#network security firewall
Text
IT Skill Classes is going to start Fortinet Firewall NSE4 Training with the best Trainers
About Fortinet Firewall NSE 4

In Fortinet, there is a device called FortiGate. Fortigate transmits one of the top secure SD-WAN tools in the market at no extra cost. It ensures the highest price performance in the industry, enabling superior security and inspection services for advanced traffic management. In simple language, Fortigate is a next-generation firewall that ensures your network security from any cyber threat. There are a total of 8 NSE Fortinet Firewall Training Certifications to improve your skill in cyber security.
NSE 1 to 3: Basic of Next-Generation Firewall
NSE 4: Network Security Professional (Deployment & maintenance of Next-Generation firewall)
NSE 5: Network Security Analyst(designation recognizes your ability to implement network security management and analytics using Fortinet security devices using FortiManager & fortianalyser
NSE 6: Network Security Specialist (Cloud Security)
NSE 7: Network Security Architect
NSE 8: Network Security Expert
FortiGate is the only firewall instrument to fundamentally integrate zero-trust network access (ZTNA) policy enforcement points. Because it can be deployed anywhere in the network (on-premises and in the cloud), FortiGate can establish universal application access enforcement protected by encrypted tunnels for a consistent user experience. FortiOS can automatically trigger user verification and device risk assessment for each application session, providing the foundation for building a Zero Trust Edge strategy that enables a hybrid workforce to connect to applications while maintaining consistent security wherever users and applications reside.
FortiGate firewall in the Networking Industry
A FortiGate firewall is playing an essential role in the networking security industry. It is one of the top-used vendors of the core networks, which has cost-effective instruments and is very secure. Network security engineers can improve their FortiGate skills, and develop their security foundation. For FortiGate firewall training, the best way to provide complete network security is to deploy a proper firewall at the network domain. Through firewall security, we can gain protection against the most common computer and network threats and hackers. As a security instrument, the FortiGate firewall provides some attractive performance against modern malicious attacks. With the state of the art security measures, businesses can achieve an end to end protection with advanced capabilities that share the intelligence across the entire network. By sharing the information, a great deal of protection can be provided to all layers of the network. As an IT institute, we are the best at delivering effective IT skill classes for security measures.
Career In Fortinet Firewall
The Fortinet firewall offers end-to-end security solutions across your business network. Because of its high-end architecture and functionalities, it is known as the next-generation firewall in the industry. The range of Fortinet firewalls can be optimized for data center security solutions and varied-size business network security solutions. The Fortinet firewall series comprises a high-end firewall, mid-range firewall, and entry-level firewall. It has been an answer to today’s growing threat landscape. This next-generation firewall secures your business with an easy-to-manage platform solution, understands the targeted attacks early, and has deep visibility and excellent control of applications. It includes the series FortiGate 5000, FortiGate 3000, and FortiGate 1000 series. The high-level firewall is manufactured to protect the most demanding environments and comes with advanced hardware components powered by the FortiOS Operating system. Fortinet mid-range next-gen firewall series consists of FortiGate 900-600 series, FortiGate 500-300 series, and FortiGate 200-100 series. The Fortinet entry-level next-gen firewalls include of FortiGate 90-60 series and FortiGate 50-30 series. After getting FortiGate firewall training you will be able to analyze the security layers to protect the data and you can prevent any cyber threat, it will be a plus point to add to your resume to get an attractive salary.
Training in IT Skill Classes
At IT Skill Classes, We have professional trainers who are having more than 15 years of experience in the IT training field. Trainers of IT Skill Classes deliver the knowledge and expertise to prepare you to protect the way of life in the digital world. They are very adaptive in teaching, they not only train but also lots of practical’s are done by them so the student can easily grasp the knowledge and can do well in their career at FortiGate Firewall. In FortiGate Firewall training classes, you will improve your knowledge and skills in the core Network security concepts, i.e., Next-generation firewall, Cloud delivered security services, Secure service edge, Advanced threat prevention, Advanced URL filtering, Wildfire, DNS security, Data loss prevention, SD-WAN, IOT security, etc. So if you want to be an expert in the Security field then, you can enroll with us for great learning in an enjoyable environment. Simply register in our Learning Centre and you will be given access to our digital learning classes. These online classes cover foundational material and contain narrated slides, knowledge checks, and wherever applicable, demos will be available for you to access.
Source By: https://itskillclasses.com/it-skill-classes-is-going-to-start-fortinet-firewall-nse4-training-with-the-best-trainers/
Call/Whatsapp: +919310905289
Email: [email protected]
#Fortigate training#Fortinet#fortinet nse 4#fortinet nse 5#fortinet training#Network security firewall#next generation firewall#NSE 4
0 notes
Text

Best Cyber Security Services- NewGig Secure Solutions
#firewall#security#network security services#network security solutions#network security market#antivirus
2 notes
·
View notes
Video
youtube
#1 Free Network Security Tutorial | CheckPoint CCSA | EVE-NG In Google Cloud
#Free Network Security Tutorial#CheckPoint CCSA#CheckPoint#CheckPoint Firewall#P1#CheckPoint Firewall P1
2 notes
·
View notes
Text

#eeka#eekaconsultancyservices#consultancyservices#consultancy#services#bangalore#networking#firewall#security#happy#jobs#ecs#mothers day#motherslove#motherhood#mother
1 note
·
View note
Text
How to Protect Your Computer from Viruses and Malware

Imagine you’re gearing up for a regular day. You grab a coffee, sit at your computer, and boom—something’s wrong. It’s slower than usual, files aren’t where you left them, and pop-ups are everywhere. Sounds like a nightmare, right?
This scenario is a typical day in the life of a computer infected with viruses or malware. In this article, we’ll walk through simple steps to keep your computer clean and secure like you keep your home.
Click here for details...
#antivirus software#computer safety#computer security#cyber security tips#cybersecurity education#data backup tips#digital safety#firewall settings#how to secure your computer#internet security#malware removal#network safety#online safety#PC protection#personal cybersecurity#preventing cyber attacks#ransomware solutions#safe browsing practices#secure internet browsing#spyware defense#tech security#two-factor authentication#virus protection#VPN benefits
1 note
·
View note
Text
Fortinet 𝐅𝐨𝐫𝐭𝐢𝐆𝐚𝐭𝐞 𝟏𝟎𝟎𝐅, 𝐅𝐨𝐫𝐭𝐢𝐆𝐚𝐭𝐞 𝟖𝟎𝐅, 𝐚𝐧𝐝 𝐅𝐨𝐫𝐭𝐢𝐆𝐚𝐭𝐞 𝟔𝟎𝐅 Firewalls

🔒 Strengthen your #networksecurity with our latest lineup of #FortinetFirewalls! 💪 Whether you're safeguarding a small business or a large enterprise, we've got you covered with the 𝐅𝐨𝐫𝐭𝐢𝐆𝐚𝐭𝐞 𝟏𝟎𝟎𝐅, 𝐅𝐨𝐫𝐭𝐢𝐆𝐚𝐭𝐞 𝟖𝟎𝐅, 𝐚𝐧𝐝 𝐅𝐨𝐫𝐭𝐢𝐆𝐚𝐭𝐞 𝟔𝟎𝐅.
Here's why they're your best defense:
🛡️ 𝐀𝐝𝐯𝐚𝐧𝐜𝐞𝐝 #𝐓𝐡𝐫𝐞𝐚𝐭𝐏𝐫𝐨𝐭𝐞𝐜𝐭𝐢𝐨𝐧: Combat cyber threats effectively with integrated #security features like #antivirus, intrusion prevention, and web filtering.
🔐 𝐒𝐞𝐜𝐮𝐫𝐞 𝐂𝐨𝐧𝐧𝐞𝐜𝐭𝐢𝐯𝐢𝐭𝐲: Keep your network safe with robust #VPN capabilities, ensuring secure connections for remote workers and branch offices.
🚀 𝐇𝐢𝐠𝐡 𝐏𝐞𝐫𝐟𝐨𝐫𝐦𝐚𝐧𝐜𝐞: Experience blazing-fast performance and seamless scalability to meet the demands of your growing #networkinfrastructure.
📈 𝐒𝐢𝐦𝐩𝐥𝐢𝐟𝐢𝐞𝐝 𝐌𝐚𝐧𝐚𝐠𝐞𝐦𝐞𝐧𝐭: Manage your security policies effortlessly with our intuitive interface, making network administration a breeze.
Upgrade your defenses today and stay ahead of evolving #cyberthreats with Fortinet #FortiGatefirewalls!
𝐑𝐞𝐚𝐜𝐡 𝐮𝐬 𝐨𝐮𝐭 𝐚𝐭: +𝟗𝟕𝟏 𝟓𝟔 𝟓𝟓𝟏 𝟑𝟑𝟏𝟓
𝐂𝐡𝐞𝐜𝐤 𝐡𝐞𝐫𝐞 𝐭𝐨 𝐛𝐮𝐲: https://costtocost.ae/shop-for-the-best-quality-firewall-in-dubai/
#uae#dubai#business#it support#firewalls#Fortinet firewalls#fortinet fortigate firewalls#network security#cybersecurity#costtocost#IT networking#Electronics item#electronics and IT Supplier in uae#it retailer#it supplier#Fortigate 100f#Fortigate 80f#Fortigate 60f#best seller#sale#deals#offers#security#free delivery#dubai shopping#online shopping
0 notes
Text
#cyber security#united arab emirates#network solutions#techbee dubai#it solutions company in dubai#cyber threats#firewall security
1 note
·
View note
Text
Maximizing Network Performance: A Comprehensive Guide to GCP's Network Intelligence Center
Discover, monitor, and optimize your network with GCP's Network Intelligence Center! 🔍✨ #GoogleCloud #NetworkMonitoring #CloudOptimization
In today’s fast-paced digital world, a reliable and finely-tuned network infrastructure is absolutely vital for the triumph of any organization. As cloud environments grow more intricate, the task of overseeing and enhancing network performance can seem overwhelming. Yet fear not, for the Google Cloud Platform (GCP) presents an extraordinary solution: the Network Intelligence Center. Join us on…

View On WordPress
#azure#cloud#Cloud network management#Connectivity tests#Cybersecurity#Firewall insights#GCP Network Intelligence Center#google cloud platform#Internet intelligence#network monitoring#Network optimization#Network topology#Network troubleshooting#Networking#Packet mirroring#Performance dashboard#Reachability tests#Routing visibility#Security#VPN insights
1 note
·
View note
Text
Understanding the Firewall: Your First Line of Defense in Cybersecurity
Introduction -
It is critical to protect your network from cyber dangers in the connected digital world of today. Strong cybersecurity measures are becoming essential due to the constant risk of malware infections, data breaches, and unwanted access attempts. The firewall, a vital element that creates a barrier between your reliable network and the unpredictably vast internet, is at the vanguard of this protection.
Let me tell you What exactly a Firewall is :
Consider your network as a stronghold, with the firewall acting as the gatekeeper regulating access and departure. A firewall is essentially a software or hardware security system that keeps an eye on and regulates all incoming and outgoing network traffic by pre-established security standards. These rules serve as the first line of protection against potential threats by dictating which data packets are allowed to flow through and which are blocked.
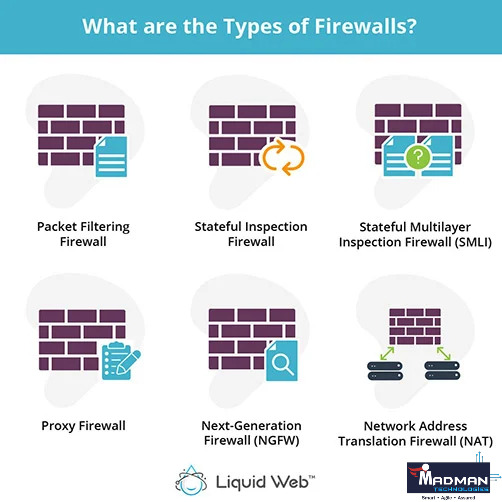
Types of Firewalls -
Firewalls come in various forms, each with its own set of functionalities tailored to meet specific security needs:
Packet-Filtering Firewalls: These inspect individual packets of data as they traverse the network, making decisions based on predetermined criteria such as IP addresses, ports, and protocols.
Stateful Inspection Firewalls: Building upon packet filtering, stateful inspection firewalls maintain a record of active connections and use this contextual information to make more informed decisions about allowing or blocking traffic.
Proxy Firewalls: Proxy firewalls operate as middlemen between internal and external network traffic, thoroughly inspecting data packets and enhancing security by masking internal IP addresses and adding more recording and analytic features.
Next-Generation Firewalls (NGFW): NGFWs offer complete security by fusing classic firewall functions with cutting-edge technologies. These characteristics include intrusion detection, application awareness, and enhanced threat protection.
The Role of Firewall in Cybersecurity -
A firewall's main function is to safeguard your network against the harmful activity, illegal access, and online threats. Firewalls assist in preventing intrusions, blocking malware infections, and reducing the dangers connected with a range of cyberattacks by enforcing security policies and filtering traffic by preset rules. These assaults include:
Denial-of-Service (DoS) Attacks: Firewalls can detect and block suspicious traffic patterns associated with DoS attacks, preventing them from overwhelming your network resources.
Malware infections: Firewalls can prevent efforts by viruses, worms, or other malware to infiltrate your network by screening incoming traffic for known malware signatures and dangerous behaviours.
Unauthorized Access Attempts: Firewalls can prevent efforts by viruses, worms, or other malware to infiltrate your network by screening incoming traffic for known malware signatures and dangerous behaviours.
Data Leakage: Firewalls help protect against data breaches and information leaks by granting granular control over outgoing traffic. This prevents sensitive data from leaving your network without the required authorization.
Best Practices for Firewall Implementation -
Firewalls are an essential part of cybersecurity, but how well they work depends on how well they are configured, maintained, and adhered to :
Define Clear Security Policies: Establish comprehensive security policies that outline the acceptable use of your network and the rules governing traffic flow.
Regularly Update Rulesets: Stay vigilant by updating firewall rulesets to address emerging threats and vulnerabilities, ensuring that your network remains protected against the latest cyber risks.
Monitor and Analyze Traffic: Implement logging and monitoring mechanisms to track network activity, detect anomalies, and identify potential security incidents in real time.
Combine with Additional Security Measures: Enhance your network security posture by complementing firewalls with intrusion detection systems (IDS), antivirus software, and other security measures.
Regular Audits and Assessments: Conduct periodic audits and security assessments to evaluate the effectiveness of your firewall configuration and identify areas for improvement.
Conclusion -
The firewall is the mainstay of network security in a time of ubiquitous cyber threats and digital connection. Firewalls are essential for protecting sensitive data, important assets, and the cybersecurity posture of your company because they efficiently manage traffic flow and enforce security standards. Accept the strength of firewalls as your first line of defence against the always-changing cyber threat landscape and provide your network the defence it needs.
One of the best sellers and service providers of firewalls is MADMAN TECHNOLOGIES, where A product must meet the following criteria to be eligible for the Firewall category:
Evaluate and filter user access;
Build barriers between networks and the internet; and
Notify administrators when unauthorized access is attempted.
Establish and uphold security and identification regulations.
Automate testing and monitoring-related duties
For any queries, you can google our website -
Contact details — 9625468776
#information technology#it products#it services#technology#itservices#it technology#application of firewall#it solutions#firewall#networking#secuity#network security
0 notes
Text
How to Protect Your Business From Cyber Threats
Cybersecurity is a major topic every business owner should be discussing. Here is some info from FRC that we hope helps.
Imagine we’re sitting down over a cup of coffee, and you’ve just asked me how to shield your trucking business from the ever-looming shadow of cyber threats. It’s a digital age dilemma, but I’m here to walk you through some straightforward strategies to bolster your defenses.
First off, let’s talk about the elephant in the room: cyber threats. They’re not just a problem for the tech industry;…

View On WordPress
#access control#antivirus software#cloud storage#cyber attacks#cyber threats#cybersecurity#cybersecurity laws#data protection#digital transformation#employee training#encryption#firewalls#incident response#legal compliance#malware#network security#password policies#phishing attacks#ransomware#secure communication#software updates#trucking industry#vendor security#VPN
0 notes
Text
How to Allow IP Addresses through Firewall Linux?
Configuring IP Access with iptables
Verifying iptables Installation
Listing Current Firewall Rules
Allowing Specific IP Addresses
Saving iptables Rules
Creating a Secure IP Whitelist
Defining Your IP Whitelist
Configuring iptables Rules
Testing Connectivity
Streamlining Firewall Management with BeStarHost
Introducing BeStarHost
Using BeStarHost for IP Whitelisting
Best Practices for Linux Firewall Management
Regularly Review and Update Whitelist
Implement Fail2Ban for Additional Security
Conclusion:
Effectively managing your Linux firewall is an integral part of maintaining a secure server environment. By mastering iptables and understanding how to allow specific IP addresses, you fortify your defenses against potential threats. Whether you opt for manual configuration or utilize tools like BeStarHost, the key is to stay vigilant, update your rules regularly, and adapt your security measures to evolving threats. Implementing these practices will empower you to keep your Linux server secure and resilient.
To Learn More, Click this Link:
#Linux Firewall Configuration#IP Address Whitelisting#Linux Firewall Rules#Network Security on Linux#Firewall Tutorial
0 notes
Link
You must have heard about firewalls but do you know what they are used for? Firewall programs are designed to protect the #vulnerabilities of your internal network from unauthorized access to the #Internet.
0 notes
Text

0 notes
Text
youtube
SOPHOS XGS SW-19.5.3 MR-3 Firewall | First Time Configuration | Step by Step in Hindi | By Sachin
#firewall#sophos xg firewall#network security tutorial#sophos xg firewall complete overview in hindi#how to setup sophos firewall in hindi#how to create rule in the sophos xg firewall#how to install sophos firewall#how to install sophos firewall on vmware#sophos xg v19#sophos xg firewall v19#xg firewall#setup sophos xg v19#configure sophos xg v19#configuring sophos xg v19#v19#xg firewall v19#sophos firewall#what is firewall#firewall explained#network firewall#Youtube
0 notes
Text
1)Who is Ionix?
We are a full-service MSP (Managed Service Provider) based in Elk City, OK.
2)What does an MSP do?
If your school or business uses technology, we can help streamline your operations and protect you from security threats and equipment failure. We can do all of this for a fixed rate, so you don't have to worry about your system stability or your budget.
3)What can Ionix provide?
This is a hard question to answer because every business is different, and we customize our solutions to fit your needs.
Small list of what we can provide:
Network Solutions: Firewall, Switches, Cabling and Wireless Access Points
Hardware for each user: Computer, Monitor, battery backup
Security Awareness Training
PCI Compliance/Consulting
Security Cameras
Data backup solutions
#WIRING#technology#Switch#smartboard#security cameras#network#MONITOR#Managed Services#laptop#firewall#desktop#cloud#cabling#backup
1 note
·
View note
Text
Always On VPN November 2023 Security Updates
Microsoft has released its security updates for November 2023. For Always On VPN administrators, it’s a light month, with just a single CVE affecting Always On VPN infrastructure.
PEAP
CVE-2023-36028 addresses a remote code execution (RCE) vulnerability in the Microsoft Protected Extensible Authentication Protocol (PEAP). An attacker could exploit this vulnerability by sending a specially…

View On WordPress
#Always On VPN#AOVPN#authentication#CVE#EAP#firewall#Microsoft#mitigation#network policy server#NPS#PEAP#protected extensible authentication protocol#security#security update#update#VPN#vulnerability#Windows#windows firewall#Windows Server#workaround
0 notes