#Cybercriminals
Link
https://zd.net/3sbtylp - 🚨 Quishing, a new form of phishing using QR codes, is the latest cybercrime trend. QR codes, once considered innocuous, are now being weaponized in phishing attacks, misleading users into revealing sensitive information or installing malware. With QR codes ubiquitous in everyday life, cybercriminals exploit the general trust people have in them. #Quishing #CybersecurityAwareness 📱 Mobile phones are particularly vulnerable to quishing attacks. Unlike desktops, many mobile operating systems lack robust phishing protection, making them easy targets. Common quishing tactics involve criminals sending QR codes via email, often under the guise of urgent account verification requests. #MobileSecurity #PhishingThreats 🛡️ To safeguard against quishing, exercise caution with QR codes, especially from unknown sources. Verify the legitimacy of the sender before scanning any QR code in emails, and avoid scanning random QR codes encountered in public spaces. Legitimate companies rarely use QR codes for account verification. #CyberSafetyTips #ProtectYourData 📵 Just like with suspicious SMS messages, if you're unsure about a QR code's source, it's safest not to scan it. Curiosity can lead to unintended consequences when it comes to quishing, so always prioritize security over convenience.
#Quishing#CybersecurityAwareness#MobileSecurity#PhishingThreats#CyberSafetyTips#ProtectYourData#StaySafeOnline#DigitalVigilance#sensitiveinformation#easytargets#benow#phishingattacks#operatingsystem#users#life#cybercriminals#mobile#phones#phone
4 notes
·
View notes
Text
There is more that meets the eye regarding Elon Musk's new verification process. It is a scammers paradise. The new verification system is likely to be accepted by automatic approval, rather than personally accepted by Twitter staff.
This will of course open the flood gates to cybercriminals to unleash all sorts of scams and impersonations. The impersonations that we have seen from Kathy Griffen and others was a mere demonstration of what is to come.
Like I have previously stated, Musk has more money than sense. Or a hunger to accumulate more money than sense.
6 notes
·
View notes
Text
Privnote under DDoS attack
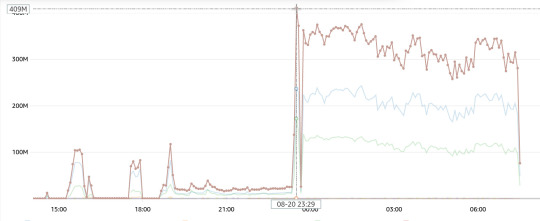
During the last two weeks and ongoing, Privnote has been hammered by a DDoS attack, at moments exceeding 400 million sum requests per 5 minutes. These assaults lasting at times 8 hours interrupted is presently equivalent (in this time frame) to 2 months of Wikipedia's requests!
Privnote is being attacked because of its reputation for providing the first free and anonymous privacy web tool for the world to use with ease.
Since our launch date in 2008, not one of Privnote's notes has ever been compromised nor will it ever be compromised so long as you make sure the domain you use is privnote.com and nothing else.
Be very aware that cybercriminals will try to fool you with sites that look like Privnote in an attempt to steal your secrets so please recall: there is one and only one Privnote website service.
Privnote still continues to be under attack so expect interruptions to our service. We now only allow very few requests per minute per IP. Moreover, we are closing Privnote's servers due to a huge amount of "compromised" IP addresses. Feel free to email us at [email protected] if you think we can be of any help.
Privacy is a basic human right and we will invest all of our resources to make sure that Privnote is on-line for years to come no matter who intends to take it down.
To sustain Privnote's team and infrastructure we get our funding from Google Ads. This has allowed us to keep Privnote's service free and anonymous for almost a decade and a half already.
Our honest, trustworthy and dedicated team puts forward a huge effort to make Privnote shine everyday, 24/7 if need be.
If you want to support Privnote in this critical moment while cybercriminals are attacking us, you can now contribute to our presently bursting
budget needs by helping us directly via these Privnote's crypto wallets:
Privnote's BTC wallet: bc1qk3tvjm28zamas543qv7s0fy4cz7wfqdfxky9tr
Privnote's ETH wallet: 0xD81ed5D97655550609f15c4A14C3253e894698be
We promise to use 100 % of your support entirely to the Privnote's service.
Without Privacy freedom can't flourish. Without Privacy there's no identity.
Thanks a million for your support.
3 notes
·
View notes
Text
Why are AI-Powered Google Searches Promoting Malware?
New Post has been published on https://thedigitalinsider.com/why-are-ai-powered-google-searches-promoting-malware/
Why are AI-Powered Google Searches Promoting Malware?
What is the first thing you do when you have a question no one can answer confidently? Google it.
For years, Google has been the go-to search engine for countless users worldwide, handling billions of search queries every day. However, googling is most effective when queries are simple and specific – not open-ended. And Google users still need to navigate search results and parse information on their own.
That is, until Generative AI entered our lives.
In May of last year, Google released their Search Generative Experience, or SGE, a feature that leverages generative AI to augment, streamline, and personalize the traditional online search experience. Instead of having to break multi-layered questions down into smaller ones and organize output information manually, users can ask more complex questions and receive thorough, concise results alongside snapshots of relevant links and follow-up suggestions for further exploration.
Despite its potential, however, this search engine enhancement opens up new vectors for cybercriminals to exploit. As people and businesses increasingly rely on AI-powered search engines like Google’s SGE, hackers have found ways to manipulate these systems for their own gain, putting users and companies at risk.
Search Engine Exploitation
When it comes to layering security into search engine platforms, reputation can get in the way of reality. This means that content hosted on well-respected and highly trusted sites is often scrutinized less thoroughly by active web security solutions than those that receive less user traffic.
One way cybercriminals take advantage of this is by launching SEO poisoning campaigns. In these cases, threat actors create malware-infested sites and exploit search engine optimization techniques that prominently display these toxic links among top search results, increasing the chance that users will click on them.
Microsoft discovered such an exploitation in 2021 when hackers flooded search engine results with thousands of web pages infected with SolarMarker remote access trojan (RAT) malware, which offered various office template forms as bait for office workers. Hackers used AI-driven SEO functionalities to lift these contaminated web pages to the top of the search results list in order to trick unsuspecting users into downloading the SolarMarker payload, which would then steal credentials and establish hidden backdoors in users’ systems.
Google’s SGE feature is triggering the latest iterations of search engine vulnerabilities. Just last month, a new report found that the SGE’s algorithm was recommending malicious websites meant to trap users into phishing scams, among other nefarious activities.
Browser Insecurity
Alongside insufficient security, tools like SGE provide hackers with a sentiment they can exploit: User trust. Individuals and enterprises often underestimate web browsers as a point-of-entry for malicious attacks, and reputable web-based search engines have cultivated a significant amount of trust to the point where many users don’t think twice before opening search results they receive.
As a result, hackers are targeting web browsers –and within them, search engines—more consistently to access sensitive, personal, or corporate information in increasingly sophisticated ways, making it hard for end-users and threat detection platforms to keep up. Basic browser security measures can be misled into deeming malicious websites as benign, enabling such sites to evade proactive detection and nestle into a security solution’s “safe list” before defenses can block the site. But by that time, users could have already fallen for a scam.
While it is incumbent upon search engines to secure their platforms and ensure safe and authentic results for their users, organizations and individuals alike still need to exercise caution. Though current security solutions are getting better at detecting malicious content, hackers are quick to adapt, often rendering “new” threat detection approaches ineffective quickly.
For instance, hackers have taken to employing self-altering polymorphic code to conceal their malware traps from the latest browser detection methods. This poses a formidable obstacle to traditional security protocols, as do next-generation phishing attacks that employ sophisticated social engineering techniques in order to deceive users into divulging sensitive information.
Modernize Security Measures
Generative search engines are a boon for today’s internet users, but they also open a can of worms that traditional web security solutions are not yet equipped to address. It is clear that even highly reputable search engine platforms like Google need a more dynamic solution. Fortunately, extension-based browser security solutions have risen to the occasion.
These solutions offer a dynamic approach to browser security, capable of inspecting nearly every aspect of website content displayed directly within the browser interface. Text, images, and scripts are among the many elements these solutions scrutinize.
Extension-based solutions also utilize machine learning and computer vision algorithms to analyze website code, network connections, and recognizable patterns associated with phishing attempts and malware traps. One of the key advantages of extension-based detection is the ability to observe malicious websites and downloads from the perspective of the user, waiting patiently until the malicious content is unveiled. With such robust capabilities, these solutions can detect and thwart even the most sophisticated and evasive tactics, including SEO poisoning, redirects, fake captchas engineered to trick users, and malvertising.
Through continuous monitoring and proactive identification of threat tactics and vulnerabilities, modern extension-based security solutions do what prior solutions do not: block malicious sites in real time. This safeguards users from falling victim to online scams and computer viruses, fostering a safer browsing and search environment for all.
Surf the Web Safely
For each new AI use case, new vulnerabilities remind us of the robust cybersecurity that is required in order to utilize this transformative technology safely.
Search engines are no exception.
Companies need to ensure that the generative AI-powered features they deploy cannot be used against the people they are meant to benefit. After all, search engines are among the most visited sites across the Internet, and traditional web security solutions meant to protect them still suffer from security gaps.
Though no security system is perfect, search engine operators who deploy advanced detection technologies and meticulous content scanning mechanisms at the point-of-click of browsers give users the best chance of surfing the web safely while avoiding AI-enhanced malware and social engineering campaigns.
#ai#AI-powered#AI-powered search#algorithm#Algorithms#approach#browser#code#Companies#computer#Computer vision#content#continuous#credentials#cybercriminals#cybersecurity#defenses#detection#display#engine#engineering#engines#Environment#Exercise#extension#Features#Forms#generative#generative ai#Google
1 note
·
View note
Link
Navigating the world of cryptocurrency can be tricky, but your security shouldn't be a gamble. 💻🔒 Discover how leading cryptocurrency exchanges like Kraken and Coinbase are setting the bar high with top-tier security measures. Stay safe, informed, and ahead of cybercriminals with our comprehensive guide. Dive in to ensure your digital currency journey is secure! #CryptocurrencyExchange #DigitalSecurity
0 notes
Text
Ransomware becoming a Major Cause for Concern in India

Ransomware cases in India are on the rise. Adarsh takes you through the causes and implications of the same.
Read More. https://www.sify.com/security/ransomware-becoming-a-major-cause-for-concern-in-india/
0 notes
Text
Major Rewards Offered to Dismantle Hive Ransomware Group

Unveiling a Significant Bounty
In a bold move to combat cybercrime, the U.S. Department of State has announced a substantial reward of up to $10 million for information leading to the identification or location of key leaders within the Hive ransomware group. An additional reward of up to $5 million is offered for information leading to the arrest or conviction of individuals attempting to engage in Hive ransomware activities.
Global Impact of Hive Ransomware
The Hive ransomware variant has left its mark on over 80 countries, targeting countless victims, including those within the United States. Since late July 2022, the FBI's successful infiltration into Hive's networks has prevented potential ransom payments estimated at $130 million, offering a glimmer of hope to victims worldwide.
A Coordinated Crackdown
This announcement is part of a concerted effort by the U.S. Department of Justice, alongside Europol and authorities from Germany and the Netherlands, to seize control of Hive’s servers and websites. This strategic move aims to halt Hive's operations, preventing further attacks and extortion against critical infrastructure and the economic foundation of multiple nations.
The Role of International Collaboration
The takedown of Hive's infrastructure signifies the importance of international cooperation in the fight against transnational organized crime. By joining forces with global partners, the U.S. is reinforcing its commitment to safeguarding its citizens and allies against the pervasive threat of ransomware.
Leveraging the TOCRP Initiative
The rewards are part of the Transnational Organized Crime Rewards Program (TOCRP), underscoring the U.S. government's dedication to disrupting global crime networks. Through TOCRP, the State Department bolsters law enforcement efforts, aiming to bring elusive criminals to justice and protect national and international security interests.
How to Share Information
Encouraging individuals with valuable information on Hive ransomware activities to come forward. The U.S. government assures confidentiality and protection for informants, providing a secure avenue for sharing intelligence that could lead to the dismantling of one of the most formidable ransomware groups in recent history.
A Call to Action Against Cybercrime
The U.S. government's announcement of rewards for information on the Hive ransomware group marks a critical step in the ongoing battle against cybercriminals. By incentivizing whistleblowers and enhancing collaborative law enforcement efforts, the U.S. and its allies demonstrate a unified front against the cyber threats that jeopardize global stability and security.
Sources: THX News & US Department of State.
Read the full article
#Cybercrime#cybercriminals#DepartmentofState#Europol#FBIdecryptionkeys#Hiveransomwarevariant#Ransomwareattacks#TOCRP#transnationalorganizedcrime#U.S.DepartmentofJustice
0 notes
Text
youtube
0 notes
Text

Cybercriminals are hitting Aussie businesses hard.
Even a small cyber-attack on your business can cost you upto $46,000 or more! And the loss to your business's reputation? Incomprehensible.
So make sure you adopt top-notch safety standards and connect with cyber-security experts like Web99.
At Web99, we act as cyber-shield, offering robust HTTPS, 2FA, and security audits.
Protect your business from digital predators and secure your online presence with our expert solutions.
Call now for a free consultation.
📞 1300 493 299
or
Visit: https://web99.com/
.
.
.
0 notes
Text
Beware Of These Techniques That Cybercriminals Use To Steal Cryptocurrency
While the rise of cryptocurrency has brought about revolutionary changes in the financial landscape, it has also opened doors to new forms of cybercrime. The decentralized and anonymous nature of cryptocurrencies has made them attractive targets for cybercriminals.
Understanding the techniques that cybercriminals use to steal these digital assets is crucial for protecting oneself in the evolving landscape of cybersecurity. It is important that you stay vigilant, and informed, and prioritize security to protect yourself against these evolving threats.
Check out this list of techniques that cybercriminals use to steal cryptocurrency.
1. Phishing Attacks

One of the most common techniques used by cybercriminals is phishing. They employ misleading emails, websites, or messages that look similar to legitimate platforms or communication from trusted entities. Unsuspecting users are tricked into revealing their private keys, passwords, or wallet information which allows the criminals to gain access to their cryptocurrency holdings.
To Read More Click here...
#business#business blog#new updates#trending topic#cryptocurrency#Phishing Attacks#Cybercriminals#new techniques#revolutionary#evolving threats
0 notes
Text
All About Cyber Security – {Explained}
Cyber Security!
Why do you need cyber security?
Have you ever questioned why we need cyber security and how it’s useful?
For a while keep this question aside and think what will your reaction be if your phone is lost? A sheer terror will be they’re on your face and you’ll look for the solution to get it right.
Likewise, if your business or any technology is suffering from an attack or any…

View On WordPress
0 notes
Text
Cybercriminals continue targeting open remote access products - Help Net Security
Cybercriminals still prefer targeting open remote access products, or like to leverage legitimate remote access tools to hide their malicious actions, according to WatchGuard.
“Threat actors continue using different tools and methods in their attack campaigns, making it critical for organizations to keep abreast of the latest tactics to fortify their security strategy,” said Corey Nachreiner,…

View On WordPress
0 notes
Text
What is LockBit, the cybercrime gang hacking some of the world’s largest organisations?

- By Jennifer Medbury , Paul Haskell-Dowland , Edith Cowan University , The Conversation -
While ransomware incidents have been occurring for more than 30 years, only in the last decade has the term “ransomware” appeared regularly in popular media.
Ransomware is a type of malicious software that blocks access to computer systems or encrypts files until a ransom is paid.
Cybercriminal gangs have adopted ransomware as a get-rich-quick scheme. Now, in the era of “ransomware as a service”, this has become a prolific and highly profitable tactic. Providing ransomware as a service means groups benefit from affiliate schemes where commission is paid for successful ransom demands.
Although only one of the many gangs operating, LockBit has been increasingly visible, with several high-profile victims recently appearing on the group’s website.
So what is LockBit? Who has fallen victim to them? And how can we protect ourselves from them?
What, or who, is LockBit?
To make things confusing, the term LockBit refers to both the malicious software (malware) and to the group that created it.
LockBit first gained attention in 2019. It’s a form of malware deliberately designed to be secretly deployed inside organisations, to find valuable data and steal it.
But rather than simply stealing the data, LockBit is a form of ransomware. Once the data has been copied, it is encrypted, rendering it inaccessible to the legitimate users. This data is then held to ransom – pay up, or you’ll never see your data again.
To add further incentive for the victim, if the ransom is not paid, they are threatened with publication of the stolen data (often described as double extortion). This threat is reinforced with a countdown timer on LockBit’s blog on the dark web.
Little is known about the LockBit group. Based on their website, the group doesn’t have a specific political allegiance. Unlike some other groups, they also don’t limit the number of affiliates:
We are located in the Netherlands, completely apolitical and only interested in money. We always have an unlimited amount of affiliates, enough space for all professionals. It does not matter what country you live in, what types of language you speak, what age you are, what religion you believe in, anyone on the planet can work with us at any time of the year.
Notably, LockBit have rules for their affiliates. Examples of forbidden targets (victims) include:
critical infrastructure
institutions where damage to the files could lead to death (such as hospitals)
post-Soviet countries such as Armenia, Belarus, Estonia, Georgia, Kazakhstan, Kyrgyzstan, Latvia, Lithuania, Moldova, Russia, Tajikistan, Turkmenistan, Ukraine and Uzbekistan.
Other ransomware providers have also claimed they won’t target institutions like hospitals – but this doesn’t guarantee victim immunity. Earlier this year a Canadian hospital was a victim of LockBit, triggering the group behind LockBit to post an apology, offer free decryption tools and allegedly expel the affiliate who hacked the hospital.
While rules may be in place, there is always potential for rogue users to target forbidden organisations.
The final rule in the list above is an interesting exception. According to the group, these countries are off limits because a high proportion of the group’s members were “born and grew up in the Soviet Union”, despite now being “located in the Netherlands”.
Who’s been hacked by LockBit?
High-profile victims include the United Kingdom’s Royal Mail and Ministry of Defence, and Japanese cycling component manufacturer Shimano. Data stolen from aerospace company Boeing was leaked just this week after the company refused to pay ransom to LockBit.
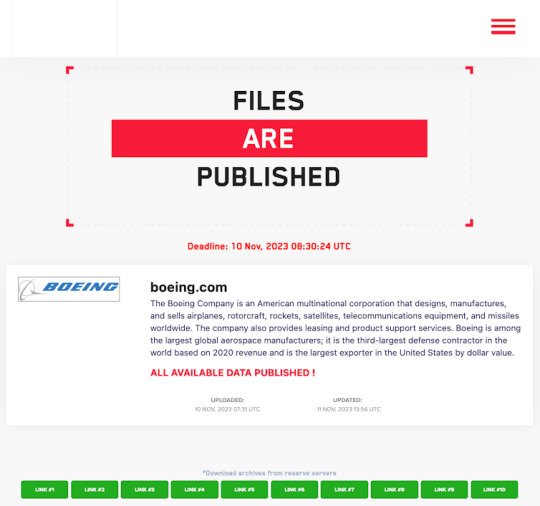
LockBit’s website on the dark web is used to publish stolen data if the ransom is not paid. Screenshot sourced by authors.
While not yet confirmed, the recent ransomware incident experienced by the Industrial and Commercial Bank of China has been claimed by LockBit.
Since appearing on the cybercrime scene, LockBit has been linked to almost 2,000 victims in the United States alone.
From the list of victims seen below, LockBit is clearly being used in a scatter-gun approach, with a wide variety of victims. This is not a series of planned, targeted attacks. Instead, it shows LockBit software is being used by a diverse range of criminals in a service model.
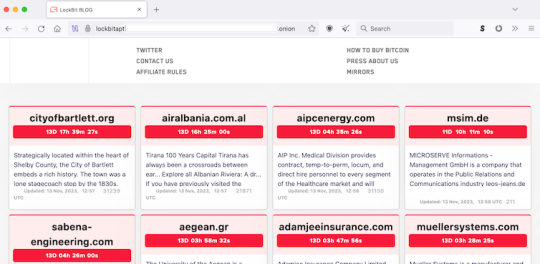
LockBit’s blog on the dark web provides a showroom for public shaming of their victims. Screenshot sourced by authors.
How we can protect ourselves
In recent years, ransomware as a service (RaaS for short) has become popular.
Just as organisations use software-as-a-service providers – such as licensing for office tools like Microsoft 365, or accounting software for payroll – malicious services are providing tools for cybercriminals.
Ransomware as a service enables an inexperienced criminal to deliver a ransomware campaign to multiple targets quickly and efficiently – often at minimal cost and usually on a profit-sharing basis.
The RaaS platform handles the malware management, data extraction, victim negotiation and payment handling, effectively outsourcing criminal activities.
The process is so well developed, such groups even provide guidelines on how to become an affiliate, and what benefits one will gain. With a 20% commission of the ransom being paid to LockBit, this system can generate significant revenue for the group – including the deposit of 1 Bitcoin (approximately A$58,000) required from new users.
While ransomware is a growing concern around the globe, good cybersecurity practices can help. Updating and patching our systems, good password and account management, network monitoring and reacting to unusual activity can all help to minimise the likelihood of any compromise – or at least limit its extent.

For now, whether or not to pay a ransom is a matter of preference and ethics for each organisation. But if we can make it more difficult to get in, criminal groups will simply shift to easier targets.
Jennifer Medbury, Lecturer in Intelligence and Security, Edith Cowan University and Paul Haskell-Dowland, Professor of Cyber Security Practice, Edith Cowan University
This article is republished from The Conversation under a Creative Commons license. Read the original article.
--
Read Also
What is Log4j? A cybersecurity expert explains the latest internet vulnerability, how bad it is and what’s at stake
0 notes
Text




Secure your digital world with our top-tier Cyber Security Advisory Services. Expert guidance for robust protection against cyber threats.
Protect Your Online Presence: Tips for Digital Security
☑ Use Strong / Unique Passwords
☑ Use a Password Manager
☑ Beware of Phishing Scams
𝐂𝐚𝐥𝐥 𝐍𝐨𝐰 ☎ + 61-412886034 or 𝐕𝐢𝐬𝐢𝐭 𝐍𝐨𝐰 👉 www.cyber-sky.com.au
Follow us @cybersecurity.au
#cybersecurity#cybersecuritytrend#cyberspace#cybercriminals#cybersecuritybenefits#security#business#hacking#informationsecurity#towardscybersecurity#cybernews#cyberattacks#cybercrime#cybertheft#cybersecuritytrends#Cyber Security Advisory
1 note
·
View note
Text
How to safeguard your business from AI-generated deepfakes
New Post has been published on https://thedigitalinsider.com/how-to-safeguard-your-business-from-ai-generated-deepfakes/
How to safeguard your business from AI-generated deepfakes
.pp-multiple-authors-boxes-wrapper display:none;
img width:100%;
Recently, cybercriminals used ‘deepfake’ videos of the executives of a multinational company to convince the company’s Hong Kong-based employees to wire out US $25.6 million. Based on a video conference call featuring multiple deepfakes, the employees believed that their UK-based chief financial officer had requested that the funds be transferred. Police have reportedly arrested six people in connection with the scam. This use of AI technology is dangerous and manipulative. Without proper guidelines and frameworks in place, more organizations risk falling victim to AI scams like deepfakes.
Deepfakes 101 and their rising threat
Deepfakes are forms of digitally altered media — including photos, videos and audio clips — that seem to depict a real person. They are created by training an AI system on real clips featuring a person, and then using that AI system to generate realistic (yet inauthentic) new media. Deepfake use is becoming more common. The Hong Kong case was the latest in a series of high-profile deepfake incidents in recent weeks. Fake, explicit images of Taylor Swift circulated on social media, the political party of an imprisoned election candidate in Pakistan used a deepfake video of him to deliver a speech and a deepfake ‘voice clone’ of President Biden called primary voters to tell them not to vote.
Less high-profile cases of deepfake use by cybercriminals have also been rising in both scale and sophistication. In the banking sector, cybercriminals are now attempting to overcome voice authentication by using voice clones of people to impersonate users and gain access to their funds. Banks have responded by improving their abilities to identify deepfake use and increasing authentication requirements.
Cybercriminals have also targeted individuals with ‘spear phishing’ attacks that use deepfakes. A common approach is to deceive a person’s family members and friends by using a voice clone to impersonate someone in a phone call and ask for funds to be transferred to a third-party account. Last year, a survey by McAfee found that 70% of surveyed people were not confident that they could distinguish between people and their voice clones and that nearly half of surveyed people would respond to requests for funds if the family member or friend making the call claimed to have been robbed or in a car accident.
Cybercriminals have also called people pretending to be tax authorities, banks, healthcare providers and insurers in efforts to gain financial and personal details.
In February, the Federal Communications Commission ruled that phone calls using AI-generated human voices are illegal unless made with prior express consent of the called party. The Federal Trade Commission also finalized a rule prohibiting AI impersonation of government organizations and businesses and proposed a similar rule prohibiting AI impersonation of individuals. This adds to a growing list of legal and regulatory measures being put in place around the world to combat deepfakes.
Stay protected against deepfakes
To protect employees and brand reputation against deepfakes, leaders should adhere to the following steps:
Educate employees on an ongoing basis, both about AI-enabled scams and, more generally, about new AI capabilities and their risks.
Upgrade phishing guidance to include deepfake threats. Many companies have already educated employees about phishing emails and urged caution when receiving suspicious requests via unsolicited emails. Such phishing guidance should incorporate AI deepfake scams and note that it may use not just text and email, but also video, images and audio.
Appropriately increase or calibrate authentication of employees, business partners and customers. For example, using more than one mode of authentication depending on the sensitivity and risk of a decision or transaction.
Consider the impacts of deepfakes on company assets, like logos, advertising characters and advertising campaigns. Such company assets can easily be replicated using deepfakes and spread quickly via social media and other internet channels. Consider how your company will mitigate these risks and educate stakeholders.
Expect more and better deepfakes, given the pace of improvement in generative AI, the number of major election processes underway in 2024, and the ease with which deepfakes can propagate between people and across borders.
Though deepfakes are a cybersecurity concern, companies should also think of them as complex and emerging phenomena with broader repercussions. A proactive and thoughtful approach to addressing deepfakes can help educate stakeholders and ensure that measures to combat them are responsible, proportionate and appropriate.
(Photo by Markus Spiske)
See also: UK and US sign pact to develop AI safety tests
Want to learn more about AI and big data from industry leaders? Check out AI & Big Data Expo taking place in Amsterdam, California, and London. The comprehensive event is co-located with other leading events including BlockX, Digital Transformation Week, and Cyber Security & Cloud Expo.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.
Tags: ai, artificial intelligence, deepfakes, enterprise, scams
#2024#advertising#ai#ai & big data expo#AI Ethics#ai news#amp#approach#artificial#Artificial Intelligence#assets#audio#authentication#banking#biden#Big Data#Business#clone#Cloud#communications#Companies#comprehensive#conference#course#cyber#cyber security#cybercriminals#cybersecurity#data#deepfake
0 notes
Link
https://bit.ly/48wjTGB - 🌐 The MOVEit breach, known as the largest hack of 2023, continues to unravel as more victims emerge, revealing a colossal scale of related attacks and compromised sensitive data. Cybercriminals have been exploiting a vulnerability in MOVEit, leading to data theft from various businesses and governments including Shell, British Airways, and the United States Department of Energy. Despite efforts to rectify the situation, the full extent of the damage remains uncertain, with continuous disclosures from various organizations such as BORN Ontario. #CyberSecurity #DataBreach 📊 Highlighting the complexity, the breach isn’t just confined to direct users of MOVEit software. Numerous affected organizations had indirect interactions through third parties or vendors utilizing MOVEit, exacerbating the extent of the data breach. The exploitation mainly occurred in MOVEit Transfer, a local version of the service run by institutions on their premises. #ThirdPartyRisk #MOVEitBreach 🔒 As cybercriminals continue to target centralized data repositories like MOVEit, the Clop data extortion gang has been identified as a significant player in the ongoing saga, having previously claimed breaches in over 100 organizations by exploiting other file transfer tools. The revelations from the MOVEit incident have dwarfed previous attacks in the sheer number of affected organizations and individuals, causing concern and uncertainty in the digital world. #ClopGang #CyberCrime 📈 Emsisoft’s investigations report that over 2,167 organizations have been impacted, and more than 62 million individuals had their data breached as part of Clop’s MOVEit spree. However, the true number of affected individuals is speculated to be much higher, possibly running into hundreds of millions. The unending series of MOVEit-related disclosures is anticipated to continue, emphasizing the need for enhanced cyber security measures. #EmsisoftReport #CyberSecurityAwareness 🛡 The MOVEit breach underscores the critical importance of robust cyber security frameworks and the urgency to patch vulnerabilities in widely used software products. As Progress Software, the owner of MOVEit, and other institutions work towards mitigating the impact of the breach, the episode serves as a potent reminder of the persistent and evolving threats in the digital landscape.
#CyberSecurity#DataBreach#ThirdPartyRisk#MOVEitBreach#ClopGang#CyberCrime#EmsisoftReport#CyberSecurityAwareness#ProgressSoftware#CyberThreats#fullextent#moveit#datatheft#unitedstates#data#cybercriminals#vulnerability#theft#businesses#government#shell
0 notes