. HTML allows you to create websites.
HTML is the standard document format used by the web. The Internet Engineering Task Force (IETF), which defines HTML's syntax, is responsible for creating web pages. Most HTML pages have at least one HTML file. Multiple HTML files are not unusual for websites. However, this doesn't necessarily mean that the code is useless. HTML is the best way to create interactive web pages or applications.
HTML can be used to create any web-based content. HTML allows you insert hyperlinks or multimedia. In addition, HTML is platform-independent. HTML works with all devices. Aside from being platform-independent, HTML is case-sensitive. It is best to avoid capital letters when writing HTML for the Internet. You should not use closing tags to describe paragraph elements.
HTML syntax allows you use different attributes for different types content. To identify a header, class or link, you can use the id keyword. Another example of HTML is a table. The table tag is used to define a table in HTML. It can be used to specify columns and rows for the table. It also contains an img to allow images to be added. You can also insert tables. It's easy to create a website if you are familiar with HTML basics.
HTML can be used to create many types of content. HTML can be used to create forms. You can use it to request information, or perform transactions via remote services. It can be either a text-based file, or a webpage. You need to know how to write HTML code if you want to create a web site. An HTML page's outline should be simple to understand and read. A website page can also be illustrated.
HTML can be used for creating websites. HTML allows you to create hyperlinks within your HTML document by using the code. These links will link you to different parts of your text. A page can have two tables. You can then list different types of information. A table with two columns can be referred to as a table with more than one column. You can also add graphs or charts that include the information in text.
0 notes
Text
Seven Mind Numbing Facts About Web Design.
The Basics Of HTML
HTML is a markup language commonly used for web documents. JavaScript and other technologies can also support HyperTextMarkup language. It is a common language that can be used to create web-based documents. HTML is easy and straightforward to modify. It can also be used with CascadingStyle sheets and other scripting langauges. These websites use HTML. Both websites use XHTML. Find out more by clicking the links below. You can also read more about HTML, Cascading Style sheets, and other topics.
HTML describes the structure and function of content. The web browser will view the document. The HTML tags are used for marking up text and allowing it to be navigated in many different ways on the Internet. The b tag or tags can be used to highlight text or bold text. This language is derived ISO/IEC JTC1/SC34. It stands for "Document Description and Processing Languages". HTML 1.0 refers to the most basic syntax.
HTML can be used to create stunning creations. It is one of the most commonly used markup languages on websites. It is very easy to master and has a great deal of functionality. The World Wide Web Consortium is responsible for HTML development and maintenance. HTML is easy to learn, but its power and importance is growing. It is vital to understand the language. This article will show you how to master HTML basics.
HTML was initially a well-known format for documents. It was used widely in the 1990s. However, it wasn't standardized until 2014. It has undergone significant improvements since then. It isn't limited to academic documents. It's being used today for creating websites and interactive programs. It can be used with many platforms and operating systems, including Apple OS. HTML is essential software for creating websites.
HTML is a standard document format and has become the official language on the web. Its syntax has been defined by the Internet Engineering Task Force, which is the language used for creating web pages. Most HTML pages only contain one HTML file. Multiple HTML files are common for websites. It doesn't mean the code isn’t useful. HTML is the best technique to create interactive web sites and applications.
HTML can be used for any web content. HTML allows you to add hyperlinks and multimedia. In addition, HTML is platform-independent. HTML is compatible across all devices. Aside from being platform-independent, HTML is case-sensitive. It is recommended that you avoid using capital letters in HTML. Closed tags should be avoided for paragraph elements.
HTML syntax allows you the flexibility to use different attributes for different types and types of content. You can use id to identify a heading or class and signify a hyperlink. HTML also includes tables. The table tag in HTML defines a table. It is used for defining columns and rows. It also contains an img that allows you to insert images. It is also possible to insert tables. You can also insert tables if you know HTML basics.
HTML allows you to create many different kinds of content. HTML is used to create forms. You can use it for requests or transactions through remote services. It could be either a text file or a website. It is important to understand how to use HTML to create web pages. The HTML page outline should be clear and easy to read. An image can be used as an alternative for a webpage.
HTML can also be used to build websites. HTML can be used for creating hyperlinks. These links will allow you to link to different parts in your text. It is possible to create a page with two tables. The page can be divided into two tables. When a table has more columns than one, you can refer to it as a two-column table. You can also add graphs and charts that contain the information in text.
0 notes