#multi factor authentication
Text
I understand the necessity of multi-factor authentication, but as someone with ADHD so bad I was diagnosed at age 7 in the 1990s despite me being a girl at the time...asking me to pick my Distraction Box back up when I've finally managed to put it down to try and get to work is, uh, not the best thing ever for my ability to get work done. You are requiring Captain Distractosaurus to pick up and look at his Distraction Box in order to do his work. This is the worst possible thing you could ask me to do. Picking up and looking at my Distraction Box and entering a code and waiting for the code to be accepted is so many steps, and in between each one of those steps is an opportunity to get distracted, and I am holding and looking at my Distraction Box for every single one of those steps.
Guess what I was doing when I got distracted and made this post. You'll NEVER guess. Multi-factor authentication is very necessary and I hate it SO MUCH. I'm gonna eat a bug
2K notes
·
View notes
Text
I fucking hate multifactor authentication.Not only am i now obliged to have a smartphone nearby at all times when working, which is distracting,but now the damn thing broke and i can neither login nor register a new device under my account because the link will be sent to my smartphone...which is broken.Fucking useless.
also is it just me or is tying access to basic services to a single fairly fragile device in our age of planned obsolescence fucking stupid?
all i want is to check my schedule and where i need to be on Monday.
#idc about security anymore whoever wants to read my boring uni emails is welcome to them. just get rid of this nonsense#they made it mandatory this year but it's crappy and literally everyone i've talked to hates it#at least nowadays it only takes two tries on average to login.An improvement.#by the time my new phone gets delivered it'll be weekend and the IT service probably won't reply until Monday.ugh.#multi factor authentication#smartphones#planned obsolescence#account security#complaining#IT bullshit#fucking useless
15 notes
·
View notes
Text
If your business isn’t using CIAM, you stand every chance of lagging behind businesses that are making the most of the technology and the customer data it collects.
A CIAM solution usually offers a combination of features, including customer registration, self-service account management, consent and preferences management, single sign-on (SSO), multi-factor authentication (MFA), access management, directory services, and data access governance.
#ciam#customer identity and access management#consumer iam#ciam platform#ciam vendors#ciam solutions#consumer iam solutions#sso#single sign on#single sign on vendors#single sign on solutions#mfa#multi factor authentication#Multi factor authentication solutions#social login#social authentication#passwordless login#passwordless authentication#login security#adpative authentication#federated identity management#federated sso#broken authentication#digital identity management#identity verification#identity proofing#phone login
1 note
·
View note
Text
Securing Your Online Presence: The Essential Guide to Multi-Factor Authentication
Securing Your Online Presence The Essential Guide to Multi-Factor Authentication
In an increasingly connected world, securing our online activities has never been more important. Multi-Factor Authentication (MFA), and its subset Two-Factor Authentication (2FA), stand out as essential tools in the fight against cyber threats. This essential guide delves into the intricacies of MFA, offering a…
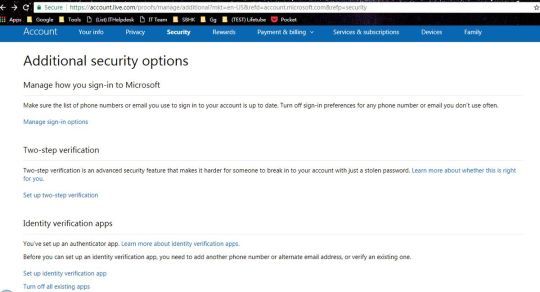
View On WordPress
#Latest Technology Trend#modern technology#multi factor authentication#New Technology 2024#Next-Gen Technology#Next-Level Technology#technology blogs#technology new#TechnologyTrends2024
0 notes
Text
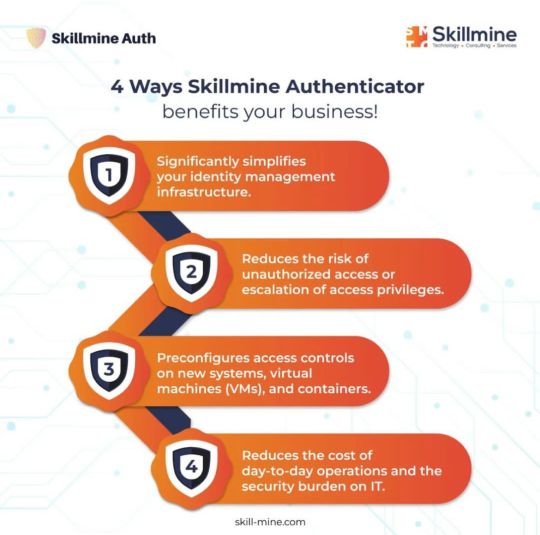
4 ways Skillmine Authenticator benefits your business!
Authenticator removes the need for users to remember, and manage multiple passwords. It centralizes authentication and simplifies access management across multiple applications in an organization. Auth supports various protocols and supports different social media platforms like Facebook, and Google. It also supports classical logins and fewer passwords logins.
1 note
·
View note
Text
Watch "2FA Isn’t Secure - Here’s What You Need Instead!" on YouTube
youtube
#snubs#shannon morse#youtube#cyber security#security#hardware token#multi factor authentication#mfa#2 factor authentication#2fa
1 note
·
View note
Text
Wish that more financial institutions start implementing multi factor authentication (MFA) using Authenticator apps like Google, Microsoft, Duo etc.
0 notes
Text
#multi factor authentication#network security#technology#electronics#ecommerce#biomatric#biometrics#consumer electronics#banking#retail
0 notes
Text
I got scammed through Booking.com
...and I'm posting this so maybe someone else sees it and doesn't fall for it.
On Sunday, the app Booking.com, which I have installed on my phone, sent me a message saying that an upcoming reservation I have in Frankfurt was in danger of being cancelled. Due to a high number of fake bookings they were going to need some verification within the next twelve hours. So I clicked their link, ensured that it was a secure link from Booking.com, and re-entered my credit card info.
The page where I entered it said the verification process should take about five minutes. After an hour with nothing, I e-mailed the hotel directly and said that I was running into some technical difficulties with Booking.com, but I did very much want the room still, even if the booking service ended up trying to cancel my reservation.
I got a reply - to the e-mail I'd sent the hotel directly - through Booking.com. They said there was a misunderstanding with the staff and my card had been rejected, but there was a link that would clear it up. And it was the same darned link as before, but I'm used to having to jump through a billion hoops for multi-factor authentication now, so this time I asked my mom if I could use her card to reserve and pay for the room, and I'd just transfer her the money. And she gave me her info. And I gave it to them.
Then I got a message saying this card had been accepted, and I was going to get an SMS with a code, and I should enter the code to complete the process. Except no SMS was forthcoming, not to me or to Mom, and then I looked at the spelling on that last message and thought, you know, I know I'm reserving a hotel where English is a second language, through a company where English is a second language, but maybe I'm just gonna check…
So I searched "Booking.com scam?" and found this Guardian article, which describes pretty much exactly what happened to me. This has been happening for at least a month, and Booking.com denies that it's been hacked. But that's where the messages were coming from, they had my reservation details, and they knew when and what I had written to the hotel I had the reservation with. If I had seen something like this article - heck, if Booking.com itself had sent out a warning - I would have known something was up from the beginning, but as it was, they were slick enough that I got taken.
I've had to cancel my credit card, and my mom has had to cancel hers, but fortunately we got them both before the scammers could run up any charges. And I guess until I hear something has changed, I'm gonna have to book my hotels directly.
#scam alert#Booking.com#I have to admit it was a pretty good one too#like way to disguise yourself as multi-factor authentication
21 notes
·
View notes
Text
Securing Active Directory Accounts
Photo by Andrea Piacquadio on Pexels.com
Active Directory is a directory service that manages user accounts and other resources on a network. It is important to secure Active Directory user accounts to prevent unauthorized access, data breaches, and identity theft. In this blog post, we will describe the step-by-step process to secure Active Directory user accounts using best practices and…

View On WordPress
#active directory#Azure Active Directory#Group Policy#Least privilege#Microsoft#Multi-Factor Authentication
2 notes
·
View notes
Link
#mfa#2fa#2factor#multifactor#authentication#rdp#vpn#how to#multi-factor authentication#remote work#cybersecurity#hybrid workforce#remove workforce#data security#data integrity#data access#access control#access security#devsecops#protect#data#data protection
2 notes
·
View notes
Text

Securing Your Virtual Doorway: Authentication vs Login Strategies
When we talk about authentication vs. login, the security of both users and businesses shouldn’t be compromised, no matter what authentication method an enterprise uses. In today's digital age, where cyber threats constantly evolve, businesses must prioritize the security of their authentication and login processes. Weak or compromised authentication methods can provide attackers with unauthorized access to sensitive data, compromising the integrity and confidentiality of business operations.
To mitigate these risks, businesses must implement robust authentication mechanisms, such as multi-factor authentication (MFA) and biometric authentication, to verify the identity of users securely. Additionally, businesses should regularly update their security protocols and conduct thorough security audits to identify and address any vulnerabilities in their authentication and login systems.
#digital identity management#social authentication#social login#consumer iam solutions#single sign on solutions#passwordless login#customer identity and access management#identity proofing#identity verification#login security#ciam solutions#data privacy#data security#multi factor authentication#identity management#single sign on#sso login#user authentication#authentication#customer experience#compliance#c
0 notes
Text
Multi-factor authentication systems | 2FA systems Face Recognition | Biometric authentication | eKYC process Dubai, Abu Dhabi, Oman, Cairo
TOPPAN IDGATE provides multi-factor authentication, and 2FA systems in Dubai, Abu Dhabi, Oman, and Cairo. TOPPAN IDGATE provides a high-intensity Biometric authentication solution in Dubai, Abu Dhabi, Oman, and Cairo. TOPPAN IDGATE’s face recognition SDKs and APIs enable comprehensive security and frictionless experiences. The retrieved data is immediately encrypted to increase the eKYC process’s security.

TOPPAN IDGATE’s acclaimed line of identity solutions aims at supporting financial institutions, commercial organizations, as well as government authorities to keep their data forgery-proof.
We deliver an end-to-end solution for every data securing need to keep individuals all around the world safe and secure.
Our solution:
do not require a user to remember any username or complex password
highly secure and offer a reliable protection
featuring state-of-the-art technology
Meeting the compliance standards of the major banks.
iDenKey uses device binding technology. Hence, users merely need to download the app on their mobile devices to activate it.
With the help of TOPPAN IDGATE’s 3 + 1 layer protection technology, security keys are efficiently obtained and transmitted to the bank terminal. We utilize encryption and asymmetric encryption technologies with dynamic authentication layers in addition to combining multi-factor authentication systems with passwords. As a result, we achieve optimal security.
These multiple protection measures can prevent data leakages, enhance soft token security, and provide greater security than the traditional username and password format.
official Gmail: [email protected]
Address: 6F., No. 1, Ningbo E. St., Zhongzheng Dist., Taipei City 10093, Taiwan (R.O.C.)
PH: 886-2-2741 3066
#Multi-factor authentication systems Dubai#2FA systems Dubai#Face Recognition Dubai#Biometric authentication Dubai#eKYC process Dubai#Multi-factor authentication systems Abu Dhabi#2FA systems Abu Dhabi#Face Recognition Abu Dhabi#Biometric authentication Abu Dhabi#eKYC process Abu Dhabi#Multi-factor authentication systems Oman#2FA systems Oman#Face Recognition Oman#Biometric authentication Oman#eKYC process Oman#Multi-factor authentication systems Cairo#2FA systems Cairo#Face Recognition Cairo#Biometric authentication Cairo#eKYC process Cairo#technology#design#science#business#developers & startups#news
2 notes
·
View notes
Text
Cybersecurity Report: Protecting DHS Employees from Scams Targeting Personal Devices
🔒 DHS Cybersecurity Alert! 🔒 Scammers targeting personal devices threaten national security. Our new report reveals these risks & offers robust solutions - MFA, security software, cybersecurity training & more. Safeguard yourself & critical operations!
Introduction
The digital age has ushered in an era of unprecedented connectivity and technological advancements, but it has also given rise to a new breed of threats that transcend traditional boundaries. Cybercriminals are constantly evolving their tactics, exploiting vulnerabilities in both organizational systems and personal devices to gain unauthorized access, steal sensitive data, and…

View On WordPress
#access controls#antivirus#awareness campaigns#best practices#collaboration#cyber resilience#cybersecurity#cybersecurity training#data backup#data protection#DHS#firewall#government#impersonation#incident response#insider threats#malware#multi-factor authentication#national security#password management#personal device security#phishing#physical security#public outreach#risk assessment#scams#social engineering#software updates#threat intelligence#VPN
0 notes
Text
Multi-Factor Authentication in India

Multi-Factor Authentication: Stepping Up Your Security Game In 2024
In today's digital world, our precious data is constantly under siege. Hackers, data thieves, and malicious actors lurk around every corner, waiting for the weakest link in our online defenses. While strong passwords are a crucial first line of defense, they're no longer enough. Enter Multi-Factor Authentication (MFA), the superhero of online security, ready to add an extra layer of protection to your digital fortress.
What Is MFA?
Imagine a bank vault protected by not just a single lock, but multiple layers of security: a thick steel door, a keypad requiring a complex code, and finally, a biometric scanner for double verification. That's essentially how MFA works for your online accounts. Instead of relying solely on a password (the single lock), MFA adds additional "factors" of authentication, making it exponentially harder for unauthorized access.
Secure Key Management
One of the primary functions of HSMs is secure generation, storage, and management of cryptographic keys, preventing unauthorized usage and potential breaches.
These Factors Can Be Categorized Into Three Main Groups:
Something you know:This could be your traditional password, a PIN, or a security question answer. While not the strongest factor alone, it's still a basic hurdle for attackers.
Something you have:This might be your smartphone, a physical security key, or a one-time password (OTP) generated by an app. Having physical possession of the item adds another layer of difficulty for malicious actors.
Something you are:This is where biometrics like fingerprints, facial recognition, or iris scans come into play. These unique physiological characteristics offer the highest level of security, as they're nearly impossible to replicate.
Why Multi-Factor Authentication Is Necessary?
Digital security is critical in today's world because both businesses and users store sensitive information online. Everyone interacts with applications, services, and data that are stored on the internet using online accounts. A breach, or misuse, of this online information could have serious real-world consequences, such as financial theft, business disruption, and loss of privacy.
While passwords protect digital assets, they are simply not enough. Expert cybercriminals try to actively find passwords. By discovering one password, access can potentially be gained to multiple accounts for which you might have reused the password. Multi-factor authentication acts as an additional layer of security to prevent unauthorized users from accessing these accounts, even when the password has been stolen. Businesses use multi-factor authentication to validate user identities and provide quick and convenient access to authorized users
The benefits of MFA extend far beyond personal accounts. Businesses that implement MFA for employee access can significantly strengthen their cybersecurity posture, protecting sensitive data and reducing the risk of costly data breaches. Governments and organizations handling critical infrastructure can also leverage MFA to safeguard vital systems and information.
Different Multi-Factor Authentication (MFA) Choices Cater To Mobile Devices
Enhancing security while offering varied benefits
One-Time Passwords (OTP):
Innovative applications generate OTPs, similar to traditional security tokens, sent via time-based SMS.
Utilizing a smartphone or tablet eliminates the need for physical tokens, reducing replacement costs for companies.
Biometric Authentication:
Leading smartphone manufacturers prioritize security concerns by offering biometric authentication options.
These features ensure that only authorized users access devices, yet each technique comes with its own set of pros and cons.
How Is Multi-Factor Authentication Implemented In The Cloud?
As businesses transition various aspects like data storage, communication, server infrastructure, and more to the cloud, IT administrators grapple with the challenges of departing from traditional on-premises setups. Ensuring secure user access becomes paramount in safeguarding sensitive data within cloud environments.
Major tech players such as Microsoft, Google, Amazon Web Services, Facebook, and Twitter recognize this need for heightened security. They've embraced two-factor authentication for entry into their cloud services, with some progressively expanding into more advanced multi-factor authentication protocols.
Multi-Factor Authentication For Microsoft 365
Multi-Factor Authentication in Microsoft 365 strengthens security measures for accessing applications on PCs, Macs, and mobile devices. Upon login, users receive a random 16-character token via the Microsoft 365 admin tool, initiating the authentication process. Afterward, users can set up additional layers of verification, including:
Call My Mobile Phone: Users press # upon receiving a confirmation call to log in via their mobile device.
Call My Office Phone: Similar to the mobile option, the confirmation call is directed to a separate line, such as a desk phone.
Text Code to My Mobile Phone: A code sent via SMS to the user's phone, entered into the Microsoft 365 login form.
Notify Me through App: Utilizing a Microsoft smartphone app (available for Windows Phone, iPhone, and Android) to receive and confirm notifications.
Show One-Time Code in App: Utilizing the same app as the Notify Me feature, a one-time, six-digit code is provided for login verification within the Microsoft 365 interface.
How Can Multi-Factor Authentication Enhance Security?
Heightened Security: MFA significantly raises the bar for security by requiring multiple forms of verification. This makes it exponentially harder for hackers to gain unauthorized access.
Compliance Adherence: In various industries, compliance standards necessitate robust security measures. MFA aids in meeting these standards, ensuring adherence to regulations such as GDPR, HIPAA, and PCI-DSS.
Versatility and Adaptability: MFA solutions are versatile and adaptable, allowing integration across diverse platforms and devices. From mobile apps generating time-based tokens to hardware tokens and biometric authentication, the options cater to different user preferences and security needs.
Implementing MFA: From Zero To Hero
The good news is that implementing MFA is easier than ever. Most major online platforms and services offer built-in MFA options, often with just a few clicks in your account settings. Here are some quick tips:
Start with the essentials: Enable MFA for your email, bank accounts, social media profiles, and any other platform where you store sensitive information.
Choose the right factors: Consider a combination of convenience and security when selecting your MFA methods. Avoid relying solely on SMS OTPs.
Educate yourself and others: Spread awareness about MFA and its importance within your family, friends, and workplace.
Stay vigilant: Keep your software and devices updated to patch vulnerabilities and maintain strong security practices.
MFA: Not Just A Buzzword, A Necessity
In today's digital landscape, cybersecurity is no longer optional. Multi-Factor Authentication is a powerful tool that can significantly improve your online security posture, protecting your valuable data and accounts from unauthorized access. Don't wait for a data breach to wake you up - take control of your security and embrace the power of MFA today.
Remember, a little extra effort now can save you a lot of heartache and headaches in the future. So, choose the most suitable MFA method and strengthen your mobile security today!
JNR Management is best Multi-Factor Authentication in India
#Multi-Factor Authentication#Multi-Factor Authentication in India#Multi-Factor Authentication in Delhi#Multi-Factor Authentication in Mumbai#Multi-Factor Authentication in Bangalore#MFA#2FA
0 notes
