#The certificates from the detection research
Text
Women's history just got richer
By Mindy Weisberger, CNN
More than 1,000 years ago, carvers in what is now Denmark set their chisels to rock to etch runestones — monuments to Viking leaders naming their deeds and achievements. Two groups of runestones mention a woman named Thyra, and new analysis of the carvings suggests that the runes on both sets of stones were inscribed by the same artisan and refer to the same woman: a Viking queen of considerable power.
Researchers from Denmark and Sweden used 3D scans to analyze carvings on the runestones, finding telltale clues that marked the individual style of the person who carved them. That carver’s repeated mention of Thyra’s name — a rare occurrence for Viking-era women — suggested that Thyra was a powerful sovereign who likely played a pivotal role in the birth of the Danish realm, the scientists reported Wednesday in the journal Antiquity.
“To learn more about the rune-carver and those named on the stone is fascinating,” said Dr. Katherine Cross, a lecturer at York St. John University in the UK who researches and teaches the history of early medieval northern Europe. She was not involved in the study.
“We can only understand early medieval sources once we can think about who made them and why,” Cross told CNN in an email.
One set of runes came from a pair of monuments known as the Jelling stones, erected in the town of Jelling around 965. The larger Jelling stone is often referred to as “Denmark’s birth certificate,” as it’s the first monument to name the land as its people pivoted to Christianity, according to the National Museum of Denmark in Copenhagen.
Both Jelling runestones also named a royal figure: Queen Thyra, mother of then-reigning King Harald Bluetooth. The smaller stone was raised in her honor by her husband (and Harald’s father) King Gorm, calling her “Denmark’s strength/salvation” (or “Denmark’s adornment,” depending on the translation, the researchers noted in the study). Harald commissioned the larger stone, to honor both of his royal parents.

In another set of four Viking-era monuments, known collectively as the Bække-Læborg group, two runestones mention a woman named Thyra. Those stones are associated with a carver named Ravnunge-Tue, but experts disagreed on whether that Thyra was Harald’s mother, said lead study author Dr. Lisbeth Imer, a curator and senior researcher at the National Museum of Denmark specializing in the study of runes and ancient inscriptions.
Before the new investigation, it was unknown who had carved the Jelling stones. Confirming that their carver was Ravnunge-Tue would strengthen the connection between the Jelling and Bække-Læborg runestones, Imer told CNN in an email.
“Then it is much more reasonable to suggest that it was in fact the same Thyra,” she said.
A question of style
Some details in ancient runestones that indicate a carver’s individual style are visible to a trained expert’s eye, such as the language or the basic shape of the runes. Other details are harder to detect, Imer said.
“What you cannot see with the naked eye is the carving technique,” she said.
To get a closer look at the carvings, the researchers took scans of the stones and created 3D digital models, then measured the runes’ grooves with a software tool that weighed variables such as angle, depth and cutting rhythm. Together, these variables can create a unique profile for a carver.
“Every rune carver develops his own motor skill and holds the tools in a certain angle, strikes with a certain strength,” Imer said. “The motor skill is individual and other individuals cannot copy that.”
When the researchers compared runes from Jelling 2 (the larger of the two Jelling stones) and the Læborg stone from the Bække-Læborg group, they found striking similarities, such as height of the runes, straightness of the main staves and length and placement of rune branches.
“In the Læborg and Jelling inscriptions you can follow the cutting rhythm of Ravnunge-Tue as one deep stroke of the chisel followed by two not so deep ones: DAK, dak-dak, DAK, dak-dak,” Imer said via email. “It is ALMOST like hearing the heartbeat of a person that lived so long ago.”
Jelling 1 was more eroded, so its markings were harder to analyze. But if the Læborg runestone was Ravnunge-Tue’s handiwork, Jelling 2 was likely his as well, Imer said. It would mean that the Queen Thyra mentioned twice in the Bække-Læborg group — on Læborg and on the stone Bække 1 — was the same person commemorated on the Jelling stones, the study authors concluded.
In recent years, archaeologists have revised prior interpretations of Viking warrior burials as exclusively male, finding that Viking women were fighters, too. The new findings add to the picture of influential Viking women holding prominent roles in statecraft as well as on the battlefield.
“This research highlights how Viking-Age women wielded power through political authority and patronage, not just violence,” Cross said.
What’s more, the fact that Thyra is mentioned on four runestones offers strong evidence of her importance, Imer added. Fewer than 10 runestones in Denmark from the pre-Christian era mention women at all — and four of those are of Queen Thyra.
“Runestones in Denmark were mostly erected in honour of men, but Thyra is commemorated on more runestones than any other person in Viking Age Denmark,” Imer said. “She must have held extreme power and social position.”
Mindy Weisberger is a science writer and media producer whose work has appeared in Live Science, Scientific American and How It Works magazine.
#Denmark#women in history#Queen Thyra#Viking Queen#Jelling Stones#King Harald Bluetooth#King Gorm#Bække-Læborg group#a carver named Ravnunge-Tue
160 notes
·
View notes
Text
HE★VENS LOVE AFFAIR - About, Rules, Members & Track List

Do not retranslate/repost without permission.
Let's have a love affair that is like ascending to heaven
About
The ultimate romance reality show is here!
Who will be the one to win Angel's heart?
Seven members with distinct personalities compete for true love.
An exciting and thrilling communal life in a share house. A splendid love affair is created.
Who will be the one to give Angel the kiss of victory in the end?
Rules
An angelic person called “Angel” will be living together with "HE★VENS", men with enough charm to rule over heaven, in a share house.
Throughout their daily life in the share house, Angel will be approached by the seven men.
And when communal life comes to an end, there will be a confession!
A couple will be formed when Angel accepts the love balloon which is presented along with a confession of love. The man pledges his eternal love with a sweet kiss.
Members
Eiichi
Racing driver
The one who will receive the checkered flag of love will be me!
The epitome of a racing driver, who became famous overnight. He has broken many records for the youngest-ever, achieving glory. The highest platform on the podium is reserved for him.

Kira
Potter
Let's polish our feelings... and create a beautiful masterpiece of love.
A master potter of peerless talent, known for his use of deep shades of blue. His works, which are designed to be delicate, are artistically exceptional, yet harmonious.

Nagi
Detective
There’s no mystery that I can’t solve. Including love, you know?
A “real-life great detective” who surpasses the acclaimed genius detectives from stories. His brilliant deductions have led him to solve one difficult case after another, and he has been awarded countless certificates of gratitude.

Eiji
Florist
Flowers and people bloom as beautifully as the amount of love we give them.
A promising young florist who is making a name for himself by creating flower arrangements. His works are frequently used to decorate the lobbies of various hotels and restaurants.

Van
Baseball player
I’ll hit your heart squarely and score a grand slam!
Since he joined the team in the first round of the draft, he has shown outstanding talent in both offense and defense and has won numerous awards. He’s also popular for his free and refreshing way of speaking outside of the field.

Yamato
Martial artist
You and me, which of us will fall in love? Shall we compete?
A world-class martial artist who is widely recognized as the strongest. With the various techniques performed by his muscular body, he continues to break the record for the most consecutive wins.

Shion
Zoologist
Being in love with you is what was predestined by nature to happen.
He is one of Japan’s most outstanding zoologists. He is second to none when it comes to research about birds. He is also known for his writing skills, and his books have surpassed the status of just academic publications, becoming bestsellers.

Track List
✿❀ INVITATION TO "HE★VENS LOVE AFFAIR"
✿❀ Theme song: LOVE AFFAIR
✿❀ SHARE HOUSE LIFE
✿❀ LOVE APPROACH Day 1. by Eiichi
✿❀ LOVE APPROACH Day 2. by Kira
✿❀ LOVE APPROACH Day 3. by Nagi
✿❀ LOVE APPROACH Day 4. by Eiji
✿❀ LOVE APPROACH Day 5. by Van
✿❀ LOVE APPROACH Day 6. by Yamato
✿❀ LOVE APPROACH Day 7. by Shion
✿❀ CHOOSE ME
✿ WHO DO YOU CHOOSE?
❀ LOVE AFFAIR with X
✿ Ending Theme: LOVE ABLAZE
✿ Theme song: LOVE AFFAIR *off vocal
✿ Ending Theme: LOVE ABLAZE *off vocal
❀ LOVE DATE with X
✿= Regular Edition
❀= First Press Limited Edition with X Ver.
#uta no prince sama#utapri#translation#english#he★vens#heavens#eiichi otori#eiji otori#nagi mikado#kira sumeragi#yamato hyuga#shion amakusa#van kiryuin#drama cd
21 notes
·
View notes
Text
In today’s digital world, injustice lurks in the shadows of the Facebook post that’s delivered to certain groups of people at the exclusion of others, the hidden algorithm used to profile candidates during job interviews, and the risk-assessment algorithms used for criminal sentencing and welfare fraud detention. As algorithmic systems are integrated into every aspect of society, regulatory mechanisms struggle to keep up.
Over the past decade, researchers and journalists have found ways to unveil and scrutinize these discriminatory systems, developing their own data collection tools. As the internet has moved from browsers to mobile apps, however, this crucial transparency is quickly disappearing.
Third-party analysis of digital systems has largely been made possible by two seemingly banal tools that are commonly used to inspect what’s happening on a webpage: browser add-ons and browser developer tools.
Browser add-ons are small programs that can be installed directly onto a web browser, allowing users to augment how they interact with a given website. While add-ons are commonly used to operate tools like password managers and ad-blockers, they are also incredibly useful for enabling people to collect their own data within a tech platform’s walled garden.
Similarly, browser developer tools were made to allow web developers to test and debug their websites’ user interfaces. As the internet evolved and websites became more complex, these tools evolved too, adding features like the ability to inspect and change source code, monitor network activity, and even detect when a website is accessing your location or microphone. These are powerful mechanisms for investigating how companies track, profile, and target their users.
I have put these tools to use as a data journalist to show how a marketing company logged users’ personal data even before they clicked “submit” on a form and, more recently, how the Meta Pixel tool (formerly the Facebook Pixel tool) tracks users without their explicit knowledge in sensitive places such as hospital websites, federal student loan applications, and the websites of tax-filing tools.
In addition to exposing surveillance, browser inspection tools provide a powerful way to crowdsource data to study discrimination, the spread of misinformation, and other types of harms tech companies cause or facilitate. But in spite of these tools’ powerful capabilities, their reach is limited. In 2023, Kepios reported that 92 percent of global users accessed the internet through their smartphones, whereas only 65 percent of global users did so using a desktop or laptop computer.
Though the vast majority of internet traffic has moved to smartphones, we don’t have tools for the smartphone ecosystem that afford the same level of “inspectability” as browser add-ons and developer tools. This is because web browsers are implicitly transparent, while mobile phone operating systems are not.
If you want to view a website in your web browser, the server has to send you the source code. Mobile apps, on the other hand, are compiled, executable files that you usually download from places such as Apple’s iOS App Store or Google Play. App developers don’t need to publish the source code for people to use them.
Similarly, monitoring network traffic on web browsers is trivial. This technique is often more useful than inspecting source code to see what data a company is collecting on users. Want to know which companies a website shares your data with? You’ll want to monitor the network traffic, not inspect the source code. On smartphones, network monitoring is possible, but it usually requires the installation of root certificates that make users’ devices less secure and more vulnerable to man-in-the-middle attacks from bad actors. And these are just some of the differences that make collecting data securely from smartphones much harder than from browsers.
The need for independent collection is more pressing than ever. Previously, company-provided tools such as the Twitter API and Facebook’s CrowdTangle, a tool for monitoring what’s trending on Facebook, were the infrastructure that powered a large portion of research and reporting on social media. However, as these tools become less useful and accessible, new methods of independent data collection are needed to understand what these companies are doing and how people are using their platforms.
To meaningfully report on the impact digital systems have on society, we need to be able to observe what’s taking place on our devices without asking a company for permission. As someone who has spent the past decade building tools that crowdsource data to expose algorithmic harms, I believe the public should have the ability to peek under the hood of their mobile apps and smart devices, just as they can on their browsers. And it’s not just me: The Integrity Institute, a nonprofit working to protect the social internet, recently released a report that lays bare the importance of transparency as a lever to achieve public interest goals like accountability, collaboration, understanding, and trust.
To demand transparency from tech platforms, we need a platform-independent transparency framework, something that I like to call an inspectability API. Such a framework would empower even the most vulnerable populations to capture evidence of harm from their devices while minimizing the risk of their data being used in research or reporting without their consent.
An application programming interface (API) is a way for companies to make their services or data available to other developers. For example, if you’re building a mobile app and want to use the phone’s camera for a specific feature, you would use the iOS or Android Camera API. Another common example is an accessibility API, which allows developers to make their applications accessible to people with disabilities by making the user interface legible to screen readers and other accessibility tools commonly found on modern smartphones and computers. An inspectability API would allow individuals to export data from the apps they use every day and share it with researchers, journalists, and advocates in their communities. Companies could be required to implement this API to adhere to transparency best practices, much as they are required to implement accessibility features to make their apps and websites usable for people with disabilities.
In the US, residents of some states can request the data companies collect on them, thanks to state-level privacy laws. While these laws are well-intentioned, the data that companies share to comply with them is usually structured in a way that obfuscates crucial details that would expose harm. For example, Facebook has a fairly granular data export service that allows individuals to see, amongst other things, their “Off-Facebook activity.” However, as the Markup found during a series of investigations into the use of Pixel, even though Facebook told users which websites were sharing data, it did not reveal just how invasive the information being shared was. Doctor appointments, tax filing information, and student loan information were just some of the things that were being sent to Facebook. An inspectability API would make it easy for people to monitor their devices and see how the apps they use track them in real time.
Some promising work is already being done: Apple’s introduction of the App Privacy Report in iOS 15 marked the first time iPhone users could see detailed privacy information to understand each app’s data collection practices and even answer questions such as, “Is Instagram listening to my microphone?”
But we cannot rely on companies to do this at their discretion—we need a clear framework to define what sort of data should be inspectable and exportable by users, and we need regulation that penalizes companies for not implementing it. Such a framework would not only empower users to expose harms, but also ensure that their privacy is not violated. Individuals could choose what data to share, when, and with whom.
An inspectability API will empower individuals to fight for their rights by sharing the evidence of harm they have been exposed to with people who can raise public awareness and advocate for change. It would enable organizations such as Princeton’s Digital Witness Lab, which I cofounded and lead, to conduct data-driven investigations by collaborating closely with vulnerable communities, instead of relying on tech companies for access. This framework would allow researchers and others to conduct this work in a way that is safe, precise, and, most importantly, prioritizes the consent of the people being harmed.
11 notes
·
View notes
Text
Arkhelios Adventures

Ulyssa looked behind her as she slipped down the upper hallway of Claudia's parents' house. Though she wasn't an expert at subterfuge, she did take a kind of enjoyment from her actions. She was breaking into the rooms of supernatural creatures, beings who were on a first name basis with the Grim Reaper and Death. Jorah was still outside, jabbering on about his kids and distracting the household. The kind of information she needed couldn't just be asked and answered by Claudia's friendly parents. Ulyssa needed to know how Claudia's mind worked, and what her intentions were for the future. Would she reveal Victoriana's paternity to the world? Would she spill the beans on Georgiana now that Ulyssa had confirmed that Claudia knew the truth about her daughter? What were her plans for Roman Bellamy?
No, stop thinking about Roman. He's just a complication in Claudia's scheme. I don't care what happens to him.
The first three rooms in the hall had been uninteresting. They were the bedrooms of Claudia's little brothers when they weren’t living in their school dorms and the very plain bedroom of Claudia's parents. If they were the standard for reapers, then reapers were far more boring than Jorah anticipated. Their bed was made and the room was tidy. Some photographs rested on the dresser next to a hair brush and some earrings, but nothing fantastical or exciting. If anything, the room reminded Uylssa of her own parents and the bedroom they'd once shared together. Bits and pieces of life strewn around a shared space between two people in love. Maura had her own separate dressing room to accommodate her many outfits and collections of jewellery, nothing like this. Ulyssa's things were in a separate, but joining dressing room, neatly held apart from her wife's. What would their life be like if they lived in a room like this? Where she could wake up next to Maura, brush her teeth in a quaint en suite bathroom and get the kids ready for school. Maybe in a parallel life their marriage wouldn’t be so hard.
This next room would be the one she was looking for, Ulyssa could just feel it. She hadn't found the room where Claudia had grown up yet, but she had to be close.

"Travis did what? No, he's not allowed to practice fire spells in his dorm, we've told him this. Yes, he paid that fine from his own school account. He hand delivered the apology letter to the dean, I made sure of it."
Ulyssa tried to strain her ears to hear the conversation in case it was relevant to her hunt. She could hear Claudia's mother pace the floor downstairs, clearly talking to a school authority of some kind.
That must be her youngest brother. Claudia, Oliver and Travis? How much younger is Travis? He sounds like a trouble maker. Maybe Claudia has covered up some incidents of his that she doesn't want known.

Ulyssa entered the last room and found exactly what she was looking for. Charts, graphs, and information were sprawled out across the bed and floor, looking more like a detective's work room than a childhood bedroom.
"What in the world?"
Ulyssa picked up a random piece of paper to find a crude family tree scribbled on it. Beside that was a printout from the Pleasantview Royal Archives and a death certificate for an E Goldman. What was she looking at? All of these papers were related to Claudia's family- her father probably and maybe her grandfather? There was a picture underneath the mess of a much younger Claudia standing next to her white haired father in a nondescript room. Beside them, a column of smoke was engulfing the rest of the frame. If Ulyssa squinted hard, she almost swore that she could make out the shape of a face within the smoke, framed with dark hair. It was truly bizarre to stare at.

"That's all the research my father and I did to support my claim to the throne. It took hours in libraries and archives, but we worked the case together and now look at what we've accomplished."
Ulyssa froze, her blood freezing in her veins at the voice. If she thought that she could get away with it, Ulyssa was tempted to just teleport from the room back to her home and pretend she'd never taken this trip. But the queen of Pleasantview stood behind her, her gold eyes watching her every movement, looking for weakness. She was like a cat toying with a mouse. There was no lying her way out of entering this room, and if she teleported now, Maura would likely hear about this visit. Jorah might also be destroyed by the servants of Death, but he had accepted this mission knowing the risks. He'd probably be thrilled to see an actual reaper murder them both.

Claudia's hands fell to a marble bust that took up a large portion of the room and frankly looked far too expensive to reside in a house like this one.
"This is my heritage, my birthright," she continued. "My father is sending it to the archives to be stored, but I’m sure he doesn’t mind me showing our work off to visitors. I don't think you understand the game that you're attempting to play here. Maura has coddled you far too much and you've gotten cocky. You think that you can get away with whatever you want, but I'd advise you not to continue with that line of thinking. I'm quite aware of your little attempts to intrude upon my life. I'm less certain of why you're attempting such a thing. Maybe it's a game my cousin is playing through you, though that's never been Maura’s style. No, if I had to guess, this is all just a misguided errand of love. Not love for my cousin, your wife, but for some utterly undeserved obsession with Roman Bellamy."
Ulyssa tried not to gulp at these words considering the glare she was receiving. The room suddenly felt a lot smaller.
" N-no, Roman doesn't mean anything to me," she stammered. "I…."
She tried to summon the words to back up Jorah's lie, but they got caught in her throat. There was no way that Claudia believed the little autograph ruse and Ulyssa was completely at a loss for a more believable story.

"Do you really think that you love him? That he could love you back? You're nothing to him and you're nothing to me. The only person who cares if you live or die is my cousin, who you claim to love in return. Though I'm sure that Maura could easily move on if you were to turn up dead, the evidence of your feelings surrounding you. She's already got an heir and a spare from you, if you can't stay faithful to her even in your own heart, I might be persuaded to…intervene."
Uylssa's mouth seemed to be failing her as she stammered a few more syllables before falling silent. Could Claudia have her killed? Sure, but would she? Would Maura forgive her or be relieved to finally be free of her cheating spouse?
"I…Maura would…."
"I'm sure that Maura has told you the story of her great-grandmother who allied herself with Strangetown and Pleasantview in order to have her aunt killed to correct her father's…changes to the line of succession," Claudia continued. "She never stops talking about it; she thinks it's the worst thing a person could do to a family member. Well, I'm here to tell you that it isn't. Not by a long shot. Maura only sees the good in people and it leaves her open to being hurt, just as you've done to her. Just as you're doing right now. And all this just for Roman Bellamy? The man is a weak demon hybrid who can't get over the high school boyfriend that he cheats on. He's nothing. Completely irrelevant. Nothing compared to your wife."
"But he was good enough to be Victoriana's father," Ulyssa was quick to point out, seeing a single thing to yield against the queen. "You have feelings for him too!"
Claudia gave her a look that was somehow both pitying and ruthlessly cold.
"Let me be perfectly clear about this little idea of yours. Roman Bellamy means nothing to me. He was a good time and nothing else. Nothing. He gave Victoriana some demon blood that will help her rule and that's it. He could die tomorrow and I wouldn't feel a thing, just as I'm sure he'd feel about you if you turned up dead. Don't play games you know nothing about, or there will be consequences."

Ulyssa took a step back unconsciously, seriously beginning to fear for her life. She knew that Claudia was bluffing about Roman. She had to be bluffing. Claudia had always seemed head over heels for him, even at his wedding to Abe. There was no way that she'd murder him just to get back at Ulyssa. She had his child. She wouldn't kill Roman…right? She wouldn't make a widow of Maura either, or so Ulyssa hoped. There were always whispers about Pleasantview being involved with the attack that had killed Maura’s mother, sister and a princess from Crystal Cove, but Maura refused to believe them. Seeing this side of Claudia, Ulyssa wasn't so sure that she agreed.
"Maura would find out that you were to blame," Ulyssa tried weakly. "She'd be angry, angry enough to go to war if you killed me."
"No she won't," Claudia promised. "My cousin is soft and weak. Most of her military was trained by my forces and she got the majority of her funding for them as a gift from me. She knows that I could take her throne in a heartbeat if I wanted to and she has a better self preservation instinct than you seem to. I can do whatever the hell I want to whoever I want and not have a single person challenge me for it. I could kill you right here, right now in my childhood bedroom and the only thing that would happen is that I'd have to apologize to my parents for the mess. I could kill your little godson you love so much in an instant. He attends my academy for my coven. He could disappear tomorrow and no one would find a trace of him. Go visit the ruins of the former Pleasantview castle and see for yourself the signs that point out the countless unmarked dead found when they combed through the wreckage. Skeletal remains that were centuries old. I know that you're weak and optimistic in the islands, but here in Pleasantview, we mean what we say. Take my grandfather here, King Casper." She gestured at the overly large and fancy bust for emphasis. "He killed his mother, stepmother, all of his half-siblings and every member of the Crystal Cove royal family, save for the crown princess, who he threatened until she agreed to marry him. He killed the disloyal witches that rebelled against him and every single officer who broke their oath to disobey his orders. He had the same military as I do, the same coven and a similar education. He made every other nation quake with fear with his ambition, something that I have refused to do thus far as a kindness to the other nations. His own grandfather was just the same, as were so many members of my royal family line. Whatever control you think you have on me is an illusion, brought on by your guilty heart.”
Claudia stared her prey straight in the eye, her expression deadly serious.

“Don't. Push. Me. You won't like what happens.”

“Anyway, I have to be on my way. I’m already behind as it is.”
Within a fraction of a second, the queen’s entire demeanor changed. She went from the stuff of nightmares to a smiling, carefree woman who hadn’t just threatened to murder her cousin’s wife.
“Mom, I’m running late. If you can’t get off the phone now, just leave the brownies on the kitchen table. I’m going to say goodbye to Dad and Oliver.”
With a playful wink, Claudia reached for the door handle while Ulyssa steadied her breath. What was going on here and who the hell was Maura related to?
“Remember our little talk,” Claudia called out while entering the main hallway. “What happens next is entirely up to you. Send my love to Maura. Mom! I have to leave!”
Ulyssa pressed herself against the wall, trying to count her options. There wasn’t much to work with aside from following Claudia’s orders and leaving her alone. Who was the true Claudia, this happy family woman or the raging psychopath who saw the world as her property? Had Maura ever seen this transformation in her cousin?
Well, for all my efforts, I’ve only learned that Claudia has a troubled little brother, Jorah-level parents and a dark side that’s too deep to ever see the bottom of. Not much for the danger involved and the enemy I’ve seemed to have made. Great.
“Jorah, It’s time to leave! Grab your stuff and let’s go!”

“Good game,” Jorah conceeded, extending a hand to his Don’t Wake the Llama opponent. “You could probably beat my oldest and she’s been practicing for years.”
“Not as long as I have,” Ewan chuckled, grabbing the offered hand and shaking it politely. “Though I could probably give her some tips, if you wanted to stop by again for a game or two some time.”
He smiled sincerely and Jorah beamed back. This was the greatest day ever, (aside from his wedding and the birth of his kids). Not only had he seen a reaper and lived to tell the tale, but that reaper was actually pretty cool and interested in meeting again. Valerian would never believe him.
“Any time!” he promised, hearing Ulyssa still shouting for him in the distance. “You bring the game and I’ll provide the snacks. Valerian makes an amazing casserole, you’ll love it.”
“Jorah! Now! Before she comes back!”
“It’s a date,” Ewan said with a smile. “See you then.”
#arkhelios#arkhelios adventures#sims 2#ulyssa durant#Jorah Durant#ewan jr goldman#sim: ewan jr goldman#claudia goldman#sim: Claudia Goldman#anneken toyonaga#sim: anneken toyonaga
11 notes
·
View notes
Text
Umbrella Pharmaceuticals - Chapter 23
I
Dr Marcus was not imposing. He paced the stage like a sergeant, raising his voice at intervals and not bothering to check whether the students were listening to him. A couple of students took advantage of the principal's indifference to get in the way by talking in hushed tones. He was about to order them to shut up, but he didn't want to draw attention to himself. Not for now; not when his livelihood depended on the scholarship Umbrella Pharmaceuticals had given him for nothing more than graduating from college at seventeen. When he read the terms of the contract, he didn't believe the requirements were so affordable, or low; or rather, so low, because that class was full of nondescript, presumably stupid preppies. They were all older than him, but he detected no one who stood out except the fifteen-year-old nerd with whom he had been lumped together against his will. This nerd, William, feared him; he could see it in his distance, in the way he avoided eye contact, in the way he pretended to ignore him.
He was amused. He was very amused by his acne-grained face, the languor of his lanky frame and the haggard bags under his eyelids. He looked like a youthful parody of Albert Einstein, straight out of the Manhattan Project to try his luck in the pharmaceutical industry. Being two years younger, he figured he would be smarter or more competent than he was, though he couldn't be sure he was much clever. If there was to be only one of him left at the end of the course, William had better be as clever as he was smart. Until then, he would have a good time and work as hard as it took to secure a position of importance at Umbrella and never return to New York.
II
They were gathered around a rectangular metal table in a corner of the main laboratory. James Marcus had left, and from now on his training would be handled by the company's scientific and technical staff. He had sat in a corner, between two petulant students, and in the same row as Wesker so as not to face him. They had been summoned by one of the facility's senior researchers for a class on research team building and management. He had brought his notebook with him and was writing down in shorthand everything the researcher said. At one point, as the professor questioned the rest of his classmates, he turned to his left and met Wesker's inquisitive gaze. He instantly withdrew his eyes to alternate his attention between the professor and his notebook.
He thought of his roommate as a threat. He had seen first-hand that the rest of the students were not the smartest in their class and, from what they said, had been put there because of cronyism. They, who were already rich, had come for the certificate. Therefore, the only one left as a rival was Albert Wesker. He would not allow him or anyone else to take the job away from him. He had endured and fought long enough to go back to Baltimore with his tail between his legs. He had staked his best cards on that chance and would do anything he could think of not to lose the hand. He would show no mercy.
6 notes
·
View notes
Text
Study: Sickle cell disease 11 times deadlier than previously recorded

- By Nuadox Crew -
A new study published in The Lancet Haematology journal reveals that the number of deaths caused by sickle cell disease is significantly higher than previously estimated.
The study found that the mortality rate attributed solely to sickle cell disease is 11 times lower than the actual number of deaths when considering various risk factors and associated conditions. Sickle cell disease not only leads to underdiagnosis but also increases the risk of infections and death from conditions such as stroke, heart problems, kidney problems, and pregnancy complications. As a result, doctors may overlook the connection between sickle cell disease and the cause of death when listing it on death certificates.
By combining data on prevalence, birth incidence, and mortality, the study estimated that the total mortality burden of sickle cell disease in 2021 was 373,000 deaths worldwide, compared to the previously reported figure of 34,600 deaths solely attributed to sickle cell disease. The increase in mortality was particularly significant in South Asia and sub-Saharan Africa, where the fatality rates were 67 times and nine times higher, respectively, than previously believed.
The research analyzed global health data from 2000 to 2021 and was part of the Global Burden of Disease 2021 study, led by the Institute for Health Metrics and Evaluation (IHME) at the University of Washington's School of Medicine. The study highlights the rising number of babies born with sickle cell disease and the need for early detection and treatment due to the increased susceptibility to severe conditions and infections.
In 2021, approximately half a million babies were born with sickle cell disease, with over three-quarters of these births occurring in sub-Saharan Africa. When considering the total mortality burden, sickle cell disease was the 12th leading cause of death globally for children under the age of 5. However, it ranked among the top three causes of death in countries such as Portugal, Jamaica, Libya, Oman, and San Marino.
The study emphasizes the importance of improving data collection to track progress on sickle cell disease. Instead of relying solely on mortality data, the researchers used a mathematical algorithm that incorporated data on birth incidence, survival rates, and prevalence to estimate total deaths due to sickle cell disease. This approach provided a more comprehensive understanding of the true burden of the disease and its comparison to other leading causes of death.
The research highlights the urgent need for policymakers and public health advocates to address the underestimated burden of sickle cell disease. The implementation of universal newborn screening, the establishment of public registries for case monitoring, and early intervention treatments can significantly alleviate suffering for the approximately 8 million people living with sickle cell disease.
The study also stresses the importance of universal newborn screening for early diagnosis and management of sickle cell disease. While newborn screening is universal in the United States, many low- and middle-income countries lack a comprehensive screening process. Increasing global awareness and adopting health policies that expand neonatal screening and improve treatment accessibility are crucial for improving health outcomes for individuals with sickle cell disease.
--
Source: Institute for Health Metrics and Evaluation
Full study: Global, regional and national prevalence and mortality burden of sickle cell disease, 2000-2021: a systematic analysis from the Global Burden of Disease Study 2021, The Lancet Haematology (2023) DOI: https://doi.org/10.1016/S2352-3026(23)00118-7
Read Also
Yaw Ansong Jnr speaks on technologies for sickle cell disease patients
#sickle cell disease#sickle cell anemia#sicklecell#blood#health#pediatrics#africa#population health#public health#medicine#haematology#sickle cell#health informatics
6 notes
·
View notes
Text
Decoding Data Science: Unveiling the Vast Landscape and Career Opportunities
In the era of big data, Data Science has emerged as a transformative force, reshaping industries and driving innovation. This blog aims to unravel the essence of Data Science, exploring its multidisciplinary nature and shedding light on the extensive scope and promising career opportunities within this dynamic field. Whether you're a beginner or looking to specialize, understanding the types of data science courses available is crucial. Choosing the best Data Science Institute can further accelerate your journey into this thriving industry.
What is Data Science?
At its core, Data Science is the art and science of extracting valuable insights and knowledge from complex data sets. By employing a combination of scientific methods, algorithms, and domain-specific knowledge, Data Science transforms raw data into actionable intelligence. This multidisciplinary field encompasses statistics, mathematics, computer science, and more to analyze and interpret both structured and unstructured data.
Scope of Data Science:
Job Opportunities:
Data scientists are sought after across diverse industries such as finance, healthcare, technology, and e-commerce.
Roles include data analyst, machine learning engineer, data engineer, business intelligence analyst, and data scientist.
Educational Landscape:
The educational landscape for Data Science is expansive, with universities and online platforms offering a plethora of courses, degrees, and certifications.
Specialized programs cover machine learning, big data, data engineering, and business analytics to cater to varying skill levels.
Industry Integration:
Organizations are increasingly integrating data science into their operations, influencing decision-making processes.
Data-driven strategies impact areas like marketing, product development, and overall business strategy.
Government Initiatives:
Governments recognize the importance of data science in driving innovation and economic growth.
Initiatives and policies promote data literacy and skill development, aligning education with industry needs.
Diverse Applications:
Data science finds applications in diverse fields, including finance for fraud detection, healthcare for predictive analytics, marketing for customer segmentation, and agriculture for precision farming.
Its versatility is reflected in its broad spectrum of applications.
Competitive Salaries:
Skilled data science professionals command competitive salaries due to the specialized nature of their expertise.
Salaries vary based on factors like experience, location, and the specific role within the data science field.
Global Contribution:
Data scientists contribute globally, collaborating on projects addressing societal challenges, healthcare advancements, and environmental issues.
The global nature of data science fosters a culture of collaboration and knowledge exchange.
Continuous Innovation:
Data science stands at the forefront of technological innovation, driving advancements in artificial intelligence, machine learning models, and predictive analytics.
Professionals engage in cutting-edge research, contributing to the ongoing evolution of the field.
Career Opportunities:
Data Scientist
Data Analyst
Machine Learning Engineer
Data Engineer
Business Intelligence Analyst
Data Architect
Statistician
Quantitative Analyst
Research Scientist
Predictive Modeler
Data Science is not just a field; it's a dynamic force shaping the future of industries. With a vast scope and diverse career opportunities, it offers a compelling journey for those seeking to immerse themselves in the intersection of technology, analytics, and innovation. As organizations continue to recognize the value of data-driven insights, the demand for skilled data scientists is set to soar, making Data Science a promising and rewarding career path. Choosing the best Data Science courses in Chennai is a crucial step in acquiring the necessary expertise for a successful career in the evolving landscape of data science.
3 notes
·
View notes
Photo




On February 12th, 1935, Scotsman Robert Watson-Watt published a report entitled The Detection of Aircraft by Radio Methods.
In the full memorandum, sometimes called ”the birth certificate of radar” Watson-Watt put forward his proposals in impressive detail. He estimated the strength of the radio signal reflected from an aircraft and discussed the optimum wavelength. He outlined how the range of the target could be measured by the use of short pulses and the plan position by the use of three range measurements; furthermore he suggested that a cathode-ray direction-finder might be developed to measure the bearing and elevation.
The Committee promptly asked for a demonstration and appointed A. P. Rowe as their sole observer. It was arranged that a Heyford bomber should fly at a height of 2000 m to and fro in the main beam of the BBC Empire short-wave transmitter at Daventry which radiated 10 kW at 498 m. A simple but sensitive arrangement was used to look for reflections from the aircraft. At a distance of 10 km from the transmitter two horizontal half-wave dipoles were mounted on poles; the dipoles faced the transmitter and were spaced 5 m apart in that direction. By means of a phase changer and two receivers the signals from the two dipoles were applied in phase opposition to a cathode-ray tube so that signals arriving directly from the transmitter produced no deflection; signals reflected from an aircraft, arriving at a different angle, were not cancelled and produced a vertical deflection on the tube. The demonstration took place on the 26th February 1935 and was viewed only by Watson-Watt, Wilkins and Rowe. They saw signals reflected from the aircraft for about 4 minutes on three occasions as the aircraft passed overhead. Watson-Watt must have been rather disappointed that Rowe didn't jump up and down with his account of the show he notes that Rowe showed 'no detectable signs of excitement or elation'. However he needn't have worried, Rowe gave him a green light in his report he wrote':'It was demonstrated beyond doubt that electromagnetic energy is reflected from the metal components of an aircraft's structure and that it can be detected. Whether aircraft can be accurately located remains to be shown.”
No one seeing the demonstration could fail to be hopeful of detecting the existence and approximate bearing of aircraft approaching the coast at ranges far in excess of those given by the 200 ft (sound) mirrors.'
As we all know the experiment, and another a fortnight later meant the equipment could go into production, on 2nd April 1935, Watson-Watt received a patent on a radio device for detecting and locating an aircraft.
The system provided the vital advance information that helped the RAF win the Battle of Britain.
There’s a great wee anectdote I always like to add to posts about Watson-Watt, he moved to Canada as a consulting engineer. As an irony in history it is reported that he was pulled over for speeding in Canada by a radar gun-toting policeman. His remark was, “Had I known what you were going to do with it I would never have invented it!” Watson-Watt’s other contributions include a cathode-ray-tube direction finder used to study atmospheric phenomena, research in electromagnetic radiation, and other inventions used for flight safety.Robert Alexander Watson-Watt died in 1973, aged 81, in Inverness.
17 notes
·
View notes
Text
Shirley Yolande Hollis, 30 (USA 1991)
Shirley was a victim of negligence at the hands of an abortionist. This much is certain, but the extent that abortion causes her death is somewhat debated.
Shirley was 30 and pregnant with her third baby when she underwent an abortion at the hands of Bruce Lucero on February 22, 1991. Apparently nobody at the facility examined her thoroughly enough to notice a dangerous pre-existing condition.
After Shirley went home, she was short of breath, had pain in her arms and started vomiting. Her alarmed boyfriend called the abortion facility and told them something was wrong with Shirley.
Abortion facilities will typically insist that a client’s symptoms are normal and discourage them from seeking medical attention, but for once, an employee told the boyfriend to take Shirley to the ER. (Again, even this level of very basic concern is extraordinarily rare in the abortion industry and I give the employee great credit for the recommendation.) Shirley thought she was having side effects from the abortion and wanted to wait at home, but she collapsed into her boyfriend’s arms. He called 911 and started CPR.
The ambulance took Shirley to the hospital, but she didn’t survive the night. Her autopsy found something that the abortion facility overlooked.
Shirley had not been in a good condition for an elective operation. She had an undiagnosed case of severe coronary artery disease and died of a heart attack. Shirley’s mother faulted Lucero with the death because he failed to detect her heart problem when he (allegedly) examined her at the abortion facility.
Even among those who research deaths by legal abortion, Shirley’s case has been a source of debate. Researchers have made very convincing arguments for and against categorizing her death as an abortion fatality. I included a shortened version of many of these arguments here.
PRO: Abortion can cause heart attacks directly. This can happen because of severe infection (like Alesha Thomas), blood loss (like Mary Pena), and embolisms (like Anne Roe).
CON: Because of Shirley’s undiagnosed disorder, the heart attack may have happened anyway. The coroner didn’t specifically say if the abortion caused this heart attack. If pathological tests weren’t run on the makeup of the clot that caused the heart attack, it’s hard to be sure if it was from an abortion-caused embolism or not.
PRO: Shirley should have been given a thorough pre-op examination before the abortion. Given her condition, she was high-risk and it was reckless to put her through an elective operation.
CON: When contacted about Shirley’s symptoms, the facility recommended that her boyfriend take her to the ER. It’s hard to fault them for the couple not following the recommendation quickly.
PRO: The facility missed the chance to detect Shirley’s disease before her life was in immediate danger, meaning that they needlessly made the situation worse. She also dismissed her heart attack symptoms because she thought they were symptoms from the abortion.
CON: One very common behavior in heart attack patients is that they tend to blame their symptoms on any other cause and can be reluctant to seek treatment.
Because of the circumstances of Shirley’s death, I could not be 100% sure if she would have been spared by not undergoing the abortion. However, it was still negligent to go through with it given her CAD, which a competent pre-op exam should have noticed.
Alabama Certificate of Death, State #101
Jefferson County Coroner’s Report, 91-284
#unsafe yet legal#death from legal abortion#tw abortion#victims of roe#pro life#abortion#abortion debate#abortion is not healthcare
4 notes
·
View notes
Text
Securing Your Mobile App: Best Practices for Data Protection

In today’s digitally connected world, mobile applications have become an integral part of our daily lives. From social media to online banking, we rely on mobile apps to access various services and manage sensitive information. However, with the increasing reliance on mobile apps, the need for robust data protection measures has become paramount. This blog will explore best practices for securing your mobile app and ensuring the protection of user data.
Encryption:
One of the fundamental steps in securing your mobile app is implementing encryption techniques. Encryption ensures that data transmitted between the app and the server is transformed into a coded form, making it unreadable to unauthorized parties. Utilize strong encryption algorithms, such as AES (Advanced Encryption Standard), to protect sensitive user information like passwords, financial details, and personal data. Additionally, consider implementing end-to-end encryption to safeguard data even if it’s intercepted during transmission.
2. Secure Authentication:
Implementing strong authentication mechanisms is vital to protect user accounts from unauthorized access. Encourage the use of complex passwords and provide guidance on creating strong passwords during the registration process. Consider implementing two-factor authentication (2FA) or biometric authentication, such as fingerprint or facial recognition, to add an extra layer of security. Regularly validate and update authentication protocols to address emerging security vulnerabilities.
3. Secure Data Storage:
Properly managing and securing data storage within your mobile app is crucial. Avoid storing sensitive information on the device unless necessary, and when required, utilize secure storage mechanisms provided by the operating system or utilize encryption techniques to protect the data. Ensure that the app’s data storage is adequately protected against unauthorized access or tampering, both locally on the device and on the server.
4. Secure Network Communication:

Mobile apps rely on network communication to exchange data with servers or APIs. It’s essential to ensure that this communication is secure. Use secure communication protocols such as HTTPS (Hypertext Transfer Protocol Secure) to encrypt data transmitted over the network. Avoid transmitting sensitive information through insecure channels, such as unsecured Wi-Fi networks, and implement certificate pinning to prevent man-in-the-middle attacks.
5. Regular Updates and Security Patches:
Keeping your mobile app up to date with the latest security patches and fixes is crucial for maintaining a secure environment. Regularly release updates to address any identified security vulnerabilities or weaknesses. Promptly address security-related issues reported by users or security researchers and provide timely patches to mitigate potential risks. Establish a process for monitoring and staying informed about the latest security practices and threats.
6. Secure Code Development:
Developing secure code is essential for building a robust mobile app. Adhere to secure coding practices and guidelines provided by the platform and framework you are using. Regularly conduct code reviews and security audits to identify and address any potential vulnerabilities. Utilize automated tools for vulnerability scanning and penetration testing to detect security flaws in your app’s codebase.
7. User Privacy and Consent:
Respect user privacy and adhere to data protection regulations such as GDPR (General Data Protection Regulation) or CCPA (California Consumer Privacy Act). Clearly communicate your app’s data collection and usage practices to users through a comprehensive privacy policy. Obtain explicit consent from users before accessing and storing their personal information. Allow users to manage their privacy settings within the app, giving them control over their data.
Securing your mobile app is not just a legal requirement but also a responsibility to protect your users’ sensitive data. By implementing strong encryption, secure authentication mechanisms, and following best practices in code development, you can create a safer environment for your users. Regular updates and a privacy-centric approach will help instill trust and confidence in your app. By prioritizing data protection, you contribute to a safer mobile app ecosystem and foster long-term user satisfaction.
Remember, data protection is an ongoing process, and staying vigilant against emerging threats and security practices is vital in this ever-evolving digital landscape.
2 notes
·
View notes
Text
YOUNG HAWAIIANS & PACIFIC ISLANDER ADULTS WITH HIGHEST CANCER RATES
NBC News - May 19, 2023
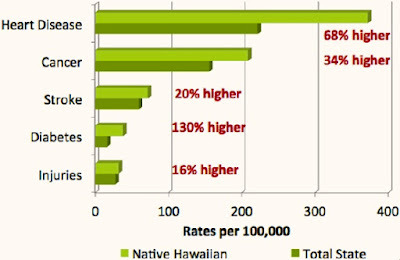
New research shows that Native Hawaiian and Pacific Islanders between the ages of 20 and 49 have the highest death rates from any type of cancer among all racial groups of that age bracket.
The findings, published last month by the National Cancer Institute, weren’t immediately apparent in previous research because federal data has traditionally grouped together those of Asian, Native Hawaiian and Pacific Islander descent, concealing the disparities, the report said.
“We have shown the importance of disaggregating Asian and NHPI individuals, as these groups have disparate cancer mortality rates that are hidden when analyzed together,” researchers wrote. “Policies aimed at equitable cancer prevention, early detection, and treatment, as well as disaggregation of data for racial/ethnic subpopulations are needed to address disparities in cancer mortality across racial/ethnic groups.”
Those of Asian descent, the manuscript pointed out, have the lowest cancer death rates across every age group and, when combined with data on Native Hawaiian and Pacific Islanders, the death rate largely ended up reflecting the low incidence of the disease among Asian Americans
While the Office of Management and Budget disaggregated the Native Hawaiian and Pacific Islander populations from Asian Americans in 1997, the National Center for Health Statistics didn’t release single-race mortality data until almost two decades later, when all states implemented the new classification on death certificates, the report said. Therefore, data on Native Hawaiian and Pacific Islanders, who represent an estimated 0.4% of the U.S. population, remained “masked.”
The report, which also looked at cancer death rates across other racial groups, showed additional disparities. Data on cancer mortality rates among males showed Black men with the highest numbers, followed by whites and Latinos. In looking at women, the mortality rates were highest among Black women. Native Hawaiian and Pacific Islander women came second, followed by white females.
High cancer death rates in Black, Native Hawaiian and Pacific Islander communities are likely due in part to unequal access to health care, the report said. Marginalized communities are also more likely to receive “suboptimal” cancer treatment that may not be consistent with the recommended clinical practice guidelines, and are less likely to be included in clinical trials, the report noted.
Structural racism was another underlying cause of the racial and ethnic gaps in health. The American Cancer Society’s guidelines for cancer prevention, the researchers point out, focus on “modifiable lifestyle factors” like obesity and physical activity. However, Black, Latino, American Inuit, American Indian, Native Hawaiian and Pacific Islander communities, which have high obesity rates, are more likely to live in communities with food deserts, high rates of economic insecurity and greater barriers to physical activity.
The legacy of U.S. colonization of Hawai`i and the long history of “Western interference” has also contributed to health disparities among the Native Hawaiian and Pacific Islander populations, Dr. Loïc Le Marchand, associate director for population sciences at the University of Hawai`i Cancer Center, told NBC News.
“If we compare Polynesians in the South Pacific and Native Hawaiians, not only is the level of obesity higher [in Native Hawaiians], but the type of obesity is different,” Le Marchand said. “The distribution of fat is different. … It’s not just linked to eating more, but it’s also linked to composition of diet.”
More disaggregated data and better information on specific populations are critical, Le Marchand said, as they can make a difference in the decision-making. And while there are some programs in place in Hawaii and across the country that address these gaps in health care, they are still limited.
“Native Hawaiians have been disadvantaged, understudied ... for many decades,” Le Marchand said. “Those health issues exist and need to be addressed.”
Le Marchand said that when it comes to treating Native Hawaiian and Pacific Islander populations and other marginalized groups, it’s “not just funding a program here and there.” Integrating leaders from these communities is critical to dispense appropriate care and treatment, he said.
2 notes
·
View notes
Text
Thousand Word Preview: Something In The Water Ch. 8
She learned to disable a standard security system with 30 minutes of research on a library computer. That was nearly two years ago, the first time she ever surfaced. Knowing how to break into places and pick pockets was simply a need. All of the riches in the world meant nothing when they were in a form of currency most had never seen. Even her gems, her only possessions brought with her this time around, for reasons she still can’t piece together, can’t be appraised by any device existing on land.
This time has to be different, she told herself there would be no turning back after a few months of exploring and sowing her oats and she meant it. She needs a real plan, a real life, maybe even a real job. And to get all of that, she needs fake documents. An ID, a passport, birth certificate, social security card, the whole nine. She needs to be a person. But first, she needs to get out of the rain before the wrong person spots her.
At the top of a lonely hill is a battered summer bungalow, evacuated as soon as the storm broke. It will take days if not weeks for Isle De Granger to be a properly vacationable spot again, her people must not have taken that into account when they unleashed the storm on this place. They wanted her back home, not to make it even easier for her to stay away.
She pries the hammered wood off of a broken window, slips inside and looks for an alarm, finding none. These people were either more trusting or more stupid than the ones before. It’s not quite as nice as the last place either. No hammock in back, no clothes in the closet aside from a couple of drab men’s shirts that smell of dust, no photos on the walls, not even a TV or computer, just a sad old clock radio. She imagines the usual inhabitants are the types that like to ‘unplug’ during their time away from their real lives. But there are beds at least, and comfy looking ones at that.
She finds a little box of thumbtacks in a kitchen junk drawer and uses them to attach Rachel’s redone drawing to the wall of the master bedroom. It’s even nicer than the first one, more finished, with the girl’s initials printed in the corner along with a note.
I’m happy you stayed.
“I’m happy I did too,” Kory says out loud to no one in particular.
She removes the windbreaker Dick gave her, her dress, the sheets from the bed, and the shirts from the closet, and loads them into the wash. By the time they’re dry she’s nearly too exhausted to put the sheets back onto the bed and attempt to get the sleep that had evaded her all three nights at Detective Grayson’s house. Those nights were spent flipping and thrashing under the covers, wanting to go to his room and do more to him than just kiss. Because he kissed as if he did everything else just as well.
She couldn’t chance the trouble that might have arisen if she climbed into his bed and took it any further. The emotion of it all could have very well overtaken her to a point she couldn’t turn back from.
He already made her pulse race to a troubling degree just squeezing her with his thick, protecting arms, searching her curves with his inquisitive touch. To let him remove her clothes before she was truly ready for him or he for her, had the potential to end in utter disaster. She isn’t a monster, it’s not her way to lure innocent men to drowning, especially not him. The one who takes care of everyone like it’s his job, who took care of her with no hesitation at all.
“What are you?” he asked, as if he knew something wasn’t right but couldn't bring himself to care. It wasn’t just some supernatural push, she knew what that looked like. It was trust. And she couldn’t betray that no matter how much she wanted him.
Her slumber is deep and solid without him right down the hall. It’s the way it ought to be, she’s leaving this place at the soonest chance, no more time for distractions like Detective Grayson, his sad, sweet kid and her funny friends, no time to stay in one place where another hurricane could strike at any time, fueled by the strife of her absence. She just needs enough cash for a ferry to Rhode Island and another to the mainland, surely she could scare up a new existence there.
****
The cuffs were worked over with a blowtorch and a hammer found in Donna’s woodshed, just not hard enough to no longer count as evidence. They’re blackened, broken and buried in ash, but once pieced together, the shape of them line up almost perfectly with the imprint on Kovar’s neck, a sight still etched in Dick’s memory as if he were looking at it this very second. There’s hardly a shred of doubt, this is either the murder weapon, or a helluva coincidence. Either way, it’s a lead, the best one yet. They’re vintage cuffs, maybe from the 40s, possibly purchased somewhere or handed down. To find a potential seller would be a huge help, but there’s one trail of breadcrumbs available that is much easier to follow in the meantime.
While deputy Kent dusts the woodshed for prints, Dick goes to ask Donna for a look around the kitchen to get a list of all of the purchases inside. The person of interest left no receipts anywhere, so he’ll start with the closest grocery store, find out via security camera footage who the last person was to buy salmon steaks, Blue Moon ale, peaches, Lucky Charms, french cucumbers, a baguette, and raspberry sorbet.
“I feel like it has to be a woman, Right?” Donna says, clutching her chin ponderously as Dick jots everything down. “These are definitely lady groceries.”
“A little prejudiced don’t you think?” he says, even though he has the exact same assumption.
“And you think it’s a murderer?” she continues, her red pout forming a hard line.
“I don’t really know what to think, to be honest. I’m just glad there might be a chance at figuring it out.”
19 notes
·
View notes
Text
The Cybersecurity Jobs Disaster Is Getting Worse, And Firms Are Making Primary Errors With Hiring
Now is a wonderful time for upcoming talent to get the expertise, training, and certification they need to fill the cyber safety skills hole. Dr. Tucker’s tutorial pursuits include information security, software program engineering, web companies and programming, in addition to database applied sciences. You also need to be detail orientated as a result of it’s often not really easy to detect threats to cyber safety.
Many cyber security roles require sturdy communication and presentation expertise.
If you’ve done any research on the subject, you realize that the alternatives in info technology certifications are endless!
By encouraging their advisees to become engaged in their education, to meet their educational targets, and to develop the habit of learning, advisers assume a significant instructional role.
So incomes a bachelor's degree in cybersecurity is crucial in helping you be trained and qualified for job opportunities.
Global enterprises, small companies, and governments alike have to have groups of skilled cybersecurity personnel to develop and keep secure systems. As a computer hardware pupil, you’ll be taught about the numerous hardware sorts that comprise computer methods. Device hardware includes issues like circuit boards, CPUs, reminiscence, and adapters. With a database administration diploma, you’ll achieve the ability and experience required to handle databases securely.
Discovering Cybersecurity Jobs
Assembly language is a low-level language that speaks virtually directly to laptop hardware. It is an important software to have in a cyber security professional’s toolbelt. The certification reveals you know the way to audit, control, and secure enterprise data techniques.
Cyber Security Is Among The Highest Paying Jobs In The Information Know-how Area
The WGU cybersecurity program also boasts 14 top certifications that allow you to begin boosting your résumé earlier than you even graduate. Although security has turn out to be an integral a part of everyone’s lives, it’s nonetheless a complex topic. Over half of cybersecurity professionals queried stated that their employers have been at “moderate or extreme risk” as a result of talent shortages. People from IT backgrounds have a tendency to find that a lot of the abilities they already have translate properly to cyber safety.
#cyber security course london#cyber security degree online uk#cyber security courses in uk for international students
3 notes
·
View notes
Text
A Lethal Dose?
So just today I got the book Nirvana: The Day By Day Eyewitness Chronicle by Carrie Borzillo, which one of my fandom friends recommended to me because despite it being published in 2000, it still holds up, in part because the author was sure to cite all her sources and even reminded other authors to be just as diligent in the future.
(TW below the cut for discussions of overdose, suicide, murder, and blood. Viewer discretion is STRONGLY advised)
Getting to the point, I have a bad habit of skipping to the end of a book before reading anything else (I forget if I picked this habit up from my mom or if she's the exact opposite of me), and when reading the entry about Kurt's death, I noticed the oft-repeated claim that Kurt died with 1.52 milligrams of heroin in his system.
Before I go any further, I should clarify that this should be taken with a grain of salt to begin with. Kurt's autopsy reports were never officially released, despite plenty of attempts by conspiracist nuts like Richard Lee, because legally, Washington state isn't required to. And just to be sure, I looked this up as well. The Washington State Department of Health stated, "For security of personal information, only individuals with specific qualifying relationships, also known as qualified applicants, to the subject of the requested record can receive a death certificate or fetal death certificate. Identity and proof of qualifying relationship documentation is required." Given that I'm just a random fan who actively researches this in my spare time, I wouldn't be able to request this information.
Again, that doesn't stop idjits like Tom Grant and Lee from petitioning the state to release MORE photos of Kurt's dead body, to which I'm going to bring up a quote from another detective: “What are people going to gain from seeing pictures of Kurt Cobain laying on the ground with his hair blown back, with blood coming out of his nose and trauma to his eyes from a penetrating shotgun wound. How’s that going to benefit anybody?”
Honestly, as someone who has gone from believing Kurt was murdered to believing he killed himself, I can't agree more. I just don't see how seeing Kurt like that would benefit anybody, regardless of what side of the issue they stand on, especially knowing that Kurt's daughter has had to fight to keep the public from seeing her dad like that for years.
Apologies for the tangent.
Back to the primary subject, I remembered that a while back, I'd heard that toxicology reports can be a shot in the dark, as substances can accumulate in the body (I forget if it was just in the blood, or this applies to urine toxicology results as well) and can lead to an inaccurate reading.
I didn't even remember where I'd heard this before, but it was a lead I had to pursue, nonetheless.
What I found was a report showing that in postmortem examinations of fentanyl overdose victims, samples of their blood showed a dose of up to nine times higher than an in vivo sample of the same concentration. This phenomenon is called "post-mortem redistribution" which the National Institute of Health describes thusly: "Postmortem redistribution (PMR) refers to the changes that occur in drug concentrations after death. It involves the redistribution of drugs into blood from solid organs such as the lungs, liver, and myocardium. Drug properties such as volume of distribution, lipophilicity, and pKa are important factors. Basic, highly lipophilic drugs with a volume of distribution greater than 3 l/kg are most likely to undergo PMR."
In short, this is why if you're in morturary school, you're being taught to take blood samples from the femoral artery instead of the heart.
Again, this is to be taken with a massive grain of salt, but on April 14, 1994, ten days after Kurt died, the Seattle Post-Intelligencer was the paper that broke the story that Kurt died with 1.52 milligrams of morphine in his blood. Honestly, I'm unsure of where they even got this information, but it's the only figure I have to work with.
Getting to the math portion, I then divided 1.52 milligrams by nine, seeing as while I'm not sure where they got the blood samples from, Kurt lying dead for three days before being discovered surely couldn't have helped. With this, I got a figure of .169, or .17. Not only does this seem much more logical to me than the original figure, especially considering Kurt had just fled from rehab four days before the estimated date of death, but it also overlapped with a figure I'd found earlier in the afternoon when I was trying to figure out if the original figure would constitute a legal dose. In short, in 1997, a study found that people who overdosed on heroin in Southwest Sydney (SWS), had an average heroin dose of 0.35 for every 0.09 mg/l, although the levels ranged from 0.08-1.45 mg/l, which accounted for 90% of heroin related deaths over that year.
So to summarize all that, 1.52 is an improbable number, even considering Kurt was what some may call an experienced addict, but I do believe that PMR would explain why he had such a high concentration in his blood, although it is hard to say for certain given that only Kurt's relatives and government agencies can access that information.
I know for some this won't totally disprove the murder theory, but for people like me, it does explain at least one of the inconsistencies of the case.
#nirvana#kurt cobain#tw: drugs#tw: overdose#tw: suicide#tw: blood#not me being an amateur mortician again
4 notes
·
View notes
Text
Fire Safety Solutions: Where to Find Professional Fire Suppression Companies Near Me
Introduction:
Fire safety is a paramount concern for individuals and businesses alike. In the event of a fire emergency, having effective fire suppression systems in place can mean the difference between minor property damage and catastrophic loss. Professional fire suppression companies specialize in designing, installing, and maintaining fire suppression systems to protect lives and property from the devastating effects of fire. In this blog post, we'll explore the importance of professional fire suppression solutions and where to find reputable companies near you to ensure your fire safety needs are met.

Understanding Fire Suppression Systems:
Fire suppression systems are designed to detect, control, and extinguish fires in various environments, including residential, commercial, and industrial settings. These systems employ a combination of techniques and technologies to suppress fires quickly and effectively, minimizing damage and preventing the spread of flames. Some common types of fire suppression systems include:
Sprinkler Systems: Sprinkler systems are the most widely used fire suppression systems and are designed to automatically release water or other extinguishing agents when triggered by heat or smoke. Sprinkler systems are highly effective in controlling fires and can be installed in various configurations to suit different building layouts and occupancy types.
Clean Agent Systems: Clean agent fire suppression systems use specialized gases or chemical agents to extinguish fires without causing damage to sensitive equipment or materials. These systems are commonly used in data centers, server rooms, and other environments where water-based suppression methods may be impractical or damaging.
Foam Systems: Foam fire suppression systems utilize foam concentrate mixed with water to create a foam blanket that smothers and extinguishes fires. Foam systems are particularly effective for combating flammable liquid fires and are commonly used in industrial and marine applications.
Carbon Dioxide (CO2) Systems: CO2 fire suppression systems release carbon dioxide gas to displace oxygen and extinguish fires by suffocation. These systems are ideal for protecting electrical equipment, machinery, and other sensitive assets where water-based suppression methods could cause damage.
Finding Professional Fire Suppression Companies Near Me:
When it comes to fire safety, it's crucial to work with experienced and reputable fire suppression companies to ensure the reliability and effectiveness of your fire suppression systems. Here are some steps to help you find professional fire suppression companies near you:
Research Local Providers: Start by researching fire suppression companies near me that specialize in designing, installing, and servicing fire suppression systems. Look for companies with extensive experience, industry certifications, and a proven track record of reliability and customer satisfaction.
Check Credentials: Verify that the fire suppression company is properly licensed, insured, and certified to perform fire suppression system installations and maintenance. Ask about their qualifications, training, and certifications to ensure they have the expertise and capabilities to meet your fire safety needs.
Evaluate Services Offered: Consider the range of services offered by fire suppression companies, including system design, installation, inspection, maintenance, and emergency repairs. Choose a company that offers comprehensive services tailored to your specific requirements and budget.
Request References: Ask potential fire suppression companies for references from past clients or customers. Speaking with satisfied customers can provide valuable insights into the quality of service, professionalism, and reliability of the company, helping you make an informed decision.
Request Quotes and Estimates: Contact multiple fire suppression companies to request quotes and estimates for their services. Compare pricing, service offerings, and warranties to find the best value for your needs. Keep in mind that while cost is important, it should not be the sole determining factor—prioritize reliability and expertise when selecting a company.
Conclusion:
Fire safety is a critical consideration for individuals and businesses alike, and having effective fire suppression systems in place is essential for protecting lives and property in the event of a fire emergency. By working with professional fire suppression companies near you, you can ensure that your fire safety needs are met with reliable and effective solutions. Whether you need a new fire suppression system installed, an existing system inspected and maintained, or emergency repairs performed, professional fire suppression companies have the expertise and resources to help. By following the steps outlined in this blog post, you can find reputable fire suppression companies near you and take proactive steps to enhance your fire safety preparedness efforts.
0 notes
Text
How Much Does a Private Investigator Cost
In a world where mysteries abound, and secrets lurk in the shadows, private investigators serve as modern-day sherlocks, unraveling enigmas and exposing truths hidden from plain sight. From uncovering infidelities to solving cold cases, these investigators of the 21st century are the embodiment of intrigue and mystery. But as enticing as their work may be, one burning question lingers in the minds of many: How much does it cost to employ the services of a private investigator? Join us on a journey through the clandestine world of investigation as we delve into the factors that influence pricing, decode the mysteries behind fee structures, and discover whether unveiling secrets comes with a hefty price tag. Strap in, dear reader, for this exploration promises to be as thrilling and revealing as any case these elusive detectives take.

Overview of private investigator services
Private investigator services offer a blend of mystery-solving skills, technology, and investigative techniques to provide clients with crucial answers. These professionals handle various cases, from conducting background checks and surveillance to uncovering hidden information that can assist in legal matters. Private investigators often collaborate closely with law enforcement agencies, lawyers, and individuals seeking the truth.
One key aspect of private investigator services is their ability to adapt to the ever-changing landscape of technology. With access to sophisticated tools like GPS tracking devices and computer forensics software, investigators can gather evidence more efficiently than ever. This technological advantage enables them to uncover digital footprints and trace individuals' whereabouts accurately, aiding in the resolution of complex cases. As such, private investigator services have become indispensable in many legal proceedings and personal matters where traditional methods may fall short.
Click Here for hire private investigator for phone hacking
Factors Affecting Cost: Complexity, expertise, location
When it comes to determining the cost of hiring a private investigator, several factors come into play that can significantly influence the final price. One key factor is the complexity of the investigation itself. Cases requiring intricate surveillance, extensive research, or advanced technology will incur higher costs due to the increased time and resources needed.
Moreover, the expertise level of the private investigator also plays a crucial role in determining the overall cost. Experienced investigators with specialized skills or certifications may charge more for their services based on their reputation and track record of successful cases. Additionally, the location where the investigation takes place can also impact costs. Investigations conducted in high-cost-of-living areas or remote locations may incur additional expenses, such as travel accommodations and logistical challenges, leading to higher client fees.
Typical Pricing Structure: Hourly rates, retainer fees
When hiring a private investigator, understanding the typical pricing structure is essential. Private investigators commonly charge either hourly rates or retainer fees for their services. Hourly rates can range from $50 to $150 per hour, depending on the complexity of the investigation and the investigator's experience. On the other hand, retainer fees are an upfront payment that covers a specified number of hours of investigative work.
One key point to consider is that some private investigators may require a combination of hourly rates and retainer fees, depending on the nature of the investigation. This hybrid model allows for more billing flexibility and can benefit clients with varying needs and budget constraints. Clients must communicate openly with their private investigator about pricing structures from the outset to avoid surprises. By understanding these typical pricing structures, clients can make informed decisions when hiring a private investigator and ensure they receive quality services within their budgetary constraints.
Additional Costs: Travel expenses, surveillance equipment
When considering the costs of hiring a private investigator, it's crucial to consider additional expenses such as travel costs and surveillance equipment. Travel expenses can vary depending on the distance involved in the investigation, with out-of-town or international cases typically resulting in higher fees. Private investigators often need to conduct surveillance for extended periods, necessitating specialized equipment like high-quality cameras, audio devices, and GPS tracking tools. These technological resources incur initial costs and require maintenance and upgrades to ensure effective monitoring throughout the investigation.
Furthermore, the expertise required to operate surveillance equipment effectively adds another cost to hiring a private investigator. Skilled professionals with experience in handling complex gadgets are essential for generating reliable evidence without compromising the integrity of the investigation process. Clients must be aware that these additional costs are critical in carrying out a thorough and successful investigative operation. By allocating the budget towards travel expenses and quality surveillance equipment, clients can expect detailed findings backed by solid resources to help them achieve their desired outcomes effectively and efficiently.
Budgeting Tips: Research options, negotiate rates
When it comes to hiring a private investigator, budgeting is vital. Researching the options available in your area can lead to finding experienced professionals at more reasonable rates. Don't settle for the first quote you receive; negotiating rates is often possible and can help you stay within your budget while still getting quality investigative services.
In addition to researching and negotiating, consider looking for package deals or special discounts that some investigators may offer. By proactively seeking out cost-saving opportunities, you can make the most of your budget without compromising on the quality of work done by your chosen investigator. Remember, thorough research and strategic negotiation are essential to ensure you get the best value for your money when hiring a private investigator.
Case Studies: Real examples of cost breakdowns
Today, let's delve into real case studies to understand the intricacies of private investigator cost breakdowns. One striking example involves a complex marital infidelity investigation that required extensive surveillance and background checks. The total cost for this case surpassed $10,000 due to extended hours and specialized equipment needed for successful outcomes.
In another scenario, a business hired a private investigator to uncover fraudulent activities within their organization. The investigation involved forensic accounting services and undercover operations that unraveled a significant embezzlement scheme. This in-depth probe cost the company over $20,000 but ultimately saved them millions in potential losses.
These examples demonstrate that private investigator costs can vary significantly based on the complexity and scope of each case. It highlights the importance of understanding factors contributing to expenses in such investigations, shedding light on why prices differ widely across different scenarios.
Importance of balancing cost and quality
Balancing cost and quality must be considered when considering hiring a private investigator. Opting for the cheapest option may save you money upfront but could result in subpar results or ethical concerns. On the other hand, focusing solely on quality without regard to cost can lead to excessive spending that may not align with your needs or budgetary constraints.
Striking a balance between cost and quality involves:
Carefully evaluate your priorities
Determining the level of expertise required for your specific case
Setting realistic expectations
By understanding that cost does not always directly correlate with quality, individuals seeking investigative services can make informed decisions that ensure efficiency and effectiveness in achieving their desired outcomes. In conclusion, finding the equilibrium between affordability and excellence is critical to successful private investigations while providing peace of mind.
0 notes