#SOC analysts
Text
Hiya, I feel like I’ve not been doing as much analysis in here recently and I realise that’s probably why most of you follow me so sorry about that, I have quite a lot of ideas but the analysis posts tend to take a long time to write and so I thought I’d do a quick poll to see what you guys would prefer I focus on :)
My intention is to do all of these at some point but if I know which one people are most interested in then it gives me something to focus on
Explanation of options beneath cut
1) I’ve posted a quote-by-quote analysis of chapters 2, 3, and 4 of Six of Crows and have started but not yet fully written one of chapter 5 so I’d love to carry that on and I would also be happy to go back to chapter one if anyone wanted to read that. I love writing these and I would also say that my Crooked Kingdom Bathroom Scene analysis post is quite similar to these ones since I went quite by quote for the second part of that analysis.
2) Fairly self explanatory I guess but I have a lot of asks that have been sitting in there for a long time now and I’m so sorry to have kept people waiting
3) I have talked about minor characters in detail within posts, such as Rojax and Alys, and I have written a full analysis on Bajan but I think it would be really interesting to do a fully structured series on minor characters, you guys could vote for who you wanted next, and also being able to expand in more detail than I have done before on some of these folks might be really fun
4) Honestly I expect this will continue alongside anything else anyway because I feel like there’s always more to discover in these books and I’m always realising something new, it’s wonderful
Also: would people be interested if I brought my fan-written Soc spinoff script back? I had so much fun writing it but I’ve had a lot in and been focused on writing my fic so I’ve not written anything beyond the first two parts I already posted, but I really love the idea so yeah if anyone’s interested I’m more than happy to bring that back.
Thanks guys! 🖤
#grishaverse#six of crows#crooked kingdom#leigh bardugo#soc analyst#soc analysis#soc analysts#six of crows analysis#six of crows meta#crooked kingdom meta#she posts nerdy stuff
34 notes
·
View notes
Text
SOC Success Stories: Lessons from Cybersecurity Frontlines
Introduction to SOC (Security Operations Center)
Welcome to the thrilling world of cybersecurity! In an era where digital threats loom large, organizations are arming themselves with powerful tools and strategies to safeguard their sensitive information. One such weapon in their arsenal is the Security Operations Center (SOC), a formidable force that stands as a beacon of protection against cyber attacks.
But what exactly is SOC? Well, SOC stands for Security Operations Center - a centralized unit within an organization tasked with monitoring, detecting, and responding to security incidents. Think of it as the nerve center, where skilled analysts work tirelessly round the clock to keep your data safe from malicious actors.
In this blog post, we will explore the importance of having a SOC in today's digitized landscape. We'll dive into real-life success stories that highlight how these teams have thwarted sophisticated attacks and saved countless organizations from potential devastation. So buckle up and get ready for some edge-of-your-seat tales from the cybersecurity frontlines!
Importance of a SOC for Organizations
In today's digital world, the importance of cybersecurity cannot be overstated. With cyber threats becoming increasingly sophisticated and widespread, organizations need to have robust measures in place to protect their sensitive data and systems. This is where a Security Operations Center (SOC) comes into play.
A SOC is a dedicated team within an organization that focuses on monitoring, detecting, analyzing, and responding to security incidents. It serves as the central nervous system for an organization's cybersecurity efforts. The primary role of a SOC is to keep a constant watch over the network infrastructure, applications, and endpoints to identify any potential security breaches or suspicious activities.
By having a SOC in place, organizations can proactively defend against cyber attacks rather than being caught off guard and reactive when an incident occurs. A well-functioning SOC helps minimize downtime by swiftly identifying and mitigating threats before they can cause significant damage.
Moreover, a SOC plays a crucial role in ensuring compliance with industry regulations such as GDPR or PCI DSS requirements. By monitoring network traffic and conducting regular vulnerability assessments, the SOC helps organizations meet regulatory standards while maintaining data integrity and confidentiality.
Another key aspect of the importance of a SOC lies in its ability to provide valuable insights through threat intelligence analysis. By continuously collecting information about emerging threats from various sources like dark web monitoring or threat feeds from vendors, the SOC can stay one step ahead of potential attackers.
Additionally, having an internal team responsible for managing cybersecurity allows for better coordination between different departments within an organization. The communication channels established within the SOC enable faster response times during incidents and facilitate collaboration among IT teams across different locations or business units.
Real-life Examples of SOC Success Stories
1. Foiling a Sophisticated Phishing Attack
One success story involves a Security Operations Center (SOC) team that successfully prevented a sophisticated phishing attack on a large financial institution. The SOC analysts detected anomalous network traffic and quickly identified the malicious email campaign targeting employees. By promptly alerting the organization's IT department, they were able to take immediate action to block the malicious links and prevent potential data breaches.
2. Unraveling an Insider Threat
In another instance, a manufacturing company faced an insider threat from one of its disgruntled employees who intended to sabotage critical systems. Through continuous monitoring and analysis of user behavior within the network, the SOC team noticed unusual activity associated with this employee's account. They swiftly intervened, disabling the account before any damage could occur.
3. Swift Response to Ransomware Attack
A healthcare provider was hit by a ransomware attack that encrypted vital patient records across their network infrastructure. Thanks to their well-prepared SOC team, they were able to respond swiftly and effectively mitigate the impact of the attack. The SOC analysts isolated affected systems, restored data from secure backups, and implemented additional security measures to prevent future incidents.
These real-life examples highlight how Security Operations Centers play a crucial role in safeguarding organizations against various cyber threats by employing proactive monitoring techniques, advanced analytics tools, and skilled personnel capable of rapid response when incidents occur.
Collaboration and Communication within the SOC
Collaboration and communication are the lifeblood of a successful Security Operations Center (SOC). In an environment where threats can evolve rapidly, SOC teams must work together seamlessly to detect, respond to, and mitigate cyber incidents.
Within the SOC, analysts from different specialties come together to form a cohesive team. This diversity of skills and perspectives allows them to tackle complex security challenges from various angles. Whether it's network monitoring, threat intelligence analysis, or incident response, each member plays a vital role in safeguarding the organization's assets.
Effective collaboration within the SOC involves constant information sharing. Analysts must communicate findings, share insights, and update their colleagues on ongoing investigations. This real-time exchange of knowledge helps identify patterns and trends that might otherwise go unnoticed.
Furthermore, collaboration extends beyond just internal teamwork within the SOC. It also entails close cooperation with other departments such as IT support or legal teams. By fostering strong relationships with these stakeholders across the organization, SOC analysts can gain valuable context about potential risks and vulnerabilities specific to different business units.
Communication channels within the SOC should be streamlined yet flexible. Regular meetings or huddles provide opportunities for analysts to discuss emerging threats or brainstorm solutions collectively. Additionally, technology tools like chat platforms enable instant messaging for quick updates during critical incidents.
Collaboration and communication lie at the heart of every successful SOC operation. By working closely together and sharing information effectively both internally and externally with other departments in an agile manner; organizations can enhance their overall cybersecurity posture while staying ahead of ever-evolving threats.
Conclusion
In today's ever-evolving digital landscape, organizations face constant threats to their cybersecurity. To protect themselves from these risks, many organizations have implemented Security Operations Centers (SOCs). These centralized hubs of expertise and technology play a vital role in defending against cyber attacks and ensuring the overall security posture of an organization.
Throughout this article, we have explored the importance of SOC for organizations and shared real-life success stories that highlight the effectiveness of these centers. From preventing major data breaches to detecting advanced persistent threats, SOCs have proven time and again their value in safeguarding sensitive information.
One key factor contributing to the success of SOCs is collaboration and communication within the team. The seamless exchange of information between analysts, incident responders, threat intelligence experts, and other stakeholders enables faster response times and more effective incident handling. This teamwork ensures that all relevant insights are considered when making critical decisions during a security incident.
While there is no one-size-fits-all approach to building a successful SOC, these success stories provide valuable insights into what works best in different scenarios. Organizations can learn from these examples by adopting similar strategies such as leveraging automation tools, investing in continuous training for SOC analysts, conducting regular threat-hunting exercises, and fostering strong partnerships with external entities like law enforcement agencies or industry peers.
2 notes
·
View notes
Text
Oh lord, those alerts will slow down a bit?
Like, did people forgot how to use a fucking pc in a weekend?
#ada.txt#now i understand why SOC analysts are all burned out#I'm going to join them soon#lol#i hope not
3 notes
·
View notes
Text
Enhancing IT Security: Strategies and Best Practices

Introduction:
In the contemporary digital landscape, where businesses and individuals heavily rely on interconnected systems, ensuring robust IT security is paramount. The exponential growth of cyber threats poses significant challenges to organizations of all sizes, requiring proactive measures to safeguard sensitive data, protect privacy, and maintain operational integrity. This article explores the importance of IT security, key challenges, and effective strategies to fortify digital defenses.
Importance of IT Security:
IT security encompasses a range of measures designed to safeguard digital assets, including hardware, software, networks, and data, against unauthorized access, breaches, and cyber attacks. The consequences of security breaches can be severe, leading to financial losses, reputational damage, legal liabilities, and compromised customer trust.
With the proliferation of connected devices, cloud services, and sophisticated attack vectors, the attack surface has expanded, making organizations more vulnerable to exploitation. Consequently, investing in robust IT security frameworks is essential to mitigate risks and ensure business continuity in an increasingly volatile threat landscape.
Key Challenges in IT Security:
Despite advancements in security technologies, organizations face several challenges in maintaining effective IT security:
1. **Sophisticated Threat Landscape**: Cybercriminals leverage advanced techniques such as malware, ransomware, phishing, and social engineering to infiltrate networks and compromise systems.
2. **Insider Threats**: Malicious insiders or negligent employees pose significant risks to organizational security by intentionally or inadvertently disclosing sensitive information or engaging in malicious activities.
3. **Compliance Requirements**: Organizations must adhere to regulatory mandates and industry standards governing data protection and privacy, such as GDPR, HIPAA, PCI DSS, and SOX, which impose stringent requirements and penalties for non-compliance.
4. **Resource Constraints**: Limited budgets, shortage of skilled cybersecurity professionals, and competing priorities often constrain organizations' ability to implement comprehensive security measures.
Strategies for Enhancing IT Security:
To address these challenges and bolster IT security posture, organizations can adopt the following strategies and best practices:
1. **Risk Assessment and Management**: Conduct regular risk assessments to identify potential threats, vulnerabilities, and impact on critical assets. Develop risk management frameworks to prioritize mitigation efforts and allocate resources effectively.
2. **Implement Multi-Layered Defense Mechanisms**: Deploy a multi-layered approach to security, combining preventive, detective, and corrective controls at the network, host, and application layers. This includes firewalls, intrusion detection systems (IDS), antivirus software, endpoint protection, encryption, and access controls.
3. **User Education and Awareness**: Foster a culture of security awareness among employees through training programs, workshops, and simulated phishing exercises. Educate users about common threats, phishing scams, password hygiene, and best practices for safeguarding sensitive information.
4. **Regular Software Patching and Updates**: Keep software, operating systems, and firmware up-to-date with the latest security patches and fixes to address known vulnerabilities and mitigate potential exploitation by attackers.
5. **Secure Configuration Management**: Harden system configurations, disable unnecessary services, and enforce least privilege access controls to minimize the attack surface and limit the impact of security incidents.
6. **Data Encryption and Privacy Controls**: Encrypt sensitive data both in transit and at rest using robust encryption algorithms and cryptographic protocols. Implement data loss prevention (DLP) solutions and access controls to prevent unauthorized disclosure or misuse of confidential information.
7. **Incident Response and Contingency Planning**: Develop incident response plans outlining procedures for detecting, analyzing, and responding to security incidents promptly. Establish communication channels, escalation paths, and recovery strategies to minimize downtime and restore normal operations.
8. **Continuous Monitoring and Auditing**: Deploy security information and event management (SIEM) solutions to monitor network traffic, detect suspicious activities, and generate real-time alerts. Conduct regular security audits, penetration testing, and vulnerability assessments to identify weaknesses and remediate security gaps proactively.
Conclusion:
In conclusion, prioritizing IT security is imperative for organizations to mitigate cyber risks, protect critical assets, and preserve stakeholder trust in an increasingly interconnected world. By adopting proactive measures, leveraging best practices, and fostering a culture of security awareness, organizations can strengthen their resilience against evolving threats and maintain a competitive edge in today's digital landscape. Remember, in the realm of cybersecurity, vigilance and preparedness are key to staying one step ahead of adversaries and safeguarding the integrity of digital ecosystems.

#Cybersecurity Analyst#Information Security Specialist#IT Security Consultant#Network Security Engineer#Security Operations Center (SOC) Analyst#Penetration Tester (Ethical Hacker)#Chief Information Security Officer (CISO)#Security Architect#Security Compliance Officer#Incident Response Analyst
0 notes
Text

1 note
·
View note
Text
Best Cybersecurity Institute in Mumbai

Cybersecurity is one of the most important and in-demand skills in today's digital world. With the increasing threats of cyberattacks, data breaches, and identity theft, organizations need professionals who can protect their systems, networks, and data from malicious hackers. But where can you learn the skills and knowledge to become a cybersecurity expert?
PathGlow Edulab in Mumbai is the answer. PathGlow is an industry-focused centre of excellence that trains and develops skilled professionals in the software testing and cybersecurity domain, with 100% placement assistance. PathGlow offers a range of courses and certifications that cover the latest and most relevant topics in cybersecurity, such as:
- Certified SOC Analyst: This course prepares you to monitor, detect, analyze, and respond to cyber incidents using a Security Operations Center (SOC). You will learn how to use various tools and techniques to identify and mitigate threats, as well as how to communicate and collaborate with other security professionals.
- Certified Network Defender: This course teaches you how to design, implement, and manage secure networks using best practices and standards. You will learn how to secure network devices, protocols, services, and applications, as well as how to perform network vulnerability assessment and penetration testing.
- Ethical Hacking: This course introduces you to the concepts and methodologies of ethical hacking, or hacking for a good cause. You will learn how to scan, test, hack, and secure systems and networks using various tools and techniques. You will also learn how to think like a hacker and anticipate their moves.
- Certified Hacking Forensic Investigator: This course equips you with the skills and knowledge to investigate cybercrimes, analyze digital evidence, and respond effectively. You will learn how to use various forensic tools and techniques to recover data, trace sources, and solve cases. You will also learn how to deal with different types of cybercrimes, such as Dark Web, IoT, and Cloud investigations.
These are just some of the courses that PathGlow offers. All of them are designed by industry experts and delivered by experienced trainers in a best-in-class environment. You will get hands-on training on live projects, real work simulations, and cutting-edge tools and methodologies. You will also get guidance on resume building, interview preparation, and career counselling.
PathGlow is not just a training institute; it is a launchpad for your career in cybersecurity. By joining PathGlow, you will become part of a community of learners and professionals who share your passion and vision. You will also get access to a network of employers who are looking for talented and certified cybersecurity professionals.
PathGlow also provides software testing courses for those who want to pursue a career in quality assurance. Software testing is another crucial skill that ensures the functionality, reliability, and security of software products. PathGlow's software testing courses cover topics such as manual testing, automation testing, performance testing, security testing, agile testing, and more.
Whether you want to become a software tester or a cybersecurity pro, PathGlow is the best place to start your journey. PathGlow is the best cybersecurity institute in Mumbai that offers quality education at affordable prices. Don't miss this opportunity to join PathGlow and become a full-stack software tester & cybersecurity pro!
Visit their website https://www.mypathglow.com/ for more information.
#cyber security traning in ghatkopar#cyber security course n ghatkopar#cyber security soc analyst training
0 notes
Photo

An SOC analyst is responsible for being the main point of contact for tracking and avoiding digital attacks, tracking network activities to ensure no suspicious activities take place, working with sales or HR teams to secure and correct issues and report new learnings about existing cyber threats and vulnerabilities.
0 notes
Text
SOC Analyst Online Training Course
Cybersecurity is important now more than ever, and Lorcam Securities has got you covered! Our SOC Analyst Online Training Course offers a comprehensive curriculum that covers the fundamental principles and techniques of security operations. You'll gain hands-on experience on threat hunting, incident response, and more, all done in a convenient online setting. Start your journey towards becoming a security expert and join our training course today!
0 notes
Text
Thinking about how the Dregs canonically have a pleasure house but Kaz vehemently had nothing to do with it even when he was involved in the finances of all their other businesses, and that shutting it down was probably one of the first things he did after the coup
See below cut for evidence/quotes and lil smidgen of analysis
In chapter 3 Van Eck calls Kaz “a bawd and a murderer”, to which Kaz replies “I don’t run whores, and I kill for a cause”. Whilst the more obvious implication of this would be that the Dregs isn’t affiliated with a pleasure house, we learn later that this assumption is incorrect. When Kaz pays off her contract Inej believes she’s moving to another house and Heleen replies “Haskell does own a pleasure house, somewhere in the lower Barrel, but you’d be a waste of his money there”, both confirming that the Dregs have a pleasure house and implying that they get very little income from it. Since we know that Kaz is the only one who actually does any work with the finances and that many times it’s been said that the Dregs would collapse without him not only because they would lose a lot of the fear his presence brings but also because they would lose most of their income, it’s fair to assume that the reason this business is unsuccessful is because Kaz refuses to be involved with it. I think that Van Eck’s accusation comes from him looking through the Dregs’ businesses (he has a collection of papers and information on Kaz and reads them during this conversation) and assuming Kaz is involved in all of them, and we can also follow the implication that Kaz is offended by this false accusation since he’s so quick and blunt in defending it during an otherwise lengthy and often philosophical conversation.
#kaz brekker#kaz my beloved#six of crows#grishaverse#crooked kingdom#leigh bardugo#inej ghafa#jesper fahey#wylan van eck#nina zenik#matthias helvar#kanej#ketterdam#kaz x inej#inej x kaz#six of crows analysis#soc analysis#soc analyst#soc and ck#soc meta#six of crows meta
517 notes
·
View notes
Text
SOC Analyst Online Training
SOC Analyst Online Training Course is the perfect place to start! This comprehensive course covers a range of topics, such as network monitoring, security operations, and incident response. With real-world scenarios and hands-on training, you'll be equipped with the skills and knowledge to become a successful SOC analyst in no time. Enroll now and let us help you reach your career goals Read More

0 notes
Text
0 notes
Text
What is Managed SOC?

A security operation center is a vital part of a business's cybersecurity strategy. This organization is responsible for analyzing new threats, prioritizing them based on severity and damage, and regaining access to network systems. In case of a data breach, the SOC can wipe endpoints or reconfigure systems to prevent infection. When necessary, the SOC can also deploy backups to avoid ransomware infections. Successful restoration of a network can return it to its pre-incident state.
An SOC consists of a team of security specialists who constantly monitor and analyze an enterprise's technology infrastructure. Rather than relying on traditional methods like virus scanning, SOCs use proactive and reactive security measures. Proactive security measures include behavioral monitoring and logging to identify suspicious behavior, which minimizes false positives. All activity and communications in an enterprise must be logged to provide SOC personnel with historical context. Activity logs help identify past actions and establish a baseline of normal activity. Moreover, security incidents are not created equal - a severity ranking helps prioritize those that warrant the highest priority.

The SOC is a vital tool for any security officer. Its global dispersal means that it can analyze threats in real time. SOC professionals can be anywhere in the world, and this allows for proactive analysis of threats. This, in turn, helps security officers fight cyber claims at every stage of the process. If an SOC isn't functioning properly, it can result in incorrect decisions. Therefore, it is imperative that security officers invest in a security operations center.
Threat hunting is a crucial aspect of proactive monitoring. The security threat environment is ever-changing, and it is important to stay ahead of them with proactive monitoring. By analyzing external threat intelligence, organizations can identify bad actors and avoid them. This makes them more effective at preventing attacks, thereby reducing the risk of being hit by a cyberattack. While proactive monitoring is the core of security operations, threat hunting helps identify bad actors before they can strike.
0 notes
Text
The job of a SOC Analyst
The #1 thing people ask me about is what I do for a job.
I'm a tier 1 SOC Analyst and I'm currently training to do some Cyber Threat Intelligence.
I will explain in detail what I do on a daily basis and why I've decided to do this job... And the negatives.
First of all, what's a SOC. SOC stands for "security operations center". It's a place (in my case virtual as I'm full remote) where a group of people, divided by experience and area of expertise, do the following:
Monitor the activities going on the customer's network or endpoints(= every device connected to the network);
Assess and mitigate alerts coming from the network and/or the endpoint of the client -> These tools send alerts that need to be evaluated and mitigated/responded in a certain amount of time (it depends on the SOC and the type of alert, generally I can assume an amount of time from 15 to 30 minutes per alert. Which is not that much;
Investigate cybersecurity incidents -> the SOC also analyses the kind of "incident" that happens in deep detail by analysing malware, spam emails, the behaviour of users and so on;
If the SOC is big/mature enough there could be some sort of prevention of cybersecurity issues, generally we talk about threat hunting (here for more information on that) and cyber threat intelligence (gathering information from various sources to produce a report about the potential attackers considering also the characteristic of the customer's company such as the size, the geographical area of operations, media exposure, geopolitical issues and what they do - doing this for a bank is different than doing it for a industry)
There are also other functions (such as we have a Security Architect that prepares a personalised solution for each client).
I know what you're thinking. But the AI...
No, they cannot do my job, as the ability of a human to notice patterns and correlate the information among various sources is unique. I memorised, with time, the usual activities my customers do, therefore I can interpret the user actions even with limited sources. And this is just one example.
Soc analysts are roughly divided in three "categories", always keep in mind that every SOC is different and has its own internal rules, that are not to be divulged. This is the rough division I've learned studying cybersecurity and NOT my organisation division.
Tier 1 Analysts are the one that monitors the traffic and activities I've mentioned before. They triage the alerts and if something deserves more investigation or can be discarded. They often perform simple actions of remediation of incidents.
Tier 2 Analysts are the ones that go deeper - they collect malware samples from the incident and analyse it, investigate and remediate more complex security incidents.
Tier 3 Analysts perform more active prevention duties like threat hunting and vulnerability assessments.
Some sources put intelligence activity on the tier 3, others consider it a different activity from the scenario I've described. If a SOC is big enough they might have their own intelligence team separated from the "regular" soc analysts. The rigidity of these roles can vary, as you probably got from my own duties.
On the top we have a SOC manager to coordinate the activities I've described and security architects that design the solution (although the deployment of these solutions can be delegated to the analysts, since we also have to monitor how well these perform).
All these people are usually referred as "blue teamers" btw, which are the ones that perform defensive actions.
A company can have a red team (basically they attack the customer to gain information that the blue team will use to improve their activities). I actually wanted to be a red teamer at first, since it's considered the "cooler" job.
Ok, got it. Now explain to me how you got there since I've never heard anything about this before.
I have a friend that's a system engineer and recommended this job to me.
I studies physics at university but I failed (in my country physics include some computer science classes btw) and I had some related experience I won't share for privacy reasons. No I'm not a criminal lol.
I then started studying - did a bootcamp and got a couple of certifications. Then I got my job.
However. Generally you get a degree in computer science or software engineering, and some universities offer cybersecurity degrees. Unfortunately I cannot tell you what to pick as every university has its own program and I cannot help you with that.
Certifications are a big part of my job unfortunately - mostly because due to how fast it goes you absolutely need to be "on top". It's annoying, yes, I hate it.
However. Consider that once you're hired you definitely will get them paid by your employer - at least in Europe this is on them(idk about the US), but you need some knowledge of cybersecurity to start.
Since some of them are stupid expensive I 100% recommend the compTIA ones. They're basics and respected worldwide. A+, Network+ and Security+ are basics, vendor neutral (which doesn't tie you to a particular "source", as every company works differently), and is relatively cheap (~300€).
Remember that I had previous experience so no one cares that I don't have a degree - I do however and I hope that in the future I will be able to "fix" this.
Great. How do I know if I'm good for this job?
This is on you. However:
One important thing if you don't live in an English speaking country is a good attitude towards foreign languages. I speak 5 for example, but it's an hobby I do since I was a teen;
Can you manage stress? A SOC is a fast paced environment, and you have a limited time to deal with whatever gets thrown at you. You have 15 to 30 minutes to deal with an alert and make a decision. Can you do that without panicking, crying or throwing a tantrum?
Are you a fast learner? You need to learn quickly how to do things, since the tools we use are quite complicated.
Are you willing to work on shifts, Saturdays, Sundays, festivities included? A lot of people can't cope with this and it's fine because it's a massacre. The job is so stressful to the point a lot of people leave cybersecurity because of it. Do not underestimate it, please.
How good are you at remembering random information and making correlations? Because I can remember random bits of information that no one ever thinks of it and it's one of my greatest strengths.
You need to do teamwork and be good with people, customers and so on - you have to explain complicated things you probably read in another language to people that don't know anything about what you do. It's more difficult than most people think.
Procedures are everything here - and for good reasons.
I think this is it.
Money.
USA avg salary: 74 307$ (Glassdoor)
France avg salary: 42 000€ (Glassdoor)
UK avg salary: 28 809 £ (Glassdoor)
There are random numbers I've found online(and with a lot of discrepancies). Consider that you MUST negotiate your salary, and that in certain places you get paid more if you work out of the usual 8-19 work shift. Obv since I live in a different place I cannot tell you if it's worth it - you do your own calculations.
But that's beyond the purpose of this post.
10 notes
·
View notes
Text
4 ways to advance your global security operations center - CyberTalk
New Post has been published on https://thedigitalinsider.com/4-ways-to-advance-your-global-security-operations-center-cybertalk/
4 ways to advance your global security operations center - CyberTalk


EXECUTIVE SUMMARY:
If your organization maintains a Global Security Operations Center (GSOC), ensure that you’re not heavily reliant on legacy systems and processes. In this article, find out about how to strategically advance your operations, enabling you to effectively prevent threats and drive more sustainable business outcomes.
What is a global security operations center?
In the early days of computing, a Security Operations Center (SOC) functioned as a physical ‘command center’ for security analysts. SOCs were comprised of rooms where staff sat shoulder-to-shoulder, looking at screens showing details from dozens of different security tools.
Large organizations with multiple Security Operations Centers (SOCs) began to consolidate them into Regional Security Operations Centers (RSOC) or a Global Security Operations Center, leading to faster remediation, reduced risk and a stronger cyber security posture overall.
In terms of function, a global security operations center monitors security, addresses threats before they become disruptive issues, responds to incidents, and liaise with stakeholders.
What are the benefits of a global security operations center?
A global security operations center allows an organization to contend with diverse security threats at-scale. Specific benefits include continuous monitoring, centralized visibility, increased efficiency and reduced costs. A global security operations center can also oversee and coordinate regional SOCs, network operations centers (NOCs) and operational teams.
What makes a good global security operations center?
For any global security operations center, access to timely and relevant threat intelligence is critical. GSOC staff need to remain updated on emerging cyber and physical security threats, as to stay ahead of potential risks.
Highly trained staff who can collaborate effectively with all stakeholders are also invaluable assets for a global security operations center.
Top-tier GSOCs have built-in redundancies of all kinds; from communication to data backups.
All GSOCs need to ensure that their organization adheres to industry regulations and compliance standards.
4 ways to advance your global security operations center
1. Ensure that the cyber security strategy aligns with business objectives. GSOCs need to know what the business aims to achieve, and must understand the corresponding threats and vulnerabilities that could hamper progress. Risk assessments should include both cyber security and business stakeholders, who can assist with the identification of resources that require protection.
Security policies and standards should also meet customer expectations. To gain insight around this, cyber security leaders may wish to join business planning meetings. Attendance can also assist with awareness around any upcoming business changes and implementation of appropriate, corresponding security measures.
2. Global security operations centers should shift towards the zero trust model. Zero trust is designed to reduce cyber security risk by eliminating implicit trust within an organization’s IT infrastructure. It states that a user should only have access and permissions required to fulfill their role.
Implementation of zero trust can be tough, especially if an organization has numerous interconnected and distributed systems. Organizations can simplify zero trust implementation through vendor-based solutions.
Tools like Quantum SASE Private Access allow teams to quickly connect users, sites, clouds and resources with a zero trust network access policy. In under an hour, security teams can apply least privilege to any enterprise resource.
Security gateways also enable organizations to create network segmentation. With detailed visibility into users, groups, applications, machines and connection types, gateways allow security professionals to easily set and enforce a ‘least privileged’ access policy.
3. Advance your global security operations center by mapping to industry standards and detection frameworks. Explore the MITRE ATT&CK framework. Standards like NIST and ISO27001 can also assist with identifying and reconciling gaps in an organization’s existing security systems.
4. Consider deploying a tool like Horizon SOC, which allows organizations to utilize the exact same tools that are used by Check Point Security Research, a leading provider of cyber threat intelligence globally.
Horizon SOC offers 99.9% precision across network, cloud, endpoint, mobile and IoT. Easily deployed as a unified cloud-based platform, it has powerful AI-based features designed to increase security operations efficiency.
Further thoughts
Strategic updates to global security operations centers not only enhance cyber security, they also enrich overarching business resilience – an increasingly common point of discussion among C-level stakeholders and the board.
By implementing the suggestions outlined above, organizations will maximize their opportunities for business longevity and continued business success.
Related resources
#ai#amp#applications#Article#assets#awareness#backups#board#Business#business resilience#c-level#Check Point#Cloud#clouds#collaborate#command#communication#compliance#computing#consolidation#continuous#cyber#cyber security#cyber security strategy#cyber threat#data#details#detection#efficiency#endpoint
2 notes
·
View notes
Text
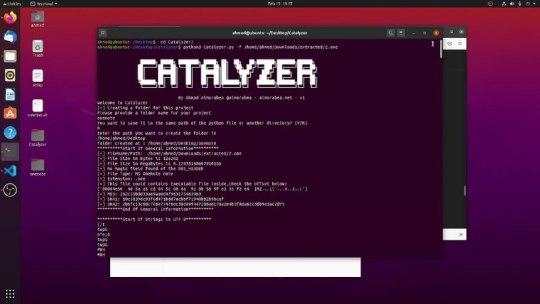
[Media] Catalyzer
Catalyzer
A small tool that helps Incident responders and SOC analysts do a quick and initial analysis/assessment of malicious files.
https://github.com/Almorabea/Catalyzer
YouTubeCatalyzer, Small Tool For Incident Responders and SOC AnalystsA small tool that helps Incident responders and SOC analysts do a quick and initial analysis/assessment of malicious files that could contain some Powershells, WMI, Vbs, and many more scripting languages inside them. It will even try to detect if the file includes some sort of executable inside it. For now, you can use it for the new wave of malicious .one or OneNote files. I hope it he https://github.com/Almorabea/Catalyzer https://twitter.com/almorabea
7 notes
·
View notes
Text
Fight back against digital brand threats
Fight back against digital brand threats
Cyberwebnic is a global organisation protecting over 4000 brands against the dangers of online fraud. Our Melbourne-based Security Operations Centre (SOC) comprises expert analysts who are dedicated to tracking and removing phishing and malware sites, trademark infringements and fake social media profiles and mobile apps. Our team operates 24x7x365, as we understand immediate detection and action is critical for online brand protection. Renowned for having the fastest SLAs in the industry, as well as 100% takedown success, our in-house proprietary anti-phishing tools have enabled us to become world-leaders in the online brand protection industry.
2 notes
·
View notes