#cybersecruity
Text

What is Security Testing And Types of Security Testing
Businesses and governments are highly impacted by the increasing number of cyber attacks and threats in today’s virtual world. Such attacks mainly target the customers’ data the organization serves. Therefore, there is a constant need to ensure the organization’s security. This is where Security Testing plays a crucial role.
#pci dss compliance#pci dss saq#pci software security framework#pci secure software standard#pci secure software lifecycle#iso 27001 audit#GDPR.risk assessment#vulnerability assessment#Cybersecruity
0 notes
Text
2023: PRC Freedom of Information Blogger Ruan Xiaohuan Persecuted
A Chinese language interview with imprisoned Chinese freedom blogger Ruan Xiaohuan on the Conversations with Yuan Li Bumingbai podcast gives insights on Ruan’s core beliefs and influences, including the ethos surrounding the open software and freedom of information that propelled the social construction of USENET and the Internet in its early days as well as a portrait of a young Chinese couple…
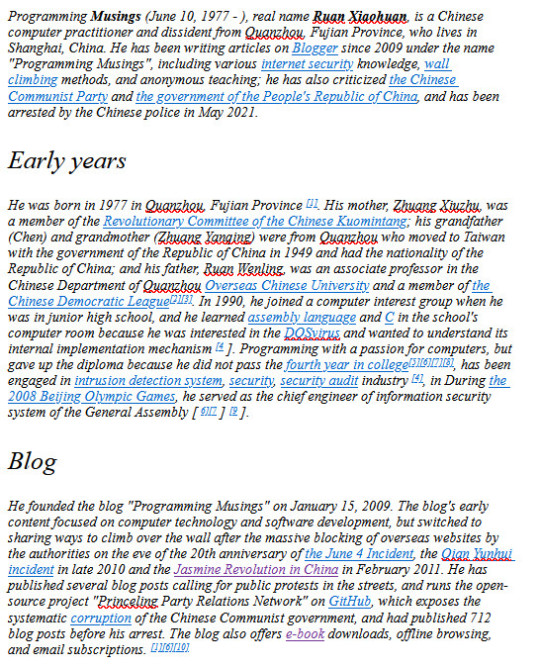
View On WordPress
#arrest#blog#China#Chinese#Communist Party#courts#cybersecruity#cybersecurity#编程随想#detention#expression#阮晓寰#顛覆政權罪#firewall#freedom of expression#freedom of thought#GNU#Guobao#hacker#judicial#law#legal system#overthrow#PRC#prosecution#Public Security#regime#Ruan Xiaohuan#speech#system
1 note
·
View note
Photo

0 notes
Text
Know the Skill-set Required to be Successful in Cybersecurity
Among the careers that have become relevant and highly-sought after over the past decade or so is cybersecurity. Those who successfully acquire their certification from a professional institute of ethical hacking embark on an even more successful career in the days to come. However, it also needs to be remembered that nobody can be a successful cybersecurity professional unless they have a specific skill-set. Anyone can, indeed, complete a course and be trained for all events and eventualities at an institution. Without the innate skills, however, it is a given that they are not going to go too far in their quest for a successful career. With that in mind, discussed below are the skills that one needs to have to be a preeminent cybersecurity expert.

Here are the Skills Need to be a Successful Cyber-security Expert
• Incident Handling and Appropriate Response
It can be rather easy to get bogged down in situations that require a cool head, even for a qualified professional. However, when a skilful and cool-headed person is at the helm of the affairs of handling incidents of cybersecurity breaches, their response is in keeping with whatever needs to be done to undo the situation.
• Audit and Compliance
It is imperative for an ethical hacking professional to ensure that they are up to date in their knowledge with the entire audit and compliance related matters. If somehow, anything gets overlooked, then the company can stand to pay hefty fines for non-compliance. Basically, the professional should be able to review the company’s compliance with the regulations in place. If anything in particular needs to be ironed out, then they should be able to do so.
• Analytical Skills and Intelligence
When someone decides to learn ethical hacking, the institute where they get trained imparts all the necessary knowledge into the person. However, there need to be ingrained analytical skills on part of the individual, so that when they are practising their profession, and some security situation comes up, he or she should be able to detect the cause and solve the matter as soon as possible.
• IDS/IPS/Firewall Skills
The thing that needs to be understood is the importance of a firewall in an organisation as far as being able to prevent unauthorised access into a network is concerned. The professional needs to have a thorough understanding of firewalls. Additionally, he or she also needs to have a sound knowledge of Intrusion Prevention Systems (IPS) and Intrusion Detection Systems (IDS) and know how they work with the firewall of an organisation to keep security breaches at bay.
There are the skills that one needs in order to be successful as a cybersecurity professional. With the number of breaches as high as they are in recent times, it can be safely said that the demand for such professionals is going to skyrocket in the days to come. If he or she has the above skills, then even the sky would fall short of being the limit for the success that can come their way.
0 notes
Text
JRL NEWSWATCH: "American Hustle; What Mueller Found-and Didn't Find-About Trump and Russia" - Foreign Affairs/ Stephen Kotkin
JRL NEWSWATCH: “American Hustle; What Mueller Found-and Didn’t Find-About Trump and Russia” – Foreign Affairs/ Stephen Kotkin
“… Russian intelligence organizations had no need to collude with the … Trump campaign. They could manage entirely on their own to hack e-mail accounts, line up cutouts such as WikiLeaks to disseminate damaging material, impersonate Americans on social media, and study elementary research available in open sources about battleground states and swing voters. * * * … The report is incomplete in…
View On WordPress
#Cybersecruity#Donald Trump#FBI#Internet#JRL NewsBlog#Mueller#Newswatch#Rodham Clinton#Russia#Russiagate#Russian News#Social Media#Spies#U.S. Elections#U.S.-Russian Relations
0 notes
Photo

International Cyber Deal Won by Rafael
Managing sensitive financial information and combating cyber threats are imperative for the safety and continuity of financial institutions. One of the major components of cybersecruity strategy is the establishment of SOCs - Security Operations Centers. RAFAEL Advanced Defense Systems was
https://i-hls.com/archives/98570
#cybersecurity#Dominican Republic#financial sector#Israel#Rafael#Business Security#Cyber Crime#Cyber Security#InnoTech Expo#News#South America#Technology News#Video News
0 notes
Text
Technology in films and games
Technology is apart of our everyday lives. We use our phones, TV's to watch and communicate with others. Technology is always portrayed differently in films however some show how it is behind the protective scenes the public have. One example would be the tv show ‘Mr. Robot’ a show about a young anti-social computer programmer Elliot who works as a cybersecruity engineer during his days while at night he works as a somewhat vigilante hacker. He gets recruited by a mysterious leader of a underground group of hackers who are tasked with taking down corporate America while also including the company Elliot works for, presenting him with moral dilemmas.
In my opinion the show it self represents technology in a bad way as it shows the true nature of company's with money while also showing the danger without security. This is presented as we see how server hacks are done but also the influence this has on the person doing it. We can see Elliot lose parts of himself during this phases which could be related to his social disorders.
This show portrays both sides of cybersecruity. We see how it is used to protect both servers and data for the company's which is meant to be the good side. Its where the hero is while we also see the hacking and servers being taken down while data is being stolen and leaked. This represents the good and bad in technology as a whole.
0 notes
Photo

Google Launches Its First CyberSecruity Company, Chronicle Google Launches Its First CyberSecruity Company, Chronicle
0 notes
Link
A senior Securities and Exchange Commission regulator said public companies will soon face new guidelines for how they report cybersecruity breaches to investors.
0 notes
Text
New cybersecruity vulnerability with fitness monitors Digital Journal
SNPX.com : New cybersecruity vulnerability with fitness monitors Digital Journal http://dlvr.it/PtGglV
0 notes
Text
Capital OneVoice: Back to School: Uncovering Tech-Savvy Classroom Cheating
McAfee, the antivirus company, found that 62% of US students in their 2017 Cybersecruity 101: Teens in the Classroom survey reported seeing or hearing of another student using a connected device to cheat on an exam, quiz or project. Naturally, only 29% admitted to doing it themselves.
from Forbes Real Time http://www.forbes.com/sites/capitalone/2017/08/17/back-to-school-uncovering-tech-savvy-classroom-cheating/
via IFTTT
0 notes
Photo

0 notes
Text
How did the HBO hack happen? A cybersecurity expert has 2 theories
A massive HBO hack resulted in high profile episodes from Game of Thrones, Ballers, and Insecure being leaked. Cybersecruity expert Roderick Jones details two theories that explain how HBO could have been hacked and the ramifications.
The post How did the HBO hack happen? A cybersecurity expert has 2 theories appeared first on Digital Trends.
from Computing–Digital Trends https://www.digitaltrends.com/movies/hbo-hack-explained/
0 notes
Text
This is Why We Booked Tech Profits…
This post This is Why We Booked Tech Profits… appeared first on Daily Reckoning.
We’re screwed.
Federal Reserve chair Janet Yellen tempted the fates Tuesday, declaring that we won’t see another financial crisis in our lifetimes.
“Would I say there will never, ever be another financial crisis? You know probably that would be going too far but I do think we’re much safer and I hope that it will not be in our lifetimes and I don’t believe it will be,” Yellen said.
Unfortunately, the market gods were listening.
They were not amused…
The Nasdaq shed 100 points by the closing bell. That’s a drop of more than 1.6%, plummeting the composite near one-month lows. The S&P 500 and the Dow also finished the day on their lows…
We’ve tracked the potential for a tech stock selloff since shares showed their first signs of exhaustion weeks ago. Investors set their crosshairs on tech stocks, with the FAANG brigade (Facebook, Amazon, Apple, Netflix and Google) and semiconductors taking most of the heavy damage yesterday.
2017 has been all about the big tech stocks. Every financial fluff piece has marveled at their unstoppable strength. It should come as no surprise that the cap-weighted Nasdaq Composite is still up more than 14% year-to-date – even after factoring in yesterday’s selloff.
But if these conditions persist, as we noted back on June 5th, it could be time for this winner-take-all market to share some of its spoils. We’ve already seen unloved sectors like small-caps sneak higher as mega-cap tech falters. Now the big banks are catching a bid amid the tech weakness.
That’s why we cashed in some of our big tech winnings earlier this month. After posting gains of more than 30% in less than six months, it’s time for these over-loved stocks to take a break…
Even the news cycle is now beginning to turn against the exuberant bulls.
We recognize that politics and the markets are two separate beasts. But plenty of investors are counting on Republicans to score legislative victories this year. So we’re already hearing about backlash after lawmakers have decided to delay the health care bill vote until after the July 4th holiday.
Too many holdouts are getting in the way of passing the bill that would ultimately repeal and replace the Affordable Care Act. That’s made some investors wonder whether anything will get done at all…
“While this bill is important to some sectors, market participants are more concerned about the GOP’s ability to push through tax reforms (which are already priced into the market)” The Wall Street Journal’s Daily Shot notes.
Oh, and don’t forget the massive cyberattack that shook the globe yesterday.
“A new cyberattack similar to WannaCry is spreading from Europe to the U.S. and South America,” Bloomberg reports, “hitting port operators in New York, Rotterdam and Argentina, disrupting government systems in Kiev, and disabling operations at companies including Rosneft PJSC, advertiser WPP Plc. and the Chernobyl nuclear facility.”
You’ll no doubt recall the ransomware cryptoworm WannaCry. WannaCry takes over files and demands $300 to restore access. According to multiple media reports, more than 200,000 computers in at least 150 countries initially fell prey to the hack last month. Cyber threats are becoming a bigger issue by the day. That’s probably good for our cybersecruity plays in the long-run, but bad for short-term market sentiment.
Now we have the Fed running victory laps, political bickering and unprecedented cyber warfare dominating the financial news. After an incredible first half of the year for stocks – especially tech names – a summer pullback is in the works.
You’re already perfectly positioned to handle additional market weakness. We’ll remain on the lookout for any new “rotation trades” as the long weekend approaches…
Sincerely,
Greg Guenthner
for The Daily Reckoning
The post This is Why We Booked Tech Profits… appeared first on Daily Reckoning.
0 notes
Text
Manager, Advanced Vehicle Electronics
Mitsubishi Motors R & D of America, Inc. Location : Ann Arbor MI US Provide daily direction to Engineers. Telematics, Cybersecruity, V2V & V2X communications. Develop and apply formal training plans for Engineers…. More >> Tweet
Manager, Advanced Vehicle Electronics was originally published on Autonomous Vehicle Jobs
0 notes
Text
Data Privacy Series 1: Malware and Cybersecurity
There are so many terms that are prevalent on the Internet like malware, spyware, ransomware, but it may seem impossible to know what all these terms mean, and how they affect your devices and personal information.
A virus is classified as a self-replicating piece of malicious code that travels by inserting itself into files or programs. The cyber landscape has changed to more than just viruses and can cause much more damage. All the threats on the Internet landscape are types of malicious software, and therefore now fall under the “malware.” Malware is another term used to identify any form of malicious software on the Internet landscape from annoying adware to devastating ransomware.

Malware can cause extremely annoying behaviors such as generating an overabundance of pop up advertisements or causing your computer to run slowly. This type of malware is not classified as a virus; however, it can still negatively affect a computer and can even introduce other security risks. Some that can cause annoying behaviors are adware or spyware. Malware that is malicious aims to steal data from your machine or can cause data corruption. Some examples are ransomware or a Trojan horse.
Getting malware to protect your devices and personal information can be done in many ways. You can download programs to your device, file share, or use scareware.
Cybersecurity is the body of technologies, processes, and practices designed to protect networks, computers, programs and data from attack, damage or unauthorized access. Cyberspace is exceptionally difficult to secure due to a couple of factors: the linkages between cyberspace and physical systems and the difficulty of reducing vulnerabilities and consequences in complex cyber networks.

As information technology becomes increasingly combined with physical infrastructure operations, there is an enlarged risk for wide-scale events that could cause harm upon which our economy and the daily lives of millions of Americans depend. Considering the risk and potential consequences of cyber events, strengthening the security and resilience of cyberspace has become an important homeland security mission.
0 notes