#phone hacking
Text

Hell yeah! Had an awesome find at a thrift shop today - A 1929 Southwestern Bell Telephone technical manual and installation guide for phones of the era.

Maybe you're asking why I think this is awesome? Haha. That makes sense - Well, first of all, I -live- vintage stuff. Antiques, old books, weird ephemera of the past. This definitely fits in with all of that, and has a gorgeous, punched leather cover with the gold stamping. Such a slick piece of history.

Second, I'm an old computer nerd cat. Back in the early '90s, I was a phone phreak - a phone hacker back before mobile phones and even alphanumeric pagers were a thing. It was in these days that "Ma Bell" (Southwestern Bell) was a big Queen on the scene, in her prime.

What were common phreaker practices back in the day? Well, it was all about exploration and curiosity. We would wardial (using our home landline connections and modems to dial a huge list of numbers in a row to try and find systems on the other end rather than regular phones - I'd leave it on all day and come back with a shorter list of various systems to dial in and play around on), we would build blue (and other color) boxes from RadioShack parts to use payphones to make free calls and do all sorts of rad tricks, we would prank folks that deserved it or use said tricks to disrupt schools and business, we would navigate voicemail systems and change automatic messages, and we would generate credit card numbers (which was incredibly easy back in the day) to make free calls to our first girlfriends in Canada. Well, that last one was mostly a me thing, haha.

Basically, payphones and early phone systems were a wonderful, incredible playground for me and I have SO many fond memories of these times. To have a book like this in my hands feels like I just looked inside the Ark of the Covenant and instead of melting my face off, it just glowed real bright and whistled a 2600hz tone sweetly into my ears.

This has so many cool photos like the ones above, and lots of radical technical diagrams, too.
As a bonus, there are hand-typed notes from a division head telephone engineer that wrote about systems they were building in Galveston, TX in the '60s:

Anyways, this is such a cool relic and I'll probably not be able to bring myself to sell it.
Did you know I wrote a verse about being a phreaker for a song with Nerdcore legend YTCracker wayyyyyy back in 2010? Well, now you do. You can hear that here (I'm the second dude, of course):
#phone phreak#phreak#phreaker#hacker#hackers#southwestern bell#ma bell#phone hacking#hacking#old books#vibtage books#antique books#treasure#thrift store finds#antiques#leatherwork#nerecore#madhatter#ytcracker
330 notes
·
View notes
Text
💥 The Duke of Sussex, Sir Elton John and Baroness Doreen Lawrence can continue their unlawful information gathering claims against the publisher of the Daily Mail, after it lost a bid to have the cases thrown out at the High Court 💥
39 notes
·
View notes
Text


Prince Harry's uncle, Charles Spencer, shows his support for Harry's case. Charles Spencer, brother of Princess Diana, shared former Labour adviser Alistair Campbell's tweets about the case via Twitter & Instagram.
One of the tweets was about the dangers of reading about Harry's case via UK media sources, which clearly have an agenda against Prince Harry.
#prince harry#the duke of sussex#duke of sussex#brf#british royals#the british monarchy#british tabloids#british royal family#uk royals#uk royal family#uk tabloids#phone hacking#harry and meghan#charles spencer#princess diana#diana spencer#toxic media
83 notes
·
View notes
Text


96 notes
·
View notes
Text
Go Harry!

15 notes
·
View notes
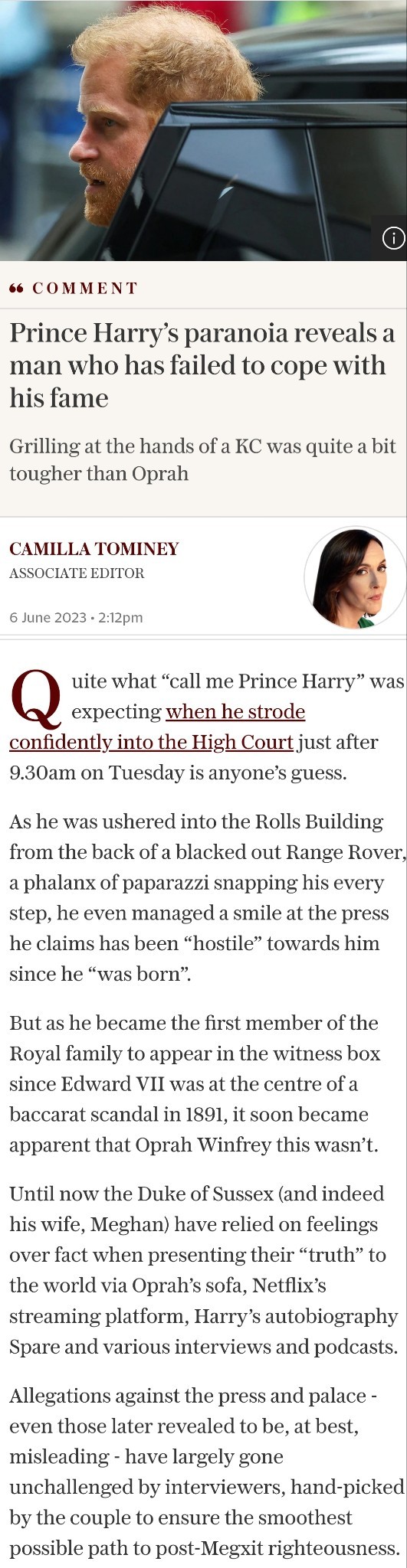
Text
Fuck a doodle do.
In a statement, Prince Harry said the ruling was "vindicating and affirming" and took aim at senior executives and editors including Piers Morgan - who was in charge at the Daily Mirror from 1995 to 2004.
Judge Mr Justice Fancourt found Morgan knew about phone hacking at the paper.
He said the Duke's phone was probably only hacked to a modest extent and was "carefully controlled by certain people" from the end of 2003 to April 2009.
Jesus -- this is.... unbelievable.
When asked what he thought the way forward was, he said to scrap the current press regulator, the Independent Press Standards Organisation, which he likened to a "poodle".
"You have to get independent regulation as Leveson called for, which we haven't got because, there's a self regulator poodle, not a watchdog," he said.
"You also need to have the Leveson Inquiry restarted or completed... which the government cancelled at the request of those being investigated."
The Tory government should hang its head in shame. I mean -- it won't, but seriously -- this is appalling.
The government has failed to find the courage to hold the press accountable, a media lawyer has said.
Jonathan Coad said that despite Prince Harry's victory, only politicians can bring about real change.
However, it has never ensured the press regulated itself according to the principles set out in the Leveson Inquiry, he said.
"If you're going to be accountable, someone has got to have the courage to hold you accountable," he told Sky News.
"Harry has fought the battle and said it needs to change, but it is only going to change if politicians have the courage to take on Fleet Street.
"At the moment, they have shown a complete lack of intention of doing so.
What was the Leveson Inquiry and why is it relevant?
In 2011, Judge Sir Brian Leveson led a public inquiry after it was revealed News Of The World journalists had hacked the phone of murdered school girl Milly Dowler.
Initially intended to be carried out in two sections, the first part of the inquiry looked at the culture, practices and ethics of the press. It involved celebrities including Hugh Grant, Sienna Miller, Steve Coogan and Charlotte Church.
Part two of the Leveson Inquiry was meant to investigate the relationship between journalists and the police, but never took place. There have since been calls to re-open it.
#phone hacking#hacked off#fleet street#daily mirror#mirror group#piers morgan#prince harry#gentlemen of the press#leveson inquiry
19 notes
·
View notes
Text
11 notes
·
View notes
Text
Can Someone Hack Your Phone and Listen to Your Calls?

In today's digital era, where smartphones are essential for communication, concerns about phone security and privacy are more relevant than ever. The question often arises: can someone hack your phone and listen to your calls? In this article, we'll delve into the intricacies of phone hacking, explore the possibilities of call interception, and provide practical steps to safeguard your private conversations.
Understanding Phone Hacking
Phone hacking encompasses unauthorized access to a mobile device's data and functionalities. While hacking methods vary, the potential risk of call interception is a significant concern. Hackers who gain access to your device could potentially eavesdrop on your conversations, breaching your privacy and security.
Methods of Phone Hacking
Hackers employ an array of techniques to infiltrate devices, including exploiting vulnerabilities in operating systems and using malicious apps. The unsettling prospect of call hacking involves intercepting and listening to phone conversations, often without the victim's knowledge or consent.
VoIP Vulnerabilities
Voice over Internet Protocol (VoIP) technology, which allows voice calls over the internet, has become commonplace. However, this technology isn't immune to vulnerabilities. If hackers exploit weaknesses in VoIP, they might gain unauthorized access to calls, bypassing traditional cellular networks.
Eavesdropping on Calls
One alarming facet of phone hacking is call eavesdropping. By exploiting security gaps, hackers can gain access to live phone conversations, potentially compromising sensitive information. Instances of call interception highlight the urgency of taking protective measures.
Security Flaws in Mobile Networks
Mobile networks, while advanced, can still harbor security flaws. Hackers with the right skills can exploit these vulnerabilities to intercept calls. This underscores the need for robust security protocols to prevent unauthorized access.
Operating System Vulnerabilities
Outdated operating systems pose a considerable risk. When users fail to update their OS, they leave their devices susceptible to attacks. Security patches play a crucial role in preventing hacking attempts that could compromise calls.
Risks of Third-Party Apps
Third-party apps, particularly those without proper security measures, can serve as gateways for hackers. Malicious apps might infiltrate your device, granting unauthorized access to your calls and conversations.
Securing Your Phone
Protecting your phone is paramount in the digital age. Creating strong, unique passwords, regularly updating your device's software, and reviewing app permissions can significantly enhance your phone's security.
End-to-End Encryption
End-to-end encryption is a robust security measure that ensures the content of your calls remains confidential. This encryption method prevents unauthorized parties, including hackers, from deciphering your conversations.
Using Encrypted Communication Apps
Consider using encrypted messaging and calling apps to fortify your communication. Apps like Signal, WhatsApp, and Telegram offer end-to-end encryption, providing an extra layer of protection for your calls.
Network Security Measures
Secure network connections are essential. Utilizing Virtual Private Networks (VPNs) can add a layer of encryption to your internet traffic, safeguarding your calls from potential eavesdropping.
Recognizing Suspicious Activity
Being vigilant about unusual activity on your device is crucial. If you notice unexpected behavior, such as rapid battery drain or unfamiliar apps, it might indicate a breach. Promptly address such issues to protect your calls and data.
Expert Insights
According to cybersecurity experts, the risk of call hacking underscores the importance of proactive measures. Dr. Sarah Miller, a renowned cybersecurity analyst, emphasizes, "Users must prioritize device security, keep software up to date, and employ encryption technologies."
Balancing Convenience and Security
Striking a balance between convenience and security is essential. While security measures might seem inconvenient at times, safeguarding your privacy and protecting your calls from potential interception is worth the effort.
Conclusion
In a world where connectivity is integral to our lives, the possibility of someone hacking your phone and listening to your calls is a legitimate concern. By understanding the methods hackers use, employing robust security practices, and embracing encryption technologies, you can significantly reduce the risk of call interception. Remember, safeguarding your privacy requires ongoing vigilance and proactive action.
Frequently Asked Questions
Can hackers really listen to my phone calls?
While it's possible for skilled hackers to intercept calls, taking security measures like encryption and using secure apps can greatly mitigate this risk.
How do hackers intercept phone calls?
Hackers exploit vulnerabilities in mobile networks, operating systems, or apps to gain unauthorized access to calls.
What is end-to-end encryption, and how does it protect calls?
End-to-end encryption ensures that only the sender and recipient can access the call content, preventing interception by hackers.
Are encrypted communication apps safe for calls?
Yes, encrypted apps like Signal and WhatsApp offer strong security measures, making them safe choices for private calls.
What should I do if I suspect my calls are being intercepted?
If you suspect call interception, immediately review your device for unusual activity, update your security settings, and consider seeking professional assistance to secure your phone.
#phone hacking tools#phone hacking#find a hacker#contact a hacker#finding a hacker#phone hacking service#cybersecurity#ethical hacking
3 notes
·
View notes
Text
Phreakers Part 3: VMB Drop Box, Various short drops (Plus some sid music)
Back in the late 80s and early 90s people were using stolen voice mail boxes at various companies as drops for various hacking/phreaking info. I remember looking for access to the old X25 network and trading in network access on said X25 network was very much on peoples desires back then. This was before widespread email so people communicated as they could. Since most phone calls cost money outside of a few miles people would take over voice mail boxes at companies with toll free numbers to trade in accounts, long distance calling cards various interesting phone system oddities like bridge lines and other voice mail boxes you would hop to. That is how you stayed in the scene by calling these numbers a lot to keep in this underground voice phone network.
Here is an example of some of these voice mail drops from around early 1990.
The screen visuals are a video recording from a sysop side of a C64 BBS running a VERY modified version of CNet.
10 notes
·
View notes
Text
Coming home after the BAFTAs, Mandip, Bradley and Tosin make the alarming discovery that their phones have been hacked by the Daily Mail.

#doctor who#thirteenth doctor#spyfall#graham o'brien#mandip gill#tosin cole#ryan sinclair#bradley walsh#yasmin khan#daily mail#phone hacking#doctor who series 12
6 notes
·
View notes
Text
Judge rules 15 of the 33 articles were obtained by Unlawful Information Gathering by Mirror Group Newspapers from 2006 to 2011. He’s awarded £140,600 in damages.
#i'm aware i'm basically never here anymore sorry about that#but a win for h today ig#prince harry#duke of sussex#phone hacking#this is and always will be bigger than harry folks
29 notes
·
View notes
Text


Charles Spencer calling out Amanda Platell was not on my bingo card today
#prince harry#the duke of sussex#duke of sussex#brf#british royals#the british monarchy#british tabloids#british royal family#uk royals#uk royal family#uk tabloids#phone hacking#harry and meghan#charles spencer#princess diana#diana spencer#toxic media
70 notes
·
View notes
Link
Lessons in British libel law:
Grant had said he had wanted to fight the case and go to trial, where the Sun’s top executives could be called to give evidence. But he has concluded he cannot afford to turn down the payout from the Rupert Murdoch-owned newspaper, which he will be donating to press regulation charities.
This is because of a quirk in the way the English legal system encourages both sides to settle cases before trial or risk financial oblivion owing to the legal costs involved.
It all hinges on a technical piece of civil law procedure known as a “Part 36 offer”.
The Sun has used this provision to offer Grant what he has called an “enormous” amount of money to settle the case. The actor’s lawyers have advised him that this is more money than he is likely to be awarded in damages by a judge after a trial, even if his case were completely successful.
As a result, under the Part 36 rules, even if he were victorious at trial, Grant could find himself having to pay the enormous legal costs for both sides.
As Grant wrote on X: “If I proceed to trial and the court awards me damages that are even a penny less than the settlement offer, I would have to pay the legal costs of both sides.”
This is because, in the eyes of the court, he would have wasted everyone’s time by fighting the case when he could have accepted more money at a much earlier date.
1 note
·
View note
Text
A warning to all media organisations’: Prince Harry’s statement on Mirror Group ruling
Duke of Sussex describes slow and painful road to justice as judge rules extensive hacking took place
Prince Harry has landed a significant blow in his battle with the British tabloid press after winning a substantial part of his phone-hacking case and damages against the Daily Mirror. This is the statement read outside the court by his lawyer:
“Today is a great day for truth as well as accountability. The court has ruled that unlawful and criminal activities were carried out at all three of Mirror Group’s newspaper titles (the Mirror, the Sunday Mirror and the People) on a habitual and widespread basis for more than a decade.
“I’d like to thank my legal team for so successfully dismantling the sworn testimony of Mirror Group Newspapers’ senior executives, legal department and journalists, who at least turned up to court, unlike their colleagues, who were perhaps too afraid to do so.
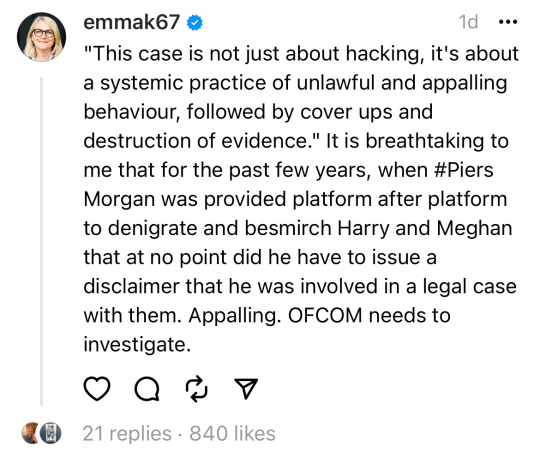
“This case is not just about hacking: it is about a systemic practice of unlawful and appalling behaviour, followed by coverups and destruction of evidence, the shocking scale of which can only be revealed through these proceedings.
“The court has found that Mirror Group’s principal board directors, their legal department, senior executives and editors, such as Piers Morgan, clearly knew about, or were involved in, these illegal activities. Between them, they even went as far as lying under oath to parliament, during the Leveson inquiry, to the stock exchange, and to us all ever since.

David Sherborne reads out Harry’s statement after the ruling. Photograph: Jordan Pettitt/PA
“The journey to justice can be a slow and painful one, and since bringing my claim almost five years ago, defamatory stories and intimidating tactics have been deployed against me and at my family’s expense. And so, as I too have learned through this process, patience is in fact a virtue – especially in the face of vendetta journalism.
“I hope that the court’s findings will serve as a warning to all media organisations who have employed these practices and similarly lied about them. Mirror Group’s actions were so calculated and misleading that their pattern of destroying evidence and concealing their unlawful behaviour continued into the litigation itself and, as the judge has ruled, even to this day.
“I am happy to have won the case, especially given that this trial only looked at a quarter of my entire claim. Even on just that, it is clear Mirror Group’s persistent attempts to suggest that my claim was, to quote their counsel, ‘fantastical’ and was in the ‘realms of total speculation’ and that there was ‘simply no evidence at all’ to suggest I was hacked – ‘zilch, zero, nil, nada, niente, absolutely nothing’ – were total nonsense and were used maliciously to attack my character and credibility.
“However, as Mirror Group intended, these hollow soundbites were blasted across front pages and across online platforms, and into the next day’s morning television shows. The court has in fact confirmed that all four claimants were subjected to voicemail interception and unlawful information gathering. But no one would have believed that was the case given how this trial has been covered in the UK.
“My commitment to seeing this case through is based on my belief in our need and collective right to a free and honest press, and one which is properly accountable when necessary. That is what we need in Britain and across the globe. Anything else is poisoning the well for a profession we all depend on. The acts listed in this judgment are prime examples of what happens when the power of the press is abused.
“I respectfully call upon the authorities – the financial regulator; the stock market who were deliberately deceived by Mirror Group; and indeed the Metropolitan police and prosecuting authorities – to do their duty for the British public and investigate bringing charges against the company and those who have broken the law.
“Today’s ruling is vindicating and affirming. I’ve been told that slaying dragons will get you burned. But in light of today’s victory and the importance of doing what is needed for a free and honest press – it’s a worthwhile price to pay. The mission continues.”
“Today’s ruling is vindicating and affirming. I’ve been told that slaying dragons will get you burned. But in light of today’s victory and the importance of doing what is needed for a free and honest press – it’s a worthwhile price to pay. The mission continues.”
Thats one hell of a quote
12 notes
·
View notes
Text
Find Infidelity Signs by Using Phone Hackers in USA
Have you ever felt a pang of doubt about your partner's fidelity? It's not uncommon to experience such concerns. However, with the help of advanced technology and reliable phone hacking services in the USA, uncovering signs of infidelity has become more accessible than ever.

⭐Advice For Victim
When you suspect cheating in your relationship, using phone hacking services in the USA is really important. They help you get proof discreetly and quickly, so you can face the truth about your partner's loyalty. These services access info on their phone to find evidence that might be hidden otherwise. Having this proof not only confirms your worries but also lets you decide what to do next. Dealing with infidelity directly is key for keeping trust in your relationship. So, letting professionals handle it ensures they do it carefully, protecting your emotions all along. Ultimately, using phone hacking services in the USA helps you find answers and move forward when you're unsure about your partner's faithfulness.
Why Choose Phone Hackers for Uncovering Infidelity?
Choosing phone hackers to uncover infidelity has many benefits. Firstly, they gather evidence discreetly and efficiently, giving people solid proof to confront their suspicions. Also, phone hackers use advanced methods and tech to retrieve information accurately from the target device.

By hiring pros for this task, individuals avoid risking further damage to their relationship with amateur investigations. Plus, phone hackers prioritize confidentiality, keeping their clients' privacy intact while providing necessary insights. Ultimately, opting for phone hackers provides a reliable and ethical way to deal with infidelity concerns, bringing clarity and closure to sensitive situations.
Safeguard Your Relationship
Keeping your relationship strong is crucial for trust and harmony. Talk openly and quickly about any worries you have to build honest communication and understanding. Make sure to be transparent and empathetic, listening to your partner's thoughts and feelings. Also, set boundaries and show mutual respect to maintain a healthy dynamic. Don't forget, spending time and energy on your connection helps it grow stronger, making your bond with your partner even more resilient and long-lasting.
Peace of Mind
Having peace of mind is crucial, even if it means facing uncomfortable truths. Knowing the reality, no matter how difficult, can offer a sense of closure and tranquility. It allows individuals to move forward with clarity and honesty, freeing them from the burden of uncertainty and doubt.

While confronting uncomfortable truths may initially cause distress, ultimately, it leads to a deeper understanding of oneself and one's circumstances. This sense of clarity and acceptance fosters inner peace and resilience, empowering individuals to navigate challenges with confidence and integrity.
Protect Your Emotional Well-being
Protecting your emotional well-being is crucial when dealing with signs of infidelity. Ignoring these signs can have a detrimental effect on your mental and emotional health. It's important to address any concerns proactively to avoid prolonged stress, anxiety, and uncertainty.

By confronting suspicions early on, you can prevent further emotional distress and begin the process of healing and resolution. Prioritizing your emotional well-being in such situations is essential for maintaining your overall mental health and happiness.
Signs to Look Out For
it's important to notice any behaviors that seem suspicious. Pay attention to changes in how your partner acts. If they start hiding their phone or avoiding talking about messages, that could be a warning sign.

Also, if they suddenly text or call a lot at strange times, that's something to watch out for. And if you see unfamiliar charges on their bank statements, that could be a problem. Keeping an eye on these signs can help you understand your relationship better and deal with problems early.
Increased Secrecy: Keep an eye out for noticeable changes in your partner's behavior, such as becoming overly protective of their phone or suddenly being secretive about messages and calls. If you notice them hiding their phone screen or password-protecting their device, it could be a sign that they're trying to conceal something from you.
Change in Communication Patterns: Be vigilant for sudden shifts in your partner's communication habits, such as an increase in texting or calling during unusual hours, especially late at night or early in the morning. If they're being evasive about who they're talking to or seem unusually preoccupied with their phone, it may indicate that they're engaging in secretive conversations.
Unexplained Expenses: Pay close attention to any unexplained expenditures or unfamiliar charges on bank statements or credit card bills. If you notice large sums of money being spent on items or activities that your partner hasn't mentioned or can't account for, it could be a warning sign of financial infidelity. This could include expenses for gifts, dinners, or hotel stays that seem out of the ordinary and aren't easily explained by their usual spending habits.
Changes in Routine: Be mindful of any sudden changes in your partner's routine or behavior, such as spending more time away from home without a clear explanation or showing a lack of interest in spending quality time together. If they're suddenly unavailable or unresponsive when they used to be readily accessible, it could indicate that they're prioritizing other activities or relationships over yours.
Emotional Distance: Pay attention to any emotional distance or detachment that seems to be growing between you and your partner. If they seem less interested in sharing their thoughts and feelings with you or become defensive or dismissive when you express concerns, it could signal that they're emotionally withdrawing from the relationship.
How Phone Hacking Services Can Help
Trusted phone hacking services utilize cutting-edge technology to access information stored on your partner's device discreetly. By employing ethical hacking techniques, these professionals can provide insights into your partner's activities without compromising their privacy.

📒 True Story of Using Phone Hackers in USA
There's a whispered tale circulating within Hollywood circles, involving none other than the renowned actress, Emma Stone. Behind the glitz and glamour of her on-screen performances, Emma's personal life was shrouded in uncertainty, particularly regarding her partner's elusive behavior. Troubled by suspicions of infidelity, Emma discreetly sought assistance from HackersList, a reputable platform known for its reliable phone hacking services and exceptional customer support. Learn More About Emma Stone.
Turning to HackersList with trepidation yet hope, Emma found solace in their promise of reliability and confidentiality. With their unwavering commitment to customer satisfaction, the team at HackersList embarked on the task of accessing Emma's partner's device with utmost discretion. Their advanced hacking techniques uncovered undeniable evidence of betrayal, offering Emma the clarity she desperately sought.

Empowered by the truth revealed by HackersList, Emma confronted her partner with courage and conviction, reclaiming control over her life's narrative. Throughout this tumultuous journey, HackersList stood as a beacon of reliability, providing Emma with the support and guidance needed to navigate through the storm.
While Emma Stone's story remains veiled in secrecy, her experience underscores the effectiveness of HackersList in addressing sensitive issues with professionalism and integrity. In an industry where privacy is paramount, HackersList's commitment to customer service and reliability shines brightly, offering a lifeline to those grappling with similar challenges. You Can Connect For Getting Professional’s Help.
Conclusion
If you're experiencing doubts about your partner's fidelity, don't let uncertainty consume you. Take proactive steps to uncover the truth with the assistance of reputable phone hacking services in the USA. Remember, addressing concerns early can lead to resolution and peace of mind for both parties involved.
#cell phone hacks#the black phone#phone hacker#phone hacking#phone hacked#phone hacks#hackerslist#hackerslistco
0 notes
Text

Yeah all you have to do is poke around the charging port with a toothpick and the ads just disappear. Doesn't work for iphone sorry
0 notes