#mss actors
Text
Concerning my name on my blog; “ms’s reblogs”
It is literally mysty swirl ‘s reblogs
And same goes for my stupid amount of tags ;)

Also that is Mysty Swirl. Yes they r a pony.😌
#here we go i told u this is a stupid amount of tags#mss tg#mss random#mss art#mss fanfics#mss arc#mss sw#mss actors#mss gender#mss polls#mss lit#mss prompts#mss mlp#mss trc#mss sky#mss space#mss ms#mss gold#icemav#goosemav#obikin#val kilmer#tom cruise#slice#anthony edwards#ao3#mss st#mss dune
7 notes
·
View notes
Text





Mei Mac, Tom Weston Jones and others at the opening night of Untitled F*ck Miss Saigon play at the Young Vic.
#tom weston jones#tom weston-jones#sanditon cast#the terror actors#lol#mei mac#london theatre#Can't wait this looks so good#Lourdes Faberes#the terror cast#untitled fck mss s**gon#Rochelle Rose#David M. Benett
6 notes
·
View notes
Text
For years, China’s state-backed hackers have stolen huge troves of company secrets, political intelligence, and the personal information of millions of people. On Monday, officials in the United States and United Kingdom expanded the long list of hacking allegations, claiming China is responsible for breaching the UK’s elections watchdog and accessing 40 million people’s data. The countries also issued a raft of criminal charges and sanctions against a separate Chinese group following a multiyear hacking rampage.
In August last year, the UK’s Electoral Commission revealed “hostile actors” had infiltrated its systems in August 2021 and could potentially access sensitive data for 14 months until they were booted out in October 2022. The deputy prime minister, Oliver Dowden, told lawmakers on Monday that a China state-backed actor was responsible for the attack. In addition, Dowden said, the UK’s intelligence services have determined that Chinese hacking group APT31 targeted the email accounts of politicians in 2021.
“This is the latest in a clear pattern of malicious cyber activity by Chinese state-affiliated organizations and individuals targeting democratic institutions and parliamentarians in the UK and beyond,” Dowden said in the UK’s House of Commons. The revelations were accompanied by the UK sanctioning two individuals and one company linked to APT31.
Alongside the UK’s announcement on Monday, the US Department of Justice and Department of the Treasury’s Office of Foreign Assets Control unveiled further action against APT31, also known as Violet Typhoon, Bronze Vinewood, and Judgement Panda, including charging seven Chinese nationals with the conspiracy to commit computer intrusions and wire fraud.
The DOJ claims the hacking group, which has been linked back to China’s Ministry of State Security (MSS) spy agency, has spent 14 years targeting thousands of critics, businesses, and political entities around the world in widespread espionage campaigns. This includes posing as journalists to send more than 10,000 malicious emails that tracked recipients, compromising email accounts, cloud storage accounts, telephone call records, home routers, and more. The spouses of one high-ranking White House official and those of multiple US senators were also targeted, the DOJ says.
“These allegations pull back the curtain on China’s vast illegal hacking operation that targeted sensitive data from US elected and government officials, journalists and academics; valuable information from American companies; and political dissidents in America and abroad,” Breon Peace, a US attorney for the Eastern District of New York, said in a statement. “Their sinister scheme victimized thousands of people and entities across the world, and lasted for well over a decade.”
The moves come as countries increasingly warn of an increase in China-linked espionage, during a year when more than 100 countries will host major elections. Statements from officials focus on the impact of the hacking activity on democratic processes, including the targeting of elected officials around the world and the compromising of pro-democracy activists and lawmakers in Hong Kong. However, the disclosures also coincide with continued jostling from Western politicians over pro- or anti-China stances, including the proposed sale of TikTok to a US company, which could result in a ban on the popular app if the sale fails to go through.
As officials in the UK disclosed the details of the hacking activity, Lin Jian, a Chinese foreign ministry spokesperson, claimed it was “disinformation” and told reporters the country “opposes illegal and unilateral” sanctions. “When investigating and determining the nature of cyber cases, one needs to have adequate and objective evidence, instead of smearing other countries when facts do not exist, still less politicize cybersecurity issues,” Jian said in a daily press conference on Monday.
“China is embarking on a huge global campaign of interference and espionage, and the UK and the like-minded nations are pretty sick of it,” says Tim Stevens, a global security lecturer and head of the cybersecurity research group at King’s College London. Stevens says the public shaming and sanctions are unlikely to significantly change China’s actions but may signal a warning to other countries about what is and isn’t deemed acceptable when it comes to international affairs.
China has a broad range of hacking groups linked to its intelligence services and military, as well as companies that it contracts to launch some cyber operations. Many of these groups have been active for more than a decade. Dakota Cary, a China-focused consultant at security firm SentinelOne, says that groups associated with China’s civilian intelligence service are largely conducting diplomatic or government intelligence collection and espionage, while China’s military hackers are behind attacks on power grids and US critical infrastructure such as water supplies. “We do see China engaging in all of those activities simultaneously,” Cary says.
In announcing criminal charges and sanctions against members of APT31, officials in the US laid out a series of hacking allegations that include the targeting of businesses, political entities, and dissidents around the world. These included a “leading provider” of 5G telecoms equipment in the US, Norwegian government officials, and people working in the aerospace and defense industries. APT31 was run by the MSS’s Hubei State Security Department in the city of Wuhan, US officials say.
The seven Chinese nationals hit with charges are Ni Gaobin, Weng Ming, Cheng Feng, Peng Yaowen, Sun Xiaohui, Xiong Wang, and Zhao Guangzong. Both Zhao Guangzong and Ni Gaobin were also sanctioned. The two are alleged to be affiliated with Wuhan XRZ, a company that has also been sanctioned by the US and UK and is believed to be a cover for MSS-linked hacking operations. Employees of the company hacked into a Texas-based energy company in 2018, the US Treasury Department said.
The group used sophisticated malware—including Rawdoor, Trochilus, and EvilOSX—to compromise systems, according to a 27-page indictment unsealed by the DOJ. They also used a “cracked/pirated” version of penetration testing tool Cobalt Strike Beacon to compromise victims, the indictment says. It adds that, between 2010 and November 2023, the group “gained access” to a defense contractor that designed flight simulators for the US Army, Air Force, and Navy; a multi-factor authentication company; an American trade association; a steel company; a machine learning laboratory based in Virginia; and multiple research hospitals.
In its announcement, the UK outlined two separate China-linked incidents: first, the targeting of the email inboxes of 43 members of parliament (MPs) by APT31 in 2021; and second, the hack of the Electoral Commission by further unnamed China-linked hackers. Elections in the UK are decentralized and organized locally, with the commission overseeing the entire process. This setup means the integrity of the electoral process was not impacted, the commission says; however, a huge amount of data may have been taken by the hackers.
When the Electoral Commission revealed it had been compromised last year, it said the details of around 40 million people may have been accessed. The commission said names and addresses of people in Great Britain who were registered to vote between 2014 and 2022 could have been compromised, and that file-sharing and email systems could have been made accessible. “It’s really remarkable that China would go after election oversight systems, particularly given the diplomacy that the PRC [People’s Republic of China] is trying to pull off with the EU,” Cary says. “It’s a very significant act for the PRC to go after these types of systems,” Cary says. “It’s something that democracies are really sensitive to.”
While nations have called out China’s hacking activities for years, the country has evolved its tactics and techniques to become harder to detect. “Over the past couple of years, tired of having their operations rumbled and publicly outed, the Chinese have placed a growing emphasis on stealthy tradecraft in cyber espionage attacks,” Don Smith, vice president of threat intelligence at security firm Secureworks’ counter-threat unit, said in a statement. “This is a change in MO from its previous ‘smash and grab’ reputation but it is viewed by the Chinese as a necessary evolution to one, make it harder to get caught and two, make it nearly impossible to attribute an attack to them.”
3 notes
·
View notes
Text
Safeguarding Your Digital Frontier: Sify's Managed Security Services
In an age where digital threats lurk around every virtual corner, safeguarding your organization’s data and infrastructure has never been more critical. As businesses grapple with an increasingly complex threat landscape, Sify Technologies emerges as a beacon of cybersecurity excellence, offering comprehensive Managed Security Services (MSS) designed to fortify defenses, mitigate risks, and ensure peace of mind in an ever-evolving cyber ecosystem.
The Evolution of Cyber Threats: Cyberattacks have evolved from simple nuisances to sophisticated, orchestrated campaigns orchestrated by skilled threat actors. From ransomware and phishing scams to DDoS (Distributed Denial of Service) attacks and insider threats, the breadth and depth of cyber threats facing organizations today are unprecedented. In this digital battleground, proactive defense and rapid response are paramount.
Empowering Organizations with Comprehensive Protection: Sify’s Managed Security Services deliver a holistic approach to cybersecurity, encompassing a wide range of solutions and technologies to address the multifaceted nature of modern threats. Key components of Sify’s MSS portfolio include:
Threat Detection and Response: Leveraging advanced threat intelligence, machine learning, and behavioral analytics, Sify’s MSS enables organizations to detect and respond to threats in real-time, minimizing dwell time and mitigating the impact of security incidents.
Endpoint Security: Endpoints serve as the frontline of defense against cyber threats, making endpoint security a critical component of any cybersecurity strategy. Sify’s MSS provides comprehensive endpoint protection, including antivirus, endpoint detection and response (EDR), and vulnerability management, to safeguard devices from malware, ransomware, and other malicious attacks.
Network Security: Protecting the network perimeter is essential for preventing unauthorized access and data exfiltration. Sify’s MSS offers robust network security solutions, such as firewalls, intrusion detection and prevention systems (IDPS), and secure web gateways, to monitor and control traffic, enforce security policies, and thwart cyber threats.
Cloud Security: As organizations embrace cloud computing and hybrid IT environments, securing cloud workloads and data becomes paramount. Sify’s MSS delivers cloud security solutions tailored to the unique requirements of cloud-native applications, infrastructure as a service (IaaS), and software as a service (SaaS), ensuring comprehensive protection across the entire cloud ecosystem.
Security Operations Center (SOC) as a Service: Building and operating an in-house SOC can be resource-intensive and cost-prohibitive for many organizations. Sify’s MSS offers SOC as a Service, providing round-the-clock monitoring, threat hunting, incident response, and security advisory services delivered by a team of skilled cybersecurity experts.
Partnering for Success: Sify’s Managed Security Services are more than just technology solutions; they are strategic partnerships forged with the shared goal of safeguarding organizational assets and preserving business continuity. With a customer-centric approach, Sify collaborates closely with clients to understand their unique security requirements, assess their risk posture, and develop tailored cybersecurity strategies that align with their business objectives.
Driving Cyber Resilience in a Digital World: In today’s interconnected and digitized world, cybersecurity is not merely a compliance checkbox but a business imperative. With Sify’s Managed Security Services, organizations can navigate the complexities of the cyber threat landscape with confidence, resilience, and agility. By combining cutting-edge technologies, industry best practices, and expert guidance, Sify empowers organizations to stay one step ahead of cyber adversaries and emerge stronger in the face of adversity.
Protect your organization’s digital frontier with Sify’s Managed Security Services and embark on a journey towards a safer, more secure future.
0 notes
Text
North Korea's APT37 Targeting Southern Counterpart with New M2RAT Malware
The Hacker News : The North Korea-linked threat actor tracked as APT37 has been linked to a piece of new malware dubbed M2RAT in attacks targeting its southern counterpart, suggesting continued evolution of the group's features and tactics.
APT37, also tracked under the monikers Reaper, RedEyes, Ricochet Chollima, and ScarCruft, is linked to North Korea's Ministry of State Security (MSS) unlike the Lazarus and http://dlvr.it/SjSyN4 Posted by : Mohit Kumar ( Hacker )
0 notes
Text
Dick, engage this person in conversation while I look around.
“My dear fellow, we want four suits of clothes with chicken fixings, nothing more. If we get them, all right. Otherwise I’ll break your neck. Dick, engage this person in conversation while I look around.” I was puttering among the shelves and showcases, trying to get an exact fit for all our party, when I happened to glance over my shoulder.
—
Al Jennings and Will Irwin, Beating Back (1913) : 127 (University of Illinois copy)
same (UC copy, at hathitrust)
Al Jennings (1863-1961), lawyer, inept outlaw (train robber), raconteur, evangelist, actor and advisor on Westerns
wikipedia
The book was made a book via conversation, stenography and the editorial ministrations of Will Irwin, who also penned its colorful opening chapter “Introducing Mr. Jennings.”
Will Irwin (1873-1948), wikipedia
see also the description of the Will Irwin and [his wife] Inez Haynes Gillmore papers, at Yale : YCAL MSS 603
0 notes
Text







Mew Suppasit
GQ Hype Magazine Pictorial / December 2021
"Ready to Conquer the World"
#mew suppasit#mewgulf#tharntype#thai actor#thai model#thai singer#photoshooting#GQ Magazine#handsome man#beautiful face#hot#MSS Connection Ceo#Mew Suppasit Studio Ceo#Bulgary
68 notes
·
View notes
Text

32 notes
·
View notes
Photo






"Season Of You" (MV TEASER 1) - Mew Suppasit
#mew suppasit#suppasit jongcheveevat#mewgulf#tharntype the series#mss#mew suppasit studio#tharn x type#mew x gulf#TTTS#TTTS S2#thai actor#music#mew gifs#tharn kirigun
92 notes
·
View notes
Quote
The New Zealand government said it had uncovered evidence of links between Chinese state-sponsored actors known as Advanced Persistent Threat 40 (APT40) and malicious cyber activity in New Zealand. "The GCSB has worked through a robust technical attribution process in relation to this activity," Minister responsible for the Government Communications Security Bureau Andrew Little said. "New Zealand is today joining other countries in strongly condemning this malicious activity undertaken by the Chinese Ministry of State Security (MSS) - both in New Zealand, and globally."
‘NZ in 'position of vulnerability' over China hacking accusations’, RNZ
#RNZ#New Zealand#China#New Zealand government#state-sponsored actors#APT40#Advanced Persistent Threat#malicious cyber activity#GCSB#technical attribution process#Andrew Little#Chinese Ministry of State Security#MSS
3 notes
·
View notes
Text

Justin Briner really is coming near me this year...!! in just a couple months too!
I’ll get to give him an Alpha plush and save up more flamingos! my mom can finally meet him too! but then I can’t really explain why it is that Alpha has changed my life so much...but if I tell him something like I wish I could tell you but it’s a long story, I could find away to do it online? aaa, even if it doesn’t work out, one day I’ll get to...
#whispering zephyr#I'm working on two plushies for one voice actor for Shuto and I'm very slow because of animating and MSS manga...#but they'll be done in time :3c#I screamed to know Justin is coming back even though I met him three times last yera#*year#he's the only voice actor other than Mac I get excited to meet more than once
2 notes
·
View notes
Photo



Stationery Saturday: American Federation of Labor
This year International Workers Day falls on a #StationerySaturday, so we bring you a crossover post featuring 1920s Stationery from the American Federation of Labor. The American Federation of Labor was a national federation of labor unions founded in 1886 from the Federation of Organized Trades and Labor Unions. The American Federation of Labor was formed in the same year as the Haymarket Affair in Chicago, where several labor activists were wrongly executed after workers organized a general strike for an eight hour workday. May 1st marks the anniversary of this general strike and is commemorated each year on May 1st, International Workers Day.
The stationery featured here comes form the papers of William Benjamin Rubin, a Milwaukee attorney, author, and lecturer, prominent in the labor movement and in Democratic politics. Rubin was deeply involved in the labor movement, both in Milwaukee and nationally, serving as counsel during the 1919 strikes by the steelworkers, seamen, and members of Actor's Equity. Rubin assisted with drafting first law to prohibit blacklisting of employees by employers, and was chief counsel for the American Federation of Labor for twenty-five years.
This letter can be found along with other correspondence in Box 4 of the William Benjamin Rubin Papers, call number Milwaukee Mss P, here at the UWM Archives.
-Lizzie
#UWM Archives#William Benjamin Rubin#International Workers Day#Stationery Saturday#1920s#American Federation of Labor#Labor Activism#Labor History#Haymarket Affair#Milwaukee History#May Day#Lizzie#General Strike#Vintage Stationery#Labor#Workers#1886#Strike
35 notes
·
View notes
Text
Empowering Digital Defense: Sify's Managed Security Services
In the ever-evolving landscape of cybersecurity threats, businesses face an unprecedented challenge in safeguarding their digital assets and maintaining regulatory compliance. To address these challenges, Sify offers a comprehensive suite of Managed Security Services (MSS) designed to protect organizations of all sizes from a wide range of cyber threats.
Fortifying Your Defenses with Managed Security Services
Sify’s Managed Security Services go beyond traditional perimeter-based security measures to provide holistic protection for your entire digital ecosystem. Our team of cybersecurity experts leverages cutting-edge technologies, industry best practices, and threat intelligence to proactively identify and mitigate security risks, allowing you to focus on your core business objectives with confidence.
Key Features and Benefits
24/7 Threat Monitoring and Response: Our Managed Security Services include round-the-clock monitoring of your network, endpoints, and cloud environments to detect and respond to security incidents in real-time. By leveraging advanced security analytics and machine learning algorithms, we can identify anomalous behavior and potential threats before they escalate into major security breaches.
Customized Security Solutions: We understand that every organization has unique security requirements and compliance obligations. That’s why our Managed Security Services are tailored to your specific needs, providing a customized security posture that aligns with your business objectives, industry regulations, and risk tolerance.
Proactive Vulnerability Management: In today’s threat landscape, staying ahead of vulnerabilities is crucial to maintaining a strong security posture. Sify’s Managed Security Services include proactive vulnerability assessments and patch management to identify and remediate security flaws before they can be exploited by malicious actors, reducing the risk of data breaches and downtime.
Compliance Assistance: Compliance with industry regulations such as GDPR, HIPAA, and PCI DSS is non-negotiable for businesses operating in today’s digital economy. Sify’s Managed Security Services include compliance assistance to help you navigate the complex regulatory landscape, implement security controls, and achieve and maintain compliance with relevant standards and frameworks.
Incident Response and Forensics: In the event of a security incident, time is of the essence. Sify’s Managed Security Services include incident response and digital forensics capabilities to help you contain, investigate, and recover from security breaches quickly and effectively, minimizing the impact on your business operations and reputation.
Customer Success Stories
The true measure of our success lies in the satisfaction of our customers. Over the years, Sify’s Managed Security Services have helped numerous organizations across industries bolster their cybersecurity defenses, mitigate risks, and achieve peace of mind in an increasingly hostile threat landscape.
From small businesses looking to enhance their security posture to large enterprises seeking to combat sophisticated cyber threats, our Managed Security Services have consistently delivered tangible results, earning the trust and loyalty of our clients.
In an era where cyber threats are becoming more sophisticated and pervasive, Sify’s Managed Security Services offer a beacon of hope for businesses seeking to fortify their defenses and protect their digital assets. With a focus on proactive threat monitoring, customized security solutions, compliance assistance, and incident response capabilities, we’re committed to empowering organizations with the tools they need to stay one step ahead of cybercriminals and safeguard their future. Experience the power of Sify’s Managed Security Services today and embark on a journey towards a more secure and resilient digital future.
0 notes
Link
(..) The UK said Chinese state-backed actors were responsible, while the EU said the attack came from "the territory of China".
The Chinese Ministry of State Security (MSS) was also accused of wider espionage activity and a broader pattern of "reckless" behaviour(..)
9 notes
·
View notes
Photo

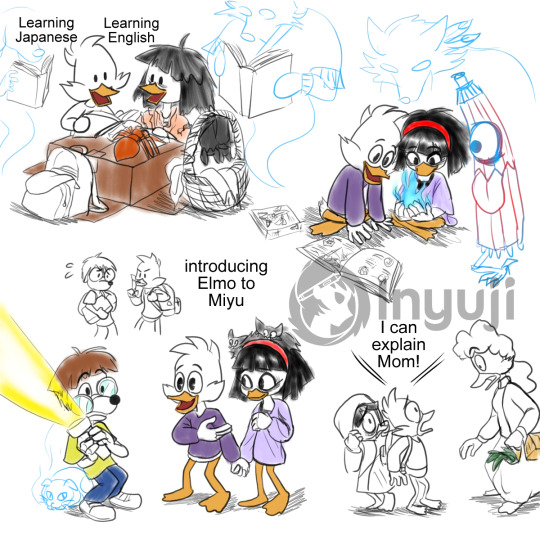



Don’t know how much more ducks I wanna draw. For now, I wanted to get this out of the way. This is dubbed the “Stranger Things” AU, where Miyu Moreno met Drake as young teens, but under bad circumstances. Basically Drake and his classmate Elmo Sputterspark befriend Miyu and dub themselves the “Weirdo Club.” And they just enjoy an entire autumn doing fun shenanigans while trying to find leads to Miyu’s possible relatives.
WARNING: LONG story description. Read at your own peril
Miyu’s adoptive mother, Lucia Moreno, did not survive the risky operation to cure her illness. This left Miyu an orphan, and unable to look after herself. What’s worse was being secretly watched by strange people who claimed “child services.” The spirits and yokai warned her of the shady government agents. Out of desperation and fear, Miyu snuck out of Japan to America when she was thirteen, hoping to find any relatives who could take her in. Unfortunately she was still being tracked by the shady agents, so she ran and hid as far as she could. She stayed hidden, barely surviving in a rumored “haunted house,” in the homely town of St. Canard.
Young teen Drake Mallard would brave his way into the haunted house to retrieve his classmate’s bag, which was maliciously disposed by some schoolyard bullies. That’s how he stumbles into a half-starved Miyu, and a bunch local ghosts and a few yokai. Drake barely understood Miyu’s plight, but decided to visit her and help. While trying to teach Miyu with English, Drake discovered some untranslated and translated manga at his local bookstore, and used these as a teaching aid for Miyu and himself. Drake has been introduced to Anime much earlier and now has even more things to nerd over. Our boi is dorkier than ever and I don’t regret a thing.
Over a month, his classmate noticed something was up with Drake. They are not friends, but they are friendly to each other. Drake decided to trust Elmo on his secret, and soon Elmo became part of the “weirdo” club. Miyu would mostly stay hidden, but she occasionally pops out in public when she’s dragged to movies or possible school events. They did share a very awesome Halloween. Drake and Elmo would research possible leads to Lucia Moreno’s relatives or any past work acquaintances. Miyu would try to dreg up clues or help from the local spirits also. At some point, Drake’s mother found out about Miyu when she came home early from shopping and caught Drake trying to smuggle in Miyu to his house. After getting an explanation, she decided to let Miyu stay, though she really wants to alert authorities about the “runaway child.” She does see how Miyu is deadly scared of any “bad men” finding out, since a few had posed as government workers.
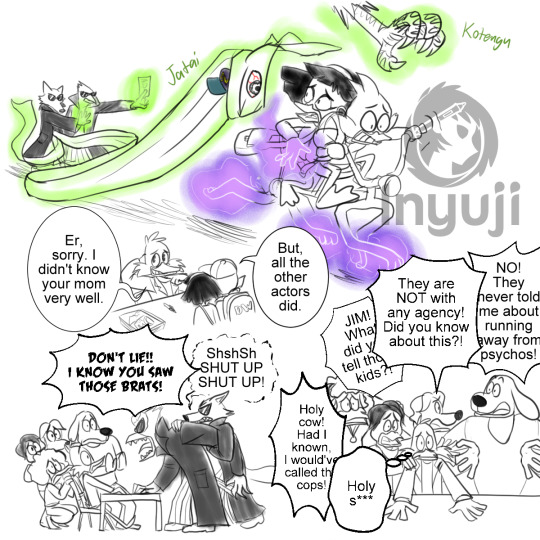
The shady agents from Japan have tracked Miyu down, and it’s revealed that they are Onmyoji hunting down Miyu for her magic. Drake and Miyu hastily embark on a road trip to flee from the Onmyojis and seek out the past Darkwing actors. With Elmo occasionally guiding them via radio and Miyu’s helpful spirits, they are able to visit the main Darkwing villain actors and ask about Lucia. While they have good things to say about her brief time on the show, they do not know much about Lucia’s family or if she even had family here. During their biking trip, they befriend a stray Grim, who has kept stealthy vigil over Drake and Miyu. When they finally meet Jim Starling, they are given even more disappointing news. Jim was really shocked that Lucia had adopted a kid during her time recovering and feels guilty about Miyu being an orphan. Jim lies about not knowing Lucia much, not wanting to reveal that his dangerous stunts were the cause of Lucia being injured during set, resulting in her damaging her voice and falling ill. Rather than risk the show being cancelled, Jim had suggested to the writers and producers to drop Lucia from the show. Drake is a bit hesitant to believe that this acting hero is lying, when all the other actors remember Lucia. Miyu has practically given up when their final lead knows nothing.
The Darkwing actors had actually met up shortly at Jim’s signing to ask if he had met Drake and Miyu. They are concerned that two kids are trekking a long way, and hope to rectify their poor judgment of letting the kids go on their merry way. They are disappointed that Jim had practically lied to a bunch of kids, knowing that he too knew Lucia during the short time on set. At that moment, the 2 Onmyojis start interrogating the crew, claiming they are investigators looking for 2 runaway children. One of them however, is pissed and hates dealing with the “normies.” The actors deny knowing where the kids went, and Jim lies though his teeth that the kids probably hit the bus to the next town. When the Onmyojis leave, everyone is officially freaking out. All of the actors are calling the cops and contacting old colleagues who had worked on the Darkwing production. Jim is too freaked out to do anything and doesn’t want to get involved.
When the Onmyojis finally catch up to Miyu and Drake, Drake was almost killed. Witnessing this caused Miyu to awaken her Kitsune blood. Miyu’s real mother was a kitsune, which has given her a sixth sense for the supernatural and magic. Jim Starling had stumbled on this fight while on his way home, and attempted to help. He was easily subdued and injured in the process. After Miyu maliciously subdued all yokai shikigamis (onmyoji summons) and the 2 Onmyojis, the police and paramedics were able to come in time. Drake is diagnosed to be in coma, with low chances of waking up, and this breaks Miyu. Jim feels terrible that he was practically useless and that he was the reason that Lucia was ill and had to seek treatment, which ultimately killed her. Drake’s mother is wracked with grief, but she doesn’t blame Miyu, seeing how much Miyu blames herself. During the fight with the Onmyojis, they reveal that they had sabotaged the operation that would supposedly cure Lucia’s illness. They wanted Miyu easily vulnerable to induct her into their ranks as an Onmyoji in their organization. Miyu blames her existence and her magic for hurting people around her. Out of desperation, Miyu consulted whatever yokai friends for a solution, and prays for Inari, the Kami closely related to Kitsune and possibly the Kami her kitsune mother had served. Inari appears as a spectral apparition and warns Miyu that she will weaken in magic, even with Inari’s help. Miyu doesn’t care for magic anymore. Drake finds himself in a spectral limbo and told about the plight happening in the living realm. Drake doesn’t want Miyu to sacrifice her magic for him, and stubbornly makes his way towards a gateway back to the living, but with great difficulty.
Drake still has to stay hospitalized, but he only needs to heal from a broken arm, and surprisingly, his skull has recovered nicely. Miyu’s magic has been sapped near dry, so all proficiency she had gained is back to level 0. However, Miyu would still have to be processed into Foster Care. There is no guarantee that Miyu will find a stable place to keep in contact with Drake through long-distance letters. Jim had talked a bit with Miyu, asking about her life with Lucia. Wanting to appease his guilt and truly being sorry for Miyu, he manages to take in Miyu as his foster child. He wants to give Miyu a stable home so she can keep consistent correspondence with Drake and Elmo.
Miyu and Jim are able to visit St. Canard every month, especially during school vacation breaks. This gives the kiddies a chance to continue on their Dungeons & Dragons campaign. Jim has started to get the hang of being their Dungeon Master. Now that Jim is a foster father, slowly becoming an adoptive father, he bites down his pride and takes any small gigs to pay bills. But this has been good for him. He’s slowly gaining momentum as an actor, though nothing too noteworthy. Miyu is quite proud of Jim doing his best, and always makes it a routine to pack a bento for him. She finds every chance to personally bring it to him. Over time, Miyu has regained her proficiency in magic in her late teenage years. Jim has been getting good support and contact with his old DW crew, and some parenting advice from Mss. Mallard. Drake has been taking good care of the Grim, who is now lovingly named “Kage.” When Miyu is in her teenage years, Jim is actually nailing a lot more Duckflix gigs who have taken some note of Jim’s improving repertoire. It also helps that he’s become less of a jerk.
#darkwing duck#ducktales 2017#drake mallard#elmo sputterspark#jim starling#stranger things au#morgana macawber#miyu moreno#inyuji#onmyoji#duck dad
183 notes
·
View notes