#It Security
Text
Evil Malware
Welcome back to another episode of An Actual Post. As usual, no prior computer science education needed.
Today I'm going to talk about the worst of the worst malware. A lot of things has happened since what the general population consider to be viruses; annoying and maybe steals some money or logins. Unfortunately it's nowadays way way way worse than that so prepare for some uncomfortable reading!
Since the dawn of Stuxnet (which I wrote about here), malware has gotten increasingly more real-life, with real-life complications. It could be the Pegasus spyware, that targets political activists in authoritarian regimes, or disruptive infections that put a stop to Copenhagens metro trains for a few hours. But we're merely in the beginning, because in the last few years, some nasty shit has been going down. I'm going to write about two (technically three but I'll group the first two together for obvious reasons) of the worst incidents we've seen today.
BlackEnergy and CrashOverride
This piece of malware has been around since early 2000's, for the intention of creating DDoS attacks (which I wrote about here) from infected computers. It has since then branched out in its usage, particularly into targeting infrastructure environments.
Most notable is the 2015 Ukrainian powergrid incident, which occured when the Russian hacking group known as "Sandworm", infected three Ukrainian energy companies, wiping out systems and causing a power outage for over 250 000 households during winter.
The attack began with just one infected document being opened in the affected companies. When BlackEnergy infected their systems, it opened up a remote connection to the attackers, making them able to control the entire powergrid opreation from inside Russia, and thereby switching it off.
That was not enough though, as the attackers also implanted another piece of malicious software known as KillDisk, which wiped out many of the ciritical operation systems, as well as cutting off the connection to the UPS units, which are backup generators in case of system outage. To add a cherry on top, BlackEnergy did what it was originally intended to do - DDoS attacks - towards the energy companies call-centers, so that customers were not able to call and ask what was happening.
The Ukrainian powergrid is quite outdated, which made the attack easier, but it was also the saving grace, as they still had manual power-switches (as opposed to purely digital, which were under the attackers control), so power was eventually restored before they had to rebuild all of their digital systems. This is more concerning for countries with modern powergrids, as manual switches have all been replaced by only digital, meaning power restoration could take weeks or months in case of a similar attack.
Besides the energy companies, three other critical Ukrainian infrastructure organisations were hit by BlackEnergy, but did not result in any operational outages.
But it didn't stop there. Just one year later, in December 2016, a similar attack struck Kiev, successfully taking down one-fifth of the countrys electrical power. Like with the BlackEnergy incident, it was quite quickly restored, but there was a far more horrifying infection this time. Named CrashOverride, the malware was much more sophisticated than BlackEnergy, did more things automatically without the need of input from a remote attacker. It was also modular, meaning that functionalities could just be added to it like lego-pieces, adapting it to whatever kind of electrical grid it was entering. This meant that it wouldn't just be able to infect only Ukranian electrical grids, but just about any country's. Furthermore, evidence points to the 2016 CrashOverride infection only being a test-run.
Triton
Last but definitely not least - Triton, the first (known) malware designed to kill.
But before we talk about it, we need to look at what happened in Bhopal, India in 1984 when what has since been considered the worst industrial disaster of all time occured. At the Union Carbide India Limited pesticide plant in December 2nd, one of the gas tanks had a fatal malfunction, creating a massive gas leak of methyl isocyanate, which is extremely toxic. The leak spread to the surrounding city of Bhopal, resulting in almost 600 000 injured people, 40 000 temporary injuries, 4 000 permanent or severe injuries and over 8 000 people died within the first two weeks, with an estimated additional 8 000 deaths following due to injuries in the time after.
This was of course not caused by Triton, but it became the inspiration for the creation of the malware
In 2017, a new piece of malware was discovered in Schneider Electrics industrial control system (called Triconex) at a Saudi Arabian petrochemical facility, which unravelled a horrible and complex secret. The infection chain for Triton contains many steps, so let's start with a brief overview of what the Triconex ICS and SIS is. ICS (Industrial Control System) are computers that handles all the industrial processes, computers that are programmed to do one thing and one specific thing only, unlike our regular PCs which you can play games or surf the internet and whatever. ICS will be computers who control valves, releases chemicals into vats, spins stuff around, or whatever automated processes may happen at an industrial facility.
SIS (Safety Instrumented System) are a kind of ICS that are responsible to check that everything is going alright and, if needed, will take over the process in case some ICS is failing and may result in damage, fire, injury or other disasters. So a SIS are monitoring failsafes, meant to prevent what happened in Bhopal.
Unless, of course, you program a malware intended to make the SIS malfunction.
What happened in the Saudi Arabian petrochemical facility started as follows:
The attackers successfully implanted a remote access trojan, which just like in the BlackEnergy case, makes the attackers able to control infected machines remotely. However, you can't infect a ICS or SIS this way, you need to enter a regular computer with internet access first, which is what they did. The initial machine was an engineering station, on which ICS and SIS computers are controlled. From there, the attackers wanted to plant their own software on the ICS and SIS machines, but there was a problem; the software can't be installed without someone turning a physical key on the Triconex devices, as a security measure. A second problem is that every time new software changes are made to a Triconex device, the old software will be deleted and replaced entirely by the new, which meant that the malware was at risk of being deleted if any engineer made any software changes.
So a second piece of Triton malware was made to overcome those hurdles. Instead of being save where the software should be saved in the Triconex devices, it saved itself where the firmware was installed (the piece of software that's made to have the Triconex work as opposed to where the software that tells the Triconex what to do), this not only gave Triton persistence even if new software was loaded, but also overrides the physical key as firmware always has administrator privileges.
With all this in place, the attacker could execute any commands at the comfort of their home to both the ICS and SIS systems in the facility.
As luck would have it, before the attackers were able to cause any harm, the facility experienced a safety incident, prompting shutdown of the whole operation, and an investigation later uncovered the malware in the systems. Had Triton not been discovered in time, it would have been able to cause catastrophic failures similar to what happened in Bhopal. But just because it was thwarted this time, doesn't mean it's gone for good. There will always be some actor who is willing to try again.
Thank you for reading and sorry if I scared you, but honestly I think people need to be aware of the situation, as for some bisarre reason, events like these are not reported in the news. If you have any questions, feel free to send an ask!
139 notes
·
View notes
Note
Are passwords with words actually good? I ask because you mentioned being shown that xckd comic in security class
Short Answer:
Yes! Its easier to remember, and the chance of a hacker guessing your password is very low- especially if the words are unrelated (such as CorrectHorseBatteryStaple)
Long answer:
Yes, but there are lots of different ways passwords can be compromised.
A password with words- or a passphrase- is good because it adds many possibilities. For example, CorrectHorseBatteryStaple has 25 characters in total. A hacker has no idea WHAT those 25 characters are, making a brute force attack (a method where you try every POSSIBLE combination) will take fucking eons- and nobody has time for that. Using a passphrase also prevents modifications, ie. when you use 1337speak or add random capitalization (password -> p455w0rd -> Password!).
However, a password/passphrase is only as good as how many times its used. If you use CorrectHorseBatteryStaple for everything, from your Tumblr account to your bank, it makes it REALLY EASY to hack into your stuff. If you use the same email and password for a random forum that is the SAME email and password for your paypal, they could theoretically access your paypal. There's another great xckd comic on this:

So, its best to have a different password for everything. I recommend a password manager. I personally use BitWarden since its free, can connect between your phone and your computer, and it requires one master password to access everything! (Which is easier than remembering 25 different long ass passwords). I tend to randomly generate them then punch them in.
If you want to be more secure, I recommend 'peppering' your randomly generated passwords. I wont go to into what that means, but basically, a password 'pepper' is adding an extra little bit at the end. lets say you choose your pepper to be 'xkcd', your password would look like 'passwordxkcd'. That way, if something ever happens to your password manager, you STILL don't have to worry to much about your passwords!
What I do is save a password in Bitwarden (8zeCSdv7k$), then whenever it autofills, i add my pepper onto as my official password! (8zeCSdv7k$xkcd). Therefore, the only things i have to remember are:
A) a master password, where I recommend using a passphrase, and
B) a random 'pepper' word to add onto the end of your passwords
And boom! That's IT security 101 with a dude who has taken one class.
TLDR: Passphrases are good and great for memorizing, but try not to reuse them! Use a password manager and keep your info safe!
#Anon i hope youu know i started this; drafted it; then went on my laptop to finish it#perhaps classically trans of me but i think IR security is cool af and i want a job in it lol#This was fun omg i spent like 20 minutes writing this#thank you anon!#vodka.ask#it security
9 notes
·
View notes
Text
just got this email with the subject line being "stinky cheese". that's pretty silly and quirky lol. gonna open it
10 notes
·
View notes
Text
"The UK government has set in train plans to introduce legislation requiring tech companies to let it know when they plan to introduce new security technologies and could potentially force them to disable when required.
The measures were announced just minutes ago in the King's Speech – when the country's monarch reads out a declaration that is written by the ruling political party, marking the start of the parliamentary year. The proposed changes could give the Home Office advance access to technical details of security measures employed by popular big tech platforms so it can access user data and monitor nefarious activity."
5 notes
·
View notes
Text
Peran dan Tugas seorang IT Infrastructure dalam Perusahaan
Seorang profesional IT Infrastructure memiliki peran yang sangat penting dalam sebuah perusahaan karena mereka bertanggung jawab atas desain, implementasi, pemeliharaan, dan keamanan infrastruktur teknologi informasi perusahaan. menurut pengalaman saya selama beberapa tahun bekerja di bidang IT Infrastructure, Berikut adalah beberapa peran dan tugas penting seorang IT Infrastructure dlm…
View On WordPress
#Disaster Recovery#it infrastructure#IT Infrastruktur#IT Security#Peran IT#Technical Support#tugas it
2 notes
·
View notes
Text

untuk pegiat IT / Hobbist / dan yang tertarik soal IT Security. Mari merapat. Sekaligus kopdar. Untuk area solo dan sekitarnya yok..
4 notes
·
View notes
Text
SentryPC offers a wide range of features, including:
SentryPC is a cloud-based computer monitoring software that allows you to remotely monitor, filter, and control all user activity on your PC or Mac. It is a powerful tool that can be used for a variety of purposes, including employee monitoring, parental control, and IT security.
SentryPC offers a wide range of features, including:
Content filtering and blocking
Website and application monitoring
Time and activity tracking
Keystroke logging
Screenshot capturing
Remote access and control
Reporting and analytics
SentryPC is easy to use and can be deployed on any PC or Mac. It is also affordable, with plans starting at just $10 per month.
If you are looking for a powerful and affordable computer monitoring software, SentryPC is a great option.
Here are some of the benefits of using SentryPC:
Remote monitoring and control: You can remotely monitor and control all user activity on your PC or Mac from anywhere in the world.
Content filtering and blocking: You can block access to websites, applications, and files that you deem inappropriate or harmful.
Website and application monitoring: You can track which websites and applications users are visiting and using.
Time and activity tracking: You can track how long users are spending on their computers and what they are doing.
Keystroke logging: You can log all keystrokes made by users, including passwords and other sensitive information.
Screenshot capturing: You can capture screenshots of user activity at any time.
Reporting and analytics: You can generate reports and analytics on user activity to help you identify potential problems or areas for improvement.
SentryPC is a powerful and versatile computer monitoring software that can be used for a variety of purposes. It is easy to use, affordable, and offers a wide range of features. If you are looking for a way to monitor and control user activity on your PC or Mac, SentryPC is a great option.


#makemoney#marketingagency#marketing101#videomarketing#marketingplan#marketingmultinivel#marketingdigital#marketing#marketingtips#marketingonline#computer monitoring software#IT security#Content filtering#Website and application monitoring#Keystroke logging#Screenshot capturing#Remote access and control#Reporting and analytics
6 notes
·
View notes
Text

It's always a good time to update your passwords, folks. Chart from here. Turn your 2FA on everywhere while you're at it, too.
2 notes
·
View notes
Text
The Unending Struggle of the Klingon System Admin
Point of view: You're the Klingon IT admin on a warship.
"By the spirit of Kahless how many times do I have to tell you fools, your passwords must be secure, they should not be the name of your favorite targ from your childhood nor should they be the date you became a warrior and made your first kill!"
"And you Captain, give another random warrior with strong arm and an opera voice the envy of Q'onoS access to our systems on their word of honor that their house needs our records without verifying they actually belong to that house again, and I will show the crew what degenerate human filth you look up in the privacy of your cabin!"
-----
Every other race in the quadrant is in awe, because when klingons get a good IT Security chief.
"Tell me again about that time you shoved your captain's head into a bulkhead for considering breaching computer security with an alien probe!"
The newbie refills the tankard of bloodwine in front of the battle-scarred Klingon system admin, dreaming about how many disasters his federation ship could've avoided if he'd just be allowed to do the same.
"To this very day, there is an impression in the wall in the shape of the old captain's head." The Klingon reminisces.
------
Other allied factions dread the day they learn that the ships new Sys Admin was trained by the Klingons.
"Mr. Riker, make sure the crew know that I expect all regulations to be observed," Picard said, "We have Mr Worf's cousin coming on board to help with the upgrade of the Enterprise's Operating System."
"You mean?"
"Yes, a Klingon System Admin"
#star trek#klingon IT specialist#klingon comptuer security#writing prompt s#writing prompt#klingons#it security#klingon system admin#system admin
12 notes
·
View notes
Text
To know more information about this video click on this link :
You need an enticing lead magnet, professionally designed funnel pages, a reliable emailing platform, and an autoresponder as well as a sequence of emails written to
engage, grow their audience across multiple networks, increased merchandise sales, and expand to other income streams, which you can now give them with SociEmpire.
SociEmpire is the world's first and only influencer system that finds high-paying risk clients, builds a unique solution for them, and their life, and is ready to hand over with just a few clicks. Just moments from now,
your agency website can be live capturing highly targeted leads And turning them
into paying clients for you.
#tumblr#blogging#social media#computers#technology#it security#internet security#internet culture#internet#privacy#google#operating systems#apps#algorithmic bias#algorithmic stablecoin#i hate algorithms#tiktok algorithm#tumblr algorithm#generative#connect#app#influencer#thursdaythoughts#fridayfeeling
2 notes
·
View notes
Text
Qradar coming with some subtle commentary with the alert
"Ransomware Behaviour: Microsoft Windows System"
4 notes
·
View notes
Text
What Is Cybersecurity?
In information systems, we can define cyber security as the protection of the security, integrity and confidentiality of our communication, life, integration, tangible or intangible assets and even our data in the electronic environment.
In today’s technology age, we have begun to reflect a large part of our lives in electronic media. Not just us individuals! But states, public institutions,…

View On WordPress
4 notes
·
View notes
Text
Purdue Model for OT Security
What is the Purdue model for OT Security?
The Purdue Enterprise Reference Architecture (PERA) identifies the different tiers of vital infrastructure utilized in manufacturing lines, as well as how to safeguard them. If implemented correctly, PERA could achieve the air gap between OT and IT systems. The Purdue model was adopted from the Purdue Enterprise Reference Architecture model by ISA-99. This model provided a framework for segmenting industrial control system networks from corporate enterprise networks and the internet. It’s segmented into separate levels.
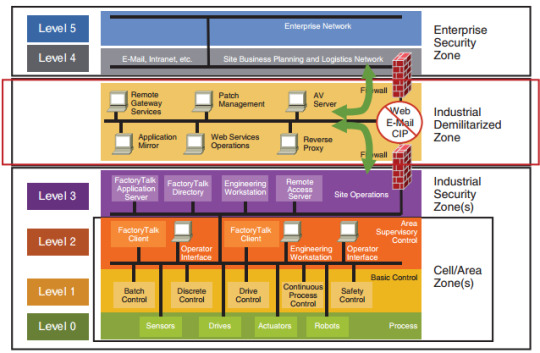
Level 5 – Enterprise Network
This level’s systems are typically corporate-wide and span many locations or factories. They collect data from subordinate systems in specific plants and combine it with other information. The majority of these systems are housed in corporate data centers. Plant production schedules, material usage, shipping, and inventory levels are all controlled by ERP systems present in this level.
Level 4 – Site Business Planning and Logistics
All the IT systems that support the production process in a facility are present here. Web servers, file servers, print servers, business workstations, email clients are a few of the types of systems found in this level. Active Directory networks are also implemented in this level. These systems send production information to corporate systems, such as uptime and units produced, and they collect orders and business data from corporate systems to disseminate to OT and ICS systems.
Read complete blog - https://redfoxsec.com/blog/purdue-model-for-ot-security/
2 notes
·
View notes
Text
The US, on 29 February, vetoed a UN Security Council (UNSC) statement that would have condemned Israel for the mass murder of over 100 Palestinian civilians who were awaiting the delivery of humanitarian aid in Gaza City.
“We don’t have all the facts on the ground – that’s the problem,” US deputy ambassador to the UN Robert Wood told reporters on Thursday.
He then claimed there are “contradictory reports” about the Israeli army's latest massacre and highlighted that Washington was focused on finding “some language that everyone can agree on.”
Thursday's veto is the fifth time Washington has blocked a UNSC statement or ceasefire resolution that would hold Israel accountable for the atrocities it has committed in Gaza.
#yemen#jerusalem#tel aviv#current events#palestine#free palestine#gaza#free gaza#news on gaza#palestine news#news update#war news#war on gaza#genocide joe#united nations#united nations security council#joe biden#gaza genocide#genocide
21K notes
·
View notes
Text


Vanny gets arrested at Five nights at Freddy’s
#myart#chloesimagination#doodles#vanessa fnaf#vanessa shelly#vanessa afton#fnaf vanny#fnaf#fnaf fanart#five nights at freddy's#fnaf movie#security breach#Vanny if killing was illegal#arrested for being a silly goose#if anyone says ‘can someone draw x?’ I’ll be there
28K notes
·
View notes
Text
IT Sicherheit: Der Schlüssel zur digitalen Unversehrtheit in der modernen Geschäftswelt

In der Ära der Digitalisierung, wo Daten als das neue Gold betrachtet werden, spielt die IT Sicherheit eine entscheidende Rolle im Schutz unternehmerischer Ressourcen und im Vertrauensaufbau bei Kunden. Mit der Zunahme von Cyberangriffen und Datenlecks wird die Notwendigkeit einer robusten IT-Security-Strategie immer dringlicher. Dieser Artikel beleuchtet die vielfältigen Aspekte der IT Sicherheit und gibt Einblicke, wie Unternehmen ihre digitalen Vermögenswerte wirksam schützen können.
Grundlagen der IT Sicherheit
IT Sicherheit, oder IT Security, umfasst die Praktiken und Technologien, die eingesetzt werden, um digitale Informationen und IT-Infrastrukturen vor unerlaubtem Zugriff, Beschädigung oder Diebstahl zu schützen. Sie ist ein vielschichtiges Feld, das physische Sicherheitsmaßnahmen, Netzwerksicherheit, Anwendungssicherheit und Informationssicherheit einschließt. Jede dieser Komponenten trägt dazu bei, eine sichere und stabile IT-Umgebung zu schaffen.
Bedeutung der Netzwerksicherheit
Die Netzwerksicherheit spielt eine zentrale Rolle, indem sie das Rückgrat eines jeden Unternehmens, sein Netzwerk, absichert. Firewalls, Antivirenprogramme und Intrusion-Detection-Systeme sind nur einige der Tools, die dabei helfen, unerwünschte Eindringlinge fernzuhalten. Angesichts der zunehmenden Komplexität von Cyberangriffen wird es immer wichtiger, diese Systeme kontinuierlich zu aktualisieren und zu überwachen, um sicherzustellen, dass sie gegen die neuesten Bedrohungen gerüstet sind.
Die Rolle der Anwendungssicherheit
Softwareanwendungen sind oft das Ziel von Cyberangriffen, da sie wertvolle Daten verarbeiten und speichern. Die Sicherheit von Anwendungen beginnt bereits in der Entwicklungsphase mit dem Einsatz von Secure Coding-Praktiken. Regelmäßige Sicherheitsaudits und Penetrationstests helfen, Schwachstellen zu identifizieren und zu beheben, bevor sie von Angreifern ausgenutzt werden können.
Bedrohungen durch Malware und Ransomware
Malware und Ransomware sind zwei der gefährlichsten Bedrohungen für IT-Systeme. Sie können Daten verschlüsseln, stehlen oder sogar ganze Systeme lahmlegen. Ein effektiver Schutz erfordert eine Kombination aus proaktiven Maßnahmen, wie der Schulung von Mitarbeitern im Umgang mit verdächtigen E-Mails, und reaktiven Maßnahmen, wie dem Einsatz spezialisierter Sicherheitssoftware, die darauf abzielt, solche Bedrohungen zu erkennen und zu blockieren.
Datenschutz und Compliance
Die Einhaltung gesetzlicher Vorschriften und Industrienormen ist ein weiterer kritischer Aspekt der IT Sicherheit. Vorschriften wie die Datenschutz-Grundverordnung (DSGVO) der EU legen strenge Richtlinien für die Verarbeitung personenbezogener Daten fest und erfordern von Unternehmen, angemessene technische und organisatorische Maßnahmen zum Schutz dieser Daten zu treffen. Nicht-Einhaltung kann nicht nur zu Bußgeldern führen, sondern auch das Vertrauen der Kunden beeinträchtigen.
IT Sicherheit als fortlaufender Prozess
IT Sicherheit ist kein einmaliges Projekt, sondern ein kontinuierlicher Prozess. Angesichts der sich ständig weiterentwickelnden Cyberbedrohungen müssen Sicherheitsstrategien regelmäßig überprüft und angepasst werden. Dies umfasst die Schulung von Mitarbeitern, die regelmäßige Überprüfung von Sicherheitsrichtlinien und -prozeduren und die Anpassung der Infrastruktur an neue technologische Entwicklungen und Bedrohungsszenarien.
Die IT Sicherheit ist ein unverzichtbarer Bestandteil der Unternehmensstrategie in der digitalen Welt. Sie schützt nicht nur wertvolle Informationen und Systeme, sondern sichert auch das Vertrauen von Kunden und Partnern. Unternehmen, die in ihre IT Sicherheit investieren, schützen nicht nur ihre gegenwärtigen Assets, sondern bauen auch eine robuste Grundlage für zukünftiges Wachstum und Erfolg. Durch die Integration fortschrittlicher Technologien und Strategien kann jedes Unternehmen seine digitale Präsenz sichern und die Herausforderungen der Cyberwelt erfolgreich meistern.
0 notes