#daily browser offer message
Text
Setting up AO3 Enhancements on a mobile browser
Hey there! Do you:
read fic primarily on your phone?
feel tired of having to punch in a lot of filter tags every time you browse for fics?
have an android device?
then I might be able to help you make fandom a cozier place! (and hopefully nip future drama in the bud, lol)
With this post, I'm gonna guide you through the process of installing the AO3 Enhancements browser extension, normally only available on desktop, on your mobile device. It works a charm, and I've been using it for months, and it's made the Undertale tag navigable again despite my utter disinterest in AU content.
Here's an archived version of the full post in case my dumbass accidentally deletes it for some reason
Let's get started!
UPDATE: For IOS users! You can download the browser app "Orion" which allows firefox extensions! No need to do this procedure, just install it and download the extension as you normally would from Firefox Add-ons
1) Download Firefox Nightly.
For those who are hearing of it for the first time, Firefox Nightly is a separate Firefox browser made specifically for developers. The name itself is due to the fact that it's patched and updated on a daily (er, nightly) basis. This makes it more prone to crashing and issues than the standard Firefox app, but I've switched over to nightly as my main browser months ago now, and if I ever encounter a problem, I just... download the latest update and I'm good to go.
What's crucial about Nightly, however, is that it gives the user access to various additional features. One of them being desktop extensions on mobile, which is what we're here for.
Here's the Google Play link.
2) Make a Firefox Account
This will be necessary to install the extension later
Once you've done that, go to the Firefox add-ons website and log into your account in the upper right (where it says "Biscia" in the screenshot below). Click on "View My Collections"
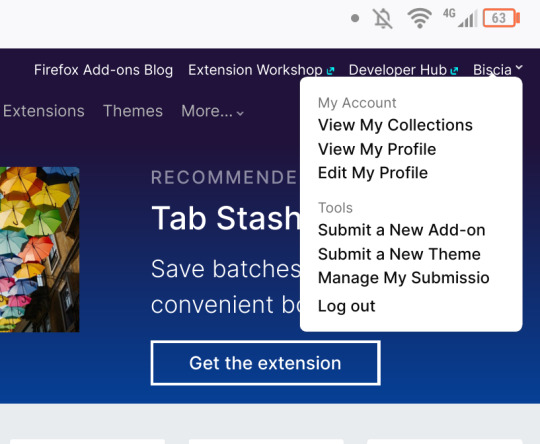
3) Making an add-on collection
Since browser extensions are technically blocked from being directly installed by the browser, Nightly offers a workaround.
Create a collection, and give it a name without spaces to avoid errors.
4) Adding the extension
Here is the link to ao3 enhancements (if it's not showing up, try reloading the page in desktop mode). Scroll down until you see the option "Add to a collection" and select the one you just created.
You can do it with any extension! Go nuts. There's lots of good stuff out there. Just remember that it's not guaranteed every one of them will work, since they aren't intended to be used on a mobile device.
5) Activating debug mode.
In your browser, tap the little sandwich menu in the bottom right, scroll down and click Settings. It should be under "Save to Collection".
Scroll down even more until you reach the "About" section, and click on "About Firefox Nightly"

Click on the firefox logo 5 times, and it should be done.
6) Activating your add-ons
Go to "View my profile" as seen in the screenshot in step 2. At the end of the link, there should be a string of numbers. Copy it.
After this, go back to the browser settings again, scroll down until you reach the add ons section and click on "custom add on collection". Paste the numbers you copied from your profile where it says "User ID", and the name of your collection EXACTLY as it appears in the link, where it says "Collection name". Mind, it's case sensitive.
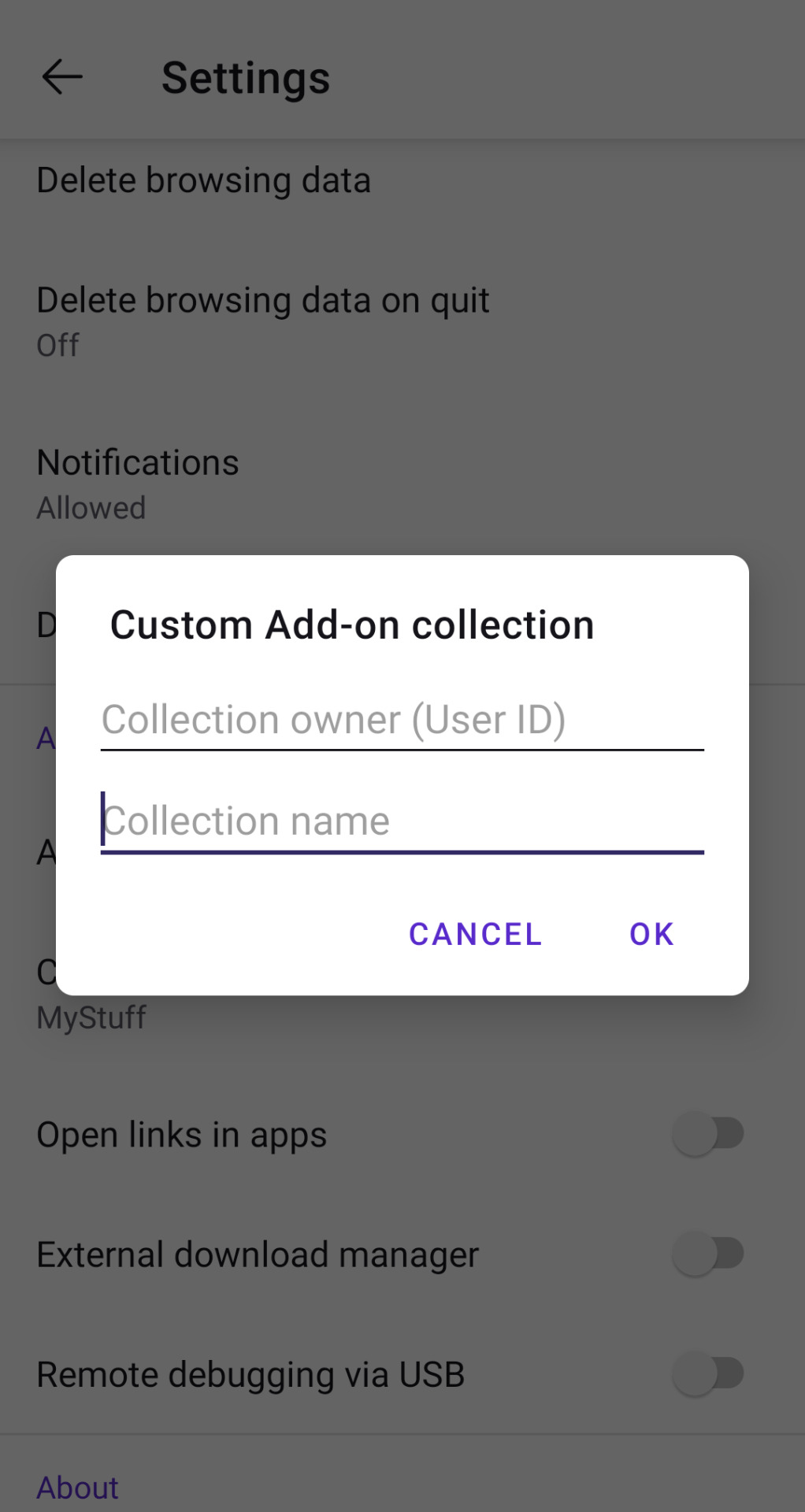
Press okay, and it should kick you out of the app. Open it again and, going in add-ons then add-ons manager, you should be able to add your extension.
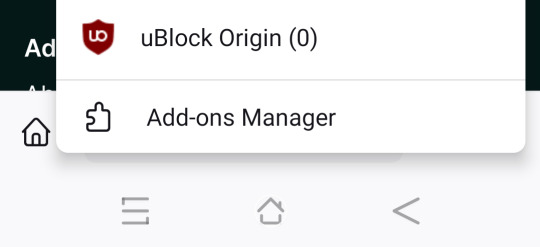
ATTENTION!! If you get the error message "failed to query add-ons" you either inputted the wrong user id or the wrong collection name
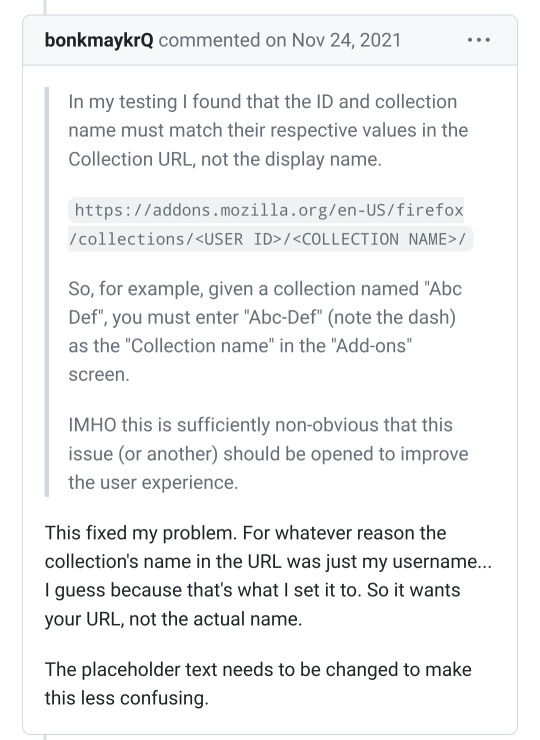
To avoid this type of issue, don't name your collection something that has spaces or punctuation in it, as it might mess with the link formatting.
7) Setting up your AO3 enhancements filters
If everything's worked out fine, you should be able to visit ao3 and see a new drop-down window.
Click on it, click on option, and it should open up a new window with all the settings available! Tweak them to your heart's content. Though mind, the background tag wrangling done by the ao3 volunteers doesn't work with this extension, so the extension is going to hide only the works tagged EXACTLY what you filtered. Character for character. This makes things a bit tricky when people aren't consistent with their tagging, but if it proves to be enough of a problem, you can just filter out the author name in full and be done with it.
You can choose to hide the fic behind a "show" button, or make it not show up at all. If you choose the latter option, and you blocked a tag that has lots of fics, it might look like certain pages of searches are almost empty, since all the fics were hidden.
And that's it! I sincerely hope this helps people avoid their triggers and other topics that make them uncomfortable. No more excuses fellas. You find a tag you haven't filtered yet? You add it to the list and move on. Easy peasy.
Hope I haven't missed anything. Let me know if you need any help!
2K notes
·
View notes
Note
22 and 23 for Canada or America or both? I adore your writing so much.
🥺🥺🥺 thank you!! I'll do both.
22: Given a blank piece of paper, a pencil, and nothing to do, what would happen?
With a very low tolerance for boredom, America snatches the paper before Canada has a chance to react. His first instinct is to make a paper airplane and doodle some designs on it; an eagle on one wing, perhaps a catchphrase on the other, and a wreath of flames as an outline. Before letting it soar, he asks Canada if he wants to add something to the little plane. Canada draws a maple leaf and he paper airplane flies perfectly.
But I'd be wary of leaving America with nothing to do for too long. Now, Canada? Not a problem. He can easily slip into dreamland and imagine himself in a canoe, fishing for rainbow trout along freshwater, backcountry rivers for hours at an end. But America craves stimulation and if he's in a rather bad mood, he'll try playing Five Finger Filet with the pencil and his own hand. He's immortal and if he makes a mistake, it'll heal quickly anyways, right? Canada nags him as soon as he starts playing, and with enough passive aggressive fuss, America rolls his eyes and flips the pencil eraser-side down.
However, if America's in a good mood, and there's still nothing to do, he'll explain how worm holes work, by folding the paper in half and poking the pencil through it; a trademark method that appears in every Hollywood sci-fi film. Slightly forgetful, he doesn't realise that he's explained this to Canada many times before, but Canada doesn't interrupt. Instead, he offers up a few questions and lets his brother babble about the spacetime continuum until the sun goes down, not because it keeps America occupied, but because America loves the topic, and has a wonderful habit of turning anything he loves into something genuinely interesting through his own sheer excitement. Even when said topic involves a lot of heavy math.
23: How organized are they? How does this organization/disorganization manifest in their everyday life?
I'd give them both a 5/10 when it comes to their organizational skills. Part of this is because they're physically younger than their Old World counterparts; college-aged nations with some college-aged habits. However, I think it's also woven into their personalities a bit.
⭐ America ⭐
Leaves empty soda bottles in his pickup truck
100+ tabs open in his internet browser
No sorting system to the catalogue of video games on his shelves
Bad habit of buying gadgets he won't use
Sports & Hollywood memorabilia cluttering the walls
Unpaid credit card bills
Low-priority government docs MUST be labeled, otherwise he'll lose them
"It's fine, I'll clean it later," and "I know where everything is," are his mantras. His mess doesn't bother him and it rarely impacts his daily life. However, if certain people are coming to visit, (senators, the President, certain nations that make him uncomfortable, etc.,) then America will definitely tidy up.
🍁 Canada 🍁
Often 5 - 20 minutes late to everything
Forgets to do his laundry; wears dirty blue jeans
Some fresh fruits and veggies go bad before he uses them
Cannot fit a car in his garage because it's filled with hiking gear and old woodworking tools
Too many canoes
Unless it's important, he forgets to respond to text messages
Spaces out during meetings, asks for notes, misplaces the notes
Unlike his brother, Canada's disorganization gives him anxiety and he chastises himself for it. He'll tidy up in a panic at the last minute when guests are on their way.* Then, he's the type to say, "Sorry, my place is a mess right now," even if he just finished cleaning and only forgot to dust one bookshelf. Truly, he should cut himself some slack once in a while.
*The only exception is America. If he's the guest, Canada won't panic-clean. He'll just sort a few things out and welcome his brother inside no matter the state of his house.
Excessively Detailed Headcanon Meme
#aph america#aph canada#hws america#hws canada#alfred f jones#matthew williams#hetalia headcanons#my writing#ask game#sorry that got a bit long#i also struggle with organization so it's easy to relate to these boys#my headcanons
63 notes
·
View notes
Text
REBELFORUMS v.1.0.2.3 THREAD TAG:53173EXPRNC, 53173FINDS TYPE: HACK/LEAK
USERCODE: ThatsDefinitelyJelly
I got a copy of the MoJ OS, specifically the one used on their computers, it seems they have their own social media/forum board too.
What it says on the tin, they pretty much have their own chatter going on around the internet.
The copy seems to have belonged to someone else or is just unlocked somehow, here is what i found.
-So first of all, the accounts rarely have any usernames and instead use random codes of numbers and flairs seem to be the only way to find out atleast something of the person like an advocate or doctor flair.
-The platform seems to be simply named "MoJ Online Social Network".
-Settings seem to be quite simple, it registers where are you, what device you are using, the time, etc. however there doesn't seem to be things such as a block or report button, knowing the ministry this is most likely due to a certain group of personnel being in charge of monitoring the platform at all times.
-Out of curiosity i began snooping around threads and other users accounts to see if i found anything interesting and all i can say is that there is a lot to dig into.
-Most of the posts are just like, well celebrations, daily routine in the MoJ and such.
However i find it quite silly that they seem to be aware of the existence of rebel forums.
Some discussions related to the last point seem to always talk about taking our sites down, calling us unruly and you know the usual which isn't really surprising and tbh i kinda giggled reading all of those comments from scientists and personnel saying how we "need correction" and stuff.
Besides that there is also the discussions about marmalisation and happy stuff, also some advocates showing crafts, drawings or art in general that of course is mostly about happy things.
Digging deeper i found discussions about future MoJ projects but these discussions were locked and only specific flairs could reply to these, possibly due to their classified nature.
There was also a live tab that only seems to work when something like the fear test or that show of the felix guy is live, basically whenever a MoJ show or game is available the tab goes live.
I might add more things i found in the discussions in another post but for now, moving on.
There is a message/email inbox, it surprisingly can take even TERABYTES of information or files which i have to admit is quite impressive.
There was also a tab for updates or patches to the platform, which had your typical bug error fixes and stuff but what caught my attention is that apparently there is a platform related to oblivion as well, however the description seems to be vague so if any eclipse rebels are reading this feel free to leave anything you might have found related to this in the comments.
Moving on from the MoJ Online Social Network, lets move on to the other things this OS has to offer!
-The weather, time, date and curiously enough how many people the smiler has marmalised.
-There is pre-set folders to store information about advocates, personnel and other data, of course since this PC isn't completely connected to the MoJ it doesn't have any profiles in there or anything.
-There is your typical minesweeper, solitaire and strangely enough purble place but themed to the ministry, i found it quite silly.
-Your usual media player and photo display
-Customization seems to be limited, there is pre-set wallpapers and colors, the only thing that seems to be more open is the fonts.
-The internet besides the aforementioned social media seems to also be made by the MoJ, specifically a browser, now here is where things get truly interesting:
I said this browser was made by the MoJ, so it means it has access to basically an ENTIRE database server of them which it means i can definitely extract media, classified files and other things with ease BUT there is a catch, some of these files and pieces are titled as specific serial numbers or digits to prevent leaks...but that is NOT gonna stop me.
I'll try to see what i can find and give you all updates if there is something interesting i wanna show.
During the documentation of this post i came to the realization this is basically a very much modified and i mean very MODIFIED version of 'Windows 7' which means that if you know the knicks and knacks of PCs, coding and stuff you might have A LOT of things to archive and leak with just a few clicks and taps, lookin' at you Joy-Leakers and co.!
Anyway, CYA all! Will keep you all updated, specially if i manage to make another copy of this OS to dump here!
2.4k Dots - 560 replies
4 notes
·
View notes
Text
The Evolution of Media and Its Impact on Surveillance and Privacy Issues: A Family Legacy of Control?
Let's dive into the rabbit hole and explore how the evolution of media over time has led to the surveillance and privacy issues we face today in our digital world, and how one family's legacy might be influencing it all.

Let's rewind to the 1940s and 1950s when television was this fresh new medium on the block. Back then, programming was pretty limited, but as TV sets became more affordable and widespread, content started to diversify and reach broader audiences. The role of television in society began to grow, and with it came the government's increasing influence over media narratives.
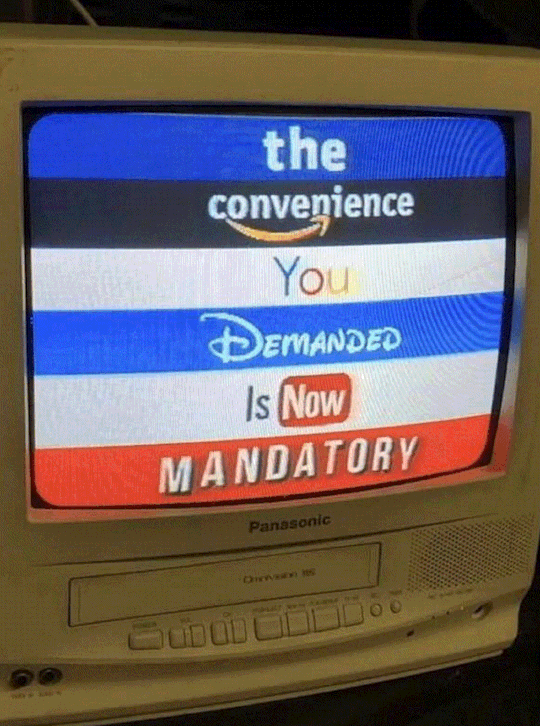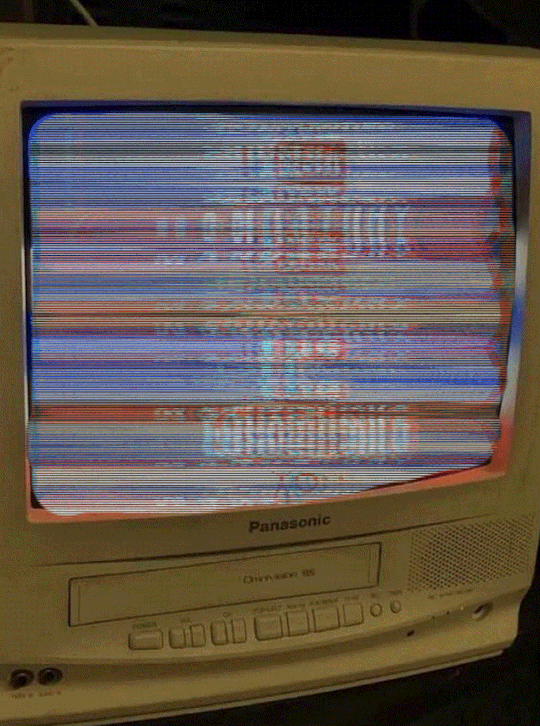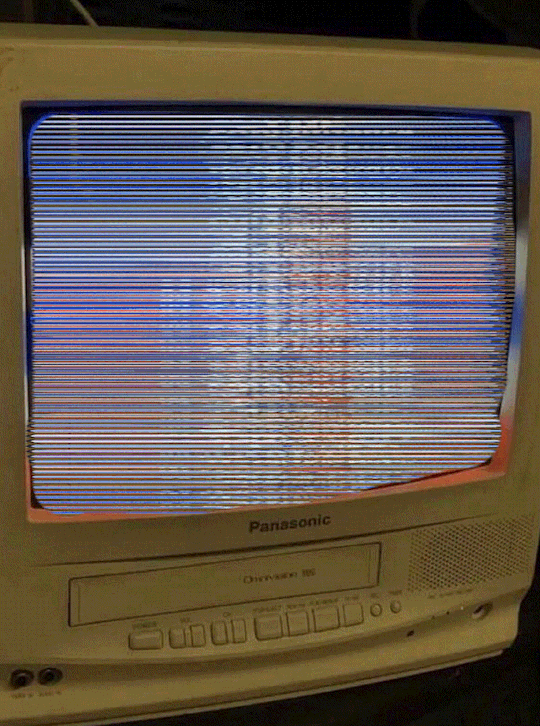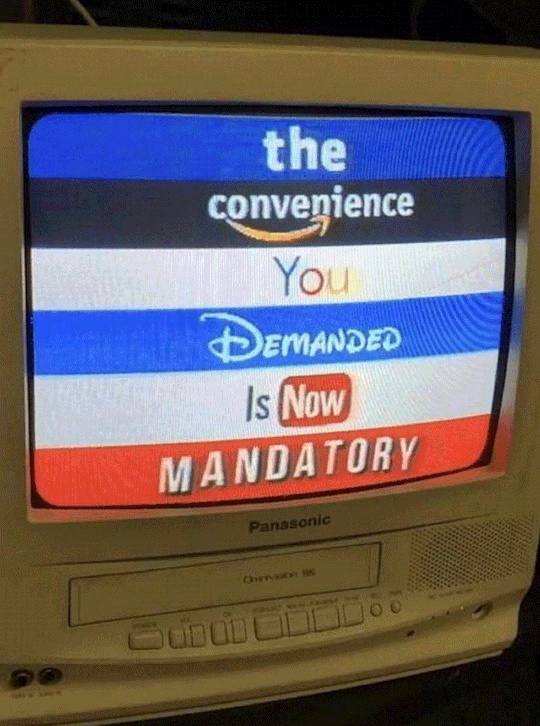
The 1960s saw TV become even more politically engaged, with news outlets giving more coverage to social and political issues, like the civil rights movement and the Vietnam War. As television continued to evolve and diversify, it became a crucial tool for governments to spread their messages and manipulate public opinion.

Now let's fast forward to the present day, where the digital age has taken media to a whole new level. We consume information through various platforms, from social media to streaming services, which offer governments even more opportunities to collect data and keep an eye on us. And it's not just Big Brother watching us; we live in a world of browser cookies and sophisticated algorithms that track our every move.

Enter Edward Bernays, the "father of public relations," who believed that by understanding human behavior, one could create a more compliant and easily controlled society. It's no coincidence that his grand-nephew, Marc Randolph, went on to become the first CEO of Netflix. The connection between media and manipulation runs deep in that family tree!

My hypothesis is that the studies and observations of Sigmund Freud, the founding father of psychoanalysis, have been passed down through the generations, from Bernays to Randolph. As a result, their methods and practices have evolved alongside media, making their influence on society even more potent.

We can't talk about surveillance and privacy issues without mentioning the Patriot Act. Passed after the 9/11 attacks, this controversial legislation gave the government unprecedented access to our personal information without a warrant. This invasion of privacy has led to numerous lawsuits against the government for spying on its own citizens.

The evolution of media over time has played a pivotal role in shaping the surveillance and privacy issues we face today. As media continues to evolve and become more integrated into our daily lives, we need to stay vigilant and question the motives behind the narratives we're fed. The legacy of Freud, Bernays, and Randolph serves as a stark reminder of the power that media and manipulation can have over society.
- JOREEEZY
https://k4v3.com/

12 notes
·
View notes
Text

#JakeReviewsItch
1977: Radio Aut
by Alex Camilleri
Genre: N/A
Pitch: A visual short story documenting the true struggles of an anti-Mafia activist Peppino Impastato in mid-20th century Sicily.
My expectations: The Itch page provides a one-sentence description and no screenshots. Pretty gutsy. I have absolutely no idea what to expect.
Review:
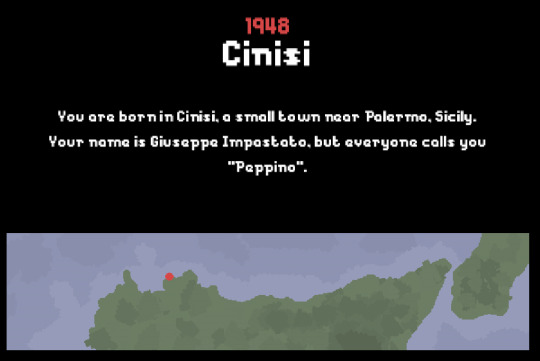
Prior to 1977: Radio Aut, I’d never heard of political activist Giuseppe "Peppino" Impastato or his efforts to free the Sicilian town of Cinisi from Mafia control. It’s a great story… in the wrong format.
1977: Radio Aut casts players as Peppino, presenting his story through text, illustration, mood-setting audio, and interactive decisions.
The 8-bit-ish style looks fine, but thematically, it’s completely out of place. Text is often difficult to read, not helped by a number of typos—significant issues in a game that’s mostly about reading words.
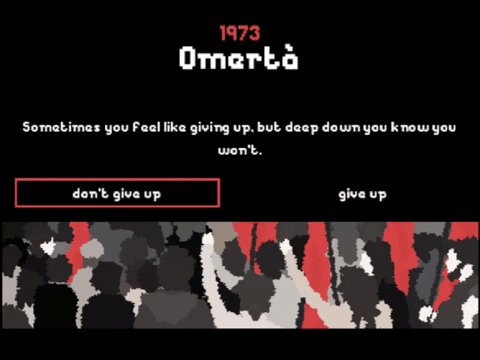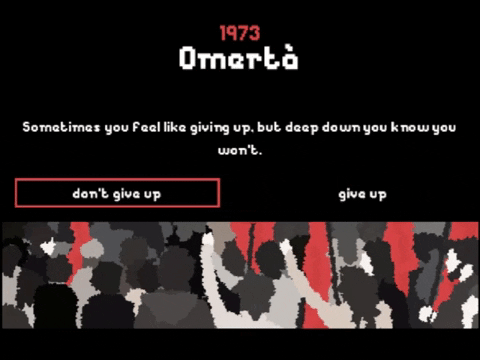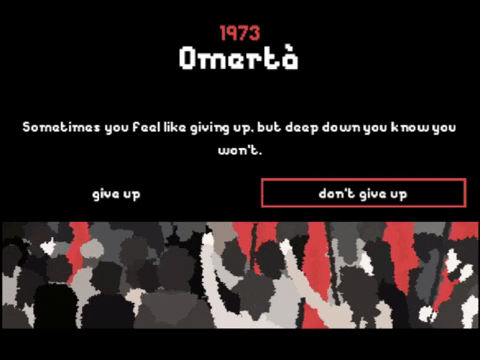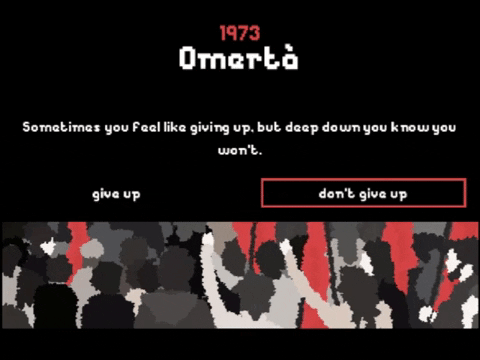
By my rough tally, there are 104 text screens, 26 of which ask for player input. Not a bad ratio, except that most offer only a single option or otherwise prevent the story from going down the wrong path. That leaves just seven screens with two selectable choices, and none of those make any difference, because this is a true story about a real person. It only happened one way.
Why not show Peppino’s story from another point of view, casting players as a fictional Cinisi resident, pulled between Mafia intimidation and Radio Aut’s call to action? Why not make a YouTube video? Or a Tumblr post? This medium doesn’t suit the message.
+ A great, true story I'd never heard before, and might not have ever heard otherwise.
+ Despite my complaints about playing the role of Peppino, the second-person narrative structure is a reminder that you, the one playing the game, have the power to fight for change.
+ Fully playable in a browser for free. Start to finish, you're looking at 5-10 minutes
– What's the point of interactive fiction without interactivity?
– Games have the power to put players in a place and time, encouraging empathy and understanding in a unique way. 1977 speeds through decades of Peppino's life, giving an overview of a few major turning points, but rarely pausing to consider the texture of his life or the small steps toward big action.
– Wikipedia says Peppino's newsletters and broadcasts were full of satire and puns. A joke or two would have gone a long way in this deadly serious downer.
– Text is difficult to read.
🧡🧡🤍🤍🤍
#JakeReviewsTwitch is a series of daily game reviews. You can learn more here. You can also browse past reviews...
• By name
• By rating
• By genre
#JakeReviewsItch#Reviews#Computer Games#Video Games#Itch.io#1977: Radio Aut#Radio Aut#Giuseppe Impastato#Peppino Impastato#Mafia#Cinisi#Sicily#Italy#Anti-mafia#Activism#True Story#Interactive Fiction#Visual Novel#Socialism
2 notes
·
View notes
Text
she will cheat porn new 0DCR+
💾 ►►► DOWNLOAD FILE 🔥🔥🔥🔥🔥
Pornhub Porn Videos She Will Cheat - Bored Asian Wife Mai Li Needs Some Bbc She Will Cheat – Dava Foxx's Worthless Cuckold Husband Sit There And. 'she will cheat' Search, free sex videos. SheWillCheat - Tia Cyrus Ride Black Cock While Husband Is At Work. k % 9min - p. Watch as horny slutwives cheat on their clueless husbands in beautiful 4K video. These pornstar hotwives live out their fantasies in everything from. She Will Cheat Porn Videos! - Touch My Wife, Do The Wife, Bigcockbully Porn - SpankBang. Enjoy of She Will Cheat porn HD videos in best quality for free! It's amazing! You can find and watch online She Will Cheat videos here. Offering exclusive content not available on Pornhub. Pornhub provides you with unlimited free porn videos with the hottest adult performers. Enjoy the largest amateur porn community on the net as well as full-length scenes from the top XXX studios. We update our porn videos daily to ensure you always get the best quality sex movies. Thank you for your contribution in flattening the curve. The Free Premium period has ended, you can continue to help by staying home and enjoying more than , Premium Videos from more than studios. Get Free Premium No thanks, continue to pornhub. Warning: either you have javascript disabled or your browser does not support javascript. To view the video, this page requires javascript to be enabled. Member login Access your Pornhub or Pornhub Premium account. Logging in. Remember me on this computer not recommended on public or shared computers. Don't have an account yet? Sign Up here. Forgot Username or Password? Resend confirmation email. A text message with your code has been sent to:. Didn't receive the code? Don't have your phone? Please contact support. You are now leaving Pornhub. Go Back You are now leaving Pornhub. All Professional Homemade. Duration minutes. All HD. Most Relevant. Rank: She Will Cheat. Spicevids videos. Japanese estrus wife! She want to be fucked by cock, so she appears adult video. Her libido couldn't Spicevids. Her libido couldn't Japanese Amateurs Pounded. Searches Related to "she will cheat".
4 notes
·
View notes
Text
Best Productivity Tools in 2022

When it comes to productivity, there are a lot of different tools out there that can help you get the job done. But with so many options available, it can be hard to know which ones are actually worth your time.
To help you out, we've rounded up some of the best productivity tools that you can use to make your work easier and more efficient. From task management apps to document collaboration platforms, these tools will help you get the most out of your day.
So without further ado, here are the best productivity tools that you should start using today:
DeskTime
DeskTime is a productivity app that lets you track your time, plan and track your projects, and calculate costs simultaneously.
The project cost tracking feature lets you fill in your hourly rate and calculates automatically how much you have to charge the client based on the time you’ve spent on a specific task or project.
Kill News Feed
Kill News Feed is a Chrome extension that blocks your News Feed on Facebook when you need to focus on work. Knowing that the habit of scrolling Facebook News Feed is a real productivity killer, this simple extension is a serious focus-booster and time saver.
If you use Facebook for work purposes – worry not! While you won’t be able to see and scroll your newsfeed, you’ll still be able to check your messages and notifications and access your business pages.
LastPass
Like 1Password, LastPass saves all your passwords, so you only have to remember one – your master password. Contrary to 1Password, LastPass has a free version, which is perfect enough to use without the upgrade.
Install the extension on your browser, then start saving your passwords to LastPass – it will automatically offer you to save a password when you log in to a new website for the first time. Once saved, you’ll be able to log into the sites with one click.
Google Alerts
If you’re looking for info on a specific topic but don’t want to spend all day searching the web for the most recent news, then set up a Google Alert. Enter the keyword you’re looking for and customize by selecting which sources you want, how often you wish to be notified, etc.
You’ll receive emails whenever anything is published about that specific topic. Set it to notify you how often you like. I suggest once at the end of the day to avoid constant distractions and updates.
Grammarly
Whether your daily tasks are directly related to loads of writing, or you’re only sending a few emails from time to time, a language-checking tool always comes in handy.
Meet Grammarly (if you haven’t met it yet) – an AI-powered tool that helps the written communication. Correcting your grammatical mistakes is just one of the many amazing things that the tool does. It also suggests improvements for clarity, engagement, delivery, and more, based on your audience and goals that can be variously adjusted.
Source: https://desktime.com/blog/the-great-list-of-25-productivity-tools-to-try-in-2021
2 notes
·
View notes
Text
stepmom cheats new NQW!
💾 ►►► DOWNLOAD FILE 🔥🔥🔥🔥🔥
Check out free Cheating Stepmom porn videos on xHamster. Watch all Cheating Stepmom XXX vids right Pampered Stepmom Cheats With Stepson - Family Therapy. stepmom cheats with son FREE videos found on XVIDEOS for this search. Horny Wife Cheats With Her Stepson! 5 minBang My Stepmom - M Views. Watch Stepmom Cheats With Stepson porn videos for free, here on Discover the growing collection of high quality Most Relevant XXX movies and. Free featured cheating stepmom porn videos on xHamster for New videos every day! Explore tons of XXX movies with hot sex scenes ready to be watched. Watch stepmom cheats on her spouse with his son on SpankBang now! - Priapus, Jackerman, 3D Porn - SpankBang. Offering exclusive content not available on Pornhub. Pornhub provides you with unlimited free porn videos with the hottest adult performers. Enjoy the largest amateur porn community on the net as well as full-length scenes from the top XXX studios. We update our porn videos daily to ensure you always get the best quality sex movies. Thank you for your contribution in flattening the curve. The Free Premium period has ended, you can continue to help by staying home and enjoying more than , Premium Videos from more than studios. Get Free Premium No thanks, continue to pornhub. Warning: either you have javascript disabled or your browser does not support javascript. To view the video, this page requires javascript to be enabled. Member login Access your Pornhub or Pornhub Premium account. Logging in. Remember me on this computer not recommended on public or shared computers. Don't have an account yet? Sign Up here. Forgot Username or Password? Resend confirmation email. A text message with your code has been sent to:. Didn't receive the code? Don't have your phone? Please contact support. You are now leaving Pornhub. Go Back You are now leaving Pornhub. Pornhub Literacy , learn more about our commitment to trust and safety! All Professional Homemade. Duration minutes. All HD. Most Relevant. Stepmom cheats with stepson while husband is on the phone Erin Electra. Stepmom cheats with stepson Erin Electra. Oh god, stepmother! Don't cheat on your father, at least let me put on a condom Sasha Paradise. Stepmom cheats with stepson MissLatinDoll. Alina Rai. Stepmom got a foot massage and then stepson fucked her hard Luna Roulette. Spicevids videos. Searches Related to "stepmom cheats with stepson".
3 notes
·
View notes
Text
stepmom cheats working K2I&
💾 ►►► DOWNLOAD FILE 🔥🔥🔥🔥🔥
Check out free Cheating Stepmom porn videos on xHamster. Watch all Cheating Stepmom XXX vids right Pampered Stepmom Cheats With Stepson - Family Therapy. stepmom cheats with son FREE videos found on XVIDEOS for this search. Horny Wife Cheats With Her Stepson! 5 minBang My Stepmom - M Views. Watch Stepmom Cheats With Stepson porn videos for free, here on Discover the growing collection of high quality Most Relevant XXX movies and. Free featured cheating stepmom porn videos on xHamster for New videos every day! Explore tons of XXX movies with hot sex scenes ready to be watched. Watch stepmom cheats on her spouse with his son on SpankBang now! - Priapus, Jackerman, 3D Porn - SpankBang. Offering exclusive content not available on Pornhub. Pornhub provides you with unlimited free porn videos with the hottest adult performers. Enjoy the largest amateur porn community on the net as well as full-length scenes from the top XXX studios. We update our porn videos daily to ensure you always get the best quality sex movies. Thank you for your contribution in flattening the curve. The Free Premium period has ended, you can continue to help by staying home and enjoying more than , Premium Videos from more than studios. Get Free Premium No thanks, continue to pornhub. Warning: either you have javascript disabled or your browser does not support javascript. To view the video, this page requires javascript to be enabled. Member login Access your Pornhub or Pornhub Premium account. Logging in. Remember me on this computer not recommended on public or shared computers. Don't have an account yet? Sign Up here. Forgot Username or Password? Resend confirmation email. A text message with your code has been sent to:. Didn't receive the code? Don't have your phone? Please contact support. You are now leaving Pornhub. Go Back You are now leaving Pornhub. Pornhub Literacy , learn more about our commitment to trust and safety! All Professional Homemade. Duration minutes. All HD. Most Relevant. Stepmom cheats with stepson while husband is on the phone Erin Electra. Stepmom cheats with stepson Erin Electra. Oh god, stepmother! Don't cheat on your father, at least let me put on a condom Sasha Paradise. Stepmom cheats with stepson MissLatinDoll. Alina Rai. Stepmom got a foot massage and then stepson fucked her hard Luna Roulette. Spicevids videos. Searches Related to "stepmom cheats with stepson".
2 notes
·
View notes
Text
wife cheats porn trainer 9PEE+
💾 ►►► DOWNLOAD FILE 🔥🔥🔥🔥🔥
POV College Milf Cheating Sucking dick in public while her husband is away. Neyney the Nympho. показов. Mega Sims- Cheating wife cheats. 'cheating-wife' Search, free sex videos. Cheating Wife Husband Doesn't Mind Vintage porn with hunky guy and busty milf. Check out free full-length Cheating Wife porn videos on xHamster. Watch all Cheating Wife XXX vids right now! Watch Free Porn Videos Of Cheating Wife With Other Men. CLICK To See Unfaithful Wives Getting Pregnant On Youporn. 'cheating wife' Search, free sex videos. Cheating On Husband In Real Time FakeAgentUK Unexpected threesome surprise from cheating wife. Offering exclusive content not available on Pornhub. Pornhub provides you with unlimited free porn videos with the hottest adult performers. Enjoy the largest amateur porn community on the net as well as full-length scenes from the top XXX studios. We update our porn videos daily to ensure you always get the best quality sex movies. Thank you for your contribution in flattening the curve. The Free Premium period has ended, you can continue to help by staying home and enjoying more than , Premium Videos from more than studios. Get Free Premium No thanks, continue to pornhub. Warning: either you have javascript disabled or your browser does not support javascript. To view the video, this page requires javascript to be enabled. Member login Access your Pornhub or Pornhub Premium account. Logging in. Remember me on this computer not recommended on public or shared computers. Don't have an account yet? Sign Up here. Forgot Username or Password? Resend confirmation email. A text message with your code has been sent to:. Didn't receive the code? Don't have your phone? Please contact support. You are now leaving Pornhub. Go Back You are now leaving Pornhub. All Professional Homemade. Duration minutes. All HD. Most Relevant. Add Friend. Cheating Wife. Doctor fucks her ass while she is talking on the phone with her boyfriend Sweetbuttocks. I let the mover fuck me quick and hard Rosa Josefin. Cheating on her husband before work Samantha Flair Official. She got cum all kisankanna. Cheating wife asks him to take off the condom and cum inside SexwithCami. I filmed myself fucking a friend's girlfriend while he was looking at it! MMF Marido cornudo se folla a su mujer tras el fontanero. Esposa compartida FMM par3jahorny. Cheating Wife meets her lover at a hotel - 4K misslexa. Cheating partners in front of them- WetKelly Wet Kelly. We fucked all night long. Indigo Sin. While the husband does not see the wife Fucks with a neighbor in the dorm DickForLily. The Dick Suckers. Spicevids videos. Japanese estrus wife! She want to be fucked by cock, so she appears adult video. Her libido couldn't Spicevids. Her libido couldn't Japanese Amateurs Pounded. Horny wife cheats husband with a black guy while husband is out of town Spicevids. Horny wife cheats husband with a black guy while husband is out of town Big Boobs At Play. Searches Related to "cheating wife".
1 note
·
View note
Text
Top 5 Android Phones Of 2012
Some say that Google is on a diehard mission get over the business. They already have a world-dominating search engine, PPC program, Android OS, Google maps with an eerily accurate portrayal of everyone's neighborhood, and much considerably! What other Google features can you think of off the the surface of your head? Lots, we're sure! If you can't think of any more, we know what you will do, you'll Google the application!
365 Puzzle Club - A new number puzzle every day's the holiday season! 365 Puzzle Club has 3 modes of play: Calendar mode offers a meaningful puzzle daily, Seasonal mode offers a gradual increase of different puzzle types, or practice on quickplay way. Play games such as Sukodu, Tempenki, and Kakuro.
And a lot of say this Gphone's QWERTY keypad just isn't as nice as it could be, in which may be true, wish to realize the alternative on similar phones: no physical keypad at every bit.
If you mastered the Android games and apps already along the device you happen to be ready to branch to you browser based Apps like Facebook and Twitter. fairly simple as both have mobile optimized web website.
A year or two ago, such high-tech tracking systems enjoy been the stuff of science trouvaille. But with easy to use, affordable Android GPS apps, anyone with an Android phone maintain a track on his/her phone instantly time. You happen to be amazed in the accuracy of these apps as they can pinpoint the location among the phone exactly. If you are anxious where your phone (or rather, its user) is, these apps are just wonderful.
If you happen to be huge NFL fan, this app always be on your phone. Desires to give a great app personal for game day or if perhaps you're just like me and prefer to look up every stat for every player! Assassins Creed Odyssey Gold Edition Free Download full version is classy my entire life too crowded.
The HTC Tattoo is really a GPRS and Wi-Fi enabled handset, allowing the users to access the Internet. Through GPRS, you must be take the support of network providers in order to access the World-wide-web. On Assassins Creed Odyssey Gold Edition torrent , Wi-Fi facilitates you to obtain unlimited access of Internet at the Wi-Fi covered places. Websites can be surfed on its browser that supports HTML verbiage. SMS, MMS, Email and IM end up being the messaging features of this nice device to stay in touch with special loved one. Through Bluetooth connectivity you can transfer info to other compatible devices wirelessly. Moreover, this device can get in touch with other gadget through USB data cable via USB dock.
If good for your health to watch on them remotely, the particular 'hidden' apps would serve your needs better. By simply cooking you simply need to know where these kinds of in case of an emergency, the 'visible' kind would do good the right amount. In the end, the sort of Android GPS app invest in will depend upon what quite needs and budget. You're able to easily discover the wide selection of apps from the Android store and see which ones fit your needs. The more features and power you want, a lot you ought to prepared invest. But on the inside end, equipped to see to learn where your kid set in case a good emergency keepin in mind the expense.
2 notes
·
View notes
Text
Unveiling the Power of Meokapp Login: A Comprehensive Guide
In the fast-paced digital age, where convenience and efficiency reign supreme, Meokapp login emerges as a beacon of seamless accessibility and user-friendly navigation. As avid users of the platform, we understand the importance of unlocking its full potential and harnessing its myriad features to streamline our daily tasks. In this comprehensive guide, we delve deep into the intricacies of Meokapp login, unraveling its functionalities, and empowering you to navigate the platform with ease and confidence.Introduction to Meokapp LoginUnderstanding the SignificanceMeokapp login serves as the gateway to a world of possibilities, offering users access to a plethora of services and resources tailored to their needs. Whether you’re a seasoned professional seeking to optimize your workflow or a novice exploring the platform for the first time, mastering the Meokapp login process is essential for unlocking its full potential.Navigating the InterfaceUpon logging in to Meokapp, users are greeted with an intuitive interface designed for seamless navigation. From the dashboard, users can effortlessly access various features and functionalities, including:Profile Management: Update personal information, preferences, and settings to tailor the Meokapp experience to your unique needs.Task Management: Organize tasks, set deadlines, and collaborate with team members to boost productivity and efficiency.Data Analytics: Gain valuable insights into performance metrics, track progress, and make informed decisions to drive growth and success.Communication Tools: Foster collaboration and communication with colleagues through integrated messaging and collaboration tools.Mastering the Meokapp Login ProcessStep-by-Step GuideVisit the Meokapp Website: Open your preferred web browser and navigate to the official Meokapp website.Locate the Login Button: On the homepage, locate the Login button typically situated in the top-right corner of the screen.Enter Your Credentials: Enter your registered email address and password in the designated fields.Click Login: Once your credentials are entered, click the Login button to access your Meokapp account.Explore the Dashboard: Upon successful login, you will be redirected to the Meokapp dashboard, where you can begin exploring its myriad features and functionalities.Tips for a Seamless ExperienceRemember Your Credentials: To expedite the login process, consider saving your login credentials securely or utilizing password management tools.Stay Updated: Keep abreast of any updates or enhancements to the Meokapp platform to leverage the latest features and improvements.Explore Tutorials and Resources: Take advantage of tutorials, guides, and online resources provided by Meokapp to enhance your proficiency and maximize productivity.Enhancing Productivity with MeokappLeveraging Advanced FeaturesMeokapp offers a plethora of advanced features and functionalities designed to streamline workflow, enhance collaboration, and drive productivity. Some notable features include:Task Automation: Automate repetitive tasks and workflows to save time and resources, allowing you to focus on high-priority initiatives.Integration Capabilities: Seamlessly integrate Meokapp with other essential tools and platforms to consolidate workflows and optimize efficiency.Customization Options: Tailor Meokapp to your specific needs by customizing layouts, dashboards, and workflows to align with your unique requirements.ConclusionIn conclusion, mastering the Meokapp login process is the first step towards unlocking the full potential of this powerful platform. By familiarizing yourself with its features and functionalities, you can streamline your workflow, enhance collaboration, and drive productivity to new heights. Embrace the power of Meokapp and embark on a journey towards success and efficiency like never before.Read More : https://meokapp.com/
0 notes
Text
couldn't download video try turning off wifi or vpn whatsapp
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
couldn't download video try turning off wifi or vpn whatsapp
Video download troubleshooting
Are you experiencing issues while trying to download videos from the internet? Downloading videos can be a convenient way to watch your favorite content offline, but sometimes technical difficulties can arise. Here are some common troubleshooting tips to help you resolve video download issues.
First, ensure that you have a stable internet connection. Slow or interrupted connections can lead to download failures. Try restarting your router or connecting to a different network to see if that improves the download speed.
Next, check the video source to make sure the file is not corrupted or incomplete. If the video file is damaged, downloading it again from a different source may solve the problem.
Clearing your browser's cache and cookies can also help resolve download issues. These temporary files can sometimes interfere with the download process, so it's good practice to regularly clear them.
If you are using a video downloading software, make sure it is up to date. Outdated software may not be compatible with the latest video formats or protocols, leading to download errors.
Lastly, if you are still encountering problems, consider using a different video download method or tool. There are various online services and software available that may offer better compatibility with the video you are trying to download.
By following these troubleshooting tips, you should be able to overcome common video download issues and enjoy seamless offline viewing of your favorite content.
Disable VPN for WhatsApp
Title: How to Disable VPN for WhatsApp: Ensuring Seamless Connectivity
Using a VPN (Virtual Private Network) offers privacy and security benefits, but it can sometimes interfere with specific applications like WhatsApp. If you're experiencing connectivity issues or limitations while using WhatsApp with a VPN enabled, disabling it temporarily might resolve the problem. Here's how you can do it:
Access VPN Settings: Begin by locating your VPN app on your device. This could be in the form of a standalone application or integrated settings within your device's system preferences.
Turn Off VPN: Once you've located your VPN settings, toggle the VPN switch to disable it. This action will terminate the VPN connection and revert your device to its regular network connection.
Restart WhatsApp: After disabling the VPN, close WhatsApp completely and then reopen it. This step ensures that WhatsApp establishes a new connection using your device's regular network.
Test Connectivity: Check if WhatsApp is now working smoothly without the VPN. Send messages, make calls, and ensure that all features are functioning as expected.
Consider Alternatives: If you regularly use a VPN for privacy or security reasons but encounter issues with WhatsApp, consider alternative solutions. Some VPN providers offer split tunneling features, allowing you to exclude certain apps like WhatsApp from the VPN connection while keeping others protected.
Re-enable VPN: Once you've finished using WhatsApp or resolved any connectivity issues, you can re-enable your VPN if desired. Simply access the VPN settings again and toggle the switch to reconnect.
By following these steps, you can easily disable your VPN for WhatsApp when necessary, ensuring seamless communication without compromising your privacy and security. Remember to re-enable the VPN when you're done to continue benefiting from its protective features.
WiFi connection issues
Experiencing WiFi connection issues can be frustrating and disruptive to our daily routine. Whether you’re working from home, streaming your favorite shows, or just trying to browse the internet, a stable WiFi connection is crucial for staying connected.
One common issue that many people face is a slow or weak WiFi signal. This can be caused by various factors such as distance from the router, interference from other electronic devices, or even physical obstructions like walls or furniture blocking the signal. To improve your WiFi signal strength, consider relocating your router to a more central location in your home, away from obstructions, and ensure it is placed on an elevated surface for better coverage.
Another common WiFi problem is intermittent connection drops. This can be frustrating, especially when you are in the middle of an important video call or online gaming session. To resolve this issue, try restarting your router, checking for any firmware updates, and ensuring that your network equipment is functioning properly.
In some cases, WiFi connection issues may stem from outdated hardware or software. Ensure that your router and devices are running on the latest firmware and that your devices are compatible with the WiFi network you are trying to connect to.
If you continue to experience WiFi connection issues despite trying these troubleshooting steps, it may be beneficial to contact your internet service provider for further assistance. Remember, a stable and reliable WiFi connection is essential in today’s digital age, so don’t hesitate to address any issues that may be hindering your online experience.
WhatsApp video download error
When trying to download videos from WhatsApp, users may encounter various errors that can prevent successful download. One common issue is when the download fails due to network connectivity problems. This can happen if the Wi-Fi or mobile data connection is weak or unstable. In such cases, ensuring a stable internet connection or switching between Wi-Fi and mobile data can help resolve the problem.
Another reason for WhatsApp video download errors could be insufficient storage space on the device. If the device storage is full, there may not be enough space to save the downloaded video. To fix this, users can try deleting unnecessary files or apps to free up storage space and then attempt the download again.
Sometimes, the video file itself may be corrupted or incompatible with the device, leading to download errors. In such situations, trying to download the video on a different device or asking the sender to re-send the video may solve the issue.
Additionally, updating the WhatsApp application to the latest version can also help resolve download errors as updates often include bug fixes and improvements to the download functionality.
If all else fails, restarting the device or reinstalling the WhatsApp application may provide a solution to persistent download errors. By following these troubleshooting steps, users can troubleshoot and fix WhatsApp video download errors effectively, ensuring seamless downloading of videos on the platform.
Troubleshooting download problems
Title: Troubleshooting Download Problems: Solutions for Seamless Downloads
Downloading files is a routine task for many internet users, but encountering problems during the process can be frustrating. From slow download speeds to incomplete downloads, various issues can hinder your online experience. Here's a guide to troubleshooting common download problems and ensuring seamless downloads:
Check Your Internet Connection: Slow or unstable internet connections are often the culprit behind download issues. Ensure that your internet connection is stable and functioning properly. You can try resetting your router or switching to a wired connection for faster and more reliable downloads.
Clear Browser Cache: Your browser's cache can sometimes cause download problems by storing corrupted data. Clearing the cache can help resolve this issue. Simply go to your browser's settings and clear the browsing history, cookies, and cached images and files.
Disable Antivirus and Firewall: Sometimes, overly strict antivirus or firewall settings can block legitimate downloads. Temporarily disable these security measures and try downloading the file again. Remember to re-enable them once the download is complete to maintain your device's security.
Use a Different Browser: If you're experiencing download issues on a particular browser, try using a different one. Some browsers may have compatibility issues with certain file types or websites, so switching to an alternative browser could solve the problem.
Check File Size and Format: Ensure that the file you're trying to download is not too large for your internet connection to handle. Additionally, verify that the file format is supported by your device and software. If necessary, try downloading a different version of the file or using a file conversion tool.
Contact the Website or Service Provider: If you're still unable to download the file despite trying the above steps, reach out to the website or service provider for assistance. They may be able to provide alternative download options or troubleshoot the issue on their end.
By following these troubleshooting tips, you can overcome common download problems and enjoy a smoother online experience. Remember to stay patient and persistent, as solutions may vary depending on the specific issue you're facing.
0 notes
Text
what's the difference between dns and vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what's the difference between dns and vpn
DNS Explained
Title: Demystifying DNS: Understanding the Backbone of the Internet
DNS, or Domain Name System, is the unsung hero of the internet, quietly working behind the scenes to ensure that when you type a web address into your browser, you're taken to the correct website. Essentially, DNS acts as the internet's phonebook, translating human-friendly domain names like "example.com" into IP addresses, which are the unique numerical identifiers assigned to each device connected to the internet.
Imagine you're trying to find a friend's house in a sprawling city. You might know their name and general location, but without an address, you'd be lost. DNS provides those addresses for websites, allowing your device to locate and connect to them.
The DNS system operates through a distributed network of servers worldwide. When you enter a domain name into your browser, your device sends a query to a DNS resolver, typically operated by your internet service provider (ISP) or a third-party DNS provider like Google or Cloudflare. The resolver then communicates with other DNS servers to find the IP address associated with the requested domain.
This process involves several steps, including querying authoritative DNS servers, which are responsible for storing and providing information about specific domains. Once the resolver obtains the IP address, it caches the information to speed up future requests, reducing the need to query multiple servers for the same domain.
DNS plays a critical role in ensuring the smooth operation of the internet, enabling users to access websites and other online services with ease. Without DNS, navigating the vast digital landscape would be akin to finding a needle in a haystack.
In conclusion, while DNS may seem like a technical concept reserved for experts, it's a fundamental component of the internet that impacts our daily online experiences in profound ways. So the next time you visit a website, remember to thank DNS for effortlessly guiding you to your destination.
VPN Basics
A Virtual Private Network (VPN) has become an essential tool for ensuring online privacy and security. VPNs work by creating a secure and encrypted connection between the user's device and a remote server operated by the VPN service. This connection masks the user's IP address, making it difficult for anyone to track their online activities.
One of the primary benefits of using a VPN is the ability to browse the internet anonymously. By connecting to a VPN server, users can hide their real IP address and location, preventing websites, advertisers, and even internet service providers from tracking their online behavior. This not only protects users' privacy but also helps to bypass censorship and geo-restrictions.
Additionally, VPNs enhance security by encrypting data that is transmitted over the internet. This is crucial when using public Wi-Fi networks, as it prevents hackers from intercepting sensitive information such as passwords, credit card details, and personal messages. By using a VPN, users can protect themselves from potential cyber threats and maintain their online security.
Moreover, VPNs are valuable for accessing restricted content and bypassing internet censorship. By connecting to a VPN server in a different country, users can unblock websites and services that may be unavailable in their region due to geo-restrictions or government censorship.
In conclusion, VPNs are powerful tools that offer online privacy, security, and freedom. By using a VPN, users can protect their sensitive information, browse the internet anonymously, and access restricted content from anywhere in the world. Considering the growing concerns about online privacy and security, integrating a VPN into your online routine is a wise decision.
DNS vs VPN
DNS (Domain Name System) and VPN (Virtual Private Network) are both critical components of modern internet usage, but they serve different purposes and operate at different levels of the online infrastructure.
DNS is like a phonebook for the internet. It translates human-readable domain names (like www.example.com) into IP addresses (such as 192.0.2.1) that computers use to communicate with each other. When you type a URL into your browser, your device sends a DNS query to a DNS server, which then returns the corresponding IP address, allowing your device to connect to the desired website.
On the other hand, a VPN creates a secure, encrypted connection between your device and a remote server operated by the VPN service. This tunnel encrypts all the data passing between your device and the internet, protecting it from prying eyes and potential hackers. VPNs are commonly used to enhance online privacy, bypass geo-restrictions, and secure connections on public Wi-Fi networks.
While both DNS and VPNs can enhance online security and privacy, they serve different functions. DNS primarily focuses on translating domain names into IP addresses, while VPNs encrypt and secure internet traffic. However, they can complement each other when used together. For example, a VPN can encrypt your internet traffic, while a private DNS resolver can prevent your ISP from logging your browsing history.
In conclusion, DNS and VPNs are essential components of the internet, each serving distinct purposes in enhancing security and privacy online. Understanding how they work and when to use them can help users navigate the digital landscape more safely and securely.
DNS Functionality
Title: Understanding DNS Functionality: Navigating the Web's Address Book
DNS (Domain Name System) is the backbone of the internet, serving as its address book. When you type a website address into your browser, like "www.example.com," DNS translates that human-readable domain name into an IP address, such as "192.0.2.1," which computers understand. This translation enables seamless communication between devices across the internet.
The functionality of DNS involves several key components:
DNS Resolver: When you enter a domain name into your browser, your device sends a query to a DNS resolver, typically provided by your Internet Service Provider (ISP) or a third-party service. The resolver then seeks the IP address associated with the requested domain name.
Root Servers: If the resolver doesn't have the IP address cached, it contacts a root server. These servers maintain a database of all top-level domain (TLD) names, such as ".com," ".org," and ".net."
Top-Level Domain (TLD) Servers: The root server directs the resolver to the appropriate TLD server based on the domain's extension (e.g., ".com"). TLD servers manage domain names within their respective domains.
Authoritative DNS Servers: Once the resolver reaches the appropriate TLD server, it is directed to the authoritative DNS server responsible for the specific domain name. This server holds the most up-to-date information about the domain's IP address.
Caching: To improve efficiency, DNS resolvers cache IP address information for a specified time, reducing the need to repeatedly query authoritative servers for frequently accessed domain names.
Overall, DNS functionality ensures that users can access websites by name rather than remembering complex numerical IP addresses. It plays a crucial role in facilitating the seamless navigation of the internet, making it accessible and user-friendly for billions of people worldwide. Understanding DNS is essential for anyone navigating the digital landscape, as it underpins virtually all online activities.
VPN Encryption
VPN Encryption: Keeping Your Online Activities Secure
VPN encryption is a method of securing your internet connection by creating a private network from a public internet connection. Through encryption, a VPN protects your data from being intercepted, monitored, or manipulated by potential hackers, government authorities, or internet service providers.
Encryption in VPN services scrambles the data you send over the internet into a code that only the intended recipient can decipher. This process ensures that even if someone manages to intercept your data, they won't be able to make sense of it without the decryption key.
There are several encryption protocols used in VPN services, including OpenVPN, IPSec, and L2TP/IPSec. Each protocol has its level of security and speed, so it's essential to choose a VPN provider that offers strong encryption methods while maintaining a fast connection.
When selecting a VPN provider, look for one that utilizes AES-256 encryption, which is considered military-grade encryption and is virtually unbreakable. Additionally, ensure that the VPN provider follows a no-logs policy, meaning they do not store any information about your online activities.
By using a VPN with robust encryption, you can browse the internet anonymously, access geo-restricted content, and secure your online transactions. Whether you're working remotely, traveling, or simply want to enhance your online privacy, VPN encryption is a crucial tool in safeguarding your digital information.
0 notes
Text
does a vpn help protect me on non-encrypted http sites
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does a vpn help protect me on non-encrypted http sites
VPN Encryption
VPN Encryption, or Virtual Private Network Encryption, is a crucial component of online security and privacy. In simple terms, VPN encryption is the process of encoding data transmitted over a VPN connection in order to secure it from unauthorized access. By using encryption techniques, VPNs ensure that your online activities, such as browsing, streaming, and file sharing, remain private and protected from hackers, government surveillance, and other prying eyes.
There are several encryption protocols commonly used by VPNs, including OpenVPN, IKEv2, and L2TP/IPsec. These protocols employ advanced encryption algorithms such as AES (Advanced Encryption Standard) to scramble data packets, making them unreadable to anyone without the decryption key. This secure tunneling of data between your device and the VPN server shields your sensitive information, such as login credentials, financial transactions, and personal messages, from potential cyber threats.
When choosing a VPN provider, it is essential to consider the strength and type of encryption they offer. Ideally, opt for a VPN service that implements military-grade encryption standards and follows a no-log policy to guarantee the utmost privacy and anonymity. Additionally, ensure that the VPN provider employs secure key exchange mechanisms to prevent potential man-in-the-middle attacks and data tampering.
In conclusion, VPN encryption is a vital aspect of safeguarding your online presence and data integrity. By utilizing robust encryption protocols, you can browse the web with peace of mind, knowing that your digital footprint is shielded from nefarious entities and cyber intruders.
Non-Encrypted HTTP
Non-Encrypted HTTP, also known as HTTP (Hypertext Transfer Protocol), is a protocol used for transferring data over the internet. This protocol is widely used for accessing websites, downloading files, and sending information between a web server and a web browser.
One of the key characteristics of non-encrypted HTTP is the lack of data encryption. This means that the data transferred between the web server and the web browser is sent in plain text, making it vulnerable to interception by malicious third parties. This poses a significant security risk, as sensitive information such as login credentials, personal details, and financial data can be easily accessed by hackers if intercepted.
In contrast to non-encrypted HTTP, HTTPS (Hypertext Transfer Protocol Secure) provides an extra layer of security through data encryption. When a website uses HTTPS, the data transmitted between the server and the browser is encrypted, making it significantly more difficult for hackers to intercept and decipher the information.
It is highly recommended for websites that handle sensitive information to implement HTTPS to ensure the security and privacy of their users' data. Many web browsers now display a "Not Secure" warning for websites that use non-encrypted HTTP, prompting website owners to transition to HTTPS to safeguard their users' information.
In conclusion, the use of non-encrypted HTTP poses a serious security risk for websites and their users due to the lack of data encryption. By migrating to HTTPS, websites can enhance data security and protect sensitive information from potential cyber threats.
Internet Privacy
Internet privacy is a crucial issue in today's digital age, where the internet plays a significant role in our daily lives. With the increasing use of social media, online shopping, and digital communication, it has become more important than ever to protect our personal information online.
Maintaining internet privacy involves safeguarding sensitive data such as passwords, financial information, and personal details from falling into the wrong hands. This can be achieved by using secure passwords, enabling two-factor authentication, and being cautious about the information shared on social media platforms.
One major concern regarding internet privacy is the collection of personal data by companies for targeted advertising purposes. Internet users often unknowingly provide access to their browsing habits, location data, and online purchases, which can be used to create detailed profiles for targeted marketing campaigns. To address this issue, internet users can utilize privacy tools such as virtual private networks (VPNs) and browser extensions that block tracking cookies.
Government surveillance and data breaches are also significant threats to internet privacy. Enhanced encryption techniques and strong cybersecurity measures are essential in protecting sensitive information from potential hackers and cybercriminals. It is important for individuals to stay informed about privacy policies of websites and online services they use, and to regularly review their privacy settings to control the information shared online.
In conclusion, internet privacy is a fundamental right that every individual should actively safeguard. By adopting secure online practices and utilizing privacy tools, we can protect our personal data and ensure a safer online experience.
Online Security
Online security has become a paramount concern in today's digital age. With the increasing reliance on the internet for various aspects of our lives, it is crucial to prioritize safeguarding our personal information and data from potential cyber threats. Cybercrime is on the rise, with hackers and malicious actors constantly seeking to exploit vulnerabilities in online systems for their gains.
One of the key ways to enhance online security is by using strong and unique passwords for each online account. It is important to avoid using easily guessable passwords such as "123456" or "password," and instead opt for complex combinations of letters, numbers, and special characters. Furthermore, enabling two-factor authentication adds an extra layer of security by requiring a second form of verification to access an account.
Another aspect of online security is being cautious of phishing scams. These fraudulent attempts to obtain sensitive information such as passwords or credit card details often occur through deceptive emails or websites. It is crucial to verify the authenticity of emails and links before providing any personal information.
Additionally, keeping software and antivirus programs up to date helps protect against known vulnerabilities that cybercriminals may exploit. Regularly updating operating systems, browsers, and security software ensures that the latest security patches are in place to mitigate potential risks.
In conclusion, prioritizing online security is essential in safeguarding our digital identities and sensitive information. By following best practices such as using strong passwords, being vigilant against phishing attempts, and keeping software up to date, individuals can better protect themselves against cyber threats in the online realm.
Data Protection
Data protection refers to the practice of safeguarding sensitive information from unauthorized access, use, disclosure, disruption, modification, or destruction. In today's digital age, where a vast amount of data is stored and transferred online, ensuring its protection is crucial to maintaining privacy and security.
One of the key aspects of data protection is implementing secure measures to prevent data breaches. This includes encryption, firewalls, secure networks, and access controls to limit who can view or edit sensitive information. Regular risk assessments and vulnerability scans can help identify potential weaknesses in data protection measures and address them promptly.
Compliance with data protection regulations is another essential component. Laws such as the General Data Protection Regulation (GDPR) in the European Union set guidelines for how personal data should be collected, stored, and processed. Adhering to these regulations not only protects individuals' privacy rights but also helps organizations avoid costly fines and reputational damage.
Data protection also involves creating backups of data to prevent loss in case of emergencies such as cyberattacks, natural disasters, or hardware failures. Regularly updating software and systems can also help defend against evolving cyber threats and vulnerabilities.
Overall, data protection is an ongoing process that requires a proactive approach to safeguarding information, respecting privacy rights, and maintaining trust with customers and stakeholders. By prioritizing data protection measures, organizations can mitigate risks and ensure the confidentiality, integrity, and availability of their valuable data.
0 notes
Text
does vpn work when app is on
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn work when app is on
VPN functioning with active applications
Title: Understanding VPN Functioning with Active Applications
In today's interconnected digital landscape, virtual private networks (VPNs) have become indispensable tools for safeguarding online privacy and security. However, many users are often left wondering about the functionality of VPNs when running active applications. Let's delve into how VPNs operate in conjunction with these applications.
Firstly, it's essential to grasp the fundamental role of a VPN. A VPN creates a secure and encrypted connection between your device and the internet by routing your traffic through a remote server. This process shields your data from prying eyes, such as hackers, ISPs, and government surveillance, ensuring confidentiality and anonymity online.
When it comes to active applications, such as web browsers, messaging platforms, or streaming services, the VPN operates transparently in the background. Once you establish a VPN connection, all data transmitted from your device, including the traffic generated by active applications, is encrypted and routed through the VPN server. This means that regardless of the application you're using, your online activities remain protected.
Moreover, VPNs offer additional benefits when using active applications. They enable users to bypass geographical restrictions and access region-locked content on platforms like Netflix or Hulu. By connecting to a server in a different location, users can appear as if they're browsing from that region, unlocking a vast array of content otherwise unavailable in their location.
However, it's crucial to note that VPNs may impact the performance of active applications to some extent. Since the data is routed through an external server, there might be a slight increase in latency or a decrease in connection speed. Nevertheless, reputable VPN providers strive to minimize these effects by maintaining high-speed servers and optimizing network infrastructure.
In conclusion, VPNs seamlessly integrate with active applications, ensuring that users can enjoy the benefits of privacy, security, and unrestricted access to online content. By understanding how VPNs function in conjunction with these applications, users can make informed decisions to enhance their online experience.
App compatibility with VPN usage
App Compatibility with VPN Usage
Using a Virtual Private Network (VPN) has become increasingly popular for individuals seeking to enhance their online privacy and security. However, ensuring that your favorite apps are compatible with VPN usage is essential for maintaining seamless functionality and protecting your data across various platforms.
One of the primary concerns when using a VPN is whether it will work seamlessly with the apps you rely on daily. Fortunately, most reputable VPN providers offer broad compatibility across a wide range of devices and operating systems, including Windows, macOS, iOS, and Android. This compatibility ensures that whether you're browsing the web, streaming content, or accessing sensitive information, your VPN can provide the necessary protection without hindering your app usage.
However, there may be instances where certain apps encounter compatibility issues when used alongside a VPN. This can occur due to various factors, such as the app's design, network configurations, or how it handles connections. In such cases, troubleshooting steps like adjusting VPN settings, updating the app, or contacting the VPN provider's support team can often resolve the issue.
It's also worth noting that while most apps should function normally with a VPN, there may be exceptions, particularly with region-specific services or apps that rely heavily on precise location data. In these cases, you may need to temporarily disable the VPN or explore alternative solutions to ensure optimal app performance.
Ultimately, choosing a reputable VPN provider known for its compatibility and reliability is crucial for ensuring a seamless experience across all your favorite apps. By selecting a VPN service that prioritizes compatibility and provides robust support, you can enjoy enhanced privacy and security without sacrificing app functionality.
VPN effectiveness during application operation
Virtual Private Networks (VPNs) have become indispensable tools for ensuring online security and privacy, particularly during application operation. The effectiveness of VPNs in this regard stems from their ability to encrypt data traffic, thereby shielding it from potential interception by malicious entities.
One of the primary benefits of using a VPN during application operation is the encryption of data transmissions. When an application communicates with servers over the internet, the data exchanged can be vulnerable to interception by hackers or other unauthorized parties. By routing this traffic through a secure VPN server, all data passing between the application and the server is encrypted, making it virtually impossible for anyone to intercept and decipher without the encryption key.
Moreover, VPNs offer additional layers of security by masking the user's IP address and location. This makes it significantly harder for cybercriminals to track the user's online activities or launch targeted attacks based on their geographic location.
Furthermore, VPNs can bypass geographic restrictions imposed by certain applications or services. For example, streaming platforms often limit access to content based on the user's location. By connecting to a VPN server in a different country, users can circumvent these restrictions and access content that may be otherwise unavailable in their region.
However, it's essential to note that the effectiveness of a VPN during application operation relies on the quality and reliability of the VPN service provider. Users should choose reputable VPN services that offer robust encryption protocols, a wide selection of servers, and a strict no-logs policy to ensure their online privacy and security are adequately protected.
In conclusion, VPNs play a crucial role in ensuring the effectiveness of application operation by encrypting data traffic, enhancing online security and privacy, and bypassing geographic restrictions. By utilizing a reliable VPN service, users can enjoy a safer and more secure online experience while using their favorite applications.
Impact of active apps on VPN performance
When it comes to using a Virtual Private Network (VPN), the performance of the VPN can be significantly impacted by active apps running on the device. Active apps consume device resources such as bandwidth, CPU power, and memory, which can in turn affect the speed and stability of the VPN connection.
One of the primary ways active apps impact VPN performance is by competing for bandwidth. Bandwidth-hungry applications such as streaming services, online gaming, or large file downloads can consume a significant portion of the available bandwidth, leading to decreased speeds and potential connection drops when running a VPN at the same time.
Moreover, resource-intensive apps can also hog CPU power and memory, slowing down the device's overall performance and potentially causing lags in the VPN connection. This can be particularly noticeable on older devices with limited processing power and memory.
To mitigate the impact of active apps on VPN performance, users can consider closing or pausing unnecessary apps while running a VPN to free up valuable resources. Prioritizing VPN-sensitive activities and avoiding bandwidth-heavy tasks can also help maintain a stable and fast connection.
In conclusion, the impact of active apps on VPN performance is significant and cannot be overlooked. By understanding how active apps affect VPN performance and taking steps to optimize resource usage, users can ensure a smoother and more reliable VPN experience.
Application behavior within VPN environment
In the realm of cybersecurity, understanding how applications behave within a Virtual Private Network (VPN) environment is paramount. A VPN creates a secure tunnel between a user's device and the internet, encrypting data and masking the user's IP address. However, this encryption and rerouting can impact the performance and behavior of applications in various ways.
One significant aspect of application behavior within a VPN environment is latency. Because VPNs route internet traffic through their servers, it can introduce delays in data transmission, leading to increased latency. This delay can affect real-time applications like video conferencing or online gaming, causing lag or buffering issues.
Moreover, VPNs may encounter compatibility issues with certain applications. Some applications rely on specific network configurations or protocols that may not work optimally within a VPN's encrypted tunnel. As a result, users may experience difficulties accessing or using these applications while connected to a VPN.
Additionally, the geographic location of the VPN server can influence application behavior. For example, accessing region-restricted content through a VPN server located in another country may impact streaming quality due to longer distances and potential network congestion.
Security concerns also play a significant role in application behavior within a VPN environment. While VPNs enhance security by encrypting data, some applications may bypass the VPN tunnel, exposing sensitive information to potential threats. Users must be vigilant and ensure that all applications are configured to route traffic through the VPN to maintain privacy and security.
In conclusion, while VPNs offer valuable security and privacy benefits, their usage can impact the behavior of applications in various ways, including latency issues, compatibility challenges, and security concerns. Understanding these dynamics is crucial for users to effectively navigate the complexities of the VPN environment.
0 notes