#Virtual Second Phone Number App
Text



✌🏻 That was so hot… but don’t you dare do that again… ✌🏻
✎ Pairing: Chan x fem!reader
✎ Genre: Smut
✎ Summary: Channie’s Room is live, but you’re bored in the bedroom. Good thing he’s already looking at his phone.
✎ CW: Established relationship, sexting, nudes, vibrator use, swearing, teensy bit of dirty talk, unprotected sex
✎ Word count: 1,373
❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥ ❥
“Everybody put your hands up, Stray Kids sing it loud loud loud…”
As usual, Fam plays at the beginning of Channie’s Room. The webcam is pointed at an empty chair, and he appears as the song comes to an end.
“안녕하세요!” Chan sings, greeting the fans watching his stream. “Helllloooooo!”
The chat is full of the usual comments and questions:
ur so hot!
what are you working on? excited for the next album 💕
marry me!
when are you coming to Brazil?
But then there’s yours:
check your texts, babe 🎡☄️🛋️🎒
It’s the odd combination of emojis you agreed to use if you wanted him to know that one anonymous fan was actually you.
He’s reading through the comments, humming between replies. The chat moves so quickly, you’re prepared to send your comment multiple times before finally catching his eye. But then his finger stops scrolling and thumbs at the bottom of the screen to close the app. Bingo.
The “delivered” under your photo changes to “read,” and you can see his expression change ever so slightly. He clears his throat and tries to keep his cool, but blood rushes to his head, spreading from his ears to his cheeks to his throat. Practically every inch of visible skin is now a deep pink.
“Uh, Stay are being so nice today, you’re making me blush,” he says kind of convincingly. But you know better.
While he set up for the stream, you freshened up and donned your new lingerie. You considered being sweet and waiting until he came back to the bedroom to surprise him, but honestly, this is way more fun.
You took a bunch of selfies: one angled down, one angled up, one straight on your tits, another right on your ass. Lots of options, but you decided on the full body shot from above — your lower lip pinched between teeth at the top of the screen, fingers pulling at the bra strap in the middle, and your long, smooth legs crossed in front of the tiniest pair of underwear at the bottom.
He’s having trouble focusing on the chat now, and who could blame him? You look amazing, and there’s just a wall and some wiring between your bodies right now. Two dozen steps, and he could be on top of you, inside of you.
Chan readjusts his body in the chair, undoubtedly making more room in his jeans for his stiffening cock. He fidgets uncomfortably and tries his best to maintain some semblance of normalcy.
Whoosh
Off goes the second image — this one focused on your chest. But the straps are pulled down and one hard nipple sits just above the edge of the bra’s cup, pinched between two fingers.
This photo goes unseen for a little longer than the first, and you’ll let him open it in his own time. He’s seemingly back in his groove on camera, reading fan-suggested pickup lines and discussing whether a tomato is actually a vegetable or a fruit. You know he won’t be able to resist forever, though.
And of course, you’re right — you know him too well. A shaky inhale from virtual Chan encourages you to check your phone, and, yep, he saw the second one. The blush is back and this time, it’s accompanied by a tiny smirk and narrowed eyes. He cheekily stares at his phone’s screen for just a second too long, prompting commenters to ask if something’s wrong.
“Oh, naur, all good here!” he reassures. “I’m gonna play some songs for you guys and I’m just picking the first one!”
Ok, liar. Fib your way through this one.
Whoosh
Photo number 3 is simple, but speaks volumes. A long, thick vibrator sits atop your bare thigh. It’s a new toy, and he’ll know that. He’ll also know you��ll use it if he takes too long, and the thought of him sitting there listening to music on a livestream while his girlfriend fucks herself in the next room over will drive him crazy.
🎒🎡 wow i’m so bored……. ☄️🛋️
Another comment to push him to check his texts. You may get some less-than-nice replies from Stay for this one, but that’s fine. This is for him, not them.
…but there’s no reaction. You’re not sure if he didn’t see it or is simply ignoring it, but he’s vibing to Le Sserafim’s Antifragile like he isn’t thinking about your tits. Too bad you don’t give up that easily.
💕 you look so good today, 🛋️🎒 차니 🎡☄️
Still nothing. Fine, you’ll just start without him.
Your slender fingers pull the lacy underwear to the side to check how wet you are. Teasing your boyfriend like this always revs you up, so you’re not shocked to discover that two fingers slide in with more than enough room to spare. Time for photo number 4.
This one crosses the line from suggestive to straight-up filthy. Half of the vibrator is visibly slick from your arousal, and the other half is buried deep inside your cunt.
Whoosh
You were so distracted with your little photoshoot that you didn’t notice he replied two minutes ago.
you’re so bad
The last photo shows up as “read” almost immediately, and you glance at your laptop to see his reaction. He’s slumped into the corner of the chair, nervously giggling at his phone. So much for keeping his cool.
He’s stopped paying attention to the chat almost entirely, but you don’t even know if he’s noticed. You tend to have that effect on him. One more text while you know he’s still looking.
get your ass in here 🫦
He bites his lip just a little too seductively for YouTube, then he’s saying his goodbyes with unmistakable urgency.
“Bye Stay!!! Big hug? Big hug!” he coos, leaning in and closing his arms around the camera.
Even the hug is shorter than usual.
“See you next time, byyeee,” he chirps, throwing up that signature peace sign with a wink before disappearing from view.
Seconds later, he’s at the door with the same eagerness you saw on screen. But this time, you can also see the outline of his huge, hard cock in his jeans, complete with a small wet spot of pre-cum where the tip pushes against the denim.
“Hey, handsome,” you hum. “Need something?”
“You know what I need, you fucking tease.”
He’s on top of you before you can blink, groping at your tits and sucking at your neck.
“That stupid thing is nothing compared to me, and you know that,” he says, pushing the shiny new sex toy off the bed.
He unzips his pants and unsheathes his cock, giving it a few solid pumps before sliding those panties he saw earlier to the side and driving himself inside you.
“Oh fuck,” Chan breathes. “God, fu-”
Your lips engulf his, ending his moaning and mumbling. His mouth is citrusy, and it’s making your tongue tingle.
There’s really no rhyme or reason for any movement or grasp. You’re going at each other just like you did when you were nothing more than horny teenagers exploring something — and someone — new. Fingers and nails drag on skin and rake through hair, and you’re not sure how much longer you can last.
“Channie, I’m gonna…” you moan, breaking the sloppy kiss. “Are you…”
“Yeah, baby,” he pants. “Come.”
Manicured nails dig into his shoulder blades and you finish with force, crying out his name over and over. God, you hope he actually ended the livestream.
Then he’s coming too, emptying his balls deep inside you. His thrusts weaken, but the small movements are still enough to push some liquid down your legs and onto the comforter. Something to worry about later.
He collapses on top of you, lacking the strength and will to even pull out. His deep breaths tickle your neck, and you’re still seeing stars on the ceiling. Warm, wet fingers caress your damp collarbones, then he speaks.
“Baby, that was so hot… but don’t you dare do that again. I will fucking block you.”
“Agreed, and deal. I’ll only do it when you’re live on TikTok.”
He can’t tell if you’re serious, and if he’s bothered by the idea, he doesn’t show it. As he said, it was hot. And he was 100% right.
#My only thoughts during his lives#bang chan imagines#bang chan oneshot#bang chan scenarios#bangchan x you#stray kids imagines#stray kids x you#bang chan x reader#bangchan x reader#bang chan hard thoughts#bang chan smut#bangchan hard hours#chan smut#chan imagines#channies room#stray kids smut#skz scenarios#skz smut#channie smut
2K notes
·
View notes
Text
🌊Digital Detox + Egyptians lucid dreaming method 🌊



Idk what to put on the title of this post so I wrote digital detox and I have copy pasted the main lines.
In the ancient Egypt the Egyptians use to have lucid dreaming alot and it was extremely easy for for them not just Egyptians but it was also mention ancient Indian scriptures.
You’re probably wondering ‘what’s the secret’?
The real problem is often NOT your technique.
It’s actually another issue that no amount of techniques, articles, reality checks, supplements or uncomfortable masks is going to fix.
It’s your ‘inner game’.
Specifically, your subconscious motivation and reward circuits, and ‘dopamine cycle’.
Travel in your mind for a second, to ancient Egypt.
There were no smart phones, internet connections, computer animated action movies or virtual reality headsets.
Your brain back then would have produced a healthy amount of dopamine as a reward for pretty basic things like eating, working, exploring, and taking some time to relax or meditate
Now our average attention spans are literally less than 7 SECONDS.
It’s probably a lot lower than that, and It’s declining every single year with the rise of new, highly addictive and stimulating social media apps and platforms.
When was the last time you meditated for over 90 minutes?
Have you ever?
I’m not saying you have to do that to lucid dream, but this sort of practice was very common 5000 years ago. In fact, it was weird NOT to do that.
And herein lies the main problem.
Your brain is ‘fried’ with an overly stimulated dopamine pathway.
Dopamine is the neurotransmitter that stimulates the feeling of WANTING to keep doing something.
It’s the reason you keep scrolling through Instagram, or keep refreshing your Facebook feed to see if there are any new comments or notifications.
But it’s also the SUBCONSCIOUS reason you aren’t able to lucid dream easily.
In the last decade especially, there have been billions of dollars spent by big tech to essentially ‘addict you’ to their platforms.
Why?
Money.
The more time and energy you spend on platforms like that, the more money they make. So the task has been given to artificial intelligence.
The AIs often just get trained and told a few basic things:
1: Get people to spend more time on the platform
2: Get people to keep coming BACK to the platform as often as possible
The ‘AI’ pays almost NO attention to what that would do to your mental health, attention span, motivation, emotions, or really anything else.
Much LESS attention is paid to the effect it has on your ability to focus, or do things like, say, lucid dream.
Now, the ‘dopamine cycle’ is one part of the problem, but it’s actually pretty easy to fix.
There are several little pieces to what I call the ‘modern brain puzzle’.
Things that just weren’t a problem 5000 years ago.
You can see some of this playing out in children today.
On average, children or people under the age of 15, find it MUCH easier to lucid dream than adults do. It’s because at that age, their dopamine system has not been damaged too much.
This is of course changing now, as more and more children are having access to smartphones, but it’s an interesting point.
In fact not only does the dopamine problem affect your ability to lucid dream, it also affects your ability to WANT to lucid dream (consciously and subconsciously).
Specifically I’m talking about your motivation and focus.
And you guessed it, there’s your number one cause of problems when trying to meditate, practice techniques like the WILD, or recall your dreams.
After reading this paragraph or stanza whatever,I noticed something,as a kid I had lucid dreams alot with just putting intentions.
My first lucid dream was at around 7-8 years old,and I was sinking when I realised I was dream and I tried controlling my dream and even succeeded,and I was probably there for about 10 minutes playing with underwater creatures and mermaids.
And till 7 grade I use to have alot of lucid dreams but after that I was allowed to use phone and so I was always invested in phone like all the time. By the way lucid dream was pretty normal for me and I pretty much forgot about it and never really paid attention to lucid dreaming. And then I rarely had any lucid dreams, probably 4 times ever since 8 grade and I've noticed every time I lucid dream it's always whenever I don't use any social media.
In 9 grade my phone was taken again because my mother noticed my social media addiction. And after few months I again start to lucid dream for fun easily and effortlessly but during COVID I was again allowed to have my phone and then a new laptop so now my life was revolving around social media again and for the past few year I only lucid dream whenever I don't get to use my phone more then 2 days.
Idk bout y'all but I wasn't allowed to use phones or laptop till 8th grade so the only thing I knew was TV which I only watched after coming home so like my mind was most of the te bored because I didn't had anything to keep it entertain which made it easy for me to observe around looking for things to do.
So how can you reverse the ‘dopamine problem’ and several of the other issues modern life has created?
By the way:
This is NOT about destroying your phone and going back to live in a cave.
There are actually several powerful habits you can install, that will let you KEEP using your phone, laptop etc, but without these harmful effects.
Here’s the simple solution to more lucid dreams:
1. Reverse engineer your life and remove distractions, manipulation, ‘dopamine hijacking’ and harmful blue light exposure from your daily routine (along with some other ‘problem patterns’)
2. Get inside your subconscious brain and rewire yourself to WANT to practice lucid dreaming, and to effortlessly do reality checks at the right time, without even trying
3. Learn powerful ‘all day awareness’ and ‘lucid living’ techniques that give your brain superpowers in the fight
4. On top of THAT foundation, learn the most effective techniques and concepts, use our tools to stay motivated, and experience lucid mastery within 14 days.
Let’s dive a little bit deeper:
First, you have to ‘reverse engineer’ the problem.
This can be complicated if you don’t know what you’re doing, but we’ve laid everything out step by step for you.
If dopamine addiction is part of the problem, we have to break that addiction first.
Then comes your mindset, and your motivation pathways.
You need to actually feel GOOD when you practice these things. I see so many people saying they’re struggling to remember to do reality checks, or they just don’t want to wake up at ‘weird times’ to practice.
Don’t worry, you won’t have to.
It will feel good, and you’ll ENJOY practicing these things.
Next, your subconscious mind. It’s SO important to fix your internal beliefs about lucid dreaming, because the chances are you have ‘internal blocks’ about becoming lucid.
They’re easy to pick up, but a bit harder to ‘unlearn’. The system shows you how to ‘unlearn’ them, and install new, powerful and self affirming beliefs into your mind. This gives your brain lots more motivation to keep trying.
Now, one of the most common things I hear people say is that they can’t REMEMBER to keep doing reality checks. It’s linked to the dopamine problem we mentioned earlier, but it’s also connected to a few other psychological principles that we’ll get onto.
We’ll give you a new framework to ENJOY reality checks, remember them without any annoying reminders, and actually get them to SHOW UP in your dreams, 9 out of 10 times.
And then finally, we’ll build the most effective techniques, methods and concepts on top of that new, strong foundation. Of course, I’m simplifying this here, but that’s the outline.
Here are some videos that may help.
youtube
youtube
If you want to know more about it or get the steps to lucid dream you can buy the book or go through a long step to get it for free but the procedure is very long and probably only for Iphone user.
You find some good articles ways to do the 'reverse dopamine' thingy.(I donot trust my research on this topic cuz I got confuse)
You may use Adambja's tape to reprogram your subconscious and this hacking the matrix tape the comments under the video was so good and I found this tape on someone's success story. You can use this two tapes to reprogram your subconscious and of course psych-k.
This is pretty much all you need digital detox,observing your surroundings and subconscious reprogramming to change your belief or assumptions.
And this will make you even more motivated that you are working on your goals as many of us have the access of devices it's hard for us to keep up with all this method and it's not like we are always busy if we are we wouldn't be scrolling through Tumblr and Pinterest all the time. If you read the the copy pasted part you'll see what I mean.
Edit: I forgot to mention it 🥲 if we follow do this we CAN HAVE lucid dream everyday.
Egyptians lucid dreaming tea

This will be quick,so I went to my aunt's place with my mother and my aunt's ran out of tea powder/leaves so she used her daughter's blue lotus tea and after getting home I took a nap and I HAD A FOKING LUCID DREAM,so basically I didn't knew that it was the tea until I was doing some research on LD and found out that in ancient Egypt they use Blue Lotus tea and I found some review about it on YouTube and people had very vivid dreams aswell. This tea basically put you in REM which y'all probably know about.
But I don't like tea😐,so if anyone have interest you can try I honestly want to but my hate for tea is on top on the list of top 5 things I hate,you can find them online people even use Blue Lotus in vape😐not encourageling y'all to smoke but if anyone does you can.
159 notes
·
View notes
Text
can vpn app see ur password
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can vpn app see ur password
VPN encryption
Title: Understanding VPN Encryption: Securing Your Online Privacy
In today's digital age, where online privacy is increasingly threatened, Virtual Private Networks (VPNs) have emerged as essential tools for safeguarding personal information. At the heart of VPNs lies encryption – a complex process that encodes data to make it indecipherable to unauthorized users. Let's delve into the world of VPN encryption to understand how it works and why it's crucial for protecting your online activities.
VPN encryption functions by creating a secure tunnel between your device and the VPN server. When you connect to a VPN, your data is encrypted before it leaves your device and travels through this tunnel. This encryption process employs advanced algorithms, such as AES (Advanced Encryption Standard) with key lengths ranging from 128-bit to 256-bit, ensuring robust protection against cyber threats.
One of the primary benefits of VPN encryption is its ability to shield sensitive information from prying eyes, including hackers, government surveillance, and internet service providers (ISPs). By encrypting your data, VPNs prevent unauthorized access and interception, thereby preserving your privacy and anonymity online.
Moreover, VPN encryption plays a vital role in securing your online transactions and communications. Whether you're banking, shopping, or simply browsing the web, encryption ensures that your sensitive data remains confidential and inaccessible to cybercriminals.
It's important to note that not all VPNs offer the same level of encryption. When choosing a VPN provider, opt for reputable services that implement strong encryption protocols and follow strict privacy policies. Additionally, regularly updating your VPN software and using a combination of encryption protocols can further enhance your online security.
In conclusion, VPN encryption serves as a cornerstone of online privacy protection, empowering users to browse the internet securely and anonymously. By understanding how encryption works and selecting the right VPN provider, you can take control of your digital footprint and safeguard your sensitive information from external threats.
Password privacy
Password privacy is a crucial aspect of personal and online security. In today's digital age, where most of our sensitive information is stored online, protecting our passwords is essential to prevent unauthorized access to our accounts and data.
One of the fundamental aspects of password privacy is creating strong and unique passwords for each of our accounts. A strong password typically includes a combination of uppercase and lowercase letters, numbers, and special characters. By using different passwords for each account, we can limit the damage in case one of our passwords is compromised.
Furthermore, it is essential to store passwords securely. Avoiding writing down passwords on sticky notes or saving them in easily accessible digital files can help prevent unauthorized access. Instead, consider using reputable password managers that encrypt and store your passwords securely.
Regularly updating passwords is another key aspect of password privacy. Changing passwords periodically reduces the risk of unauthorized access, especially after a security breach or if you suspect that your password may have been compromised.
Additionally, enabling two-factor authentication (2FA) adds an extra layer of security to your accounts. 2FA typically requires you to provide a second piece of information, such as a code sent to your phone, along with your password, further enhancing the security of your accounts.
In conclusion, maintaining password privacy is essential to safeguarding our online security and protecting our sensitive information. By following best practices such as creating strong passwords, storing them securely, updating them regularly, and enabling 2FA, we can greatly reduce the risk of unauthorized access to our accounts and data.
Data interception prevention
Data interception prevention is a critical aspect of maintaining the security and confidentiality of sensitive information in today's digital age. With the increasing prevalence of cyber threats and attacks, organizations and individuals must take proactive steps to safeguard their data from interception by unauthorized parties.
One of the most effective ways to prevent data interception is through the use of encryption. Encryption involves encoding data in such a way that it can only be accessed by authorized parties with the corresponding decryption key. By encrypting sensitive information in transit and at rest, organizations can significantly reduce the risk of interception by cybercriminals.
Another essential measure for data interception prevention is the use of secure networks and communication channels. Implementing secure protocols such as HTTPS for web communications and VPNs for remote access can help protect data from interception during transmission over public networks. Additionally, organizations should enforce strong authentication measures to ensure that only authorized individuals have access to sensitive data.
Regular security audits and vulnerability assessments are also crucial for identifying and addressing potential weaknesses in an organization's data security posture. By conducting regular assessments and promptly addressing any vulnerabilities that are discovered, organizations can proactively mitigate the risk of data interception.
Overall, data interception prevention requires a multi-faceted approach that combines encryption, secure communication channels, strong authentication, and regular security assessments. By taking proactive measures to safeguard their data, organizations and individuals can reduce the risk of falling victim to data interception attacks and maintain the confidentiality of their sensitive information.
Secure tunneling technology
Title: Exploring Secure Tunneling Technology: Ensuring Safe Data Transmission
In today's interconnected digital landscape, secure tunneling technology plays a pivotal role in safeguarding sensitive data during transmission over public networks. Essentially, secure tunneling establishes a private, encrypted connection between two endpoints, ensuring confidentiality, integrity, and authenticity of the transmitted data.
At its core, secure tunneling encapsulates data packets within encrypted layers, effectively creating a virtual tunnel through which information travels securely. This encryption prevents unauthorized access and eavesdropping by malicious actors, thereby mitigating the risk of data breaches and interception.
One of the most widely used protocols for secure tunneling is the Virtual Private Network (VPN). VPNs utilize encryption algorithms to secure data traffic, making it unreadable to anyone without the appropriate decryption keys. By routing traffic through VPN servers, users can mask their IP addresses and obscure their online activities from prying eyes.
Another notable technology is Secure Shell (SSH), primarily used for secure remote access and file transfers. SSH employs cryptographic techniques to establish a secure channel between a client and a server, protecting sensitive information from interception and tampering.
Furthermore, Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), are instrumental in securing communication over the web. These protocols encrypt data exchanged between web servers and clients, ensuring confidentiality and integrity of online transactions, such as e-commerce and online banking.
Moreover, secure tunneling technology is indispensable for businesses operating in cloud environments. By leveraging technologies like IPsec (Internet Protocol Security) and TLS/SSL VPNs, organizations can establish secure connections between their on-premises networks and cloud infrastructure, safeguarding critical data and ensuring compliance with regulatory requirements.
In conclusion, secure tunneling technology serves as a cornerstone for maintaining privacy and security in an increasingly connected world. By adopting robust encryption protocols and implementing secure communication channels, individuals and organizations can mitigate cybersecurity risks and protect sensitive information from unauthorized access and exploitation.
User authentication security
User authentication security is a critical aspect of safeguarding sensitive information and protecting user privacy online. It is the process of verifying the identity of a user to ensure that only authorized individuals have access to a particular system or account.
One of the most common methods of user authentication is the use of passwords. However, passwords alone may not provide sufficient security, especially if they are easily guessable or if they fall into the wrong hands through techniques like phishing or data breaches. To enhance security, many organizations implement multi-factor authentication, which requires users to provide two or more forms of identification before granting access.
Biometric authentication is another increasingly popular method of user authentication security. This technology uses unique physical characteristics such as fingerprints, facial features, or even voice patterns to verify a user's identity. Biometric data is difficult to duplicate, making it a more secure option compared to traditional passwords.
In addition to the methods mentioned above, organizations can also implement security measures such as encryption, secure socket layer (SSL) certificates, and security tokens to further enhance user authentication security. It is crucial for companies to continuously update and strengthen their authentication protocols to stay ahead of evolving cyber threats.
By prioritizing user authentication security, businesses can build trust with their customers, protect sensitive data, and mitigate the risk of unauthorized access to their systems. It is essential for organizations to invest in robust authentication measures to ensure the safety and security of their users' information in an increasingly digital world.
0 notes
Text
Quotex Broker – Have Your Covered All The Aspects?
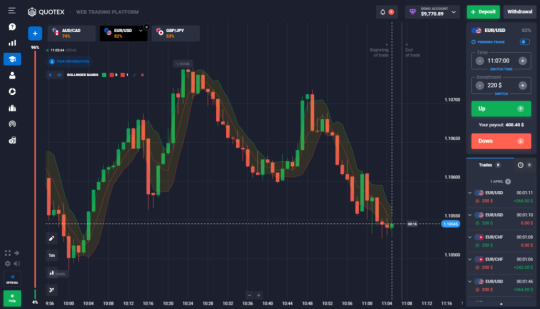
If you’re having trouble logging into your Quotex trading account, follow this step-by-step guide to resolve the issue. You can also try setting up two-factor authentication (2FA) to further secure your account. When registering, make sure to enter your email address correctly and read the service agreement carefully. This will ensure that you can easily access your trading account whenever needed.
What is Quotex?
Traders who wish to trade on the quotex broker platform are required to provide documents to verify their identity, which helps protect against financial fraud and other threats. The broker uses banking-grade security protocols and encryption, ensuring the safety of personal information. Traders can also activate two-factor authentication for added protection. The website offers a variety of deposit and withdrawal methods, including credit cards and cryptocurrencies. It also doesn’t charge fees for deposits or withdrawals. This can save you money when trading online.
Many reviewers have noted the platform’s user-friendly interface, making it easy for new traders to quickly learn the ropes. Additionally, the platform allows traders to invest in a wide range of tradable assets, including stocks, commodities, and currencies. It also has a comprehensive charting package, with 14 timeframes ranging from five seconds to one day and 29 indicators. In addition, the platform offers a number of educational resources. Nevertheless, a lack of regulation and the possibility of unexplained account closures may concern some investors. One can visit the site Quotex Login to get complete insights about quotex login broker.
Signing up for an account
When you first create an account with Quotex, you will need to verify your account. This is done by providing proof of identity and address. Some brokers may also ask for additional documents. Once your account is verified, you can begin trading with a real money account. This is a great way to get started in binary options trading. However, it is important to remember that there are risks involved in any type of trading, and it is recommended to use a demo account before investing real money.
Traders can access the QUOTEX platform on their computer or smartphone. The platform is easy to use and offers a variety of trading options. It has great charts, data, and indicators to help traders make informed decisions. The broker also provides guidance videos and news to help traders become successful in their trades. Moreover, the platform is mobile-friendly and supports a variety of deposit methods. In addition, it offers a free demo account with virtual money of up to $10,000.
Accessing your account
Once you’ve signed up for an account, you can access your trading platform on any device. To do so, simply enter your email address and password into the fields on the login page. Then click “Sign In” to gain access to your account and start trading. If you’ve enabled two-factor authentication (2FA) for your account, you may be asked to verify your identity via a code sent to your phone or generated by an authenticator app. This additional step ensures that only you can access your account, thereby protecting your funds from security threats.
The Quotex login process is simple and straightforward, making it easy for traders to use the platform. Additionally, the broker’s support team is always on standby to assist customers with any issues they might have. If you need to contact the support team, you can do so through email or live chat. This is a great way to get the help you need quickly and easily.
vimeo
Managing your account
Managing your account with Quotex is simple and hassle-free. The platform offers a wide variety of trading assets, easy one-click trading, and convenient methods of depositing and withdrawing funds. In addition, the broker offers an advanced e-learning center to help you develop your trading skills and make wise trades.
To manage your account, click on the “Settings” or “Account” option on the dashboard. Depending on the platform’s layout, this is usually found in a dropdown menu or at the top of the screen. If you have enabled two-factor authentication (2FA), you will be prompted to enter the code sent to your registered email or phone number. Alternatively, you can use the mobile app to access your account. Download the app from the Google Play Store or the Apple App Store, and login using your credentials to start trading. In case you lose your password, the broker has a dedicated support team to help you recover it.
0 notes
Text
The new direction of dynamic wallpapers - sharing of product ideas for Live2D wallpapers

When the team was working on the interactive wallpaper project, they thought about product positioning and implemented the functions in version 1.0. The market performance was also pretty good. Later, due to some special reasons, the continuation of 2.0 was abandoned. Now the author shares this content, hoping to help everyone.
1. Product introduction
XX Wallpaper is a wallpaper software with Live2D wallpaper (interactive wallpaper) as its core function. Version 1.0 mainly realizes HE Tuber the display and setting of live2d wallpapers, and is positioned as a wallpaper tool; version 2.0 plans to support users to upload live2d files, and will eventually What we do is a community of all types of two-dimensional picture resources.
2. Technical introduction
Live2D is a graphics rendering technology used in video games. The technology was developed by the Japanese company Cybernoids. To put it simply, Live2D can not only "upgrade" 2D pictures to be dynamic, making the pictures "breathing"; it can also realize "interaction" between people and pictures, such as users clicking on different positions of the picture, and the characters in the picture. Different movements and expressions can be produced, and the eyes of the characters in the picture can even follow the movements of the fingers. Just imagine that when you slide your finger left and right on the mobile phone desktop, the eyes of the cute "wife" in the wallpaper follow your movements, which really fills you with a sense of companionship~
The core technology used by the Live2D wallpaper application is the display of Live2D on mobile devices.
3. Product positioning analysis
1. 1.0 version tool direction ideas
Environmental status
The application of Live2D in 2D games has made it increasingly famous among 2D users. Second-generation Live2D based on games/animations/virtual anchors, etc. has been able to gain considerable attention. There are currently a small number of Live2D animators and a larger audience (in the two-dimensional circle) in the market.
Current state of technology
The core technology used by Live2D wallpaper applications is the display of Live2D on mobile devices. Live2D display technology is already a mature technology among game manufacturers, and the threshold is not high.
Competitive product opportunities
The only Live2D wallpaper tool currently on the market is live2d viewer EX (other major wallpaper platforms only support video format). Creators can upload their own Live2D works in this software, and fans can experience interaction and set wallpapers in this software. After analysis, it is believed that this software has the following problems in the domestic market:
The software is paid (¥26), which means that ordinary users need to purchase the software first to use a certain live2d wallpaper , which actually creates a certain threshold for the popularity of the work.
At the same time, the resources in live2d viewer EX are free, which results in users actually paying, but the creators do not benefit.
Live2d viewer EX is positioned as a tool product with weak social attributes . Users cannot interact with the author on the platform. The frequency of use of the APP is low, and users communicate on other platforms.
Functional opportunities
1) On the Android version, the advantage of wallpaper software is that it can be used without downloading, which just makes up for a major pain point of image sharing platforms: the conflict between resource use and copyright protection. And Live2D is different from ordinary file formats. Even if ordinary users download the source file, they don’t know how to open it. Therefore, Live2D wallpaper software can not only meet the needs of creators without uploading source files for others to download, but also meet the needs of users who can set live2D wallpapers without watching complicated tutorials.
2) MiHoYo's artificial desktop is currently the most popular wallpaper product in the 2D market. Through text analysis of TapTap1.6w comments, it was found that the most common feedback was " cannot interact " (competitive product analysis will not be carried out here for the time being), indicating that Users of two-dimensional wallpaper products have expectations for interactive wallpapers. Product positioning and promotion can focus on [ interactive two-dimensional wallpaper]
2. Community direction ideas for version 2.0
User needs analysis
The user roles of the wallpaper community can be divided into creators and users.
1) Creator
a. Users with certain or higher dynamic image creation skills.
What they need is a platform for display: for example, the producers of live2d, they need a platform that can directly display the effect of the work - after uploading the work, fans can directly experience the work instead of experiencing the effect of the work through the creator's video display; at the same time , they also need a tool that fans can use directly without obtaining the original files. This can reduce the communication cost between creators and fans, and avoid the separation of the work provision and acquisition platform from the communication platform, and the separation of the communication platform from the creator. Diversion of traffic.
b. Users who have certain static image creation skills. They also need tools and display platforms to optimize the effects of their works.
Most users with original art skills are static image producers. Among wallpaper resources, dynamic images are more competitive. Therefore, the biggest demand for static image creators is a tool with low threshold but good effect. To help them convert static resources into dynamic resources, Yuanqi Wallpaper's "Wallpaper Editor" is a tool for this need. The opportunity here is that it is a client-side tool. If it can be used as a mobile-side editing tool, the threshold for use will be further lowered.
c. Users who have ready-made resources and can make secondary creations. They need both tools and a presentation platform.
Users who have no original ability but have time and interest need a low-threshold tool to re-create their own resources and convert them into resources more suitable for wallpaper/lock screen.
2) User
For wallpaper users, their requirement is that the resources they like can be set as wallpapers with one click, instead of downloading a new paid APP or performing a complicated operation according to the creator's guidance after seeing the resources they like.
Community points of importance and opportunity
The community has two advantages: first, it provides a barrier-free display platform for creators' works, and second, it provides users with barrier-free use.
For example, Wallpaper Engine and live2d viewer involve different technologies for making wallpapers, but they both have "creative workshops". Wallpaper makers can directly upload their works to the "creative workshop" of the application, and other users can directly view them. To get this working, there is no need to go through any complicated operations.
Judging from the domestic environment, many Live2D creators still record their works into videos, and then upload and display them on the video platform. Fans can feel the effect of the works through the video, but if they want to download or set it to the desktop, they generally need to download Paid software live2d viewer, there are two "obstacles" here:
One is that the two paths of communication between creators and users and the use of works are separated, and they must be completed using two platforms respectively;
The second is that for domestic users who are accustomed to using free software, paid software is a "barrier" between creators and users. The buyout payment model is not in line with the general purchasing habits of domestic Internet users.
These two obstacles are also opportunities for new products.
Current status of static to dynamic technology
1) For a team that does not have strong technical capabilities, it is almost impossible to move Live2D production to the mobile terminal. Live2D is a file type that requires a specialized editor. It is too difficult to implement this huge editor on the mobile terminal. From a user's perspective, in order to create a Live2D file, the producer not only needs to divide a picture into many layers, but also needs to define the boundary values of actions and other content. The production threshold is very high.
2) Alternatives with lower thresholds. The "breathing effect" and "hair fluttering" effects of Yuanqi wallpaper hit users' pain points, and can achieve the effect of turning static into dynamic with one click, which is the most critical function of turning static into dynamic. The core technology of these functional applications is not Live2D technology visually. It may be Spine or other technologies that have been applied in some picture/video editors (such as Meitu Xiuxiu, Silhouette, etc.). These are relatively mature technologies. It is not difficult to implement.
3) Application of AI. AIGC is now very powerful, and many static-to-dynamic AI tools have already appeared on the market. If such AI can be integrated into applications, it will be a very good choice.
4. Summary
The above is a reflection on product positioning when working on the interactive wallpaper project. In fact, the 1.0 version part of the article has been implemented, and the market performance is not bad (more than 200 W downloads), but due to some reasons, I did not continue to work with the original team. Version 2.0, this product actually takes the direction of an AI companion, this article can be used as a commemoration.
0 notes
Text
The new direction of dynamic wallpapers - sharing of product ideas for Live2D wallpapers

When the team was working on the interactive wallpaper project, they thought about product positioning and implemented the functions in version 1.0. The market performance HE Tuber was also pretty good. Later, due to some special reasons, the continuation of 2.0 was abandoned. Now the author shares this content, hoping to help everyone.
1. Product introduction
XX Wallpaper is a wallpaper software with Live2D wallpaper (interactive wallpaper) as its core function. Version 1.0 mainly realizes the display and setting of live2d wallpapers, and is positioned as a wallpaper tool; version 2.0 plans to support
users to upload live2d files, and will eventually What we do is a community of all types of two-dimensional picture resources.
2. Technical introduction
Live2D is a graphics rendering technology used in video games. The technology was developed by the Japanese company Cybernoids. To put it simply, Live2D can not only "upgrade" 2D pictures to be dynamic, making the pictures "breathing"; it can also realize "interaction" between people and pictures, such as users clicking on different positions of the picture, and the characters in the picture. Different movements and expressions can be produced, and the eyes of the characters in the picture can even follow the movements of the fingers. Just imagine that when you slide your finger left and right on the mobile phone desktop, the eyes of the cute "wife" in the wallpaper follow your movements, which really fills you with a sense of companionship~
The core technology used by the Live2D wallpaper application is the display of Live2D on mobile devices.
3. Product positioning analysis
1. 1.0 version tool direction ideas
Environmental status
The application of Live2D in 2D games has made it increasingly famous among 2D users. Second-generation Live2D based on games/animations/virtual anchors, etc. has been able to gain considerable attention. There are currently a small number of Live2D animators and a larger audience (in the two-dimensional circle) in the market.
Current state of technology
The core technology used by Live2D wallpaper applications is the display of Live2D on mobile devices. Live2D display technology is already a mature technology among game manufacturers, and the threshold is not high.
Competitive product opportunities
The only Live2D wallpaper tool currently on the market is live2dviewer EX (other major wallpaper platforms only support video format). Creators can upload their own Live2D works in this software, and fans can experience interaction and set wallpapers in this software. After analysis, it is believed that this software has the following problems in the domestic market:
The software is paid (¥26), which means that ordinary users need to purchase the software first to use a certain live2d wallpaper , which actually creates a certain threshold for the popularity of the work.
At the same time, the resources in live2d viewer EX are free, which results in users actually paying, but the creators do not benefit.
Live2d viewer EX is positioned as a tool product with weak social attributes . Users cannot interact with the author on the platform. The frequency of use of the APP is low, and users communicate on other platforms.
Functional opportunities
1) On the Android version, the advantage of wallpaper software is that it can be used without downloading, which just makes up for a major pain point of image sharing platforms: the conflict between resource use and copyright protection. And Live2D is different from ordinary file formats. Even if ordinary users download the source file, they don’t know how to open it. Therefore, Live2D wallpaper software can not only meet the needs of creators without uploading source files for others to download, but also meet the needs of users who can set live2D wallpapers without watching complicated tutorials.
2) MiHoYo's artificial desktop is currently the most popular wallpaper product in the 2D market. Through text analysis of TapTap1.6w comments, it was found that the most common feedback was " cannot interact " (competitive product analysis will not be carried out here for the time being), indicating that Users of two-dimensional wallpaper products have expectations for interactive wallpapers. Product positioning and promotion can focus on [ interactive two-dimensional wallpaper]
0 notes
Text
Stay One Step Ahead: Expert Tips for Enhancing Your Online Privacy and Security

Welcome to the digital age, where convenience and connectivity are at our fingertips. We live in a world where we can instantly connect with loved ones across the globe, shop for groceries without leaving our homes, and access a wealth of information with just a few clicks. But amidst this rapidly evolving technological landscape, there is one crucial element that often gets overlooked - online privacy and security.
In today's interconnected world, protecting your personal information and ensuring your online safety has become more important than ever before. From identity theft to cyber attacks, the risks we face in the digital realm are real and constantly evolving. That's why it's essential for us all to stay one step ahead by enhancing our online privacy and security measures.
Are you ready to safeguard your digital presence? In this blog post, we'll dive into expert tips on how you can protect yourself from online threats while still enjoying all that the internet has to offer. So grab your virtual armor as we embark on this journey together!
Understanding the Risks: Common Threats in the Digital World
Understanding the Risks: Common Threats in the Digital World
The digital world is vast and ever-evolving, with countless opportunities for connection and convenience. However, it also comes with its fair share of risks that we must be aware of. In order to enhance our online privacy and security, it's crucial to understand these common threats.
One prevalent risk is malware or malicious software. This can infect your devices through various means such as email attachments, infected websites, or even fake apps. Once on your device, malware can steal personal information or cause significant damage.
Another threat to watch out for is phishing scams. These deceptive emails or messages often masquerade as legitimate entities like banks or online retailers in an attempt to trick you into revealing sensitive information like passwords or credit card details.
Social engineering attacks are yet another concern in the digital realm. Cybercriminals use psychological manipulation techniques to deceive individuals into sharing confidential data unwittingly. They may pose as a trusted source over phone calls or create convincing scenarios through which they gain access to sensitive information.
Data breaches have become increasingly common in recent years. Large-scale cyberattacks on organizations result in massive amounts of personal data being exposed and potentially used for nefarious purposes like identity theft.
Additionally, public Wi-Fi networks can pose a significant risk if not properly secured. Hackers can easily intercept data transmitted over these networks and gain unauthorized access to your devices or accounts.
By understanding these common threats present in the digital world today, we can take proactive measures to protect ourselves from falling victim to them. Stay tuned for expert tips on how you can enhance your online privacy and security!
Expert Tips for Enhancing Your Online Privacy:
Expert Tips for Enhancing Your Online Privacy:
In today's digital age, protecting your online privacy is of utmost importance. With cyber threats becoming increasingly sophisticated, it is crucial to stay one step ahead and safeguard your personal information. Here are some expert tips to enhance your online privacy.
Use strong passwords and enable two-factor authentication whenever possible. A strong password should be unique and contain a combination of letters, numbers, and symbols. Two-factor authentication adds an extra layer of security by requiring a second form of verification.
Next, keeping your software and devices updated is essential for maintaining online privacy. Software updates often include security patches that address vulnerabilities in previous versions. Regularly updating your operating system, antivirus software, and other applications can help protect against potential cyber attacks.
Another important tip is to be cautious with what you share on social media platforms. Cybercriminals can exploit personal information shared publicly on social media sites such as birthdays or addresses. Adjusting privacy settings and being mindful of the content you post can significantly reduce the risk of identity theft or unauthorized access.
By following these expert tips for enhancing your online privacy, you can take proactive measures to protect yourself from various threats in the digital world. Remember that staying vigilant and informed about the latest cybersecurity practices will always keep you one step ahead!
- Use Strong Passwords and Enable Two-Factor Authentication
In today's digital age, where our lives are increasingly intertwined with the online world, ensuring the security and privacy of our personal information is paramount. One of the most basic yet crucial steps you can take to enhance your online privacy is to use strong passwords and enable two-factor authentication.
Let's start with passwords. We've all heard this advice before, but it bears repeating: avoid using easily guessable passwords like "123456" or "password." Instead, create a unique password that combines uppercase and lowercase letters, numbers, and special characters. And don't reuse passwords across different accounts!
But even the strongest password won't provide foolproof protection on its own. That's where two-factor authentication (2FA) comes in. By enabling 2FA, you add an extra layer of security by requiring a second form of verification when logging into your accounts. This can be anything from a fingerprint scan or facial recognition to receiving a code via SMS or through an authenticator app.
By combining strong passwords with 2FA, you significantly reduce the risk of unauthorized access to your accounts. Remember that protecting your online presence requires constant vigilance and staying one step ahead of potential threats! So take these simple steps today to safeguard your digital life!
- Keep Your Software and Devices Updated
Keeping your software and devices updated is crucial for enhancing your online privacy and security. By regularly updating your operating system, apps, and antivirus software, you can stay one step ahead of potential threats.
Software updates often include important security patches that address vulnerabilities in the code. Hackers are constantly discovering new ways to exploit weaknesses in outdated software, so staying up-to-date is essential. It's like fortifying the walls of your digital fortress!
Updating your devices also helps protect against malware and other malicious attacks. Manufacturers release firmware updates that fix bugs and improve device performance. These updates not only enhance functionality but also bolster security measures.
Additionally, updating your web browser is equally important since it serves as a gateway to the internet. Browser updates typically include improved security features that safeguard against phishing attempts, drive-by downloads, and other cyber threats.
Remember: hackers are always looking for opportunities to infiltrate systems with outdated software or devices. Stay vigilant by enabling automatic updates or setting reminders to manually update regularly! Take control of your digital safety by keeping everything up-to-date – it's an easy yet effective way to maintain online privacy and security!
- Be Careful with What You Share on Social Media
Be Careful with What You Share on Social Media
Social media has become an integral part of our lives, allowing us to connect with friends and family, share updates, and express ourselves. However, it's important to be cautious about what we choose to share online. The information we put out there can have serious implications for our privacy and security.
One of the first things you should consider is adjusting your privacy settings on social media platforms. Take some time to review your account settings and make sure that only people you trust can see your posts and personal information. Remember, once something is shared online, it can be difficult to control who sees it.
Think twice before sharing sensitive or personal details publicly. This includes things like your address, phone number, or even vacation plans. Cybercriminals are always looking for opportunities to exploit this kind of information for their own gain.
Another aspect you should be wary of is oversharing. It's easy to get caught up in the excitement of sharing every moment of our lives online but remember that not everything needs to be documented. Think carefully about what you post and ask yourself if it could potentially compromise your privacy or security.
Additionally, avoid clicking on suspicious links or accepting friend requests from unknown individuals. Scammers often use social media as a way to gather personal data or spread malware. Stay vigilant and trust your instincts when interacting with unfamiliar accounts.
By being mindful about what you share on social media platforms, you can greatly enhance your online privacy and security. Remember that prevention is key – taking a few extra moments now could save you from potential headaches down the line!
Expert Tips for Enhancing Your Online Security:
Expert Tips for Enhancing Your Online Security:
1. Use a Virtual Private Network (VPN): One of the most effective ways to enhance your online security is by using a VPN. A VPN creates a secure and encrypted connection between your device and the internet, making it difficult for hackers or third parties to intercept your data. By masking your IP address, a VPN also adds an extra layer of anonymity when browsing the web.
2. Be Wary of Suspicious Emails and Links: Phishing attacks are prevalent in today's digital landscape, so it's crucial to exercise caution when receiving emails or clicking on links from unknown sources. Always double-check the sender's email address and avoid opening attachments or downloading files if you're unsure about their legitimacy. Hover over links before clicking on them to verify their destination.
3. Regularly Backup Your Data: In case of any security breach or ransomware attack, regularly backing up your data can be a lifesaver. Store backups on external hard drives or cloud storage services that offer encryption options for added protection.
4. Secure Your Wi-Fi Network: Ensure that your home Wi-Fi network is password-protected with a strong passphrase consisting of upper/lowercase letters, numbers, and special characters. Also, consider changing this password periodically to minimize the risk of unauthorized access.
5. Enable Two-Factor Authentication (2FA): Adding an extra layer of authentication through 2FA can significantly enhance your online security by requiring users to provide two forms of verification before accessing an account or service.
Remember that no single measure can guarantee complete online security; it requires adopting multiple layers of protection tailored to individual needs and staying vigilant against evolving threats in the digital realm
- Use a Virtual Private Network (VPN)
In today's digital age, protecting your online security is of paramount importance. One effective tool that can help enhance your online privacy is a Virtual Private Network (VPN). So, what exactly is a VPN and how does it work?
Essentially, a VPN creates a secure connection between your device and the internet by encrypting your data and routing it through servers located in different countries or regions. This means that when you browse the web or access sensitive information, such as banking details or personal files, your data remains private and protected from prying eyes.
Using a VPN offers several benefits. It masks your IP address, making it difficult for anyone to track your online activities. It adds an extra layer of encryption to prevent hackers from intercepting your data. Using a VPN allows you to bypass geographical restrictions and access content that may be blocked in certain locations.
However, not all VPNs are created equal. It's important to choose a reputable provider with strong encryption protocols and a strict no-logging policy.
By employing this simple yet powerful tool in conjunction with other security measures like strong passwords and updated software, you can stay one step ahead in safeguarding both your online privacy and security. Remember: taking proactive steps now will go a long way in protecting yourself against potential threats down the line!
- Be Wary of Suspicious Emails and Links
Be Wary of Suspicious Emails and Links
One common method that cybercriminals use to gain access to your personal information is through phishing emails. These deceptive messages are designed to trick you into revealing sensitive data or downloading malicious software onto your device. To protect yourself, it's essential to be wary of suspicious emails and links.
Always double-check the sender's email address before opening any attachments or clicking on any links. Cybercriminals often try to mimic legitimate companies or individuals, so a close examination can reveal telltale signs of fraud. Look for misspellings or slight variations in the domain name that may indicate a fake email.
Avoid providing personal information or login credentials via email unless you are certain of the recipient's identity and trustworthiness. Legitimate organizations will never ask for sensitive details through an unsolicited email.
Additionally, exercise caution when clicking on links within emails. Hover over them with your mouse cursor first to see if the URL matches what was displayed in the message. If something seems off or unfamiliar, it's best not to click on it at all.
Remember, staying vigilant and skeptical when dealing with emails is crucial for maintaining online security. By being cautious and questioning suspicious messages, you can significantly reduce the risk of falling victim to phishing attacks.
-
Enhancing your online privacy and security is an ongoing process that requires vigilance and awareness. By implementing the expert tips mentioned above, you can stay one step ahead of potential threats in the digital world.
Remember to use strong passwords, enable two-factor authentication, and keep your software and devices updated to protect your personal information from being compromised. Be cautious about what you share on social media platforms and be wary of suspicious emails and links that could lead to phishing attempts or malware infections.
Additionally, using a Virtual Private Network (VPN) can add an extra layer of security by encrypting your internet connection and masking your IP address. This helps to safeguard your data from prying eyes when browsing online.
Taking these precautions may seem like small steps but they can make a big difference in protecting yourself against cyber threats. Stay informed about the latest techniques used by hackers and continue educating yourself on best practices for online privacy and security.
By remaining proactive in safeguarding your digital presence, you can enjoy the benefits of technology while minimizing the risks associated with it. Remember, staying one step ahead means prioritizing your privacy and security at all times!
0 notes
Text
Mobile App Scraping for Retail | eCommerce

How to Leveraging Mobile App Scraping for Retail Success?
July 13, 2023
Mobile apps have become a vital consumer shopping channel in today's post-pandemic world. With smartphone users spending an average of over 3 hours on their phones daily, it's clear that mobile apps are increasingly preferred over traditional eCommerce apps. Recognizing this shift, Mobile App Scraping has introduced an innovative mobile app scraping solution to complement its successful eCommerce app scraping technology. This advanced solution is designed to help businesses thrive in the evolving retail landscape.
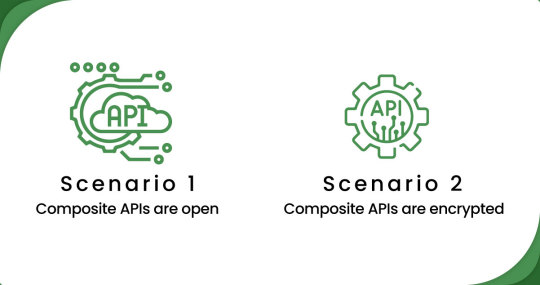
Scenario 1:
When composite APIs are open (e.g., Amazon) - In such cases, the scraping process is similar to standard app scraping, with some initial setup required. Mobile App Scraping can utilize the available APIs of platforms like Amazon to access and extract the desired data. The process involves making API requests, handling responses, and parsing the retrieved data.
Scenario 2:
Whenever composite APIs get encrypted (e.g., Dollar General, HEB, Target, Stop & Shop, etc.) - This scenario presents a more complex challenge. Mobile App Scraping employs specialized techniques such as mobile device extraction, OCR (Optical Character Recognition), as well as other machine learning methods to overcome the encryption and extract data from these apps. Mobile App Scraping leverages advanced technologies to navigate the encrypted APIs and interfaces, ensuring accurate and reliable data extraction.
In both scenarios, Mobile App Scraping utilizes its expertise and advanced methodologies to scrape mobile apps efficiently and effectively, providing businesses with valuable data insights to enhance their operations and decision-making processes.
Methodology
Step 1: Recording a mobile session/navigation using unique visual navigation scrapers Technology consideration
Mobile App Scraping employs a virtual device cloud infrastructure to ensure scalability and efficiency. It utilizes an emulated cluster of devices that connect through an intelligent proxy network.
In the first step of the methodology, special visual navigation scrapers are utilized to record mobile sessions and navigation. These scrapers interact with the mobile app interface, mimicking user actions and capturing the relevant data. This approach allows Mobile App Scraping to navigate the app, access different screens, and interact with various elements to gather the desired information.
To achieve scalability, a virtual device cloud infrastructure is employed. This infrastructure emulates a cluster of devices, ensuring that the scraping process can be performed at scale. Additionally, an intelligent proxy network handles communication between the devices and the app, ensuring efficient data retrieval.

Step 2: Identify product ROI (Region of Interest)
To accurately scrape text for each product, Mobile App Scraping utilizes an Object Detection algorithm to identify the ROI of individual products within a frame, regardless of the number of products present.
The input files are passed through a custom fine-tuned version of the YOLOv5 (You Only Look Once) architecture, which excels in fast and accurate inference. YOLOv5 can swiftly detect and localize each product's ROI within the frame.
Since a video typically consists of multiple frames per second, the exact product ROIs are possible. To address this, a deduplication stage is introduced. This stage eliminates identical product ROIs, allowing faster and more efficient data processing. The resulting ROIs from the video frames are then cached as images, ready for further analysis and extraction.

Step 3: Identify product components
In this stage, Mobile App Scraping focuses on identifying specific components of the products, such as price, product information, product image, and more. The same components to be identified may vary based on the specific mobile app being scraped.
To achieve precise component identification, Mobile App Scraping applies YOLOv5 again, but with a different instance or configuration compared to Step 2. This allows for more granular consideration in detecting and localizing the desired components within the product ROIs.
Step 4: Extract components with OCR
In this stage, Mobile App Scraping completes the textual extraction process now that all details of the products have been identified. A custom-trained OCR (Optical Character Recognition) framework is deployed to achieve this.
The OCR framework is specifically trained to recognize and extract text from the identified components of the products. It utilizes advanced algorithms and machine learning techniques to accurately extract textual information such as product names, prices, descriptions, and other relevant details.

Step 5: Accessing the final output
In the final stage, the text extraction output and relevant metadata are stored in a database. Mobile App Scraping applies unit tests and quality checks to ensure the accuracy and integrity of the extracted data.
Once the data is verified and validated, it is transformed into the desired format suitable for the client's needs. This transformation process ensures the information is structured appropriately and ready to be accessed, sent, uploaded, or requested via API (Application Programming Interface).

Conclusion
In conclusion, as the retail landscape evolves with the rise of mobile and social commerce and the emergence of the metaverse, the need for advanced AI and analytics becomes paramount. Mobile App Scraping recognizes this need and is dedicated to providing retailers and brands with sophisticated and accurate analytics across the retail ecosystem. They have developed an cutting-edge mobile app scraping solution to cater to the evolving needs of the retail industry.
Moreover, Mobile App Scraping has extended its proprietary technology to the metaverse, enabling the scraping of retail stores in virtual platforms like Decentraland, Roblox, Sandbox, Meta, and more. This expansion reflects their commitment to staying at the forefront of technological advancements and ensuring that retailers have access to critical data and insights across multiple platforms.
With the growing popularity of mobile commerce and the increasing competition in the retail space, mobile app scraping has become essential for maintaining competitive prices, assortments, and digital shelf ranking. By leveraging Mobile App Scraping's cutting-edge solutions, retailers can stay ahead of the curve and make informed decisions based on accurate and real-time data.
In summary, Mobile App Scraping offers innovative mobile app scraping solutions alongside their established eCommerce app scraping technology, empowering retailers to thrive in the dynamic retail landscape and meet the demands of modern consumers.
know more:
https://www.mobileappscraping.com/mobile-app-scraping-for-retail-success.php
#RetailAppScraping#AppScrapingForRetail#EcommerceAppScraping#ScrapeEcommerceAppData#ExtractRetailAppData
0 notes
Text
👉 vCard Agency Review ✅ This Works In Any Niche Without Fail & No Tech Skills Required!

First-To-Market Breakthrough App + AI Training Let’s You Start A Lucrative Side Hustle Selling vCards To Businesses In 60 Seconds Or Less! Best Part – This Works In Any Niche Without Fail & No Tech Skills Required!
FAST ACTION BONUS: Agency License Included!

Get vCard Agency For A Low One-Time Fee
Instantly Set Up Virtual Business Cards, That Grabs Attention & Interest For Your Own Business, Sell Vcards & Use It To Close Any Deal…
► Multiple Templates
With vCard Agency App, you can several vcard templates to choose from and customize.
► Click to Call
Your clients can reach you by just tap on phone number and contact you for any query.
► 1 Click Sharing
Share Your Business Information with your prospects directly via SMS, Email or any other ways.
► Social Media
Click To Follow On The Most Trafficed Social media sites & build brand awareness.
►Scan QR Code
Scan Your QR Code, So your clients can see your details and also then can share your QR Code to others.
► More Leads & Bookings
Collect leads (email & telephone number) so you can do follow-ups and book appointments on the fly.
Get vCard Agency For A Low One-Time Fee
People Are Loving This Brand New Tool! Using It In Their Businesses And Getting Results
vCard Agency is a great marketing tool which allows you to engage with customers in a more professional manner.
What makes Card different is that you can actually have your very own call center type structure.
Set up is a breeze and I love that I can create a custom, professional vcard. All you have to do is make a few clicks, enter your information and you’re done.
The best part, you can control everything right from your fingertips!( J. Blyte - Freelancer )
vCard Agency is an amazing piece of software bringing a never before seen state of the art technology to the Internet Marketing space. A lot of products overpromise but undeliver. This was not the case with the amazing app, thanks you OJ for bringing this app to the IM market. ( Rob N - Agency Owner )
vCard Agency App is a very cutting edge engagement software i have seen so far.
I used this software and found this very much helpful for any business and website out there. ( Eric S - Agency Owner )
TIME TO MODERNIZE YOUR OWN MARKETING Or You Can Easily Sell vCards As A Service To Other Businesses!
Look, This New Revolutionary Technology Is Now Needed More Than Ever. As business everywhere are struggling to get attention and close sales/
And I know what you’re likely thinking…
You’ve heard all this “future of online marketing” before… From Video, To Social Media, To Chatbot marketing, AI and everything else in-between…
And while those are all great marketing channels we personally use and recommend, what we have to show you today will quickly take your online marketing to a whole new level!
And since we are currently in a global recession where there are talks about economic downturn, now more than ever… businesses of all types and sizes need to be able to engage with their prospects and customers online in the fastest and best ways possible…
Because let’s face it, if you’re not doing business online, you need to be or you simply will not survive going forward.
Information overload has caused clients and customers to become blind to business websites, social media pages and as a result vCards are proven to bring re-engagement and attention to any business, with vCards you can offer sometime FRESH TO Your existing clients or starting a new service that you can use to make profits.
Get vCard Agency For A Low One-Time Fee
From The Desk Of OJ James
If you are looking for a way to selling a new service or existing the life time value of your customer base, vcards is the perfect solution for you.
I’m sure you have been in the situation before where you had a brilliant idea
And, you’re ready to grind and make profits online
But you end up with not so great results from your efforts, which left you feeling like you are heading towards being
Financially Ruined
Feeling Like nothing is going right for you
No Enough Income
Demanding Boss & Job Duties
Long & Boring Commutes
Difficult Schedules
Not Meeting Deadlines
Restless Nights
Just Imagine How Much Success You Could Potentially Have Selling This Revolutionary Technology To Businesses
With vCards you extend the life-time-value of your customers to make more profits or add a new service to your agency business/
Just imagine what this could do for other businesses out there, who are literally begging for these vcard campaigns to be set up for their businesses, they would happily pay big bucks for it.
Get vCard Agency For A Low One-Time Fee
And the best part you can do this from anywhere in the world, all you need is an internet connection to get started
Thanks to the internet, AI and using our tool.
Creating a life of freedom is very much possible…
That can result in being:
Free from Day Job…
Free from hectic work schedule…
Free to Travel The World…
Free to manage own time.
And what’s even more amazing is that you can start using this amazing technology for rapid results starting Today!
vCard Agency is the easiest & fastest Way To Launch A Lucrative Business In Just 3 Simple Steps
STEP 1
Log into the app and see all the amazing vcard templates you can offer to local businesses.
STEP 2
Enter all the necessary information that to customize the vcard to the specific business
STEP 3
Hit Activate & Get PAID for Helping Businesses.
Get vCard Agency For A Low One-Time Fee

Secure vCard Agency Today For A Low One Time Fee!
👉 Manage Everything For A Easy To Use Dashboard
👉 Powerful Point & Click vCard Page Builder
👉 Over 15 Ready to use vCard Templates
👉 1 Click to Call & Information Sharing
👉 Collect Leads (Name, Phone, Email)
👉 QR Codes Builder
👉 Deep Analytics
👉 Premium Dedicated Support
👉 30 Days No-Risk Money-Back Guarantee
COMMERCIAL RIGHTS – Included $1497 value
Get vCard Agency For A Low One-Time Fee
We Have Added Some EXCLUSIVE Bonuses To Make This A No Brainer Decision For You!
With all the amazing features that vCards comes with, I’ve also included all these exclusive bonuses alongside our purchase today:
BONUS 1
Free Commercial Licence
(Only For Today! $497 FREE!)
We have already reached the obvious conclusion that every business needs to have a strong digital presence in this day and age.
There is no other way to survive let alone make profits. So quite naturally, having an agency that provides just what everyone needs will never go out of business.
An unending list of clients coupled with effective tools is just what you need to get your own agency going.
Our commercial is included free of charge and gives you the opportunity to make unprecedented profits.
P.S. Once this special launch ends… customers who get access later, will have to pay an extra $497 for the Commercial License.
BONUS 2
Local Restaurant Agency App
(Valued at $197)
This is a powerful restaurant management platform app you can use to set-up online order stores for local restaurants, yours as a bonus with vCard Agency.
BONUS 3
Social Marketing School
(Valued at $97)
Social Media is the most powerful marketing tool available today.
It’s a way for people and businesses alike to connect with their customers, build relationships, and grow their business. But it can be hard to know where to start or what strategies work best.
That’s why we created this course – so you can learn everything from the basics of social media marketing all the way up through advanced strategies that will help you get more customers, revenue and profits!
BONUS 4
Solopreneur Success
(Valued at $97)
This training course has everything you will want to know. As a solopreneur, you will be responsible for your own productivity- which can be difficult for many people.
Solopreneurship is not easy but it’s worth it! You’ll have the freedom of working on what interests you most, and being able to set your own schedule. But there are also challenges that come with this type of work such as finding clients or managing finances.
Get vCard Agency For A Low One-Time Fee
Frequently Asked Questions
Do I Have To Install vCard AGency Anywhere?
NO! vCard Agency is a web-based software that you can use from anywhere once you have internet connection.
Do I Need Any Tech Skills Or Experience To Make This Work?
NO – skilles or experience required to get this working for you!
Does This Cost A Monthly Fee?
Absolutely NOT! When you act now, you’re getting one-time access to vCard Agency without EVER having to pay a monthly fee! 🙂
Will This Work In Any Niche?
Definitely, 100%!
Can I Get Results With This?
Yes – but as with any product, your results will vary based on the amount of effort you put into it.
Is Support & Training Included?
Absolutely…by purchasing vCard today you get instant access to the training portal and our 24/7 support desk!
Get vCard Agency For A Low One-Time Fee
#vCardAgencyReview#vCardAgencyReviews#vCardAgencyReviewAndBonus#vCardAgencyPreview#vCardAgencyDemo#vCardAgencyLiveDemo#vCardAgencyScam#vCardAgencyLegit#vCardAgencySoftware#vCardAgencyApp#vCardAgencyDownload#vCardAgencyOTO#vCardAgencyOTOs#vCardAgencyUpgrades#vCardAgencyUpsells#vCardAgencyDiscount#vCardAgencyBonus#vCardAgencyBonuses#HowDoesvCardAgencyWork#HowtoBuyvCardAgency#HowtoMakeMoneywithvCardAgency#MakeMoneywithvCardAgency#vCardAgencyScamorLegit#vCardAgencyGoodOrBad#vCardAgency#marketing#affiliatemarketing#onlinemarketing#makemoneyonline#usa
0 notes
Text
Buy TextNow Accounts
Textnow Accounts provide users with a convenient and affordable way to make phone calls and send texts using a virtual number. Textnow is a popular app that allows users to make and receive calls as well as send and receive text messages using a virtual phone number.
With Textnow Accounts, users can enjoy the benefits of having a second phone number without the need for an additional SIM card or device. This makes it a cost-effective solution for individuals who want to keep their personal and business communication separate or for those who need a temporary phone number for certain purposes.
We will explore the features and benefits of Textnow Account and how to set up and use them effectively. So, let’s dive in and discover how Textnow Accounts can enhance your communication experience.
Enhance Communication And Connectivity
TextNow account have brought about a revolution in communication, offering numerous benefits that enhance connectivity. First and foremost, TextNow accounts allow for seamless and unlimited texting and calling to anyone in the US and Canada, free of charge. This means that you can stay connected with your loved ones and colleagues without any limitations or expensive phone bills. Furthermore, TextNow account offer the convenience of Number Porting, which enables you to keep your existing phone number when switching to TextNow. This eliminates the hassle of notifying everyone about your new number and ensures that you don’t miss any important calls or messages. Additionally, TextNow account come with customizable voicemail, call forwarding, and call screening features, providing you with complete control over your communication preferences. Overall, TextNow account are a game-changer in terms of accessibility, affordability, and convenience, revolutionizing the way we connect and communicate.
Cost-effective Communication Solution
Textnow accounts provide a cost-effective communication solution for individuals and businesses. By opting for Textnow account, users can significantly reduce communication expenses while enjoying the benefits of a reliable and efficient communication platform.
Textnow account offer a budget-friendly alternative to traditional phone plans, allowing users to make voice and video calls, send text messages, and even make international calls at affordable rates. With Textnow accounts, users can also enjoy unlimited texting and calling within the United States and Canada, which further adds to the cost savings.
Moreover, Textnow account provide the flexibility to use the service on various devices such as smartphones, tablets, and computers, ensuring seamless communication across different platforms. This versatility makes Textnow account suitable for both personal and professional use, catering to the diverse communication needs of individuals and businesses alike.
Versatility Of Textnow Accounts
are a versatile communication solution that can be adapted to both personal and business use. Whether you need a secondary number for personal calls or a dedicated line for your business, Textnow account provide the flexibility you need.
For personal use, Textnow account offer the convenience of having a separate number for specific purposes. You can use it for online dating, buying and selling goods online, or simply keeping your personal and professional life separate.
For business use, Textnow account are an affordable alternative to traditional phone lines. You can use it for customer service, marketing campaigns, or as a dedicated line for specific departments.
Additionally, Textnow account offer features such as call forwarding, voicemail, and SMS messaging, making them suitable for various communication needs. With Textnow, you have the freedom to customize your account to fit your specific requirements.
With their versatility and affordability, Textnow account are a valuable communication solution for individuals and businesses alike. Whether it’s for personal or professional use, Textnow accounts offer a flexible and reliable communication solution.
Streamlining Communication Processes
Streamlining communication processes is essential for any business or individual looking to efficiently manage messages and calls. With Textnow account, you can seamlessly integrate this communication tool with other platforms and unleash a wide range of benefits.
One of the key advantages of using Textnow account is the ability to consolidate your communication channels. By centralizing your messages and calls within Textnow, you can simplify your workflow and avoid the hassle of juggling multiple platforms.
Furthermore, Textnow account offer advanced features that enhance productivity. Features like message filtering, call forwarding, and voicemail transcription enable you to stay organized, prioritize important communications, and save time.
Integrating Textnow account with other communication tools brings even more efficiency. By connecting Textnow with your customer relationship management (CRM) system or email client, you can seamlessly track and manage all your interactions in one place.
In conclusion, Textnow account are a valuable asset for streamlining communication processes. By efficiently managing messages and calls, consolidating communication channels, and integrating with other tools, you can optimize productivity and enhance communication within your business or personal life.
Collaboration Made Easy
Enhancing teamwork and collaboration with Textnow account
In today’s fast-paced business environment, effective teamwork and collaboration are crucial for project success. One powerful tool that can help streamline communication and coordination is Textnow account. With Textnow, teams can easily communicate and share information, regardless of their location or device. This enables real-time collaboration and seamless project management.
Textnow accounts offer a range of features that enhance team productivity. Users can send instant messages, make voice and video calls, and share files with team members. The ability to create group chats and video conferences simplifies team meetings and discussions, fostering efficient decision-making. Moreover, Textnow’s user-friendly interface and intuitive design make it easy for team members to navigate and access information.
By leveraging Textnow accounts, organizations can improve their project management and coordination processes. From assigning tasks and setting deadlines to tracking progress and resolving issues, Textnow provides a centralized platform for effective teamwork. Teams can collaborate in real-time, ensuring that everyone is on the same page and working towards shared goals.
Overall, Textnow accounts empower teams to work collaboratively, boosting productivity and accelerating project success. With its range of communication and coordination features, Textnow is a valuable tool for any organization looking to enhance teamwork and maximize efficiency.
Simplifying Client Communication
Personalizing client communication is crucial for improving customer service. With Textnow account, businesses can simplify and streamline their communication processes. By using Textnow, companies can create a personalized and efficient way to interact with their clients.
Textnow account allow businesses to send and receive text messages, make phone calls, and even send media files to their customers. This platform ensures that communication is quick and convenient, enhancing the overall customer experience. With Textnow, businesses can easily manage client inquiries, provide support, and address any concerns in real-time.
Moreover, Textnow account provide businesses with a flexible and cost-effective solution for client communication. Companies can track and monitor conversations, ensuring that no client request goes unanswered. Additionally, businesses can easily integrate Textnow accounts with their existing CRM systems, further simplifying the communication process.
Seamless Call Recording and Transcription
Call recording has become an essential tool for businesses, allowing them to improve customer service, train employees, and maintain accurate documentation. By recording and transcribing calls, companies can easily reference and analyze important conversations. Textnow Accounts offers a call transcript feature that simplifies this process.
Utilizing call recording for training and documentation purposes is crucial in today’s fast-paced business environment. Through Textnow Accounts, conversations can be stored and reviewed at any time, ensuring that employees receive the necessary guidance and support to excel in their roles. Additionally, call transcripts provide a convenient way to revisit crucial details, helping staff accurately address customer inquiries and resolve issues efficiently.
Textnow Accounts not only offers seamless call recording capabilities but also ensures reliable call transcription that can be easily accessed for analysis and future reference. With this feature, businesses can enhance their customer interactions, improve employee performance, and maintain comprehensive documentation.
Personalization With Textnow Accounts
Textnow account offer a range of personalization options to make your messaging experience unique. You can customize message templates to save time and add a personal touch to your conversations. Whether for business or personal use, having predefined messages ready to go can greatly improve your efficiency. Additionally, you can create multiple signatures for different contexts, allowing you to tailor your messages based on the recipient or the purpose of the communication.
When it comes to voicemail, Textnow account provide the flexibility to create personalized voicemail greetings. You can record your own voice or choose from a variety of pre-recorded options to add a personal touch to your voicemail messages. This not only sets your messages apart but also adds a professional touch to your communication. Impress your callers and ensure they remember you by personalizing your voicemail greeting with TextNow Account.
Protecting Confidential Information
Encryption and security measures play a pivotal role in protecting confidential information within Textnow account. With the ever-increasing concern for data privacy, it is crucial to ensure that sensitive data transmitted through TextNow Account is safeguarded. Textnow employs state-of-the-art encryption techniques to secure your communication. This ensures that any data sent or received remains confidential and inaccessible to unauthorized entities. Additionally, TextNow Account enforces stringent security measures to prevent unauthorized access and protect user accounts. A combination of secure password policies and multi-factor authentication ensures that only authorized individuals can access the account. Continuous monitoring and regular security updates further enhance the security of Textnow account. Overall, TextNow Account prioritizes the security and privacy of user data, providing a safe and secure platform for communication.
Privacy Features
Textnow account offer various privacy features to help users manage their privacy settings and control their contact visibility and call screening options.
Managing Privacy Settings: Users can easily manage their privacy settings within Textnow accounts. They have the freedom to choose what information they want to share and with whom.
Controlling Contact Visibility: TextNow Account allows users to control the visibility of their contacts. They can choose to display all contacts or only certain contacts, enabling them to maintain their privacy.
Call Screening Options: With TextNow Account, users can customize their call screening options. They have the ability to block unwanted calls, screen calls from unknown numbers, and protect their privacy.
These privacy features within Textnow account ensure that users have full control over their privacy settings, enabling them to communicate securely and confidently.
Branding And Marketing Opportunities
One effective way to capitalize on branding and marketing opportunities is by leveraging Textnow accounts. These accounts offer a unique avenue for reaching a targeted audience and promoting your brand. By utilizing Textnow accounts, businesses can execute targeted marketing campaigns. This allows for tailored messaging to specific demographics, increasing the likelihood of conversions and brand recognition.
Textnow account provide a valuable platform for businesses to engage with their target market. With a well-crafted marketing strategy, companies can utilize Textnow account to build brand awareness, generate leads, and boost sales. By leveraging the features and capabilities of Textnow accounts, businesses can maximize their marketing efforts and effectively reach their desired audience.
Business Expansion With Textnow Accounts
Textnow Account can be a valuable tool for businesses looking to expand their reach and increase communication with their customers. By utilizing Textnow account, businesses can gather important market research and customer feedback that can be used to drive decision-making and improve products or services. This platform allows businesses to easily send surveys or conduct interviews to gain insights into customer preferences, needs, and pain points. Additionally, Textnow account enable businesses to communicate with customers in real-time, providing personalized support and building stronger relationships.
With its user-friendly interface and robust features, Textnow account offer businesses a cost-effective solution for effective and efficient communication. The ability to send messages, make calls, and even host video conferences all within the TextNow Account platform streamlines communication processes and saves valuable time and resources. With the increasing demand for seamless communication, integrating Textnow account into a business’s strategy can help facilitate growth and drive success.
Streamlined Customer Relationship Management
Textnow account are an essential tool for managing customer interactions and streamlining customer relationship management (CRM) processes. By integrating Textnow account with CRM systems, businesses can effectively track and manage customer communications, ensuring a seamless and personalized experience. These accounts provide a centralized platform for storing customer information, including contact details and communication history. With Textnow account, businesses can easily access and update customer information, ensuring that the latest data is always at their fingertips. This integration also allows for automated processes, such as capturing and logging customer interactions, creating follow-up tasks, and generating reports for analysis and improvement. By leveraging the power of Textnow account within CRM systems, businesses can enhance customer satisfaction, increase efficiency, and ultimately drive growth.
How Can I Create A Textnow Account?
To create a Textnow accounts, simply download the TextNow Account app and open it. Tap on the “Sign Up” button and follow the prompts to enter your desired username, password, and email address. Once you’ve completed the registration process, your Textnow account will be ready to use.
Is It Possible To Have Multiple Textnow Accounts?
Yes, you can have multiple Textnow account. Each account requires a unique email address during the registration process. Simply follow the steps to create a new account with a different email address, and you’ll be able to switch between your Textnow account within the app.
Can I Use Textnow Account On Multiple Devices?
Absolutely! TextNow Account allows you to use your account on multiple devices. Download the TextNow Account app on each device, and sign in using your account credentials. Your conversations, contacts, and other data will be synchronized across all devices, providing a seamless experience.
Are Textnow Accounts Free To Use?
Yes, Textnow account are completely free to use. The app offers free texting and calling services, which are supported by ads. If you prefer an ad-free experience or additional features, you can upgrade to a premium subscription plan, but it is not mandatory.

Conclusion
Overall, TextNow account provide a convenient and cost-effective solution for communication needs. With its free texting and calling features, users can stay connected with friends and family without worrying about expensive phone bills. Additionally, the ability to customize voicemail greetings and use the app on multiple devices adds to its versatility.
Whether you want a secondary number or an alternative to traditional phone plans, TextNow account offer a reliable and budget-friendly option. Experience the benefits of this user-friendly platform and enjoy seamless communication at your fingertips.
1 note
·
View note
Text
How to make sure about safety in online transaction:

How to make sure about safety in online transaction
Ensuring safety in online transactions is crucial to protect your financial information and personal data. Here are some essential steps to help you stay safe when conducting online transactions: see more
Use Secure Websites: Only make transactions on websites that are secure and reputable. Look for "https://" in the URL and a padlock symbol in the browser's address bar. These indicate a secure connection.
Keep Software Updated: Regularly update your operating system, web browsers, and security software. These updates often include security patches that protect against known vulnerabilities.
Use Strong Passwords: Create strong, unique passwords for your accounts. Use a combination of upper and lower case letters, numbers, and special characters. Avoid using easily guessable information like birthdays or names.
Enable Two-Factor Authentication (2FA): Whenever possible, enable 2FA on your online accounts. This adds an extra layer of security by requiring you to provide a second verification method, such as a code sent to your phone, in addition to your password.
Beware of Phishing: Be cautious of emails, messages, or links that ask for personal or financial information. Cybercriminals often use phishing scams to trick you into revealing sensitive data.
Verify Website Legitimacy: Before entering payment information, verify the legitimacy of the website by checking for reviews, reading the website's terms and conditions, and looking for contact information.
Use a Secure Payment Method: Whenever possible, use secure payment methods like credit cards or digital wallets, which offer more protection against fraudulent transactions. Avoid using debit cards for online purchases since they are directly linked to your bank account.
Monitor Your Accounts: Regularly review your bank and credit card statements for any unauthorized transactions. Report any discrepancies immediately to your financial institution.
Be Cautious with Public Wi-Fi: Avoid making online transactions over public Wi-Fi networks, as they may not be secure. If you must use public Wi-Fi, consider using a virtual private network (VPN) to encrypt your connection.
Secure Your Devices: Keep your devices secure with passwords or PINs. Use biometric authentication methods like fingerprint or facial recognition if available. Lock your device when not in use.
Be Wary of Impersonators: Be cautious if someone contacts you claiming to be from a financial institution or online service. Verify their identity independently before providing any information.
Educate Yourself: Stay informed about common online scams and fraud tactics. Knowledge is one of the best defenses against online threats.
Use Trusted Apps: If you're using mobile apps for transactions, download them from official app stores like the Apple App Store or Google Play Store. Be cautious of third-party app sources.
Regularly Backup Data: Back up important data regularly to avoid losing valuable information in case of cyberattacks or data breaches.
By following these best practices and staying vigilant, you can significantly reduce the risks associated with online transactions and protect your financial and personal information.
0 notes
Text
272 - First Impressions of iOS 17 With Guest Jill McKinley, Jeff Gamet, and Ben Roethig
The latest In Touch With iOS with Dave he is joined by guest Jill McKinley, Chuck Joiner, and Ben Roethig. iOS 17 was released to everyone this week. We discuss some of the new features including live transcripts of voicemails, standby mode, and more. Security updates released for all OS must install. Apple Watch double tap is not released just yet. iOS 17 tips including ping Apple Watch and Find My watch is set up. Much much more.
The show notes are at InTouchwithiOS.com
Direct Link to Audio
Links to our Show
Give us a review on Apple Podcasts! CLICK HERE we would really appreciate it!
Click this link Buy me a Coffee to support the show we would really appreciate it. intouchwithios.com/coffee
Another way to support the show is to become a Patreon member patreon.com/intouchwithios
Website: In Touch With iOS
YouTube Channel
In Touch with iOS Magazine on Flipboard
Facebook Page
Mastadon
X
Instagram
Spoutible
News
Imazing released Beta Version 3 : Introducing iMazing 3 (Mac Beta)
Apple Now Encrypts Titles of Voice Memos Stored in iCloud on iOS 17 and macOS Sonoma for Added Privacy
Apple TV Can Be Restored With an iPhone Starting With iOS 17
Apple Updates Pages, Keynote, and Numbers for iOS 17 and macOS Sonoma
Apple Releases watchOS 10.0.1 With Bug Fixes
watchOS 10.1 to Enable Apple Watch's New 'Double Tap' Gesture
iOS 17 makes it easier to play Spotify music on HomePod
Topics
Beta this week. No Beta iOS 17 was released to all.
Apple Releases iOS 17.0.1 and iPadOS 17.0.1 With Bug Fixes
https://www.apple.com/ios/ios-17/
First impressions of iOS 17 with the panel
Apple provided for the first time a New features available with iOS 17 PDF.
Here are some new items on iOS 17
Phone changes include a new button grid
add a contact poster. In Phone tap contacts and tap your contact card. Contact Photo & Poster
Live transcripts of voicemail. You can answer during the message.
Messages - all apps in one place
Customize the apps list Settings > Messages > iMessages Apps
Turn off messages apps you don’t use. Settings > Messages > Message apps and toggle off apps you dont want in that list.
Standby mode put on the charger in landscape mode
FaceTime record audio or video when missed call
Custom stickers
These features launch later this year. These iOS 17 Features Are Launching Later This Year
AirDrop contacts and photos bump phones
iOS 17 Tips
2FA authentication messages can be automatically deleted. Goto Settings > Passwords > Password Options > Turn on Clean up automatically Under verification codes.
In Find My you can now share an AirTag with someone. Open the AirTag and choose Share this item.
You can now set multiple timers.
Bring back haptic touch. Settings > Accessibility > Touch > Haptic Touch. Set it to fast for 3D Touch
Turn on Crossfade in Apple Music. Settings > Music > Crossfade and adjust seconds.
Add Ping My Watch in Control Center. Settings > Control Center and add. You can now ping your watch like you can your iPhone on the Watch,
Somona updates
Announcements
Macstock 7 2023 Virtual Pass is now available. Relive the conference as you can Purchase a virtual pass to see the talks that many of our regular guests and contributors did including Dave, Brittany, Chuck, and Jeff. https://macstockconferenceandexpo.com
Our Host
Dave Ginsburg is an IT professional supporting Mac, iOS and Windows users and shares his wealth of knowledge of iPhone, iPad, Apple Watch, Apple TV and related technologies. Visit the YouTube channel https://youtube.com/intouchwithios follow him on Mastadon @daveg65,
Twitter @daveg65.and the show @intouchwithios
Our Regular Contributors
Jeff Gamet is a podcaster, technology blogger, artist, and author. Previously, he was The Mac Observer’s managing editor, and Smile’s TextExpander Evangelist. You can find him on Mastadon @jgamet as well and Instagram as @jgamet His YouTube channel https://youtube.com/jgamet
Ben Roethig Former Associate Editor of GeekBeat.TV and host of the Tech Hangout and Deconstruct with Patrice Mac user since the mid 90s. Tech support specialist. Twitter @benroethig Website: https://roethigtech.blogspot.com
About our Guests
Jill McKinley is a professional in the field of enterprise software, server administration, and IT. She started her technical career in Windows but now exclusively uses a Mac in her personal life. She hosts several podcasts, including Start with Small Steps and Small Steps with God, where she offers tips and insights for a better life. Her podcast is at https://startwithsmallsteps.com and X @schmern.
Chuck Joiner is the host of MacVoices and hosts video podcasts with influential members of the Apple community. Make sure to visit macvoices.com and subscribe to his podcast. You can follow him on Twitter @chuckjoiner and join his MacVoices Facebook group.
Here is our latest Episode!
0 notes
Text
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can t use paypal with vpn
PayPal VPN restrictions
PayPal VPN restrictions refer to the limitations imposed by PayPal on users who access their accounts through a Virtual Private Network (VPN). VPNs are commonly used to enhance online security and privacy by encrypting internet traffic and masking the user's IP address. However, PayPal has strict policies against using VPNs, which can lead to various restrictions and complications for users.
When a user attempts to log in to their PayPal account through a VPN, PayPal's security systems may flag the activity as suspicious. This can result in the user being required to verify their identity through additional security measures, such as providing a phone number or answering security questions. In some cases, PayPal may even suspend or limit the user's account until they can confirm that the VPN usage was legitimate.
PayPal's VPN restrictions are in place to help protect users from fraudulent activities and unauthorized access to their accounts. By blocking VPN usage, PayPal aims to ensure that users are accessing their accounts from trusted and secure connections. While these restrictions may inconvenience some users who rely on VPNs for privacy reasons, PayPal views them as necessary to maintain the security of their platform.
To avoid running into issues with PayPal VPN restrictions, users should refrain from accessing their PayPal accounts through VPNs. Instead, it is recommended to use a secure and trusted internet connection when logging in to PayPal to prevent any account limitations or security challenges. By following PayPal's guidelines and accessing your account responsibly, you can help ensure a smooth and secure online payment experience.
PayPal account security measures
PayPal account security is crucial to ensure the safety of personal and financial information in today's digital age. To safeguard your PayPal account, it is essential to utilize various security measures provided by the platform.
One of the fundamental security features offered by PayPal is two-factor authentication. This extra layer of security requires users to not only enter their password but also verify their identity through a second method, such as a unique code sent to their mobile device. By enabling two-factor authentication, users can significantly reduce the risk of unauthorized access to their accounts.
Another important security measure is regularly updating your password and using strong, unique passwords for your PayPal account. A strong password should consist of a combination of letters, numbers, and special characters to make it harder for hackers to crack. It is also advisable to avoid using easily guessable information, such as birthdays or names, in your password.
PayPal also provides users with the option to set up email and text notifications for account activity. By enabling these notifications, users can stay informed about any significant changes or transactions made on their account. This allows for immediate action in case of any suspicious activity.
Furthermore, users should be cautious of phishing attempts and only log in to their PayPal accounts through the official website or app. Phishing emails and websites often mimic legitimate platforms to trick users into disclosing their login credentials. It is essential to verify the authenticity of any communication received from PayPal to prevent falling victim to phishing scams.
In conclusion, by implementing these security measures and staying vigilant against potential threats, PayPal users can enhance the protection of their accounts and enjoy a safer online payment experience.
VPN and PayPal transactions
Title: Enhancing Security: Using VPN for PayPal Transactions
In an era where cyber threats loom large, safeguarding online transactions has become paramount. Among the myriad of tools available, Virtual Private Networks (VPNs) stand out as a robust solution for bolstering security, particularly when it comes to PayPal transactions.
VPN technology encrypts your internet connection, routing it through a secure server, thereby shielding your online activities from prying eyes. When conducting PayPal transactions, this encryption plays a pivotal role in safeguarding sensitive information such as account details, financial data, and personal credentials.
One of the primary benefits of using a VPN for PayPal transactions is anonymity. By masking your IP address and encrypting your connection, a VPN obscures your online identity, making it significantly harder for malicious actors to trace your transactions back to you. This added layer of anonymity not only protects your privacy but also mitigates the risk of identity theft and fraudulent activities.
Moreover, VPNs provide an extra layer of security when accessing PayPal accounts on public Wi-Fi networks. Public Wi-Fi hotspots are notorious hunting grounds for cybercriminals, who exploit vulnerabilities to intercept data transmitted over the network. By using a VPN, users can create a secure tunnel between their device and the internet, shielding their PayPal transactions from potential eavesdropping and hacking attempts.
Furthermore, VPNs enable users to bypass geo-restrictions and access PayPal services from anywhere in the world. This flexibility is particularly advantageous for travelers or individuals residing in regions where PayPal services are limited or restricted.
In conclusion, integrating a VPN into your online security arsenal can significantly enhance the safety and privacy of PayPal transactions. By encrypting your connection, ensuring anonymity, and bypassing geo-restrictions, VPNs provide a robust defense against cyber threats, empowering users to transact with confidence in an increasingly digital landscape.
PayPal geolocation restrictions
PayPal, the popular online payment platform, implements geolocation restrictions to ensure the security of its users' accounts and prevent fraudulent activities. Geolocation restrictions refer to the practice of monitoring and limiting access to PayPal accounts based on the geographical location of the user.
These restrictions are in place to protect users from unauthorized access to their accounts from unfamiliar locations. When a user tries to log in to their PayPal account from a different country or region, PayPal may flag this activity as suspicious and prompt additional verification steps to confirm the user's identity.
Geolocation restrictions also help PayPal comply with local regulations and anti-money laundering laws. By monitoring the geographic locations of its users, PayPal can detect and prevent potentially fraudulent transactions that may originate from high-risk countries or regions.
It is important for PayPal users to be aware of these geolocation restrictions to avoid account limitations or suspensions. Users traveling abroad or relocating to a new country should update their account information with their current location to prevent any disruptions in accessing their funds.
Overall, PayPal's geolocation restrictions play a crucial role in safeguarding the security and integrity of its platform, ensuring a safe and reliable payment experience for users worldwide. By staying informed and complying with these restrictions, PayPal users can enjoy peace of mind while conducting online transactions securely.
VPN bypass methods for PayPal restrictions
In recent years, PayPal has implemented various restrictions and limitations on its platform, often frustrating users who rely on its services for online transactions. One common issue faced by PayPal users is geographic restrictions, which can prevent access or limit functionality based on the user's location. However, there are several VPN (Virtual Private Network) bypass methods that users can employ to circumvent these restrictions and regain access to PayPal's full range of features.
Firstly, utilizing a reputable VPN service is essential. VPNs reroute internet traffic through encrypted servers located in different regions, effectively masking the user's true IP address and location. By connecting to a VPN server in a region where PayPal restrictions are less stringent or nonexistent, users can bypass geographical limitations and access their PayPal accounts with ease.
Another effective method is to use dedicated IP addresses offered by VPN providers. These IP addresses are less likely to be flagged by PayPal's security systems, reducing the risk of encountering restrictions or being blocked from accessing the platform.
Additionally, employing advanced VPN protocols such as OpenVPN or WireGuard can enhance security and improve the likelihood of successfully bypassing PayPal restrictions. These protocols offer stronger encryption and better performance, making them ideal choices for users seeking to circumvent geo-blocks and access PayPal from restricted regions.
It's important to note that while VPN bypass methods can be effective in overcoming PayPal restrictions, users should always exercise caution and adhere to PayPal's terms of service. Engaging in fraudulent or prohibited activities using VPNs can result in account suspension or permanent bans. Therefore, users should use VPNs responsibly and solely for legitimate purposes when accessing PayPal from restricted regions.
0 notes
Text
How To Reset SengLED Light Bulb In Just A Few Minutes
Is your SengLED light bulb not responding? And you don’t know how to reset SengLED light bulb. I can help you fix that issue.
In addition, if you are facing issues with Alexa Connect, I can also help you with how to connect SengLED Bluetooth bulb to Alexa. As well, I will guide you on how to connect SengLED bluetooth bulb to Google Home.
How To Reset SengLED Light Bulb: A Step-By-Step Guide
Make sure that the bulb is in a standard on-off fixture. No dimmers, variable power setting switches such as low, medium, or high switches, or ceiling fans of any kind can be used with these bulbs. The inconsistent flow of electricity that such fixtures supply is damaging to the bulbs.
Turn the bulb off.
Wait 5 seconds.
Turn the bulb on.
Wait 5 seconds.
Repeat steps 4 and 5 five times.
Bulbs blink twice after three flashes. The bulb has reset.

Why Are Sengled Bulbs Special?
There are several reasons why stranded light bulbs vary. Here are some popular ones:
Sengled light bulbs provide connection choices such as Bluetooth, Wi-Fi, and Zigbee. Bluetooth lamps need a direct smartphone connection, but Wi-Fi bulbs may be operated from anywhere with an internet connection. If you have several smart home devices, Zigbee lights can establish a mesh network with a hub.
Sengled light bulbs provide functions such as dimming, color change, and scheduling. Voice control and motion detection are available on certain lamps.
The lumen output of a light bulb measures its brightness. Sengled smart light bulbs have different lumen outputs, so you may select the best one.
The color temperature of a light bulb indicates its warmth or coldness. Sengled light bulbs come in several color temperatures, so you can pick the right environment.
The lifetime of a light bulb is the number of hours it is predicted to endure. Sengled light bulbs last 25,000 hours, longer than incandescent lights.
Price: Seungled light bulbs cost around $10 to $50. The bulb’s features, connection, and lumen output determine its pricing.

How To Connect To The Sengled Home App?
Get Sengled Home on iTunes or Google Play. To add Wi-Fi LEDs and accessories to the app, click the “+” button in the upper right and open the app.
Make sure that your bulb is in pairing mode. To do this, turn the bulb on and off quickly five times.
The bulb will appear in the list of devices. Tap on it. Select “Next” after entering your Wi-Fi password.
When you do that, the bulb will join your home’s wireless network.
You can follow the in-app prompts to add your bulb to a room.
Some additional considerations:
Use the same Wi-Fi network as the one on your phone or tablet.
For bulb connection issues, restart your phone or tablet, network, and bulb.
You may manage many Sengled bulbs at once by grouping them.
The Sengled Home App allows scene creation. A scenario pre-programs bulb brightness, color, and on/off status.

When To Reset Your Sengled Light Bulbs
There are a few reasons why you might need to reset your Sengled bulbs.
Smart bulbs may experience unresponsiveness issues when connected to virtual assistants like Alexa, Google Assistant, or Siri. The bulb can be reset to fix software issues.
Your Wi-Fi network is changing. You must reset your lights to connect them to a new Wi-Fi network.
Issues with the bulb. Sometimes smart lights switch on unexpectedly or flicker continually. The bulb may be reset to solve these issues and enhance the user experience.
You’re providing bulbs. Before gifting your Sengled bulbs to a friend or family member, reset them. This will make putting up the bulbs easy for the future owner.
READ ALSO: How To Brighten Up Your Home With LED Magic Light Bulbs In 2023
How To Connect Sengled Bluetooth Bulb To Alexa?
Turn on and link your Sengled Bluetooth light. Press and hold the bulb reset button for 10 seconds. The light blinks twice after flashing three times to signal coupling.
Launch Alexa and hit “Devices”.
Use the top-left “+” button.
Tap “Skills & Games”.
Find and tap “Sengled” under skills.
Tap “Enable Skill”.
Log in to Sengled.
Alexa will find your Sengled Bluetooth light when you sign in.
Tap the bulb to pick it up.
Tap “Pair”.
The bulb will be added to Alexa.

How To Connect Sengled Bluetooth Bulb To Google Home
A Sengled Bluetooth bulb can be paired with Google Home by pressing and holding the reset button for 10 seconds. The next step is to launch the Google Home app, tap the “+” icon, choose “Set up device,” and finally choose “Bluetooth.” The bulb will appear in the list of devices.
Tap on it and enter the passcode that appears on the bulb. The bulb will be added to your Google Home devices. Once the bulb is connected, you can control it with your voice.
READ ALSO: Dimmable LED Flashing: Why And How To Fix It?
Bottom Line
I think you have enough ideas about how to reset your SengLED light bulb.
It’s easy to reset your Sengled light bulb to fix connectivity issues or set it up. These instructions may vary slightly depending on your Sengled model, so consult the manufacturer’s instructions.
0 notes
Text
Mobile App Scraping for Retail | eCommerce
How to Leveraging Mobile App Scraping for Retail Success?
July 13, 2023
Mobile apps have become a vital consumer shopping channel in today's post-pandemic world. With smartphone users spending an average of over 3 hours on their phones daily, it's clear that mobile apps are increasingly preferred over traditional eCommerce apps. Recognizing this shift, Mobile App Scraping has introduced an innovative mobile app scraping solution to complement its successful eCommerce app scraping technology. This advanced solution is designed to help businesses thrive in the evolving retail landscape.
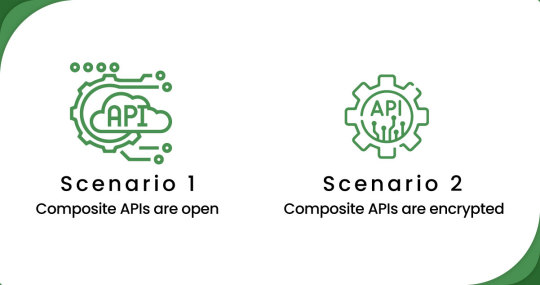
Scenario 1:
When composite APIs are open (e.g., Amazon) - In such cases, the scraping process is similar to standard app scraping, with some initial setup required. Mobile App Scraping can utilize the available APIs of platforms like Amazon to access and extract the desired data. The process involves making API requests, handling responses, and parsing the retrieved data.
Scenario 2:
Whenever composite APIs get encrypted (e.g., Dollar General, HEB, Target, Stop & Shop, etc.) - This scenario presents a more complex challenge. Mobile App Scraping employs specialized techniques such as mobile device extraction, OCR (Optical Character Recognition), as well as other machine learning methods to overcome the encryption and extract data from these apps. Mobile App Scraping leverages advanced technologies to navigate the encrypted APIs and interfaces, ensuring accurate and reliable data extraction.
In both scenarios, Mobile App Scraping utilizes its expertise and advanced methodologies to scrape mobile apps efficiently and effectively, providing businesses with valuable data insights to enhance their operations and decision-making processes.
Methodology
Step 1: Recording a mobile session/navigation using unique visual navigation scrapers Technology consideration
Mobile App Scraping employs a virtual device cloud infrastructure to ensure scalability and efficiency. It utilizes an emulated cluster of devices that connect through an intelligent proxy network.
In the first step of the methodology, special visual navigation scrapers are utilized to record mobile sessions and navigation. These scrapers interact with the mobile app interface, mimicking user actions and capturing the relevant data. This approach allows Mobile App Scraping to navigate the app, access different screens, and interact with various elements to gather the desired information.
To achieve scalability, a virtual device cloud infrastructure is employed. This infrastructure emulates a cluster of devices, ensuring that the scraping process can be performed at scale. Additionally, an intelligent proxy network handles communication between the devices and the app, ensuring efficient data retrieval.

Step 2: Identify product ROI (Region of Interest)
To accurately scrape text for each product, Mobile App Scraping utilizes an Object Detection algorithm to identify the ROI of individual products within a frame, regardless of the number of products present.
The input files are passed through a custom fine-tuned version of the YOLOv5 (You Only Look Once) architecture, which excels in fast and accurate inference. YOLOv5 can swiftly detect and localize each product's ROI within the frame.
Since a video typically consists of multiple frames per second, the exact product ROIs are possible. To address this, a deduplication stage is introduced. This stage eliminates identical product ROIs, allowing faster and more efficient data processing. The resulting ROIs from the video frames are then cached as images, ready for further analysis and extraction.
Step 3: Identify product components
In this stage, Mobile App Scraping focuses on identifying specific components of the products, such as price, product information, product image, and more. The same components to be identified may vary based on the specific mobile app being scraped.
To achieve precise component identification, Mobile App Scraping applies YOLOv5 again, but with a different instance or configuration compared to Step 2. This allows for more granular consideration in detecting and localizing the desired components within the product ROIs.
Step 4: Extract components with OCR
In this stage, Mobile App Scraping completes the textual extraction process now that all details of the products have been identified. A custom-trained OCR (Optical Character Recognition) framework is deployed to achieve this.
The OCR framework is specifically trained to recognize and extract text from the identified components of the products. It utilizes advanced algorithms and machine learning techniques to accurately extract textual information such as product names, prices, descriptions, and other relevant details.

Step 5: Accessing the final output
In the final stage, the text extraction output and relevant metadata are stored in a database. Mobile App Scraping applies unit tests and quality checks to ensure the accuracy and integrity of the extracted data.
Once the data is verified and validated, it is transformed into the desired format suitable for the client's needs. This transformation process ensures the information is structured appropriately and ready to be accessed, sent, uploaded, or requested via API (Application Programming Interface).

Conclusion
In conclusion, as the retail landscape evolves with the rise of mobile and social commerce and the emergence of the metaverse, the need for advanced AI and analytics becomes paramount. Mobile App Scraping recognizes this need and is dedicated to providing retailers and brands with sophisticated and accurate analytics across the retail ecosystem. They have developed an cutting-edge mobile app scraping solution to cater to the evolving needs of the retail industry.
Moreover, Mobile App Scraping has extended its proprietary technology to the metaverse, enabling the scraping of retail stores in virtual platforms like Decentraland, Roblox, Sandbox, Meta, and more. This expansion reflects their commitment to staying at the forefront of technological advancements and ensuring that retailers have access to critical data and insights across multiple platforms.
With the growing popularity of mobile commerce and the increasing competition in the retail space, mobile app scraping has become essential for maintaining competitive prices, assortments, and digital shelf ranking. By leveraging Mobile App Scraping's cutting-edge solutions, retailers can stay ahead of the curve and make informed decisions based on accurate and real-time data.
In summary, Mobile App Scraping offers innovative mobile app scraping solutions alongside their established eCommerce app scraping technology, empowering retailers to thrive in the dynamic retail landscape and meet the demands of modern consumers.
#Scrape Retail App Data#Mobile App Scraping for Retail#Retail App Scraper#Extract Retail Mobile App Data#Retail app scraping service
1 note
·
View note
Text
Is It Safe to Buy Stuff From TikTok Shop?

What is TikTok Shop?
Seemingly every other video on the social media platform has a button that appears right above the caption; when you tap on it, it takes you to a virtual store where you can order crop-top bras, Lion Latches or personalized tumblers without ever leaving the TikTok app.
It’s easy to use — but is there a catch? As with any online retailer, you should know what you’re getting into before you type in your credit card number.
According to the company, TikTok Shop is very much still in a development phase. It soft-launched in November and moved to beta testing this past April.
Since its inception in 2016, TikTok has proven to be so much more than a silly dance app — it’s a business powerhouse where users love to discover, review and share products. (Need proof? The hashtag #tiktokmademebuyit has over 64 billion views.)
Is TikTok Shop safe?
TikTok says merchants are vetted before they can launch on TikTok Shop, and once they’re live, they must follow a set of guidelines that prohibits fake, fraudulent or misleading content. When someone makes a purchase, the company collects data “to provide our shopping features and facilitate the purchase and delivery of products, goods and services,” according to its privacy policy.
But TikTok doesn’t actually handle the payment itself — it uses the third-party services PayPal and Stripe to process the transaction.
PayPal and Stripe are considered relatively safe; they both use encryption to guard folks’ financial data. TikTok also claims it doesn’t store customers’ personal information after they buy an item.
Even so, Don Grant, a certified financial planner, says to proceed with caution.
“Those who post on TikTok want something from you,” he points out. “The TikTok platform wants something from you. If that ‘something’ is of value, viewers may only know it once it’s missing.”
How does TikTok Shop make money?
Here’s the rub: TikTok takes a cut of shop sales from merchants, so it has a vested interest in getting you to shop — and splurge — in the app.
The company has big plans for expansion, too. The Wall Street Journal reported last month that the social platform is gearing up to launch a marketplace called the TikTok Shop Shopping Center. The Atlantic wrote that “TikTok’s turn to e-commerce, in theory, has the potential to be massive, capable of competing with the likes of Amazon.”
How to shop responsibly on TikTok
The TikTok Shop interface is so smooth that “you can basically click on something and buy it in a matter of seconds,” says shopping expert Trae Bodge. It reduces the pain of paying, a behavioral economics concept that refers to the unpleasant feelings a person gets when they spend money.
That “pain” is important because it regulates people’s desire to buy stuff. When it goes away — say, because you’ve seen 50 increasingly convincing bra videos and the button to buy one is right there — so is that self-regulation.
“Because of the ease of shopping, people don’t take the time to read reviews or look for ways to save more,” Bodge says. “That ease is a gateway for potential overspending, or less informed spending, on the general internet.”
She recommends slowing down and pausing whenever possible. Sure, TikTok Shop might be convenient, but it means you might miss out on discounts and coupons offered by other vendors elsewhere online.
Before mindlessly throwing things into your cart on TikTok Shop, Grant suggests you ask yourself two crucial questions: 1) “Do I really need this?” and 2) “Is there another platform that I trust from which I can purchase the same product or service?”
The answers will guide you.
More from Money:
The Best Deals Around Are in Your Local ‘Buy Nothing’ Facebook Group
How to Protect Yourself from Identity Theft
Is It Risky to Give My Phone Number to Stores and Restaurants?
Read the full article
0 notes