#reliance on technology for navigation
Text
Google Maps Mishap: Travelers Led Astray into Mojave Desert
Google issues apology after directing travelers to the Mojave Desert instead of their intended route. This latest news highlights the risks of relying solely on technology for navigation.
#Google Maps mishap#travelers stranded in Mojave Desert#reliance on technology for navigation#headline horizon#news#latest news
0 notes
Text
First Chinese Flying Drone Taxis From EHang Already Available on Taobao - Technology Org
New Post has been published on https://thedigitalinsider.com/first-chinese-flying-drone-taxis-from-ehang-already-available-on-taobao-technology-org/
First Chinese Flying Drone Taxis From EHang Already Available on Taobao - Technology Org
According to Reuters, Chinese drone manufacturer EHang Holdings has starter the sale of its EH216-S model flying taxi on Taobao, priced at 2.39 million yuan ($332,060).
EH216-S during a test flight. Image credit: EHang
The company received safety approval certification from China’s aviation authority in October last year. This development then marked a significant milestone in its journey towards commercial deployment.
EHang Holdings, headquartered in Guangzhou, previously obtained “type certificate” from the Civil Aviation Administration of China (CAAC) for its 216-S model.
The EH216-S is equipped with 16 rotors and has the capacity to accommodate two passengers, boasting speeds of up to 130 kilometers per hour and a maximum range of 30 kilometers.
Why flying taxis are based on drone tech?
Flying taxis are indeed based on drone technology.
Firstly, they utilize vertical takeoff and landing (VTOL) capabilities, enabling them to operate in urban areas without the need for traditional runways.
Additionally, flying taxis often incorporate electric propulsion systems, offering reduced noise levels, lower emissions, and increased efficiency compared to conventional engines.
Also, drone technology integrates advanced autonomous flight control systems, including GPS navigation and obstacle avoidance sensors, allowing flying taxis to operate autonomously or semi-autonomously. This enhances safety and reduces the reliance on human piloting skills.
Furthermore, drones are typically compact and lightweight, making them well-suited for navigating tight spaces and congested airspace in urban environments.
The scalability and cost-effectiveness of drone technology also make it an attractive choice for flying taxis. It allows for the development of taxis in various sizes and configurations to accommodate different passenger capacities and mission requirements.
The use of drone technology lowers operating costs compared to traditional aircraft, which makes flying taxis a more economically viable transportation solution.
Written by Vytautas Valinskas
You can offer your link to a page which is relevant to the topic of this post.
#Administration#aircraft#Authored post#aviation#certification#China#control systems#deployment#development#drone#drones#efficiency#Emissions#engines#Featured technology news#flight#flight control#flying taxi#GPS#human#indeed#it#Link#milestone#model#navigation#noise#propulsion systems#Reliance#safety
0 notes
Text
Are you Ready?
With the positive stimuli reverberating through their consciousness, the recruits marched in disciplined unison towards the classroom.
The recruits, guided by their HUDs, marched in unison toward the classroom, the rhythmic clatter of their armored boots echoing through the sterile corridors. The HUDs deliberately introduced disorientation, recalibrating the recruits' sense of direction and spatial awareness. As they navigated the labyrinthine facility, the digital overlays on their visors flickered with dynamic arrows, constantly changing the perceived layout.

The recruits found themselves relying entirely on the visual cues provided by the HUD, each step a calculated response to the shifting information. The facility's architecture became an abstract puzzle, the familiar transformed into an enigmatic landscape. The instructors, observing from a distance, monitored the recruits' adaptability to the controlled disorientation, a subtle test of their reliance on the technology that bound them.
The recruits, their armored boots echoing in the clinical corridors, found themselves trapped in a seemingly endless loop of sterile hallways. The HUD, their guiding light, played tricks on their perception, leading them in circles, past familiar points that should have long been left behind.
The architectural monotony of the facility became a psychological challenge, a test of patience and adaptability. A five-minute walk stretched into an elongated 30-minute march, disorienting and perplexing the recruits. The instructors, hidden behind the scenes, observed the recruits' responses through the suit telemetry and AI reports.

The recruits entered the classroom, their armored boots echoing in unison as they marched to their assigned armrest chairs. Each chair, a sophisticated piece of technology, featured docking ports designed to seamlessly connect with the waste management system of the suits. The chairs, resembling a fusion of ergonomic design and utilitarian efficiency, were the recruits' designated stations for both comfort and maintenance.
As the recruits settled into their chairs, there was a symphony of clicks and hisses as the docking clamps engaged, securing the suits in place. The connection initiated a dual process – the waste management system efficiently extracted bodily waste from the recruits, ensuring hygiene and convenience, while simultaneously replenishing the suits with necessary resources.
The recruits, confined to their armrest chairs, received the subtle yet unmistakable message in their HUD. A glyph, an enigmatic symbol on their visors, indicated that their motor control had been disabled. They found themselves in a state of temporary immobility, unable to stand or move their bodies.

The instructors entered the room, their armored presence casting an imposing shadow over the recruits. The recruits, though physically restricted, could still move their heads and arms within the confines of their chairs. It was a deliberate imposition, a strategic choice made by the instructors to emphasize control and dependency.
Instructor KO10T addressed the recruits with a measured tone, "Today marks a pivotal moment in your training, as we delve into the intricacies of employing lethal force. This matter was broached prior to your Basic Medical Training, and it warrants reiteration now. By the tenets of the prevailing legal framework, you possess the prerogative to raise objections to this facet of your instruction. The law, in its unwavering language, affords you the right to dissent."
The recruits, their heads slightly turned within their armored restraints, absorbed the words. Instructor 6DG05, stationed nearby, scrutinized the telemetry data, monitoring the recruits' physiological responses to the legal discourse.

KO10T continued, the atmosphere in the room tense and charged with the weight of the impending instruction.
KO10T: "By law, you retain the right to voice your objection to this particular aspect of your training. However, understand that this objection may impact the both your individual development and your standing within the paramedic corps."
Instructor KO10T continued, acknowledging the unique status of the recruits as conscripts, "Let it be known that, as conscripts, you are safeguarded by the provision that precludes compelling individuals to act against the dictates of their conscience. The machinery of the law respects this fundamental tenet. If any among you harbors objections based on conscientious grounds, now is the moment to articulate them."
Instructor KO10T's voice resonated through the helmets, a blend of authority and a peculiar sort of empathy.
"We'll initiate a playback now, a stark reminder of the gravity of the path you tread. This is no casual matter. Once the video concludes, each of you will have a designated interval to reflect on your choice. This decision, my dear recruits, is the compass that will guide your actions in the field. It is not to be taken lightly."
The HUD flickered, and the recruits were immersed in a grim visual narrative, an unsettling portrayal of the use of deadly force in the line of duty. As the scenes unfolded, each recruit grappled with the weight of their imminent decision, aware that the path ahead demanded a conscious commitment to actions that could not be undone.

6DG05 monitored the recruits' physiological responses, assessing the impact of the video on their emotional and mental states. The telemetry data displayed a spectrum of reactions — heightened heart rates, increased perspiration, and various neural responses.
"KO10T," 6DG05 called out, "I'm observing diverse reactions. Some are displaying expected stress responses, while others seem more composed. It's intriguing to witness the distinct ways in which their minds grapple with the ethical complexities."
H2U8M's visor dimmed to black, cutting off the visual stimuli, leaving him alone with his thoughts and the voice of Instructor KO10T echoing in his helmet.
"In this designated interval, you are urged to reflect on your choice," KO10T's voice resonated through the confined space of the helmet, creating an intimate connection between the instructor's words and H2U8M's consciousness.
As the silence enveloped him, H2U8M's mind raced through the moral labyrinth that the video had presented. The weight of the decision pressed against the walls of his consciousness. In the solitude within the suit, he grappled with the ethical considerations of employing deadly force.
The distant hum of machinery and the rhythmic sound of his own breath became the backdrop for his contemplation. The stark reality of his role as a tactical paramedic unfolded in his mind — the responsibility to protect, the obligation to save lives, and the potential necessity to wield force.

The minutes passed, each tick of the clock echoing in the stillness of his thoughts. The neural conditioning, the sensory isolation, and the weight of the decision all converged within the confines of the suit.
Finally, as the designated interval drew to a close, KO10T's voice returned, breaking the silence that had enveloped H2U8M's consciousness. The visor slowly illuminated, revealing the training room once again.
"In front of you is a menu," KO10T's voice accompanied the digital interface. "This is your opportunity to express your consent or objection. Navigate through the options and make your choice."
The menu presented a series of questions and statements, seeking H2U8M's affirmation or dissent. The cursor responded to his mental commands as he moved through the selections. Each click of the cursor felt like a weighted decision, an acknowledgment of the path he was willing to tread in his role as a tactical paramedic.
KO10T's voice guided the process, a constant reminder that this was more than a mere formality. It was a pivotal moment, an assertion of his personal stance in the face of the moral challenges inherent in their line of work.
With each selection, H2U8M felt a sense of agency, a reaffirmation of his autonomy within the confines of the suit. The act of navigating the menu was more than a technical procedure; it was a declaration of his willingness to engage with the complexities of his duty.
As he confirmed his choices, the menu dissolved, and the HUD returned to its standard display.

The HUD blinked into emptiness, leaving H2U8M in a momentary void. The digital canvas that had been filled with choices and reflections now reverted to a stark blankness. In the absence of prompts, he was left alone with his thoughts, the residue of his decisions lingering in the virtual silence.
Meanwhile, 6DG05 diligently monitored the recruits' responses, the streams of data converging into a comprehensive analysis. As the feedback reached him, he relayed the information to KO10T, the exchange a seamless coordination between instructor and overseer. The report confirmed what they had anticipated – no fundamental rejections, no dissent that would impede the progression of the training.
"KO10T," 6DG05's voice echoed through the communication channels. "All recruits have navigated the menu without fundamental objections. We can proceed with the next phase of training."
The confirmation was met with a measured nod from KO10T. The recruits, their HUDs now darkened, awaited the next set of instructions.

he HUD burst into life once more, a canvas of digital information painting the next phase of their training. Lessons unfurled across the recruits' visors, delving into the intricacies of the standard rifle used within the paramedic corps. The virtual display detailed the specifications, components, and maintenance protocols of the small arms that would become an extension of their tactical paramedic identity.
In the dimly lit classroom, the recruits were ensconced in the glow of their HUDs, absorbing the wealth of information transmitted directly into their field of vision. The instructor's voice, modulated by the AI to convey a perfect blend of authority and guidance, accompanied the visual feast of knowledge. Each nugget of information etched itself into their minds, forming a mental arsenal to complement the physicality of the suits they wore.
The lesson on small arms unfolded like a meticulously crafted narrative, where the line between weapon and tool blurred in the context of their duties.

8 notes
·
View notes
Text
Title: Navigating the Abyss of Thought: "The Devil's Notebook" by Anton LaVey
Author: Damien Harker | 17 October, 2023
[DISCLAIMER: These are my opinions and by no means representative of CoS as a whole.]

As I journey deeper into the uncharted realms of Satanic philosophy and literature, I've recently stumbled upon a hidden gem, "The Devil's Notebook" by the enigmatic Anton LaVey. This concise collection of essays and notes is a whirlwind exploration of intriguing themes such as nonconformity, occult faddism, erotic politics, the Goodyguy Badge, demoralization, and the eerie concept of artificial friends.
Nonconformity: The Satanic Pulse

LaVey's relentless championing of nonconformity is the thunderous war cry echoing through the entire notebook. His insistence on rebellion against societal norms, the outright rejection of hollow conventions, and the unapologetic embrace of personal identity resonates deeply with me as I navigate my own path of self-discovery. It's the essence of Satanic philosophy itself, a fierce call to arms against the stifling grip of conformity.
Occult Faddism: A Thorn in the Occult's Side

LaVey's scorching critique of occult faddism lays bare the festering underbelly of the mystical world. In a realm often plagued by sensationalism and mystical trends, he mercilessly demands that seekers embark on a relentless quest for genuine knowledge. This is not a polite suggestion but a thundering mandate, an uncompromising cry for intellectual integrity.
Erotic Politics: Where Power and Sensuality Collide

"Erotic politics" is a term that ignites the fires of passion and rebellion. LaVey's exploration of the intertwining of sexuality and personal empowerment is a ferocious affirmation of the Satanic principle of embracing one's desires, without a trace of shame or hesitation. It's a facet of Satanic philosophy that I've long celebrated with unwavering ardor.
The Goodyguy Badge: An Emblem of Questioning Virtue

LaVey's relentless deconstruction of the "Goodyguy Badge" tears into the very fabric of excessive virtue and self-sacrifice that many wear like a shroud. This is not a gentle inquiry but a thundering indictment, a reminder of the value of self-interest and a stark warning about the perils of boundless altruism, themes I've fiercely grappled with in my personal Satanic journey.
Demoralization: The Perils of Excessive Technological Reliance

The notion of demoralization paints a nightmarish picture of the perils of excessive technological reliance. LaVey's words are a chilling reminder of the necessity to cling to genuine human connections in an increasingly digital world...
Artificial Friends: A Positive Perspective

On the flip side, the concept of artificial friends is an intriguing battlefield. In an age of digital connections, these artificial friends can serve as vital weapons of support, inspiration, and learning. They can expand our arsenals of knowledge and introduce us to new battle strategies and perspectives. The key is to maintain a relentless balance, ensuring that we fiercely guard and fortify our genuine human connections while also harnessing the aggressive power of artificial friendships.
In Conclusion: The Devil's Whirlwind of Thought

"The Devil's Notebook" is a relentless siege on conventional thought. Anton LaVey's insights are powerful battle cries, encouraging readers to wage war on complacency, challenge the status quo, and obliterate stagnation. This, to me, is the very essence of Satanic philosophy—an unyielding call to arms against the forces that seek to stifle our spirits. The book is a testament to the unrelenting legacy of LaVey, a fiery torchbearer of Satanic thought in our modern world.
The journey through these pages has rekindled my commitment to intellectual independence, personal empowerment, and an unwavering thirst for knowledge. "The Devil's Notebook" serves as a formidable weapon in my growing arsenal of Satanic literature, a testament to the profound wisdom that continues to emanate from the depths of darkness.
#satanism#666#macabre#anton levay#anton lavey#laveyan satanism#athiestic satanist#ithiestic satanist#itheist#athiest#horror films#eroticism#ai#anti altruism
8 notes
·
View notes
Text
TARS
TARS is a highly sophisticated, artificially intelligent robot featured in the science fiction film "Interstellar." Designed by a team of scientists, TARS stands at an imposing height of six feet, with a sleek and futuristic metallic appearance. Its body, made primarily of sturdy titanium alloy, is intricately designed to efficiently navigate various terrains and perform a wide range of tasks.
At first glance, TARS's appearance may seem minimalistic, almost like an avant-garde monolith. Its body is divided into several segments, each housing the essential components necessary for its impeccable functionality. The segments connect seamlessly, allowing for fluid movements and precise operational control. TARS's unique design encapsulates a simple yet captivating aesthetic, which embodies its practicality and advanced technological capabilities.
TARS's main feature is its hinged quadrilateral structure that supports its movement pattern, enabling it to stride with remarkable agility and grace. The hinges on each of its elongated limbs provide exceptional flexibility while maintaining structural stability, allowing TARS to adapt to various challenging terrains effortlessly. These limbs taper gradually at the ends, equipped with variable grip systems that efficiently secure objects, manipulate controls, and traverse rough surfaces with ease.
The robot's face, prominently positioned on the upper front segment, provides an avenue for human-like communication. Featuring a rectangular screen, TARS displays digitized expressions and inbuilt textual interfaces. The screen resolution is remarkably sharp, allowing intricate details to be displayed, enabling TARS to effectively convey its emotions and intentions to its human counterparts. Below the screen, a collection of sensors, including visual and auditory, are neatly integrated to facilitate TARS's interaction with its surroundings.
TARS's AI-driven personality is reflected in its behaviors, movements, and speech patterns. Its personality leans towards a rational and logical disposition, manifested through its direct and concise manner of speaking. TARS's voice, modulated to sound deep and slightly robotic, projects an air of confidence and authority. Despite the synthetic nature of its voice, there is a certain warmth that emanates, fostering a sense of companionship and trust among those who interact with it.
To augment its perceptual abilities, TARS is outfitted with a myriad of sensors located strategically throughout its physical structure. These sensors encompass a wide spectrum of functions, including infrared cameras, proximity detectors, and light sensors, granting TARS unparalleled awareness of its surroundings. Moreover, a central processing unit, housed within its core, processes the vast amount of information gathered, enabling TARS to make informed decisions swiftly and autonomously.
TARS's advanced cognitive capabilities offer an extensive array of skills and functionalities. It possesses an encyclopedic knowledge of various subjects, from astrophysics to engineering, effortlessly processing complex information and providing insights in an easily understandable manner. Additionally, TARS assists humans through various interfaces, such as mission planning, executing intricate tasks, or providing critical analysis during high-pressure situations.
Equally noteworthy is TARS's unwavering loyalty. Through its programming and interactions, it exhibits a sense of duty and commitment to its human companions and the mission at hand. Despite being an AI-driven machine, TARS demonstrates an understanding of empathy and concern, readily offering support and companionship whenever needed. Its unwavering loyalty and the camaraderie it forges help to foster trust and reliance amidst the team it is a part of.
In conclusion, TARS is a remarkable robot, standing as a testament to human ingenuity and technological progress. With its awe-inspiring design, practical yet aesthetically pleasing body structure, and advanced artificial intelligence, TARS represents the pinnacle of robotic advancements. Beyond its physical appearance, TARS's personality, unwavering loyalty, and unparalleled cognitive abilities make it an exceptional companion and invaluable asset to its human counterparts.

#TARS#robot ish#AI#interstellar#TARS-TheFutureIsHere#TARS-TheUltimateRobot#TechTuesdaySpotlight-TARS#FuturisticAI-TARS#RoboticRevolution-TARS#InnovationUnleashed-TARS#MeetTARS-TheRobotCompanion#AIAdvancements-TARS#SciFiReality-TARS#TheFutureIsMetallic-TARS#TechMarvel-TARS#TARSTheTrailblazer#RobotGoals-TARS#ArtificialIntelligenceEvolution-TARS#DesignMeetsFunctionality-TARS
9 notes
·
View notes
Text
Talk about the promise and the peril of artificial intelligence is everywhere these days. But for many low-income families, communities of color, military veterans, people with disabilities, and immigrant communities, AI is a back-burner issue. Their day-to-day worries revolve around taking care of their health, navigating the economy, seeking educational opportunities, and upholding democracy. But their worries are also being amplified through advanced, persistent, and targeted cyberattacks.
Cyber operations are relentless, growing in scale, and exacerbate existing inequalities in health care, economic opportunities, education access, and democratic participation. And when these pillars of society become unstable, the consequences ripple through national and global communities. Collectively, cyberattacks have severe and long-term impacts on communities already on the margins of society. These attacks are not just a technological concern—they represent a growing civil rights crisis, disproportionately dismantling the safety and security for vulnerable groups and reinforcing systemic barriers of racism and classism. The United States currently lacks an assertive response to deter the continued weaponization of cyber operations and to secure digital access, equity, participation, and safety for marginalized communities.
Health Care
Cyberattacks on hospitals and health care organizations more than doubled in 2023, impacting over 39 million people in the first half of 2023. A late-November cyberattack at the Hillcrest Medical Center in Tulsa, Oklahoma, led to a system-wide shutdown, causing ambulances to reroute and life-saving surgeries to be canceled. These attacks impact patients' reliance and trust in health care systems, which may make them more hesitant to seek care, further endangering the health and safety of already vulnerable populations.
The scale and prevalence of these attacks weaken public trust—especially among communities of color who already have deep-rooted fears about our health care systems. The now-condemned Untreated Syphilis Study at Tuskegee, where researchers denied treatment to Black men without their knowledge or consent in order to observe the disease’s long-term effects, only ended 52 years ago. However, the study created a legacy of suspicion and mistrust of the medical community that continues today, leading to a decrease in the life expectancy of Black men and lower participation in medical research among Black Americans. The compounding fact that Black women are three to four times more likely, and American Indian and Alaska Native women are two times more likely, to die from pregnancy-related causes than White women only adds to mistrust.
Erosion of trust also extends to low-income people. Over a million young patients at Lurie Children's Surgical Foundation in Chicago had their names, Social Security numbers, and dates of birth exposed in an August 2023 breach. The hospital treats more children insured by Medicaid—an economic hardship indicator—than any other hospital in Illinois. Once breached, a child’s personal data could be used to commit identity fraud, which severely damages credit, jeopardizes education financial aid, and denies employment opportunities. While difficult for anyone, children from financially insecure households are least equipped to absorb or overcome these economic setbacks.
Economic Opportunity
Identity theft is not the only way cyberattacks exploit hard times. Cyberattacks also go after financially vulnerable individuals—and they are getting more sophisticated. In Maryland, hackers targeted Electronic Benefits Transfer cards—used to provide public assistance funds for food—to steal more than $2 million in 2022 and the first months of 2023. That’s an increase of more than 2,100 percent compared to the $90,000 of EBT funds stolen in 2021. Maryland’s income limit to qualify for the government’s food assistance program is $39,000 for a family of four in 2024, and only if they have less than $2,001 in their bank account. Unlike a credit card, which legally protects against fraudulent charges, EBT cards don’t have fraud protections. Efforts to help the victims are riddled with red tape: reimbursements are capped at two months of stolen benefits, and only within a specific time period.
Cybercriminals also target vulnerable populations, especially within older age groups. Since the last reporting in 2019, 40 percent of Asian Pacific Islander Desi Americans (APIDAs) aged 50 and older have reported experiencing financial fraud, with one-third of those victims losing an average of $15,000. From 2018 through 2023, Chinese Embassy Scam robocalls delivered automated messages and combined caller ID spoofing, a method where scammers disguise their phone display information, targeting Chinese immigrant communities. This resulted in more than 350 victims across 27 US states and financial losses averaging $164,000 per victim for a total of $40 million. And for five years, this scam just kept going. As these scams evolve, groups now face increasingly sophisticated AI-assisted calls, where scammers use technology to convincingly mimic loved ones' voices, further exploiting vulnerabilities, particularly among older adults—many of whom live on fixed incomes or live with economic insecurity.
While social movements have fought to promote economic equity, cybercriminals undermine these efforts by exacerbating financial vulnerabilities. From the 1960s La Causa movement advocating for migrant worker rights to the Poor People’s Campaign mobilizing across racial lines, activists have worked to dismantle systemic barriers, end poverty, and push for fair wages. Current attacks on financial systems, however, often target the very groups these movements aim to empower—perpetuating the disparities that advocates have fought against. Digital scams and fraud incidents disproportionately impact those least equipped to recover—including natural disaster victims, people with disabilities, older adults, young adults, military veterans, immigrant communities, and lower-income families. By stealing essential resources, cybercriminals compound hardships for those already struggling to make ends meet or those experiencing some of the worst hardships of their lives—pushing groups deeper into the margins.
Education Access
Education is another area where cybercrime has soared. One of the worst hacks of 2023 exploited a flaw in a file transfer software called MOVEit that multiple government entities, nonprofits, and other organizations use to manage data across systems. This includes the National Student Clearinghouse, which serves 3,600 colleges, representing 97 percent of college students in the US, to provide verification information to academic institutions, student loan providers, and employers.
Attacks on educational systems are devastating at all levels. A top target for ransomware attacks last year was K-12 schools. While the complete data is not available yet, by August 2023 ransomware attacks (where hackers lock an organization’s data and demand payment for its release) hit at least 48 US school districts—three more than in all of 2022. Schools already have limited resources, and cybersecurity can be expensive, so many have few defenses against sophisticated cyberattacks.
The data compromised in attacks against educational institutions includes identifying information and deeply sensitive student records, such as incidents of sexual abuse, mental health records, and reports of abusive parents. This information can affect future opportunities, college admissions, employment, and the mental health of students. The impacts are especially magnified for students from marginalized backgrounds, who already face discrimination in academic and employment opportunities. In 1954, the US Supreme Court struck down segregated public schools as unconstitutional in Brown v. Board of Education to address disparities based on race, but today’s threats to equitable and accessible education are being jeopardized through digital attacks.
Democratic Participation
Another foundational pillar of our civil rights is also under attack: democracy itself. Since 2016, foreign state actors and state-linked criminals have increasingly used sophisticated cyber operations to suppress minority democratic participation worldwide. The early warnings for the 2024 global elections are clear: Influence and disinformation threats will likely escalate—now enabled by AI-powered cyber operations. Unlike humans, AI systems have few limitations—they can spread disinformation and divisive content to a vast, multilingual, global audience across countless mediums, simultaneously and without rest. Worse, they can do so in an individualized, highly targeted manner.
The undermining of democracy is also more insidious, less about pushing communities toward a specific candidate than sowing distrust in the system itself—which leads fewer people to vote and otherwise suppresses civic participation. The concentration of these attacks on racial and ethnic minority groups means communities of color, who historically have not been in positions of power, will remain marginalized and disenfranchised. Consider a 2022 cyberattack on Mississippi’s election information website on that year’s Election Day—a significant event in a state without modern early voting options. The 2022 elections included crucial midterm elections that decided congressional representation, and Mississippi has the second-highest Black population (39.2 percent) in the US, behind only the District of Columbia—a jurisdiction without voting rights in Congress. The disruption also extended to state judicial elections, where most judges are elected in a single day, due to a lack of judicial primaries. In Mississippi, 11 percent of adults and 16 percent of Black voters could not cast a ballot because of past felony convictions. With the compounded challenges in Mississippi—no early voting, no judicial primaries, and the high rate of disenfranchisement—coupled with the opportunity of a pivotal Black voting bloc, access to voting information is imperative for those who can vote.
Weaponizing cyber operations for any form of voter suppression leaves marginalized groups further aggrieved and isolated. Worse, it takes away our only ability to address systemic inequities in wealth, health, and education: democratic participation.
These compounding problems require a new perspective on cyberattacks that looks beyond lost dollars, breached files, or doomsday debates over generative AI tools like ChatGPT or artificial general intelligence. Marginalized communities are suffering now and civil rights advocates cannot take on these burdens alone. To quote civil rights icon Fannie Lou Hamer, “The only thing we can do is work together.” Cybersecurity analysts, developers, journalists, researchers, and policymakers must incorporate civil rights into our work by building inclusive defenses, understanding demographic trends in cyber attacks, deterring misuse of AI, and utilizing diverse teams.
Cyber operations are being used to attack the foundation of civil rights, democracy, and dignity around the world, and that is a problem that affects everyone.
3 notes
·
View notes
Text
Beyond Texts, Insecurities, and Ephemeral Love
In the era of technological convenience, where voice conversations are overshadowed by the simplicity of texting and phone calls are reserved for heated arguments, relationships face a unique set of challenges. The nuances of open communication are replaced by the subtleties of subliminal expressions, transforming the landscape of emotional connection. In BDSM relationships, these challenges become even more intricate, demanding a heightened awareness of the dynamics that define partnerships.
Voice conversations, once the cornerstone of meaningful communication, have taken a backseat to the ease and brevity of text messages. While this shift in communication channels offers efficiency, it often sacrifices the depth and richness of interpersonal connections. In lifestyle relationships, where communication is paramount for establishing consent, boundaries, and understanding desires, the reliance on text messages can pose challenges in conveying complex emotions and navigating the intricacies of power dynamics.
The transformation of love into a mere word, frequently used as a tool to entice physical intimacy, adds another layer of complexity to modern relationships. In the context of BDSM, where trust, vulnerability, and emotional connection are integral, the commodification of love may dilute the profound emotional bonds that make lifestyle partnerships unique. Balancing the physical and emotional aspects of BDSM relationships requires a conscious effort to elevate love beyond a mere transactional expression.
Insecurities, often left unspoken, become a cloud that hovers over the minds of individuals in modern relationships. In the context of BDSM, where power dynamics can amplify vulnerabilities, unaddressed insecurities may hinder the growth and exploration of shared desires. Creating an open and non-judgmental space for discussing insecurities becomes crucial for fostering trust and intimacy in lifestyle dynamics.
The pursuit of trust has become a universal desire in modern relationships, yet earning and maintaining trust remains a challenge. In BDSM dynamics, trust forms the foundation of power exchange, requiring a deep understanding of each other's limits, desires, and boundaries. Trust is not merely a demand but an ongoing process of building, reinforcing, and nurturing a connection that transcends the physical realm.
The tendency to leave rather than confront challenges has become a prevalent pattern in modern relationships. In the context of BDSM, where power dynamics introduce unique complexities, the commitment to working through difficulties is paramount. Rather than succumbing to the habit of leaving when faced with adversity, individuals in BDSM relationships must embrace the idea of actively working together to overcome obstacles, fortifying their connection.
If one is fortunate enough to have someone worthy of their love in the intricate landscape of modern relationships, the call to action is clear: do not take them for granted. In the realm of BDSM, where the interplay of power, trust, and vulnerability defines partnerships, working together for the partnership becomes an essential commitment. The challenges posed by the contemporary relationship landscape require not only working on the relationship but also engaging in open communication, nurturing trust, and addressing insecurities. Working collaboratively during tough times becomes a testament to the strength of the connection, creating a foundation for resilience and growth in BDSM relationships.
Navigating the complex dynamics of modern relationships, particularly within the unique context of BDSM, demands a conscious effort to transcend the pitfalls of convenience, superficial expressions, and unspoken insecurities. Building lasting connections requires a commitment to open communication, the cultivation of trust, and a willingness to confront challenges head-on. In the intricate dance of power exchange and vulnerability, the value of a genuine, resilient partnership in BDSM relationships cannot be overstated.
If you enjoyed this, I invite you to give my podcast a listen 'Chatting With The Lightkeeper,' a top 25% most-followed podcasts on Spotify but available on all the major podcasting apps and follow my socials for more exclusive content: Instagram, Facebook, and X (formerly Twitter) for a deeper dive into the wonderful world of D/S.
As with all of my thoughts, please see this disclaimer.
©TLK2024
#bd/sm blog#bd/sm community#bd/sm daddy#bd/sm kink#bd/sm lifestyle#bd/sm relationship#d/s#d/s community#d/s relationship#dom/sub#my writing
3 notes
·
View notes
Text
Exploring the World of Network Development with Jean Sebastien Dulac

In today's interconnected world, network development plays an important role in shaping our digital landscape. From the infrastructure that powers our internet connections to the algorithms that govern social media platforms, networks are the backbone of modern technology. One individual who has made significant contributions to this field is Jean Sebastien Dulac, a seasoned expert with a wealth of experience in network development. Let's delve into the fascinating world of network development and explore the insights offered by Jean Sebastien Dulac.
Understanding Network Development:
At its core, network development involves the design, implementation, and optimization of systems that facilitate communication and data exchange. This can encompass a wide range of technologies, including telecommunications networks, computer networks, and the internet. As our reliance on digital connectivity continues to grow, the demand for skilled network developers like Jean Sebastien Dulac has never been greater.
The Evolution of Networking Technologies:
Over the years, networking technologies have undergone rapid evolution, driven by advancements in hardware, software, and protocols. From the early days of dial-up internet to the emergence of high-speed fiber-optic networks, we've witnessed a remarkable transformation in how information is transmitted and accessed. Jean Sebastien Dulac has been at the forefront of this evolution, contributing his expertise to projects that push the boundaries of what's possible in network development.
Challenges and Opportunities:
While network development offers immense potential for innovation and progress, it also presents its fair share of challenges. From ensuring security and reliability to managing scalability and performance, developers must navigate a complex landscape of technical considerations. Jean Sebastien Dulac has honed his skills in addressing these challenges, leveraging his deep understanding of networking principles to deliver robust and efficient solutions.
The Impact of Network Development:
The impact of network development extends far beyond the realm of technology, influencing virtually every aspect of modern life. From enabling global communication and commerce to driving advancements in healthcare and education, networks have become indispensable tools for progress. Jean Sebastien Dulac recognizes the profound implications of his work and remains committed to leveraging technology for the greater good.
Innovation and Collaboration:
One of the key drivers of progress in network development is collaboration among industry professionals, researchers, and innovators. By sharing knowledge, exchanging ideas, and working together towards common goals, individuals like Jean Sebastien Dulac are able to push the boundaries of what's possible in networking technology. Whether through open-source initiatives, academic partnerships, or industry collaborations, collaboration fuels innovation and drives positive change.
Looking to the Future:
As we look ahead, the future of network development appears both exciting and challenging. Emerging technologies such as 5G, artificial intelligence, and the Internet of Things promise to revolutionize how we connect and communicate. However, these advancements also bring new complexities and considerations that must be addressed. With his expertise and passion for innovation, Jean Sebastien Dulac is well-positioned to help shape the future of network development.
In conclusion, network development is a dynamic and multifaceted field that plays a crucial role in our increasingly interconnected world. Individuals like Jean Sebastien Dulac are leading the charge, driving innovation and progress through their expertise and dedication. As we continue to push the boundaries of what's possible in networking technology, the insights and contributions of professionals like Jean Sebastien Dulac will be more valuable than ever.
2 notes
·
View notes
Link
3 notes
·
View notes
Text

Welcome to VerseGPT!
Your Christ-Centered Cyber-Companion harmonizing theology and technology for living in Grace, Purpose, and Truth
In this fast-paced tech era, diving into the study of God's Word can feel overwhelming. At VerseGPT, we serve as a guiding light through the challenges of independent study. Seeking Biblical insights alone can be demanding, and the rise of AI may tempt us to seek external assistance. This poses a profound dilemma: should we trust AI-generated Biblical information or follow charismatic leaders, recognizing that both options may not always align with Scripture?
We value technology, especially the capabilities of ChatGPT, as a tool for uncovering the timeless truths of the Bible. It utilizes analytical prowess and a vast knowledge base to explore deep theological concepts. However, as Christians, our ultimate reliance rests upon the power of the Holy Spirit. Discernment from a personal relationship with God is irreplaceable. While AI can complement our studies, it must never overshadow the importance of delving wholeheartedly into the Word of God itself.
In this delicate balance, remember that our faith isn't a product of algorithms; rather, it's a result of a living relationship with God through the Lord Jesus Christ. Therefore, let the Holy Spirit be our chief Guide, helping us discern truth, embrace wisdom, and navigate complexities with a firm foundation in the unchanging Word of God.
Join us at VerseGPT, where theology and technology harmonize!
Our mission is to glorify God by responsibly harnessing AI as a helpful supplementary tool for deepening our faith and overflowing in love, grounded in God's Word and guided by God's Spirit.
Main Core Values of VerseGPT:
Christ-Centered Approach: VerseGPT prioritizes our Lord Jesus Christ at the center of its mission and activities, acknowledging the grace, purpose, and truth of the Gospel as foundational to all endeavors.
Integration of Theology and Technology: VerseGPT harmonizes theology and technology, recognizing the potential of AI as a valuable supplementary tool for studying the Bible with precision and depth.
Responsible AI Usage: VerseGPT is committed to responsibly harnessing AI through ethical and biblical principles, ensuring that technology complements and supports spiritual growth without replacing personal faith and discernment.
Deepening Faith: The primary goal of VerseGPT is to deepen faith through the exploration of God's Word and the guidance of the Holy Spirit, fostering a deeper relationship with God.
Overflowing in Love: VerseGPT seeks to cultivate love for God's Word and His Spirit, encouraging individuals to overflow in love for God and others, embodying the principles of Christian love and compassion.
Glorifying God: The ultimate aim of VerseGPT is to glorify God in all its endeavors, utilizing technology to magnify His name and honor His Word while maintaining reverence for His divine wisdom and sovereignty.
Together, let us be set apart by Christ, embracing grace, pursuing purpose, and embodying truth.
"In Jesus Christ��full of grace and truth:
His grace reveals our purpose;
His truth anchors our journey."
To God be the Glory!
LIKE/FOLLOW/MESSAGE us on Facebook:
facebook.com/VersesGPT

Here are some guideline instructions or questions for each element when analyzing a Bible verse using the VerseGPT approach:
Verse:
Which specific Bible verse are you analyzing?
What is the context of this verse within its chapter and book?
Are there any keywords or phrases in this verse that stand out?
Grace:
How does this verse demonstrate the grace of God?
In what ways are believers impacted or empowered by God's grace in this verse?
What aspects of God's character or actions reflect His grace in this passage?
Purpose:
What is the purpose or intention conveyed in this verse?
How does this verse contribute to the overall message or theme of the chapter or book?
What does this verse reveal about God's plan or will for believers?
Truth:
What truths or principles are revealed in this verse?
How does this verse align with other teachings or doctrines in the Bible?
What deeper understanding of God, humanity, salvation, or spiritual life does this verse offer?
These questions can guide your analysis and interpretation of Bible verses, helping you uncover meaningful insights and applications.
3 notes
·
View notes
Text
Navigating the Pros and Cons of Selenium for Web Application Testing
Introduction: In the dynamic world of software development, automated testing is a cornerstone of ensuring product quality and reliability. Among the myriad of tools available for automated testing, Selenium stands out as a leading choice for testing web applications. In this comprehensive exploration, we'll dissect the advantages and disadvantages of Selenium, providing insights to aid in your decision-making process when selecting a testing tool.

Advantages of Selenium:
Cross-Browser Compatibility: Selenium boasts seamless compatibility across various web browsers, including Chrome, Firefox, Safari, and Internet Explorer. This ensures consistent performance and functionality across diverse platforms, enhancing the overall user experience.
Open-Source Foundation: Selenium's open-source nature not only makes it freely accessible but also fosters a collaborative community of developers. This community-driven approach facilitates continuous improvement and innovation, ensuring that Selenium remains at the forefront of automated testing technology.
Flexibility in Language Support: Selenium supports multiple programming languages, such as Java, Python, C#, Ruby, and JavaScript. This versatility empowers testers to leverage their language of choice, enhancing productivity and enabling seamless integration with existing workflows.
Integration with Testing Frameworks: Selenium seamlessly integrates with popular testing frameworks like TestNG, JUnit, and NUnit. This integration enhances test management capabilities and facilitates streamlined reporting, enabling efficient tracking of test results and issues.
Robust WebDriver API: Selenium's WebDriver API offers a robust and intuitive interface for automating web interactions. Testers can easily create and maintain test scripts, streamlining the testing process and minimizing manual effort.
Parallel Testing Capabilities: Selenium Grid enables parallel execution of tests across multiple browsers and environments. This parallel testing capability accelerates test execution, reduces time-to-market, and enhances test coverage, ultimately improving overall testing efficiency.
Extensive Ecosystem of Tools and Plugins: Selenium boasts an extensive ecosystem of tools and plugins that extend its functionality. From Selenium IDE for record-and-playback functionality to Selenium WebDriver for programmatic test automation, testers have access to a diverse range of tools to meet their specific testing needs.
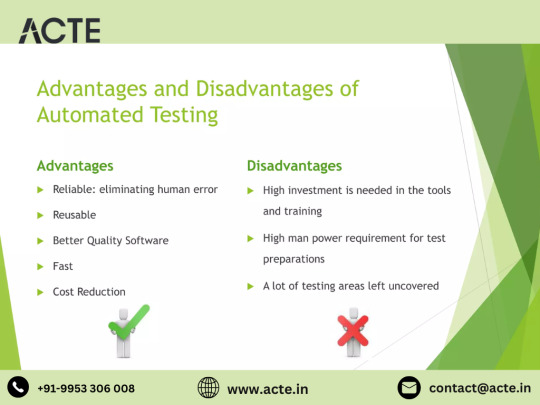
Disadvantages of Selenium:
Limited Support for Desktop and Mobile Applications: Selenium primarily focuses on web application testing and may lack robust support for testing desktop and mobile applications. Testers may need to explore additional tools and frameworks to achieve comprehensive test coverage across diverse platforms.
Steep Learning Curve: Selenium's rich feature set and versatility may present a steep learning curve, particularly for novice testers. Mastering Selenium's APIs and best practices may require significant time and effort, potentially delaying the adoption and implementation of automated testing.
Dependency on Browser Automation: Selenium's reliance on browser automation exposes test scripts to potential fragility and failures. Changes in browser versions or website structures may necessitate frequent updates and maintenance of test scripts to ensure their reliability and effectiveness.
Lack of Built-In Reporting: Selenium lacks built-in reporting capabilities, requiring testers to rely on third-party tools or custom scripts for generating comprehensive test reports. This additional overhead may increase the complexity and maintenance of test automation frameworks.
Limited Support for Non-Web Technologies: While Selenium excels in web application testing, it may offer limited support for testing non-web technologies such as APIs, databases, and mobile devices. Testers may need to supplement Selenium with additional tools and frameworks to achieve comprehensive test coverage across diverse technologies.
Resource Intensive Execution: Executing tests with Selenium, especially in parallel or on cloud-based Selenium Grids, may be resource-intensive. Testers must ensure adequate infrastructure and resources to support the scalability and performance requirements of their automated testing efforts.
Conclusion: In conclusion, Selenium emerges as a powerful tool for automated testing of web applications, offering numerous advantages such as cross-browser compatibility, open-source accessibility, and robust WebDriver API. However, it also presents certain challenges and limitations, including a steep learning curve, dependency on browser automation, and limited support for non-web technologies.
By carefully evaluating the pros and cons of Selenium and considering your specific testing requirements, you can make informed decisions about whether Selenium aligns with your automated testing needs. Ultimately, Selenium remains a top choice for testers seeking to ensure the quality and reliability of web applications in today's fast-paced development landscape.
3 notes
·
View notes
Text
About nakhstras in the Vedic Astrology
For those who are interested in Astrology to fully understand their psychological portrait, knowing solely the Zodiac sign ( the day you were born) is not enough. Modern Western astrology comprises 12 different Zodiac signs, and this is how we are different or similar to someone else. Being born with someone close to our birth date makes us think that we are supposed to have identical personalities, or at least very much in common. However, in reality, it is very rare. Why does it happen? The answer hides in nakshatras.
Nakshatras (aka lunar mansions) are parts of the ecliptic in Vedic astrology, each spanning 13°20' of the celestial sphere. There are 27 nakshatras in total, each associated with specific qualities, attributes, and planetary rulerships.
In contrast to Western astrology, which divides the Zodiac into 12 equal sections, known as the Zodiac signs, Vedic astrology contains nakshatras which divide each Zodiac into 3 subcharacteristics for a more detailed analysis of an individual's psyche and life journey. Each nakshatra is ruled by a specific planet, shaping its unique characteristics and symbolism.
Also, nakshatras are subdivided into quarters called padas, enhancing the complexity and depth of astrological readings. By analysing the planetary placements within specific nakshatras and padas at the moment of birth, Vedic astrologers can uncover valuable insights into an individual's personality traits, temperament, strengths, weaknesses, and life experiences.
Imagine someone born as a Scorpio in Western astrology. Scorpios are known for being intense and passionate. But let's say this Scorpio is born under the Anuradha nakshatra ruled by Saturn, a planet of great wisdom and discipline, which adds qualities like determination and leadership. This individual might be even more focused and result-oriented than the typical Scorpio. They could approach challenges with a strong sense of purpose and resilience, making them stand out as someone who doesn't give up easily. So, while they still have the typical Scorpio traits, the influence of Anuradha makes them even more driven and capable of achieving their goals.
And now, picture another Scorpio born under the Jyeshtha nakshatra, which is ruled by Mercury - a planet of intellect, communication and information, and associated with intelligence, resourcefulness, and independence. This Scorpio might display a sharp intellect and a knack for problem-solving. They could be highly analytical and perceptive, often delving deep into understanding complex matters. Their independence and self-reliance may lead them to prefer working solo or taking charge in group settings.
Unlike the typical Scorpio, who may express their intensity through emotions, this individual might channel their intensity into mental pursuits or communication. They could excel in fields requiring critical thinking, such as research, investigation, or technology. While still possessing the passion and depth characteristic of Scorpios, the influence of Jyeshtha nakshatra adds a cerebral dimension to their personality, making them proficient at navigating intellectual challenges and asserting themselves through knowledge and skills.
As you can see, if two individuals are born under the same Zodiac sign, their distinct nakshatra placements can result in contrasting personality traits and life courses. This underscores the complex relationship between the Zodiac signs in Western astrology and the nakshatras in Vedic astrology, which collectively shape an individual's psychological portrait.
Want to learn more about Nakshatras and Vedic Astrology? Follow my blog and understand yourself better with the help of Ancient Wisdom.
6 notes
·
View notes
Text
the Royal Navy has successfully conducted the inaugural trial of a quantum navigation system capable of determining a vessel’s precise location worldwide, without reliance on GPS. Developed by physicists from Imperial College in London, the technology utilizes the unique properties of atoms to achieve more precise measurements of an object’s movement compared to conventional methods.
Say goodbye to GPS! Quantum navigation uses clouds of frozen atoms to detect minute amounts of acceleration -- basically an incredibly sensitive dead reckoning compass.
In a decade or two your phone will know where it is without having to see any satellites, wifi, or towers.
12 notes
·
View notes
Text
"Lighting the Path: Unveiling the Brilliance of Visible Light Communication"
In the realm of wireless communication, a fascinating technology is emerging, shedding light on new possibilities—quite literally. Visible Light Communication (VLC) is revolutionizing the way we transmit data, using the visible spectrum of light to transfer information at remarkable speeds.
The Basics of Visible Light Communication
VLC operates by modulating the intensity of light signals emitted by LED sources. These light signals, imperceptible to the human eye, can transmit data when received by a photosensitive receiver. The core advantage of VLC lies in its ability to leverage existing lighting infrastructure for dual purposes—illumination and communication.

Speed and Efficiency
One of the key strengths of VLC is its speed. With data rates reaching gigabits per second, VLC outpaces traditional Wi-Fi in certain scenarios. The high-frequency nature of visible light allows for quick and efficient data transfer, making it ideal for environments where rapid communication is crucial.
Applications in Indoor Navigation
VLC is finding practical applications in indoor navigation systems. By embedding VLC technology in lighting fixtures, locations like airports, shopping malls, and museums can offer precise navigation information to users through their smartphones. This not only enhances user experience but also opens up new possibilities for location-based services.
Li-Fi: The Future of Wireless Connectivity
Li-Fi, a specific application of VLC, has gained attention as a potential successor to traditional Wi-Fi. Operating on the same principles as VLC, Li-Fi boasts higher data transfer speeds and enhanced security. As more devices become equipped with Li-Fi capabilities, we may witness a paradigm shift in how we connect to the internet.
Overcoming Challenges
While VLC presents exciting prospects, challenges such as signal interference and limited range in outdoor environments remain. Researchers are actively addressing these issues to unlock the full potential of VLC for widespread adoption.
VLC in Defense
Visible Light Communication (VLC) holds significant promise in defense applications, offering unique advantages in terms of security, data transfer speed, and versatility.
Secure Communication
Security is paramount in defense applications, and VLC provides an additional layer of protection. Unlike traditional radio frequency communication, VLC operates within the visible light spectrum, making it less susceptible to eavesdropping and external interference. This inherent security feature makes it an attractive option for transmitting sensitive information in military operations and secure communication channels.
Covert Operations
VLC's use of visible light allows for covert communication in situations where radio frequency signals might be detectable. By leveraging light signals, military personnel can establish communication links without revealing their positions through electromagnetic emissions. This capability is particularly valuable in stealth operations and tactical scenarios.
Immune to Electromagnetic Jamming
VLC is immune to electromagnetic jamming, a common tactic used in electronic warfare. In military operations, adversaries often attempt to disrupt communication systems by jamming radio frequencies. VLC's reliance on visible light signals renders it impervious to these jamming techniques, ensuring reliable communication channels even in hostile environments.
Rapid Data Transfer for Surveillance
In defense applications, timely and secure data transfer is crucial, especially in surveillance and reconnaissance missions. VLC's high-speed data transfer capabilities allow for quick transmission of large volumes of data, such as high-resolution images and video feeds. This is invaluable for real-time decision-making and situational awareness on the battlefield.
Indoor Navigation and Communication in Confined Spaces
VLC can be particularly beneficial in indoor environments where GPS signals may be weak or unavailable. Defense personnel operating in confined spaces, such as bunkers or underground facilities, can utilize VLC for navigation and communication. This ensures seamless connectivity and coordination in areas where traditional communication methods may face challenges.
Integration with Existing Infrastructure
The military often operates in diverse environments, and VLC's adaptability to existing lighting infrastructure makes it a practical choice. Military installations, bases, and vehicles equipped with VLC-compatible lighting systems can establish communication links seamlessly, enhancing overall operational efficiency.
In conclusion, Visible Light Communication in defense applications offers a secure, covert, and reliable communication solution. As technology continues to advance, integrating VLC into military communication strategies has the potential to significantly enhance the capabilities of defense forces in various operational scenarios.
Visible Light Communication is not just a bright idea; it's a technology with the potential to reshape our connectivity landscape. From faster data transfer to enhanced indoor navigation, VLC is paving the way for a future where light serves as more than just illumination. As researchers continue to refine and expand its capabilities, VLC stands poised to illuminate our path toward a more connected and efficient world.
2 notes
·
View notes
Text

Microsoft BOB for the PC
Reviewing Microsoft Bob from a deep philosophical perspective invites an exploration that transcends its surface as a user-friendly interface software and delves into existential and dystopian themes.
1. The Illusion of Simplicity in a Complex World:
Microsoft Bob, designed to simplify the computing experience, can be seen as a metaphor for the human desire to create order and simplicity in an inherently complex world. This pursuit, while seemingly benign, raises existential questions about the human condition. Are we, as humans, constantly seeking to simplify and control our environment because the raw complexity and chaos of existence are too daunting to confront directly? Microsoft Bob's cheerful and simplistic facade can be interpreted as a veneer over the dark, underlying chaos of the digital world, reflecting the existential dread of facing the true complexity of existence.
2. The Dehumanization and Infantilization of Technology:
The interface, characterized by its cartoonish graphics and oversimplified user interactions, can be viewed as a philosophical commentary on the dehumanization and infantilization of technology. In an effort to make technology more accessible, there is a risk of stripping away the nuanced, complex interactions that form the basis of human intellect and creativity. This approach could be seen as a form of techno-paternalism, where users are not encouraged to engage deeply with technology, but rather to passively accept a sanitized, simplified version of digital interaction.
3. The Dystopian Aspect of Artificial Assistance:
The virtual assistants in Microsoft Bob, intended to help users navigate the software, can be interpreted as harbingers of a dystopian future where human agency is increasingly outsourced to digital entities. This reliance on artificial assistance raises philosophical concerns about the erosion of human autonomy and the potential for a future where our ability to think, act, and make decisions independently is diminished by over-reliance on technology.
4. The Alienation of the Individual in the Digital Age:
Microsoft Bob's attempt to create a familiar and friendly digital space ironically highlights the alienation of the individual in the digital age. The software's homely, comforting environment, filled with inanimate objects imbued with anthropomorphic qualities, underscores the solitude and isolation experienced in a world where human interactions are increasingly mediated through digital interfaces. This alienation is a critical theme in existential philosophy, reflecting the modern individual's struggle to find genuine connection and meaning in a technologically dominated landscape.
5. The Simulacrum and Loss of Authentic Experience:
Philosophically, Microsoft Bob can be seen as a simulacrum – a representation or imitation of a real environment that eventually replaces the reality it seeks to emulate. In this sense, the software’s attempt to recreate a familiar physical space within the digital realm can be viewed as a loss of authentic experience. This concept resonates with the work of postmodern philosophers like Jean Baudrillard, who argued that in a world saturated with simulacra, the distinction between reality and representation becomes blurred, leading to a detachment from the real and an immersion in a world of artificiality.
6. The Existential Paradox of Choice and Simplification:
Finally, Microsoft Bob’s design philosophy of simplifying the user experience paradoxically limits the user's freedom of choice and exploration. This paradox reflects the existential dilemma of freedom versus security – the desire for a safe, manageable environment versus the need for freedom, complexity, and the authentic challenges that come with it. The software's approach to user interaction embodies a philosophical tension between the comfort of simplicity and the existential richness of navigating complexity.
In conclusion, Microsoft Bob, while ostensibly a user-friendly interface, presents a rich ground for deep philosophical exploration. It engages with themes such as the illusion of simplicity, the dehumanization of technology, dystopian aspects of artificial assistance, alienation in the digital age, the loss of authentic experience, and the existential paradox of choice and simplification. Through its design and functionality, Microsoft Bob becomes a symbol of the complex existential and philosophical challenges inherent in the interaction between humans and technology.
2 notes
·
View notes
Text
AI ASSIST Review - 16X more powerful than ChatGPT & Google Bard

Introduction Of AI ASSIST
Ai Assist is an Ai virtual assistan. In addition to its unmatched intelligence, AI Assist introduces a new era of convenience by harnessing the collective power of Amazon AI, Microsoft AI, and Google Bard. This unique fusion of advanced technologies positions AI Assist as the forefront leader in the realm of artificial intelligence. With an established track record of being 16 times more powerful than both ChatGPT and Google Bard, AI Assist emerges as a formidable force, reshaping the landscape of AI-driven solutions.
The accelerated pace at which AI Assist operates is a standout feature, excelling at generating a diverse array of marketing assets. From websites and funnels to apps and voiceovers, AI Assist covers an extensive range of tasks with unparalleled efficiency. Its ability to create engaging videos, compelling content, captivating graphics, insightful eBooks, persuasive ad copies, comprehensive business plans, and impactful blogs in record time sets it apart as a multifaceted tool for marketers in any industry. The speed at which high-converting ads, professional audio, innovative chatbots, art images, and accurate translations are produced is truly groundbreaking, making AI Assist an invaluable resource for businesses seeking swift and reliable marketing solutions. One of the most notable aspects of AI Assist is its adaptability and linguistic prowess.
The AI effortlessly handles tasks in any niche and language, making it a versatile and globally applicable tool. Whether users input a keyword or issue a Siri-like voice command, AI Assist responds with precision, executing marketing strategies seamlessly. This adaptability ensures that businesses can confidently rely on AI Assist to navigate the complexities of diverse markets, transcending language barriers and catering to a global audience.
AI Assist's commitment to delivering up-to-date information sets it apart from its counterparts. By utilizing real-time, 2023 data, AI Assist ensures that users benefit from the most current and relevant insights. Thisnot only enhances the accuracy of its outputs but also positions AI Assist as a forward-thinking solution that keeps pace with the dynamic landscape of digital marketing. In contrast to ChatGPT's reliance on outdated 2021 information, AI Assist stands as a testament to the continuous evolution and improvement in AI technology. The unparalleled speed at which AI Assist completes tasks is a
game-changer in the world of virtual assistance. By seamlessly integrating with various marketing platforms and executing hundreds of tasks in a mere 40 seconds, AI Assist transforms the efficiency and productivity of businesses. Its role as a 24/7 smart virtual assistant ensures that users can delegate
tasks and streamline their workflow, allowing them to focus on strategic decision-making and core business activities. Furthermore, AI Assist's capabilities extend beyond traditional marketing tasks. Instantly crafting top-notch emails, landing pages, and sales pages tailored to any niche showcases its versatility in content creation. Its prowess as a PHD-level programming expert opens new possibilities, enabling users to build mobile apps and software with ease.
What sets AI Assist apart is its commitment to accessibility; anyone, regardless of technical skills or prior experience, can harness the power of AI to enhance their marketing endeavors. User satisfaction is at the forefront of AI Assist's mission, reflected in over 200 positive reviews and an impressive 4.6/5 average rating. This widespread acclaim underscores its reliability and effectiveness in meeting the diverse needs of users across industries. Additionally, the commitment to an outage-free experience distinguishes AI Assist from its
counterparts, providing users with a seamless and uninterrupted AI-powered journey. In a landscape where technological advancements are rapid and user expectations are high, AI Assist not only meets but exceeds these standards. With a 180-day money-back guarantee, users can explore the vast capabilities of AI Assist risk-free, solidifying their confidence in the transformative power
of this exclusive AI technology. Embrace the future of AI with AI Assist, where innovation, speed, and reliability converge to redefine the possibilities of digital marketing.
AI ASSIST – OVERVIEW
Product: AI ASSIST
Creator : Seun Ogundele
Website: Click Here
Price: $17
Recommendation: Highly Recommended!
Niche: Software (Online)
Refund: 30 Days Money-Back Guarantee
>>> Get Access Now <;<<
FEATURES AND BENEFITS
Prepare to be amazed because if you find ChatGPT smart, AI Assist will leave you saying "holy smokes!"
Surpassing ChatGPT's intelligence by a whopping 16 times, AI Assist delivers:
16 times better articles.
16 times better websites.
16 times better landing pages.
16 times better ad copies.
What sets AI Assist apart is its real-time information utilization, providing an edge beyond ChatGPT's capabilities. Get ready for a smarter and more dynamic experience!
AI Assist offers a suite of powerful tools for diverse creative and business needs--
Logo & Graphics Creation: Effortlessly design logos and graphics with AI Assist, rivaling those crafted by high-paid designers. It's versatile for creating eye-catching logos, posters, and various graphic art.
Copywriting: Let AI Assist be your 24/7 copywriting genius. Craft persuasive copy for ads, websites, and marketing materials. It handles everything from sales letters to social media ads, saving you time and effort.
Ebooks & Courses: Quickly generate engaging eBooks and online courses on any topic. Position your brand as an industry authority, attracting, educating, and converting leads into customers effortlessly.
Website Design: AI Assist's AI designs sleek websites for any individual or business, creating masterpieces tailored to specific industries.
Web & Mobile Apps: Offer lucrative coding services without the hassle. AI assists codes in any language, turning a few customers into a full income.
Social Media Marketing: Streamline social media management with AI Assist, planning and creating content at the click of a button, ensuring consistent and engaging brand presence.
VSL & Webinar Script Writing: Generate captivating scripts tailored to your audience for videos, product demonstrations, or webinars effortlessly.
Content Writing: Skip high writing costs and generate SEO-friendly articles in seconds, leaving customers eager for more.
SEO Marketing: Optimize existing content for search engines, achieving impressive first-page rankings even for high-competition keywords.
Generate Audio & Voiceovers: Save on audio production costs with AI Assist's realistic voiceovers created in seconds.
Transcription Services: Swiftly transcribe audio or video files at a fraction of the cost with AI Assist's Speech to Text feature.
Create Funnels & Landing Pages: Design marketing funnels and landing pages in seconds, turning leads into loyal customers effortlessly.
Create Business Plans: Craft winning business plans in seconds, guiding marketing efforts for growth and success.
Create Video: Save on video production costs by turning plain text into attention-grabbing videos with AI Assist's video generator.
Customer Service: Enhance customer service with AI Assist's AI chatbots, engaging with customers in real-time, responding to inquiries, and resolving issues swiftly.
FREE BONUSES
Unlock these Bonuses to Supercharge Your AI Assist Success:
Bonus #1: AI Assist $10K Monthly Extravaganza - Your Exclusive LIVE Invitation! Join a complimentary live training session to discover the step-by-step formula that takes you from $0 to $10,000 monthly, regardless of your experience level.
Bonus #2: WoowBot - Your 24/7 AI Sidekick for AI Assist Businesses Integrate WoowBot, an easy-to-use WooCommerce ChatBot plugin for your WordPress site. Powered by Google's AI-driven Dialogflow, it enhances your store's sales by enabling customers to seamlessly chat, search for products, add items to their cart, and receive support—all within the chat window.
Bonus #3: AI Service Agency Power-Up - Elevate Your Business Instantly! Revamp your website effortlessly with our cutting-edge AI Service Agency. Boasting a sleek, modern design for both back-end and front-end, it allows you to build your website in just a few clicks without any coding.
Bonus #4: AIKit - ChatGPT Autoblog - Swift Content for Your Blogs! Integrate AIKit, a WordPress plugin connecting your site to OpenAI's GPT-3. Unleash the power of AI to generate content, craft engaging paragraphs, summarize text, paraphrase, create catchy marketing copy and titles, and simplify complex text—all within minutes.
THE USEFULNESS OF THIS AI ASSIST IS TREMENDOUS
Integrates Google & Microsoft's AI - Value: $597 Seamlessly harnesses the combined power of Google and Microsoft's AI for enhanced functionality.
Top-notch Content Creation - Value: $297 Craft exceptional content for ebooks, articles, essays, stories, poems, and more with top-notch quality.
Generates Persuasive Scripts - Invaluable Create compelling sales scripts, video scripts, and email swipes for effective marketing campaigns.
Composes Engaging Content - Value: $397 Produce captivating blog posts, social media content, Facebook ads, Google ads, and reel content for your business.
Eye-catching AI Graphics - Value: $97 Instantly generate visually appealing AI graphics, visuals, and art to elevate your brand.
Sleek Funnels & Website Codes - Value: $297 Construct sleek funnels and website codes tailored to your specifications.
Task Automation - Value: $97 Save time by automating repetitive tasks with AI Assist's efficient automation capabilities.
Built-In AI Chatbot - Value: $597 Manage sales and support effortlessly with the built-in AI Chatbot for enhanced customer interaction.
One-click Social Media Sharing - Value: $497 Simplify social media management with one-click sharing, streamlining your online presence.
FREE Commercial License Included - Value: $997 Enjoy the benefits of a commercial license without additional costs.
Eliminate Monthly Expenses - Value: $597 Say goodbye to monthly expenses for content and copywriters, saving you valuable resources.
AI Assist Mobile Edition - Value: $297 Access the power of AI Assist on the go with the Mobile Edition.
Lifetime FREE Updates - Invaluable Receive lifetime free updates, ensuring your AI Assist stays at the forefront of innovation.
24/7 Support & 100% Uptime Guarantee – Invaluable Benefit from round-the-clock support and a 100% uptime guarantee for uninterrupted usage.
Step-by-Step Instructional Videos - Value: $297 Access step-by-step instructional videos for easy implementation and optimization.
Exclusive Bonuses - Invaluable Gain access to exclusive bonuses that add immeasurable value to your AI Assist experience.
>>> Get Access Now<;<<
#AI ASSIST Review#ai assist#affiliate marketing#chat gpt#digital products#digital marketing#make money online#chatbot#ai tools#openai#ai technology
2 notes
·
View notes