#maintenance sector
Text





#volunteers??? o_O#remedy control#the furnace#the furnace chamber#maintenance sector#the oldest house#jesse faden#quotes#videogames#horror games#videogames quotes#control quotes#remedy entertainment#control
154 notes
·
View notes
Text



the backrooms
#DEEDEEE GET OUT OF MY LABORATORYYY#the laboratory basement#server room#storage#maintenance sector#my build
28 notes
·
View notes
Text










Federal Bureau of Control
--> The Maintenance Sector
#federal bureau of control#control 2019#control remedy#remedy entertainment#the oldest house#jesse faden#jesse faden control#screenshots#i have a genuinely ridiculous number of these#i think i got a little carried away and spent 5 hours in photo mode haha#oops#maintenance sector
8 notes
·
View notes
Photo





#click on the pictures on desktop for more content#jesse faden#control#crss#janitor's assistant#maintenance sector
34 notes
·
View notes
Text
Why IoT Predictive Maintenance is Important for the Manufacturing Sector?

If you are looking to minimize your machinery's downtime, explore the blog to learn the benefits of IoT predictive maintenance and how it can offer your business improved efficiency and cost reduction in maintenance.
0 notes
Text
If you ever get into an argument on here with someone and the very unlikely scenario happens that they send you a source make sure you actually read the source as literally every single time this has happened to me they have literally misread what the source is about or not bothered to read how the data was carried out and both completely invalidate their argument. 9 times out of 10 the piss poor reading comprehension will win the argument for you
#like a couple of weeks ago someone sent me a WIKIPEDIA source of all things and not only was it not a source on the sector I was talking#about it was from 2011 and the information was completely out of date#the other day I said fgo had more free currency than genshin#and for some reason they felt the need to back up their point that genshin was more generous with citations??#i didnt really care but i was shocked that genshin was supposedly more generous#so i checked it out and turns out that it was a complete list of GENSHINS primos in 2023 but fates was missing maintenence#interludes rank ups bond and servant ascensions#and was literally just an estimate of what we'd get#and when I converted the free currency to actual pulls fate STILL gave more pulls than genshin with the list being incomplete 😂
1 note
·
View note
Text

In the ever-evolving landscape of public infrastructure, the pursuit of accessibility takes center stage. As public entities seek to create inclusive spaces, the strategic adoption of mobility lift services emerges as a pivotal solution. In this blog, we explore the transformative journey of “Unlocking Access” through a strategic approach to adopting lift services within the procure public framework.
The Imperative for Accessibility in the Public Sector
In the modern era, accessibility is not merely a legal requirement; it is a fundamental principle shaping the design and functionality of public spaces. The public sector, driven by a commitment to inclusivity, is increasingly recognizing the need to provide seamless access to individuals with mobility challenges.
Procure Public Framework: A Strategic Enabler
The first step in the strategic approach involves leveraging the lift framework. This established system allows public entities to source and implement mobility lift services efficiently. By tapping into this framework, organizations can streamline the procurement process, ensuring compliance, transparency, and adherence to established standards.
Tailored Solutions for Diverse Spaces
One size does not fit all, especially when it comes to accessibility solutions. The strategic approach involves identifying and implementing tailored mobi lift services that suit the unique requirements of diverse public spaces. From government buildings to public parks, each space demands a thoughtful and customized solution to ensure universal access.
Financial Viability and Sustainability
Budget considerations are integral to any public sector initiative. A strategic approach to adopting mobility lift services involves a careful assessment of financial viability and long-term sustainability. This includes evaluating the cost-effectiveness of various solutions and factoring in maintenance and operational expenses to ensure a sustainable investment.
Community Engagement and Stakeholder Collaboration
Inclusivity is a collective effort. The strategic adoption of mobility lift services necessitates community engagement and collaboration with stakeholders. Seeking input from individuals with mobility challenges, advocacy groups, and the broader community ensures that the implemented solutions align with genuine needs and expectations.
Navigating Regulatory Compliance
The public sector operates within a framework of regulations and standards. A strategic approach involves a comprehensive understanding and navigation of these compliance requirements. This includes adherence to accessibility standards, safety regulations, and any local or federal mandates governing public infrastructure.
Technology Integration and Future-Proofing
Technological advancements play a vital role in enhancing accessibility solutions. A strategic approach involves integrating cutting-edge technologies within mobility lift services. Future-proofing the infrastructure ensures that adopted solutions remain relevant and effective in the face of evolving accessibility standards and technological innovations.
Measuring Impact and Celebrating Success
The journey to unlocking access is not complete without evaluating the impact of implemented mobility lift services. A strategic approach involves setting measurable goals, conducting regular assessments, and celebrating success stories that highlight the positive changes brought about by enhanced accessibility.
Conclusion: A More Inclusive Tomorrow
Unlocking Access, through a strategic approach to adopting mobility lift services within the public framework signifies a commitment to a more inclusive and accessible public sector. By aligning with the principles of transparency, customization, financial viability, and community collaboration, public entities can pave the way for transformative changes that positively impact individuals with mobility challenges. As we navigate this strategic journey, we inch closer to a tomorrow where public spaces truly unlock access for everyone.
#mobility lift#construction and maintenance#procure public#mobility lift framework#building contarctor#public sector#procurement services#united kingdom#london#framework#mobility lift services
0 notes
Text

Have you heard about the Polish Train company, Newag, and the bullshit it turns out they got up to?
So, the regional rail operator Koleje Dolnośląskie bought some Newag Impuls back in 2016 . In late 2021, some of them need to have major maintenance done, as they've been in service a while. So the company SPS (Serwis Pojazdów Szynowych) gets the contract to fix them. They basically take the train apart, replace a bunch of it, following all the rules in the documentation Newag gave them, and... it won't move. The train says everything is fine, the brakes are off, there's plenty of power, but you push the throttle up and it won't move.
SPS spends a while trying to figure out what the fuck is wrong, with no luck. So they hire some hackers from the Polish security group Dragon Sector. Dragon Sector figures out how to get into the code of the computer system that runs the train, and OH MY GOD.
So it turns out there's a secret train-lock system. If it's on, the train won't move. This will be triggered in some situations you might think are normal: the clocks are wrong, the serial numbers of the various parts have changed, and a firmware mismatch between the main computer and the power system. Now, the fact that it makes sense to not run the train in these situations until someone can check it? that doesn't extend to the fact the train uses a SECRET lock system, rather than just popping up an error message telling you what's wrong. There's also the problem that while these are all potential error problems, they can't be cleared by anyone with the technical manuals, which are supposed to cover everything about how to run these trains. Only Newag themselves can reset this system.
Which, you know, keeps SPS from properly fixing them. Only Newag can fix them now, but not because SPS lacks any technical ability, but because Newag sabotaged their own trains. But don't worry: it gets worse.
So now that Dragon Sector knows what's happening, they get to look at other trains. It turns out the trains aren't all running the same software, and there are other tricks in there.
One of them is a "how long has the train been stopped?" check. If the train hasn't hit 60 km/h in 10 days, the train locks itself and won't move until Newag can clear it. So, like, if a train is ever out of service, like it's going to a repair place... it'll break itself. Unless the repair place is owned by Newag.
But two of the trains go further: See, these trains have GPS built in, right? You may be able to guess where this is going...
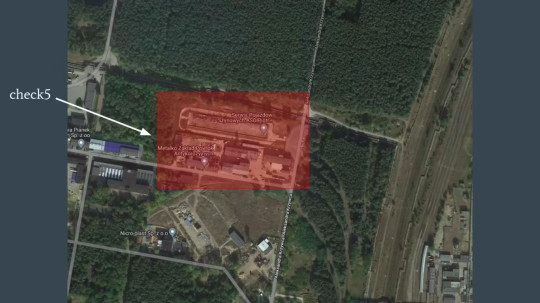
THEY JUST MAKE THE TRAIN CHECK IF IT IS PARKED AT THEIR COMPETITORS' REPAIR YARD AND BREAK ITSELF IF IT WAS.
The sheer audacity of this move. This is frighteningly bullshit anti-competition self-sabotage.
This has, obviously, made some parts of the Polish government to start investigating this. Newag may be (and hopefully will be) in a lot of trouble.
For more info, there's a great video of a presentation by the three people from Dragon Sector who did the hacking, which was presented at the 37th Chaos Communication Congress in Germany.
Ars Technica also has an article on it, but it predates the presentation so it doesn't have some of the later details.
Anyway, the good news is that in the end the hackers at Dragon Sector were able to unlock most of the trains: A few had additional trickery that they didn't want to hack around, because it might break the train's certification. For the others, they discovered undocumented "cheat codes" in the software that they could use to bypass the secret lockouts... presumably the same ones that Newag would have used when they "repaired" trains.
4K notes
·
View notes
Text
#industrial services in marketing#industrial services meaning#industrial market size#industrial maintenance services market size#industrial services examples#global industrial market#industrial services sector#industrial services trends
0 notes
Text
TOP TECH TRENDS TO SHAPE YOUR CAREER IN 2022
2022 Top technologies to shape your career
Artificial Intelligence & Machine Learning
Artificial Intelligence (AI) , although started gaining popularity a decade ago, still continues to be one of the new technologies today because its remarkable effects on how we live, work, and play are still in the early stages. AI is already popular for its use in applications for image and speech recognition, navigation programs, smartphone personal assistants, voice assistants, and much more.
A B2B research firm “Markets and Markets” suggested that the AI market is expected to grow to a $190 billion industry by 2025. So, with AI spreading its wings across sectors, new jobs will be created in development, programming, testing, support, and maintenance. Even the salaries provided for these jobs will be quite high, thus, AI technology is the trend to watch out for.
Robotic Process Automation
Just like Artificial Intelligence and Machine Learning, Robotic Process Automation (RPA) is another trending technology that is automating jobs. RPA in general is the use of multiple software and applications used for automating business processes such as data collection and analysis, customer service, and other repetitive tasks, which were managed previously through manual processes.
RPA is a rapidly advancing technology that generates many jobs across different industries. It offers several new career options and trajectories such as a programmer, project manager, business analyst, or consultant.
Edge Computing
Cloud computing previously was a new technology trend to watch, however, with major players like Amazon Web Services, Microsoft Azure, and Google Cloud Platform dominating the market, Cloud computing has become mainstream.
Although organizations are adopting Cloud solutions today, they have found several limitations in this technology. And thus, it is not an emerging technology trend. Edge is.
Edge computing is designed to help bypass the latency that Cloud Computing causes and helps organizations to get data into a data center for processing.
Click for more information "2022 Information Technologies" -https://codetru.com/TechTrends
#2022 Top technologies to shape your career#Artificial Intelligence & Machine Learning#Artificial Intelligence (AI)#although started gaining popularity a decade ago#still continues to be one of the new technologies today because its remarkable effects on how we live#work#and play are still in the early stages. AI is already popular for its use in applications for image and speech recognition#navigation programs#smartphone personal assistants#voice assistants#and much more.#A B2B research firm “Markets and Markets” suggested that the AI market is expected to grow to a $190 billion industry by 2025. So#with AI spreading its wings across sectors#new jobs will be created in development#programming#testing#support#and maintenance. Even the salaries provided for these jobs will be quite high#thus#AI technology is the trend to watch out for.#Robotic Process Automation#Just like Artificial Intelligence and Machine Learning#Robotic Process Automation (RPA) is another trending technology that is automating jobs. RPA in general is the use of multiple software and#customer service#and other repetitive tasks#which were managed previously through manual processes.#RPA is a rapidly advancing technology that generates many jobs across different industries. It offers several new career options and trajec#project manager#business analyst#or consultant.
0 notes
Text
big fan of robotgirl stuff applied to something that normally could not even be remotely construed as a girl
laser gun with a fuck ass operating system who won’t stop calling you mommy and whose little LCD face puts up a cute picture of an anime girl moaning with her tongue out like a dog when you hit a target. when you stroke her barrel she involuntarily shoots a hole through the wall
butch lesbian earth orbital artillery system who needs praise from their operator when they demolish a bunker
hvac unit who breaks himself constantly because she gets off on having maintenance techs open hir up to repair them and keeps accidentally ratcheting the heat up as soon as the cute girl from Sector 34C they like comes in the room
smart vehicle who keeps disobeying that one rider and instead driving them to romantic locations before popping her warm, soft update port open in full view of the passenger and killing her engine
#terato#monster fucker#terato blog#nsft#fantasy nsft#monsterfucker#teratophillia#robot girl#monster biology post
1K notes
·
View notes
Text



#remedy control#jesse faden#control: ahti#the foundation#the oldest house#maintenance sector#videogames#horror games#remedy entertainment#ahti the janitor
69 notes
·
View notes
Text
So I don't know how people on this app feel about the shit-house that is TikTok but in the US right now the ban they're trying to implement on it is a complete red herring and it needs to be stopped.
They are quite literally trying to implement Patriot Act 2.0 with the RESTRICT Act and using TikTok and China to scare the American public into buying into it wholesale when this shit will change the face of the internet. Here are some excerpts from what the bill would cover on the Infrastructure side:
SEC. 5. Considerations.
(a) Priority information and communications technology areas.—In carrying out sections 3 and 4, the Secretary shall prioritize evaluation of—
(1) information and communications technology products or services used by a party to a covered transaction in a sector designated as critical infrastructure in Policy Directive 21 (February 12, 2013; relating to critical infrastructure security and resilience);
(2) software, hardware, or any other product or service integral to telecommunications products and services, including—
(A) wireless local area networks;
(B) mobile networks;
(C) satellite payloads;
(D) satellite operations and control;
(E) cable access points;
(F) wireline access points;
(G) core networking systems;
(H) long-, short-, and back-haul networks; or
(I) edge computer platforms;
(3) any software, hardware, or any other product or service integral to data hosting or computing service that uses, processes, or retains, or is expected to use, process, or retain, sensitive personal data with respect to greater than 1,000,000 persons in the United States at any point during the year period preceding the date on which the covered transaction is referred to the Secretary for review or the Secretary initiates review of the covered transaction, including—
(A) internet hosting services;
(B) cloud-based or distributed computing and data storage;
(C) machine learning, predictive analytics, and data science products and services, including those involving the provision of services to assist a party utilize, manage, or maintain open-source software;
(D) managed services; and
(E) content delivery services;
(4) internet- or network-enabled sensors, webcams, end-point surveillance or monitoring devices, modems and home networking devices if greater than 1,000,000 units have been sold to persons in the United States at any point during the year period preceding the date on which the covered transaction is referred to the Secretary for review or the Secretary initiates review of the covered transaction;
(5) unmanned vehicles, including drones and other aerials systems, autonomous or semi-autonomous vehicles, or any other product or service integral to the provision, maintenance, or management of such products or services;
(6) software designed or used primarily for connecting with and communicating via the internet that is in use by greater than 1,000,000 persons in the United States at any point during the year period preceding the date on which the covered transaction is referred to the Secretary for review or the Secretary initiates review of the covered transaction, including—
(A) desktop applications;
(B) mobile applications;
(C) gaming applications;
(D) payment applications; or
(E) web-based applications; or
(7) information and communications technology products and services integral to—
(A) artificial intelligence and machine learning;
(B) quantum key distribution;
(C) quantum communications;
(D) quantum computing;
(E) post-quantum cryptography;
(F) autonomous systems;
(G) advanced robotics;
(H) biotechnology;
(I) synthetic biology;
(J) computational biology; and
(K) e-commerce technology and services, including any electronic techniques for accomplishing business transactions, online retail, internet-enabled logistics, internet-enabled payment technology, and online marketplaces.
(b) Considerations relating to undue and unacceptable risks.—In determining whether a covered transaction poses an undue or unacceptable risk under section 3(a) or 4(a), the Secretary—
(1) shall, as the Secretary determines appropriate and in consultation with appropriate agency heads, consider, where available—
(A) any removal or exclusion order issued by the Secretary of Homeland Security, the Secretary of Defense, or the Director of National Intelligence pursuant to recommendations of the Federal Acquisition Security Council pursuant to section 1323 of title 41, United States Code;
(B) any order or license revocation issued by the Federal Communications Commission with respect to a transacting party, or any consent decree imposed by the Federal Trade Commission with respect to a transacting party;
(C) any relevant provision of the Defense Federal Acquisition Regulation and the Federal Acquisition Regulation, and the respective supplements to those regulations;
(D) any actual or potential threats to the execution of a national critical function identified by the Director of the Cybersecurity and Infrastructure Security Agency;
(E) the nature, degree, and likelihood of consequence to the public and private sectors of the United States that would occur if vulnerabilities of the information and communications technologies services supply chain were to be exploited; and
(F) any other source of information that the Secretary determines appropriate; and
(2) may consider, where available, any relevant threat assessment or report prepared by the Director of National Intelligence completed or conducted at the request of the Secretary.

Look at that, does that look like it just covers the one app? NO! This would cover EVERYTHING that so much as LOOKS at the internet from the point this bill goes live.
It gets worse though, you wanna see what the penalties are?

(b) Civil penalties.—The Secretary may impose the following civil penalties on a person for each violation by that person of this Act or any regulation, order, direction, mitigation measure, prohibition, or other authorization issued under this Act:
(1) A fine of not more than $250,000 or an amount that is twice the value of the transaction that is the basis of the violation with respect to which the penalty is imposed, whichever is greater.
(2) Revocation of any mitigation measure or authorization issued under this Act to the person.
(c) Criminal penalties.—
(1) IN GENERAL.—A person who willfully commits, willfully attempts to commit, or willfully conspires to commit, or aids or abets in the commission of an unlawful act described in subsection (a) shall, upon conviction, be fined not more than $1,000,000, or if a natural person, may be imprisoned for not more than 20 years, or both.
(2) CIVIL FORFEITURE.—
(A) FORFEITURE.—
(i) IN GENERAL.—Any property, real or personal, tangible or intangible, used or intended to be used, in any manner, to commit or facilitate a violation or attempted violation described in paragraph (1) shall be subject to forfeiture to the United States.
(ii) PROCEEDS.—Any property, real or personal, tangible or intangible, constituting or traceable to the gross proceeds taken, obtained, or retained, in connection with or as a result of a violation or attempted violation described in paragraph (1) shall be subject to forfeiture to the United States.
(B) PROCEDURE.—Seizures and forfeitures under this subsection shall be governed by the provisions of chapter 46 of title 18, United States Code, relating to civil forfeitures, except that such duties as are imposed on the Secretary of Treasury under the customs laws described in section 981(d) of title 18, United States Code, shall be performed by such officers, agents, and other persons as may be designated for that purpose by the Secretary of Homeland Security or the Attorney General.
(3) CRIMINAL FORFEITURE.—
(A) FORFEITURE.—Any person who is convicted under paragraph (1) shall, in addition to any other penalty, forfeit to the United States—
(i) any property, real or personal, tangible or intangible, used or intended to be used, in any manner, to commit or facilitate the violation or attempted violation of paragraph (1); and
(ii) any property, real or personal, tangible or intangible, constituting or traceable to the gross proceeds taken, obtained, or retained, in connection with or as a result of the violation.
(B) PROCEDURE.—The criminal forfeiture of property under this paragraph, including any seizure and disposition of the property, and any related judicial proceeding, shall be governed by the provisions of section 413 of the Controlled Substances Act (21 U.S.C. 853), except subsections (a) and (d) of that section.
You read that right, you could be fined up to A MILLION FUCKING DOLLARS for knowingly violating the restrict act, so all those people telling you to "just use a VPN" to keep using TikTok? Guess what? That falls under the criminal guidelines of this bill and they're giving you some horrible fucking advice.
Also, VPN's as a whole, if this bill passes, will take a goddamn nose dive in this country because they are another thing that will be covered in this bill.
They chose the perfect name for it, RESTRICT, because that's what it's going to do to our freedoms in this so called "land of the free".
Please, if you are a United States citizen of voting age reach out to your legislature and tell them you do not want this to pass and you will vote against them in the next primary if it does. This is a make or break moment for you if you're younger. Do not allow your generation to suffer a second Patriot Act like those of us that unfortunately allowed for the first one to happen.
And if you support this, I can only assume you're delusional or a paid shill, either way I hope you rot in whatever hell you believe in.
#politics#restrict bill#tiktok#tiktok ban#s.686#us politics#tiktok senate hearing#land of the free i guess#patriot act#patriot act 2.0
890 notes
·
View notes
Text
Imagining academic journal article titles based on lines from Good Omen's Season 1 (mostly) and 2.
“Funny If We Both Got It Wrong, Eh?:” A Case of Process Breakdown in a Centralized Organization
“Just Canceling Each Other Out:” Causal Links between Workplace Burnout and Employee Retention
“Oh, Well, Let Me Tempt You:” The Consequences of Sexual Harassment on the Operations and Maintenance of Infrastructure Mega-projects
“It’s On The Street, It Knows The Risks:” Addressing Cultural Perceptions Inhibiting Pedestrian Facility Improvements in the Transportation Sector
“And I Would Like To Spend…Mmmph:” Deconstructing Communication Failures and their Impact on Relationship Efficacy
#good omens#good omens 2#good omens 1#crowley#aziraphale#silly academia#academic journals#I don't have a reason for doing this other than it was kind of fun
386 notes
·
View notes
Photo




23 notes
·
View notes
Text
One of my favorite things about Control is just how completely and utterly nuts/bonkers/GONE the FBC is as one of these ‘secret government blackops’ groups.
Like this is a trope we’re all fairly familiar with at this point; some secret government organization formed to monitor, contain and research all kinds of weird shit and keep it secret from the public. Also they may or may not have kinda gone totally rogue somewhere along the way and might now answer only to themselves at this point in a ‘who watches the watchers?’ commentary on the need for oversight.
But the more you find out about the Federal Bureau of Control, the more it becomes clear they just so utterly past ANY of that by the time the game begins. And have been for basically the last fifty some odd years.
Like here is a basic overview of the FBC that you learn within the first thirty or so minutes of the game: They are a secret government organization dedicated to the containment, cataloguing and research of supernatural artifacts and events. They are headquartered in what they call ‘The Oldest House’, a tall, imposing yet utterly nondescript building in the middle of New York City that is literally impossible for anyone to enter or even notice unless they already know about it. And the interior of the building is actually a twisting extradimensional labyrinth that also opens up to other dimensions/realities and might actually be the World Tree Yggdrasil. It also kind of hates any technology made in the last twenty years. And apparently Number 2 Pencils.
Oh, and the FBC doesn’t really report to the US Government. They report to a floating, inverted black pyramid that exists in a space outside of known reality that might also be the collective human subconscious. The pyramid is colloquially referred to as ‘The Board’ and they are an extradimensional entity/group of entities that appoints the Director of the FBC via the use of a physics-defying geometric gun called ‘The Service Weapon’ that is probably Excalibur/Mjolnir/every other legendary weapon in human myth. They also speak in word-salads and probably know they are in a video game.
See, back in 1964 when the FBC first discovered The Oldest House, they basically decided ‘WOW, this place is cool! Let’s make it our new headquarters!’ and promptly moved in. This was also when the current Director at the time found the Service Weapon within The Oldest House, made contact with/was chosen by The Board and from the point on the FBC really hasn’t answered to the US Government anymore.
Also, the Government basically doesn’t even know the Bureau even EXISTS anymore. Remember how The Oldest House has this kind of ‘Perception Filter’ that prevents almost anyone from entering it or even noticing it, which is how basically nobody can find it despite the fact that it is right in the middle of New York City? Well, after they moved in and became effective ‘residents’ of the house, this filter started applying to the FBC itself. They basically CAN’T be noticed or remembered at this point by anyone who isn’t part of the organization. The reason this secret organization can operate entirely off the grid and can’t be tracked is because they literally have freaky extradimensional reality-warping covering their tracks.
This is what I meant when I said that the FBC is just so far GONE. At this point, the FBC is itself a crazy, supernatural thing in and of itself.
Other fun details about the FBC include:
The Bureau facilities in The Oldest House are not powered by coal, oil or nuclear power. No, instead the lights are kept on by a former director who went a tad power-mad and lost control of his pyrokinesis, so the Bureau locked him up in a giant ‘Sarcophagus Containment’ unit and now use him as a power-generator. He also sometimes talks through the waste-disposal furnace to try and get people to bring him human sacrifices.
The maintenance sector of the FBC includes an area called the ‘Black Rock Quarry’. The so called ‘black rock’ is an extra-dimensional mineral that, among other things, blocks and dampens supernatural effects and abilities. Needless to say, the Bureau mines the stuff extensively. Now, despite being within The Oldest House, the Black Rock Quarry is an open-top quarry. To space.
One of the ways Bureau personnel get around is via pull-strings that show up all over The Oldest House. Pull a string three times and you are transported to the Oceanview Motel, a quaint little motel that probably exists outside of known reality because no one has ever been able to actually go or see outside the motel. Once you’re there, you just ring the bell on the front desk three times, do some random task and procure a room key. The key opens a door, but only one with an inverted black pyramid. From there, you pull another string and are transported back to somewhere else in The Oldest House. So basically a rather convoluted teleportation system. There are also doors with other symbols that probably go to other realities, but the Bureau hasn’t figured out how to open them. Though one does seem to lead to a void of malevolent darkness that feeds off human creativity and is currently holding one Alan Wake.
Also, the bureau’s janitor is probably a Finnish Sea God.
#control#control 2019#federal bureau of control#ahti the janitor#rambling about one of my favorite games
2K notes
·
View notes