#cybersecuritytips
Text
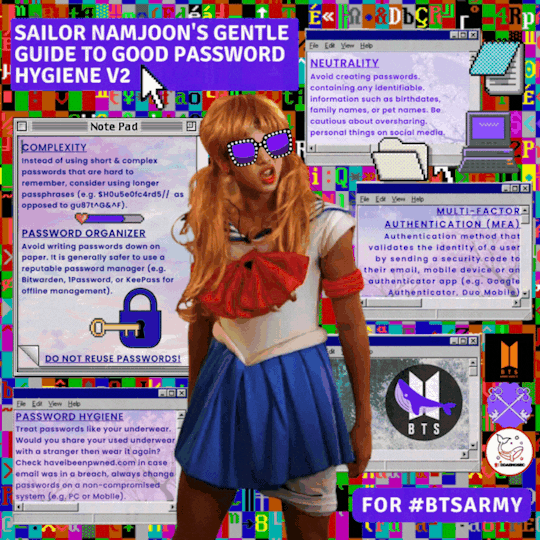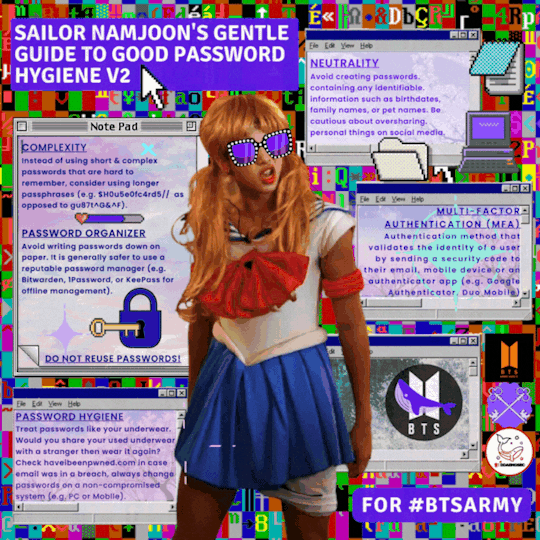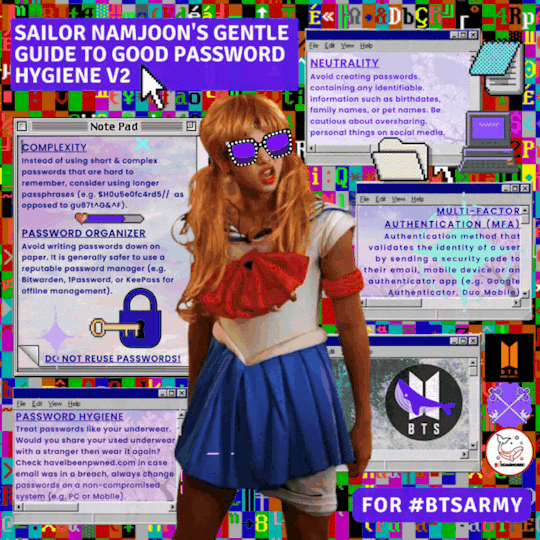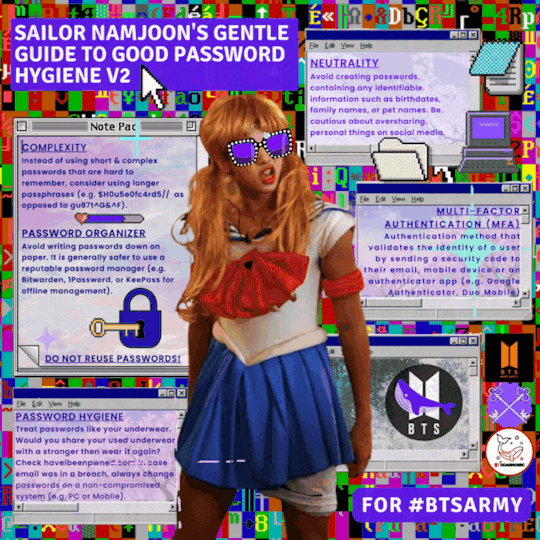

Contributors
ddaengsec
btsarmysafety
ArmyCompSci
#bts#btsarmy#bts army#bts rm#passwords#infosec#information security#cybersecurity#hacking#cybersecurity awareness#cybersecuritytips#security awareness#security education#bts fanart#cybersecurity tips#lastpass#1password#privacy#internet#digital privacy
9 notes
·
View notes
Text

The security🔐 of our gadgets is currently the most important concern, and it cannot be disregarded under any circumstances. Because we rely so much on computers and 🧑💻💻laptops, we find it impossible to envision life without them. Let's keep them secure.
𝗛𝗮𝗽𝗽𝘆 𝗖𝗼𝗺𝗽𝘂𝘁𝗲𝗿 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗗𝗮𝘆!💾💽🌐
#ComputerSecurity#nationalcomputersecurityday#ComputerSecurityDay2022#CyberSecurity#cybersecuritytips#passwordsecurity#datasecurity#ComputerSecurityDay#cyberattacks#ComputerSecurityDayawareness#RaysTechServ
2 notes
·
View notes
Text
15 Important Things to Keep in Mind When Choosing Cybersecurity Services Companies
0 notes
Text
Unlock Fort Knox for Your Laptop: The Definitive Guide to Bulletproof Security

What steps can I take to enhance my laptop's security?
Dive into my latest Blog post and discover the ultimate secrets to fortifying your laptop's defenses! Transform your device into a digital fortress and safeguard your data like never before.
From foolproof password strategies to state-of-the-art encryption techniques, explore a treasure trove of tips and tricks to keep hackers at bay. Say goodbye to cyber worries and hello to peace of mind!
Ready to take control of your laptop's security? Arm yourself with knowledge now!
Read the full post and become the guardian of your digital domain. #LaptopFortress #SecureYourData #ReadMore
#LaptopSecurity#DataProtection#CybersecurityTips#Laptop security#Data protection#Cybersecurity tips#Digital privacy#Encryption#Password management#Cyber threats#Data security measures#Online safety#Tech security#Information security#Secure computing#IT security#Protecting sensitive data#Internet safety
1 note
·
View note
Text

🚨Alarmstufe Rot: Die neue WhatsApp-Falle – So schützen Sie sich vor dreisten Behörden-Betrügern!🚨
Ok, Leute, schnallt euch an, es wird haarig. Stellt euch vor, ihr checkt eure Nachrichten und – zack – da ist sie: Eine Nachricht, die aussieht, als würde sie von der Polizei kommen. Aber halt! Es ist die neueste Masche skrupelloser Betrüger, und sie zielt genau auf diejenigen ab, die schon mal auf einen Betrug hereingefallen sind. Das Landeskriminalamt Niedersachsen läutet die Alarmglocken und ich kläre euch auf, worauf ihr achten müsst.

Es könnte eine Versprechung sein, verlorenes Geld zurückzubekommen, oder eine dringende Warnung, die eure persönlichen Daten fordert. Die Nachrichten sehen täuschend echt aus, mit echten Namen und genauen Details zu früheren Betrugsfällen. Aber lasst euch nicht täuschen: Die echte Polizei würde niemals per WhatsApp an euer Portemonnaie wollen!
Das LKA Niedersachsen sagt klar: Gebt keine Daten raus und überweist kein Geld. Wenn ihr so eine dubiose Nachricht bekommt, geht direkt zur Polizei. Für diejenigen unter euch, die bereits in die Falle getappt sind: Kontaktiert umgehend eure Bank und macht eine Anzeige.
Aber wartet, es gibt noch mehr: Ihr könnt selbst zum Detektiv werden und checken, ob eure Daten schon durchs Netz geistern. Tools wie der „🔎HPI Identity Leak Checker🔍“ oder „🔎Have i been pwned🔍“ sind eure besten Freunde dabei. Ihr könnt dort sehen, ob eure E-Mail oder Handynummer schon irgendwo im Internet auftaucht.

Quelle
Bleibt wachsam, meine Community, und lasst euch nicht von diesen digitalen Gaunern über den Tisch ziehen!
#WhatsAppWarnung#callcentermaschen#Betrugsmasche#SchutzVorBetrug#CyberSecurityTips#Datenschutz#PolizeiInfo#LKAUpdate#VorsichtImNetz#CommunityAlert
1 note
·
View note
Text
Ready to Take Charge of Your Inbox? How to Stop Unsolicited Messages and Reclaim Your Digital Space!
It’s not uncommon to find our inboxes flooded with unsolicited emails, messages, and communication from unknown sources. Whether it’s spam emails, promotional messages, or random friend requests, dealing with unsolicited correspondence can be both annoying and time-consuming.
In this blog post, we’ll explore effective strategies to reclaim control over your communication channels and put an end…

View On WordPress
#CyberAware#CyberSecurityTips#dataprotection#DigitalHygiene#DigitalPrivacy#DigitalWellness#EmailEtiquette#EmailManagement#InboxControl#InternetSecurity#OnlineSafety#OnlineSecurity#PrivacyAware#PrivacyMatters#SafeOnline#SecureCommunication#SecureMessaging#SpamFreeLife#StayProtected#TechSafety#mailbox
0 notes
Link
https://bit.ly/3REwoJG - 🔐 Zero-click attacks, requiring no user interaction, are increasingly becoming a significant cybersecurity threat. These attacks exploit vulnerabilities in messaging, SMS, and email applications, allowing threat actors to install malware such as spyware or stalkerware. This stealthy nature makes it challenging to track and stop malicious activities. #ZeroClickAttacks #CybersecurityThreats 📱 In 2019, WhatsApp was vulnerable to a zero-click attack through a missed call, demonstrating the ease with which these attacks can compromise devices. Companies are now prioritizing defense against such attacks. For instance, Samsung's Message Guard and Apple’s BlastDoor are designed to sandbox and scrutinize incoming data, reducing the risks of zero-click attacks. #WhatsAppVulnerability #MobileSecurity 🛡️ Despite advancements in anti-zero-click solutions, users must remain vigilant. Vulnerabilities can still be exploited, especially in devices with outdated software. Regular updates, using phones from brands known for security updates, and sticking to official app stores are crucial practices for protection. #DeviceSafety #CyberHygiene 📊 Basic cybersecurity tips remain essential to prevent zero-click attacks. Keeping devices and apps updated, using mobile antivirus solutions, and practicing good cybersecurity hygiene are key strategies. Regular backups can also aid in data recovery if a reset is needed. #CybersecurityTips #MobileProtection In summary, zero-click attacks present a growing challenge in mobile security, requiring both advanced technological solutions and diligent cybersecurity practices from users.
#ZeroClickAttacks#CybersecurityThreats#WhatsAppVulnerability#MobileSecurity#DeviceSafety#CyberHygiene#CybersecurityTips#MobileProtection#ZeroClickCybersecurity#DigitalSafety
0 notes
Text
Tips for Secure Code Review | CybersecurityTv
youtube
🔐 Unlock the secrets of secure code with our latest video on CybersecurityTv! 🚀 Dive deep into the world of code review and discover essential tips to fortify your applications against cyber threats. 💻 Don't miss out on this must-watch guide for developers, security enthusiasts, and anyone passionate about safeguarding digital landscapes.
#SecureCodeReview#CybersecurityTips#CodeSecurity#DeveloperLife#TechSafety#InfoSecInsights#HackProofCode#CodeReviewBestPractices#CyberAware#DigitalDefense#LearnToProtect#Youtube
0 notes
Text
#artificial intelligence#machine learning#software engineering#programming#python#coding#linux#ETHICALHACKINTOOLS#cybersecuritytips#marketing
1 note
·
View note
Text
बैंक स्टेटमेंट सर्च के दौरान आपकी व्यक्तिगत जानकारी की सुरक्षा
ऑनलाइन स्कैम किसी भी समय, किसी भी तरीके से, और किसी के साथ भी हो सकता है। बैंक से संबंधित सर्च को गूगल पर करना इतना खतरनाक हो गया है कि ठगी होने की संभावना 100 फीसदी है। ताजा मामला पुणे का है, जहां एक महिला ने बैंक स्टेटमेंट के लिए गूगल पर सर्च किया था, जिसके बाद उसके खाते से 11 लाख रुपये निकल गए।
#BankStatementSecurity#ProtectYourInfo#SecureBanking#PrivacyMatters#OnlineSafety#DataProtection#GuardYourInfo#SafeBankingPractices#CyberSecurityTips#StaySecureOnline
0 notes
Text

Is Your Money at Risk? Safeguard Your Global Finances with Secure Online International Money Transfers
Sending money internationally online is a convenient and efficient way to transfer funds, but it's essential to ensure that the process is safe and secure. This guide will give you a full rundown of the safety and security measures for sending money online and tips for keeping yourself safe from fraud. We will also include some facts and data better to understand the current state of online money transfers.
What are The Security Measures for Money Transfers?
First, let's talk about the security measures for online money transfers. Most banks and money transfer companies use encryption technology to protect their customers' personal and financial information. This technology ensures that the data is scrambled and can only be decrypted by authorized parties. A study by the Aite Group, a financial services research and advisory firm, found that 80% of consumers think encryption is the most crucial online transaction security feature. Additionally, many of these institutions also use multi-factor authentication, which requires customers to provide multiple forms of identification before they can access their accounts.
Another essential safety measure is using secure servers to store customer information. Many banks and money transfer companies use servers located in safe, off-site locations and protected by firewalls and other security measures. This ensures that customer information is protected from unauthorized access or hacking attempts. A study by the Ponemon Institute, a research firm focusing on data protection, found that a data breach costs a company an average of $3.86 million. This shows how important it is to keep customer information safe.
#OnlineMoneyTransfers#InternationalTransfers#MoneyTransferSafetyMeasures#CybersecurityTips#SecureTransactions#FraudPrevention#PaymentSecurity
0 notes
Text
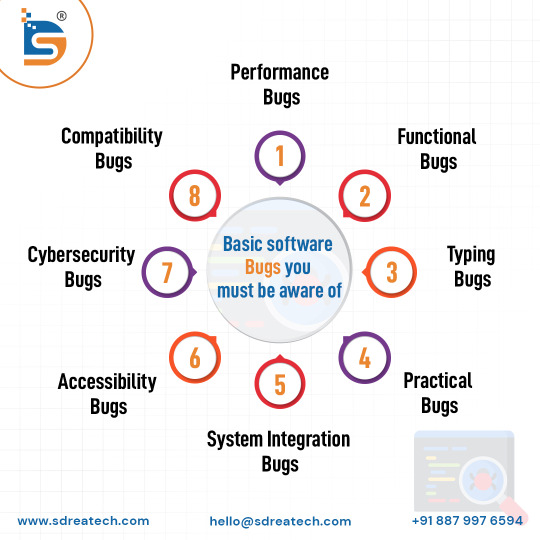
Basic software bugs you must be aware of
1. Performance Bugs
2. Functional Bugs
3. Typing Bugs
4. Practical Bugs
5. System Integrating Bugs
6. Accessibility Bugs
7. Cybersecurity Bugs
8. Compatibility Bugs
#bugfixes#bug#ios#software#programming#bugs#webdesign#debugging#tech#developing#mobileappdevelopment#cybersecuritytips#sdreatech
1 note
·
View note
Link
https://bit.ly/3G3uHPj - 🚨 The FBI has issued warnings about ongoing email scams exploiting the Gaza conflict, tricking people into donating cryptocurrencies to fake charities. Cybercriminals and sometimes terrorist organizations are using emails, social media, cold calls, and crowdfunding websites, posing as fundraisers for Palestinian or Israeli victims. This sophisticated scamming method has already led to significant financial losses, with one report tracing $1.6 million in crypto to these fraudulent accounts. #FBICyberWarning #GazaEmailScams #CryptoScams 💻 Cybersecurity experts explain that these scams are effective because they play on human emotions, using tactics like spoofed email domains and emotional, urgent language. The scammers often request donations in cryptocurrencies, which are harder to trace and allow them to avoid detection by traditional email security filters. Links in the emails are used to lend credibility, often pointing to legitimate news sources or organizations. #CyberFraudTactics #EmailScams #SecurityAwareness ⚠️ The danger of these scams is further compounded by the use of crypto wallet drainers, which can empty a victim's crypto wallet completely, turning small donations into significant financial losses. This tactic has been instrumental in the high amount of money lost to these scams, which is likely even higher than reported figures. #CryptoWalletDrainers #FinancialLoss #CyberSecurityTips 🛡️ To combat these scams, experts recommend using behavioral AI-enabled spam filters and exercising common sense. Donating through reputable organizations' official websites or known contacts is advised over responding to unsolicited emails.
#FBICyberWarning#GazaEmailScams#CryptoScams#CyberFraudTactics#EmailScams#SecurityAwareness#CryptoWalletDrainers#FinancialLoss#CyberSecurityTips#AIinCybersecurity#SafeDonations#OnlineScamPrevention
0 notes