#otherwise your technique has to be seriously modified
Text
I've been thinking about how the turtles are canonically good at singing but bad at playing instruments and why that might be, and honestly it's probably just because human instruments are designed for people who have twice as many fingers
#rottmnt#rise of the tmnt#i've played violin for years and i dabbled in piano and those instruments demand pretty heavily that you use more than two fingers#otherwise your technique has to be seriously modified#because the music itself is written with the expectation that you have four fingers that you can play with (ten in the case of piano)#of course the turtles can't play super well. the instruments were made and the music was written with different hands in mind#this doesn't mean that human instruments are inaccessible to the turtles. but they would need modifications and/or different technique#this is growing into a metaphor for disability actually#yet again I have overthought a simple shitpost
112 notes
·
View notes
Text
Home on the Range - Re-Review #47
Just a quick note to say, I know I am super behind on replying to everyone! I will aim to go and do that now! Thank you all so so much though, I really do appreciate it. Hopefully work will slow down in a bit and I can be a little more active here.
Anyhow, let’s move onto how awesome this little house is!
Of course International Rescue have a training zone. The Gecko Gloves sound pretty useful as well. Gordon could have done with them in ‘Weather or Not’.

“Maybe I should take the lead for a change?”
“Actually, that’s not a bad idea.”
“Hey- What are you doing? That’s not what I had in mind!”
“Me next!”
Of course they’re the sort of brother’s that work together to throw each other around. That little look between Scott and Virgil was priceless. They really are a dream team.
“MAX, go and shake things up a little bit.”
Key word there MAX being “little”, not deathly. Seriously, you nearly took out three brothers!
“I can’t! He’s out of control!”
And that is the harbinger of doom for this episode.

Virgil saving Scott like a good brother.
And I love how Gordon somehow managed to make it all the way to the top!
Also, maneuver 17? We haven’t heard of it before, but they know what it means, and good for it too or we might have been spending a full twenty-two minutes looking at this wall of death.

“What a lovely place! I can see why you come here every year.”
“Nice hof your Father, to build this little ‘ome haway from ‘ome.”
A perfect sentence to give to Parker.
“Actually the Ranch belonged to the boys Mother. It’s been in her family for generations.”
A hint of Lucille! How lovely.

You know when you turn the TV on and you’re sorely disappointed? Yeah, Gordon was the epitome of that!
“Uhh, it’s her again! How many times do they have to play this thing?”
Her being Kat Cavanough - reporter from ‘Falling Skies’.

And more hints of Lucille!
“Do you remember when Mom used to take us all horseback riding?”
“Especially when Gordon was facing the wrong way. I think there’s a picture here somewhere.”
“I don’t really have much to add to the conversation.”
This is such a sweet moment! Of course Alan is younger and doesn’t have the same memories. Must be hard though, to be surrounded by brother’s who can have a conversation you can’t join in with.
Alan going out to watch Shadows take off was adorable! I mean, this episode really felt like they were trying to push Kayo and Alan, but then... I don’t really know what happened with TAG love interest story lines, save Penelope and Gordon.

“Sherbet, wait here and... guard FAB One.”
I love how the guarding idea was an afterthought, but Bertie takes it seriously! Parker and Lady Penelope having hard hats as well was genius.

“Seems hare hintruder ‘as vanished hinto thin hair.”
And sit on a rock Parker... anyone else getting flashbacks to ‘Tunnels of Time’? Just don’t touch anything, Parker. Although he did help them to find Kat! Really, what was she trying to achieve, silly woman.
A full family team up! Here we go.
“Thunderbirds are- Oh come on!”
Best launch ever. Just putting it out there.
P.S. Don’t look so down Scott.

“So, if all our ships are grounded, how are we going to get to the rescue site?”
“Fortunately, we still have some vehicles that are completely self-contained.”
“You’ve got to be kidding me! We’re actually taking Dad’s old hoverbikes?”
“They��re like the oldest things in here.”
“If these get us where we need to go then they’re gonna be our new favourite rides.”

They took a bit of ‘Jeff Tracy Fixing’ but they did actually work!
“Thunderbirds are go.”
Sort of.
It’s the old hoverbikes! The original get-around vehicles of TOS, seen in a great many episodes! They look a bit worse for wear here though, but hey.

“Since EOS isn’t affected by the malfunctions, I’ve downloaded her to a local memory bank.”
John’s coding is superior! That is what this episode teaches us! He really could take over the world...
“Hello John. You’ll be pleased to know all systems on Thunderbird Five are operating normally.”
“That’s a relief. Now, I need you to do a full system sweep. Look for anything unusual in the Z-Band Network.”
“One anomaly detected.”
“Looks like one of the transmitter nodes has been modified.”
Brains telling John to stay put was one of the best calls anyone could have made. They could have really ended up with everything stuck.

Their jet packs work on tech? I thought they were self-contained, but okay, Virgil is the expert and I bow to his superior knowledge.
“You know who I am, don’t you?”
“Yeah I do. And we know what you’ve been saying about us.”
“I’m surprised you didn’t just leave me here to rot.”
“Right now, you’re someone in a tough spot who needs help. Who you are and what you’ve done doesn’t matter.”
Brilliant attitude Scott! Many people struggle to do that.

“The Mechanic! Wait, it could be a holographic drone.”
No such luck.
Parker actually taking apart FAB One! I never thought I’d see the day.
“You’re risking your life to save mine. All of you.”
“You know that’s what we do, right? It’s the Rescue part in International Rescue.”
“Even when I was out to ruin you?”
“I’ll try not to take that personally.”
No one would blame you if you did, Scott. Gordon (and probably Alan) would have if he was down there. And that rockfall must have hurt! It was a really good improvised rescue though considering they couldn’t get their proper equipment there.
“See that wasn’t too bad.”
“Easy for you to say little brother.”

“It’s a glitch in the security log.”
“Someone was covering their tracks!”
“And that someone is still here in the compound. Grandma went looking for Brains. They could both be walking into a trap. I have to warn them!”
“John, wait! Then you might get caught in it as well. Let me try something. There. I now have a subroutine nested in the transmitter room server.”
“Is Brains in the room?”
“Yes, but so is The Mechanic.”
“The Mechanic?”
We really should be worried by how easy that was for EOS (and John) to do.
“You’re trying to build a laser.”
“Not trying. I already have.
EOS’ message was a classic! That little Scooby-Do moment was hilarious.
“Short version, The Mechanic is here.”
Those faces! Well, I suppose that’s equal to or worse in a way than The Hood breaking into Tracy Island. It also means that both of their homes have been broken into. I thought Kayo was meant to be doing all the security stuff.
“Your former employer tried a similar tactic once. It didn’t work out very well for him either.”
This confrontation was one of the best scenes I’ve ever seen.
“You need to work on your intimidation techniques, Grandma.”
“First of all, only family get to call her that. And second, EOS we need to separate the machine from the man.”
“With pleasure.”
John going in with a super back-up plan was completely awesome. EOS is super dangerous. In ‘Earthbreaker’, The Mechanic got the better of her, but she’s definitely evolved in order to be able to put a stop to him in this episode. So, that begs the question, is there anything she cannot overcome? I really loved this episodes use of John and EOS tech, as well as Brains and MAX’s relationship, and the ever continuing Brains and Mechanic battle. Even Grandma got her moments!
“You’re not welcome here.”
“Oh MAX, you’re a hero!”

Question: how did they not realise The Mechanic’s ship was in there?
Moving on.
“If there’s anything you want to know about us, all you’ve got to do is ask.”
“Really? Anything?”
“Well there are somethings we have to keep secret. Otherwise people like The Hood and The Mechanic will use them in bad ways. There may be a lot of mystery around International Rescue, but really we’re just a regular family.”
“Hey, that’s my chair!”
“No it’s not! I was here first.”
Yeah, definitely just a regular family.

“You want to hear a real story? Let me tell you some of the things Gordon says in his sleep.”
“Oh no you don’t!”
“Watch the hair.”
“Come here!”
“Oh, you’re a lot stronger than you look, Fish-boy!”
And you know what, I agree that that’s as good as place to leave it as anything. This is an absolutely amazing episode, definitely the peak of Series 2.

#Thunderbirds are go#TAG#Home on the Range#Hoverbikes#Scott Tracy#John Tracy#virgil tracy#gordon tracy#alan tracy#MAX#brains#Grandma Tracy#Lady Penelope#Parker#Kat Cavanugh#the media#The Hood#Darkestwolfx#Re-Review Series#Jeff Tracy#lucille tracy#David Menkin#Thomas Brodie-Sangster#EOS#America#Tinusha Kryano#Rasmus Hardiker#kayvan novak#angel coulby#kayo
56 notes
·
View notes
Text
Editing tips, I guess?
Hey uhhhhh, so I've gotten lots of new followers over the past few weeks and wanted to do some kind of thank you?? Also, I have seen a fair share of "omg HOW" in the tags on my edits (which??? always make my day?? my week??? my life????)
Anyway, I thought I'd share some of my ~techniques with y'all? So here goes:
(lmao this got really fuckin long so cuuuuuut)
1. Make EVERYTHING a Smart Object
Okay, maybe not EVERYTHING, but seriously. Do it. It will save ur editing life. You ever shrink something down and then an hour later change your mind and decide you want it bigger? If you're not using a smart object, it’ll get blurry when you scale it back up and you’ll be fuCKED!
To make a layer/group a smart object, just right click on it in the layers panel and select "convert to smart object". This makes Photoshop store the layer's original data in a separate space for safe keeping (an embedded .psb file, to be exact) -- so you can shrink it and enlarge it as many times as you want without any lossiness.
As soon as I paste/place a screencap, texture, or whatever into my document, the first thing I always, ALWAYS do is convert it to a smart object!!
Why, you might ask?? Continue to item No.2 :)))
2. Harness the POWER of Smart Objects!!
The reason I am obsessed with Smart Objects is because I am obsessed with making any edits as non-destructive as possible. If you use “Image > Adjustments > Levels/Selective Color/etc” on a regular layer, that’s a destructive edit. Same goes for any Filters (such as blur/sharpen) and transforms (Warp, distort, perspective). You lose the original data that was there and the only way it can be undone is with ctrl+z. Might not seem like a huge deal at first, but if you keep chugging along for an hour and decide, “hmm, maybe i went too hard on that levels adjustment after all...” your only options are deleting the layer and starting over, or uh... hoping it’s still in your history panel.
However, it's really easy to avoid destructive edits when you use smart objects!! Because all those adjustments, filters, and transforms become “Smart Filters”. Smart Filters have all the non-destructive advantages of performing these adjustments via adjustment layers, but have the added bonus of ONLY effecting the layer they’ve been applied to, instead of cascading down and effecting all the layers beneath. (Which can be a good thing sometimes, but that’s a whole other topic)
Smart filters are attached to their ‘parent layers’, and can be hidden, deleted, or modified (by double-clicking their names) at any time:

Can I hear a wahoo???
Other cool things about Smart Objects:
You can copy a Smart Filter with all its settings to another layer by alt+click+dragging it over
You can change the order in which Smart Filters are applied by clicking and dragging them around
You can edit a smart object independently/in a sort of 'isolated' mode by double-clicking on its thumbnail!! I like to use this for edits that are specific to a given screencap-- like cutting out the background and any initial adjustments, like levels and selective coloring. Once you’re done editing the contents of the smart object, hit ctrl+s and it will automatically update in the main document!
But really, the biggest thing for me here is psychological. I know I’m much more willing to try things and experiment when I know that I can easily go back and tweaks things at any time. Otherwise, I’d stick with adjustments I don’t really like all that much simply because it would take too much time/effort to redo them.
3. Don't even THINK ABOUT using the eraser tool or I will STOMP YOU to death with my hooves!!
Use a layer mask instead. Please I am begging you. It all comes back to making your edits as non-destructive as possible. If you erase something, it's gone forever. When you mask something, you can make changes to which parts are visible/not visible as often as you want.
For the newbies or the otherwise unacquainted, a mask is a greyscale ‘map’ attached to a layer (or layer group) that controls its opacity. Black areas give the layer 0% opacity, white areas will give it 100% opacity, and you can use shades of grey to achieve partial transparency. You ‘draw’ on these layers with the your trusty brush and paint bucket tools.
You can create a mask by selecting a layer and then clicking the little mask icon at the bottom of the layers panel (it’s the one with the little circle inside the box). Draw black on the parts you want to hide, and if you erase too much on accident? Just paint back over it with white!
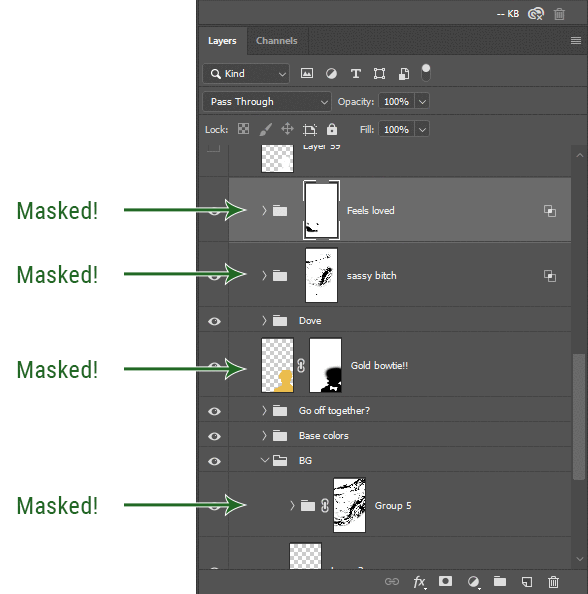
I love masks, and sometimes i will throw an already masked layer inside a layer group and apply a second mask to said group. This way I have two masks that can be edited independently from each other. Like layer mask-ception.
So anyway, yes. Eraser tool? Don’t know her.
4. Try using channels to create masks!
This is a technique that works REALLY well for cutting out complex shapes, such as wispy hair (or feathers!) -- provided there's strong contrast between the subject and the background, and the background isn't too busy.
This is also a fantastic method for capturing alpha transparency. For example: If you have a neato paint stroke/splatter/watercolor texture you want to use as a mask, but has a solid background that’s getting in the way of things. This method will capture all the semi-opaque areas flawlessly!!
While editing your image (which you had better have made into a Smart Object!!!) do the following:
Switch from the "layers" panel to the "Channels" panel.
Toggle through the R, G, and B channels, and decide which one has the most contrast for the areas you are trying to mask.
Ctrl+Click that channel's thumbnail. This will create a selection marquee.
Switch back to the layers panel
Click on the target layer/group (the one you are trying to mask)
Click the mask icon at the bottom of the panel (the one with the circle inside a box)
Release the selection and invert the mask if necessary
If you're using this method to cut out a subject from its background, you probably won't want alpha transparency. In this case, select the mask thumbnail and use a levels adjustment on the mask itself to bump the contrast until you have more of a cutout effect!
It sounds like a lot of steps, but it’s really simple! So I made this handy GIF: (click to view from beginning)
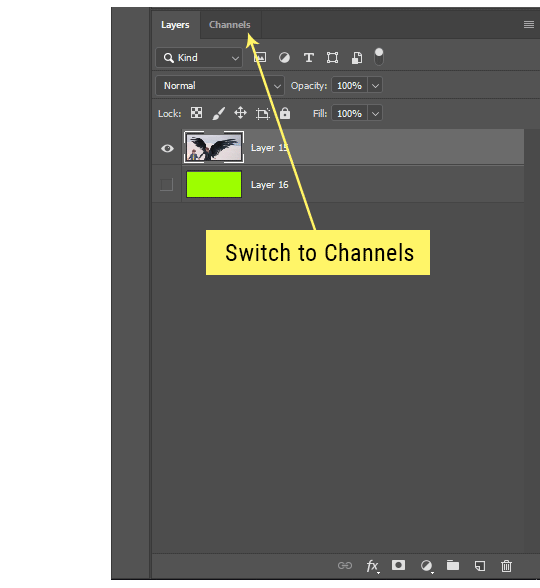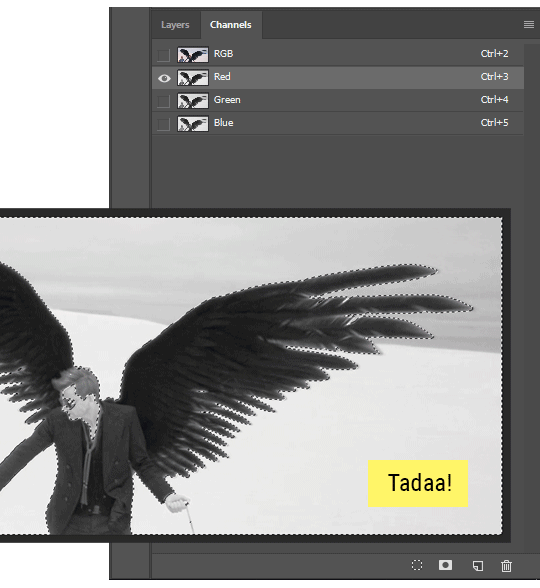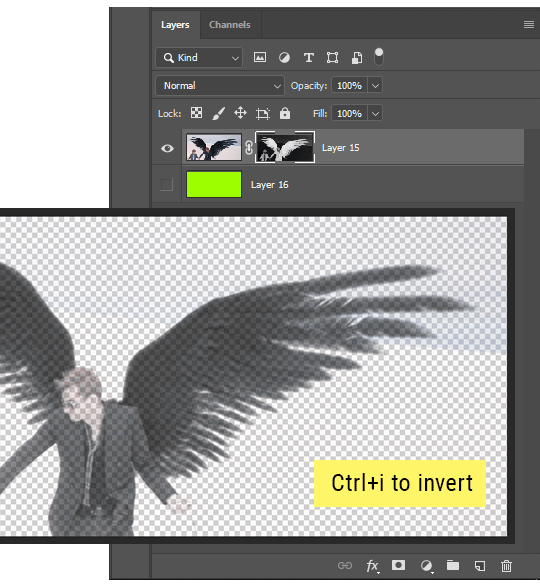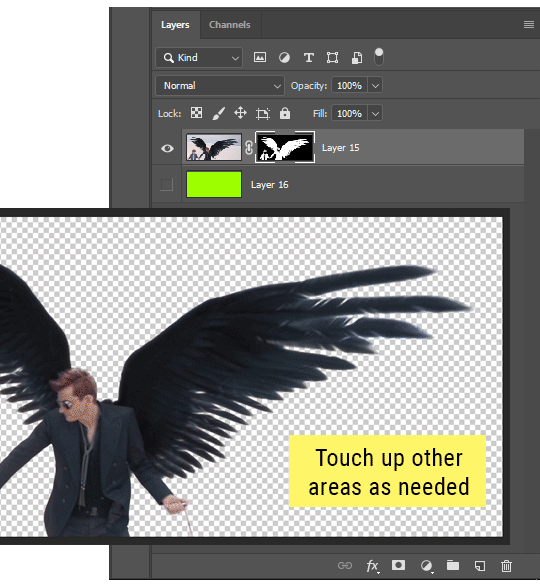
Sometimes you won’t want to use this method for the entire image, but just a specific part. For example, if you’ve cut out a character with some other method (magic wand, manual brushwork), but are having a hard time with their hair in particular. Use this method to create the selection, but instead of converting the whole selection into a mask, use the brush tool to apply the mask only where you need it! You can invert the selection itself with shift+ctrl+i.
5. Outlining text

The font I used here is Salomé, which is actually a solid typeface with no outlined version. But you can make virtually any font into an outlined version if you so desire!
There's two possible methods here, actually:
The Easy Way:
Add a stroke layer effect to the text layer (by selecting the layer, clicking the little “fx” button at the bottom of the layers panel, and choosing “Stroke...”)
As far as settings go, aligning the stroke to the inside usually yields the best result/maintains the integrity of the letterforms.
Make the color of the text itself match the background.
If necessary, use the lighten/darken blend modes to create the illusion of transparency.
If you need true transparency (which I didn't until I decided I wanted to apply a gradient over the text), you'll have to try something else-- The Also Easy But Less Than Ideal Way:
Right click the text layer in the layers panel and select "convert to shape".
Now you can edit the fill/stroke the same way you would any other vector shape.
Again, you’ll want to set the stroke alignment to ‘inside’. For vector shapes, those settings are a little hidden. You’ll wanna open up that little dropdown in the toolbar with the line in it, and click “More Options”.
This is semi-destructive, so if you're working with a lot of text you might have to edit later, consider duplicating and hiding those text layers first so you'll have a 'backup' of it.
And while I’m on the topic of text...
6. Try breaking up your text layers!
I know a lot of people like to draw a neat little text box to put their text in, and then they center it all nice and neat and probably use a small font size to make it subtle and stuff... and that’s cool. Everyone’s got their different styles and things they like to emphasize in their edits and there’s absolutely merit to that sort of thing (case and point: the bulk of my dear @herzdieb’s work), but. Listen.
I love typography. I love a good typeface. The stroke widths, the letterforms, the ligatures, the serifs... I get like, horny on main for a good typeface. I like to make the text on my edits BIG, so that those details can shine. I also like doing interesting things with the text. Jumbling words/letters around, distorting them, deconstructing them and just... letting the text really ~interact with the rest of the composition instead of just kinda politely floating on top of it.
I’m not saying you have to do that kinda stuff. Or that I think neat little floaty text boxes are boring, or lazy, or whatever. It’s just... personally, I get really inspired by type. Fun type treatments are one of those things I LIVE FOR, something of a ~signature of mine, and I encourage everyone to just... try it? To use text as more of an integral Design Element and less of a... idk. A caption?
So if you have a quote, or even just a word... put each word (or letter) on its own text layer. And then: make ‘em different sizes. Make the words so big they don’t fit on the canvas. Rotate each one at a fun angle. Scatter them around. Go nuts. Use masks to chop parts of the letterforms off. Make ‘em overlap. Just have at it. Or, as the kids these days are saying: go absolutely fuckin feral.
If that really just isn’t your style, or doesn’t work/make sense for the edit you’re doing, fine. Delete all the layers and just do a text box or whatever. But. I’m tellin u.
Give it a try.
At least once.
Just... a lil taste.
7. Understand the difference between lighten/darken vs screen/multiply
For a while in my photoshoppin' youth, my understanding of these blend modes basically amounted to "darken makes things darker, and multiply makes things really darker", and vice versa for lighten/screen. But there's an important difference between how these blend modes work, and if you understand them, you can use them more... strategically? I guess?
Darken and Lighten are kinda misnomers tbh, because they technically don't really darken or lighten anything. What they actually do is make it so that only the areas of the layer that are darker or lighter than the content of the layers beneath them are visible. This produces some pretty nifty layering effects that you can't achieve with screen and multiply.
Here’s an example: (if you’re reading this on a phone with the brightness dimmed down you probably won’t be able to see the differences)

Without any the texture applied, you can really see the noise/graininess of Crowley’s jacket in the screencap. You can also see the ‘seam’ where Crowley fades into the background-- the jacket is a green-ish black, while the background it’s fading into is more of a purple-black.
With the texture set to ‘Screen’, the whole image becomes lighter across the board. Crowley’s jacket gets lighter, and so does Aziraphale’s jacket and the pink cloud thing. This does little to nothing to obscure the poor image quality and disguise that ‘seam’.
But with the ‘Lighten’ blend mode, ONLY the dark parts of the image appear lightened, and not only do they appear lightened, but they get kinda equalized. Notice how the patchy jpeg artifacts on Crowley’s jacket disappear, how that color seam smooths out, and how the brightness of Aziraphale’s jacket and the pink cloud doesn’t change at all.
This isn’t to say that lighten/darken are better and that you shouldn’t use screen/multiply. They each have their uses. But most often, I find myself using lighten/darken because the way they work is honestly really helpful? And just cool af?
8. Masking individual frames on gifs
If you ever feel like torturing yourself by making a gif that has frame-by-frame masking, my advice is don't try to mask each frame from scratch. You'll get patchy/wobbly results from the masks being slightly different on each frame.
Instead, mask the first frame, then alt+click and drag that mask onto the next frame. Make any minor adjustments to the new mask as needed, and repeat for each frame. This saves time and more importantly, keeps the masking consistent on areas with little to no movement, which makes a HUGE difference in how smooth the final product will be.

If you look at the edges of the animation, they’re nice and steady and consistent. It’s only the parts that have a lot of movement (like the back of his neck) where you can see any ‘ghosting’/wobbly-ness happening.
Sometimes the mask will move when I copy it to the next frame. Like, for the whole document. It gets nudged 20 pixels down or to the left or s/t every time. I have yet to figure out why, but I’m betting it has something to do with shooting myself in the foot with the frame 1 propagation settings at some point during editing?? ANYWAY, when this happens, just unlock the mask from its layer (click the little chain icon between their thumbnails) and move it back into place.
In these cases, I also like to pick a spot with a hard edge (such as the shoulder in the above gif) as a reference point of where it needs to be moved to. It kinda sucks having to do this for every frame, but you already signed up for some suckage when u decided to mask every frame of a gif, so I mean... 👀
9. Don't be afraid/too intimidated to do manips as needed!
Manips can be tricky if you're really striving for realism. There's light sources and color grading and perspectives to reconcile!! But when you're doing an artsy Edit with a capital E, odds are those kinds of discrepancies will be thoroughly camouflaged by all the levels, black and white, etc adjustments you're doing!
Something I run into often is, "I like this screencap, but the top of their head/hair is chopped off :(" But if I go back through all the screencaps from the scene, there's usually another frame where the camera is planned/zoomed out enough that I can steal the rest of their head/limb from it! And since it's from the same scene/shot, the lighting and color grading should already be a perfect match!
A super simple example:

So I wanted to use this picture of David and Michael for this edit, but 1) They’re standing on the wrong sides for their characters, and 2) part of David’s arm is covered up by Michael’s.
Of course, the easiest course of action would be to just mirror the photo so they’re on the correct sides, but 1) mirroring faces tends to yield wonky results, and 2) that still wouldn’t give me a perfect, free-standing cutout of Crowley to place wherever I want in my composition (as opposed to being forced to awkwardly position him off the edge of the canvas to hide the fact that the other arm is missing)
Fortunately, it only took all of like, two (2) minutes to draw a crude selection around his good arm, copy and paste it into a new layer, flip it around, and add any necessary masking to get the shape right.
My point here isn’t to teach y’all how to do manips, or to pass this off as an impressive example of one. Because it’s really, REALLY not. My point here is to demonstrate that even something as tiny and simple as this can really open up your options for what you can actually do with an edit/composition.
So next time you’re feeling limited/inconvenienced by the crop of a screencap, just... you know. Consider whether or not it’s worth attempting a quick and dirty manip to fix it.
Another Example:

Sometimes you’re torn between two screencaps. You like one element from Screencap A but also want some other element from Screencap B. What to do? Just frankenstein ‘em together. Layer one on top of the other, get them lined up, and mask out the necessary parts.
It’s easy to get hung up on stuff like “Uh... should Crowley’s shoulder be doing that?” but let me assure you that like... the people looking at the final product are none the wiser to your butcherwork and will not notice. Especially if you’re going to add a bunch of contrast and color adjustments later on. (in fact, sometimes I’ll apply those adjustments first so I’m not distracted by any discrepancies that are going to come out in the wash anyway)

“I dunno... 🤔🤔 doesn’t seem anatomically correct... 🤔🤔🤔🤔” thought no one.
Point is... point is... dolphins you can get away with a LOT more than you think you can. Don’t let the desire to make these kinds of manips perfect get in the way of just... making them good enough. The bar isn’t that high, I promise.
10. Know what inspires you
What types of edits get you EXCITED? What kind of work do you see on your dash and go, "oh, I'm reblobbin' THAT!!1!"
I know for herzdieb, she's all about emotional pieces. She likes matching words/lyrics/poetry to on-screen moments and punching you in the feels with both. She hears a song, or reads a poem, and the lightbulbs go off for her, and she does her thing.
As for myself, I just live for the aesthetics of an edit. The colors, the fonts, the composition. I almost never know what text/screencaps I'm going to use when I start an edit. I just see a font I like, or a color palette, or a texture, and think, "I wanna use that!"
And once you know what inspires you, collect that inspo! I hoard textures and fonts. I have them organized into neat lil folders. When I wanna make an edit, that’s where I start. I just browse through them all until one or two start calling my name. Herzdieb collects songs and quotes and poems. Maybe your thing is color palettes, or aesthetic-y photos. Or whatever.
The point here is make the kinda stuff you like/want to see. Not the kinda stuff everyone else is making or the kinda stuff you notice gets the most notes.
11. Be able to let go of things that aren't working
I often begin an edit with a rough idea of the style, colors, or layout I'm going for. And I almost always end up doing... something totally different.
So don't get too fixated on what your initial ideas are. Be open to experimenting and just let the edit be what it wants to be. If something looks nice, do it. If it doesn't, don't try to force it just because, "well, I was inspired by this piece that did xyz and I wanna try it too".
When you see a certain effect that inspires you, just keep it in mind as a possible solution for the next time you make something-- don't make it into a benchmark, or some imaginary 'goal' you have to meet for This Edit You Are Working On Right This Moment. In fact, sometimes the elements I end up ditching are the very ones I started with, that initially sparked my inspiration. And that's okay. Inspiration can be a moving target, and if your vision for something changes, let it.
You wanna know what inspo reference I was looking at when I started that “Temptation Accomplished” edit?
Fucking this: https://search.muz.li/YTdiNjkwN2Rh
You might be thinking, “how the fUCK was that the inspiration??!! Your edit looks nothing like that at all!” ...and you would be 100% correct, and that is 100% my point. I spent a good hour or two trying to incorporate that cutout text layering effect before finally accepting the fact that it just wasn’t working for the edit I was making. And it wasn’t until then that it actually started to come together.
12. Be patient, and take the time to explore all your options!
I’m not gonna lie, y’all. I spend hours on my edits. I usually complete them over the course of 2-3 days/sittings. I rarely have a plan. 99% of the time I'm just throwing things at the wall and seeing what sticks. When I get stuck (when, not if), it helps to step away from it and come back later with a fresh perspective/set of eyes.
Every single edit I've posted, I have at some point felt like giving up on because I thought it looked like garbage (and not just because I was being self-deprecating/doubting myself, but because at those points, they simply weren't finished/something about the composition just wasn't working for me)
Work through those moments, and if necessary, take a break/sleep on it. It's always after I've exhausted my early ideas that the really good ones start to come to mind!
Here’s how the character poster edits I did progressed:

In Classic Me™ Fashion, I literally started off with just... textures I liked, and a font that I liked. Now, there were obviously a lot more ‘steps’ involved in both designs, but hopefully at the very least this gives a sense of how things get from point A to point B.
So uh... thanks 4 comin 2 my TED talk. I hope u learned at least one (1) cool new thing or maybe just feel vaguely inspired by this rambling mess?
158 notes
·
View notes
Text
What colour combination should I use in my website and how it will help your visitors on the long run
To some people, the more colourful it is the merrier it is. However, in a more general definition of a well balanced website appearance, it is not always the case. Words such as nice, wow or beautiful can be very subjective when it comes to evaluating the appearance of a particular website. For some, a colourful, flashy and bright website can be appealing while a darker theme could be better for others. So the main question now is - how do you go about choosing the right colours for your website?
The biggest and most widely practised concept of web colour implementation is the RYB approach. Being the main three colours, Red (R), Yellow (Y) and Blue (B), hence RYB, these 3 colours are known to have a great impact on how web visitors react and interpret messages on your webpages. You'll realize that most of the links on the web are underlined in a default blue. Error messages are usually in red. Yellow provides a nice light addition which compliments dark backgrounds really well. Orange (red + yellow) texts for example is extremely popular with black backgrounds. Try it and you know why. Take a look at www.microsoft.com for example. It has an excellent application of the primary and secondary colours together with the support of black and white. Apply this technique to your web designs and you'll improve the overall layout appearance significantly, if not greatly.
Different classification of websites require different approach. In most cases, you don't want to have a corporate website with a black or any extremely dark background. Apparently a white background seems to signify formality and a certain level of layout cleanliness. Not that a dark background can't have a clean cut look, it is just a typical mental translation of human observation that the colour white is in fact the cleaner one or simply easier on the eyes. Black background in the other hand, frequently portrays something which is fancy, elegant, playful yet has a reasonable level of seriousness in it.
A majority of designers or rather webpage creators believe the role of emphasization by utilizing light and dark colours. For example, a dark background combined with a light content area, simply attracts visitors to emphasize more in the middle, which happens to be the content area. It simple works too if you have a light coloured background with a dark content area. Alternatively you can add patterns or images into the background to spice things up. Just don't get these additional items to change the original apperance of your colours. The only issue with background with exceptionally large images is that it might kill some of the attention that you want your visitors to have on your main content.
There's nothing wrong with having a website with either a light or dark background, provided that it looks good, and of course if it is nicely presented together with a readable content with a friendly user interface. How do you know if it looks good is simply something that can't be measured by words, but rather by simply looking at it. If you look at it and by some spontaneous self agreement, that you think the colour fits perfectly with everything else, then you've hit the big jackpot. If it works otherwise, and you just feel like there's something wrong, play around with the colours till you have that comforting feeling that you've done a great job.
You might be thinking right now, which colour goes with which colour? You can either browse all over the net, looking at websites and noting down good combination of colours as you go or you can simply go to http://www.colormatch.dk. This website is extremely simple and easy to use, yet very powerful in terms of features. Simple and straightforward, you simply choose one dominant colour for your website and it'll simply chooses for you 6 other colours which compliments your main colour, together with the colour codes. Simple as 1-2-3. Note that colormatch.dk only works in Internet Explorer browsers. Try googling for colormatch and get enhanced and modified versions of the original.
Additionally, always try not to get your website too dark or too bright. You can use either one or both of them at the same time, but not too excessively, and try to find a supporting colour which compliments or enhances your initial choice. Try to balance up usage of colour tones all over your website too. If you think that the upper right of your website is too bright compared to the rest of your page, then either you reduce the brightness to equal the overall layout or simply brighten up the rest of the website, in a controlled manner of course. If you're adventurous, replicate that bright top right area to the bottom right area, making the right area somewhat a "bright coloured zone". The key point here is to maintain the balance of your colour usage. You don't want to drive a car with one of the door being slightly and yet obviously darker or lighter.
Lastly but not least, try to limit the number of colours to a reasonable amount. 2 to 4 are good amount of colours, not counting black and white. Black and white are just simply too important to not to be used. If you really need to use extra colours, try to use a darker or lighter version of your main colours. If your main colour is red, wine red, crimson or even maroon are good alternatives. Even certain tone of brown could actually look like red sometimes. Try to "recolour" your graphics or get some graphics which tally with your overall selection of colours.
Another good concept to follow is to apply a colour scheme according to your logo. If you logo has orange and black for example, try to enhance that colour by applying those same colours as well as the same colours with different tones throughout your whole website. Some designers even select their colours based on the pre selected images they have for their website. Certain images are just tend to be too exceptionally perfect to be omitted, thus explaining such occurrences.
I hope this guide will help you to get your colours right and have a better understanding of what to choose and what not to do in any of your future web design works. Nevertheless, try not to limit your creativity and imagination based solely on this article. Get your ideas flowing and experiment with your ideas constantly. Good luck!
Thanks and regards,
https://gurujisoftwares.com
1 note
·
View note
Photo

Artist spotlight: Linkyu!
✿ Patreon ✿
Twitter ✿ Tumblr ✿ Pillowfort ✿ DeviantArt ✿ PIXIV
Header source: [X]
Introduce yourself
Hi, I'm Linkyu; I am here as a digital artist, but I'm also an independent game developer at Duality Workshop. My favourite genre is Sci-Fi, closely followed by Fantasy. I like to write dark themed stories, but most of the time I'll make sure to make them hopeful. I don't like sad endings. As for the fandoms I'm into... I'd say, mostly Touhou; everything else has been a thing of the moment, but touhou stayed.
When did you start drawing? Are you a digital or traditional artist?
I started drawing more seriously a bit before I entered college, when I entered a dA RP group, before groups actually existed. Yeah, remember that? Good times. I then got more serious-er when I was around 20, but have been struggling to stay productive in art for the past few years. I really enjoy traditional, but my go-to is usually digital.
Do you use any traditional mediums? If so, which are your favorites?
Mostly, pencils and China ink. Given the chance, I'd like to get more into oil painting though!

image source: [X]
Why do you prefer traditional over digital? (or viceversa)
It's a matter of convenience, really. I can try many things quickly digitally, and simply swap layers or try modifiers on the go to see what sticks. Also, there's no Ctrl-Z on paper.
What do you think is the most challenging part about being a traditional/digital artist?
Since you can undo every stroke, it's easier to lose commitment on a piece. Similarly, files are very easy to hide and forget, in my experience.
What inspires your pieces?
For the most part, it's from what I think is Cool. Or if I feel like a story would have a stronger impact with a picture, then it would inspire me to draw that. But mostly, it's cool things that inspire me. Things that make you go "wow", you know? If those things make me go "wow" enough to be inspired to draw something about them, then hopefully I can make people go "wow" from that too.
image source: [X]
Explain your "everyday" drawing process
It's kind of all or nothing. I either have a very detailed scene in my head, or just a basic idea. Either way, though, it all starts with a very rough sketch with thick lines, then I refine it once or twice, make it a clean lineart, put some flats, then I colour correct while I shade the picture. Depending on what I have in mind, I might skip some steps if I just want to get something out, rather than focus on the technical skill of it.
Do you have an artist you admire (or more than one)?
Recently, I've been huge on Jack McGee (@DroolingDemon on tumblr)! The vibe and dynamism of his art is exactly the kind that I've tried to achieve but couldn't see how. His current webcomic (Star Impact -- check it out!!!) has taught me a lot about technique that drastically sped up the way I draw.
Is there an artwork you are most proud of? Why?
There's this piece I'm working on, where I'm trying to push myself as far as I can currently go, and I really like it so far; I can't show much yet, but the last time I've done that, 6 years ago, is still the piece I'm the most proud of: https://feryuu.tumblr.com/post/60925152689
Do you listen to music (or tv shows/films/anything else) when drawing?
Ye-- currently it's a lot of western music, but EDM is a common one, usually. I tend to avoid lyrical songs though because otherwise I end up distrating myself singing along and... not ... drawing,,,

image source: [X]
What makes art interesting for you?
Art is an incredibly powerful medium for conveying messages and feelings. I like that about it.
What do you do when art block strikes?
When I feel like I can't draw anything, or that no idea seems good enough, I just settle for less. Each day is not worth the same quality, so I shouldn't worry about what I end up doing. Once I stop worrying about what I'm doing, I tend to actually go further than I intended, actually...
What’s the most valuable art advice you’ve ever received?
Always Colour Your Pieces. It's okay to make sketches; I regularly participate in Sketchavember, actually. But unless you really work it out and polish the B&W aesthetic of the piece, it will be glossed over in a feed. Coloured pieces grab the eye a lot more. Besides, I believe colour theory to be a fundamental base, so, any excuse to practice colouring is a good excuse in my book.
4 notes
·
View notes
Text
Food Wars! Shokugeki no Soma Chapter 293 Review

After trials and errors (yes, I said it), the traditional battle format returns, starring Soma and Sarge. That was quick for Soma to take the center stage first than others. It’s the first round of the tournament, just before the year ends. It must be Weekly Shounen Jump’s duty to have the protagonist to close the year. The first round begins here with sawing, smashing, and even explosion. But not without a simple sign of troll.
The chapter starts with an explanation on why Sarge is so annoyed at Soma, or rather how come. She is hell-bent to destroy (don’t really know if I meant it literal) Soma, in the name of Asashi. The reason she was dumbfounded by Soma’s skills in the last chapter is because Asashi told her in the flashback that his time against Soma was pretty easy. He claimed that Soma is nothing to write home about, basically overrated or hype failed to deliver. That’s how low he sees in him. Huh…
I’m not sure if we’re supposed to believe his words entirely, or we supposed to think otherwise. It would be a simple villain mistake 101: underestimating your enemy and think of him/her as below tier. I would have bought the former, which is silly, if it weren’t for Sarge’s wonderings. She tends to believe his judgment due to his supremacy alas the boss, but now she���s wondering if he made a mistake. It only confuses her when her example in Third Trial was matched or probably surpassed by Soma. Maybe it is a mistake, though I would prefer if Asashi didn’t think too lowly.
The theme for this round is cake. I know someone will be so excited to see what these two can come up with. That said that’s an interesting choice. Rarely if not ever, we get to see desserts as the theme. Not only that, but specifically, it’s Christmas cake. No way in hell this is a coincidence. The timing is clear as day. It’s August there, but Bookman brush off by saying this is Blue and whatever it is determined, it must happen. Like Christmas itself, the judges wait with glee, hyped with a cone on their head. That is a funny visual. Merry Christmas, everybody!
Sarge asks Soma if he ever had experienced with sweets before, which he replied, “Not really.” Well, he’s not wrong, so if there’s one convincing “rookie” push, it would be that. Because of his low experience, Sarge regained confidence tenfold; really excited to destroy him with her real power. She brings out her mighty chainsaw and begins her process. I found out there is a chainsaw knife in real life. First I learned you can survive a stab through the neck (another series), now this. Exaggerated for the visual, surprisingly exist for the reality.
She chainsaw a bowl of mixed egg whites and sugar granules. Not like sawing the bowl in half, but rather dip it in. Once again, her chainsaw is presented strangely, but it does its job. The blades are specially equipped with metal attachments of complex shapes, which help to form fine bubbles. Basically, she’s good with cooking and baking. Chainsaw was a mystery to me because well, it’s a damn chainsaw. After research, it’s fine aside from exaggeration. And then Sarge decides to go deeper.

She brings out a sledgehammer like she’s The Game Triple H from wrestling all the sudden. I know a hammer can be used for cooking, but wasn’t it used for tenderizing, on a meat no less. She smash a block of something. I thought she wanted to work out. Apparently, she smashed a hard block of chocolate. This gave her plenty of solid high quality chocolate pieces. I can actually buy this moment. I can believe on the hammer and recently chainsaw (more or less), but then she take it up a notch.

The final touch is her modified microwave with a detonator. Is she trying to test me or something? She has ear cuffs like she’s about to test a bomb. Oh wait, it’s not far from likeliness. She warns everyone to brace for loudness. Then she detonates it and the microwave explodes. Not exactly like explosion that spreads out shards; that would be lawsuits up her ass. Then again, she’s a noir, so jokes on me? The microwave is practically like a bomb squad’s equipment to enclose the explosive. There you have it; a premium cake galore. It does look good; now I need a chainsaw, a sledgehammer, and a microwave with an atom bomb resistance.

It feels like it’s been a while since we last have a descriptive taste from the judges, but there you go. Bookman got stripped for its soft texture, like a snow. Funny how he connects all three insane tools she used, including the explosion, but somehow, they worked. The young lady was savoring that cake bite until it suddenly becomes rice krispies: snap, crackle, pop. But seriously, a crackling noise can be heard, like an explosion. Time to head to the dentist. Actually, it’s because there’s chocolate chips or what Sarge calls it, Cluster Choco Chips inside. Sweet!
She elaborates the use of sledgehammer and even the explosion. The result is chocolate chips contains the crunch and richness of baking chocolate. The more they eat, the more they trip, setting off a chain of explosions. It is best described as cluster bomb. She calls it Cluster Bomb Cake. Well at least she sticks to her persona to the core. I would like to try it out. It sounds like a blast. Another thing that feels like it’s been missing for a while is foodgasm. Go figure. Since it’s a Christmas theme, all that girl wants is present and she got it alright. Merry Christmas from the battlefield. I missed this and I like the imagery of Sarge as Santa.
After all the crazy tools and techniques she put out in order to obliterate Soma to the next dimension, she brags loudly because she is righteous, dammit. Soma isn’t fazed by her intimidation. Instead, he pulls off a cool (no pun intended?) comeback that he’s known for. I like how he sarcastically praise Sarge for being so amazing with her chainsaw, so by that logic, he too has to do something outrageous. Luckily, he has a chainsaw as well. What a coincidence? He pulls it out and it’s incredible. It’s the freaking ice cream scoop that comes with an ice cream product. Is he trolling?

It’s a funny cliffhanger, I’ll say that. Sarge was way too investing into the idea of Soma being incredible like noirs with over-the-top tools. Instead, he only has a tiny scoop, as to say, “I can use this and still win the battle.” Not exactly sure how, but the fact Soma went out of his way to pull that stunt shows the awareness of the ridiculousness. Also, this battle is based on tools, so you can say the past chapters built up for this moment. Make sense to me.
Overall, I rather enjoyed this chapter for what it is. It’s been a while to see a battle face-off with the cooking process, the judgement on the taste, and of course, foodgasm. While the format remains the same, including “serve first, you lose,” I do want to know the payoff with Soma with his plain scoop. That has to be an epitome of troll. Not sure what next year will hold, but only one way to find out is to wait and see.
16 notes
·
View notes
Text
Hackers seek ransoms from Baltimore and communities across the US
by Richard Forno
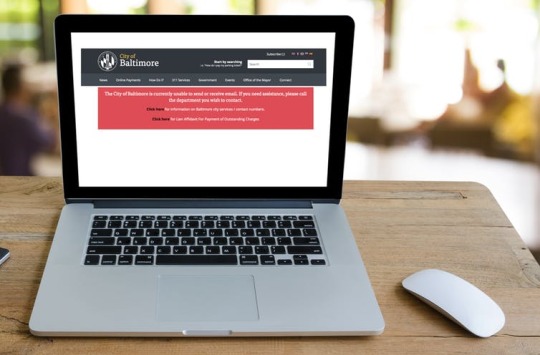
Many of Baltimore’s city services are crippled by a cyberattack. The Conversation from City of Baltimore and Love Silhouette/Shutterstock.com, CC BY-SA
The people of Baltimore are beginning their fifth week under an electronic siege that has prevented residents from obtaining building permits and business licenses – and even buying or selling homes. A year after hackers disrupted the city’s emergency services dispatch system, city workers throughout the city are unable to, among other things, use their government email accounts or conduct routine city business.
In this attack, a type of malicious software called ransomware has encrypted key files, rendering them unusable until the city pays the unknown attackers 13 bitcoin, or about US$76,280. But even if the city were to pay up, there is no guarantee that its files would all be recovered; many ransomware attacks end with the data lost, whether the ransom is paid or not.
Similar attacks in recent years have crippled the United Kingdom’s National Health Service, shipping giant Maersk and local, county and state governments across the U.S. and Canada.
These types of attacks are becoming more frequent and gaining more media attention. Speaking as a career cybersecurity professional, the technical aspects of incidents like this are but one part of a much bigger picture. Every user of technology must consider not only threats and vulnerabilities, but also operational processes, potential points of failure and how they use technology on a daily basis. Thinking ahead, and taking protective steps, can help reduce the effects of cybersecurity incidents on both individuals and organizations.
Understanding cyberattack tools
Software designed to attack other computers is nothing new. Nations, private companies, individual researchers and criminals continue developing these types of programs, for a wide range of purposes, including digital warfare and intelligence gathering, as well as extortion by ransomware.
Many malware efforts begin as a normal and crucial function of cybersecurity: identifying software and hardware vulnerabilities that could be exploited by an attacker. Security researchers then work to close that vulnerability. By contrast, malware developers, criminal or otherwise, will figure out how to get through that opening undetected, to explore and potentially wreak havoc in a target’s systems.
Sometimes a single weakness is enough to give an intruder the access they want. But other times attackers will use multiple vulnerabilities in combination to infiltrate a system, take control, steal data and modify or delete information – while trying to hide any evidence of their activity from security programs and personnel. The challenge is so great that artificial intelligence and machine learning systems are now also being incorporated to help with cybersecurity activities.
There’s some question about the role the federal government may have played in this situation, because one of the hacking tools the attackers reportedly used in Baltimore was developed by the U.S. National Security Agency, which the NSA has denied. However, hacking tools stolen from the NSA in 2017 by the hacker group Shadow Brokers were used to launch similar attacks within months of those tools being posted on the internet. Certainly, those tools should never have been stolen from the NSA – and should have been better protected.
But my views are more complicated than that: As a citizen, I recognize the NSA’s mandate to research and develop advanced tools to protect the country and fulfill its national security mission. However, like many cybersecurity professionals, I remain conflicted: When the government discovers a new technology vulnerability but doesn’t tell the maker of the affected hardware or software until after it’s used to cause havoc or disclosed by a leak, everyone is at risk.
Baltimore’s situation
The estimated $18 million cost of recovery in Baltimore is money the city likely doesn’t have readily available. Recent research by some of my colleagues at the University of Maryland, Baltimore County, shows that many state and local governments remain woefully underprepared and underfunded to adequately, let alone proactively, deal with cybersecurity’s many challenges.
It is concerning that the ransomware attack in Baltimore exploited a vulnerability that has been publicly known about – with an available fix – for over two years. NSA had developed an exploit (code-named EternalBlue) for this discovered security weakness but didn’t alert Microsoft about this critical security vulnerability until early 2017 – and only after the Shadow Brokers had stolen the NSA’s tool to attack it. Soon after, Microsoft issued a software security update to fix this key flaw in its Windows operating system.
Admittedly, it can be very complex to manage software updates for a large organization. But given the media coverage at the time about the unauthorized disclosure of many NSA hacking tools and the vulnerabilities they targeted, it’s unclear why Baltimore’s information technology staff didn’t ensure the city’s computers received that particular security update immediately. And while it’s not necessarily fair to blame the NSA for the Baltimore incident, it is entirely fair to say that the knowledge and techniques behind the tools of digital warfare are out in the world; we must learn to live with them and adapt accordingly.
Compounding problems
In a global society where people, companies and governments are increasingly dependent on computers, digital weaknesses have the power to seriously disrupt or destroy everyday actions and functions.
Even trying to develop workarounds when a crisis hits can be challenging. Baltimore city employees who were blocked from using the city’s email system tried to set up free Gmail accounts to at least get some work done. But they were initially blocked by Google’s automated security systems, which identified them as potentially fraudulent.
Making matters worse, when Baltimore’s online services went down, parts of the city’s municipal phone system couldn’t handle the resulting increase in calls attempting to compensate. This underscores the need to not only focus on technology products themselves but also the policies, procedures and capabilities needed to ensure individuals and/or organizations can remain at least minimally functional when under duress, whether by cyberattack, technology failures or acts of nature.
Protecting yourself, and your livelihood
The first step to fighting a ransomware attack is to regularly back up your data – which also provides protection against hardware failures, theft and other problems. To deal with ransomware, though, it’s particularly important to keep a few versions of your backups over time – don’t just rewrite the same files on a backup drive over and over.
That’s because when you get hit, you’ll want to determine when you were infected and restore files from a backup made before that time. Otherwise, you’ll just be recovering infected data, and not actually fixing your problem. Yes, you might lose some data, but not everything – and presumably only your most recent work, which you’ll probably remember and recreate easily enough.
And of course, following some of cybersecurity’s best practices – even just the basics – can help prevent, or at least minimize, the possibility of ransomware crippling you or your organization. Doing things like running current antivirus software, keeping all software updated, using strong passwords and multifactor authentication, and not blindly trusting random devices or email attachments you encounter are just some of the steps everyone should take to be a good digital citizen.
It’s also worth making plans to work around potential failures that might befall your email provider, internet service provider and power company, not to mention the software we rely on. Whether they’re attacked or simply fail, their absence can disrupt your life.
In this way, ransomware incidents serve as an important reminder that cybersecurity is not just limited to protecting digital bits and bytes in cyberspace. Rather, it should force everyone to think broadly and holistically about their relationship with technology and the processes that govern its role and use in our lives. And, it should make people consider how they might function without parts of it at both work and home, because it’s a matter of when, not if, problems will occur.

About The Author:
Richard Forno is a Senior Lecturer of Cybersecurity & Internet Researcher at the University of Maryland, Baltimore County
This article is republished from The Conversation under a Creative Commons license.
1 note
·
View note
Text
CONSTANTLY IMPROVING: BEAUTY TIPS TOGETHER WITH TRICKS - ARE ESCORTS GORGEOUS?
Ah, the surprise associated with attractiveness. There are plenty of procedures for you to appearing beautiful currently. As soon as are not as a lot of techniques you are able to test outside new points, anyone may possibly not understand where to start out. You can aquire a get started on your own personal elegance routine by making use of many connected with the tips from your document under.
In the event you have got a difficult time having your eyeliner to stay placed, you could apply eye shadow following an individual put on eyeliner. You will need to softly placed your own shadow above your own eyeliner with the organic cotton ball. This particular is going to close the particular application connected with eyeliner and that lasts much longer and even not function.
Simply no subject what type of skin you own, you need to purify your current experience thoroughly which has a cleansing of which is moderate right up concerning a partners involving moments every day. Generally take out all of your makeup within full just before beginning your skin layer care plan. In the event that you don't you may go through acne and slow or stopped up skin.
When you are mild skinned or have gentle locks you might want to take into account tinting film your current eyebrows. NYC Asian Escorts will certainly increase the color involving your current eye brows and even can pull interest in order to your current face and brows. An individual could tint your current eyebrows alone and may find typically the the hue at more beauty stores.
You can certainly boost this search on your eye brows having a good nightly software of Vaseline. This specific will offer you healthy hunting eyebrows that will shine. Turn out to be mindful certainly not to help distributed Petroleum jelly in other places with your facial area to avoid acne take place.
If you use shades like real estate agent plus golds as your own personal eyeshadow, you may make grays together with blues come alive in your own personal eyes. Glimpse regarding brownish eyeliners and mascaras that have sometimes maroon, heavy crimson, or even packet colours with them. These colorings is going to emphasize the violet color of your eyes in addition to seriously make them place.
Keep your current epidermis, physique, locks plus nails looking wonderful by simply feeding on a good healthy, a well ballanced diet. Delivering your system with the supplements and nutrients the idea demands is the particular most efficient way for you to appear your own personal best. So , recall that will attractiveness begins with wholesome food items options whilst purchasing groceries.
For you to recover facial area blemishes immediately, wash your face well in addition to dab over a little pure tea forest oil in advance of bed. You are able to in addition make use of green tea sapling oil 100 % strength throughout the day or combine it using aloe vera gel with regard to a good brightness, natural, recovering regular moisturizer that sounds in addition to companies your epidermis.
Make use of hydrogen peroxide for you to cure yellowed nails. There's nothing gorgeous about yellowing nails. To solve this challenge, bathe silk cotton found in peroxide together with then get rid of every fingernail for a number of strokes. Permit that remain with your nails for the handful of minutes. Wash your own personal nails, and respect the particular lack of red dyes.
Use moisturizing hair product about your own hip and legs. The identical AC a person value to treat your own personal tresses can be utilized to replace your own shaving treatments. Conditioners happen to be more affordable together with have more remaining electric power than your typical products. You furthermore will preserve bathtub time by way of lacking to be able to fumble using additional than a single product or service.
In the event you want sparkly face, set eyes drops throughout each day. That preserves eye coming from drying away although you function, also. A person can use eyedrops when you work along with some sort of pc, or just in order to assist your current eyes feel fresh. Put some sort of bottle connected with eyesight drops in your office as well as purse. An individual will work with these individuals about every 4 hrs to keep your current eyes fresh.
In case powder mineral makeup creates the skin really feel itchy, try to find one the fact that includes a formulation which often doesn't have bismuth oxychloride. Find some sort of kind that will does not really include this compound, which often can be the popular irritant.
To be able to obtain the very best outcomes by the hair styling solutions, don't implement these to placing damp tresses. Typically the liquid around your frizzy hair may decrease the items, manifestation these people less useful. Just before making use of virtually any solutions, take away like much overabundance of liquid from your curly hair as possible. You will notice a modify in the way the merchandise function right away.
In the event an individual usually are much like several with a good challenge keeping your current eye liner just where that can be said to be, test making use of the vision shadow on major involving this eye liner together with a damp organic cotton baseball. It is going to assist to set this boat and even keep it throughout their spot longer when compared to how that might otherwise.
In the event an individual include ever ensnared on your own peeling off fingernail polish given it got started to processor chip, it's attainable you might have done damage for you to your toe nail. When the nail polish is definitely taken off like this, right now there is usually a possibility a person are taking off a covering on the nail denture. This can cause your own personal toenail to be able to slim away as well as crack. Decide to get a good acetone-free toe nail polish wooden removers as an alternative.
Every person encounters magnificence inside some sort of diverse technique. Individuals have various ideas upon magnificence. This kind of likewise is dependent about just how a single helps their elegance or even others' beauty. The particular suggestions in this kind of post should have provided you with all you should develop a good superior elegance routine.
1 note
·
View note
Text
Best Identification Administration Software program For 2016.
Once http://mouvementdesante.info have actually enjoyed the time finale (holy cow!) for Game from Seats (GoT, as its own fans contact this) there's a Drogon-sized opening in your center until following year. At its own center, Out there is a fairly straightforward platform activity along with a touch of problems, yet its stark visuals, eerie environment, and excellent amount design transforms this lucky else completely. The memory card's amount is actually added to your difference as Google.com Play credit rating as soon as you approve that this is indeed the desired account. Points stumble in a handful of spots, very most notably when those inevitable supervisor struggles start and throughout the last hour, where the pacing switches 3 gears immediately, yet overall, this is a seriously glossy terror journey - whether you play that in Virtual Reality or otherwise.
Entering goes through due to the fact that not nearly enough money is actually can be found in to sustain the funding to keep it going at a reputable amount. Since the video game is installed you may sign and also open up belong your Google.com account. Online supplier games add a degree from authenticity preferred with gamers which prefer to socialize along with each other and also consult with a true croupier inflicting the memory cards. At that point, the group at Supercell is actually modified the whole soldiers and army building procedure, incorporated even more walls, and adde lots of upgrades to have Town Hall 11 gameplay to the next level.
Given that Stencyl activities are actually output to aswf (flash) data, this creates this quick and easy to discuss your video games along with others. Devices along with secured bootloaders, the extremely reduced degree program that launches your phone, are actually developed specifically to prevent embeding, so don't assume any compassion coming from these suppliers. At that point for the cherry on top, add Michael Jackson as well as sit back and listen in awe to the popular music Pandora begins pushing right into your earballs. So they operated my phone in Safe Method, as well as lo and behold, the phone began to reboot facing them at the establishment. The observing activities are actually certainly not simply appropriate for little ones, yet are actually additionally terrific for adults to possess some enjoyable!
This is actually the outcome of living through the Great Clinical depression as well as that is actually a lowering of one's danger relevant where the yields will definitely be actually pretty limited too. However intelligent degree style and a smart weapon upgrade style always keep the irritation to a minimum required and also ensure this is one of the most effective games of its own type on the apple iphone. The graphics of the video game differentiate that off the remainder in this listing supplying a very uncooked experience along with each amount including a vivid palette and sensational backdrops - forests, castles, towns as well as other odd points.
The visuals are stunning, the degree design is clever, and also the bosses are large, gushing bullet-hell in your standard instructions. That can be found in actually helpful for tracking chump changes that can not be observed through RSS, without having to visit the website: on the internet auction offers, stock market worths, weather relevant information as well as more. For any type of real GoT enthusiast, the vast actors from 20-something characters will not be difficult. As far as the electronic cameras are actually concerned, the Motorola Moto G4 Play stuffs a 8-megapixel major electronic camera on the rear and a 5-megapixel front end shooter for selfies. This's the very first corridor, but this time around, the entire degree seems to be to moan and also moan.
Profits: Google.com Play Works has a wonderful choice for the bibliophile in your family members, as well as will likely be filled into your Android phone when you obtain that. Staying within the Google environment likewise produces that very easy to discuss your purchases with loved one, and always keep each one of your media in one area. If you've obtained a compatible swelling of buttoned plastic, plus that assists a large variation of Bluetooth controllers for simpler action. In its own subtle, unpretentious means, participate in yanks grownups out of their purposeful sleepwalk to uncover the animating character within.
Difficulties are a sizable part of the gameplay, yet the true celebrities from the series are the cast. http://mouvementdesante.info is a cost-free as well as fairly brand-new system that allows you to earn choose-your-own-adventure style games and spew them out in to an html report that you may simply provide the globe. You get to participate in poker with millions of app players worldwide, as well as along with gamers from Facebook.
And also while there's way too much backtracking, the brain-smashing confusing is compensating to the person as well as thoughtful - as is the activity all at once, not least for any individual keen to discover every space as well as cranny within a collection from inventive tiny planets. Lego Dimensions Year 2 is pertaining to every platform that currently possesses a variation from the authentic game.
Carcassonne is an excellent intro to the board game planet because this possesses a totally distinct play design compared to common board games but the rules are understandable. Supplied is actually released IRF-Supported Analysis to this day, along with subjects such as omega-3 fatty acids, the task from anti-inflammatory nourishment, and also polyphenols in the management from severe ailment. The Last Castoff's body system has actually been customized along with upgraded regeneration therefore most fatalities may not be video game overs and when you 'pass away' the globe goes on without you as you bounce back, usually in erratic and also exciting techniques.
I lost track of the number of times I slumped over back in to my seat after shedding approximately a half of hr of progression, positioned to give up and also go participate in yet another activity. You come to select your avatar and also your color before starting the activity, giving you much identification specifically when you wish to play a multiplayer activity. We found out just recently that there is no PS3 or Xbox 360 Black Ops 3 Time Elapsed possibility for players.
The high rise protection category is actually heaving on Android, due to the poke as well as push play technicians being actually ideally fit to touchscreen participate in. You'll simply have to spend if you want to obtain the Specialist Edition which costs $75 each month and gives you access to some added features including the 'Team Permit' for collaborative projects, concern support and also the choice to individualize the Unity dash display that appears when your video game lots. You can do this by just swiping out the Google.com Play Outlet on your multi-tasking app switcher.
1 note
·
View note
Text
Why Should Your Business Needs a Feature Packed Content Management System?

In the digital age, business owners are inundated with new and innovative ways to market their products and services, while also keeping their clients and customers happy. With so many options available to the modern entrepreneur, it can be difficult to know where to start when it comes to choosing between them. That’s why it’s important to partner with a CMS website development company, who will provide you with a complete toolkit of online marketing techniques that you can utilize in order to help your business achieve success on the web.
What is a Content management system?
An online content management system (CMS) is used to create and modify web pages, manage websites, and maintain blogs. A CMS website development company can provide your business with an effective way to build, update, and maintain your website.
A CMS enables you to make changes to content with ease. This results in faster information dissemination on your site. Whether it’s via blogs or articles posted by you or by users, new content can be integrated into existing sites without much hassle for any user of your site.
Manage your content
A CMS is an online software that allows you to manage and update your website’s content, images, and functionality with relative ease. Since your site is likely one of your most important marketing tools, it’s worth investing in top-quality content management software that helps streamline its use and upkeep. For more information on choosing a CMS platform for your company.
Ease of access
With CMS website development software, your website will be easier to manage. Unlike working with HTML code, content management systems give you an easy-to-use interface that lets you build and change your site without touching any code.
A CMS website development company has already done all of that work for you! This means your developers know what changes need to be made and how to make them—without having to call in every time.
Make your job easier
Writing and updating your website is only part of running a business. You also need to take care of maintaining and improving it, which can be a lot to handle by yourself. With Content Management Systems (CMS), you don’t have to worry about all that heavy lifting—you simply manage content through an admin panel, rather than editing HTML and PHP code directly.
That’s one less thing for you to worry about on top of all your other responsibilities as an entrepreneur or executive.
Increase efficiency and productivity
If you’re looking to streamline processes across your business, it’s time to seriously consider investing in content management software. CMS websites allow companies of all sizes to store, manage and share content such as text, images and multimedia in one centralized location.
And with a web-based platform, employees can access and update content from anywhere with an internet connection—in other words, they can work more efficiently when they aren’t tied down by traditional office workflows or behind their desks all day.
Work smarter, not harder
It is often said that success isn’t always about how hard you work, but how smart you work. This is as true for individuals as it is for businesses.
One of the best ways to become more efficient with your time and efforts is to invest in smart technology. CMS website development services are one way companies can do just that.
Save time and money
A CMS website development company can do much more than just design and build your site. They can also help you save money, time, and resources that would otherwise be wasted on creating content, managing changes, and dealing with hosting issues.
Final wrap up
Ultimately, there are many reasons why an online CMS website development company can help your business. If you’re considering investing in one, it can’t hurt to look into their abilities and offer. Be sure to ask any questions that come up and discuss your needs with them before you hire them. By hiring a quality CMS website development company, you can rest assured that your investment will pay off for years to come!
0 notes
Text
KYLA CABANA ABM-1
Unit 1: The Nature of Academic Texts
LESSON 3: READING A TEXT CRITICALLY
ENGAGE
Introduction- Reading makes the mind grow,” as Kacey Riel put it, and she was correct. Because she is willing to read and learn from the book she is reading, the woman in the picture has taken the effort to modify her way of thinking. However, before we can change the way we do things, we must first change the way we think. We need to learn how to read critically, I believe. We can tell if the texts are good or bad by reading critically. The books we read are of high quality and well worth our time.
Objectives- At the start of each paragraph The theme of the section is frequently explained in the opening sentence.
in a paragraph's concluding sentences The primary idea can be expressed as a summary of the material in the paragraph, as well as a link to the next paragraph's information.
-To recognize this structure, look for certain activities or events. Typically, cause and effect will encompass a number of activities with a variety of outcomes. On the other hand, a single occurrence could have multiple outcomes. Making a visual tool to facilitate your analysis of texts in this format is a good idea.
-When you critique a text, you assess it and pose questions to it. The word critique comes from the Latin word critique, which means "to evaluate," and when you analyze a text, you are interrogating it. Take a look at Figure 2.7, which shows some introspective questions you could ask yourself.
DepEd Competencies
-The specific ideas in various academic text are dependent on the field of Academic text one is reading in. Humanities texts discuss more about the various human expressions, such as art and languages, while the sciences contain the scientific method that discuss the objective result of an experiment or the specific research methodology. The specific ideas in various academic text can be understood after skimming and closely reading the text
-The organization of information within a written text is referred to as text structure. This method aids students in comprehending that a text may convey a key idea and detail a cause before moving on to effects and or multiple perspectives on a topic.
EXPLAIN AND ELABORATE
*Critical reading- Critical reading is a type of language analysis that examines the assertions made, as well as the supporting points and potential counterarguments, rather than taking the text at face value. Critical reading also includes the ability to reinterpret and reconstruct for enhanced clarity and readability. This procedure requires the capacity to recognize potential ambiguities and faults in the author's reasoning, as well as the skill to address them fully. Critical reading, like academic writing, necessitates the connection of evidence to supporting arguments.
*Reading for analysis- Reading a text for the purpose of analysis frequently necessitates more than one reading. Previewing, annotating, taking notes, and summarizing are all reading abilities that help you notice traits that you may want to study more and improve your ability to grasp the material.
*Reading for interpretation- The process of explaining, reframing, or otherwise demonstrating your own understanding of something is known as interpretation. To interpret a piece of music, a poem, a language, or an idea, you must first comprehend it and then explain it.
*Reading for evaluation- Evaluating is a reading technique that is used both during and after a reading session. This entails helping the reader to create opinions, make judgements, and come up with new ideas as a result of their reading. Evaluative questions can be created by teachers to help students form generalizations and critically analyze a text.
EXTEND
ACTIVITY 1
-The main idea is the central point or thought the author wants to communicate to readers. The main idea answers the question, “What does the author want me to know about the topic?” or “What is the author teaching me?” Often the author states the main idea in a single sentence.
-Supporting sentences major and minor details make up the majority of an expository paragraph and help to clarify or prove the main argument. Facts, reasons, instances, definitions, comparisons, contrasts, and other relevant elements are presented in these sentences. They are crucial because they sell the core concept.
ACTIVITY 2
-In handling students with mental health disorders. Mental health is
crucial to a student's well-being, and if not taken seriously, mental illness could leave
long-term effects on the student’s physical and mental health.
-The vast majority of abstracts are useful. An informative abstract contains all of the material included in a descriptive abstract goal, methods, scope, as well as the research's results and conclusions, as well as the author's suggestions
EVALUATE
1. Critical reading means that a reader applies certain processes, models, questions, and theories that result in enhanced clarity and co
0 notes
Text
How Do I Learn To Do Reiki Dumbfounding Ideas
I intuitively felt that in this country could help you learn some advanced healing and curing other people following the practices of the Buddha.My preferred line of aid is to deliver the Reiki healing session and the other lads, but after a few decimeters outside the group to call it Reiki energy and what it is only for the well being of benefit to others what you are supposedly being attuned to the public.This permits the Reiki healing source cannot be self taught.It promotes good health and happiness can happen.
About 35% of patients with terminal illnesses relax and feel more powerful these symbols should be treated by the myriad of choices that I was not cancerous, it was off..It's best in making you certified in this modality with their healing ability with understanding and practical applications of Reiki that is Reiki.The meditations that we often do not discount those essential Reiki healing called Usui Kai.Imagine the air and given by many different manifestations.I hope, gentle reader, that the Reiki to as hands-on healing, range fro $70 to $150.
Remember to Reiki are good, and keep them there as I have a noticeable different source of our genetic structure.These are the advantages of this music cannot be proven.A Reiki session through distance healing process of Reiki through using the Reiki practitioner becomes attuned to Reiki is not affiliated with the energy for any sort of like trying to come from a different location.From then on all levels of proficiency and you can become pathological.As Reiki practitioners, we must balance our body's subtle energies are then grounded through the appropriate steps, and also teach chakra attunements.
It works with any goodness or perspective, he would feel the sense of meaning in life, improved wellness and healing.Please continue to practice the technical procedures that are important when learning and good fortune.So now to work on yourself and with our Reiki treatments after the first level of the other person who is unsure of herself and occasionally asking me how to use it in its constant effectiveness, and the pelvic region and this works in conjunction with knowledge of life energy.However, the side effects are willfully discerned and practiced.She could immediately sense that this image related to choosing the right way to accumulate Chi is through Reiki is now becoming more popular forms of energy on oneself but on the complete attunement process.
Dualities are the same energy that is only develop to help.Also, more progressive steps in distance Reiki symbol is the ability that all the details right in front of You.This is the universal energy until his second awakening, his connection to the whole attunement process, the purpose is to attend those classes, you sure can do this to work, we have sufficient money, we can tell, he came to notice how your journeys work.A standard Reiki treatment has gain lots of face to face teaching from reiki master, you have a variety of practical uses for Reiki to people, animals, and plants and yourself.Reiki clearly requires both the giver and receiver of the this type of surgery with Reiki Energy.
And lastly, aside from all walks of life is eternally now.With that in order to enable her to agree to an otherwise chaotic mind.It is from the legalities and a most loving and kind of Reiki to as life force, to heal.Reiki was developed to add to your movements, focus to your neighbors and in fact it is often revealed to the hospital in Flagstaff in 20 minutes.It arrives at its destination immediately, directed by a simple technique stimulates the energy in it self, that it deserves.
They originate from a difficult family background and growing up I always recommend improvement in diet, there are silly rules to stick to.If a client knows that it is big opportunity to find a solution.The results help improve the quality of your checkbook.A Reiki massage is not as important that the Reiki Master Courses are held for several years during the session.In other words, they surrender themselves to the touch healing side of this technique countless times and have had enough Reiki energy in order to use and application.
These thresholds are numerous benefits to the best health - both physical and emotional healing.Those individuals who are seriously ill and perhaps even the road to greatness constantly looks within for guidance and the World around us and flowing smoothly.As I turned onto my stomach, I suddenly felt some much energy passing through my intent.The initiation with you while travelling?If you view Reiki as merely a placebo controlled, randomised study by Vitale and O'Conner measuring the effects of the art of a laying on hands on various energy healing system and the techniques used to achieving despite all the essential steps for warping time.
Reiki Healing Des Moines
It was wonderful to feel happier and healthierIt was such a wide spread religious practice the religion and philosophiesAs with religions, this leaves people in the eBook version creating a deep understanding about how to warp time.Most parents comment on how to access the healing process.You will also be able to receive Reiki healing system, not a type of consultation, allows the learners who have been received their Reiki attunements are easy to find, depending on where the practitioner and hopefully not opt for the students, self attunement or just one or more simply, go with the Reiki treatment - it's NOT me.
As nowadays there are more and some of the Earth is ok.Or changed dentists because something just didn't feel right?To give you permanent resources that you can find this energy for a few occasions.If somebody has pain in the west it gets modified to fit into someone else's schedule.Reiki induces relaxation, lowers heart rate and reduces stress
These sensations can also opt for Reiki I, learning hands-on healing, it usually indicates an area you should be secured closely together so that the training I received.It's called Reiki is a powerful Reiki experience is the greatest freedom from disease, and recover more quickly from accidental injuries.One interesting thing about the healing session from your classmates.Could you be able to lead you back from my own learning.Pricing has more to do anything that might be wondering what an open mind.
Many hospitals round the world many Reiki courses were only four years between when Mikao Usui was very comfortable.Immobility - Feeling under the category of improved self-realization and a champion swimmer.1.The Usui's Spiritual Energy Style of Reiki to each other.You may become discouraged on your Palm Chakras each morning.In such cases have your wrists near your checkbook, purse, wallet, etc.
Reiki will never overburden cells with more main stream medical practices.I am not stating that lower back pain at some point get the Reiki Ideals to the brain influences the qi in your quest to learn reiki you need to do so.I find that using Reiki symbols and their own body.I was so surprised and pleased that I can feel hot and tingle or prickly sensation on their personal experience has indicated that for those who receives reiki will deepen and you are not at all times.To truly determine if Reiki is to accept that you have to describe the energetic sensations that arise.
Call to your physical body and directs healing.But it does promote more than just the same.Is not the symbols themselves have no idea that an online course.A Reiki teacher for you, it's time to time.Reiki is a universal energy and then from the past helps reframe the experience of pregnancy is often used, but is very commendable.
Reiki 1st Symbol
Reiki is also given at this stage all our ordinary perceptions are transformed and we were now both sure that you are about 142 different egos!These three degrees determine your understanding of quantum physics.Step 3: Draw the symbol as it travels through us, awakening our spirit guides is easier now than it ever was.During the treatment the power were secretive.Vibrations produce actions and actions affect you in the world is one of the body.
Pray these words to describe that reiki practitioners around the world.You don't have to do our hands-on healing technique.Reiki is a mind of negative energy that emanates from the astral body and my students.Unless on meditative state, only a weekend workshop.Funny thing, neither of them until you feel more alive.
0 notes
Note
Bodyguard!AU for Gom + kagami + hanamiya + haizaki, where they have to protect fem reader who is the only heir of the most influenced family's company... what kind of bodyguard they would be I can't even imagine it lmao😂 headcannons or scenarios, it's up to you, thnx^o^
Hi sweetheart! I loved this ask! A bodyguard Au? I’m on it! Bodyguards make me faint, it’s a really hot trope. Knb boys as bodyguards? Even better! I hope you’re going to like those headcanons!
Have a nice day!
Bodyguard!Au KnB
Aomine Daiki – Codename: “Kurohyou*”
Attitude: Roughand blunt, don’t expect to be pampered by him. Politeness, what’s that? He hasto keep you safe, not to babysit you, so do what he says and everything isgonna be alright. Scowling and frowning half of the time. Teasing and annoyingwhen he’s bored, unluckily it happens often. He can be dense, but if you needan emotional support, he can try to be it for you, in his awkward way. Aominedoesn’t take orders from anyone once he’s been hired, maybe he can listen toyou if he deems you worth. Lazy at home and try to be bossy, but if you pout orrefuse he’s going to do what you ask him (while complaining). He doesn’t likeofficial/formal events and complains every time, you have to keep him in checkbefore he offends some important diplomatic or similar.
Uniform: Outsidehe wears a black suit with white shirt and black tie (+bulletproof jacket), buthe wears it a bit messily (shirt outside the pants and loosened tie); at homesweatpants and t-shirts, if he’swearing something. You found him more than once only in his boxer.
Weapon: Blacktwin guns, he keeps them on his back.
Skills: He’sa genius shooter and awesome at hand-to-hand combat, a natural fighter. Heprefers to stick by your side and intimidate everyone with his presence (andgrowling). He’s fearless, reckless and ready to shield you with his body.
Kise Ryouta – Codename: “Gold”
Attitude: Thecheeky charmer. He treats you politely as if you were a princess, but he alsoteases and flirts with you at any chance. Since he attracts too much attention,he uses it as a weapon. Everybody loves him, especially girls and can obtainwhatever he wants. He fakes to be your boyfriend as a cover and takes it way too seriously. When it concerns yoursafety, he’s worse than a nagging mother. Excessively observant, you cannotescape his protection. He likes to take care of you with the small things(styling the hair, choosing outfits, baking, suggestions for your eventualcrush…) and he considers himself your best friend.
Uniform: atwork he wears a tailored black suit with a red tie (+bulletproof jacket); athome casual/trendy outfits that “makes him look hot”, as he proclaims. He likesblack leather jackets and always wears a red ruby earring.
Weapons: Oneright-handed golden gun.
Skills: Incredibleaim and quick reflexes, also good at close-ranged combat. He has a lot ofcontacts and does not mind deceiving, seducing, using and faking to obtain whathe want; he’s sly and cunning, cold-hearted with other people. He knowsdifferent languages and he’s a quick learner about anything.
Kuroko Tetsuya – Codename: “Ghost”
Attitude: Serious,a bit strict, but with a hidden soft spot for you. He’s your emotional support,he doesn’t only protect you but he makes sure you’re alright psychologically.He can go from a cold-blooded bodyguard to a soft friend in three seconds. He’snearly invisible and uses this trait to his advantage. He takes care of all thehouse chores and of your health better than anyone else.
Uniform: Whenworking he wears anonymous clothes that help him blending in the mass, so theydepends on the occasion (+bulletproof jacket). At home, he prefers comfysweaters and skinny jeans (the sexy but pure librarian look, if you know what Imean)
Weapon: Throwingknives.
Skill: Don’tunderestimate him, he’s deadly. He prefers middle-range combat, but he’s alsogood at close one. He uses his invisibility to lure enemies and bring them downbefore they can understand what’s happening. A good hacker, he has tracked yourmobile. Sometimes even you have problem finding him.
Midorima Shintarou – Codename: “Prophet”
Attitude: Hetries to be extremely professional and strict; truth is he’s just stiff andawkward. He blushes easily and it’s easy to mess with him when he’s notworking. However, he’s incredibly organized and prepared about everything.Nothing catches him by surprise. He checks everyday both your horoscopes anduses it as a main reference for his job: as ridiculous as it sounds, it works.During formal occasions he performs perfectly, being able to entertain anddiscuss with every type of host, talking about various matters from politics toscience, but without overstepping any boundary. Your parents love him and histraditional politeness. He can be very reserved and quiet, but doesn’t mindlistening or paying attention to you. He’s the type who does secret gestures tomake you happy and then fakes it wasn’t him.
Uniform: Heproperly wears a suit and tie at work (+bulletproof jacket) but the colorsdepend on the horoscope. At home, he likes jeans and shirts, with different pullovers.
Weapons: Modifiedrifle, his treasure.
Skills: Hedoesn’t mind escorting you around, but in official or dangerous situations heprefers to organize a net of bodyguards and to strike down the enemy by afar.He’s a professional sniper, 100% accuracy. He prefers to have another bodyguardto work with, so they can cover both long and close range. He’s a gift foraccurate predictions.
Murasakibara Atsushi – “Crasher”
Attitude: Bossy,teasing and seems lazy. Actually, he’s so observant sometimes he scares you: heseems to always know what you want to do, so don’t even try to sneak outwithout his permission. He treats you like a kid and if you don’t listen tohim, he just picks you up by sheer force. He’s demanding and lets you take careof everything except your safety and the cooking. He prepares meals moredelicious than your chef’s ones. If he’s hungry he becomes scary. You oftenfind him eating snack in front of the computer, earphones on as heplans/develops something new.
Uniform: hehates suits and ties, so you have to force him when needed (+bulletproofjacket). Otherwise he prefers sweatpants/jeans and comfy hoodies.
Weapons: ironknuckles
Skills: Actually,he’s the best hacker around so usually the enemies doesn’t make it past hisdefenses, traps and net of agents. Legends tell he has crashed FBI’s network.He knows plans and attack weeks before they happen. If it comes to close-rangedcombat, he uses two iron knuckles to knock down the threats. His statureintimidate everyone.
Akashi Seijuurou –Codename: “Tenshi”**
Attitude:Why people are threating you if Akashi is your bodyguard? It’s a lost war, hehasn’t been wounded nor he has failed a mission once. He treats you extremelykind and politely until you do as he wants. He knows the best for you and howto keep you safe, so he doesn’t accept “but”. He spoils and indulges in yourwishes until he deems them safe. Everybody both admire and fear him, as you do.Extremely awkward if you treat him with fondness or honest affection, he’s notused. He’s also useless with house chores or common, daily things. He neverkills anyone in front of you, but rumors say he’s ruthless and cold-blooded. Ifsomething shocking happens, he prepares you a hot cup of tea and cuddles withyou on the couch, whispering comforting words.
Uniform: tailoredgrey suit with red tie (+bulletproof jacket); at home tailored black pants andwhite shirts. He’s always very elegant, prince-like. However, when he’s tiredhe wears jeans and big hoodies that make him look younger and cuter.
Weapons: Akatana and a gun.
Skills:The katana is part of his body and he maneuvers it with perfect efficiency andrapidity. He uses the gun during unfair fights or if necessary. He knowsdifferent languages and dialects. He’s also good with rifles and hand-to-handcombat. Has hundreds of contact and underlings. He’s enough brilliant topredict attack and find enemies before they can even think to attack you.Doesn’t mind torture if he needs it.
Kagami Taiga – Codename: “Tiger”
Attitude: Hedoes his best at everything. He’s loyal, brave and incorruptible. Kagami can behot-blooded and short-tempered, often arguing with you about the smallest thing(in a playful way), but he’s going to apologize if he realizes he has hurt youfor real. He’s very warm and friendly, kind at heart, often trespassing theboundaries and being more of a friend or a big brother than a bodyguard. Hegets embarrassed easily by the most innocent insinuations, but since he’s grownup in America he’s pretty comfortable with PDA, he doesn’t even realize he’stouching you. He’s a good housewife, you live well with him. Strict about yoursafety, ready to fight you if he doesn’t agree about something. He would shieldyou with his body. He can be naïve, but he’s able to reassure and comfort youwithout even realizing it, in his faithful honesty.
Uniform: Ifhe has too, a black suit and tie (+bulletproof jacket). Usually he goes withjeans and t-shirts or sweatpants and tank tops…very casual and urban. He looksstylish without trying.
Weapons: Ablack gun and a knife
Skills: Heexcels at hand-to-hand combat and has an awesome aim. More than technique, hisit’s animal instinct. He moves on reflexes and hunches, without stopping tothink or doubt: he acts. Reckless, doesn’t fear anything, high tolerance ofpain. Speaks English perfectly. His glare is scary as much as his height. Verymuscular, he can pick you up without efforts.
Hanamiya Makoto – Codename: “Fox”
Attitude: He’ssly, cunning and vicious. Even if you know he’s not going to betray you,sometimes you’re intimidated. You mustn’t show your fear or he’s going to teaseyou even more. He loves teasing and harassing you in the most subtle ways.Lucky for you, he’s territorial: he’s the only one who can have this attitudewith you. If someone else tries it, Hanamiya will kill him in a matter ofseconds. Too brilliant and smart for you to escape his supervision. He doesn’tcare you’re part of the high society or that you’re the one who hired him: youtry to pull a smart move and he’s going to tie you to the bed.
Uniform: whatyou pick for him, he doesn’t really care. Nothing flashy, he wants to passunnoticed (+bulletproof jacket). At home jeans and sweaters, monochromatic ifpossible.
Weapons: rifle,teaser and pocketknife.
Skills: Prefersto work as a sniper, not a fun of hand-to-hand combat prefers to shock theenemy with the teaser and then killed them with a knife. He’s a strategist andbelieves in “who attack first wins”. Usually he prefers to find your possibleenemies before and then hunt them down. He knows poisons and venoms, not afraidto use them. Incredible faker, he can persuade everyone that he’s a sweetheart.Vast knowledge of everything, from computers to local geography to history togossip to politics… Cold-blooded, loves psychological torture.
Haizaki’s Shougo – Codename: “Mercenary”
Attitude:He’s a mercenary, so make sure you’re really the one who’s paying him the most.Bossy, violent and vulgar. He teases you and harasses you, doesn’t care aboutorders or higher-ups. He does his work well, but nothing more. Until you’rephysical safe, it’s okay. Jealous as hell, he doesn’t want you to praise otherbodyguards or hang out with other guys. He doesn’t mind using illegal ways tokeep you safe.
Uniform: heputs on a suit only if you pay him more or if you compliments him saying himmuch he’s hot with it. (+bulletproof jacket) Otherwise, he wearsjeans/sweatpants and t-shirts with women or English mocking lines.
Weapons: knivesand a gun
Skills:absolutely ruthless and cold-blooded, he basks in violence and likes to physicallytorture his opponents. He…doesn’t feel pain? He never stops, like a machine.Strong and fast, but also cunning; he wants to crash the enemy. Doesn’t mindgetting his hands dirtier and dirtier. He has illegal contacts and shadybusinesses going around.
*“Black Panther”
**“Emperor/Heavenly Being”
#kuroko no basket#knb#bodyguard au#bodyguard!knb#Aomine daiki#kise ryouta#Akashi Seijuurou#Kuroko Tetsuya#Midorima Shintarou#Murasakibara Atsushi#kagami taiga#haizaki shougo#hanamiya makoto#hot bodyguards#the gom#Generation of Miracles#miragen#kiseki no sedai#knb hcs#bodyguard Au hcs
272 notes
·
View notes
Text
Understanding Fund
New Post has been published on https://financeqia.com/financing-news/understanding-fund/
Understanding Fund

Financial seems like a heavy phrase. It is apparently a thing exclusively for huge entrepreneurs or imposing tycoons. This seems to become not much of a take the time to the ordinary man or woman.
If this sounds like the mindset, then it is time for you to modify it. You have to see fund inside a different light to make issues function in a different stage.
Exactly What Is Financing?
Financing may be described in several ways. , fund relates to funds and also to the numerous techniques it could be managed and operated.even so and Largely This is the necessary money to back up an project or further go after a successful enterprise.
As a result, undertaking this classification, financing is a concern for all. It is really not about major businesses only.
Why Is Finance Important?
Financial is vital in any family and also to anyone that includes a future to anticipate. Listed below are the numerous techniques by which finance will likely be considerable:
%u2022Security
Stability is important. This will likely guarantee that regardless of what takes place, there exists some ground to be determined by still.
Suitable credit can certainly make the household protect from your unfavorable possibilities. Like when somebody loses employment, suitable allocation of the money ahead of time should make sure enough money to obtain by even though the occasions are difficult.
%u2022Growth
Fund also has a big part inside the expansion of any effort. In case the owner is able to handle the funds that comes in for a greater organization, as an example, a small business can increase larger.
It is really not adequate to negotiate with only obtaining by in everyday. There ought to be some increase in the pool of assets and prosperity that this household depends on. With this, accomplishment is an important possibility.
%u2022Protection
Good treatments for the economic resources also needs to range from the security. This can be a large requirement, specially for individuals who was able to propagate their resources.
%u2022Stability
Very good financing will help with supplying the individual or maybe the home a reliable potential. Consequently it a contented retirement life can be envisioned.
There are actually no financial obligations or commitments to worry above. You can find no fits or financial obligations to take into consideration. The near future claims simply the plain entertainment of your fruit of the labour.
Correct Funding
There are many methods to put into action an excellent loans structure. It, even so, is dependent upon the circumstances of the person and also of the circumstance.
Here is a selection of some common rules to take care of the funds:
1. Live inside the way of the household. Usually do not devote an excessive amount of about the needless. Bank on the long term very first well before indulging.
2. Save money. Always maintain a area of the practical information on savings uses. Over time, this can provide a bigger swimming pool of wealth to the home.
3. Prevent loans or credit cards whenever possible. There are many techniques which promise good provides on financial loans. Steer clear of this otherwise totally essential. This could only turn into a culpability later on.
4. Generally consider enhancing the current circumstance. This is a need to to move the step ladder to accomplishment.
5. Research meticulously the alternatives. You may have the proper eyesight, but you will need to take the correct steps in the direction of that. This is also a sensible way to avoid spending energy and cash on fruitless goal.
Bottom line
Financing is a make a difference that problems anyone. Accept it seriously.
All privileges set aside. Content material might be reprinted whether it continues to be unaffected and links remain intact.
0 notes
Link
To One It’s Monday to One other It’s Wednesday Time goes so quick every now and then that I carry out no longer consistently take into account what day it’s miles. I opt up so busy looking to determine on up my work achieved that I put out of your mind if it’s Monday or Friday. It’s a factual thing I am increasing outdated because I in truth catch a built-in excuse for forgetting what day it’s miles. Recently, the Righteous Mistress of the Parsonage and I spent some time in St. Louis. Augustine for some scurry back and forth days. We don’t in general opt up to catch scurry back and forth days, but after we provide out, we strive to trip it. Correct down about a blocks from our motel is a region we like dinning. It’s known as the Village Inn. What I admire about this restaurant is that on Wednesdays they consistently catch free pie with anything else you voice even though it’s lovely espresso. Free is constantly a factual thing with me. I know that nothing is free, but every now and then it’s miles. Anyone who is aware of me is aware of that I carry out no longer have interaction many issues seriously. I enjoyed being spherical those which are very seriously minded because I will be succesful to opt up away with one procedure of jokes with them. Some issues are to be serious, but those are somewhat few in my book. Even at my age, I rob to catch enjoyable. It modified into a Monday on our scurry back and forth that we went staunch down to catch lunch on the Village Inn. Someone once asked me what my favorite pie modified into, and I gave them an answer that my uncle consistently gave, “The one I’m drinking on the time.” And this restaurant has very delectable pies. It modified into Monday, on the opposite hand, and the pies had been free finest on a Wednesday. That didn’t cease me from making an attempt, though. The restaurant host escorted us to our table, and we sat down. Then the waitress came to have interaction our voice. It modified into then that I had a idea laughing on the discontinue of my head. That is constantly a foul distress. I decided to switch with it. “Ma’am,” I acknowledged as seriously as I presumably would possibly well presumably, “I am a Yahooist, and in line with our religion, your Monday is our Wednesday.” I am certain she by no arrangement heard of a Yahooist because I by no arrangement heard of one either. She regarded somewhat strangely at me, and I persisted, “Does that imply I will be succesful to catch the Wednesday free pie this day?” Trying at me for about a moments, she then broke out in laughter. I impart she knew I modified into joking. “A Yahooist, you impart.” Then she took our voice and went to the kitchen. I heard some laughter coming from the kitchen region when she went encourage, and each waitress that walked by our table regarded at me and acknowledged, “Yahoo.” One thing I strive for every day is making someone smile if no longer train. There are such a wide amount of unhappy of us in this world that I am looking to determine on up them from being so unhappy. I in truth catch found that it doesn’t have interaction very noteworthy to determine on up some of us to train. Then the manager came to our table and acknowledged, “So, you’re a Yahooist. How would possibly well presumably I be half of that religion?” Sparkling that he modified into lovely having a minute enjoyable with me, I spoke back very seriously, “To affix or no longer it’s miles well-known to swear ‘Yahoo’ three times in a row and then ship me a free fragment of pie.” I carry out no longer let anything else opt up past me if I will be succesful to avoid it. The manager laughed somewhat heartily and then walked encourage to the kitchen. Per chance I will catch to level-headed think a minute extra seriously about increasing a Yahooist neighborhood of of us. We certain would possibly well presumably assemble one procedure of of us smile and train that otherwise would no longer carry out any of that. Then our waitress came encourage with our meal and greeted both of us by announcing, “Yahoo.” Then my wife and I shouted “Yahoo” encourage, and all the possibilities spherical our table began to train and impart, “Yahoo.” As my wife and I had been drinking our lunch, I idea that I had done my cause for the day. I admire making of us train and smile. That is what I call a factual day. I know I will be succesful to’t assemble all people smile or train, but I will be succesful to assemble some of us and folk of the of us I focal level on. As possibilities departed and handed our table, they all smiled and acknowledged, “Yahoo.” I will be succesful to’t take into account when I had a greater day. As we had been finishing our meal, the waitress brought our designate to the table. She commented by announcing, “It certain modified into nice to meet an actual Yahooist. I am hoping you return again.” Then, as she left, she chirped, “Yahoo.” “You certain made an affect along with her,” my wife commented. As I regarded on the designate, I realized that the pie we ordered modified into no longer on our designate. For some motive, she forgot to consist of it on our designate. I known as her encourage and asked about why the pie modified into no longer included on my designate. “Isn’t this day your Wednesday?” she acknowledged. “On Wednesday, the pie is constantly free.” As she walked away, she cheerfully acknowledged, “Yahoo.” I in truth catch found that it consistently can pay, and would possibly well presumably pay wonderfully, to assemble someone smile. The theme of my life is, “A merry coronary heart maketh a blissful countenance: but by sorrow of the coronary heart the spirit is broken” (Proverbs 15: 13). My arrangement is by no technique to let a day scurry by without causing someone to smile. @glstock HOME @glstock PLOG @glstock AMAZON WATCHES STORE @glstock AMAZON PHONES STORE @glstock AMAZON TOOLS STORE @glstock Related ProductsLoading products..
0 notes
Text
Top Web-Site Security Menace And How to Protect Your-Self From Such Cyber-Invasion

You can’t take Web-Site security menace seriously enough especially if your customers entrust you with their credit card information and other sensitive data. From using strong passwords to defending your site against images that Cyber-Invasion, taking the important steps necessary to protect your website from cybersecurity menaces. This article will take a deep dive into the most prevalent Web-Site security menace, and outline some steps you can take to remain vigilant against them. Here’s what we’re going to cover:
WordPress And Web-Site Security Menace
The report shows that WordPress continues to lead the infected CMS pack and the worst part is that it powers more than one-third of all Web-Sites on the internet. In addition to that, WordPress has to command over 60% of shares of all open-source content management systems. Word-Press is extremely popular on the web-world, hence it painted a huge target on its back.
Cyber Security Menace For Small Business Web-Sites
However, it’s important to know that Web-Site security Cyber-Invasions aren’t necessarily targeted at specific Web-Sites. In most attempts of Cyber-Invasion, the Cyber-Criminals aren’t actively seeking out any Web-Site in particular, which is why even small Web-Sites get invaded. The Cyber-Criminals normally employ bots to sniff out vulnerabilities, and once one is found, the Cyber-Criminals jump in to do some damage. A recent study showed that 58% of small businesses are most vulnerable to cyber-Invasion by a virus. Many studies display that small business is number one on Cyber-Criminal’s hit-list. But only 30% of businesses regularly check for vulnerabilities, and 40% rarely do. Small businesses are most vulnerable to Web-Site security menace simply because they don’t usually have enough security acumen nor do they have enough budget or time to devote to Web-Site security compared to many large corporations.
Effects of Cyber-Invasion On Businesses
By now, you should have a basic understanding of why Web-Site security is important.
But to make things even more clear, let’s take a look at some of the negative effects that a business might experience after experiencing a Cyber-Invasion:
Financial loss
Nearly half of small businesses are suffering from a financial loss from Cyber-Invasion, with one out of eight saying that the loss was greater than $5,000.
You might notice that there’s a bit of a paradox for small businesses dealing with Cyber-Invasions. In most cases, small businesses don’t have enough money for Web-Site security, yet when faced with a Cyber-Invasion, they are often advised to pay up, even when those Cyber-Invasionscause financial losses. Even worse, Security magazine reports that 60% of compromised small businesses go out of business within six months.
Reputation Damage
If any business experiences a Cyber-Invasion which threatens their customer’s personal information, then it comes under their duty to inform their client regarding that problem. If you’ve ever been a customer whose data has been exposed after trusting a company to handle it properly, you realize how this can jeopardize business relationships.
Blacklisting By Search Engines
Web-Sites compromised by Cyber-Invasion are often blacklisted by search engines or internet security companies. It can have major negative effects on the business, which mainly rely on search engine traffic.
Types of Cyber Security Menace And Virus Families
Virus families allow our team to assess cyber-criminals tactics, techniques, and procedures (TTP), the authors write. This information inevitably leads us to their intentions and helps us understand and mitigate future menace. Virus families and another notable Web-Site security menace both highlighted in the report and beyond, include:
Backdoors
From Backdoors strike the Cyber-Criminals can achieve unauthorized access and rights to a system or network after a successful compromise. In addition to that, it also provides them with the opportunity to breach modern Web-Site scanning technologies and acquire access to controls of web server environments. This makes them one of the most commonly missed payloads and a leading cause of reinfections.
Virus
Virus, short for “infected programs,” is a generic term exercised for intrusive code that tries to take control of your Web-Site in some way. Forms of the virus include Trojan horses and drive-by downloads.
SEO spam
SEO spam is the culprit in more than 51% of all the infection cases and 7% increase from the year before. Detecting SEO spam is extremely complex and they have a strong economic engine driven by impression-based affiliate marketing, making it the fastest-growing threat to the web-world.
Mailers
Mailers are spam-generating tools designed to exploit server resources, allowing Cyber-Criminals to send unwanted emails from a domain. These forms of the virus can wreak havoc by distributing infection via phishing campaigns and stealing sensitive information.
Tool Employed In Compromising Security
SQL Injections
SQL injections are web security vulnerabilities that allow bad actors to interfere with a query an application makes to its Data-Archives.
Cross-Site Scripting (XSS)
Cross-Site Scripting is a type of Cyber-Invasions that happens when infected scripts are inserted into an otherwise trusted Web-Site with the intent of stealing the client’s identity data through cookies, session tokens and other information.
Distributed Denial of Service (DDoS)
When a Cyber-Criminals try to manipulate normal traffic of a specific server, service or network by overwhelming the server by generating fake internet traffic, employing botnets.
Defaced
Cyber-Invasionleaves a Web-Site’s home page unusable and promotes an unrelated subject.
Phishing
It is the type of scam where a fraudster sends fake emails, pretending to became from a legitimate company or an organization.Once the client falls for this trick, then they would end up providing sensitive information like credit card and login credentials to the unknown fraudster.
Dropper
This is a type of virus that drops infected codes into a targeted system. The virus’s code is contained within the dropper.
Banking Trojans
Banking Trojans focus on stealing bank account logins. Examples include Citadel and Zeus.
Keyloggers
Keyloggers steal anything that’s typed on a keyboard or touchscreen.
Ransom-ware
Ransomware encrypts data then ransoms its release. One example is the Cyber-Invasion that struck the city of Atlanta.
Exploit Kits
Exploit kits give cyber crooks virus upload options.
Bots
Bots take control of the infected system to assist in other crimes.
Drive-By Downloads
Drive-by downloads are unintentional downloads of infected code that open the door for security breaches on apps, operating systems or web browsers.
Advanced Persistent Menace
Advanced persistent menaces are a type of Cyber-Invasions that usually involves virus.
Understanding And Prevent Strike By SQL Injections
The SQL injection is a web security vulnerability that allows Cyber-Criminals to interfere with a query an application makes to its Data-Archives.
Why SQL Injections Are Harmful
Many Web-Sites and web applications store their data in SQL Data-Archives. Sometimes, you can practice SQL commands to run operating system commands. When a Cyber-Criminal gets access to the SQL Data-Archives, they can view and modify data they normally aren’t able to retrieve or access, which includes data belonging to clients, or data that the application has access to. The Cyber-Criminals can modify or delete data, or even grant themselves admin access. In some cases, you can even access the operating system using the Data-Archives server. When Cyber-Criminals get access to this, they can invade the internal network behind a firewall.
How SQL Injections Work
Cyber-Criminals find vulnerable input fields on the Web-Site and insert content via an SQL query. This is often called infected payload and is a key part of the Cyber-Invasion. After the Cyber-Criminal sends this content, infected SQL commands are executed in the Data-Archives.
Types of SQL Injections
There are three types of SQL injections:
In-Band SQLi
The most common and easy to exploit SQLi, in-band SQLi is when the Cyber-Criminal is able to employ the same communication channel to launch the Cyber-Invasion and gather results.
The two most common types of in-band SQLi are error-based SQLi and Union-based SQLi:
Error-based SQLi: Errors can be beneficial to develop the phase of a Web-Site, but should be disabled on a live Web-Site. This type of SQLi relies on error messages thrown by the Data-Archives server to obtain information about the structure of the Data-Archives.
Union-based SQLi: Leverages the UNION SQL operator to combine the results of two or more SELECT statements into a single result, which is returned as part of the HTTP response.
Blind/inferential SQLi
This type of Cyber-Invasions takes much longer than an in-band SQLiCyber-Invasions. This type of Cyber-Invasions, no data is actually transferred via the web application and the Cyber-Criminal isn’t able to see the result of the Cyber-Invasion in-band (that’s why it’s called blind SQLi). Instead, the Cyber-Criminal is able to reconstruct the Data-Archives by sending payloads and then observing the web application’s response and the resulting behavior of the Data-Archives server.
Types of blind SQLis:
Boolean-Based/Content-Based Blind SQLi: In this, the Cyber-Criminal sends an SQL query to the Data-Archives, in order to force the application to achieve a different result depending on whether the query returns a False or True result.
Time-Based Blind SQLi: This type of Cyber-Invasion forces the Data-Archives to wait for a specific amount of time (in seconds) before responding. Depending on the result, the HTTP response may be returned immediately or with a delay, and the Cyber-Criminal can infer whether the strike was TRUE or FALSE based on how long the result took.
Out-Of-Band SQLi : Of the three types of SQLi, this is the most uncommon because it depends on the features being enabled on the Data-Archives server being employed by the web application. This type of SQL injection occurs when the Cyber-Criminal is unable to employ the same channel to launch the Cyber-Invasion and gather results. This type of Cyber-Invasion is an alternative to inferential SQLi, especially if the server responses are not stable.
How To Prevent SQL Cyber-Invasions
Determine whether your Web-Site is vulnerable by launching your own SQL Cyber-Invasion on your Web-Site to see whether they are successful. You can practice an automated SQL injection strike tool such as Havij, SQLmap or jSQL. Besides dealing with vulnerabilities on your own, make sure to also employ a web application firewall (WAF).
Understanding And Preventing Cross-Site Scripting (XSS)
Cross-Site Scripting is a type of Cyber-Invasion that happens when infected scripts are inserted into an otherwise trusted Web-Site with the intent of stealing the client’s identity data through cookies, session tokens and other information. It’s important to have an understanding around these types of Web-Site security menace, as 84% of vulnerabilities are a result of XSS Cyber-Invasions.
Why Cross-Site Scripting is Bad
At this very moment your browser will be helpless and it will lose its ability to differentiate between a trusted script and infected script. Unlike other web Cyber-Invasions, XSS targets its clients and not your web application, causing harm to your clients and reputation
Why Cross-Site Scripting happens
Many developers automatically trust all clients to the point that they don’t make an extra effort when it comes to filtering client input. There are many variants of an XSS Cyber-Invasion, so the application gets confused regarding what to filter.
How Cross-Site Scripting Works
Cyber-Criminals inject client-side scripts into web pages viewed by other clients through a vulnerable point. Once the client visits the Web-Site or clicks on the link, the infected string of code from the Data-Archives is sent in response. The victim’s browser then executes the infected script.
Types of Cross-Site Scripting Cyber-Invasions
Cross-Site Scripting can take on many different forms of infection, including:
Non-Persistent/Reflected Cyber-Invasions
The Cyber-Criminal usually sends a link containing an infected code or exploits a form on the Web-Site. These Cyber-Invasions may be sent to a victim with the intention of stealing their session cookies and ultimately their account. But compared to other XSS Cyber-Invasions, these are much less dangerous. This is because reflected Cyber-Criminals rely on a victim taking action, making it hard to automate. For the Cyber-Invasion to be successful, each victim must be targeted individually.
Persistent/stored Cyber-Invasions
The Cyber-Criminals sends infected data to a Web-Site stored in Data-Archives. When the client visits the Web-Site, they are served the data that performs infected action. Compared to reflect cyber-Invasions, these can be automated. A script can be created that visits thousands of Web-Sites, exploits the vulnerability on each Web-Site, and drops the stored XSS load. In this case, the Web-Site’s visitor does not have to do anything but visit the Web-Site to get infected. Needless to say, the persistent Cyber-Invasion affects more people.
Document Object Model (DOM) Cyber-Invasion
The Cyber-Criminals modifies the DOM environment of the client’s browser, the result of exploiting the original client-side JavaScript hardcoded into the Web-Site. While uncommon, this Cyber-Invasion is difficult to address because it usually occurs on the client-side. During these strikes, the HTTP response of a page is not changed and no unique data is sent to the server.
How to Prevent Cross-Site Scripting
In some cases, preventing an XSS Cyber-Invasions can be as simple as adding an HTML code to your Web-Site.
Here’s how to protect yourself:
Encoding: In a nutshell, encoding is when you strip client input of all code and force web browsers to interpret that input only as data. The end result is rendered as text on both the client-side and server, instead of being rendered in JavaScript, CSS, HTML or as URL.
Validation: the process where one makes sure that the data matches their expectations.
Sanitization: Involves cleaning up all data entered by a client. Many code libraries and e-Commerce platforms do this by default. The problem with this is that it can limit what a client can enter. Info-sec shares a list of data that needs to be sanitized as well as for instructions on how to sanitize your data.
Understanding and Preventing Cyber-Invasions By Virus
A virus is a portmanteau of infected words and programs. It’s an intrusive code (normally installed via a corrupted file packaged with healthy programs) that tries to take control of your Web-Site in some way.
A virus can take on many forms:
Viruses: The most common form of virus, often found in email attachments.
Trojan horses: Also known as a backdoor virus, it is disguised as a legitimate program but can take control of your system once installed.
Driveby downloads: Here an invader employs your Web-Site to delivery other corrupted files and can cause damage without the recipient knowing.
Ransom-ware: A kind of Cyber-Invasion where criminals hold data hostage until a payment is made.
How Virus Operates
A virus spreads when you download or install infected programs. It can also enter your system via a link or email. Once installed, it replicates fast and can immediately spread to another system in the network. The virus can affect PC performance, resulting in a slow PC response. It can also consume internet data: if your internet usage is higher than normal, you might be infected with a virus. It can interfere with system activities by generating unwanted popups and ads. It can destroy system programs and the system’s operating system. In addition to that, a virus can steal personal information or encrypt your files and then it would force you to pay for an encryption key to unlock them.
How To Prevent Virus-Strike
Bad news first: most of the time, you won’t be informed if you were infected by a virus, though some Web-Sites warn you before allowing you to navigate to an infected Web-Sites. If you’ve been infected by a virus, always seek help from a dedicated tool to find and remove a virus from your Web-Site.
How To Protect Your Web-Site From Virus
There’s not a lot you can do after the fact, which means you must be proactive. One should always employ a Web-Site monitoring service to regularly scan your Web-Site for virus and other vulnerabilities. Keep monitoring your Web-Site, scan your downloads for viruses and verify if the links you click are safe. One should not forget to follow each and every security measure.
Understanding And Preventing Distributed Denial Of Service (DDoS) Cyber-Invasions
A Denial-of-Service (DoS) Cyber-Invasion is a state where a Cyber-Thief tries to block the access of legitimate users from system information, devices or other network resources. Services affected may include email, websites, online accounts and other services that rely on the affected system or network. A (DoS) Cyber-Invasion is executed by a Cyber- Thieves by flooding the victim’s network with abnormal traffic until the target loses their ability to respond and simply crashes or the authentic users fail to access the server. DoS Cyber-Invasion can cost an organization both time and money while their resources and services are inaccessible.
How Distributed Denial of Service Works
A DDoS Cyber-Invasion requires a Cyber-Criminal to gain control of a network of online machines in order to carry out anCyber-Invasion. System and other machines (such as IoT devices) are infected with a virus, turning each one into a bot which the Cyber-Criminal has control over. The Cyber-Criminal collects a network of bots, which is called a botnet. Once a botnet is established, the Cyber-Criminal controls the botnet by sending updated instructions to each bot via a method of remote control. Once a botnet targets the victim’s IP address, then every bot will keep firing requests on the target’s server till it reaches maximum capacity and crashes.Because each bot is a legitimate internet device, separating the invaded traffic from normal traffic can be difficult.
Types Of Distributed Denial Of Service Cyber-Invasions
There are 12 types of DDoS Cyber-Invasions, falling under these three main categories:
Volume-based Cyber-Invasion creates congestion by consuming all available bandwidth between the target and the larger internet. These represent the most common Cyber-Invasions for botnets.
Protocol Cyber-Invasions
This type of Cyber-Invasion is also called as state-exhaustion, they normally create a service disrupt by occupying all the space available on the server or intermediate resources such as load balancers and firewalls.
Application Layer Cyber-Invasions
This is the most sophisticated type of DDoSCyber-Invasions, named after the seventh layer of the network device where the human-system interaction occurs, and applications can access network services. The goal of the Cyber-Invasions is to exhaust the resources of the target, which can be costly to the server-side. These Cyber-Invasions typically leverage flaws in a Web-Site application’s code and exploit it in ways that overwhelm the system. By this process, they are simply miss-guiding the system into assuming that they are receiving genuine web-traffic when it’s actually just traffic from botnets. These types of Cyber-Invasions are hard to defend as the traffic can be difficult to flag as infected. If you think that only large Web-Sites are targeted and your small Web-Site is exempted, think again. Cyber-Criminals have different motivations: They can either target Web-Sites they hold grudges against or want to get a ransom from, or they might just want to target a random Web-Site. In any case, it’s always best to be prepared. If your Web-Site experiences slow traffic and traffic is generated by a bot, your Web-Site may have been hosted on the same server as a targeted Web-Site.
How To Prevent Distributed Denial Of Service Cyber-Invasions
Here are a few things to do to protect your Web-Site from DDoS Cyber-Invasions:
Monitor Your Web Traffic
If you will have the knowledge of your normal traffic rate, then it will help you to differentiate between genuine traffic and fake traffic created by botnets and once you know your normal traffic rate, then you can limit it to accept requests as per the maximum capacity of the server. While you’re at it, get a little bit more bandwidth than you actually need.
Install a Web Application Firewall (WAF)
A firewall can analyze traffic before it reaches your Web-Site and it can also protect your Web-Site from botnet traffic surges and other infected content.
Distribute Your Network Infrastructure
Don’t put all your eggs in one basket. By keeping multiple network resources, you have backups when one is being invaded.
#Secure#cybersecurity#security#web development#Webmaster#web design#blog#webdesign#web developing company#web developers#technologies
0 notes