#mobile hacker
Text
Person of Interest (2011-2016)
#person of interest#cyberpunk aesthetic#hacking#graphic design#surveillance#science fiction#surveillence state#hackers#cybersecurity#scifi#mobile hacker#code breaker#data manipulation#network security#infosecurity#10s#command line
66 notes
·
View notes
Text
The best Children’s Monitor app for Android and iPhone

This article will guide you through the process, discussing the why’s and how’s of tracking your child’s phone. We’ll explore paid options, ethical considerations, and more. Let’s dive in.
>> Click Here To Get Best Phone Tracker App Without Permission
Why Parents Need to Track Their Child’s Phone?
Reasons Why Parents Might Want to Track Their Child’s Phone:
Safety Concerns: Parents want to ensure their child is safe, both offline and online. Tracking can alert them to potential dangers.
Monitor Online Activities: Parents can keep an eye on the websites their child visits, the apps they use, and the people they interact with.
Prevent Cyberbullying: By tracking their child’s phone, parents can detect signs of cyberbullying and take immediate action.
Control Screen Time: Tracking can help parents manage how much time their child spends on their phone, promoting healthier habits.
Location Tracking: In case of emergencies, parents can locate their child quickly and accurately.
Benefits of Tracking Your Child’s Phone:
Peace of Mind: Knowing your child’s online activities can give you peace of mind about their safety.
Early Intervention: If a problem arises, such as cyberbullying or exposure to inappropriate content, parents can intervene early.
Promotes Responsible Use: When children know their phone usage is monitored, they’re likely to use their devices more responsibly.
Emergency Situations: In case of an emergency, having a tracking system can help locate your child quickly.
Better Communication: Discussing phone tracking can open up conversations about online safety and responsible behavior.
How to Track My Child’s Phone Without Them Knowing Method : Using a Real-Time App
HackersList: This app offers a range of tracking features, including location tracking, call logs, and access to text messages.
HIRE A MONITORING EXPERT
Top 01 Tracking Apps and Services
2. HackersList
HackersList is a popular parental control app that offers a comprehensive solution for tracking and monitoring a child’s phone activities. It’s compatible with both Android and iOS devices and operates in stealth mode, making it undetectable on the target device.
Features:
GPS Location Tracking: Allows parents to track their child’s exact location in real-time.
Call and Text Monitoring: Provides access to call logs and text messages.
Social Media Monitoring: Allows parents to monitor various social media platforms.
Pros:
Comprehensive Monitoring: Offers a wide range of monitoring features, providing a complete overview of a child’s phone activities.
Stealth Mode: Operates in stealth mode, making it undetectable on the child’s device.
User-Friendly: The app is easy to use and navigate, making it suitable for parents with little technical knowledge.
Cons:
No Free Version: HackersList doesn’t offer a free version. To access its features, a paid subscription is required.
Final Word
The safety of your child is paramount, and in today’s connected world, this extends to their online activities. Tracking your child’s phone can be a valuable tool in ensuring their safety. It allows you to monitor their online interactions, keep an eye on their whereabouts, and intervene if necessary.
However, it’s crucial to approach this with respect for your child’s privacy and autonomy. Open communication is key. Discuss your concerns, explain why you’re considering tracking their phone, and assure them that it’s about their safety.
Remember, tracking tools are just that — tools. They’re not a substitute for fostering trust, teaching responsible online behavior, and maintaining an open dialogue about the challenges of the digital world. As parents, our ultimate goal is to guide our children to become responsible, savvy digital citizens who can navigate the online world safely and confidently.
6 notes
·
View notes
Text

#hackerslist#hire a hacker#hacking#cybernetics#cybersecurity#cyberpunk 2077#cybercore#iphone#android#mobile hacker#social media
1 note
·
View note
Text
Collect Evidence of Your Unfaithful Partner by Mobile Hacker
Uncover signs of infidelity by hiring a skilled mobile hacker. Obtain discreet evidence to confront suspicions and make informed decisions.

Infidelity can be a devastating blow to any relationship, causing heartbreak and shattered trust. In such situations, it's natural to seek answers and clarity, and sometimes that means collecting evidence to confirm suspicions. With the advent of technology, particularly mobile devices, one method gaining attention is through mobile hacking. This article aims to delve into the complexities of this issue, from understanding mobile hacking to the ethical considerations surrounding it.
📌Signs of an Unfaithful Partner
Before considering extreme measures like mobile hacking, it's crucial to recognize the signs of an unfaithful partner. Here are some signs that may indicate an unfaithful partner:
Behavioral Changes: Pay attention to any sudden shifts in behavior, such as increased irritability, moodiness, or unexplained absences. Changes in routine without a valid explanation could be a red flag.
Secrecy with Devices: If your partner suddenly becomes overly protective of their phone, laptop, or other devices, it might indicate they are hiding something. They may start keeping their devices locked or constantly checking messages when they didn't before.
Unusual Communication Patterns: Notice if your partner has started communicating more frequently with someone new, especially if they seem secretive about it. They might also become defensive or evasive when questioned about their interactions.
Lack of Interest in Intimacy: A decline in physical intimacy or a sudden disinterest in being close to you could signal emotional or physical infidelity. Pay attention to any changes in affection or desire for closeness.
Increased Focus on Appearance: If your partner suddenly starts paying more attention to their appearance, such as going to the gym more often or buying new clothes, it could be a sign that they are trying to impress someone else.
Unexplained Expenses: Keep track of any unexplained expenses or withdrawals from joint accounts. If your partner is spending money on gifts, meals, or activities without a reasonable explanation, it could be a sign of infidelity.
Gut Feeling: Trust your instincts. If something feels off in your relationship, even if you can't pinpoint exactly what it is, it's important to acknowledge and address those feelings. Your intuition can be a powerful indicator of underlying issues.
📌Why mobile hack is needed
Confirm Suspicions: Mobile hacking may be needed to confirm suspicions of dishonesty or infidelity within a relationship. By accessing messages, call logs, or social media accounts, individuals can gather evidence to validate their concerns and make informed decisions about the future of the relationship.
Ensure Safety: In cases where there are concerns about safety or well-being, such as suspected abuse or criminal activity, mobile hacking may be necessary to gather evidence for protection. By monitoring communications or tracking location data, individuals can take proactive steps to ensure their safety or that of others.
Protect Personal Data: With the increasing prevalence of cyber threats and data breaches, mobile hacking may be required to protect personal data from unauthorized access. Ethical hackers or security professionals can identify vulnerabilities in systems or applications, helping individuals and organizations strengthen their cybersecurity defenses and safeguard sensitive information.
Parental Monitoring: Parents may need to use mobile hacking techniques to monitor their children's online activities and ensure their safety in the digital world. By tracking their children's communication, social media interactions, and internet browsing habits, parents can identify potential risks and intervene to protect them from harm.
Recover Lost Information: In situations where individuals have lost access to their own accounts or data due to forgotten passwords or technical issues, mobile hacking may be necessary to recover valuable information. By using ethical hacking techniques, individuals can regain access to their accounts and retrieve important data, preventing potential loss or damage.
📌How to Hire a Mobile Hacker
Hire a professional mobile hacker It is very important to keep certain things in mind. Some of the points attempted are:
Research and Vet: Start by researching reputable hacking services or professionals online. Look for reviews, testimonials, and recommendations from trusted sources to vet their credibility and reliability. Ensure they have a track record of ethical conduct and successful outcomes.
Verify Expertise: Verify the expertise and experience of the mobile hacker. Look for certifications, qualifications, or previous work that demonstrates their proficiency in mobile hacking. Ideally, they should have experience in the specific type of hacking you require, whether it's accessing devices, recovering data, or monitoring communications.
Ensure Legal Compliance: Before hiring a mobile hacker, ensure they operate within the bounds of the law. Discuss the legality of the hacking services they offer and confirm that they adhere to ethical standards and privacy regulations. Avoid engaging with hackers who engage in illegal activities or compromise personal privacy.
Communication and Transparency: Establish clear communication channels with the mobile hacker and ensure transparency throughout the hiring process. Discuss your objectives, concerns, and expectations openly, and ask any questions you may have about the hacking process. A professional hacker should be transparent about their methods, potential risks, and limitations.
Agree on Terms and Payment: Once you've selected a mobile hacker, agree on the terms of the engagement and payment arrangements. Ensure that all terms, including scope of work, timelines, and fees, are clearly outlined in a written contract or agreement. Be wary of hackers who demand full payment upfront or refuse to provide written documentation of the engagement terms.
🔯 Related: How To Find A Good Phone Hacker
📌Seeking Professional Help
If suspicions persist or the situation becomes too overwhelming to handle alone, don't hesitate to seek professional help. Relationship therapy or counseling can provide valuable support and guidance in navigating difficult emotions and decisions. Additionally, consulting with a legal expert can offer clarity on your rights and options moving forward.
📌Advantages of mobile hacks

While it's important to acknowledge the risks and ethical considerations associated with mobile hacking, some individuals may perceive certain advantages in specific contexts. However, it's crucial to emphasize that these perceived advantages do not justify or outweigh the potential consequences and ethical concerns involved. Here are some points that some individuals might consider advantages of mobile hacks:
Gathering Evidence: In situations where there are genuine concerns about safety or well-being, such as cases of suspected abuse or criminal activity, accessing information through mobile hacking could potentially provide evidence to protect oneself or others.
Parental Control: Some parents may use mobile hacking as a means of monitoring their children's online activities to ensure their safety and well-being. This can include tracking their whereabouts, monitoring their communication with strangers, and safeguarding them from potential online threats.
Security Testing: Ethical hackers or security professionals may use mobile hacking techniques to identify vulnerabilities in systems or applications. By uncovering weaknesses, they can help organizations strengthen their cybersecurity measures and protect against malicious attacks.
Data Recovery: In instances where individuals have lost access to their own accounts or data due to forgotten passwords or technical issues, mobile hacking might be seen as a last resort for recovering valuable information.
Awareness and Education: Understanding how mobile hacking works and its potential consequences can raise awareness about digital security among individuals and organizations. This knowledge can empower people to take proactive measures to protect their personal information and prevent unauthorized access.
📌Final Touch
In conclusion, dealing with suspicions of infidelity is a challenging and emotionally taxing experience. While mobile hacking may seem like a solution, it's essential to consider the ethical and legal implications carefully. Open communication, trust, and respect are the foundation of any healthy relationship, and maintaining these values should always be prioritized.
#mobilehacking#mobile hacker#hackerslistco#hackerslist#cybersecurity#hacking#hackers#hacker#us hackers#phone spy
0 notes
Text
Hire Mobile Hackers to Hack Your Loved One's Mobile
Are you concerned about the safety and well-being of your loved ones? In today's digital age, where smartphones have become an integral part of our lives, ensuring the security of those we care about is more important than ever. If you find yourself in a situation where you need to access someone's mobile phone for legitimate reasons, hiring a professional mobile hacker could be the solution you're looking for.

The Best Ways to Hire a Mobile Hacker for a Mobile Hack
When it comes to hiring a hacker for a mobile hack, it's essential to proceed with caution and diligence. Here are some steps you can take to ensure you find a reputable and reliable service provider:
Research reputable hacking services: Start by researching reputable hacking services that specialize in mobile phone hacking. Look for providers with a track record of delivering quality results and maintaining confidentiality.
Check reviews and testimonials: Before making a decision, take the time to read reviews and testimonials from previous clients. This will give you insight into the experiences of others and help you gauge the credibility of the service provider.
Verify the legitimacy of the service provider: Ensure that the hacking service you choose operates within the bounds of the law and adheres to ethical standards. Avoid engaging with providers who engage in illegal or unethical practices.
Discuss pricing and payment methods: Before proceeding with the hacking process, discuss pricing and payment methods with the service provider. Make sure you understand the cost involved and are comfortable with the payment terms.
Ensure confidentiality and security: Choose a hacking service that prioritizes confidentiality and security. Your privacy should be paramount, and the service provider should take measures to safeguard your personal information.
Related Blog: Hire Professional Phone Hackers
Most Mobile Phone Hacking Services Offer a Range of Features
Mobile phone hacking services offer a wide range of features designed to meet various needs and requirements. Some of the most common features include:
Remote access to target device: Hacking services can provide remote access to the target device, allowing you to monitor activity discreetly.
Social media monitoring: Keep track of social media activity, including messages, posts, and interactions on platforms like Facebook, Instagram, and WhatsApp.
Call and message tracking: Monitor incoming and outgoing calls and text messages, including timestamps and contact information.
GPS tracking: Track the location of the target device in real-time, enabling you to keep tabs on the whereabouts of your loved ones.
Data retrieval and recovery: Recover deleted data such as photos, videos, and messages, providing valuable insights into the target user's behavior.
How Can Mobile Phone Hacking Services Help You Keep Your Loved Ones Safe?
The safety and well-being of your loved ones are paramount, and mobile phone hacking services can provide invaluable assistance in this regard. Here's how:
Monitoring children's online activity: With children spending more time online, monitoring their digital footprint is essential to protect them from online threats such as cyberbullying and grooming.
Protecting against cyberbullying and online predators: Hacking services can help identify and address instances of cyberbullying and protect vulnerable individuals from online predators.
Ensuring the fidelity of a partner: If you suspect infidelity in a relationship, mobile phone hacking can provide insights into your partner's communication and behavior, helping you make informed decisions about the future of the relationship.
Recovering lost or stolen devices: In the event of a lost or stolen device, hacking services can help track and recover the device, as well as retrieve any valuable data stored on it.
Preventing data breaches and identity theft: By monitoring for suspicious activity and vulnerabilities, mobile phone hacking services can help prevent data breaches and identity theft, safeguarding sensitive information from unauthorized access.
Risks and Ethical Considerations
While hiring a mobile hacker can be tempting, it's essential to consider the risks and ethical implications involved:
Legal consequences of hacking without consent: Hacking into someone's mobile phone without their consent is illegal and can result in severe legal consequences, including fines and imprisonment.
Ethical implications of invading privacy: Invading someone's privacy without their knowledge or consent is a violation of their rights and can have serious repercussions for your relationship with them.
Alternatives to hacking for resolving trust issues: Before resorting to hacking, consider alternative methods for addressing trust issues and concerns in your relationships, such as open communication and counseling.
Conclusion:
In conclusion, mobile hacking services offer various benefits for safeguarding your loved ones in today's digital world. Moreover, by engaging a reputable and ethical hacker, you can acquire valuable insights into their online behavior, thus enabling you to shield them from potential threats and vulnerabilities. However, it's crucial to approach mobile hacking with caution and consideration for legal and ethical boundaries. Ultimately, the decision to hire a mobile hacker should be made thoughtfully, taking into account the best interests of all parties involved.
Pros & Cons:
Pros:
Provides access to valuable information for safeguarding loved ones
Offers peace of mind in knowing the whereabouts and activities of family members
Assists in recovering lost or stolen devices and data
Helps address trust issues and concerns in relationships
Can prevent potential threats such as cyberbullying, online predators, and data breaches
Cons:
Legal and ethical implications of invading someone's privacy without consent
Risk of damaging relationships and trust by resorting to hacking
Possibility of facing legal consequences, including fines and imprisonment
Potential for misuse of hacked information or breach of confidentiality
Availability of alternative methods for addressing trust issues and concerns
FAQs:
1. Is it legal to hire a mobile hacker?
Hiring a mobile hacker without the consent of the target individual is illegal and can result in severe legal consequences.
2. How can I ensure the confidentiality of my information when hiring a mobile hacker?
Choose a reputable hacking service that prioritizes confidentiality and security, and carefully review their privacy policies and measures.
3. What are the alternatives to hiring a mobile hacker for monitoring loved ones' activities?
Alternative methods for monitoring loved ones' activities include open communication, setting boundaries, and seeking professional counseling if needed.
4. What should I do if I suspect someone is hacking my mobile phone?
If you suspect unauthorized access to your mobile phone. Act swiftly to secure your device, update passwords, and inform the relevant authorities.
5. Are there any legitimate reasons for hiring a mobile hacker?
Legitimate reasons for hiring a mobile hacker include device recovery, relationship trust concerns, and defense against online threats like cyberbullying.
0 notes
Text




wacker fursona [scalesona??] real [he's a velociraptor !]
furry merc doodles ft @sicc-nasti 's horse courier and @pinkpegacorn 's cat jack [:
#ignore that i forgot quinces stubble in the last one i added it later but im on mobile and only have this version#anyways i found out that furries are like. unreasonably fun and easier to draw#this is awesome#art tag#my ocs#people's ocs#hacker#furry
42 notes
·
View notes
Text
Building Your Own Cyberdeck:
What do you do when you have extra time between a job and your next? How about building your own Cyberdeck? Check this article out for tips on building your own!
The Ultimate Hacker Project
For aspiring cybersecurity professionals, cyberpunk enthusiasts, hardware hackers, and circuit benders, one of the best hands-on projects you can take on is building your own cyberdeck. Despite overwhelming schedules full of training programs, full time work weeks, sometimes limited funds, and the endless possibilities of hardware combinations, many fans of the…

View On WordPress
#Cyber#Cyber Security#cyberdeck#cyberpunk#Cybersecurity Specialist#Ethical Hacking#hack#hacker#infosec#IT#IT professional#mobile#mobile computer#Pentesting#programming#project
13 notes
·
View notes
Text
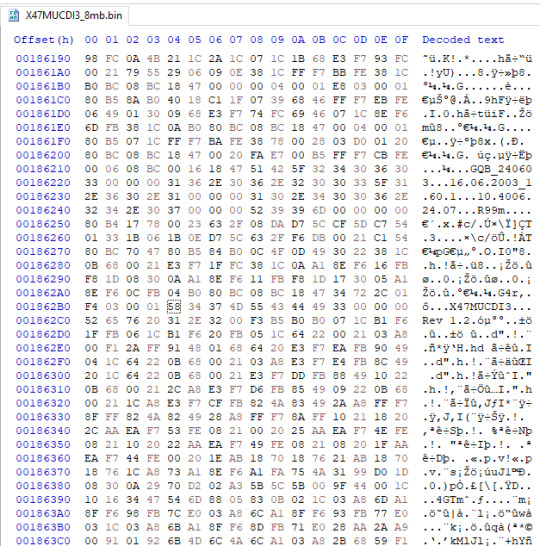
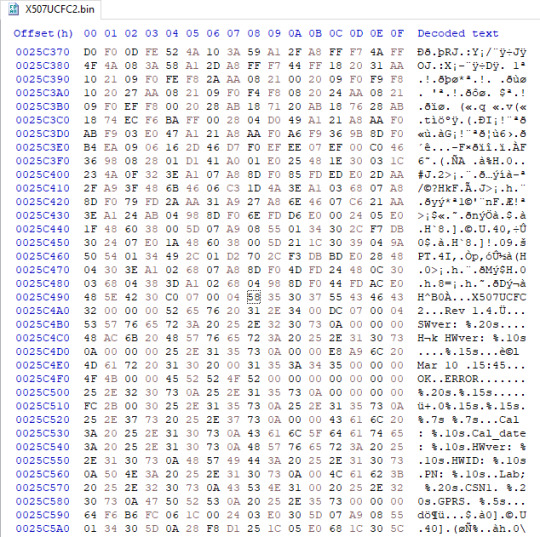


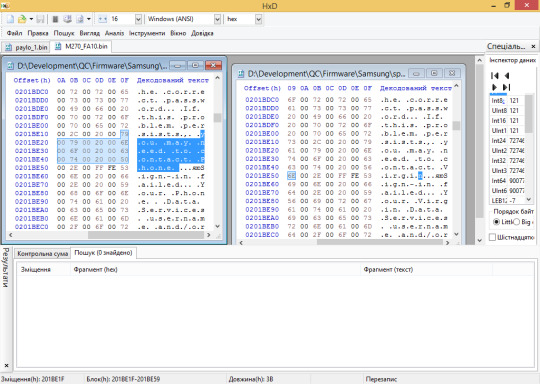
Samsung SGH-X427m and X507 dumped, plus a modified SPH-M270 firmware shipping on a prepaid carrier device..?
I know posting has been slow, but rest assured phone preservation has shown no signs of slowing down!
Some new firmware dumps as of late:
Samsung SGH-X427m, version X47MUCDI3 (incomplete; 8 of 16MB)
Samsung SGH-X507, version X507UCFC2. A previously undumped model!
Samsung SPH-M270, version FA10 on Virgin Mobile. Read on for the story of the previous FA10 dump…
The previous Samsung SPH-M270 dump was done on an unsuspecting device with a Q Link Wireless sticker on it, and appeared to be based on an existing Virgin Mobile firmware, itself still having some Sprint remains.
It wasn't put into question until the phone in question had much less restrictions compared to any Virgin Mobile feature phone, including a working Qualcomm Diagnostic port as well as working test dial codes (such as the ##2739# BREW code).
When known BREW contributor kraze1984 picked up his own M270, he noted that none of the dial codes which worked on the Q Link device worked on his, and that it only allowed for an MTP connection when plugged into a PC.
One JTAG dump later, and it was found that every single mention of Virgin Mobile was replaced with "Phone", resulting in the phrase "You may need to contact Phone" being found on the modified firmware.
It is yet to be known who made the modifications to the M270 firmware for Q Link Wireless, or why they even bothered to do such…
Last but certainly not least, thank you to MC4f for the recent donations and krzbrew for dumping the stock SPH-M270! I hope to be able to share info on a very interesting reference device soon…
#digital preservation#flip phone#samsung#mobile phone#sprint#virgin mobile#q link wireless#unknown hacker who modded a cheap flip phone's firmware where are you
9 notes
·
View notes
Text
Yooo i did it!! Had to write the text on mobile and then post from browser because my keyboard is broken and it would have been hard tagging the stuff without using S and A
#i ramble#hacker man#!!!!#i hate tunglr mobile all my homies hate tunglr mobile#i say as i never use the browser version#this just makes everything more complicated
17 notes
·
View notes
Text
Times leche has been locked out of his apartment: 4
Times leche has been locked out of his apartment and therefor his job cause the keys are on the same ring: 2
#ooc. » .001 ✦#mobile mode#hacker voice: I’m back in#you know I’m gonna just update this to laugh at myself
13 notes
·
View notes
Text
[every day the urge to give lonnie a leverage au grows...]
#[pspspsps leverage fans u know your muses wanna mentor an nb anti-establishment anarchist catgirl hacker....]#[they can fit so much child figure energy into them]#[like the opposite of someone who is a parent figure to young characters; theyre a child figure to adultier characters]#{ooc}#{mobile post}
2 notes
·
View notes
Text
How To Increase Your Photo Size In Mobile..! | @BigTvTechMan
youtube
#snapeditapp#snap#editing#bigtvtechman#photoediting#apps#whatsapp#newfeature#chandrayaan3#gaganyaan#operatingsystemmaya#indiaoperatingsystem#whatsappredtick#mobile#photosize#hackers#gmailnotrecovery#hacking#Youtube
2 notes
·
View notes
Text
Weekly output: applied AI, open innovation, Mastodon updates, AI equity, 1Password, Signal, Eve Air Mobility, travel tech, travel tips
After getting back from Brazil early Saturday morning, I’ve napped more than usual but have also spoken at an event in D.C., gotten in some gardening, and enjoyed a shorter-than-usual bike ride.
5/1/2023: Companies adopting AI need to move slowly and not break things, Fast Company
I wrote about how two companies I’ve covered elsewhere recently–the satellite-imagery firm Planet and the…

View On WordPress
#1Password#AI#air taxi#Bluesky#Brasil#Brazil#Eve Air Mobility#eVTOL#frequent flyer#FTU#FTU DC#Intercom#Mastodon#miles and points#Planet#Rio de Janeiro#Signal#travel hackers#Web Summit#Web Summit Rio
2 notes
·
View notes
Text

3 notes
·
View notes
Text
I just realized I missed Hacker's birthday omg.
2 notes
·
View notes
Text
गूगल के यह फीचर्स हैकर्स और वायरस से करते हैं आपके एंड्रोयड फोन की सुरक्षा
गूगल के यह फीचर्स हैकर्स और वायरस से करते हैं आपके एंड्रोयड फोन की सुरक्षा
New Delhi. Today mobile phone is one of the most important necessities of our life. It has become an important part of our life. It would not be wrong to say that our mobile knows everything about us. In such a situation, it is our responsibility to protect it. How secure or unsafe our Android phone or tablet is depends on how we use it?
According to Gadgets Now, Google has installed several…
View On WordPress
#android app#Android phone#android phone app#android phone phone safe from hackers#android security#android security features#Cyber Crime#features of android phone#hackers#hackers and viruses#mobile hackers#mobile safety#mobile Security#Protection from hackers and viruses
3 notes
·
View notes