#IF YOU EVEN TYPE VECTOR INTO GOOGLE
Text
something's wrong with me-
every time i hear the word vector, you know what pops up???

THIS BITCH
1 note
·
View note
Note
Re: suits, there are hundreds of different types of suits, but the most common cuts are british, american and italian. I could see Lando (aka would love to see) most likely in an italian cut (slim tailoring on trousers and jacket, unstructured shoulders, light cloth (not colour but fabric) also looks very nice with an open collar and no tie...). Typical big brand names here are Zegna, Armani or Attolini, I personally love Kiton and Brioni as well, but just googling itlian cut suits should show some good results.
For Oscar, I would adore a (for once) properly tailored brutish cut suit (higher waistline for the trousers, more structure in the shoulders, tapered waist, thicker fabrics). Maybe even make it a proper three-piece bc ever since the wetsuit pics from Australia, I think we all agree that those curves need to be shown more often. Examples here are Ted Baker, Dunhill and ofc everything Savile row.
Tho if we keep with the Mclaren sponsors, Reiss does some great work as well. There's a double-breasted tuxedo jacket in this year's collection that I would love to see Lando in (then again tuxedos are a whole nother topic ...)
This got very long and is probably not very helpful but I love infodumping about fashion lol <3
i know you were self conscious about writing at length about this but all i have to say is: yes. here is some additional photographic evidence from my POV;
lando in snazzy italian tailoring, but to take the stylised vector a bit further:
exhibit a: asymmetric waistcoat with steampunk details
exhibit b: italian but with a fun pattern
exhibit c: open collar a step further, he could so rock a 70s suit. also just really need him to rock the gucci glasses with some shiny loafers like he’s sooooo got that vibe. im thinking how bruno mars and harry styles wear that kind of suiting sometimes



now to our elusive chanteuse f1 driver oscar jack. i feel like it’s, like what you described, about a classic style but with really fine details. good fabrics, simple cuts, plain colourways. below is pretty stylised but also this is rpf and it’s my playground and if we were claiming realism we should just put the rpf toys down full stop and i am not doing that!!
if taking a costume designer’s perspective too, there could be soooo much you could say with layering and pattern and contrast depending where we are in the story or plot. the idea of fic!oscar in a classic brit cut suit with tiny revealing details like a handkerchief (lando’s) or a button (a nod to a family member or a friend) is very dear to me.
the other option i like is a classic tux jacket with tails and crisp shirt and a a sky blue handkerchief, like idk that image also tickles me for some reason.



anyway so i had been thinking about a tailor AU- *loud scuffling noise as i try to put wayward au ideas back in their box*
p.s. oscar in dunhill... like u were cooking but u especially cooked w that one....
and tagging the people who might be interested in this conversation i invite y’all to weigh in!! @cx-boxbox @kichona-s and @jusst-you-race
#i need to stop thinking#landoscar#mctwinks#twinklaren#op81#ln4#it’s getting bad guys idk how i just see random things now and im like. how do i make this landoscar#wizrambles.txt
23 notes
·
View notes
Note
Any tips on drawing Military camos?
Hello Anon!
It's been a long time since I made a drawing tutorial/tips. This one actually caught my eye since I did have a hard time on this, but after a few months of research, I finally got the hang of it!
Here's my way/tips on military camos!
Know that there are LOTS and LOTS of camo patterns, each one is for different types of terrains, and each country's military uses different types of camo patterns as well.

So, decide where your character come from. Then, look up on Google the camo patterns that the military uses, or you can use these websites :
Camopedia, a website that is dedicated to documenting the camouflage design, development, and history.
Wikipedia List of Military Clothing Camouflage Patterns according to the countries.
2. Once you found the name of the pattern, search it up on google for tracing and reference. You can even find the a free vector on google as well. If you can, find a large image and repeatable image so that you can make it look seamless.

3. Trace it/ just save the image. Yes it's fine. camo patterns doesn't really belong to anyone, and you can use it freely, especially for art. I usually make vector image and saves it as an asset so I can just use the image every time I'm drawing a military character.
How I Apply Camo Pattern Image to My Characters!
I'm going to draw Captain Eleanor "Ladybug" Graham, my Call of Duty OC. She's an American combat medic, which mainly uses Operational Camouflage Pattern (OCP). Here's how I apply the camos :
Draw the character and add base color with the clothes on different layer.
Color the character on a different layer. Alpha Lock it.
Open the camo pattern image, put it above the base color layer, then clip it down! IMPORTANT : the size of the camo pattern is actually pretty big on the uniform. Look up references to see how the camo pattern scales to the clothes. Don't make it look too small.
Don't be afraid to copy paste it over and over and place it carefully to make it seamless.
4. To shade the clothes, add another layer above, clip it, then change the effect to multiply. Then, shade away!


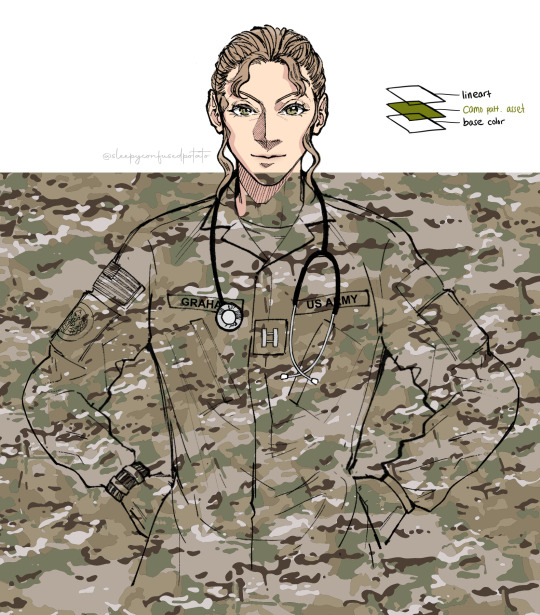


Tadahh~! Now you have a badass soldier as your character! (👉゚ヮ゚)👉
Hope this tip helps! (★‿★)
#art#art tips#art tutorial#military camos#military#art struggles#drawing#drawing tips#uniform#military uniforms#call of duty#cod#art stuff#tutorial by me!#art ref#art reference
468 notes
·
View notes
Note
Do you have any info on the Ginfaxi symbol? Seen a heathen who had it tattooed on their throat and immediately had alarms go off in my head.
I'll post what I know about Ginfaxi, but it won't tell you anything more about the person you saw than you already know. I like thinking and writing about this stuff so I wrote a lot but, yeah, none of this is really going to narrow anything down for you. I'm trying to put the rest behind a break but Tumblr doesn't like breaks anymore, and keeps moving this one around, so we'll see what happens.
I assume that what you mean by "ginfaxi" is this:
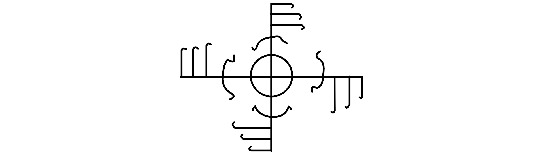
This isn't the only symbol that gets called that (more on that below) but it is the most common, and it's what comes up when you Google it. I don't really know anything about how modern people are using ginfaxi but here are some off-the-cuff thoughts:
it's probably on its way into popularity because Ægishjálmur and Vegvísir are too well-known to be mysterious and cool anymore
while less common than those, it's been commercialized for just as long. You, anon, probably know this already, because you probably googled it before asking me, and turned up all the same tchotchke shit that every other "Ancient Viking Magic" symbol is slapped onto. That has more determination over how people relate to it than any 18th/19th century black book does.
there's higher-than-average risk of it being made into a symbol of "Viking warriors" or similar because of its actual historical association with glíma even though conceptually it's closer to staves for winning at chess (which do also exist) than it is to actual combat
yeah I do think it has potential to be a "swastika with plausible deniability" but I honestly don't know if people are doing that and if anything its touristification might be the thing that prevents it
it occurs to me that TikTok is probably a serious vector for how people are experiencing this stuff, and it's something I know absolutely nothing about other than that people like to put runes and stuff on their faces. So I dunno, that could be an influence here.
When you're trying to figure out what it means when you see a galdrastafur on someone, it doesn't necessarily do you any good to learn about its background and history if the person who got it inked didn't bother to research that themselves, and I'm disinclined to believe that someone who got a vaguely swastika-like symbol on their throat did that. I have no idea if the symbol has any more frequency among racists than it does among sorta "general population" heathen/viking-interested people who relate to the past basically through the lens of the tourist gift shop, who would have been getting "Celtic" symbols if it were still the 90's, which seems to be the majority of people involved with this stuff at all. A radically different group of people also comes to mind: in my experience in east coast US, some crusty gutter punk types also use symbols like Icelandic galdrastafir and runes, and they're also more likely to get a tattoo on their throat or face or whatever than the average viking enthusiast. I know a guy who used to put runes and stuff on his panhandling signs and claimed they did get him more cash, and whether it was magic or just drawing attention or what didn't really matter to him.
Anyway, the point is, I think that tattoo was a bad idea, makes someone look like a nazi, and you should side-eye them until you know better, but for better or worse there are other possible explanations for how that symbol got there. I'm not making excuses for anyone, just stating the blunt fact that there are non-nazis who attracted to this symbol and decorate itself with it without even thinking about any of this.
It shows up in that annoying graphic of "Norse" symbols with no context that occasionally makes the rounds (that manages not to include a single symbol from the actual Viking age), with an incorrect or at least misleading description:

And as much as this sucks that is probably the main way that people experience symbolism that is related (whether in a historical or a recently-contrived way) to "the Norse."
The version of the symbol I've been talking about is the most well-known because it comes from Íslenzkar þjóðsögur og æfintýri by Jón Árnason, the most important folklore and fairy tale collection from Iceland. I'm not sure where he got that particular image. When he was writing in the mid-19th century, he said that ginfaxi and gapaldur (which often accompanies ginfaxi) were among the most widespread symbols with the most variety of uses, and even mentions them before ægishjálmur. Ginfaxi was probably always used in glíma, and since that's the context it appears in in magic books while other uses seem not to have been recorded, the association with glíma became stronger over time. It was to be written on a piece of paper or wood-chip and put in the toe of the left show, while gapaldur was supposed to be under the heel in the right shoe (there is some variation in the procedure). According to Grunnavíkur-Jón Ólafsson (via Jón Árna) the two symbols together were also used for spookier things like going into hills (i.e. like huldufólk do, I guess, there's no additional context) and repel sendingar (sort of like ghosts raised by hostile wizards to harm someone) but I don't know where Grunnavíkur-Jón wrote about that or anything else about this. Here is a variant gapaldur from Jón Árnason:

According to Jón Árnason (link in Icelandic), it was rumored that the two staves were composed by hiding the names of different æsir in them. To me, that implies either a method of encoding that is totally opaque to me, or that belief pertained to an entirely different set of visual symbols (either of these are highly plausible). It seems the names ginfaxi and gapaldur (or gapandi) were better-known than the actual visual symbols themselves, and there are many variants that look hardly anything like the one in Jón Arna (this is not surprising -- there are also many symbols called ægishjálmur other than the one we all know). Probably many more people suspected others of having used symbols like these to gain advantage over them, than actually used symbols themselves, so that the idea of ginfaxi would precede anyone knowing how to actually draw it, and perhaps there never really was an original or fixed shape.
Jónas Jónasson (another folklore collector) identified this one from Lbs 977 4to as another ginfaxi although I don't know how he knows it's that and not gapaldur:
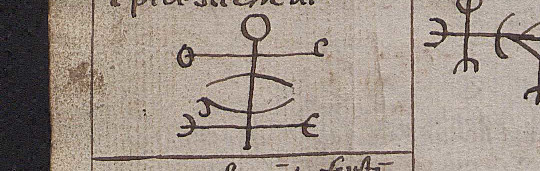
This one comes with a formula to recite that invokes Óðinn and Frigg and is specifically about winning at glíma.
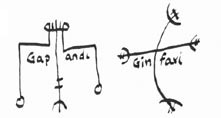
These two are from the Galdrasýning á Ströndum website (only on the Icelandic version of the page for some reason), not sure where they got them either. With these you're supposed to carve them on a piece of turf when the moon is waxing and drop some of your own blood into them, then put them in your shoes and recite a verse.
I think it's worth showing what glíma is. True, when an Old Icelandic text refers to people doing an action that is uses the verb glíma to describe, it's talking about actual fighting, but this is the stuff that the glímugaldrar ('glíma-magic') that we have is about:
youtube
21 notes
·
View notes
Text
Since I don't want to soapbox in my fanfic author's notes...

(Body illustration vector created by freepik - www.freepik.com)
Anyone who thinks a good thing has happened, yay babbies not being aBoRtEd, is not paying enough attention. Nevermind the ridiculousness of ‘life begins at conception’. Roe v Wade was about privacy, and one woman’s abortion just happened to be the private medical procedure to bring the greater legal issue to light. Judge Clarence Thomas has literally stated he’s going after LGBT+ rights, contraception, and other privacy rights next. While he’s married to a white woman! Who was involved with the January 6 riots to upend peaceful transition of power! Samuel L. Jackson has apparently nicknamed him Uncle Thomas, I won’t use it myself but I think it fits.
I won’t even type the names of the other justices who voted in favor of this, you know which two especially can rot in hell.
Women suffering miscarriages of wanted pregnancies will die, see the story of Andrea Prudente literally happening now as this is going down. Women in abusive relationships will either be forced to carry a pregnancy that ties them to someone they want/need to escape from, or they’ll be harmed by the abusive partner who wants the potential baby gone by any means necessary. Children – 13, 12, 11, 10-year-old children – will be forced to stay pregnant and give birth to their rapist’s babies even though their bodies are literally too small for that to be safe. Suffer the little children indeed, I really hate those hypocritical pro-lifers wanting to ‘save the children’. Women in poverty or other similar situations wanting to focus on the children they already have and love, will be stretched beyond their breaking point and the whole family will suffer. Fertility doctors are already stopping treatment for couples trying to start a family. Some states don’t allow women to be divorced while they’re pregnant, looping back around to that abusive partner scenario. Also, since all my examples so far have been “this all claims to be pro-life and for the children but look at how much damage to children and families it will actually do”, let me state: women are more important than the fetus they carry and if they don’t want to be pregnant and give birth, they should the right to that bodily autonomy. And of course throughout all of that and more, BIPOC women are always more at risk.
Let’s begin with a little history lesson – the pro-life movement in American began because of racism: https://www.politico.com/news/magazine/2022/05/10/abortion-history-right-white-evangelical-1970s-00031480
Next – technology has skyrocketed since the 70s, obviously. “So you're getting an abortion in the era of surveillance capitalism”. This thread and the information it links to is so super important: https://twitter.com/caitlinrcruz/status/1540498513829793795 The twitter thread has an good infographic but if you want to skip straight to the guide: https://digitaldefensefund.org/ddf-guides/abortion-privacy
This article is full of resources, “28 Ways To Protect Abortion Rights & Reproductive Freedom”, listing organizations to donate to, how to get involved politically, who to follow on social media, what to stock up on :https://www.goodgoodgood.co/articles/abortion-rights-resources
It’s a pretty comprehensive list, some of organizations and ideas include:
ACCESS is a podcast that “pulls back the curtain, demystifying abortion by bringing you real, first-person stories and expert perspectives.” https://www.apodcastaboutabortion.com
Keep Our Clinics “supports independent abortion providers nationwide... [it] financially assists small, community-based clinics with funding that covers security, building repairs, PPE and hazard pay, legal fees, and community education and advocacy.” http://keepourclinics.org/
Instead of donating to national Planned Parenthood it’s better to focus on the smaller state level now. Here’s a grassroots google doc for abortion funds in each state: https://docs.google.com/document/d/1T-aDTsZXnKhMcrDmtcD35aWs00gw5piocDhaFy5LKDY/mobilebasic
I’m also seeing posts advocating parsley tea to help bring about miscarriage, but it looks like an old wives tale that does more harm than help: https://www.refinery29.com/en-us/2019/07/238817/parsley-tea-period-miscarriage-abortion
Saved this link back in February, it’s an international organization that offer online consultations and mail order medication: https://aidaccess.org/
And of course, a book rec, “New Handbook for a Post-Roe America,” use this site to buy it from anywhere other than Amazon and maybe at a local indie bookstore near you: https://www.indiebound.org/book/9781644210581 or this amazing site: https://www.betterworldbooks.com/search/results?q=New%20Handbook%20for%20a%20Post-Roe%20America%20
I don’t have the energy right now to talk about how the good ol’ US of A is turning into a fundamentalist Christian dystopian hellscape, or how the loudest pro-lifers have the most bizarre and completely inaccurate ideas about how medical care or women’s’ bodies work. And I hate that nothing encapsulates how this minority of absolute nutjobs are dragging others into hell with them, than the state of Texas, where they’ll force women to have them innocent babies only to not give a crap about protecting them from madmen with an AR-15 just a few years later.
#roe v wade#abortion rights#reproductive rights#reproductive health#bodily autonomy#pro choice#legal abortion#abortion#womens rights#womens health#reproductive justice#roe vs. wade#american problems#united states#living in america#women's rights#women's issues#women's health
2 notes
·
View notes
Text
Here's Why You Should Always Log Out of WordPress
New Post has been published on https://thedigitalinsider.com/heres-why-you-should-always-log-out-of-wordpress/
Here's Why You Should Always Log Out of WordPress
We may think we know WordPress security. But we can’t underestimate the task at hand. It seems that surprises lurk around every corner.
Consider a recent report from the security firm We Watch Your Website, for example. The report claims that 60% of hacked WordPress sites stem from stolen session cookies. I sure didn’t see that one coming.
We know about using strong passwords and setting file permissions. We understand the importance of updating our WordPress installs. We may even use a security plugin or two.
However, even the most security-conscious among us can miss things. That one oversight can lead to a hacked website. And that’s despite taking a bevy of security measures.
Stolen session cookies weren’t on the radar. So, what can we do to prevent this from happening? The author of this report has some advice.
How to Prevent Stolen Session Cookies
Thomas J. Raef is the author of “The Real Attack Vector Responsible for 60% of Hacked WordPress Sites in 2023.” His report demonstrates the threat of stolen session cookies in great detail. And a recent appearance on the WP Tavern Jukebox podcast shed more light on the subject.
But what about remedies? How do we stop these attacks from impacting our websites? I asked Raef for some preventative tips. The answer is as simple as logging out.
Our interview was lightly edited for clarity and brevity.
How do session cookies get stolen?
Thomas J. Raef: If it’s not WordPress, they’re frequently stolen via cross-site scripting. However, WordPress uses the HttpOnly option in the headers. So, that prevents cookie theft in WordPress via XSS.
The main way is by info stealers. If you Google the term, you’ll see it’s almost as popular as ransomware. Some ransomware hackers are starting to use info stealers more for their infections. Info stealers are designed to evade detection from most anti-malware programs. Some are dedicated to evading detection on Windows, others on Macs.
They typically steal everything possible in about 10 seconds. Some ask, why would they bother stealing WordPress session cookies if they’re also stealing bank logins, etc. But look at the cybercriminal industry. What do they need for the majority of their attacks? Oh, a legitimate website to infect unsuspecting visitors.
They steal the session cookies because it totally bypasses 2FA (Two-Factor Authentication), MFA, etc. because the user is still authenticated. As long as the cookie hasn’t expired.
Raef’s report shows that nearly 60% of hacked WordPress websites were the result of stolen session cookies.
Image credit: We Watch Your Website
How can we secure our devices against this type of threat?
TJR: The easiest way is to remember to log out. That’s it! When you log out you expire the cookie. If you just close your browser window, it leaves the cookie active. So, if it’s stolen, it can be used by anyone.
One simple prevention is using SolidWP (Solid Security). Their Trusted Devices feature uses the IP address to generate the session cookie. If it’s stolen, it can’t be used anywhere other than where it was originally created. Those two things are the best way to prevent session cookies from being used against your sites.
Are there any changes the WordPress project could take to increase the security of session cookies?
TJR: Possibly. If there was a procedure that checked for inactivity after 30 minutes, and then automatically logged out the user, that might help. But I believe that would involve JavaScript and that’s getting too complicated. They already include the HttpOnly option, so they’re doing a lot to prevent this from being even bigger.
Do you have any other advice for web designers managing WordPress sites?
TJR: Make sure that everyone with admin access to your site is also focused on sanitary procedures for all local devices. We’re seeing more and more sites being infected due to malware on the local device of an admin. It can steal usernames, passwords, and session cookies.
2FA can stop the usage of username and password, but not session cookies. Tell all devs to log out! It’s quite simple and 100% effective.
One thing we’re starting to see more of is hackers attacking from the local device. Not stealing session cookies or anything else, just piggybacking on a legitimate admin session.
We see the legit IP address of an admin, and they’re doing their work and then suddenly from the same IP address at the same time, the legit admin is working – BAM! – a bogus plugin is installed from the same IP address!
The hackers have control over the local device and they’re attacking from that device. This supports the fact that you MUST be concerned about the health and well-being of your local devices.
Your Device Is Also a Factor in Website Security
A compromised computer or mobile device can impact your website’s security. On the surface, this theory makes sense. However, we typically don’t hear much about it.
Website security usually means a focus on the site itself. We attempt to filter out malicious traffic. And we employ various methods to prevent direct attacks.
It’s past time to look at our devices as well. You know, the systems we use to log into our websites. Good security should start there.
An info stealer can do untold damage in mere seconds. We won’t know the consequences until it’s too late. Let’s do something about it.
Follow best practices to secure your device – and encourage your clients and colleagues to do the same. A few simple steps could prevent a catastrophe.
And to follow Raef’s advice: Be sure to log out of your website! An expired session cookie is useless. Thus, it can’t do any harm.
Many thanks to Thomas J. Raef for chatting with us! Check out more of his security advice at We Watch Your Website.
Related Topics
Top
#2023#2fa#admin#Advice#anti-malware#authentication#browser#computer#cookie theft#cookies#cross-site scripting#Design#designers#detection#devices#factor#filter#Google#hackers#hand#headers#Health#how#how to#impact#Industry#infections#INterview#Interviews#it
1 note
·
View note
Text
AI-powered chatbot to ask complex questions
The Biggest Assortment of One Billion
Stock Resource With World's First (GPT-4 Controlled) 300-In-One Application That Makes, Create And Decipher Any Sort Of Items For Yourself As well as Your Clients In 60 Seconds
AISTOCKAPP is the Finished Across the board man-made intelligence Application Suite For Your Computerized Resources, Items, Showcasing Materials and Visual depiction Needs
Aistockapp Will Assist You With getting
Moment Admittance To:
1 Billion+ Eminence Free Excellent Stock Resources:
Stock Pictures
Stock Recordings
Stock Sounds
Stock GIFs
Stickers
Vectors
Artists
Search Vertical Pictures
Search Even Pictures
Search Vertical recordings
Search even recordings
Search Energized recordings
Add Movement to any Text and get Vivified Text recordings
10 Million DFY Articles group, PLRs, Digital books Pack
200+ PLR Articles
12k HD Recordings
1k Canva Formats Pack
Advance Simplified Pictures Manager
Dispenses with All The Issue Of Looking And Downloading Content From Various Destinations.
Make GPT-4 simulated intelligence Fueled Items:
Article
Blog introduction
Blog bullet point article
Blog frame
Blog outro
Blog section
Blog entry
Blog area
Blog labels
Blog argument
Blog title
Content punctuation
Content revise
Content outline
Section
Make GPT-4 artificial intelligence Fueled Items For Your Sites:
About us
Source of inspiration
FAQ
Include segment
Title
How it functions
Meta portrayal
Meta catchphrases
Upsides and downsides
Survey
Subheadline
Tribute
Make GPT-4 computer based intelligence Controlled Promoting Items For Your Business:
Notice
Facebook notice
Google notice
Set of working responsibilities
Statement of purpose
Pamphlet
Torment Upset Arrangement
Public statement
Item sheet
Message pop-up
Startup thoughts
Startup names
Incentive
Vision proclamation
Welcome email
Make GPT-4 computer based intelligence Fueled Items For Your Virtual Entertainment Posts:
Hashtags
Social post
Social post inscription
Tweet
Twitter string
Video portrayal
Video script
Video labels
Video title
Records
Make records utilizing 50+ premade formats or through custom layouts
Pictures
Create pictures utilizing different boundaries, like style, medium, channels, and goals.
Your Own Chatbots
Visit with the simulated intelligence progressively on your own customized artificial intelligence fueled chatbot to pose complex inquiries and Create any sort of items you need.
Records
Decipher sound discourse into text, convert sound to message precisely.
Trade
You can likewise trade every one of your archives in CSV design.
Moment admittance to 1 Billion Stock Resources, For example, Pictures, Recordings, Sounds, Images, Gif's, Movement and More in different sizes and goals...
Create Human-Like Substance In Any Specialty
Make Staggering Online Entertainment Posts for Facebook, Instagram, Tiktok, Twitter, and YouTube in 1-Snap And Get Moment Notice
Make and Sell Items for any Specialty
Moment admittance to 300-in-1 ChatGPT-4 man-made intelligence Controlled Premium Business Elements For Simply A Small Low One Time Expense with practically no limitation
Drop that large number of costly month to month memberships and Save $1,000s a Year on Items, Illustrations, Recordings and Interpretation
At no point ever Stress Over Protected Resources In the future As Every one of the Stock Resources You Want Are Presently Under One Rooftop...
Make and Sell any kind of items for Business, Site, Websites or Online business stores
Cloud Based Application, Nothing to download or introduce Begin Like a flash...
Iron-clad 30 days unconditional promise
300% Unconditional promise In the event that Application Doesn't Work For You
0 notes
Text
Where can I find such a phone holder?
Introduction:
In today’s fast-paced world, staying connected on the go is a necessity. Whether you’re navigating unfamiliar roads, enjoying outdoor adventures, or simply need to keep your phone within easy reach, a reliable phone holder is essential. If you’ve been searching for the perfect phone holder that combines durability, versatility, and convenience, look no further than Vector Off-Road. In this blog post, we’ll explore why Vector Off-Road is the ultimate destination for finding the ideal phone holder to meet your needs.
1. A Wide Range of Options:
Vector Off-Road is renowned for its extensive collection of phone holders, ensuring that there’s something for everyone. Regardless of your preferred mounting location, vehicle type, or personal style, you’ll discover a diverse selection to choose from. Whether you prefer dashboard mounts, windshield mounts, or versatile solutions like cup holder or vent mounts, Vecto`r Off-Road has got you covered.

2. Unmatched Durability:
When it comes to phone holders, durability is paramount. Vector Off-Road excels in this department, offering phone holders constructed from high-quality materials that can withstand the rigors of off-road adventures, bumpy roads, and daily commutes. You can have peace of mind knowing that your phone is securely held in place, even in the harshest conditions.
3. Easy Installation:
No one wants to spend hours fumbling with complicated installation processes. Vector Off-Road understands this, and their phone holders are designed for quick and straightforward installation. With user-friendly instructions and intuitive designs, you can effortlessly set up your phone holder and hit the road in no time.
4. Secure Phone Mounting:
Your phone’s safety is of utmost importance, and Vector Off-Road prioritizes it. Their phone holders feature secure and adjustable grips that can accommodate various phone sizes, ensuring a snug fit without compromising accessibility. You can drive with confidence, knowing that your device is securely mounted, allowing you to focus on the road ahead.
5. Versatile Adjustability:
Every individual has unique preferences when it comes to the viewing angle of their phone holder. Vector Off-Road understands this need for customization and offers phone holders with adjustable arms, swivel mounts, and rotating heads. This versatility allows you to position your phone at the perfect angle for optimal visibility and comfort.
6. Compatibility with Various Devices:
Vector Off-Road’s phone holders are designed to be compatible with a wide range of devices, including smartphones, GPS devices, and even tablets. Whether you have an iPhone, Samsung Galaxy, Google Pixel, or any other popular smartphone, you can trust that Vector Off-Road has a phone holder that suits your device.
7. Exceptional Customer Service:
When it comes to purchasing a phone holder, excellent customer service is a crucial factor. Vector Off-Road takes pride in providing exceptional support to their customers. Their knowledgeable and friendly team is ready to assist you with any inquiries or concerns you may have, ensuring a smooth buying experience from start to finish.
Conclusion:
Finding the perfect phone holder doesn’t have to be a daunting task. With Vector Off-Road’s extensive range of options, durability, easy installation, secure phone mounting, versatile adjustability, compatibility with various devices, and exceptional customer service, you can trust that you’ll find the ideal phone holder that meets all your requirements. Don’t compromise on quality or settle for subpar options. Visit Vector Off-Road’s website today at https://vectoroffroad.com/ and discover the phone holder that will keep you connected, no matter where your adventures take you!
#New defender phone mount#Bronco phone mount#Jeep phone mount#off road phone mount#ipad clamp mount#gladiator phone mount#tube mount clamp
0 notes
Text
How to check a WordPress website for malware and secure it?
Fix Hacked Site - Malware Removal and Website Security Service.
How to check a WordPress website for malware and secure it?
When we decompose WordPress, we get three main parts: WP Core, WordPress Plugins, and WordPress Themes. If these elements are not handled well, they leave the door open for hackers to get in. Web developers in their first year, content writers who want to blog about their favorite topics, and people with no technical knowledge make this mistake unknowingly and leave WordPress websites vulnerable to hacking. They don’t know what to do when things go wrong.
Some things people need to correct are installing unreliable plugins from unreliable sources, updating plugins without testing them, and installing WordPress themes vulnerable to attacks. Even if they pay for a theme or website development, they need to pay more attention to the maintenance and assistance of the website, which usually leads to the website becoming a hacker’s paradise.
WordPress websites that get infected with malware are a nightmare for website owners. When this occurs, you should be prepared for laborious cleansing to get points back in order. The most vital point is to relax because WordPress site cleaning can be complicated and time-consuming, but not impossible.
Most common WordPress malware infections
Among the most common WordPress malware types, there are mainly four types of infections you should be on the lookout for:
Backdoor: Backdoors allow hackers to access your website by exploiting outdated software, vulnerabilities in a code, and default passwords. Sometimes you can recognize this malware because a file name has been changed, for example, lok.php.
Drive-by downloads: This type of malware inserts downloads links into your website to trick your users into downloading a payload to their local computer. This payload then displays a warning that the computer has been infected and includes a link to install an antivirus program (which is another payload).
Pharma hacks: Pharma Infection adds SPAM links to your website, leading to online pharmaceutical stores. Pharma links are considered the most popular type of website infection and can even use conditional rules to control what the user sees, which makes them much harder to find.
Malicious redirects: This malware redirects users who visit your website address to a malicious website. This malicious website may also contain a payload automatically downloaded to the user’s computer.
Signs that your WordPress internet site has been hacked
The tricky thing about malware is that it is only sometimes apparent that your website has been infected. Some malware infections prefer a low profile, so your website may not show any visible symptoms.
For this reason, we list the most effective methods to determine whether your website is infected with malware – from the most likely to the more subtle ones.
Google has flagged your website
If you see this red death screen when visiting your website, it means that Google has either detected malware on the website or has good reasons to believe so:
This message is displayed if Google Safe Browsing denylists your website. This feature is used by popular browsers like Google Chrome, Mozilla, and Safari to warn their users about potential danger.
Google Search Console sends you warnings that your website has been hacked
Google may also send you alerts and emails informing you that your website has been infected, provided you have connected it to Google Search Console. These messages also contain information about suspicious URLs and possible attack vectors.
Your hosting provider shuts down your website
Hosting providers often scan their servers for signs of malware and may block hacked websites to prevent a virus from spreading. There are several reasons why your hosting provider may disable your website. These include malicious code found on your server, Google denies listing your domain, spam and phishing emails sent from your server, etc.
Your customers alert you about malware

Often, it’s not the website owners but the users who first learn about malware issues. In this case, they may contact you via a contact form or by phone to let you know that something is wrong. For instance, if you run a WooCommerce shop, your users might complain that their credit cards have been hacked.
You see spam search results for your website

Try Googling your brand name and see if you notice anything strange in the results. The warning signs can range from meta descriptions with pharmaceutical or unrelated keywords, to Google indexing pages that shouldn’t exist, to strange characters in the search results.
Your website takes much longer to load

Poor website performance can also be a sign that your website is infected. If your pages suddenly take much longer to load, malware might consume your server’s resources.
You have noticed that your website’s files have been modified

It is critical that you extensively scrutinize your website’s files if you have access to them. to see if there have been any adjustments. If a file has been changed recently but not by you, examine it closely for malicious code. Also, look for files with suspicious names, such as .aspx.
Right here are detailed guidelines on exactly how to remove malware from your WordPress site
Create a backup and scan your WordPress website for malware
Create a backup copy of your website’s files. Back up the content files, images, and other assets. Prepare your website for a detailed audit or scan. We first need to determine which files caused the infection, i.e., the source of the infection. If the source is located in your computer files, the infection may reoccur even if you restore the website.
Moreover, in this case, other parts of your system might also be infected. So, scan your computer thoroughly first. Also, download all the files from the website using an FTP program so they are scanned along with the computer files.
All potential threats stored on your computer or website files will be detected at this stage.
If you still cannot detect any potential threats that might have caused the infection, run an online scan of the WordPress website for malware. Once this scan is completed, you can view the report to see if anything suspicious happened.
Google Webmaster tool will also help you to check your website and flag the problematic areas.
Check the WordPress theme for malicious code
We are discussing WordPress, so how can we disregard plugins and themes? You will likely get infected through an outdated plugin or theme because that is the backdoor through which the hackers enter or send malicious code to do their dirty work.
Abandoned plugins or old theme files are easy prey for hackers. You need to manually scan WordPress plugins and themes for malware to determine the location of the infection. Perform a thorough scan of your theme and plugin files. Themes are files with a .php extension.
Theme Authenticity Checker
Quttera web malware scanner
Exploit scanner
Anti-malware scanner
WP Antivirus Website Protection
Google Safe’s Browsing
Delete and replace files to remove malware from the website
WP Core is the main file, also known as the heartbeat of a WordPress website. Delete the main file, but keep wp-content and wp-config; you will need them later.
Replace salts in the WPconfig file: Salts are used to kekeepordPress users’ passwords secure. Changing your salts will keep attackers at bay. Replace the salts in the WP config file even if a malicious attack already infects it.
Replace database connection files: Hackers gain access to the configuration file that contains database connection details, such as database name, database username, password, and database prefix. All of these must be replaced. And the username must not be a standard dictionary keyword such as admin, password, or a keyword corresponding to the brand name.
Passwords for the database: Change login credentials for the database and backend for all users.
Wp-config URL: Hardcode wp-config URL and keep it unique so that the bots do not see the URL’s typical pattern, terms, or structure.
Debugging mode: Debugging mode shows the errors on the front end and saves these errors in a log file. If we restore the plugins and files at the end, we can fix these errors and make the website more secure.
Download a new copy of the WordPress core files and unzip them into a folder.
Theme recovery: If the site has a premium theme, you can access all the files you need to reapply the theme. If you are utilizing a free theme, you will need to replace the parent theme, and when that is done, you can change the child theme files one at a time: footer.php, functions.php, etc., header.php, and JavaScript.
Any file you upload new to the site should be scanned: When you re-upload, paste the files into the new directories and rename them accordingly so that no file is overwritten. That will ensure that no malicious content or code comes back while you clean up the site.
Once the site is working, will activate themes and plugins. If you desire to play it safe this time, choose a paid theme from a reliable source, and the same goes for the plugins. Choose a trusted source for the plugins. Test all plugins before using them on your website.
How to make your WordPress website secure
Disable XML RPC attacks: XML RPC connects the WordPress website to external environments such as WordPress updates and applications and mobile applications for REST API. If the website does not communicate with the external environment, we can disable XML RPC. If we keep the communication open, we might get a DDOS attack that affects your database and pingbacks and slows down your website. Hackers could also try to log in through an XML RPC connection.
How to secure your WordPress internet site from malware
While the WordPress core is perfectly safe, thanks to its developers’ excellent care, the third-party plugins and themes make this CMS a popular target of online attacks. The reason is that their code may contain security vulnerabilities that make your website vulnerable to online attacks.
And since around 43% of the Internet is based on WordPress, thousands of websites become a playground for malicious actions as soon as hackers discover a vulnerability. However, many WordPress security breaches are due to other important factors. Here are some essential security tips that will help you keep your WordPress website secure:
Minimize human error: Human error is a significant cause of security breaches in all scenarios where credentials play a role. It’s usually weak passwords (think brute force attacks), sharing sensitive information online, or simply phishing links or websites. Once your credentials are compromised, it’s only a matter of time before your website is infected with malware.
Keep your WordPress up to date: Every WordPress update includes notices about what security issues have been fixed. Hackers read these notices and then look for and target websites that still need to be updated. In short, if you are using an older version of WordPress, it means that it has known security vulnerabilities.
Avoid using outdated plugins and themes: Keeping your plugins and themes up-to-date is one of the basic requirements for your website’s security. According to ScanWP, 52% of WordPress vulnerabilities are related to plugins.
Say no to nullified plugins: A nulled plugin is a hacked premium plugin that works without a license and offers many premium features. Nulled plugins usually have significant security issues and may even contain malware.
Choose a reliable hosting provider: Unfortunately, not all hosting providers offer the required level of security to ensure that your website is protected on the server side. For this factor, we strongly recommend that you choose hosting providers that are specifically designed for WordPress.
Keep a security plugin enabled: Using a security plugin (even a free one) will permit you to monitor your security status by running regular scans, enabling a firewall for better protection, and implementing additional measures like two-factor authentication.
The importance of malware detection and removal
Malware is software created to hurt a computer system. It can be offered as viruses, worms, Trojan horses, or spyware. Despite strict security measures, WordPress websites are vulnerable to malware attacks.
There are many different ways malware can get onto your WordPress website. The most common method is malicious plugins or themes. Other ways include vulnerabilities in the core WordPress software or other software on your server.
Once the malware infects a WordPress website, the person behind the attack can do much damage – delete files, insert spam web links right into your material, and take delicate information like passwords and charge card numbers. Not just can this strike cause unnecessary downtime, but it can additionally harm your credibility and also trigger you to shed company.
Final thoughts
This guide will assist you in identifying all the types of malware you may encounter and successfully removing them from your WordPress website to ensure they are back on track.
Since WordPress is a popular platform with entrepreneurs and hackers – we predict that 50% of all websites will be powered by WordPress by 2025 – we strongly recommend putting your website’s security at the top of your priorities. Even basic security measures can protect you from most online attacks, keeping your business safe and your customers happy.
Frequently asked questions
Q: What is WordPress?
A: WordPress is a free, open-source web content management system (CMS) that enables customers to develop websites and blogs. It is among the most preferred CMSs on the Internet, with over 43% of all sites based on it.
Q: How can I keep my WordPress website secure?
A: You can take several measures to ensure your WordPress website’s security. These include using strong passwords, updating WordPress and all plugins/themes, avoiding nulled plugins, choosing a reliable hosting provider, and using a security plugin.
Instructions are essential, as they provide a clear set of steps to secure your site. That means you should always read the instructions the hosting provider and WordPress provided and ensure you understand them before starting.
Perform backups. Backups are vital for the security of your website. Maintaining a backup of all your data and also information sources is essential. You stay free from the hazard of dropping them in the case of a hack or data corruption. Regular backups of your website will help ensure that your website is constantly protected in case something unexpected happens.
Q: What are the signs of WordPress malware infection?
A: There are several signs that your WordPress website has been infected with malware. First, you may notice that your website loads slowly or displays error messages.
Secondly, you may notice new users or files that you still need to add appear on your website. Lastly, you may notice that your website is on the Google block list or blocked by visitors’ antivirus software.
If you discover these signs, you must immediately clean up your WordPress website. Ignoring a malware infection can have serious consequences, including data loss and website downtime.
Q: How does malware generally infect a WordPress website?
A: There are several ways malware can infect a WordPress website. For one, it can be introduced via a WordPress plugin or theme susceptibility.
It can additionally be posted by a hacker who gains access to your website via an insecure password or other methods.
For even more protection, check out Fix Hacked Site. This website security checker scans your site for malware, removing it automatically and protecting your site from attack.
You Might Also Enjoy
Malware Cleanup Guide: How to remove malware from a WordPress website
Tips for tightening up the security of your WordPress website account
Perform on-page optimization on your website
Malware vs Virus: Are You Protected? An Overview of the Differences and Tips on Prevention
The post How to check a WordPress website for malware and secure it? appeared first on Fix Hacked Site.
https://media.istockphoto.com/id/1357765491/vector/internet-online-web-hosting-provider-service.jpg?s=612x612&w=0&k=20&c=jzBadfeZrwek2eL5quelKdFVa8u3-F9ZS0D4unN9-H8=
https://fixhackedsite.com/how-to-check-a-wordpress-website-for-malware-and-secure-it/?utm_source=rss&utm_medium=rss&utm_campaign=how-to-check-a-wordpress-website-for-malware-and-secure-it
0 notes
Text
https://yugioh-starlight.com/archives/57537576.html
Effects of Dandy White Lion is out.
https://twitter.com/PetitAngel_/status/1654851744185348098
このカード名の効果は1ターンに1度しか使用できず、この効果を発動するターン、自分はEXデッキからモンスターを特殊召喚できない。このカードがフィールドから墓地に送られた場合に発動できる。自分フィールドに綿毛トークン(?)2体を守備表示で特殊召喚する
Google Translate:
This card name effect can only be used once per turn, and you cannot Special Summon monsters from the Extra Deck during the turn you activate this effect. Activate when this card is sent from the field to the Graveyard. Special summon 2 fluff tokens (?) to your field in defense mode.
Basically, it is Dandylion, but it is restricts to you to the Main Deck, and its effect is hard Once per turn, but also you can immediately Tribute them. So it is actually better.
Original Dandylion was created for getting out Neos as quickly as possible, but this makes me wonder if the Judai support in Age of Overlord will be Evil HERO, or Yubel focused, since those are actually Tribute Summon focused themes (yes, Evil HEROes are actually Tribute focused. Don’t believe me? Read the effects of the Main Deck Evil HEROes.) In that case, the cover theme might indeed be Z-ARC, which would then mean ZEXAL reps will be Number 96 and/or Vector.
But more realistically, this means we getting Tribute Summon/Main Deck Special Summon focused Judai support in Age of Overlord. So probably just Yubel, and co. A bit awkward, but hey. This is how Yubel Decks are supposed to work.
(And yes, the card text is Hiragana heavy.)
Edit:
https://yugioh-starlight.com/archives/57527447.html
The actual text is a bit different than the Twitter post:
このカード名の効果は1ターンに1度しか使用できず、この効果を発動するターン、自分はEXデッキからモンスターを特殊召喚できない。
①:このカードが手札・フィールドから墓地へ送られた場合に発動できる。自分フィールドに「白綿毛トークン」(植物族・風・星1・攻/守0)3体を守備表示で特殊召喚する。
Google Translate:
This card name effect can only be used once per turn, and you cannot Special Summon monsters from the Extra Deck during the turn you activate this effect.
①: Can be activated when this card is sent from the hand or field to the Graveyard. Special Summon 3 "White Fluff Tokens" (Plant-Type/Wind/Level 1/ATK 0/DEF 0) to your field in Defense Position.
It summons different Tokens than Dandylion, it summons 3 of them instead of 2, and it can be activated from hand. So it is even better.
0 notes
Text
Convincing Sponsorship proposal
Create a Convincing Sponsor Proposal.
Written Paper Icons - Download Free Vector Icons | Noun Project
Now that you’ve set your goals and made a list of potential sponsors, you can start creating your sponsor proposal. This is usually in the form of a letter or email that details what your organization does, how much funding you need, and what you plan to use it for.
There are different types of sponsor proposals. These might vary according to what you’re requesting support for, and who you’re requesting it from. Is the sponsorship for a specific event, a nonprofit organization, a church, or maybe a school? Is your targeted sponsor a big corporation, a local shop, or an individual? Being specific with your proposal according to these categories might make a difference. For more detailed information on different types of sponsorship proposal letters, check out Fundly’s great blog post on sponsorship letter templates.
There are also online services like Sponseasy, which help you create professional-looking sponsorship proposals and export them easily. They usually have customizable templates that you can use, too.
Tips to Write the Most Effective Sponsorship Proposals:
Contact personally if you can. This way, your sponsors can view you as an individual, rather than a nameless and faceless organization behind a screen. Personal communication rather than letters or emails is always preferred. It helps build more solid connections.
Explain yourself clearly. Give your mission statement and provide information about your demographic. Show them why you deserve their attention and support. Tell your story in a captivating way from the get-go. A personal story will always elicit an emotional response, which will positively influence their decisions.
Present data. The best way to give information about your organization is through actual data. Prove your worth to guarantee sponsorships. Keep in mind that too many statistics can be boring to read through, so make sure you filter them well.
Be direct with your proposal. Clearly specify the estimated amount that you will need. Avoid selling yourself too short, but also state that you will consider whatever they’re willing to offer. Don’t be afraid to push limits.
Offer fitting benefits. If all you’re offering for $20,000 is a logo featured on your website, for example, you will struggle to get funds. Determine and present benefits that will intrigue your sponsors. Be open to further suggestions and offers.
Carry On!
Let’s face it, there will probably be times when your proposals will get ignored. When that happens, don’t be afraid to follow up. But when you’re doing so, try not to suffocate your potential sponsors. Simply inform them of your organization and why you need funding again. Re-clarify your needs and your benefits offering without being overbearing.
In the case that you get a negative response, ask for feedback on why they weren’t interested. You can also try offering other ways they can help instead of monetary funds. If this doesn’t change their decision as well, simply move on to other possible supporters. Rejections are bound to happen, but there are tons of other opportunities waiting for you. Don’t be discouraged, and keep trying!
To read more about nonprofit organizations and how to reach your utmost potential, check out our pillar content where we have created an ultimate guide. You can also check out our other nonprofit articles below:
Google Nonprofit Ad Grant: How to Get $10,000?
Top 10 Nonprofit Fundraising Ideas to Generate Sustainable Revenue
Successful Fundraising Ideas for Nonprofits
To see how you can grow your nonprofit even more with an all-in-one nonprofit management software, launch your new platform today!
Share:
Facebook
Twitter
Pinterest
LinkedIn
Ceylin Guven
Ceylin Guven
Hi! As the blog manager here at Raklet, I’m in charge of writing and managing our blog posts, and I also do graphic design. When I'm not creating content for our blog, you can find me scribbling poems, binge-reading sci-fi/fantasy books, or watching Studio Ghibli movies.
On Key
Related Posts
The ULTIMATE Guide to In-Kind Donations
When you think about donations, cash always comes to mind first. There are thousands of donation buttons online for corporations
College Fundraising Ideas: Best Step-By-Step Guide
In the world we live in, college fundraising is now more important than ever. But solely handing out fliers for
Online Fundraising Tools: A Focus on Facebook 
In a world where almost everything is handled digitally, we look for ways to automate manual tasks to save ourselves
online fundraising tools
Best Nonprofit Online Fundraising Tools in 2023
Fundraising is an essential part of every nonprofit organization. But it also includes many repetitive tasks that take too much
how to make donation page
How to Make a Donation Page in 5 Steps
Nonprofits put a lot of time and effort into collecting donations. But having a donation page takes away some of
Leave a comment
Save my name, email, and website in this browser for the next time I comment.
This site uses Akismet to reduce spam. Learn how your comment data is processed.
Create your account.
It’s free for as long as you need.
Get Started Free
Start for free & upgrade only if you need. Card not required.
Raklet
Raklet is a modern cloud platform that provides plug and play solutions for contacts, messages and payments.
4347 20th Street, San Francisco CA 94114
+1(415) 649-5949
PLATFORM
Features
Integrations
API & Developers
Pricing
Explore
Affiliate Program
We’re hiring!
RESOURCES
Help Center
Case Studies
Blog
References
Reviews
Countries We Serve
Alternatives
Contact Us
Schedule Demo
SOLUTIONS
Community Engagement Software
Membership Management Software
Event Management Software
Club Management Software
Alumni Engagement Platform
Digital Membership Card
Non-Profit Fundraising Software
Association Management Software
Chamber of Commerce Software
Church Software
Political Party Software
About Us
Contact Us
Privacy Policy
Terms of Use
2022 © Raklet Inc
Our website uses cookies from third party services to improve your browsing experience. Read more about this and how you can
0 notes
Text
poweriso 94fbr
The largest majority of images on the internet are JPEGs. Virtually every camera will record photos as JPEGs, and is very much habitual cameras which is the very best they conserve you an brand. Because of poweriso Registration Key , JPEGs are often considered the "default" file type in order to. And there are a handful good good. However, there are a variety of very good - even compelling - reasons why photographers should get informed about and use other file types.
Another feature of PNG is transparent color support, means in case a website has a black background for example, the transparent part of your image will appear in white. GIF supports transparent color as well, but marriage replaced by PNG in this field.
.bmp: Represent "bitmap image file." Vast majority of users is stored as pixels, which end up being individual "dots" that go to make up a screen image on a monitor. This really is the raw form of "raster" graphics (as opposition line art or "vector" graphics). Read more about poweriso those from a later manual!
.jpg: Would mean "JPEG image file." poweriso Activation Code stands for "Joint Photographic Experts Group" is relatively of useless trivia that has no impact whatsoever on anything. Another raster format, commonly used in photographs.
When one enters a website and individuals like a movie, had that countdown clock in it because always be loading the Flash file or the positioning is just like movie- in the neighborhood . flash. Might be moving images. This is termed as a self contained Flash place.
Until.I in order to open or burn a dmg file which resides in my PC doesn't imply couldn't do it right. The file simply unknown to Your windows program. Some suggested that just rename the dmg extension to you.iso and burn it using any PC burning software on the other hand found going without shoes didn't are employed by me since my DVD that I to burn, it any double Layer DVD. So, I Googled around at this time glad I conducted. And the solution is the software called Transmac.
Also, have to want your image think about up lots of space in your page. As the rule of thumb, try and make it about 1 and 1/2 inches large. Because typically the extra space your image takes up, the larger the file will be, and much more time it is going to take your website get the image and display on your world wide web page.
As you can see from a file formats for portable ebook reader reviews I've undertaken above, it really does make a change which file formats are supported. When poweriso Registration Key are in order to buy a report reader is actually important to best to find one that supports doesn't just the most file formats but supports file formats that the e-publishing industry and not just one company actually publishes in. Should don't you'll have be costing you money.
0 notes
Text
A Comprehensive guide to selecting CutFile Templates for Gadget Skin Wrap
Starting up a skin business and wondering which cut templates to use for cutting vinyl skins. Don’t worry; we are here to guide you.
There are two main options available:
Buying mobile skin software with pre-installed cut file templates for various mobile phones
Buying individual vector cut file templates for multiple devices as per your requirement
Skin Software
The phone skin design software comes with cut file templates of various phones of different brands that are used to design custom, textured, or transparent phone skins. There are only a few software available in the market, and you can choose one per your requirements.
Vector CutFile Templates
Apart from skin design software, some companies also sell individual cut file skin templates. You can explore their digital products by visiting their website or find them simply by Google.
I have compared mobile skin design software and individual cut file templates and tried to list their major pros and cons.
I have also listed a few sources which sell vector cut file templates and tried to compare them so that you can get a clear idea about each one of them.
Comparison of vector cut file of iPhone X from different sources:
I have purchased a vector cut file template of iPhone X from different sources and compared them to check their quality. I have listed my observations below:
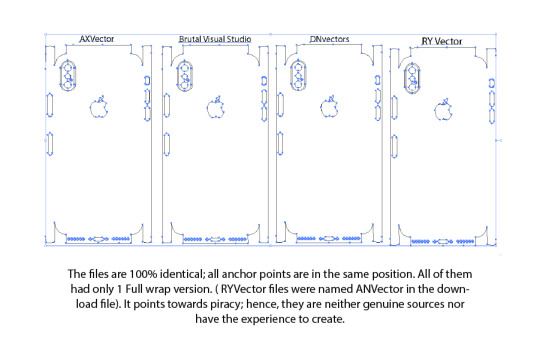
Only RoleArtDesignStudio and VecRas were unique, as depicted by the anchor points. Rest all (ANVector, Brutal Visual Studio, DNVectors, and RYVector) had the same file. The anchor points were in the same position (as shown), which seemed quite strange and pointed toward the probability of the unauthorized sale of files after purchase or the creation of files by tracing.

The file provided by SkinTemplatePro had an incomplete shape.
Major issues:
Unnecessary margin around buttons
Short/Overlap Corner Flaps
Misalignment of Speaker and Button shapes
Extra margin around the Logo
Misalignment of Front camera and sensor shapes
Conclusion
I found that VecRas offers precise vector cut files, a world-renowned and authentic brand with global dominance in creating vinyl-ready vector skin templates and Smart PSD Mockups. You will get everything you need in one shop.
As per my observation, I have listed some key features and benefits of choosing VecRas.
Vector cut files created by VecRas are much more precise than those provided in skin software as they test their files on the original devices using 3M vinyl material and two different types of cutters. They also upload skin test images, enabling them to look at precise fit skins manufactured using their vector cut templates.
They provide templates for many phones, laptops, tablets, gaming devices, audio-video devices, wearables, etc. While skin software has the majority of cut files for phones only, other device categories are usually not offered. https://vecras.com/pages/cutfiles
Their skin templates are compatible with various popular cutters/plotters, while Skin software can only be used with the hardware supplied by that particular company. Hence hardware also needs to be purchased from the same supplier.
CutFiles by VecRas are created by a team of experts with more than a decade of experience. Hence, their files are designed with a unique professional style and are highly precise, even on small holes, ports, corners, rounded shapes, etc.
They provide cut file vector templates in 5-6 different file formats (Ai, CDR, EPS, PLT, DXF, and SVG) so that they are convenient for you to use, while skin software generally offers only one format.
They also offer you the freedom to customize any cutfile per your requirement, while skin software does not provide any or little customization options.
These files allow for processing bulk orders, while there are limitations in skin software.
Additionally, their reliable support system seriously considers your requirements and works diligently to serve you. If you have any questions, want a few tips, need guidance, or wish to inquire about custom work, go ahead and contact them at [email protected] https://vecras.com/pages/contact.
Besides vector cut file templates, they also provide matching skin mockups to prepare high-quality website listing images, just like actual products. https://vecras.com/pages/smartpsds
They offer a knowledge base such as blogs and How-to videos to support the needs of their clients all over the world. https://vecras.com/blogs/knowledge-base
You also get 4K Skin Pasting Tutorials for the How-To section. https://vecras.com/collections/vinyl-skin-promotional-videos
The best part, you can check the quality for just $1 before making your decision. https://vecras.com/collections/samples
Please take your time to check the quality and services of different suppliers. This critical decision can lay a solid foundation for establishing your successful skin business.
0 notes
Text
Here is a guide to finding the best pest control services around
Pests are any living organism that is an unwanted, destructive, or nuisance, and can be a human health risk. Pests can cause serious damage to the environment and human health. There are more than 1 million known species of pests. These include rodents, insects and other arthropods, bacteria and fungi, plants, viruses, and viroids.
Pests may be found in fields and forests, as well as in homes and gardens. Pests can be controlled using various methods, including pest control products (pesticides), biological control methods, and cultural controls such as changing crop rotation or storage practices to deter pests from attacking crops.
In addition to the direct damage caused by pests to crops or livestock through consumption or transmission of diseases, biological warfare may also involve the use of vectors such as rats that have been infected with pathogens such as anthrax spores or plague bacilli.
Types of pests
When most people think of pests, they probably think of rats, mice, and roaches. But there is a whole world of pests out there that can damage your home or business. The following are some common types of pests:
Rodents — Mice, rats, and squirrels are rodents. Rodents like to chew on things, so they can cause damage to your home or business by chewing through electrical wiring and insulation. They also carry diseases such as salmonella and hantavirus.
Birds — Birds can create a lot of chaos in a building by getting into vents and dropping their feces everywhere. These droppings can get into HVAC systems and cause expensive repair bills for businesses that rely on these systems for heating and cooling needs. Bird droppings also contain bacteria that could make someone sick if ingested or touched directly by humans or pets.
Insects — Insects like bees, wasps, ants, and cockroaches can be a nuisance when they find their way into buildings through cracks in doors or windows. Some types of ants have been known to bite people while others simply make homes out of food leftovers around the house.
How to find pest control services:
You can find pest control in Waxhaw, NC by:
Checking with your local government. Many cities and counties have a list of licensed pest control companies.
Calling around to local businesses. Ask if they provide pest control services, how much they charge for the service, and if they have any recommendations for pest control services that perform well in your area.
Searching for pest control near me. You can search online for companies that offer pest control services in your area by using Google or Bing. Suppose you know what type of pest you are dealing with. In that case, you can also search for information about that particular type of insect or rodent on websites like Wikipedia and the University of Maryland Extension website (extension.umd.edu).
Ask around - Friends, family members, and neighbors may have had experience with different pest control companies in their area and can tell you which ones they liked best. Ask them if they would recommend their company or if there was another company that they would recommend instead. You might even be able to get some free advice from these people!
Check online reviews - Online reviews are usually one of the first places people turn when looking for a new service provider because there is so much information out there about each company on websites like Yelp and Google+.
Freedom Pest Services
Phone: (704) 610-1921
Address: 6201 Lowergate Drive, Waxhaw, NC, 28173
1 note
·
View note
Text
download cheat enggine dragon city 100% working J1J!
💾 ►►► DOWNLOAD FILE 🔥🔥🔥🔥🔥
Hello, I downloaded BlueStacks Dragon City, and when I change the gems should be from 5 to , so it fits me restart the game. Once it's installed, open the cheat engine on your PC. In the next screen, you'll need to select the Dragon City game and click Execute. : Dragon City Cheat Engine Dragon City Cheats, Download Icons Web Vector Color Modern Stock Vector (Royalty Free). Hello everyone! Right now we are going to tell you about How to Hack Dragon City With Cheat Engine, which is a software with which you can modify the values . 9 Like us to stay up to date with the AskMeFast community and connect with other members. Answered Unanswered. What would you like to ask? Please check and try again. This is NOT abusive. I pressed this button by accident. It is offensive or harmful. It does not contain enough information. It contains or requests illegal information. It does not make sense. Consumer Electronics. Chemistry Engineering Mathematics Physics. How to download cheat engine for dragon city but without survey??? Cheat engine for dragon city game FB.. Asked by: Bryan. Ads by Google. This site is best viewed while logged in. Top Solutions. Hello, Grrr. Please play the game fairly my friend. Cheating is prohibited in any game. Please stop i Hello Jacque, Please visit their official website to download the latest version. Add your answer. Suggested Solutions 10 What's this? Anonymous " grrr. Please stop it. Just enjoy playing fair. Was this answer helpful? Yes No. Was this comment helpful? This answer closely relates to:. We are not allowed to provide cheats here! However in order to move on in your level at dragon city you will just need to complete all the task provided to you. Anonymous "Download it on the official website Ayw gumana ng survey ehh plz pki send yung key pat Anonymous 2. Go to youtube you can look it up there most people have a download link for you. Because if you have survey its not even working i try it but it wont work. Password dragon city cheat engine v1 3 txt free download. Anonymous 1. Ok here is a password for engine 1. I need many gems and food please help me. Add Your Answer How to download cheat engine for dragon city but without survey??? Can you help us by answering one of these related questions? We need your help! Please help us improve our content by removing questions that are essentially the same and merging them into this question. Please tell us which questions below are the same as this one:. How to download cheat engine for dragon city but without survey? Sign In. Register Forgot Password. Ask Your Question Fast! Type your question here. Leader Board What's this? Time: 0. Community Experts online right now. Ask for FREE. Top Solutions Hello, Grrr. Yes No cheatercheater said: r you dumb?!!!!! Comment Reply Report. Post to Facebook Post to Twitter Subscribe me. Miss Pink. Miss Ange. Copyright askmefast.
1 note
·
View note
Text
download cheat enggine dragon city trainer C0EV+
💾 ►►► DOWNLOAD FILE 🔥🔥🔥🔥🔥
Hello, I downloaded BlueStacks Dragon City, and when I change the gems should be from 5 to , so it fits me restart the game. Once it's installed, open the cheat engine on your PC. In the next screen, you'll need to select the Dragon City game and click Execute. : Dragon City Cheat Engine Dragon City Cheats, Download Icons Web Vector Color Modern Stock Vector (Royalty Free). Hello everyone! Right now we are going to tell you about How to Hack Dragon City With Cheat Engine, which is a software with which you can modify the values . 9 Like us to stay up to date with the AskMeFast community and connect with other members. Answered Unanswered. What would you like to ask? Please check and try again. This is NOT abusive. I pressed this button by accident. It is offensive or harmful. It does not contain enough information. It contains or requests illegal information. It does not make sense. Consumer Electronics. Chemistry Engineering Mathematics Physics. How to download cheat engine for dragon city but without survey??? Cheat engine for dragon city game FB.. Asked by: Bryan. Ads by Google. This site is best viewed while logged in. Top Solutions. Hello, Grrr. Please play the game fairly my friend. Cheating is prohibited in any game. Please stop i Hello Jacque, Please visit their official website to download the latest version. Add your answer. Suggested Solutions 10 What's this? Anonymous " grrr. Please stop it. Just enjoy playing fair. Was this answer helpful? Yes No. Was this comment helpful? This answer closely relates to:. We are not allowed to provide cheats here! However in order to move on in your level at dragon city you will just need to complete all the task provided to you. Anonymous "Download it on the official website Ayw gumana ng survey ehh plz pki send yung key pat Anonymous 2. Go to youtube you can look it up there most people have a download link for you. Because if you have survey its not even working i try it but it wont work. Password dragon city cheat engine v1 3 txt free download. Anonymous 1. Ok here is a password for engine 1. I need many gems and food please help me. Add Your Answer How to download cheat engine for dragon city but without survey??? Can you help us by answering one of these related questions? We need your help! Please help us improve our content by removing questions that are essentially the same and merging them into this question. Please tell us which questions below are the same as this one:. How to download cheat engine for dragon city but without survey? Sign In. Register Forgot Password. Ask Your Question Fast! Type your question here. Leader Board What's this? Time: 0. Community Experts online right now. Ask for FREE. Top Solutions Hello, Grrr. Yes No cheatercheater said: r you dumb?!!!!! Comment Reply Report. Post to Facebook Post to Twitter Subscribe me. Miss Pink. Miss Ange. Copyright askmefast.
1 note
·
View note