#daily browser offer generator
Text
CLOUD COMPUTING: A CONCEPT OF NEW ERA FOR DATA SCIENCE
Cloud Computing is the most interesting and evolving topic in computing in the recent decade. The concept of storing data or accessing software from another computer that you are not aware of seems to be confusing to many users. Most the people/organizations that use cloud computing on their daily basis claim that they do not understand the subject of cloud computing. But the concept of cloud computing is not as confusing as it sounds. Cloud Computing is a type of service where the computer resources are sent over a network. In simple words, the concept of cloud computing can be compared to the electricity supply that we daily use. We do not have to bother how the electricity is made and transported to our houses or we do not have to worry from where the electricity is coming from, all we do is just use it. The ideology behind the cloud computing is also the same: People/organizations can simply use it. This concept is a huge and major development of the decade in computing.
Cloud computing is a service that is provided to the user who can sit in one location and remotely access the data or software or program applications from another location. Usually, this process is done with the use of a web browser over a network i.e., in most cases over the internet. Nowadays browsers and the internet are easily usable on almost all the devices that people are using these days. If the user wants to access a file in his device and does not have the necessary software to access that file, then the user would take the help of cloud computing to access that file with the help of the internet.
Cloud computing provide over hundreds and thousands of services and one of the most used services of cloud computing is the cloud storage. All these services are accessible to the public throughout the globe and they do not require to have the software on their devices. The general public can access and utilize these services from the cloud with the help of the internet. These services will be free to an extent and then later the users will be billed for further usage. Few of the well-known cloud services that are drop box, Sugar Sync, Amazon Cloud Drive, Google Docs etc.
Finally, that the use of cloud services is not guaranteed let it be because of the technical problems or because the services go out of business. The example they have used is about the Mega upload, a service that was banned and closed by the government of U.S and the FBI for their illegal file sharing allegations. And due to this, they had to delete all the files in their storage and due to which the customers cannot get their files back from the storage.
Service Models
Cloud Software as a Service
Use the provider's applications running on a cloud infrastructure
Accessible from various client devices through thin client interface such as a web browser
Consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, storage
Google Apps, Microsoft Office 365, Petrosoft, Onlive, GT Nexus, Marketo, Casengo, TradeCard, Rally Software, Salesforce, ExactTarget and CallidusCloud
Cloud Platform as a Service
Cloud providers deliver a computing platform, typically including operating system, programming language execution environment, database, and web server
Application developers can develop and run their software solutions on a cloud platform without the cost and complexity of buying and managing the underlying hardware and software layers
AWS Elastic Beanstalk, Cloud Foundry, Heroku, Force.com, Engine Yard, Mendix, OpenShift, Google App Engine, AppScale, Windows Azure Cloud Services, OrangeScape and Jelastic.
Cloud Infrastructure as a Service
Cloud provider offers processing, storage, networks, and other fundamental computing resources
Consumer is able to deploy and run arbitrary software, which can include operating systems and applications
Amazon EC2, Google Compute Engine, HP Cloud, Joyent, Linode, NaviSite, Rackspace, Windows Azure, ReadySpace Cloud Services, and Internap Agile
Deployment Models
Private Cloud: Cloud infrastructure is operated solely for an organization
Community Cloud : Shared by several organizations and supports a specific community that has shared concerns
Public Cloud: Cloud infrastructure is made available to the general public
Hybrid Cloud: Cloud infrastructure is a composition of two or more clouds
Advantages of Cloud Computing
• Improved performance
• Better performance for large programs
• Unlimited storage capacity and computing power
• Reduced software costs
• Universal document access
• Just computer with internet connection is required
• Instant software updates
• No need to pay for or download an upgrade
Disadvantages of Cloud Computing
• Requires a constant Internet connection
• Does not work well with low-speed connections
• Even with a fast connection, web-based applications can sometimes be slower than accessing a similar software program on your desktop PC
• Everything about the program, from the interface to the current document, has to be sent back and forth from your computer to the computers in the cloud
About Rang Technologies:
Headquartered in New Jersey, Rang Technologies has dedicated over a decade delivering innovative solutions and best talent to help businesses get the most out of the latest technologies in their digital transformation journey. Read More...
#CloudComputing#CloudTech#HybridCloud#ArtificialIntelligence#MachineLearning#Rangtechnologies#Ranghealthcare#Ranglifesciences
8 notes
·
View notes
Text
REBELFORUMS v.1.0.2.3 THREAD TAG:53173EXPRNC, 53173FINDS TYPE: HACK/LEAK
USERCODE: ThatsDefinitelyJelly
I got a copy of the MoJ OS, specifically the one used on their computers, it seems they have their own social media/forum board too.
What it says on the tin, they pretty much have their own chatter going on around the internet.
The copy seems to have belonged to someone else or is just unlocked somehow, here is what i found.
-So first of all, the accounts rarely have any usernames and instead use random codes of numbers and flairs seem to be the only way to find out atleast something of the person like an advocate or doctor flair.
-The platform seems to be simply named "MoJ Online Social Network".
-Settings seem to be quite simple, it registers where are you, what device you are using, the time, etc. however there doesn't seem to be things such as a block or report button, knowing the ministry this is most likely due to a certain group of personnel being in charge of monitoring the platform at all times.
-Out of curiosity i began snooping around threads and other users accounts to see if i found anything interesting and all i can say is that there is a lot to dig into.
-Most of the posts are just like, well celebrations, daily routine in the MoJ and such.
However i find it quite silly that they seem to be aware of the existence of rebel forums.
Some discussions related to the last point seem to always talk about taking our sites down, calling us unruly and you know the usual which isn't really surprising and tbh i kinda giggled reading all of those comments from scientists and personnel saying how we "need correction" and stuff.
Besides that there is also the discussions about marmalisation and happy stuff, also some advocates showing crafts, drawings or art in general that of course is mostly about happy things.
Digging deeper i found discussions about future MoJ projects but these discussions were locked and only specific flairs could reply to these, possibly due to their classified nature.
There was also a live tab that only seems to work when something like the fear test or that show of the felix guy is live, basically whenever a MoJ show or game is available the tab goes live.
I might add more things i found in the discussions in another post but for now, moving on.
There is a message/email inbox, it surprisingly can take even TERABYTES of information or files which i have to admit is quite impressive.
There was also a tab for updates or patches to the platform, which had your typical bug error fixes and stuff but what caught my attention is that apparently there is a platform related to oblivion as well, however the description seems to be vague so if any eclipse rebels are reading this feel free to leave anything you might have found related to this in the comments.
Moving on from the MoJ Online Social Network, lets move on to the other things this OS has to offer!
-The weather, time, date and curiously enough how many people the smiler has marmalised.
-There is pre-set folders to store information about advocates, personnel and other data, of course since this PC isn't completely connected to the MoJ it doesn't have any profiles in there or anything.
-There is your typical minesweeper, solitaire and strangely enough purble place but themed to the ministry, i found it quite silly.
-Your usual media player and photo display
-Customization seems to be limited, there is pre-set wallpapers and colors, the only thing that seems to be more open is the fonts.
-The internet besides the aforementioned social media seems to also be made by the MoJ, specifically a browser, now here is where things get truly interesting:
I said this browser was made by the MoJ, so it means it has access to basically an ENTIRE database server of them which it means i can definitely extract media, classified files and other things with ease BUT there is a catch, some of these files and pieces are titled as specific serial numbers or digits to prevent leaks...but that is NOT gonna stop me.
I'll try to see what i can find and give you all updates if there is something interesting i wanna show.
During the documentation of this post i came to the realization this is basically a very much modified and i mean very MODIFIED version of 'Windows 7' which means that if you know the knicks and knacks of PCs, coding and stuff you might have A LOT of things to archive and leak with just a few clicks and taps, lookin' at you Joy-Leakers and co.!
Anyway, CYA all! Will keep you all updated, specially if i manage to make another copy of this OS to dump here!
2.4k Dots - 560 replies
4 notes
·
View notes
Text
The Evolution of Media and Its Impact on Surveillance and Privacy Issues: A Family Legacy of Control?
Let's dive into the rabbit hole and explore how the evolution of media over time has led to the surveillance and privacy issues we face today in our digital world, and how one family's legacy might be influencing it all.

Let's rewind to the 1940s and 1950s when television was this fresh new medium on the block. Back then, programming was pretty limited, but as TV sets became more affordable and widespread, content started to diversify and reach broader audiences. The role of television in society began to grow, and with it came the government's increasing influence over media narratives.
The 1960s saw TV become even more politically engaged, with news outlets giving more coverage to social and political issues, like the civil rights movement and the Vietnam War. As television continued to evolve and diversify, it became a crucial tool for governments to spread their messages and manipulate public opinion.

Now let's fast forward to the present day, where the digital age has taken media to a whole new level. We consume information through various platforms, from social media to streaming services, which offer governments even more opportunities to collect data and keep an eye on us. And it's not just Big Brother watching us; we live in a world of browser cookies and sophisticated algorithms that track our every move.

Enter Edward Bernays, the "father of public relations," who believed that by understanding human behavior, one could create a more compliant and easily controlled society. It's no coincidence that his grand-nephew, Marc Randolph, went on to become the first CEO of Netflix. The connection between media and manipulation runs deep in that family tree!

My hypothesis is that the studies and observations of Sigmund Freud, the founding father of psychoanalysis, have been passed down through the generations, from Bernays to Randolph. As a result, their methods and practices have evolved alongside media, making their influence on society even more potent.

We can't talk about surveillance and privacy issues without mentioning the Patriot Act. Passed after the 9/11 attacks, this controversial legislation gave the government unprecedented access to our personal information without a warrant. This invasion of privacy has led to numerous lawsuits against the government for spying on its own citizens.

The evolution of media over time has played a pivotal role in shaping the surveillance and privacy issues we face today. As media continues to evolve and become more integrated into our daily lives, we need to stay vigilant and question the motives behind the narratives we're fed. The legacy of Freud, Bernays, and Randolph serves as a stark reminder of the power that media and manipulation can have over society.
- JOREEEZY
https://k4v3.com/

12 notes
·
View notes
Text
Favorite iOS Safari Extensions
On iOS (iPhones and iPads), Safari is the undisputed leader of the browsers, primarily because Apple puts very tight restrictions on other browser apps that makes it very difficult for them to offer the same features that Safari does.
Thankfully, you can install extensions to tweak Safari's behavior and customize websites, as long as your device is running iOS 15 or higher. Here are the Safari Extensions I use on a daily basis. Most are free (or at least have a free version), and all work on both iPhones and iPads.
For desktop computers, you can also check out my recommendations for Firefox addons)
Last updated Jan 2024 (added UnTrap and Vinegar)
Index:
AdGuard
Noir
uBlacklist
Userscripts
Sink It for Reddit
UnTrap
Vinegar
AdGuard
This addon is free if you just want to use the built in adblocking lists. For a small yearly fee, you can pay for "Pro" features, which allows you to add any custom adblocking list to the app, as well as providing a local VPN that can block ads and trackers inside any app on your phone. I use the Safari adblocking lists 24/7 because they are so helpful, but the VPN can drain your battery faster than normal, so I only turn that on when I am using an app with a lot of ads, like Apple News or a mobile game. Between AdGuard and the two YouTube-customizing extensions below, I haven’t seen an ad on YouTube in Safari in months.
Noir
Adds a dark mode to any website. It's using heuristics (fancy guessing) to figure out which website colors need to be changed so that it's properly darking, so sometimes it can make mistakes. In that case, it has a built in way to send a bug report to the developer, who is pretty responsive in my experience. You can also turn it off for specific sites right from inside Safari.
uBlacklist
This addon hides search engine results with specific domains. Example: you can hide images results from AI generator sites, OR if you search for tech support advice and one of those stupid auto-generated sites filled with SEO garbage but no actual information keeps popping up, you can use this addon to hide everything from that website, right from the Google/DuckDuckGo/other search results.
Userscripts
Allows you to install userscripts and stylesheets that customize website behavior or appearance. The addon can check for updates of your userscripts and uses iCloud to synchronize them across devices too, which is really nice. The userscripts I use are:
Bypass Paywalls Clean (removes news website paywalls)
Amazon Sponsored Products Removal (self-explanatory)
Redirect Fandom to BreezeWiki (bypasses ad-filled fandom.com domains for indie wikis or an ad-free proxy site. The link documents 2 userscripts with slightly different behavior; use whichever you prefer).
Sink It for Reddit
I switched to using Reddit in the browser only after the whole API/third party apps fiasco. AdGuard blocks the ads in the web interface, but there were still a lot of annoyances because Reddit constantly bombarded you with prompts/popups trying to get you to switch to their app so they could track you and sell you ads. Sink It for Reddit removes all of those popups and lets you customize the behavior of the Reddit website too (tapping a post can open it in a new tab, back to top buttons for long posts, and video downloads, among other things). Constantly being updated too, which is nice to see.
UnTrap (USD $1.99)
This extension cleans up the YouTube interface in the browser. You can hide Shorts, Explore, Trending, and multiple flavors of Suggestions (videos, playlists, etc.). It also has a content filter you can use to ensure you never see certain channels or even specific videos by ID, username, or keyword/regex. There are over 50 options you can tweak for the video playback page alone, so if you’re looking to remove an annoyance from YouTube in Safari on iOS, this is the addon for you. Note however that this is the first extension I’ve recommended that does NOT have a free version.
Vinegar (USD $1.99)
This extension replaces YouTube’s custom video player with a standard HTML5 one. This means that YT videos will play back using the standard iOS video player interface, including all of the accompanying benefits: better interface, Picture in Picture/popout videos work, videos continue playing in the background even if you leave Safari, etc.. I was even able to start a YouTube video in Safari, lock my phone, and then continue playing the video and hear the audio over my car’s speakers via CarPlay. These are all normally locked features reserved for YouTube Premium subscribers. You can also set a default quality that it will use so YouTube won’t use “auto” and set you to 360p just because you’re using a phone.
2 notes
·
View notes
Text
Top 10 Sites Like MangaOwl
MangaOwl is a user-friendly website that offers a wide variety of anime-related content such as anime movies, dramas, episodes, news, and more. Anime has become a billion-dollar industry and has captivated audiences worldwide for over a century. Anime enthusiasts enjoy the unique storytelling, character portraits, storylines, subplots, and character growth that make for an entertaining and educational viewing experience.
Is MangaOwl Safe?
MangaOwl is generally considered a safe website with a good reputation online. It is trustworthy, virus-free, and has no malicious content. However, users may encounter suspicious pop-up ads when streaming. To ensure safety, avoid clicking on or accepting any files from the website. Most browsers have built-in security measures that prevent automatic downloading.
If you're looking for a safe and reliable site to read manga for free, try MangaHub. This digital Japanese manga website provides users with a diverse selection of top comic novels, covering a range of genres such as action, comedy, drama, and more. MangaHub is a great alternative to MangaOwl if you're on a budget and can't afford to buy comic books.
Here are some alternative phrasings:
Mangastream
MyReadingManga is a free website where you can read Bara, shota, furry, yaoi manga and doujinshi online for free. While this site is not suitable for children under 18, it is a great choice for adult manga fans who want access to a wide range of stories. You can keep track of your favorite manga stories and use MyReadingManga as a library.
Another great MangaOwl alternative is MangaKatana, a website that offers free online manga reading. With a vast collection of manga and daily updates, MangaKatana is an excellent choice for fans who want to stay up to date on their favorite series. You can read manga adaptations of popular shows and movies without having to search for them on different websites.
Looking for alternatives to MangaOwl? Check out MangaReader, a free online library for comics and manga. You can keep track of your favorite manga stories and access a wide variety of genres, from action to romance to supernatural. MangaReader is popular in multiple countries, including Japan and China.
MangaNelo is an excellent alternative to MangaOwl for those who want a diverse selection of manga genres. This website offers free access to a broad range of manga, from shoujo-ai to manhua to webtoons. You can also find an extensive collection of pornographic works on MangaNelo, so be aware that some content may not be suitable for young readers.
Mangastream is a website that offers a vast selection of comics and serves as an excellent alternative to MangaOwl. It has a straightforward user interface that allows users to bookmark their favorite manga for later reading. The website is known for its extensive comics archive and regularly updated comic content. It is a one-stop destination for comic readers where they can access history, read manga in other languages, and explore all versions of comics all in one place.
Website: http://mangastream.mobi
Mangatx
Mangatx is a free website for reading Manga, Manhwa, Manhua, and Novel online. The website constantly updates its database of the latest comic books, making it an excellent alternative to MangaOwl. If you are a big fan and want to stay up-to-date, you can use it as a library to find your favorite manga stories. It is the best place to read manga online.
Website: https://mangatx.com
MangaBat
MangaBat
With over 70 distinct manga categories, MangaBat offers diverse stories and genres. Your manga may also be uploaded and shared. This website’s significant advantage is allowing people to leave comments on a wide range of manga. MangaBat provides something for everyone, no matter what their interests are. You can get all the information you need about a character or the latest series chapter right here. It is one of the most reliable and safe MangaOwl alternatives site to read manga and comics online.
Website: https://manga-bat.com
For the most extensive collection of Japanese manga, check out MangaRaw. This free website offers a wide range of comics, including popular titles like Bleach, One Piece, Naruto, and Dragon Ball Z. You can also read certain manga comics in Spanish. MangaRaw is a great MangaOwl alternative site for manga enthusiasts who want access to a vast library of comics.
Is MangaOwl Legal?
MangaOwl is an illegal app and website for reading manga online. The legality of online streaming sites varies from country to country, and some have yet to determine their legality. To protect your privacy and avoid illegal usage of free manga sites like MangaOwl, it is recommended to use a VPN.
Finally, SkyManga is a popular MangaOwl alternative for webtoon and manga readers. You can read manga for free on SkyManga, and the site's chapters are optimized for mobile viewing, so you can read on the go. If you want to support the site financially, you can do so as well.
Website: https://skymangas.com
What are the most popular manga on MangaOwl?
MangaOwl offers a vast selection of popular manga that you can read, such as Painter of the Night, Dangerous Convenience Store, Under the Green Light, Hana and the Beast Man, Touch to Unlock, No Love Zone, Pearl Boy, Hold Me Tight, Karina's Last Days, The Secret Life of the Demon King, Stranger Than Friends, The Kept Man Strikes Back, Mad Place, Sexercise, No Better Than Strangers, Seashell Boy, Even If You Don't Love Me, The Man Who Saved Me from My Isekai Trip, Rent a Girlfriend, The Unquenchable Mr. Kim, and many more.
What languages of manga are available on MangaOwl?
MangaOwl is an illegal website that releases new manga within hours of their release. You can stream English manga on this website, and it also provides the latest Korean, Chinese, Spanish, and French manga. All manga content is available in high definition (HD). Additionally, it allows you to download manga for free.
Final Thoughts
MangaOwl provides all popular manga series, and new manga is added daily to keep fans updated on the latest releases. It is a competitor to MangaReader but offers additional tools, features, and services with no limit. It provides manga for over 25 manga categories, allowing you to read your favorite manga from its extensive library. It is an online manga and manhua streaming service that you can use for free. Alternatively, you can consider MangaOwl alternatives to read your favorite manga online for free.
5 notes
·
View notes
Text
Ganbare Snake / 頑張れスネーク
It happened on Christmas Eve… Snake was chillin’ in his flat as he sensed an infiltrator coming in… With the power of OctoCamo, he caught the black-gloved maniac off guard! Pretty Good Snake! But… oh no… it's… It's too late for excuses!
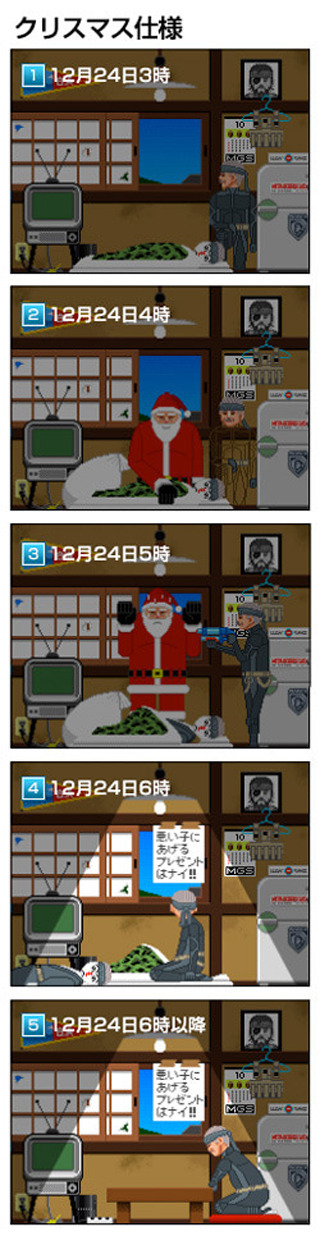
忌い子にあげるプレゼントはナイ!!
No Gifts for Nasty Children!!
Poor Snake. What a sad story… the war veteran who couldn’t help himself is now even punished for his trauma.
Will he ever manage to find peace?
In case you wonder what this is: MGS4 featured the Sony Ericsson W62S. It had an ambitious flash-based menu Design which the in-house Sony Development Team feared as it might slow down the performance of the device. It didn’t get the green light at first, but then the team proved that the impossible is possible!

As a benefit "Drama Menus" were offered to their customers.

Depending on the day and the time the phone is switched on, they would change their appearance and would give little surprises on certain days. "We wanted people to enjoy it and say things like, 'I feel a bit better today' or 'When will I get the next one?' We aimed to make it enjoyable" (Yoshinori Muramatsu, General Manager of Sony). The images furthermore contained information about the status of the phone. For example, the bench in the picture above has three planks… like the symbol for the battery… and so the color of them would fade away accordingly to the energy that is left. But the Menus would get even more playful with "Do your best, Salaryman!" (Ganbare Salaryman / 頑張れサラリーマン).

Here you could observe an "old man" working at a "certain company" being paid for… "existing as a content menu"! At the first glance, this is a contradiction to Sony's strive for coolness, but the salaryman’s everyday life became very popular and he had even fan groups on Japanese forums. Of these groups 90% were female! ….Or at least this is what somebody told director Naoto Ishibashi…
To tell a story with these menus grew organically out of the idea to make the features of the phone more enjoyable. You could look at the photos within a slideshow and the developed mechanism behind it was the foundation of such narrations. Most of the Salaryman's scenes show routines of his daily life.
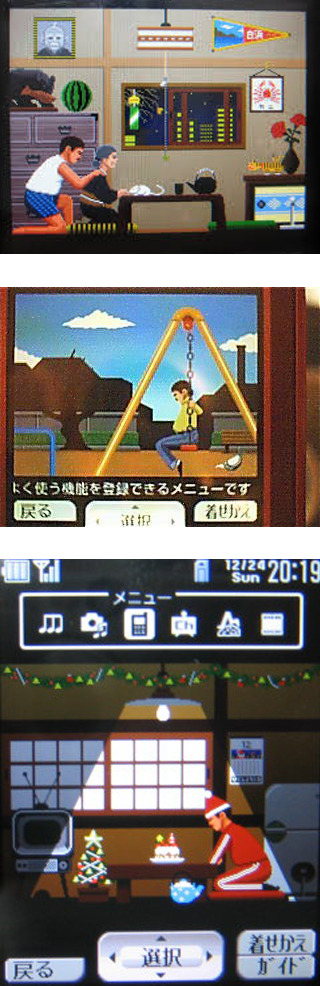
But there are rather unusual scenes at certain times… Like an Office Chair Race!
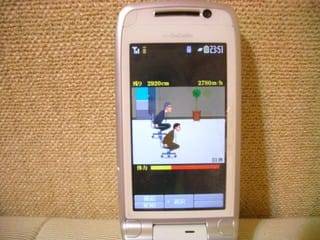
When the product placement of Sony Ericsson W62S came along, it happened that the "person in charge at the Konami side" was a fan of the Salaryman (Director Ishibashi does not mention who exactly that person is). Both sides agreed that the tone should be a fun one and so "Do your best, Old Snake!" (Ganbare Snake / 頑張れスネーク) was born.

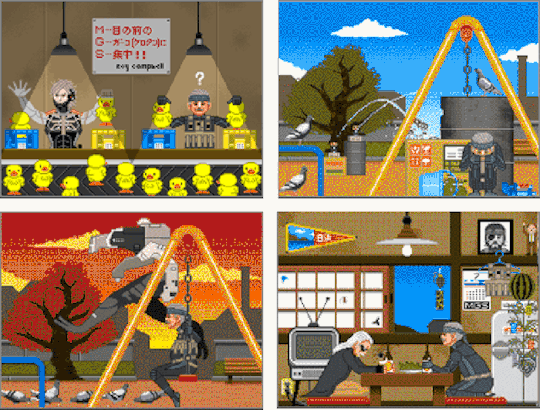


The Drama Menu was released on 15th May 2008. MGS4 was just finished two days earlier (reaching the "Gold" status). In 2009, it was no longer available for download (according to a post by the Hideoblog on 10th November 2009).
The original QR Codes can be still caught on the Wayback Machine link if your browser is a bit too slow to build the block that is supposed to cover them. Ishibashi did not rule out that the oversea customers could also be blessed with this creation. But that didn’t happen… perhaps because this MGS Oddity was built upon a phenomenon that was only known in Japan.
Sources for the text:
[https://k-tai.watch.impress.co.jp/cda/article/interview/41372.html]
[https://www.itmedia.co.jp/mobile/articles/0508/12/news077.html]
[https://ameblo.jp/kp-blogcast/entry-10385343459.html]
Official Website:
[https://href.li/?https://web.archive.org/web/20080605010843/http://www.konami.jp/mgs4/jp/gansune/index.html]
Additional Images from:
[https://plaza.rakuten.co.jp/arisalovely/4018/]
[https://blog.goo.ne.jp/gj020433/e/17faacc8d21087dc29f5681ac0d2ad33]
[https://encrypted-tbn0.gstatic.com/images?q=tbn:ANd9GcRZaJwJGAW3tGDStGQ4YsspeUPAUF5qPptgNw&usqp=CAU]
[https://likebluesnow.at.webry.info/200707/article_8.html]
[https://static.wikia.nocookie.net/metalgear/images/2/2a/MGS4_Sony_Ericsson_W62S.jpg/revision/latest/scale-to-width-down/475?cb=20150208184650]
[https://k-tai.watch.impress.co.jp/cda/parts/image_for_link/191398-41372-8-1.html]
[http://ahiru178.com/archives/51292804.html]
[http://2.bp.blogspot.com/_h5hOmDEy1n4/SIDhtOwr2xI/AAAAAAAA7eE/26ViYyqvzAE/w1200-h630-p-k-no-nu/se.JPG]
2 notes
·
View notes
Text
what's the difference between dns and vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what's the difference between dns and vpn
DNS Explained
Title: Demystifying DNS: Understanding the Backbone of the Internet
DNS, or Domain Name System, is the unsung hero of the internet, quietly working behind the scenes to ensure that when you type a web address into your browser, you're taken to the correct website. Essentially, DNS acts as the internet's phonebook, translating human-friendly domain names like "example.com" into IP addresses, which are the unique numerical identifiers assigned to each device connected to the internet.
Imagine you're trying to find a friend's house in a sprawling city. You might know their name and general location, but without an address, you'd be lost. DNS provides those addresses for websites, allowing your device to locate and connect to them.
The DNS system operates through a distributed network of servers worldwide. When you enter a domain name into your browser, your device sends a query to a DNS resolver, typically operated by your internet service provider (ISP) or a third-party DNS provider like Google or Cloudflare. The resolver then communicates with other DNS servers to find the IP address associated with the requested domain.
This process involves several steps, including querying authoritative DNS servers, which are responsible for storing and providing information about specific domains. Once the resolver obtains the IP address, it caches the information to speed up future requests, reducing the need to query multiple servers for the same domain.
DNS plays a critical role in ensuring the smooth operation of the internet, enabling users to access websites and other online services with ease. Without DNS, navigating the vast digital landscape would be akin to finding a needle in a haystack.
In conclusion, while DNS may seem like a technical concept reserved for experts, it's a fundamental component of the internet that impacts our daily online experiences in profound ways. So the next time you visit a website, remember to thank DNS for effortlessly guiding you to your destination.
VPN Basics
A Virtual Private Network (VPN) has become an essential tool for ensuring online privacy and security. VPNs work by creating a secure and encrypted connection between the user's device and a remote server operated by the VPN service. This connection masks the user's IP address, making it difficult for anyone to track their online activities.
One of the primary benefits of using a VPN is the ability to browse the internet anonymously. By connecting to a VPN server, users can hide their real IP address and location, preventing websites, advertisers, and even internet service providers from tracking their online behavior. This not only protects users' privacy but also helps to bypass censorship and geo-restrictions.
Additionally, VPNs enhance security by encrypting data that is transmitted over the internet. This is crucial when using public Wi-Fi networks, as it prevents hackers from intercepting sensitive information such as passwords, credit card details, and personal messages. By using a VPN, users can protect themselves from potential cyber threats and maintain their online security.
Moreover, VPNs are valuable for accessing restricted content and bypassing internet censorship. By connecting to a VPN server in a different country, users can unblock websites and services that may be unavailable in their region due to geo-restrictions or government censorship.
In conclusion, VPNs are powerful tools that offer online privacy, security, and freedom. By using a VPN, users can protect their sensitive information, browse the internet anonymously, and access restricted content from anywhere in the world. Considering the growing concerns about online privacy and security, integrating a VPN into your online routine is a wise decision.
DNS vs VPN
DNS (Domain Name System) and VPN (Virtual Private Network) are both critical components of modern internet usage, but they serve different purposes and operate at different levels of the online infrastructure.
DNS is like a phonebook for the internet. It translates human-readable domain names (like www.example.com) into IP addresses (such as 192.0.2.1) that computers use to communicate with each other. When you type a URL into your browser, your device sends a DNS query to a DNS server, which then returns the corresponding IP address, allowing your device to connect to the desired website.
On the other hand, a VPN creates a secure, encrypted connection between your device and a remote server operated by the VPN service. This tunnel encrypts all the data passing between your device and the internet, protecting it from prying eyes and potential hackers. VPNs are commonly used to enhance online privacy, bypass geo-restrictions, and secure connections on public Wi-Fi networks.
While both DNS and VPNs can enhance online security and privacy, they serve different functions. DNS primarily focuses on translating domain names into IP addresses, while VPNs encrypt and secure internet traffic. However, they can complement each other when used together. For example, a VPN can encrypt your internet traffic, while a private DNS resolver can prevent your ISP from logging your browsing history.
In conclusion, DNS and VPNs are essential components of the internet, each serving distinct purposes in enhancing security and privacy online. Understanding how they work and when to use them can help users navigate the digital landscape more safely and securely.
DNS Functionality
Title: Understanding DNS Functionality: Navigating the Web's Address Book
DNS (Domain Name System) is the backbone of the internet, serving as its address book. When you type a website address into your browser, like "www.example.com," DNS translates that human-readable domain name into an IP address, such as "192.0.2.1," which computers understand. This translation enables seamless communication between devices across the internet.
The functionality of DNS involves several key components:
DNS Resolver: When you enter a domain name into your browser, your device sends a query to a DNS resolver, typically provided by your Internet Service Provider (ISP) or a third-party service. The resolver then seeks the IP address associated with the requested domain name.
Root Servers: If the resolver doesn't have the IP address cached, it contacts a root server. These servers maintain a database of all top-level domain (TLD) names, such as ".com," ".org," and ".net."
Top-Level Domain (TLD) Servers: The root server directs the resolver to the appropriate TLD server based on the domain's extension (e.g., ".com"). TLD servers manage domain names within their respective domains.
Authoritative DNS Servers: Once the resolver reaches the appropriate TLD server, it is directed to the authoritative DNS server responsible for the specific domain name. This server holds the most up-to-date information about the domain's IP address.
Caching: To improve efficiency, DNS resolvers cache IP address information for a specified time, reducing the need to repeatedly query authoritative servers for frequently accessed domain names.
Overall, DNS functionality ensures that users can access websites by name rather than remembering complex numerical IP addresses. It plays a crucial role in facilitating the seamless navigation of the internet, making it accessible and user-friendly for billions of people worldwide. Understanding DNS is essential for anyone navigating the digital landscape, as it underpins virtually all online activities.
VPN Encryption
VPN Encryption: Keeping Your Online Activities Secure
VPN encryption is a method of securing your internet connection by creating a private network from a public internet connection. Through encryption, a VPN protects your data from being intercepted, monitored, or manipulated by potential hackers, government authorities, or internet service providers.
Encryption in VPN services scrambles the data you send over the internet into a code that only the intended recipient can decipher. This process ensures that even if someone manages to intercept your data, they won't be able to make sense of it without the decryption key.
There are several encryption protocols used in VPN services, including OpenVPN, IPSec, and L2TP/IPSec. Each protocol has its level of security and speed, so it's essential to choose a VPN provider that offers strong encryption methods while maintaining a fast connection.
When selecting a VPN provider, look for one that utilizes AES-256 encryption, which is considered military-grade encryption and is virtually unbreakable. Additionally, ensure that the VPN provider follows a no-logs policy, meaning they do not store any information about your online activities.
By using a VPN with robust encryption, you can browse the internet anonymously, access geo-restricted content, and secure your online transactions. Whether you're working remotely, traveling, or simply want to enhance your online privacy, VPN encryption is a crucial tool in safeguarding your digital information.
0 notes
Text
does roboform work with vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does roboform work with vpn
RoboForm compatibility
RoboForm is a popular password management tool that helps users securely store and manage their passwords across multiple devices. One key aspect of RoboForm is its compatibility with various operating systems and browsers, making it a versatile tool for users who access the internet on different platforms.
RoboForm is compatible with major operating systems such as Windows, macOS, iOS, and Android, ensuring that users can seamlessly integrate it into their daily digital activities regardless of the devices they use. This cross-platform compatibility is essential for users who switch between different devices throughout the day and need access to their passwords and other sensitive information on the go.
Moreover, RoboForm is also compatible with a wide range of web browsers, including Google Chrome, Mozilla Firefox, Microsoft Edge, and Safari. This browser compatibility means that users can use RoboForm's autofill features and password generation capabilities across their preferred internet browsers, enhancing their overall user experience and productivity.
In addition to operating systems and browsers, RoboForm is also compatible with applications such as Microsoft Outlook and Windows Explorer, further extending its usefulness for users who rely on these tools for their work or personal tasks.
Overall, RoboForm's compatibility with various operating systems, browsers, and applications makes it a versatile and valuable tool for users looking to improve their online security and productivity. By ensuring seamless integration across different platforms, RoboForm offers users a convenient and efficient way to manage their passwords and sensitive information securely.
VPN integration verification
VPN integration verification is a crucial step in ensuring the security and effectiveness of a virtual private network (VPN) solution. When setting up a VPN, it is essential to confirm that the integration has been successfully implemented to avoid any vulnerabilities or leaks that could compromise sensitive data.
The verification process for VPN integration typically involves several key steps. Firstly, it is essential to verify that the VPN connection is established correctly and that all network traffic is encrypted and routed through the VPN tunnel. This can be confirmed by checking the network settings on the device and ensuring that the VPN is enabled.
Additionally, it is important to verify the IP address assigned by the VPN server to ensure that the user's real IP address is masked and replaced with the VPN server's IP address. This helps maintain anonymity and privacy while browsing the internet.
Furthermore, conducting a DNS leak test is crucial to ensure that the device's DNS requests are also being routed through the VPN tunnel rather than through the internet service provider's DNS servers. DNS leaks can expose the user's browsing history and undermine the purpose of using a VPN for privacy and security.
Overall, VPN integration verification is essential to guarantee that the VPN solution is functioning as intended and providing the necessary level of security and privacy. By following a thorough verification process, users can confidently use VPN services to protect their online activities and data from potential threats and prying eyes.
RoboForm functionality with VPN
RoboForm, a leading password management software, has revolutionized the way users secure their online accounts. Its integration with VPN (Virtual Private Network) technology further enhances users' privacy and security measures.
VPN services encrypt users' internet traffic and route it through a remote server, hiding their IP address and location. This encryption protects sensitive data from potential cyber threats and surveillance activities. By combining RoboForm with VPN functionality, users can enjoy an extra layer of protection when accessing their accounts and browsing the web.
One of the primary benefits of using RoboForm alongside a VPN is enhanced anonymity. When logging into online accounts, RoboForm securely stores and autofills passwords, eliminating the need to manually enter them. With the added security of a VPN, users can browse the internet with confidence, knowing that their online activities are shielded from prying eyes.
Moreover, RoboForm's password generator feature ensures that users create strong, unique passwords for each of their accounts. By automatically generating complex passwords and securely storing them, RoboForm minimizes the risk of accounts being compromised due to weak passwords.
Additionally, the integration of RoboForm with VPN technology enables users to bypass geo-restrictions and access content that may be blocked in their region. This feature is particularly useful for individuals who travel frequently or reside in countries with strict internet censorship laws.
In conclusion, the combination of RoboForm's password management capabilities with VPN functionality offers users a comprehensive solution for safeguarding their online privacy and security. By leveraging these tools together, users can enjoy peace of mind knowing that their sensitive information is protected against cyber threats and unauthorized access.
VPN and RoboForm synergy
In today's digital landscape, security and privacy are paramount concerns for individuals and businesses alike. With cyber threats becoming increasingly sophisticated, it's essential to employ robust solutions to safeguard sensitive information. Two tools that work hand-in-hand to enhance online security and user convenience are Virtual Private Networks (VPNs) and RoboForm.
A VPN serves as a secure tunnel between your device and the internet, encrypting data transmitted over the network. By masking your IP address and encrypting your internet connection, a VPN shields your online activities from prying eyes, such as hackers, government surveillance, and even your Internet Service Provider (ISP). This encryption ensures that your data remains confidential and secure, especially when accessing public Wi-Fi networks or browsing sensitive information.
RoboForm, on the other hand, is a password manager and form filler designed to simplify and secure your online experience. It stores your login credentials, payment details, and personal information in an encrypted vault, eliminating the need to remember multiple passwords or repeatedly fill out forms. With RoboForm, you can generate strong, unique passwords for each account, reducing the risk of password-related breaches and ensuring hassle-free access to your favorite websites and services.
When used together, VPNs and RoboForm create a synergy that enhances both security and convenience. By encrypting your internet connection with a VPN, you can browse the web anonymously and protect your data from interception. Meanwhile, RoboForm manages your passwords and forms, streamlining your online interactions while maintaining robust security measures. Whether you're banking online, shopping, or accessing sensitive information, the combination of a VPN and RoboForm provides comprehensive protection against cyber threats and enhances your digital privacy.
Ensuring RoboForm effectiveness with VPN
RoboForm is a popular password manager that helps users securely store and manage their passwords. Using a Virtual Private Network (VPN) in conjunction with RoboForm can further enhance your online security and privacy.
When it comes to ensuring the effectiveness of RoboForm with a VPN, there are several key benefits to consider. First and foremost, a VPN encrypts your internet connection, making it more difficult for hackers or malicious third parties to intercept your data. This added layer of security is crucial when transmitting sensitive information such as your passwords through RoboForm.
Additionally, using a VPN can help you bypass geo-restrictions and access websites that may be blocked in your region. This can be particularly useful when you need to securely log in to accounts or access services while traveling or using public Wi-Fi networks.
Furthermore, by hiding your real IP address and location, a VPN adds another level of anonymity to your online activities. This can help prevent tracking by advertisers and protect your privacy while using RoboForm to fill in passwords on various websites.
It's important to choose a reputable VPN provider that offers strong encryption protocols, a strict no-logs policy, and high-speed servers to ensure optimal performance. By combining the security features of both RoboForm and a VPN, you can enjoy peace of mind knowing that your sensitive information is well-protected online.
0 notes
Text
does vpn work when app is on
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn work when app is on
VPN functioning with active applications
Title: Understanding VPN Functioning with Active Applications
In today's interconnected digital landscape, virtual private networks (VPNs) have become indispensable tools for safeguarding online privacy and security. However, many users are often left wondering about the functionality of VPNs when running active applications. Let's delve into how VPNs operate in conjunction with these applications.
Firstly, it's essential to grasp the fundamental role of a VPN. A VPN creates a secure and encrypted connection between your device and the internet by routing your traffic through a remote server. This process shields your data from prying eyes, such as hackers, ISPs, and government surveillance, ensuring confidentiality and anonymity online.
When it comes to active applications, such as web browsers, messaging platforms, or streaming services, the VPN operates transparently in the background. Once you establish a VPN connection, all data transmitted from your device, including the traffic generated by active applications, is encrypted and routed through the VPN server. This means that regardless of the application you're using, your online activities remain protected.
Moreover, VPNs offer additional benefits when using active applications. They enable users to bypass geographical restrictions and access region-locked content on platforms like Netflix or Hulu. By connecting to a server in a different location, users can appear as if they're browsing from that region, unlocking a vast array of content otherwise unavailable in their location.
However, it's crucial to note that VPNs may impact the performance of active applications to some extent. Since the data is routed through an external server, there might be a slight increase in latency or a decrease in connection speed. Nevertheless, reputable VPN providers strive to minimize these effects by maintaining high-speed servers and optimizing network infrastructure.
In conclusion, VPNs seamlessly integrate with active applications, ensuring that users can enjoy the benefits of privacy, security, and unrestricted access to online content. By understanding how VPNs function in conjunction with these applications, users can make informed decisions to enhance their online experience.
App compatibility with VPN usage
App Compatibility with VPN Usage
Using a Virtual Private Network (VPN) has become increasingly popular for individuals seeking to enhance their online privacy and security. However, ensuring that your favorite apps are compatible with VPN usage is essential for maintaining seamless functionality and protecting your data across various platforms.
One of the primary concerns when using a VPN is whether it will work seamlessly with the apps you rely on daily. Fortunately, most reputable VPN providers offer broad compatibility across a wide range of devices and operating systems, including Windows, macOS, iOS, and Android. This compatibility ensures that whether you're browsing the web, streaming content, or accessing sensitive information, your VPN can provide the necessary protection without hindering your app usage.
However, there may be instances where certain apps encounter compatibility issues when used alongside a VPN. This can occur due to various factors, such as the app's design, network configurations, or how it handles connections. In such cases, troubleshooting steps like adjusting VPN settings, updating the app, or contacting the VPN provider's support team can often resolve the issue.
It's also worth noting that while most apps should function normally with a VPN, there may be exceptions, particularly with region-specific services or apps that rely heavily on precise location data. In these cases, you may need to temporarily disable the VPN or explore alternative solutions to ensure optimal app performance.
Ultimately, choosing a reputable VPN provider known for its compatibility and reliability is crucial for ensuring a seamless experience across all your favorite apps. By selecting a VPN service that prioritizes compatibility and provides robust support, you can enjoy enhanced privacy and security without sacrificing app functionality.
VPN effectiveness during application operation
Virtual Private Networks (VPNs) have become indispensable tools for ensuring online security and privacy, particularly during application operation. The effectiveness of VPNs in this regard stems from their ability to encrypt data traffic, thereby shielding it from potential interception by malicious entities.
One of the primary benefits of using a VPN during application operation is the encryption of data transmissions. When an application communicates with servers over the internet, the data exchanged can be vulnerable to interception by hackers or other unauthorized parties. By routing this traffic through a secure VPN server, all data passing between the application and the server is encrypted, making it virtually impossible for anyone to intercept and decipher without the encryption key.
Moreover, VPNs offer additional layers of security by masking the user's IP address and location. This makes it significantly harder for cybercriminals to track the user's online activities or launch targeted attacks based on their geographic location.
Furthermore, VPNs can bypass geographic restrictions imposed by certain applications or services. For example, streaming platforms often limit access to content based on the user's location. By connecting to a VPN server in a different country, users can circumvent these restrictions and access content that may be otherwise unavailable in their region.
However, it's essential to note that the effectiveness of a VPN during application operation relies on the quality and reliability of the VPN service provider. Users should choose reputable VPN services that offer robust encryption protocols, a wide selection of servers, and a strict no-logs policy to ensure their online privacy and security are adequately protected.
In conclusion, VPNs play a crucial role in ensuring the effectiveness of application operation by encrypting data traffic, enhancing online security and privacy, and bypassing geographic restrictions. By utilizing a reliable VPN service, users can enjoy a safer and more secure online experience while using their favorite applications.
Impact of active apps on VPN performance
When it comes to using a Virtual Private Network (VPN), the performance of the VPN can be significantly impacted by active apps running on the device. Active apps consume device resources such as bandwidth, CPU power, and memory, which can in turn affect the speed and stability of the VPN connection.
One of the primary ways active apps impact VPN performance is by competing for bandwidth. Bandwidth-hungry applications such as streaming services, online gaming, or large file downloads can consume a significant portion of the available bandwidth, leading to decreased speeds and potential connection drops when running a VPN at the same time.
Moreover, resource-intensive apps can also hog CPU power and memory, slowing down the device's overall performance and potentially causing lags in the VPN connection. This can be particularly noticeable on older devices with limited processing power and memory.
To mitigate the impact of active apps on VPN performance, users can consider closing or pausing unnecessary apps while running a VPN to free up valuable resources. Prioritizing VPN-sensitive activities and avoiding bandwidth-heavy tasks can also help maintain a stable and fast connection.
In conclusion, the impact of active apps on VPN performance is significant and cannot be overlooked. By understanding how active apps affect VPN performance and taking steps to optimize resource usage, users can ensure a smoother and more reliable VPN experience.
Application behavior within VPN environment
In the realm of cybersecurity, understanding how applications behave within a Virtual Private Network (VPN) environment is paramount. A VPN creates a secure tunnel between a user's device and the internet, encrypting data and masking the user's IP address. However, this encryption and rerouting can impact the performance and behavior of applications in various ways.
One significant aspect of application behavior within a VPN environment is latency. Because VPNs route internet traffic through their servers, it can introduce delays in data transmission, leading to increased latency. This delay can affect real-time applications like video conferencing or online gaming, causing lag or buffering issues.
Moreover, VPNs may encounter compatibility issues with certain applications. Some applications rely on specific network configurations or protocols that may not work optimally within a VPN's encrypted tunnel. As a result, users may experience difficulties accessing or using these applications while connected to a VPN.
Additionally, the geographic location of the VPN server can influence application behavior. For example, accessing region-restricted content through a VPN server located in another country may impact streaming quality due to longer distances and potential network congestion.
Security concerns also play a significant role in application behavior within a VPN environment. While VPNs enhance security by encrypting data, some applications may bypass the VPN tunnel, exposing sensitive information to potential threats. Users must be vigilant and ensure that all applications are configured to route traffic through the VPN to maintain privacy and security.
In conclusion, while VPNs offer valuable security and privacy benefits, their usage can impact the behavior of applications in various ways, including latency issues, compatibility challenges, and security concerns. Understanding these dynamics is crucial for users to effectively navigate the complexities of the VPN environment.
0 notes
Text
Coinz Review: Transforms Any Device into a Cryptocurrency Generator!
What Is Coinz?
Coinz is a pioneering application that transforms any device into a platform for generating free Bitcoin and Ethereum effortlessly. It eliminates the need for investments, technical knowledge, or trading skills, allowing users to start accumulating cryptocurrency quickly and easily.
With Coinz, users can receive payments in over 100 altcoins with a simple click, leveraging the power of AI technology to exploit the crypto market and generate substantial profits without any upfront costs or risks.
The app's innovative Crypto Extraction Technology enables users to receive daily deposits of Bitcoin and Ethereum without the need to buy expensive mining equipment or engage in complex technical analysis.
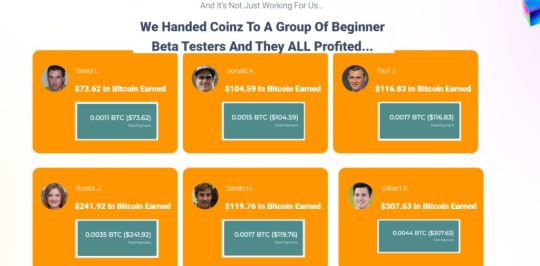
Coinz offers a risk-free solution to capitalize on the booming cryptocurrency market, empowering even total beginners to enjoy the benefits of free Bitcoin and Ethereum on autopilot.
>>>More Details Of Coinz<<<
Overview - Coinz :
Product – Coinz
Vendor – Jason Fulton
Front End Price – $16.95
Refund: 30 Days Money Back Guarantee
Niche: Cryptocurrency
operating System: Software
Bonus – Yes, Huge Bonus
How does Coinz operate?
It's a valid inquiry. Let me elucidate. Coinz harnesses a potent AI model that has long been overlooked. Why? Because it doesn't excel in providing satisfactory responses to human queries.
However, its forte lies in data processing. It boasts 84 times the power of ChatGPT, Bard, and Gemini combined. We exploit this formidable capability to deploy Coinz across a myriad of devices, be it mobile phones or antiquated laptops.
In exchange, it meticulously processes vast amounts of data for us, enabling the generation of Bitcoin at no cost. While akin to crypto mining in some respects, it diverges significantly in its approach.
>>>More Details Of Coinz<<<
Easy 3-Step Process with Coinz:
Step 1 - Log In:
Access Coinz online using any device with an internet connection. Whether it's a computer, smartphone, or tablet, Coinz works on any device with a web browser.
Step 2 - Activate:
Activate the "Crypto Extraction Technology" with a single click. This revolutionary technology allows you to start generating free Bitcoin and Ethereum without the need for mining or trading. There's zero risk involved, and you won't need to invest any money upfront.
Step 3 - Receive:
Sit back and enjoy as Coinz begins to generate daily deposits of Bitcoin and Ethereum directly into your wallet. You can sell these cryptocurrencies for real money whenever you want, giving you complete control over your earnings.
Key Features Of Coinz:
AI-Powered Processing: Utilize cutting-edge AI technology to maximize Bitcoin and Ethereum generation.
Zero Investment Needed: Unlike traditional methods, there's no requirement to invest any capital, not even $5.
No Expensive Mining Equipment: Avoid the hefty costs associated with purchasing and maintaining mining hardware.
No Technical Expertise Required: Users can participate without any prior experience or knowledge of technical analysis.
Over $68,659.80 in Free Cryptocurrency Distributed: Join a community where members have collectively received over $68,659.80 worth of free Bitcoin and Ethereum.
Risk-Free Operation: There's no trading involved, ensuring a 100% risk-free experience for participants.
Capitalization on Market Momentum: Take advantage of the current bullish trend in the cryptocurrency market, potentially maximizing returns.
Accessible to Beginners: Even individuals with minimal experience can start earning free Bitcoin and Ethereum effortlessly.
Autonomous Operation: Enjoy the benefits of earning free Bitcoin on autopilot, requiring minimal intervention from users.
30-Day Money Back Guarantee: Provide users with peace of mind by offering a 30-day money-back guarantee, eliminating any financial risk associated with participation.

Key benefits Of Coinz:
Beginner Friendly: Whether you're a seasoned pro or just starting out, Coinz provides all the tools needed to earn free cryptocurrency effortlessly.
Global Accessibility: With just a computer and internet connection, you can receive Bitcoin from anywhere in the world, whether you're in Kenya, India, the USA, the UK, Mexico, or beyond.
Easy Activation: Coinz activation is as simple as a few clicks, making it accessible to users of all ages, even a 10-year-old.
Receive Bitcoin & Ethereum: Tap into the booming cryptocurrency market and receive Bitcoin and Ethereum for free, opening up new opportunities.
No Expenses: Coinz comes with no hidden fees or expenses, eliminating the need for costly equipment or investments.
Zero Risk: There's no trading involved, and you can sell your cryptocurrency at any time for cash, ensuring a risk-free experience.
Works on Any Device: Coinz operates on any internet-connected device, including Windows, Mac, Android, iPhone, or tablets, providing flexibility and convenience.
>>>More Details Of Coinz<<<
#Coinz#CoinzApp#CoinzReview#CoinzWork#CoinzOverview#CoinzFeatures#CoinzOTO#Ethereum#Bitcoin#cryptocurrency
0 notes
Text
Unravelling the Evolution: A Journey Through the History of the Internet

Introduction: The internet, a ubiquitous part of our daily lives, has a rich history marked by innovation, collaboration, and transformation. From its humble beginnings as a military research project to its present-day status as a global communication network, the internet's evolution is a testament to human ingenuity and technological advancement.
Origins and Early Development: In the late 1960s, amidst the backdrop of the Cold War, the Advanced Research Projects Agency (ARPA) of the United States Department of Defense initiated a groundbreaking project known as ARPANET. This experimental network aimed to interconnect computers at various research institutions, laying the groundwork for what would become the modern internet. Spearheaded by visionaries such as Vint Cerf and Robert Kahn, ARPANET utilized pioneering technologies to facilitate communication and data exchange.
The First Internet Service Provider: The first Internet Service Provider (ISP) is generally considered to be The Whole Earth 'Lectronic Link (WELL), founded in 1985 by Stewart Brand and Larry Brilliant. Based in Sausalito, California, WELL provided dial-up access to the WELL community, offering email, forums, and online discussions. While WELL is often cited as the first ISP, it's worth noting that there were earlier online services such as CompuServe and The Source, which provided similar functionalities but were not solely dedicated to providing internet access.
Commercialization and Global Expansion: The 1990s witnessed a seismic shift as the internet transitioned from a research tool to a commercial platform. The advent of user-friendly web browsers like Mosaic and Netscape Navigator democratized access to the World Wide Web, opening new avenues for communication, commerce, and collaboration. Internet Service Providers (ISPs) emerged to provide connectivity to homes and businesses, fueling the rapid growth of the digital landscape.
The Dot-com Boom and Bust: Amidst the optimism of the late 1990s, the dot-com bubble emerged, characterized by frenzied speculation and exuberant investment in internet-based startups. Companies rushed to capitalize on the burgeoning digital economy, leading to inflated valuations and unprecedented growth. However, the euphoria proved short-lived, and the bubble burst in the early 2000s, resulting in widespread financial turmoil and the collapse of many dot-com ventures.
Social Media and Web 2.0: The mid-2000s ushered in a new era of interactivity and user-generated content with the rise of social media platforms and Web 2.0 technologies. Platforms such as Facebook, YouTube, and Twitter revolutionized how people connect, share information, and engage with online communities. The internet evolved from a static repository of information to a dynamic ecosystem where users actively participate in content creation and dissemination.
Mobile Revolution and Internet of Things (IoT): In recent years, the proliferation of smartphones and mobile devices has fueled the expansion of the internet into every aspect of daily life. The mobile revolution has enabled ubiquitous access to online services, transforming how individuals communicate, work, and consume media. Furthermore, the Internet of Things (IoT) has emerged as a paradigm shift, connecting everyday objects to the internet and enabling unprecedented levels of automation and connectivity.
Challenges and Future Prospects: Despite its remarkable achievements, the internet faces a myriad of challenges, including cybersecurity threats, privacy concerns, and digital inequality. As we navigate the complexities of the digital age, stakeholders must collaborate to address these issues and ensure that the internet remains a force for good. Looking ahead, emerging technologies such as 5G networks, artificial intelligence, and blockchain hold the promise of reshaping the internet landscape and unlocking new possibilities for innovation and progress.
Conclusion: The history of the internet is a testament to human innovation and resilience. From its origins as a fledgling research project to its present-day ubiquity, the internet has transformed the way we live, work, and interact with the world around us. As we embark on the next chapter of this remarkable journey, let us strive to harness the power of technology for the betterment of society and the advancement of humanity.
Read the full article
0 notes
Text
Title: Seedr: Revolutionizing File Management and Sharing
In today's digital age, managing and sharing files efficiently is crucial for individuals and businesses alike. With the vast amount of data generated daily, having a reliable and secure platform for file storage and sharing is essential. One such platform that has been making waves in this space is Seedr. In this blog post, we'll explore how Seedr helps users streamline their file management and sharing tasks.
What is Seedr?
Seedr is a cloud-based platform that offers a unique solution for storing, managing, and sharing files online. Unlike traditional file storage services, Seedr operates entirely in the cloud, allowing users to access their files from anywhere with an internet connection. The platform is known for its simplicity, speed, and security features, making it a popular choice among individuals and businesses worldwide.
Simplified File Management
One of the key benefits of using Seedr is its simplified file management system. Users can easily upload files to their Seedr account, organize them into folders, and manage their files with just a few clicks. This streamlined process saves time and effort, especially for users dealing with large volumes of data on a regular basis.
Fast and Reliable Downloads
Seedr also stands out for its fast and reliable download speeds. Whether you're downloading a single file or a batch of files, Seedr ensures swift and seamless downloads, thanks to its robust infrastructure and optimized protocols. This speed and reliability are crucial for users who depend on quick access to their files for work or personal use.
Secure File Sharing
In addition to file storage and management, Seedr offers secure file sharing capabilities. Users can easily share files and folders with colleagues, clients, or friends via email or link sharing. Seedr employs encryption and other security measures to protect shared files, ensuring that sensitive information remains safe and confidential.
Cross-Platform Accessibility
Another advantage of Seedr is its cross-platform accessibility. Whether you're using a computer, smartphone, or tablet, you can access your Seedr account and files from any device with an internet browser. This flexibility allows users to stay productive and connected on the go, without being tied to a specific device or location.
Privacy and Anonymity
Seedr prioritizes user privacy and anonymity, making it an ideal choice for those who value data security. The platform does not require users to provide personal information during signup, and it employs encryption to safeguard user data from unauthorized access. This commitment to privacy sets Seedr apart from other file management platforms.
Conclusion
In conclusion, Seedr is a game-changer in the world of file management and sharing. Its user-friendly interface, fast download speeds, secure sharing options, cross-platform accessibility, and focus on privacy make it a top choice for individuals and businesses alike. Whether you're a freelancer, student, entrepreneur, or corporate professional, Seedr can help streamline your file-related tasks and enhance your productivity. Give Seedr a try today and experience the future of file management!
https://www.seedr.cc/
1 note
·
View note
Text
How to Earn $50 Per Day on Amazon Mechanical Turk

Amazon Mechanical Turk (MTurk) is a crowdsourcing marketplace that enables individuals and businesses to outsource tasks to a distributed workforce, known as "Workers," to perform tasks that computers cannot easily do. Tasks, known as Human Intelligence Tasks (HITs), can include data processing, image labeling, transcription, and more. Workers can browse available HITs, complete them, and receive compensation for their work. MTurk is often used for tasks that require human judgment or intelligence and is widely used for research, data validation, and content moderation, among other purposes.
Types of Work
Amazon Mechanical Turk (MTurk) offers a wide variety of tasks, known as Human Intelligence Tasks (HITs), that workers can complete for compensation. Here is a list of common types of HITs found on MTurk:
1. Surveys: Completing surveys for academic research, market analysis, or customer feedback.
2. Data Entry: Entering data from one source into another, such as transcribing receipts or copying text from images.
3. Transcription: Listening to audio recordings and typing out the spoken content, such as transcribing interviews or podcasts.
4. Content Moderation: Reviewing user-generated content, such as images or comments, to ensure it meets a platform's guidelines.
5. Image Tagging: Adding descriptive tags to images to improve searchability and categorization.
6. Categorization: Sorting data or content into predefined categories.
7. Writing: Writing short articles, product descriptions, or reviews.
8. Research Tasks: Finding information online, such as identifying company contact details or researching product specifications.
9. Data Analysis: Analyzing data sets and providing summaries or insights.
10. Content Creation: Creating graphics, videos, or other digital content.
These are just a few examples, and the types of tasks available on MTurk can vary widely depending on the needs of Requesters (those who post tasks) and current market demands.

1. Focus on High-Paying Tasks: While it's tempting to complete as many HITs as possible, focusing on high-paying tasks can significantly increase your earnings on Amazon Mechanical Turk (MTurk). Tasks like surveys, transcription, and data analysis often pay better than simpler tasks. Look for HITs that offer a higher pay rate per task and prioritize these to maximize your earning potential.
2. Use Scripts and Tools: Utilizing browser extensions and scripts can help you work more efficiently on MTurk. The Bzturk Chrome extension, for example, can assist you in finding and completing HITs more efficiently. Additionally, tools like Turkopticon can help you identify Requesters with a good reputation, ensuring that you are working for reliable and fair employers.
3. Work During Peak Hours: Working during peak hours, such as during the day on weekdays, can increase your chances of finding lucrative tasks. Requesters often post more HITs during these times, giving you more opportunities to earn money. Keep an eye on the availability of HITs and try to schedule your work hours accordingly to maximize your earnings potential,By using the "bzturk" extension to identify peak hours, you can optimize your work schedule and maximize your earnings on Amazon Mechanical Turk.
4. Diversify Your Tasks: While focusing on high-paying tasks is important, it's also beneficial to diversify your tasks to find what works best for you. Trying different types of HITs can help you identify tasks that are more profitable or enjoyable for you to complete. Experimenting with different tasks can also help you discover new opportunities to earn money on MTurk.
5. Set Realistic Goals: Setting a daily earnings goal of $50 per day is a great way to stay motivated and focused on MTurk. Break down your goal into smaller, achievable targets to track your progress and celebrate your achievements. Setting realistic goals can help you stay motivated and maintain a positive attitude towards your work on MTurk.
6. Stay Active and Consistent: Consistency is key to success on MTurk. Regularly checking for new HITs and working consistently can help you maintain a steady income stream. The more active and consistent you are, the more opportunities you'll have to earn money on MTurk.
7. Build Relationships with Requesters: Building relationships with Requesters can lead to more work opportunities and potentially higher earnings. Some Requesters offer bonuses or prefer to assign tasks to Workers they trust. By providing high-quality work and communicating effectively, you can build a good reputation and increase your chances of securing more work from these Requesters.
8. Utilize Qualifications: Some HITs on MTurk require specific qualifications. Working on obtaining these qualifications can open up higher-paying tasks and increase your earning potential. Keep an eye out for qualification opportunities and complete any necessary tests to improve your qualifications and access more lucrative HITs.
9. Keep Track of Your Earnings: Tracking your earnings is essential to monitor your progress and identify areas where you can improve. Use a spreadsheet or other tracking method to record your earnings, the tasks you've completed, and any feedback you've received. Analyzing this data can help you identify patterns, optimize your workflow, and increase your overall earnings on MTurk.
By following these tips and strategies, you can maximize your earnings on How to Earn $50 per day on Amazon Mechanical Turk (MTurk)or more.
Here is a sample FAQ for Amazon Mechanical Turk (MTurk):
Frequently Asked Questions (FAQ) About Amazon Mechanical Turk (MTurk)
1. What is Amazon Mechanical Turk (MTurk)?
- MTurk is a crowdsourcing platform by Amazon that enables businesses to outsource tasks to a distributed workforce (known as Workers) to perform tasks that computers cannot easily do.
2. How does MTurk work for Workers?
- Workers browse available tasks (HITs) posted by Requesters, complete them, and receive compensation. Tasks can include surveys, data entry, content moderation, and more.
3. How do I get started as a Worker on MTurk?
- Visit the MTurk website and sign up as a Worker. You will need an Amazon account to get started.
4. How much can I earn on MTurk?
- Earnings on MTurk vary depending on factors such as the types of tasks completed and the time invested. Some Workers earn a few dollars per day, while others earn more substantial amounts by completing higher-paying tasks.
5. How do I withdraw earnings from MTurk?
To withdraw earnings from MTurk, workers can transfer funds to an Amazon Payments account or opt for an Amazon.com gift card balance. Bank account withdrawals are available in select regions. Here's a guide to easily earning $50 per day on Amazon MTurk:
Updated for 2024.
0 notes
Text
<h1>Revolutionizing Engagement: Amazon Enters TV, Reddit Redefines Ads, and Chrome Elevates Web Standards</h1>
Today's Marketing News Summary - March 14, 2024
In today's roundup of significant marketing shifts and digital advancements, we observe key players like Amazon and Reddit revamping their advertising strategies, while Google Chrome introduces a new metric to enhance web user experience. Here's a brief overview of what's new:
Amazon Launches Sponsored TV Ads
Expanding Advertising Horizons
Amazon takes a bold step into televised advertising with the introduction of Sponsored TV Ads, aiming to blend e-commerce with traditional TV viewing experiences. A move anticipated to reshape how brands engage with broader audiences. Read more about Amazon's initiative.
Reddit Ads Mimic User Posts, Shifts Strategy
Stealthy Advertisement Approach
Reddit is shifting its advertising strategy to make sponsored posts indistinguishable from user-generated content. This novel approach aims to offer a less intrusive advertising experience, potentially changing the dynamics of online community engagement. Discover more about Reddit's strategy evolution.
Amazon's Ad Sales for Unavailable Products
A Controversial Advertising Tactic
In a controversial move, Amazon has started selling ads for products that are currently unavailable. This practice has sparked debate over its impact on consumer trust and the overall shopping experience. Learn more about the implications.
Chrome's INP to Become New Core Web Vital
Enhancing Web User Experience
Google's Chrome browser is set to introduce Interaction to Next Paint (INP) as a new Core Web Vital, prioritizing user experience by measuring interactivity and responsiveness of web pages. This change underscores the importance of a smooth and engaging user experience. Read more about INP's role in web performance.
Stay tuned for more daily updates on the evolving marketing landscape.
0 notes