#web application advancement
Text
Why Is ReactJS The Most Preferred Frontend Development Tech?
In the ever-evolving landscape of web development, one technology has consistently stood out for its efficiency, flexibility, and robustness: React JS. Developed by Facebook in 2013, ReactJS has revolutionized the way developers create interactive and dynamic user interfaces. But what exactly is React, and why has it become a go-to choice for developers and companies alike? Let’s dive into the…

View On WordPress
#API Development and Integration#developing web applications#Learn advanced programming#Mobile App Development
0 notes
Text
How to improve navigation in a Shopify Store using UX?
Want users to engage with your products on your website?
Improving navigation in your Shopify Store can play an important role in providing a positive User Experience.

Here are some tips from web application Developers that can help you improve your navigation on your Shopify store:
The main menu is the first place a user views on your Shopify page. It is very important that you promptly display the categories and subcategories on the page so that it gives a strong clear idea to the viewer as to what to expect and which category to choose. It's better to use concise and clear descriptions.
We do not want to overwhelm our users with too many options. Thus it is necessary to limit the number of options on the main menu and one might consider having dropdown menus for subcategories to keep the main menu clean.
It should not be difficult for a user to find what they are looking for by creating a prominent search bar on the main menu with autofill options we can make it easier for them to find out what they might be looking for.
One might be willing to create an optimized product filter so that users can filter out the options that they will be interested in looking at. Filters could be size, color, price, etc. Filters should be easy to find out and apply.
Navigation should be mobile-friendly. Most users are on smartphones and tablets thus it is very important to have an interface working smoothly on smaller screens.
Including breadcrumb navigation can help users understand the structure of your store and understand where they are and facilitate navigating to previous pages.
Make sure that the call to action is consistent, prominent, and visually appealing for the user. You might want to include CTAs like add to cart or buy now etc.
Recommend popular products on the homepage or subcategory pages and use exciting descriptions and images for users to be interested in exploring more.
You might include sticky Navigation so that users get the important information displayed even while scrolling various pages.
One should implement an easy checkout process, include proper indicators of steps for checkout, and include minimum steps on checkout. Also shipping charges and any kind of extra charges must be mentioned before checkout to ignore any kind of friction in the process.
One must consider carrying on rigorous A/b testing on various pages to make sure menu structure, buttons, clickons, and every element of navigation is functioning properly.
The attention span and patience of the user are very short. It is very important to make sure that the pages are fast-loading. Slow-loading pages might create frustration among users and lead to an increase in bounce rates.
As we know:
Providing a user-friendly and engaging navigation experience to the users through better UX practices can help improve customer satisfaction and contribute to conversions.
Thus it is very important to trust an experienced UX designer to help you give your user a satisfactory navigation experience.
Tech Wishes has been providing such services for years now. So don't forget to contact them to grow your Shopify business and provide the best user experience to your customers.
#custom web development#web and app development#custom web application development company#custom web development company#custom website development#custom website development services#advanced web development#custom web app development#web app development agency#web application developers
0 notes
Text
youtube
Watch the American Climate Leadership Awards 2024 now: https://youtu.be/bWiW4Rp8vF0?feature=shared
The American Climate Leadership Awards 2024 broadcast recording is now available on ecoAmerica's YouTube channel for viewers to be inspired by active climate leaders. Watch to find out which finalist received the $50,000 grand prize! Hosted by Vanessa Hauc and featuring Bill McKibben and Katharine Hayhoe!
#ACLA24#ACLA24Leaders#youtube#youtube video#climate leaders#climate solutions#climate action#climate and environment#climate#climate change#climate and health#climate blog#climate justice#climate news#weather and climate#environmental news#environment#environmental awareness#environment and health#environmental#environmental issues#environmental justice#environment protection#environmental health#Youtube
7K notes
·
View notes
Text
Fortifying Digital Frontiers: Navigating Cybersecurity Challenges with Advanced Web Application Firewall
0 notes
Text
Utilize Right Social Media Marketing at Right Time

Enough has already been said about social media, how it reshapes consumer behavior, and how organizations can use it to turn the wheel of fortune in its favor.
Despite the massive amount of information on the web, so many businesses struggle to wrap their head around social media marketing and how it works. Social media is a network of over 3.5 billion users that just love to share, seek, and create information.
As a marketer or business owner, how could you utilize this network in a way that produces great results for your business?
Let's explore this!
The essentials of a effective social media marketing strategy
Social media marketing strategy will look different for every business, but here are the things they will all have in common:
Knowledge of your audience
You need to know about what platforms they use, when they go on them and why, what content they like, who else they’re following, and more.
Brand identity
A strong, unique brand image is an essential part of building a good relationship with customers.
Analytics
Quantifiable insights will inform your strategy, including who you’re reaching, the right content to share, the best times to post, and more.
Content strategy
While there is a level of spontaneity on social, you’ll need a structured content strategy to be able to have a consistent voice and produce quality content regularly.
Inbound approach
Focus on adding value through useful and interesting content and building up those around you. This, in turn, will organically promote your business.
Regular activity
Social media is a real-time platform. If you want to use it to grow your business, you need to post regularly, stay on top of engagements with your business, engage back, keep up with trends, and maintain accurate profiles.
5 Benefits Of Social Media Marketing
The concept of social media marketing has evolved over the years. A few years ago, the sole purpose of using social media channels was to generate website traffic.
Today, it has developed into something more than just a place to broadcast content.
In this article you should know about social media marketing:
SMM Builds Stronger Relationships With Customers
If you think social media marketing is all about selling and promoting, rethink. Successful brands connect and engage with their social media audiences to build lasting relationships.
Rather than selling your products or services, you can simply ask your social media followers questions about your products or share something that could make life easier for your audience.
It's always a must to serve people first before asking them to invest with you.
SMM Consistently Warms Up A New Audience For Your Business
There’s nothing worse than facing a cold audience or people who haven't interacted with your brand before.
Social media marketing opens up doors to tools and tactics that make it easy to warm up a new audience for your business.
Facebook and other social platforms allow you to use content to connect with the potential audience and warm them up. For example, creating an interesting Facebook video ad can drive people to know more about you.
SMM Generates More Leads & Conversions
Platforms like Facebook, Instagram, Twitter, and LinkedIn allows companies to generate leads. You can use a mix of paid and organic tactics to boost conversions.
Video marketing, paid ad campaigns, giveaways, and email opt-ins are some of the leading strategies to get prospects into your sales funnel.
Since everything happens online, SMM is a measurable, quicker, and easier way to build a database of prospects. With increased visibility, your business finds plenty of opportunities for conversion.
Compelling content can lead your social media followers to your company’s website and turn them into loyal customers.
SMM Gives You A Leg Up On Competitors
There’s a lot to learn from your competitors’ social media presence, especially if you have just started exploring social media and lack good marketing ideas.
Progressive companies always monitor their competition to see what’s working for them and whatnot. Tracking what your competitors are up to should be a key part of your social media marketing strategy.
You can start experimenting with things that are working for your competitors.
SMM Is Cost-Effective
Social media marketing is probably the most cost-efficient and diverse way of promoting a business.
It doesn’t cost anything to create a profile on most social networking sites. In case you want to run a paid campaign to boost your content, the cost is relatively low as compared to other advertising platforms.
One of the benefits of social media marketing is that it allows you to track your performance and fine-tune your strategy using real-time data.
Digital Marketing Companies like Mpiric Software are excellent for getting practical exposure in digital marketing at affordable prices.
There’s no better growth strategy for your business than social media marketing that is incorporated with a killer influencer marketing strategy.
#Mpiric Software#web development services#web Designing#web designing company#digital marketing#blockchain technology#Blockchain security#mobile application development#UI\UX Design#blockchain development companies#it services#advanced cryptographic techniques#social media marketing#social media marketing strategy#social media marketing campaign#paid campaign#digital advertising
0 notes
Text
Sims 2 Tools - Repository Wizard
Repository Wizard
The Repository Wizard is a utility for automating the repository technique for objects and clothing.
Object Mode
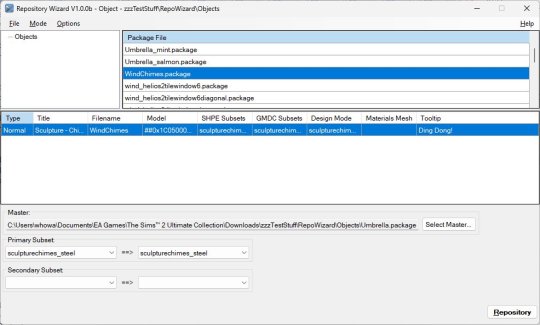
This mode of the Repository Wizard automates the process described by HugeLunatic in their Repository Technique tutorial.
Clothing Mode
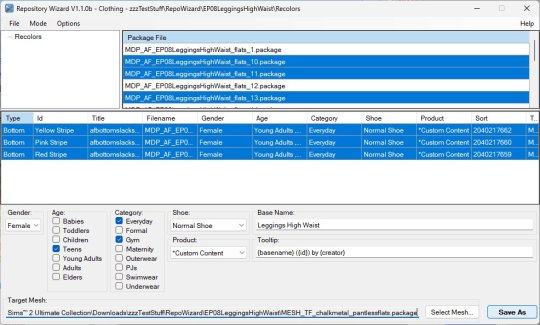
This mode of the Repository Wizard creates new re-colours for a new/modified mesh based on an existing mesh with its own set of re-colours.
This is NOT the simple approach to the repository method of linking the dependant's TXMT resource(s) to the donor's TXTR resource(s), but a new, more advanced, approach of linking via the 3IDR resource.
See the application’s web page for extensive details about both modes.
If you do not know what the repository technique is, or why you would want to use it, this application is not for you!
266 notes
·
View notes
Text
So I don't know how people on this app feel about the shit-house that is TikTok but in the US right now the ban they're trying to implement on it is a complete red herring and it needs to be stopped.
They are quite literally trying to implement Patriot Act 2.0 with the RESTRICT Act and using TikTok and China to scare the American public into buying into it wholesale when this shit will change the face of the internet. Here are some excerpts from what the bill would cover on the Infrastructure side:
SEC. 5. Considerations.
(a) Priority information and communications technology areas.—In carrying out sections 3 and 4, the Secretary shall prioritize evaluation of—
(1) information and communications technology products or services used by a party to a covered transaction in a sector designated as critical infrastructure in Policy Directive 21 (February 12, 2013; relating to critical infrastructure security and resilience);
(2) software, hardware, or any other product or service integral to telecommunications products and services, including—
(A) wireless local area networks;
(B) mobile networks;
(C) satellite payloads;
(D) satellite operations and control;
(E) cable access points;
(F) wireline access points;
(G) core networking systems;
(H) long-, short-, and back-haul networks; or
(I) edge computer platforms;
(3) any software, hardware, or any other product or service integral to data hosting or computing service that uses, processes, or retains, or is expected to use, process, or retain, sensitive personal data with respect to greater than 1,000,000 persons in the United States at any point during the year period preceding the date on which the covered transaction is referred to the Secretary for review or the Secretary initiates review of the covered transaction, including—
(A) internet hosting services;
(B) cloud-based or distributed computing and data storage;
(C) machine learning, predictive analytics, and data science products and services, including those involving the provision of services to assist a party utilize, manage, or maintain open-source software;
(D) managed services; and
(E) content delivery services;
(4) internet- or network-enabled sensors, webcams, end-point surveillance or monitoring devices, modems and home networking devices if greater than 1,000,000 units have been sold to persons in the United States at any point during the year period preceding the date on which the covered transaction is referred to the Secretary for review or the Secretary initiates review of the covered transaction;
(5) unmanned vehicles, including drones and other aerials systems, autonomous or semi-autonomous vehicles, or any other product or service integral to the provision, maintenance, or management of such products or services;
(6) software designed or used primarily for connecting with and communicating via the internet that is in use by greater than 1,000,000 persons in the United States at any point during the year period preceding the date on which the covered transaction is referred to the Secretary for review or the Secretary initiates review of the covered transaction, including—
(A) desktop applications;
(B) mobile applications;
(C) gaming applications;
(D) payment applications; or
(E) web-based applications; or
(7) information and communications technology products and services integral to—
(A) artificial intelligence and machine learning;
(B) quantum key distribution;
(C) quantum communications;
(D) quantum computing;
(E) post-quantum cryptography;
(F) autonomous systems;
(G) advanced robotics;
(H) biotechnology;
(I) synthetic biology;
(J) computational biology; and
(K) e-commerce technology and services, including any electronic techniques for accomplishing business transactions, online retail, internet-enabled logistics, internet-enabled payment technology, and online marketplaces.
(b) Considerations relating to undue and unacceptable risks.—In determining whether a covered transaction poses an undue or unacceptable risk under section 3(a) or 4(a), the Secretary—
(1) shall, as the Secretary determines appropriate and in consultation with appropriate agency heads, consider, where available—
(A) any removal or exclusion order issued by the Secretary of Homeland Security, the Secretary of Defense, or the Director of National Intelligence pursuant to recommendations of the Federal Acquisition Security Council pursuant to section 1323 of title 41, United States Code;
(B) any order or license revocation issued by the Federal Communications Commission with respect to a transacting party, or any consent decree imposed by the Federal Trade Commission with respect to a transacting party;
(C) any relevant provision of the Defense Federal Acquisition Regulation and the Federal Acquisition Regulation, and the respective supplements to those regulations;
(D) any actual or potential threats to the execution of a national critical function identified by the Director of the Cybersecurity and Infrastructure Security Agency;
(E) the nature, degree, and likelihood of consequence to the public and private sectors of the United States that would occur if vulnerabilities of the information and communications technologies services supply chain were to be exploited; and
(F) any other source of information that the Secretary determines appropriate; and
(2) may consider, where available, any relevant threat assessment or report prepared by the Director of National Intelligence completed or conducted at the request of the Secretary.

Look at that, does that look like it just covers the one app? NO! This would cover EVERYTHING that so much as LOOKS at the internet from the point this bill goes live.
It gets worse though, you wanna see what the penalties are?

(b) Civil penalties.—The Secretary may impose the following civil penalties on a person for each violation by that person of this Act or any regulation, order, direction, mitigation measure, prohibition, or other authorization issued under this Act:
(1) A fine of not more than $250,000 or an amount that is twice the value of the transaction that is the basis of the violation with respect to which the penalty is imposed, whichever is greater.
(2) Revocation of any mitigation measure or authorization issued under this Act to the person.
(c) Criminal penalties.—
(1) IN GENERAL.—A person who willfully commits, willfully attempts to commit, or willfully conspires to commit, or aids or abets in the commission of an unlawful act described in subsection (a) shall, upon conviction, be fined not more than $1,000,000, or if a natural person, may be imprisoned for not more than 20 years, or both.
(2) CIVIL FORFEITURE.—
(A) FORFEITURE.—
(i) IN GENERAL.—Any property, real or personal, tangible or intangible, used or intended to be used, in any manner, to commit or facilitate a violation or attempted violation described in paragraph (1) shall be subject to forfeiture to the United States.
(ii) PROCEEDS.—Any property, real or personal, tangible or intangible, constituting or traceable to the gross proceeds taken, obtained, or retained, in connection with or as a result of a violation or attempted violation described in paragraph (1) shall be subject to forfeiture to the United States.
(B) PROCEDURE.—Seizures and forfeitures under this subsection shall be governed by the provisions of chapter 46 of title 18, United States Code, relating to civil forfeitures, except that such duties as are imposed on the Secretary of Treasury under the customs laws described in section 981(d) of title 18, United States Code, shall be performed by such officers, agents, and other persons as may be designated for that purpose by the Secretary of Homeland Security or the Attorney General.
(3) CRIMINAL FORFEITURE.—
(A) FORFEITURE.—Any person who is convicted under paragraph (1) shall, in addition to any other penalty, forfeit to the United States—
(i) any property, real or personal, tangible or intangible, used or intended to be used, in any manner, to commit or facilitate the violation or attempted violation of paragraph (1); and
(ii) any property, real or personal, tangible or intangible, constituting or traceable to the gross proceeds taken, obtained, or retained, in connection with or as a result of the violation.
(B) PROCEDURE.—The criminal forfeiture of property under this paragraph, including any seizure and disposition of the property, and any related judicial proceeding, shall be governed by the provisions of section 413 of the Controlled Substances Act (21 U.S.C. 853), except subsections (a) and (d) of that section.
You read that right, you could be fined up to A MILLION FUCKING DOLLARS for knowingly violating the restrict act, so all those people telling you to "just use a VPN" to keep using TikTok? Guess what? That falls under the criminal guidelines of this bill and they're giving you some horrible fucking advice.
Also, VPN's as a whole, if this bill passes, will take a goddamn nose dive in this country because they are another thing that will be covered in this bill.
They chose the perfect name for it, RESTRICT, because that's what it's going to do to our freedoms in this so called "land of the free".
Please, if you are a United States citizen of voting age reach out to your legislature and tell them you do not want this to pass and you will vote against them in the next primary if it does. This is a make or break moment for you if you're younger. Do not allow your generation to suffer a second Patriot Act like those of us that unfortunately allowed for the first one to happen.
And if you support this, I can only assume you're delusional or a paid shill, either way I hope you rot in whatever hell you believe in.
#politics#restrict bill#tiktok#tiktok ban#s.686#us politics#tiktok senate hearing#land of the free i guess#patriot act#patriot act 2.0
890 notes
·
View notes
Text
MC: How's everyone's experience? *while smiling in amusement*
The first-years: *cheering*
The sophomores: *yells* NOT GOOD!
MC: Ara! Why is that? *pretends to be shocked*
Professor Crewel: Misbehaving puppies, you have no reason to complain when the sophomores were allowed to use magic while the freshmen couldn't.
Professor Vargas: You were all so cocky before the event started!
*The third-years who have watched the scene unfold*
*The first years beating their senpais at their own game*
Lilia: This teacher is quite amazing. Wouldn't you agree, Malleus?
Malleus: Yes. Teaching the students not to depend so much on using magic.
Vil: We could understand why as they're someone who can't use magic themselves, however...
Lilia and Malleus: ...
Vil: Judging by how they have influenced these students, it might be that they know more than their field.
Deuce: Let us treat you, housewarden sir!
Ace: Yeah. Bet your back hurt from falling from the spider web.
Riddle: And whose fault do you think is that?!
Ace: You wouldn't have fallen if you didn't mind our teasing, but no.
MC: That's right, Mr. Rosehearts. In fact, it wasn't any difficult. Mr. Trappola and Mr. Spade only triggered you ever so slightly.
Riddle: Gnghh!!!
MC: *pats his head* Now I'm thinking that you need a whole lot of self-meditation.
Riddle: I don't need that! I—
Riddle: *suddenly falls asleep*
Ace and Deuce: ...
Ace: When will you teach that to us?
MC: Next class. *smiles*
Floyd: Hello, guppy~.
Jade: That was a fantastic performance.
Epel: Floyd-senpai and Jade senpai...
Floyd: You moved so fast that my eyes couldn't keep up.
Jade: And we were not able to sense you at all.
Epel: That's all thanks to MC-sense—
Epel: *got hit by a piece of folded paper on the nose* Ow...
Jade: Are you alright, Epel?
Epel: Yes. By the way, Sensei doesn't like it when I don't take credit for my hardwork.
Jade: *chuckles* Why, they're certainly right with that.
Floyd: But, who hit you with that?
Epel: Sensei.
Jade and Floyd: *starts looking around*
Floyd: From where?
Jack and Sebek: *arguing, because they almost got caught by the sophomores when they were trying to conceal their presence*
Jack: I told you to shut your big mouth.
Sebek: Your ears were poking out!
Silver: Why it should matter when you've won?
Ruggie: Yeah.
Sebek: You don't understand! Sensei wouldn't excuse that—
MC: Sebek~ My favorite student. Have you not learned a thing or two about teamwork?
Sebek: ...
Jack: ...
MC: And you too, Mr. Howl. Though it was my mistake for partnering you two.
Jack: Sorry, sensei...
Sebek: P-Please don't blame yourself, sensei!
MC: Hmm... *chuckles* But it's okay. You have improved a lot. I hope you both are ready for more advanced lessons.
MC: Isn't that right, Mr. Kingscholar?
Leona: !!! *shocked as to how they know he's approaching from behind*
Ruggie and Silver: ...
The professors: *having a meeting after the event*
Crowley: Is everyone here except Professor MC?
The professors: Yes.
Crowley: Hm. I think everyone has understood the purpose of this event.
Crowley: ...
Crowley: We've been neglecting the majority of them!
Professor Trein: Headmage, no... That's not it.
Professor Crewel: The purpose of the event is to show that our students are capable of learning much more. As proven by the first-years.
Crowley: O-Oh. Is that so?
Professor Vargas: We should think more outside the box!
MC: The students are uniquely intelligent enough. Just lacking when it comes to application. Hehe~.
Crowley and the professors: *screaming*
Crowley: H-How long have you been here?
MC: A few minutes ago. I was resting on the ceiling. *smiles cutely*
Crowley and the professors: ...
#twisted wonderland#twst mc#twst crewel#twst lilia#twst malleus#twst vil#twst ace#twst deuce#twst riddle#twst jade#twst floyd#twst epel#twst sebek#twst jack#twst silver#twst ruggie#twst leona#twst vargas#twst trein#twst crowley#twst professor mc
829 notes
·
View notes
Text
http://brandefense.io/ - Devasa+
Our platform, which performs risk control of your sites and applications, is preferred by thousands of people every year. Thanks to our Threat intelligence tool, it is possible to get all the intelligence about your sites. People who do cyber intelligence research can have information about cyber attacks thanks to our platform. Our completely reliable brandefense.io platform has been among the sites that have been serving for quite some time.
It is possible to use deep web monitoring networks, which are frequently used in advanced applications, through our site. Our platform, which is preferred by thousands of people every year, stands out in this field. Thanks to our Breach monitoring panel, you can monitor all violations on your site. It becomes possible to monitor all kinds of security vulnerabilities through the vulnerability intelligence system.
2K notes
·
View notes
Text
Everything You Need To Know About Create React App
Everything You Need To Know About Create React App
The configuration of resources can be a time-consuming and difficult operation while creating a React application. There are many moving pieces in any React application. You might wish to configure Babel to translate JSX into code suitable for browsers. Additionally, you might need to set up Webpack to pack the assets for your project. You might have to put a lot of time and effort into all of…

View On WordPress
0 notes
Note
hi hi! love your blog! I am also working on building sites for my portfolio but am a little stumped on how/where to deploy them. would you mind sharing what you are using for deployment? thanks!
Places to Deploy Your Website

Hiya! I know a few places I've tried in the past and some I am yet to try but I know other developers use them!

GitHub pages
GitHub Pages is a free static site hosting service that allows you to publish your website directly from a GitHub repository. It supports HTML, CSS, and JavaScript, as well as Jekyll, a static site generator. I used GitHub pages a lot since I use GitHub to keep all my repositories.
Replit
Replit is a cloud-based development environment that provides an integrated IDE, code editor, and hosting platform all in one place. With Replit, you can easily create and deploy web apps, games, and other projects in multiple programming languages such as Python, HTML, CSS, and JavaScript. I use Replit a lot too for my other much smaller projects that I can’t upload on GitHub to run the program online!
Netlify
Netlify offers a free plan for static site hosting that includes features such as continuous deployment, custom domains, and SSL encryption. It supports HTML, CSS, and JavaScript, as well as serverless functions and other backend technologies.
Heroku
Heroku offers a free plan for hobbyist developers that allows you to deploy up to 5 applications. It supports many languages and frameworks, including Ruby, Node.js, Python, Java, PHP, and Go. Heroku allows free hosting for small applications.
Firebase Hosting
Firebase Hosting is a free service that allows you to host and deploy your web app or static content to a global content delivery network (CDN) with SSL encryption. It supports HTML, CSS, JavaScript, and other static assets. It allows free hosting for small applications.
Surge
Surge is a free static site hosting service that allows you to publish your website with a custom domain or a Surge subdomain. It supports HTML, CSS, JavaScript, and other static assets. Allows free hosting with unlimited bandwidth.

Each of these free deployment options has its own cons such as:
Its lack of server-side functionality
Limited database support
The cost of advanced features
Limited control over the infrastructure
May not be suitable for more complex websites or applications
However, for small projects, I think you’ll be fine with the free options!
Hoped this helps and good luck with your websites’ deployments! 🥰🙌🏾💗

#my asks#codeblr#coding#progblr#programming#studying#studyblr#developer#developers#comp sci#computer science#cs student#cs studyblr#resources#coding resources#deployment#deploy websites#portfolio#deployment websites#tech#web dev
197 notes
·
View notes
Note
hello! what would you say is the best draco characterisation you’ve ever read in a fic? and what have you read recently that you really liked and would read again?
also, i love everything you write :) thanks in advance!
I once saw this fanart that depicted the three main forms of Draco in Drarry and I have to say it's the most accurate thing I've ever seen lmao. My personal preference is somewhere between 'nutcase' and 'fake it till you make it' Draco. For light-hearted fics, I like those that capture the meanness of Draco's humour and his difficult personality; for serious fics I enjoy those where he truly wavers on the line of moral ambiguity.
Away Childish Things by lettered
Harry gets de-aged. Malfoy has to help him.
A great exploration of all the parts that make up the whole of Draco Malfoy.
any day now by oknowkiss
Draco Malfoy considers the circle.
I like this Draco for his moral greyness, self-preservation, internal conflict and risk aversion
Temptation on the Warfront by alizarincrims0n
Draco Malfoy is forced into hiding with the Golden Trio and dragged into their search for horcruxes. What ensues is a journey of redemption, unexpected friendships and an unwanted, turbulent romance with Harry Potter. Warnings for swearing, sexual content, and dark themes.
This is probably one of the most plausible DH-era Draco's I've ever read. The way he speaks to Hermione alone is enough to put it on this list. It's rare to find contemporary Drarry fics that are willing to commit to his nastiness and bigotry.
Such Great Heights by aideomai
Draco Malfoy, wide-eyed and pale and in a decidedly ragged shirt, was crouched next to the pile of whatever the dragon had been eating.
Harry threw himself to a halt and yelled, “Merlin, how many times do I have to save your life?”
Draco's crabbiness and difficult personality here is so good. This Draco has always been a major influence for me. This line in particular is iconic:
“Due respect, sir,” Draco said, because apparently even weird romantic feelings or whatever they were weren’t enough to keep Draco from throwing Harry under the bus the moment an authority figure appeared, “I haven’t done anything. I’ve been working nearly non-stop the past few weeks - you can ask Mr Borgin—”
Lorelei in the Menagerie by BelladonnaLee
"I think my dead son is haunting the manor," says Draco when Harry runs into him in an antique book shop. Driven by yearning and suspicion, Harry offers his help and is drawn into a web of secrets and half-forgotten nightmare.
I think anything I say about this fic would be a spoiler but I really enjoy Draco's twisted grieving here. Also considering my usual character preferences, I think you'll see why I like this one so much if you read it.
Heal Thyself by astolat
"Are you going for the course?" Lovegood asked. "You have the NEWTs.”
“What course?” Draco said, then, “No, don’t be ridiculous,” when he realized she meant the notice pinned up on the board he’d been staring at: Applicants To The Introductory Mediwizard Course For The Coming Term Shall Present Themselves In The Chief Mediwizard’s Office By August 24th.
“Oh, I thought you might,” she said. “Well, goodbye.” And off she wandered again in her addled way.
Amoral, ambitious character accidentally becomes a good person in their pursuit of status/money/power is one of my favourite tropes. It's also why I like Tom Riddle Snr in In the Bleak Midwinter so much. Astolat in general writes a great Draco.
What We Pretend We Can't See by gyzym
Seven years out from the war, Harry learns the hard truth of old history: it’s never quite as far behind you as you thought.
Despite the heavy sounded summary, this is actually a crackish humour fic. Certainly an excellent example of nutcase Draco. The villain reveal at the end is 100% my favourite part I stg.
#sorry im like a month or two late on this anon#asks#anon#fic rec#as for what i've read recently - i haven't really been reading much draco content recently tbh#it's all tom
48 notes
·
View notes
Text
Bandai Explains Why They Adopted AWS for Tamagotchi Uni and Why NFC Didn’t Work

The partnership of Tamagotchi and Amazon Web Services is so interesting, and we love hearing more about it. Yuri Okamoto of the Bandai planning team of the Toy Division Global Toy Planning Department, who was in charge of the planning and development of the Tamagotchi Uni at Bandai, and Daisuke Sakammoto of the technical design team of the same department explain further why exactly Bandai adopted AWS for the new Tamagotchi Uni.
Mr. Okamoto explains that the first connectivity method was introduced in 1997 with the Tamagotchi Osutchi and Mesutchi. The purpose of this connectivity was for one character to be able to cross over into the other device.

Then in March of 2004, after the explosive boom of Tamagotchi calmed down, the Tamagotchi Plus model was introduced with new infrared communication. The infrared technology functionality was the exact function that was tailored in the heyday of feature phones in Japan, and it was possible not only to connect two Tamagotchi’s together, but also to mobile phones.

Newer models also introduced different types of connectivity, including NFC with the Tamagotchi 4U in 2014. NFC was aimed to allow Tamagotchi’s to connect together by touching the devices together. However, the communication speed of NFC was not very fast, so it did not become a user experience the communication would end when touched.

Tamagotchi M!X back in 2016 brought back the infrared connectivity. The Tamagotchi Meets back in 2018 then introduced Bluetooth connectivity on top of the infrared functionality which enable the ability to connect to a smartphone or tablet to use the application.
The Tamagotchi Smart which was released in the midst of the COVID-19 global pandemic where contact with people was suppressed. The Tamagotchi Smart allowed caretakers to interact with their Tamagotchi with the use of voice and touch, along with wearing your Tamagotchi Smart right on your wrist.

Mr. Okamoto then discusses how the Tamagotchi demand has been higher overseas than in Japan. The Tamagotchi Uni was sought out to unify the design and content of play sot hat Tamagotchi users around the world can enjoy the same Tamagotchi Uni globally.
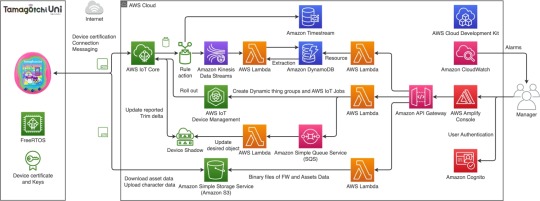
The Tamagotchi Uni also introduced Wi-Fi for the first time. This enables the new Tamaverse feature, software updates, and more. There are a wide range of functions that should be independently implemented in the cloud infrastructure to realize the concept of the Tamagotchi Uni. AWS has great infrastructure capabilities and a range of sample documents to advance development.
Monoist asks if future models after the Tamagotchi Uni will feature cloud connectivity. Mr. Okamoto responds that there alway needs to be the core play that has always been featured in the Tamagotchi, and Bandai will consider how to do that with both hardware and software. So the cloud is not necessarily a requirement for the next generation model.
#tamapalace#tamagotchi#tmgc#tamatag#virtualpet#bandai#jp#yuriokamoto#yuri okamoto#daisukesakamoto#daisuke sakamoto#monoist#aws#amazonwebservices#amazon web services#nfc
26 notes
·
View notes
Text
Hey, writing Tumblr!
Does anyone have experience/recommendations for writing apps like Scrivener or Bibisco that have a web application and/or an Android app? I'm thinking I'd like to get away from Google Docs in the new year (the AI/user suggested corrections are driving me up the wall) but I do a non-zero amount of my writing while I'm on the clock at work (ssh!) and I can't exactly download Scrivener to the front office computer.
(I mean I could because upper leadership has absolutely fucked off and left my branch to fend for itself, but that seems like asking for trouble 😂)
Please note: I am not asking about things that run on iOS, as I do not own any Apple products and don't intend to.
Thanks in advance!
#writing#scrivener#writing tools#bibisco#android#please i just want something that compares my spelling against a dictionary#not against what other people are doing#stop suggesting “Lan Zhan asos” when I write “Lan Zhan asks”
27 notes
·
View notes
Text
Almost Nowhere: Finished, Thoughts
I finished @nostalgebraist's Almost Nowhere. Here are my thoughts (with spoilers).
I was fortunate enough to speak to Nostalgebraist about the story; one of the things he told me was that he put especial care into ensuring that the first and third parts of the story were written to sound and feel alike. That statement informs much of my subsequent thoughts on the structure of the story as a whole.
Almost Nowhere has three parts, distinguished in the text by their chapter numbering scheme. Notably, in line with what Nost told me, Part 1 and Part 3 use the same numbering scheme (with Part 1's last chapter being titled XVI and Part 3's first chapter being titled XVII), whereas Part 2 uses a different numbering scheme, which sets it apart from the other two.
This disjointed numbering scheme introduces a few oddities into the story structure (notably that Part 2 ends with a chapter titled "17" only for Part 3 to begin with a chapter titled "XVII"), but overall each part, even 1 and 3, have a distinct narrative focus that makes their divisions natural:
Part 1 focuses on characters living inside individualized "crashes" (Matrix simulations)
Part 2 focuses on a unified, all-encompassing megacrash called "Advanced Containment," with a concurrent story set in one particular individualized crash of especial importance
Part 3 focuses on life outside of crashes, in the "real world."
Why, then, the especial emphasis on linking Part 1 and Part 3 stylistically and via the chapter numbering scheme, when they lack a clear narrative connection?
My thesis is that the answer to that question lies in the mirroring between the story's structure and the structure of the "worldbuilding" that guides the story itself. By the end of the story, the shape of that worldbuilding shakes up like so:
There are a virtually unlimited number of branching parallel timelines reaching all the way back to the beginning of the universe. This web of timelines is initially described as a "tree" and later called "Everywhere-Heaven." Due to how alternate timelines work, they are mostly populated by altruistic beings who seek only to improve the lives of beings on lower-level alternate timelines.
The absolute lowest (or highest, depending on how you look at it) level alternate timeline, the sort of progenitor timeline from which all the alternate timelines emerge, is called "Almost-Nowhere," and it is in this timeline that most of the characters of the story reside. These characters live in a less than idyllic state and are not altruistic, and Everywhere-Heaven is trying to help them.
Later in this "progenitor" timeline, way later, like "after the heat death of the universe" later, alien beings called Anomalings live; they have the ability to travel through time. They were created by the altruistic denizens of Everywhere-Heaven so that something might survive the heat death of the universe, but they went rogue, went back in time, and massacred many of their creators. Now they are imprisoning humanity in the aforementioned crashes.
That's the quick-and-dirty synopsis, gliding over much complexity and many physics lectures. The primary key is the three-tiered division of the worldbuilding: Everywhere-Heaven, Almost-Nowhere, and the Anomaling future.
Azad comments late in the story:
Azad: There are others like us, everywhere. Except in one respect. We happen to live on the fulcrum, around which all the rest pivots.
Azad: We live in the Almost-Nowhere. It’s an ordinary neighborhood, like all the others. People live there — we do — but people live everywhere, only we do not see them.
Azad: It’s an ordinary neighborhood, except for the fact that the tower of life hangs from its ceiling.
Azad: Do you know, Grant, that the tower of life is marked for demolition? Everyone is going to die.
Azad: Almost-everyone, I should say.
Azad: If there’s a way to save it, it can only be through some application of force at the site of the fulcrum.
Almost-Nowhere, being the central tier of this structure, is the "fulcrum" on which everything relies. Everywhere-Heaven cannot exist as parallel timelines if its progenitor timeline does not exist. The Anomalings also view Almost-Nowhere as the "center" in their initial, ominous message to humanity before the mass enslavement:
An abomination has formed near the center of the world.
Its "central" position as a "fulcrum" is what lends Almost-Nowhere its critical, multiverse-encompassing importance.
The shared stylistic and tonal elements of Parts 1 and 3, as well as their shared understated chapter numbering system, emphasizes Part 2 as the "center" of the story. Even during a cursory look at the chapter index, zoomed to display the entire work, Part 2 literally sticks out:

Beyond that, though, the narrative's conclusion emphasizes the contents of Part 2 as particularly pivotal. First, in the penultimate chapter, the resolution of the plot is framed as a return to and improvement on Advanced Containment, Part 2's setting:
“I will have our ‘dream,’ Lucifer!” Sylvie shouts. The halo-light pulses in tune with his voice.
“I will have it, dammit, no matter what it takes!
“I will make advanced containment again! With a fresh new crash, if I need to!
“I’ll make it stronger, this time! I’ll make a wall around it, a new kind of wall, Sylvie’s wall that can never be breached!
Though the narrative ends before Sylvie's plan is enacted, the plan is agreed upon by the three major warring factions on Almost-Nowhere (Sylvie, Hector, and the beasts) and is designed in a way that should, in theory, sate the competing needs of Everywhere-Heaven and the Anomalings. Essentially, it is presented without contradiction as a perfect compromise between every character in the story, the compromise that so many characters have sought without success for so long. And this plan is to create a new (better) Advanced Containment, to return to Part 2, to strengthen and defend the "center" of the story Almost Nowhere, much as Everywhere-Heaven sought to strengthen the "center" of the location Almost-Nowhere from the Anomalings via fantastical metals and technology.
Then, in the final chapter, Anne 27 returns to the other location pivotal to Part 2: Michael's Crash. Though Michael's Crash is first introduced as one of the isolated crashes in Part 1, it is quickly abandoned and only returned to in Part 2, where it serves as the setting for half of the part. Michael's Crash is itself considered a "load-bearing" center of the worldbuilding, as the oldest crash, which for a variety of technical reasons I won't delve too deeply into makes it capable of causing the most change to the "real world." Additionally, if destroyed, it would create a time paradox that might destroy the real world in its entirety. Anne 27 does not use Michael's Crash to cause some major change, however; she allows Sylvie's plan of Advanced Containment to proceed unmolested. All she does is seek a moment of personal catharsis for herself, speaking to her younger self, and reaching an emotional resolution detached from the plot resolution.
Mirrors play a fundamental role in Almost Nowhere, notably in early descriptions that seek to explain how the Anomalings think differently than the humans. (The term "bilateral" comes from this thought process.) But mirroring is also used through the narrative on a structural level. In Part 1, when three concurrent stories in three different crashes are told, and the reader has little context as to how they relate, mirrored elements in each crash are used to thematically tie them together: The moon in Mooncrash and the Shroud in CC-Crash 09μ function similarly despite their different names, preparing the reader to understand how the two crashes are alike. This thought process, the ability to see how two different things are alike, is also described as a core differentiator between humans and Anomalings, the latter of whom cannot think in metaphor and find it abhorrent. It only makes sense, then, that metaphor plays such a prominent role in Almost Nowhere itself.
(Hence also why there is so much emphasis in Almost Nowhere on addressing a "reader," the human who interprets the text. Without a reader to see that Thing 1 is "like" Thing 2, the text loses its potency. This constant addressing places the reader front and center, suggesting they are not a passive entity, but an active contributor to the text via the act of understanding it. There is even an in-text metaphor for this act of understanding in the concept of Mnemopoesis.)
So if Almost Nowhere is "like" Almost-Nowhere, what does it mean, metaphorically, that Almost Nowhere ends with a return to its center, to its fulcrum?
To understand that, it's important to understand what that center is. Specifically, what Advanced Containment is. Sylvie describes it best:
“An addictive structure that iterates the same pattern of variation upon the same pattern, nested unto infinity, appearing to contain boundless complexity and novelty, but still bounded at its outside, thus omitting most of the structure of the universe and placing reliable bounds on the entrapped mind, though the mind believes itself to journey boundlessly within . . . metaphorically an embedding of a hyperbolic space into a Euclidean one, you’ve seen the Escher drawing with the bats, something like that . . . advanced containment is full of them, we chose to embrace your frenzied cognition and divert it this time, instead of trying to shut it off . . . much more reliable . . . yes, yes, I can do this, this is the whole point!”
Alternatively, a "lotus recursion." An endlessly repeating, nested loop that provides the illusion of progress while remaining bounded. This is the structure that Sylvie and Stein and the beast ambassador Organism-2 agree to at the end of the story, with a few improvements to make it better than the original Advanced Containment. It's a trick, a way to make the mind think it is doing something of importance without the body actually doing anything at all.
This lotus recursion structure is itself mirrored throughout the text. A slowly unraveling series of mysteries that present new mysteries that often turn out to be new variations on the old mysteries; the repetition of character trauma and growth (Sylvie having innumerable manic episodes only to be talked down by Grant every time, usually by almost identical emotional appeals), Hector Stein's rise and fall and rise again and fall again and rise again, the end of one containment only to enter a new type of containment that then leads a third type, and especially the common refrain:
The return to the site of the trauma!
The re-infliction of the wound!
Advanced Containment, conceptually, uses humans' powers of metaphor against them, confounding them with an endless array of similar things to present the idea of progress without progress.
Michael describes Advanced Containment as a "dead end," "doomed to failure." And he is proven right; Advanced Containment ends quickly, lasting less time than the first containment that it sought to improve upon. Furthermore, by comparing Advanced Containment's structure to that of Almost Nowhere, it becomes a moribund solution for the problems of the story. Sylvie, Hector, the beasts, and almost every character agreeing to Advanced Containment 2.0 is not a triumphant resolution of the story. It is merely its prolonging, the creation of another ring within the lotus recursion. The characters agree merely to return to the site of the trauma (the "center" of the "world" of Almost Nowhere, where the abomination has formed!) and re-inflict the wound, to continue the story the way it has already gone, setting the stage for a new ring of conflict later.
As such, the reader is not shown Advanced Containment 2.0. There is no epilogue that ties up the end state in a nice bow, because Advanced Containment 2.0 is not an end state. The end state of the story instead comes from the one character who rejects the truce, Anne 27:
There is only one single thing in existence, with no constituent parts. There is only the one story, told over and over again.
That primeval mistake, and the working-out of its consequences.
She swims in the opposite direction, toward her starting point.
She thinks of Cordelia.
And she thinks: It is actually you, that I value, and wish to preserve. And not another one like you, even if she is better, and happier.
She thinks of her ruined sisters.
And she thinks: I harmed you, once. I will do you an honor, now, by refusing to repeat my mistake.
She comes to the central point, from which the spokes of the tracks diverge. She feels the familiar Annes there.
My sisters, she thinks. Not some other ones, like them.
I refuse teleopoesis, she thinks.
I make another wish, its opposite. I hope you will understand, Arthur.
I think that you will.
Anne 27 breaks the recursive lotus. She rejects the justifications Azad previously used for his bad behavior in Michael's Crash (there is only one story, I am doomed to repeat it, I cannot help but repeat it) and decides to not repeat it. She seeks only solace for herself, a healing of her own wounds without the infliction of others (or the same wound, re-inflicted). She leaves all others to continue as they were unmolested, removing only herself from this endless story.
And then the story ends. Thank you, reader.
Nostalgebraist has also described Almost Nowhere as following a similar structure as Homestuck, specifically likening Part 3 to Homestuck's Act 6. (Homestuck itself leans into the recursive lotus structure with its Act 6 Act 6 Act 6es.) I understand the comparison, but I would liken the ending of Almost Nowhere to the ending not of Homestuck proper, but its Epilogues: The story continues for some people, but not our protagonist; they have finally found peace, and in so doing can slip away from the canon entirely. I considered that ending to be the perfect one for Homestuck on the whole, and it's excellent here in Almost Nowhere, which is significantly more tightly coiled.
I feel like I've only scratched the surface of the structure complexities of Almost Nowhere and what they mean, and my thoughts have been somewhat disjointed, perhaps poorly articulated. I hope I've explained myself well enough at least.
31 notes
·
View notes