#SensitiveData
Text
Organizations collect data to improve their products and services and support their business. To use this data effectively, it must be shared with internal and external teams for various purposes. However, using this data for non-productive uses can lead to security breaches and compromised sensitive information.
#DataMasking#SensitiveData#PrivacyProtection#DataObfuscation#MaskingTechniques#DataAnonymization#DataSecurity#Compliance#GDPR#Encryption#DynamicDataMasking
0 notes
Text
Samsung Bans Use of Generative AI Tools in the Workplace over Data Leakage Fears

South Korean tech giant Samsung has issued a blanket ban on using generative AI tools like ChatGPT, Google Bard, and Bing AI chatbot for work-related activities. The company fears that using such AI-based platforms could lead to data leakage. According to reports, Samsung discovered that staff uploaded sensitive code to one of these platforms, prompting the ban. The memo issued by the company discusses the risks associated with using these AI-based platforms.
Memo Issued to Employees, Details and Justification
Samsung reportedly notified staff at one of its biggest divisions about the new policy through a memo. The memo stated that the company has been observing an increase in interest in generative AI platforms like ChatGPT and others, both internally and externally. The memo reads, "While this interest focuses on the usefulness and efficiency of these platforms, there are also growing concerns about security risks presented by generative AI."
Moreover, the memo even hinted that Samsung engineers accidentally leaked internal source code by uploading it on ChatGPT. Samsung will deploy additional security measures to create a secure environment for the safe use of generative AI to enhance employee productivity and efficiency. However, until these measures are prepared, Samsung has temporarily restricted the use of generative AI.
Reasons for the Ban
A few companies and even nations have started restricting the use of generative AI platforms like ChatGPT, Bing AI, and others, claiming they could harbor sensitive data. Samsung was not one of these companies. The company had allowed its engineers at the semiconductor division to use ChatGPT to help fix problems with source code. However, some employees reportedly entered top-secret data, which may have included source code for a new program and internal meeting notes relating to their hardware, into the platform.
Samsung fears that as data accepted by these platforms is stored on external servers, it may end up in the wrong hands. The new rules ban the use of generative AI systems on computers, tablets, and phones, as well as on internal networks that Samsung owns and offers its employees. Samsung products sold to consumers, such as Android smartphones and Windows laptops, aren't restricted from accessing these platforms.
Implications of the Ban
The use of generative AI in the workplace has been on the rise, with employees using it to automate tedious tasks, such as data entry and analysis. Samsung's decision to ban the use of these platforms in the workplace will affect the company's productivity and efficiency, as well as the productivity of its employees. The ban may also prompt other companies to review their policies regarding the use of generative AI in the workplace.
Read the full article
#ban#BingAI#ChatGPT#dataleakage#generativeAI#GoogleBard#internalmeetingnotes#memo#Samsung#securitymeasures#semiconductordivision#sensitivedata#servers#top-secret
0 notes
Text
12 types of malware ❗️
In today’s interconnected world, the threat of malware looms large. Malware, short for malicious software, refers to any software designed with harmful intent. It can compromise the security of computer systems, steal sensitive data, disrupt operations, and even cause financial losses. Understanding the different types of malware is crucial in order to protect yourself and your digital assets. In this article, we will explore 12 common types of malware and discuss ways to safeguard against them.
Read on 👉 https://www.valevpn.com/post/12-types-of-malware
CyberSecurity #Malware #MaliciousSoftware #SensitiveData #ProtectYourself

0 notes
Text
Tweeted
Participants needed for online survey! Topic: "Understanding how much sensitive information people will disclose" https://t.co/xu81KhZpX3 via @SurveyCircle #uniofeastanglia #psychology #ComputerScience #disclosure #SensitiveData #EstablishedSources https://t.co/EZDe6uY7Or
— Daily Research @SurveyCircle (@daily_research) Apr 24, 2023
0 notes
Text

TSAROLABS offers ERP, Telecom, Cyber Security, and Cloud Services to the B2B segment. ✅
Are you prepared for when an incident occurs? 🤔
TSAROLABS provides incident response services to help you stay ahead of the curve and protect your data.
Click the link to find out who these services are for and how they can benefit you ➡️ https://tsarolabs.com/use-case/incident-response-services-whos-it-for/
#tsarolabs #ourservices #incidentresponse #cybersecurity #cyberattack #cybercrime #security #business #databreach #recovery #rapidresponse #data #networks #dataprotection #sensitiveinformation #threats #cyberthreats #sensitivedata #documentation #prevention
0 notes
Text
Solving PCI DSS Demands On CISOs
All organizations that handle credit card or other types of payment card data must effectively and efficiently meet all of the various sections of PCI DSS 3.2 for PCI compliance and data security. Just like SOX or GDPR compliance, a failure to protect cardholder data can result in stiff penalties and fines as well as associated costs in settlements, legal fees and reputation loss. Many CISO’s have stated that a guide to meeting each section of the PCI compliance regulation is needed due to the following:
Too many vulnerabilities to sufficiently address to be PCI compliant due to limited manpower resources
A lack of a systematic and automated process which aligns to the various compliance sections for protecting credit card data
Multiple and non-integrated DLP solutions both on premise and in the cloud that do not sufficiently and specifically address the PCI security standards and mitigate risk
None or very little up-to-date threat intelligence or vigilance of data at rest and/or data in use as specified by the PCI SSC (PCI Security Standard Council)
A patch work of solutions and standard operating procedures regarding the compliance of the PCI security Standards council for PCI data
However, with the right partner for rapid discovery, accurate classification and automated protection of your PCI DSS payment card data, information security officers can now easily and cost effectively address most if not all of your PCI DSS data security compliance requirements.
How To Get There
Step 1: Rapid Data Discovery
You can’t protect what you can’t find. Easier said then done, but with the appropriate “data at rest” security solution you can do just that. The key to complying with the designated entities.2 as well as requirement 7 for PIC compliance is to make sure that all of the pre-loaded data sets to be PCI compliant are available and ready to implement. In addition, make sure that at the same time you can load your own necessary data sets that are particular to your organization and your cardholder data. Data such as intellectual property or unstructured data such as that miscellaneous credit card number associated in a word doc or Excel spreadsheet. Your solution should also continue to protect your credit card data by discovering in “real time” all new PCI cardholder data collected.
Step 2: Accurate Classification
Once you find your structured and unstructured PCI compliant sensitive data you need to have a DLP solution that can accurately classify the PCI data. Whether a small organization with a minimal sized PCI data base or an organization using Splunk for big data management, it’s impossible to do so with just your own personnel. And that includes investigating and resolving any and all false positives of the data security standard. To keep your costs down and compliance up, make sure your application can return less than 5% false positives for PCI compliance of credit card data. Under 3% is fantastic for accurate PCI compliant classification which will return an excellent ROI as well as praises from the CIO and board of directors.
Step 3: Automatic Remediation
To be cybersecure and meet requirements six and seven, the automatic remediation of all existing and newly acquired PCI cardholder data is necessary. Your application should allow for various types of data protection and also provide for the automatic remediation based on administratively set policies. Not only will this guard against unauthorized access due to phishing attacks but also from unintentional internal abuse regarding DSS compliance. The added benefit is that your organization, with the appropriate dashboard, will be able to review and monitor the audit logs for all past and present days per PCI DSS requirement 10.
This post guides CISOs in meeting PCI DSS requirements using Spirion for rapid discovery, accurate classification and automated protection of all payment card data. Request the detailed whitepaper here.
1 note
·
View note
Text
#surfacelaptop4#MobileProcessors#sensitivedata#PCIdevices#ZeroTrustsecurity#HVCI#malware#phishingattack#SystemGuard
0 notes
Text
Important Facts about PCI-DSS
You may hear about “PCI Compliance”, “PCI-DSS secured Apps” or "PCI” terms before. But you may not be aware of what PCI-DSS is and how it is important in today's digital world.
So, this article will clear out your gray areas about this topic quickly and easily.
What is PCI-DSS?
Payment Card Industry Data Security or PCI-DSS consists of standards that ensure the safety cardholder data across the world. These policies and procedures are defined in 2004 by the PCI Security Standards Council. They serve the organizations and people who work with cardholder data. Current standard documents can be found on the Councils website.

Who should follow these standards?
✓ Financial Institutions
✓ Merchants
✓ POS Vendors
✓ Hardware and Software Developers
✓ And whoever involving in processing, transferring, and storing cardholder data.
The Basics of PCI Compliance
Many organizations think that compliance is a one-time activity. No, it’s not. PCI Compliance is a continuous process.
Mainly, PCI compliance consists of 12 standards. These will apply to any business that employs in credit/debit card data regardless of the size of the business or location.
Below mentioned data should be protected which includes the following:
✓ Cardholder name
✓ Expiration date
✓ CAV2, CVC2, CVV2, CID (the security digits on the back of credit cards)
✓ Service code
✓ Full magnetic stripe data
✓ PINs
Levels of PCI Compliance

Four levels exist for the standard. These levels are divided based on the annual number of credit/debit card transactions a business processes.
✓ Level1: Merchants who process more than six million VISA transactions per year fall into this category.
✓ Level 2: Merchants who process transactions between 1 to 6 million VISA transactions per year fall into this level.
✓ Level 3: Merchants who process transactions between 20 000 to 1 million VISA e-commerce transactions per year is fall into this level.
✓ Level 4: Applies to merchants processing fewer than 20,000 VISA e-commerce transactions annually, or those that process up to one million real-world transactions
Each level has its requirements that are needed to fulfill by the merchants.
How do I become a PCI-DSS Compliant?
If you want to become a PCI complaint merchant or an organization, you need to follow twelve requirements.
Install and maintain a firewall configuration to protect cardholder data.
Do not use vendor-supplied defaults for system passwords and other security parameters.
Protect stored cardholder data.
Encrypt transmission of cardholder data across open, public networks.
Protect all systems against malware and regularly update anti-virus software or programs.
Develop and maintain secure systems and applications.
Restrict access to cardholder data by business justification.
Identify and authenticate access to system components.
Restrict physical access to cardholder data.
Track and monitor all access to network resources and cardholder data.
Regularly test security systems and processes.
Maintain a policy that addresses information security for all personnel.
Why Security is important?
Everybody needs to know about cardholder data security and it affects and who is in the digital payment industry.
If you are a merchant who accepts digital transactions then you need to ensure that the customers' card details are secured with your payment channels. When you are a payment app developer or financial institution who runs a payment app, then you all should protect customers’ card details when processing, storing and transmitting with other parties.
If the financial institutions or merchants do not follow the secure methods when transacting, customers will complain about the payment channels. When your application is unstable and not securing the customers' card details, then you will lose the credibility you have built through the community. Sometimes your business will fail because of your careless mistakes when joining with payment vendors and other parties involved in customer data handling.
As you know, PCI requirements are not “one-and-done” requirements. You need to maintain your data security every day.
0 notes
Photo

Tokenization is the process of replacing sensitive data with
unique identification symbols that retain all the essential
information about the data without compromising its security.
JISA offers Vault based Tokenization and Vaultless Tokenization.
For more details please contact us [email protected] OR CALL ON +919619222553
You can also visit www.jisasoftech.com
0 notes
Text
Fortifying Data Masking: Strategies for Protecting Sensitive Information and Ensuring Compliance in Today's Digital Landscape
In today's data-driven world, organizations harness data to refine their offerings, enhance customer experiences, and fortify their operations. However, the strategic utilization of Data Masking its dissemination among internal and external stakeholders. While this sharing is crucial for fostering innovation and collaboration, it also introduces risks of security breaches and compromises to sensitive information. Consequently, safeguarding data integrity has become paramount in contemporary data environments.
To mitigate the peril of data breaches and uphold regulatory compliance, such as GDPR, PCI-DSS, and HIPAA, organizations must adopt robust security protocols. These measures are indispensable for curtailing the exposure of sensitive data throughout its lifecycle. By implementing stringent security practices, enterprises can fortify their defenses and uphold the trust of their customers and partners.
In adhering to security and compliance imperatives, organizations deploy a multifaceted approach encompassing various phases of their operational cycle. From data acquisition to storage, processing, and transmission, each stage demands tailored security measures to mitigate vulnerabilities and thwart potential threats. By integrating security seamlessly into their workflows, organizations can engender a culture of vigilance and resilience against evolving cybersecurity challenges.
Central to data masking is the concept of least privilege, whereby access to sensitive information is restricted only to authorized personnel and systems. By limiting access based on roles and responsibilities, organizations minimize the risk of unauthorized data exposure and inadvertent leaks. Moreover, encryption techniques are instrumental in safeguarding data integrity during transit and storage, rendering it indecipherable to unauthorized entities.
Furthermore, organizations invest in robust authentication and authorization mechanisms to validate the identity of users and govern their access privileges. Multi-factor authentication, biometric verification, and access controls are pivotal in fortifying defenses against unauthorized access attempts. Similarly, audit trails and logging mechanisms enable organizations to monitor and trace user activities, facilitating timely detection and mitigation of security incidents.
In parallel, organizations leverage advanced technologies such as artificial intelligence and machine learning to augment their threat detection capabilities. By analyzing vast troves of data in real-time, these systems can discern anomalous patterns indicative of potential security breaches. This proactive approach empowers organizations to preemptively thwart threats before they escalate into full-fledged breaches.
Moreover, robust incident response plans are indispensable for orchestrating swift and coordinated responses to security incidents. By delineating roles, responsibilities, and escalation procedures, organizations can minimize the impact of breaches and expedite recovery efforts. Regular drills and simulations enable teams to refine their response strategies and bolster their preparedness for emergent cyber threats.
Beyond technological fortifications, fostering a culture of security awareness is imperative for cultivating a vigilant workforce. Comprehensive training programs equip employees with the knowledge and skills to identify and mitigate security risks in their daily activities. By instilling a sense of collective responsibility, organizations empower their employees to serve as frontline defenders against cyber threats.
In conclusion, safeguarding sensitive data is an ongoing imperative for organizations navigating the complexities of today's Data Masking. By embracing a holistic approach to data security, encompassing technological, procedural, and cultural dimensions, enterprises can fortify their defenses and uphold the trust of their stakeholders. In a landscape fraught with evolving cyber threats, proactive measures are indispensable for preserving data integrity and fostering sustainable business growth.
#DataMasking#SensitiveData#PrivacyProtection#DataObfuscation#MaskingTechniques#DataAnonymization#DataSecurity#Compliance#GDPR#Encryption#DynamicDataMasking
0 notes
Link
If you have sensitive information that should never be access by anyone but yourself, try not to store it in the cloud – use an external hard drive instead. Keep this hard drive in a secure place in your house, like your safe or a fire proof box. Whilst cloud storage is very secure, if someone guesses your password; access my be compromised.

0 notes
Link
Office computers sometimes contain sensitive data that could be imperative to the company’s operations. But if in the wrong hands, it can prove harmful to the company’s reputation and financial standing. All this happens because sometimes employees get relaxed with their computer’s security.

#computer#security#data#sensitivedata#companyoperations#financialstanding#employees#company#operation#itsupport#computersecurity
0 notes
Photo
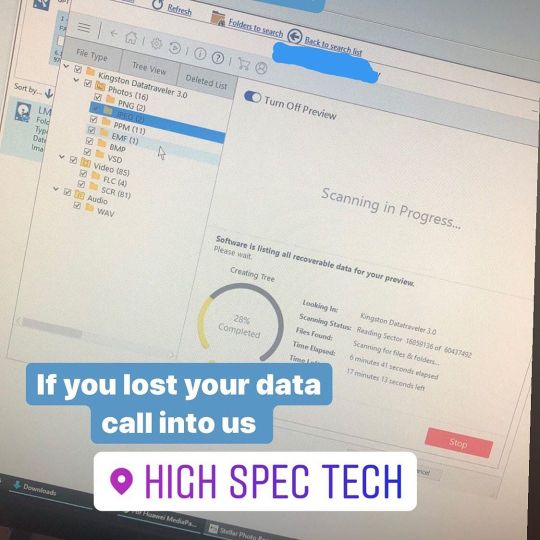
💾DATA RECOVERY💾 Today a very worried customer came into us after FORMATTING their USB key by accident thinking they were formatting another USB- the key contained very important photographs that meant a lot to them. After running this USB through our data recovery software we managed to recover all of their photographs, even photos and files that they previously deleted over time were recovered. If you find yourself in this unfortunate position, deleted or formatted your hard drive on your computer or Mac or even your your usb stick or SD card, we can help. Data and file recovery 🗂 Pictures and video recovery 📷 #datarecovery #datarecoveryservices #datarecoveryservice #recoverydata #recovermydata #datarecoveryspecialist #sensitivedata #dataprivacy #recoverydata #hddrecovery #sadrecover #ssdrecovery #usbrecovery #sdcardrecovery #filerecovery #macdatarecovery #desktopdatarecovery #laptopdatarecovery (at High Spec Tech) https://www.instagram.com/p/B7t6xZlnzl4/?igshid=njyh2z4zy8ku
#datarecovery#datarecoveryservices#datarecoveryservice#recoverydata#recovermydata#datarecoveryspecialist#sensitivedata#dataprivacy#hddrecovery#sadrecover#ssdrecovery#usbrecovery#sdcardrecovery#filerecovery#macdatarecovery#desktopdatarecovery#laptopdatarecovery
0 notes
Text

Are you struggling to keep up with the growing cybersecurity threats in today's digital age? Look no further than DevSecOps. ✅✅
This innovative methodology combines development, security, and operations to create a seamless and secure software development process. From finance to healthcare, every industry can benefit from implementing DevSecOps. ❄️❄️
Don't leave your company vulnerable to cyber-attacks. Embrace DevSecOps today! ✅
👉Learn more about how TSAROLABS can help you strengthen your cybersecurity defenses.
#devsecops #cybersecurity #tsarolabs #digitaltransformation #cyberattack #threats #security #riskmanagement #timetomarket #dataprivacy #agility #customertrust #collaboration #complaince #cybercrime #strengthen #defenses #efficiency #nationalsecurity #publicsafety #criticalinfrastructure #sensitivedata #finance #halthcare #benefit #digitalsecurity
0 notes
Text
Degaussing in Westworld?
Prior to this course, Principles of Information Assurance, I never even thought of how data could be safely deleted. I assumed every time I erase the data on my hard-drive to reset my PC for better performance that the data on it was completely erased forever!
This took me on a research journey on the topic, from watching YouTube videos of a guy degaussing his old crt monitor (80s retro computers). That in fact old crt tv monitors would become extremely effected by anything that emitted electricity, even a nearby lightening bolt hit would cause the monitor screen to scatter.
https://www.youtube.com/watch?v=qEEaZ1GGl9I Here’s a link to the degaussing of the crt monitor if you’re interested!
On my continued research path, I looked into the differences between wiping vs degaussing vs shredding. I recently built my own desktop PC, which helped me under my laptop a little bit better when it came to the motherboard and ssd vs hard drives that I installed. When my SurfaceBook 2 started getting a little glitchy, I decide to do a clean install on it. The performance is just like it was out of the box. Don’t get rid of your old computers just yet! At least not with PC rigs, because they never die really you just replace the parts inside over time.
Finally, in reference to my title and why ensuring a machine has been degaussed properly. Software claiming to wipe a drive is not always a guarantee. Due to GLB-Act & HIPPA regulations, NSA requires that sensitive data has the ability to be completely unrecoverable. If not degaussed properly, your data can still be restored from a partially corrupted drive. It can be repaired so to speak and remounted onto the drive. Additionally, something I didn’t know before researching is that USB drives cannot be degaussed due to their data storage being based on a solid-state drive. Never knew why there was a difference, having both a HD & SSD installed on my PC rig, now I really know why one is quicker than the other.
If you don’t understand my Westworld reference in the title, read this explanation:
Westworld, an HBO show deals with AI being put into this simulation park that its clients pay big money to participate in. Clients can live out their wildest fantasies, kind of like when you’re playing videogames in Red Dead Redemption and be a cowboy. Well, they put in these NPCs characters, real modern AI robots that every time are either killed by a client or client’s actions, they wipe their memory and respawn them back into this simulation world. Some memory wipes aren’t successful and certain AI protagonists have PTSD and rebel. Great show if you haven’t seen it.
All in all, remember to degauss your data storage devices so people can’t access your sensitive data and/or so your computer doesn’t become self-aware and rebel against you.
CITATIONS
What is degaussing & how does it work? (2013, March 1). DataKillers. Retrieved June 17, 2021, from https://datakillers.com/what-is-degaussing-and-how-does-it-work/
Wiping vs degaussing vs shredding - what's the difference? (2019, February 18). ERI Direct. Retrieved June 17, 2021, from https://eridirect.com/blog/2019/02/wiping-vs-degaussing-vs-shredding-whats-the-difference/
#westworld#ai#degaussing#wiping#sensitivedata#databreach#datastorage#pc#pcbuild#ssd#harddriverecovery#magneticfield#red dead redemption 2#erase#robots#cybersecurity#darkweb#usb#irobot#data#erase all data#hippa
0 notes