#cyberlaw
Text
#cyberlaw#DataMining#C#python#IDE#Git#BareRepository#DBMS#Abstraction#CloudServiceModels#CloudServiceProviderCompanies#CloudComputing#ComputerScience#java#code#pythonprojects#pythonprogramming#development#gaming#webdevelopment#pythondeveloper#html#codinglife#coding#programming#meta#javascript#javaprogramming#javadeveloper#web3
2 notes
·
View notes
Text
youtube
#youtube#news#NationalSecurity#CivilLiberties#DefenseOfficials#CyberCommand#LegalConference#USMilitary#CyberSecurity#Government#PrivacyRights#CyberWarfare#SecurityConference#CyberThreats#CyberLaw#InformationSecurity#DataProtection#NationalDefense#CyberAttacks#CyberPolicy#LawEnforcement#TechnologyGovernance
0 notes
Link
https://bit.ly/46ZaTYc - 🌐 Microsoft, in collaboration with Arkose Labs, targets the primary seller of fraudulent Microsoft accounts, Storm-1152, sending a clear message against cybercrime. These accounts are used for phishing, identity theft, and DDoS attacks. Microsoft's efforts aim to protect customers and deter criminal activities by disrupting the cybercrime-as-a-service ecosystem. #Cybersecurity #MicrosoftSecurity #OnlineFraudPrevention 🔐 Storm-1152 is responsible for creating around 750 million fake Microsoft accounts, generating millions in illicit revenue. Their websites and social media pages offer tools to bypass identity verification, facilitating cybercriminal activities. Microsoft's action not only protects their own customers but also those of other technology platforms. #CyberCrime #DigitalSecurity #IdentityTheft 🕵️ Microsoft's Threat Intelligence has linked multiple ransomware and data theft groups to Storm-1152 accounts. These include Octo Tempest and other ransomware threat actors like Storm-0252 and Storm-0455, highlighting the widespread impact of Storm-1152's activities. #Ransomware #DataProtection #CyberThreatIntelligence ⚖️ Microsoft's recent legal action resulted in the seizure of U.S.-based infrastructure and the takedown of websites used by Storm-1152. This disrupts not only fraudulent Microsoft account operations but also services affecting other technology platforms. #LegalAction #CyberLaw #TechJustice 🛡️ Microsoft and Arkose Labs have implemented a next-generation CAPTCHA defense solution to ensure users opening Microsoft accounts are human. This initiative is part of Microsoft's commitment to providing a safe digital experience. #CAPTCHA #UserVerification #DigitalSafety 🧑💻 The individuals behind Storm-1152, identified as Duong Dinh Tu, Linh Van Nguyễn, and Tai Van Nguyen from Vietnam, are now known. Microsoft's comprehensive investigation included detection, telemetry, and undercover purchases. #CyberInvestigation #ThreatIdentification #CyberSecurityAwareness 🚔 Microsoft's submission of a criminal referral to U.S. law enforcement reflects their ongoing commitment to combating cybercrime. This action is part of a broader strategy targeting the tools used by cybercriminals, emphasizing the importance of industry collaboration in fighting cybercrime.
#Cybersecurity#MicrosoftSecurity#OnlineFraudPrevention#CyberCrime#DigitalSecurity#IdentityTheft#Ransomware#DataProtection#CyberThreatIntelligence#LegalAction#CyberLaw#TechJustice#CAPTCHA#UserVerification#DigitalSafety#CyberInvestigation#ThreatIdentification#CyberSecurityAwareness#LawEnforcementPartnership#CybercrimePrevention#PublicPrivateCollaboration#criminalactivities#socialmedia#microsoft#ddosattack#identityverification#technology#labs#seller#storms
0 notes
Text
Genie in a Bottle
Will be good if we can sue an oil lamp, or a genie and see what happens.
0 notes
Text
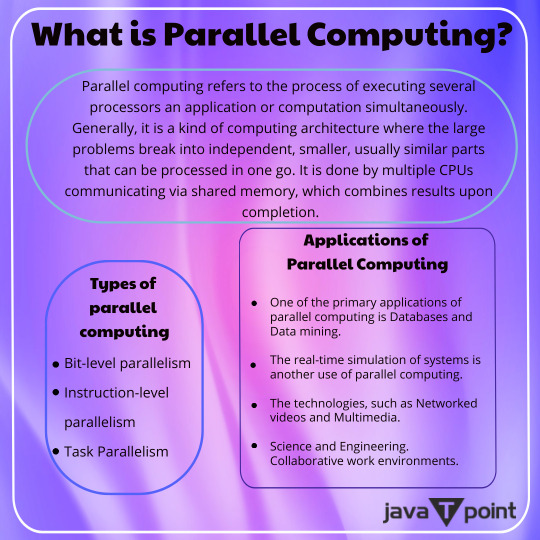
Introduction and the Need for Cyber Law
Abstract:
This comprehensive article explores the realm of cyber law, shedding light on its historical development, foundations, and the imperative need for its existence in the digital age. It delves into the intricate aspects of cybercrimes, their impact on society, and the legal framework necessary to combat them. Further, it scrutinizes the legislative and international dimensions of cyber law, emphasizing the significance of data protection, privacy, cybersecurity, e-commerce, intellectual property, digital governance, and emerging technologies. The article concludes by examining the challenges and trends in cyber law and envisaging its future directions.
Synopsis:
Cyber law is an evolving branch of legal jurisprudence that addresses the legal issues arising from the use of cyberspace and the internet. This article offers a comprehensive exploration of the subject matter, beginning with the historical development of cyber law. It then delves into the foundations of cyber law and elucidates the compelling need for its existence in the digital era. The article discusses the various forms of cybercrimes, their impact on individuals and society, and the critical role of cyber law in combating them. The legislative framework governing cyber law is meticulously examined, covering aspects such as data protection, privacy, and cybersecurity. It also explores the intersection of e-commerce and cyber law, emphasizing the legal aspects of online transactions. The article elucidates the importance of intellectual property rights in cyberspace and the legal measures in place to protect them. Digital governance and cyber sovereignty are discussed in the context of governing and regulating the internet. The article then analyses emerging technologies, their challenges, and opportunities, and how they intersect with cyber law. International perspectives on cyber law are highlighted, emphasizing the need for global cooperation in addressing cybercrimes and legal issues in cyberspace. The article concludes by assessing the challenges and emerging trends in the field of cyber law and speculates on its future prospects and directions.
Historical Development of Cyber Law
The emergence of cyber law can be traced back to the advent of the internet and the proliferation of digital technologies. It has evolved in response to the changing landscape of cyberspace. Key milestones in the historical development of cyber law include:
1970s and 1980s: The foundation of cyber law was laid during this period when computer technology began to advance. The first computer-related laws primarily focused on computer crimes and data protection.
1990s: The growth of the internet led to the need for legal regulations in cyberspace. The United States enacted the Computer Fraud and Abuse Act (CFAA) in 1986, and the World Intellectual Property Organization (WIPO) treaties on copyright and trademark laws were established.
2000s: The emergence of e-commerce and the need for online consumer protection led to the development of laws and regulations related to online transactions. The Digital Millennium Copyright Act (DMCA) was enacted in 1998.
2010s and Beyond: The 2010s witnessed the proliferation of social media, cloud computing, and the Internet of Things (IoT). New cyber threats and challenges prompted governments to strengthen cybersecurity measures and enact data protection laws, such as the European Union's General Data Protection Regulation (GDPR).
Read this full article in detail Introduction and the Need for Cyber Law
For more article visit here Parionstr
#cybersecurity#cyberlaw#law#cybersecuritynews#india#trend#news#NewsUpdate#lawyer#parionstr#unitedstate
1 note
·
View note
Photo

How to file a complaint in regards to violation of Cyber Laws?
Have a look on the process of Cyber Laws Complaints.For further reading, refer to this article.
#CyberLaw#CyberCrime#OnlineTheft#Cyberbullying#Hacking#Phishing#Complaint#violation#Legal#Law#CyberSecurity#CyberAwareness
0 notes
Text
happy valentines day!!
to celebrate, my first cyberlaw🖥⚖️ post <3
i was gonna post it anyway, i just so happened to finish it today :3c
☆ Taglist!!!.☆
@styxshipz @e-likes-bones @sunflawyer
18 notes
·
View notes
Text
Want to be Computer Programmer , Java Developer , Web Developer etc. Enroll in Master in Information Technology Course For more details speak to our education counselor at 8055 330 550 or visit https://tinyurl.com/3mh5d269 Student Review- Mr. Arshdeep Singh Pannu from Pinjore | Master in Information Technology
#cloudcomputing#javatechnologies#datastructures#digitalmarketing#webtectechnologies#cyberlaws#machinelearning#iot#bigdataanalytics#rdbms#oops#operatingsystem#softwaretesting#softwareengineering
0 notes
Text
Google falsely told the police that a father was a molesting his son

[Correction: An earlier draft of this story misstated a technical detail; Mark didn’t email his photo to his doctor; rather, he took the photo with his phone and the image was automatically synched to his Google Photos account, triggering a scan]
Mark’s toddler had a painful, swollen penis. His wife contacted their doctor, whose nurse asked Mark to send him a picture of the toddler’s penis, because the pandemic was raging and the doctor wasn’t seeing patients in person. Mark’s phone synched the photo to his Google Photos account, and Google’s scanning tools automatically detected the picture of a child’s penis and turned Mark into the SFPD, accusing him of molesting his son.
https://www.nytimes.com/2022/08/21/technology/google-surveillance-toddler-photo.html
Mark and his wife took several pictures of their son’s penis, including one that contained Mark’s hand. The child had a bacterial infection, which was quickly alleviated with antibiotics that the doctor prescribed via telemedicine.
Google refused to listen to Mark’s explanation. Instead, they terminated his account, seizing more than a decade’s worth of personal and business email, cloud files, and calendar entries. He lost all the family photos he’d synched with Google Photos (including all the photos of his toddler from birth, on). He even lost his mobile plan, because he’s a Google Fi user. He lost access to Google Authenticator and couldn’t sign into any of his other online accounts to tell them that he had a new, non-Gmail email address.
Mark received an envelope from the SFPD telling him that Google had contacted the police department, accusing him of producing child sexual abuse material (CSAM), and that the company had secretly given the police full access to all of his files and data, including his location and search history, as well as all his photos and videos.
The reason the police had to mail him all this stuff? Google had shut down his phone number and so they couldn’t reach him.
To SFPD’s credit, they’d figured out what was going on and decided Mark wasn’t a child molester. To Google’s shame, they continue to hold all his data hostage — including his address book with the contact info for everyone he is personally or professionally connected to, denying him access to it.
Google says they won’t give Mark his account back because they found another “problematic” image in his files: “a young child lying in bed with an unclothed woman.” Mark doesn’t know which picture they mean (he no longer has access to any of his photos), but he thinks it was probably an intimate photo he captured of his son and wife together in bed one morning (“If only we slept with pajamas on, this all could have been avoided.”).
Writing for the New York Times, Kashimir Hill discusses another, similar case, involving a Houston dad called Cassio, whose doctor asked him to send in photos of his child’s genitals for diagnostic purposes. Like Mark, Cassio was cleared by police, and, like Mark, Cassio is locked out of his Gmail account, along with all the services associated with it.
Hill spoke with my EFF colleague Jon Callas, who criticized Google, saying that private family photos should be a “private sphere” and not subject to routine scanning by algorithms or review by moderators. Google claims that they only scan your photos when you take an “affirmative action” related to them, but this includes automatically uploading your photos to Google Photos, which is the default behavior on Android devices.
Also cited in the article is Kate Klonick, a cyberlaw prof and expert on content moderation. Klonick pointed out that this was “doubly dangerous in that it also results in someone being reported to law enforcement,” suggesting that this could have resulted in a loss of custody if the police had been a little less measured.
Klonick criticized Google for the lack of a “robust process” for handling this kind of automated filter error. Hill describes the “AI” tools Google uses to automatically flag potential CSAM. As is so often the case with automated filtering tools, the flagging takes place in a nanosecond, while the process for questioning its judgment takes months or years, or forever.
Last summer, I called Google and its Big Tech competitors “utilities governed like empires.” The companies deliberately pursued a strategy of becoming indispensable to us, declaring mission statements like “organize all the world’s information” and backing them up with vertical stacks of products designed to capture your whole digital life.
https://www.eff.org/deeplinks/2021/08/utilities-governed-empires
That is, the tech giants set out to become utilities, as important to your life as your electricity and water — and they succeeded. However, they continue to behave as though they are simply another business, whose commercial imperatives — including the arbitrary cancellation of your services without appeal — are private matters.
Some people say this means we should just turn these companies into actual utilities, but I think that’s the wrong impulse. The problem with (say) Facebook, isn’t merely that Zuck is monumentally unqualified to be the unaccountable self-appointed dictator of three billion peoples’ digital lives. The problem is that no one should have that job. We should abolish that job.
Which is why I’m so interested in interoperability — including a mix of state-imposed interop obligations and protecting interoperators’ self-help measures like reverse-engineering, scraping and bots.
https://www.eff.org/wp/interoperability-and-privacy
That is a path to pluralizing power over the necessities of our lives — use the power of the state to set limits on the conduct of online platforms (say, by passing strong privacy laws with a private right of action), which makes sure that no matter which choice a user makes, they won’t be exploited by online companies. Then use the power of the state to safeguard interoperability, so that users who don’t like the way an online host uses its discretion can easily leave, without surrendering their data or their social connections:
https://www.eff.org/deeplinks/2021/08/facebooks-secret-war-switching-costs
Rather than entrusting the US government — including its policing and espionage arms — to run our digital lives, and the digital lives of non-Americans around the world whom the US government explicitly disclaims any duty to, we can ask the government to do a much narrower job. We can ask them to prevent companies from harming us, and we can ask them to force companies not to take our data and social connections hostage. That way, we don’t have to ask the government — which might be run by e.g. Ron Desantis in a couple years — to decide which conversations are lawful to have:
https://www.eff.org/deeplinks/2021/07/right-or-left-you-should-be-worried-about-big-tech-censorship
Instead, we can create our own, community run and community managed online spaces and services.
Image:
Cryteria (modified)
https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0:
https://creativecommons.org/licenses/by/3.0/deed.en
[Image ID: A desk with an open laptop on it. On the laptop's screen is a doctor's torso and folded arms. In the top right corner is a CCTV camera labelled with the Gmail logo. The camera's lens has been replaced with the staring red eye of HAL9000 from 2001: A Space Odyssey.]
3K notes
·
View notes
Text
USA TODAY was provided copies of the emailed threats, which were also sent to Alejandra Caraballo, a clinical instructor at the Harvard Law School Cyberlaw Clinic who writes frequently about the issues.
One emailed threat was apparently sent to Anne Perry, a state representative. Perry, a Democrat who represents a small district in far-northeastern Maine, is the main sponsor of LD227, a bill introduced this week that would protect doctors in the state who provide gender affirming care to patients from states that have laws hostile to such treatment.
The threat also apparently named Sen. Donna Bailey, Perry’s co-sponsor on the bill.
Earlier this week, Perry and Bailey were targeted in a series of posts on X, formerly known as Twitter, by Libs of TikTok. The tweets listed both lawmakers’ email addresses.
In January, the Maine State House was evacuated for a bomb threat on the first day of the legislative session. At the time, the legislature was considering another bill on transgender care. That bill died in committee later the same month.
Calls and emails to Perry, the Maine State Police, Maine Capitol Police and FBI were not immediately returned.
112 notes
·
View notes
Text

#opticalTechnology#cyberlaw#DataMining#C#python#IDE#Git#BareRepository#DBMS#Abstraction#CloudServiceModels#CloudServiceProviderCompanies#CloudComputing#ComputerScience#java#code#pythonprojects#pythonprogramming#development#gaming#webdevelopment#pythondeveloper
1 note
·
View note
Text
youtube
#youtube#usmilitary#news#NationalSecurity#CivilLiberties#DefenseOfficials#CyberCommand#LegalConference#USMilitary#CyberSecurity#Government#PrivacyRights#CyberWarfare#SecurityConference#CyberThreats#CyberLaw#InformationSecurity#DataProtection#NationalDefense#CyberAttacks#CyberPolicy#LawEnforcement#TechnologyGovernance
0 notes
Link
https://bit.ly/3FIB1eZ - 🛂 Two Russian nationals, Aleksandr Derebenetc and Kirill Shipulin, have been indicted for conspiring to hack the taxi dispatch system at JFK Airport, New York. Alongside, two American hackers, Daniel Abayev and Peter Leyman, have pleaded guilty to related charges. The scheme involved manipulating the dispatch system to prioritize certain taxis for payment, affecting taxi line order and operations. #CyberSecurity #JFKAirport ⚖️ The indictment highlights a grave concern for infrastructure systems' vulnerability to cyber hacking. U.S. Attorney Damian Williams emphasized the commitment to prosecuting criminal hackers, whether domestic or international. The Port Authority Inspector General John Gay acknowledged the impact of the scheme on hard-working taxi drivers and affirmed the authority's dedication to safe and equitable operations. #LegalNews #InfrastructureProtection 🔒 The hacking activities spanned from September 2019 to September 2021, with various attempts to infiltrate the dispatch system including using malware and unauthorized Wi-Fi access. Messages exchanged among the conspirators reveal their explicit intentions to disrupt the taxi dispatch system. #Cybercrime #Hacking 🚖 The successful hacks allowed as many as 1,000 fraudulently expedited taxi trips a day, with the American hackers charging drivers to skip the line. This large-scale disruption significantly affected the regular taxi operations at JFK. #Transportation #TaxiIndustry 📜 Derebenetc and Shipulin face two counts of conspiracy to commit computer intrusion, with a maximum sentence of 10 years each. Abayev and Leyman, having pleaded guilty, face a maximum of five years in prison. Sentencing dates have been scheduled for early 2024. The case highlights ongoing efforts to address and mitigate cyber threats to critical infrastructure. #LegalProceedings #CyberLaw Note: The defendants are presumed innocent until proven guilty. The case is handled by the Complex Frauds and Cybercrime Unit, demonstrating the intricate nature of cybercrimes in today's interconnected world.
#CyberSecurity#JFKAirport#LegalNews#InfrastructureProtection#Cybercrime#Hacking#Transportation#TaxiIndustry#LegalProceedings#CyberLaw#InnocentUntilProvenGuilty#CyberJustice
0 notes
Text
Data Breach and My Mum's Broomstick
If you think data breach is important but boring, wait till you read on how I experienced this from childhood through my mum’s broomstick and my grandma’s dentures 😯
#economy#cyberlaw#cybercrime#gdpr compliance#dataprotection#databreach#united kingdom#contractnegotiations#businessmanagement
0 notes
Text
Exploring Cyber Law in India: An In-Depth Analysis
Abstract:
This comprehensive article delves into the world of cyber law in India, tracing its historical development and discussing its foundational principles. It explores the pressing need for cyber law in the digital age, highlighting the impact of cybercrimes and the importance of cybersecurity and data protection. The article delves into the legislative framework governing cyber law in India, covering key aspects such as data protection, e-commerce, intellectual property rights, and digital governance. It also discusses emerging technologies, international perspectives, challenges, and emerging trends in cyber law. Finally, it presents future prospects, challenges, and directions for cyber law in India.
Synopsis:
Cyber law has become an integral part of modern legal systems worldwide. In India, the need for comprehensive cyber legislation has grown exponentially with the rapid expansion of the digital landscape. This article provides a detailed analysis of the historical development of cyber law in India and its foundational principles. It delves into the critical need for cyber law, exploring the profound impact of cybercrimes and the imperative of cybersecurity and data protection. The legislative framework governing cyber law in India, including data protection, e-commerce, intellectual property rights, and digital governance, is extensively covered. Additionally, the article discusses the complex domain of emerging technologies, international perspectives, challenges, and emerging trends in cyber law. It concludes by presenting future prospects, challenges, and directions for the evolution of cyber law in India.
Historical Development of Cyber Law in India
The history of cyber law in India can be traced back to the early 2000s when the internet began to gain prominence in the country. Key milestones in the development of cyber law include:
Information Technology Act, 2000: The Information Technology Act, 2000 (IT Act), served as a foundational piece of legislation in India's cyber law landscape. It provided legal recognition to electronic transactions, introduced digital signatures, and established legal remedies for cybercrimes.
Amendments to the IT Act: Subsequent amendments to the IT Act, such as those in 2008 and 2009, expanded the scope of cybercrimes and penalties. These amendments were critical in addressing emerging challenges in cyberspace.
National Cyber Security Policy, 2013: The National Cyber Security Policy aimed to protect critical information infrastructure, promote cybersecurity awareness, and strengthen the regulatory framework for cyberspace.
Data Protection Framework: The General Data Protection Regulation (GDPR) in the European Union and the Personal Data Protection Bill, 2019, in India signalled a shift towards stronger data protection and privacy regulations.
Recent Cybersecurity Initiatives: India has undertaken various cybersecurity initiatives, including the launch of the National Cyber Coordination Centre (NCCC) and the development of the Cyber Swachhta Kendra (Botnet Cleaning and Malware Analysis Centre).
Read this full article in detail "Exploring Cyber Law in India: An In-Depth Analysis"
Read Many of article at Parionstr
0 notes
Text
An Arkansas lawmaker shocked onlookers this week when he asked a transgender health care professional about her genitals at a hearing on a bill that would prohibit gender-affirming care for minors.
Gwendolyn Herzig, a pharmacist who is a trans woman, was testifying Monday in support of the treatment for minors during a state Senate Judiciary Committee hearing.
“You said that you’re a trans woman?” Republican state Sen. Matt McKee asked Herzig. “Do you have a penis?”
The audience erupted, with some audibly gasping and at least one person shouting, "Disgraceful."
"That's horrible," Herzig said, after taking a few moments to gather herself. "I don't know what my rights are, but that question was horribly inappropriate."
Herzig, who holds a doctorate of pharmacy, then added: "I'm a health care professional, a doctor. Please treat me as such. Next question, please."
Herzig said she went into Monday's hearing hoping that Republican lawmakers would be receptive to hearing her perspective as a trans woman and a health professional.
"Any other question I was expecting other than what I got," Herzig, 33, said in a phone interview with NBC News. "It was probably the most publicly humiliating thing I've ever gone through."
McKee did not immediately respond to NBC News' request for comment.
The exchange prompted outrage on social media from trans activists and the state's Democrats.
"Absolutely sickening," Alejandra Caraballo, a clinical instructor at Harvard Law School’s Cyberlaw Clinic, wrote on Twitter. "Arkansas State senator Matt McKee asked a trans person at a legislative hearing 'do you have a penis?' Does this State Senator have any basic human decency?"
The Democratic Party of Arkansas tweeted, "Republicans are not hiding their transphobia."
The legislation, S.B. 199, introduced in the Arkansas Senate this month, would prohibit physicians in the state from providing most types of gender-affirming care to minors, including prescribing puberty blockers or hormone replacement therapy, or from performing transition-related surgeries.
It would also allow anyone in the state who has received gender-affirming care as a minor to file a malpractice lawsuit against physicians for up to 30 years after they turn 18.
More than a dozen major medical organizations, including the American Medical Association, the American Academy of Pediatrics and the American Psychological Association, support the treatments that would be barred if the bill becomes law.
In 2021, Arkansas became the first state to ban gender-affirming care for minors, but a federal judge temporarily blocked the law. The 2021 legislation largely mirrors the bill introduced this year.
Five other states have enacted similar forms of the legislation, including South Dakota, whose Governor signed a measure into law on Monday.
Less than two months into 2023, lawmakers in at least 24 states, including Arkansas, have introduced legislation that would restrict transition-related care for minors, according to an NBC News analysis.
S.B. 199 advanced through Arkansas' Senate Judiciary Committee on Monday, and it is expected to pass through the state Senate in upcoming weeks.
After testifying, Herzig said she defiantly sat through the rest of the hearing before heading back to work at the pharmacy she owns, Park West Pharmacy in Little Rock, the state capital.
As video of her exchange with McKee spreads on social media, Herzig said, "Going viral, I guess, is OK."
"I really just hope it just shows people that there's people like me who want to stand up and that there are people who want to make sure there are access to resources," she added.
#us politics#news#nbc news#2023#Arkansas#trans healthcare#trans healthcare ban#transphobia#republican homophobia#trans misogyny#Gwendolyn Herzig#Arkansas legislature#Matt McKee#republicans#conservatives#gop platform#gop policy#gop#alejandra caraballo#Democratic Party of Arkansas#sb 199#Arkansas Senate Judiciary Committee#Arkansas Senate
133 notes
·
View notes