#data democratisation
Text
Top Data Management Trends for 2024: Navigating the Data Deluge
From customer transactions to sensor readings, the volume and variety of data is growing exponentially. Through 2024, we see organisations adopting data management strategies and technologies that help them to make sense of this data deluge.
Here are some key data management trends that will shape 2024:
Cloud-Based Data Management: Transition to a Cloud-Centric Approach
Automation & AI:…

View On WordPress
#ai#cloud#data democratisation#data governance#data lake#data lineage#data privacy#data strategy#real-time#self-service BI
0 notes
Text
Dear Viewer,
this short film represents a cosmic adventure of the day and modern times the word Data Democratization will come back often, a crash between era and novelty with this potion of time and adapt to your big television Wow but congratulations, exploring creativity probably you tell me yourself, good cinema :)
Data democratization is the ability for information in a digital format to be accessible to the average end user. The goal of data democratization is to allow non-specialists to be able to gather and analyze data without requiring outside help.
#movie#selfmade#entertainment#data#democratisation#montage#refreshed#youtubedust#starmovietour#90vibes
0 notes
Text
A detail about the Peacebreakers in Providence. (translated + spoilers)

Ministry of Foreign Affairs Overseas Research Department Field Survey Team/Peace Breaker
Official activity period: 2098/04~2113/04
A unit that obtains and manipulates information useful to Japan from other countries. Its main mission is to enter other countries, gather information, carry out sabotage operations, and provide weapons and operational support to anti-government organizations who support the Japanese government. Regarding anti-government support operations, operations were carried out through domestic third-party organizations
(Example 1). It has been confirmed that it was provided to and expanded to the government and rebel forces of the former Southeast Asian Union (commonly known as SEAUN) (see corresponding
data 04231 for details).
Through "monitoring"derived from [...]
The members were selected from among the soldiers who belonged to the Special Forces of the National Defense Force, based on the Sibyl System's advanced decisions, and from among them, those who had a particularly strong sense of national pride were selected.
Establishment: Wave After its establishment, the company did some original work. Main strategies and execution records.
2099_Conflict within the Union of Southeast Asia
2111_Rebellion in the Republic of South Asia
2112_Operation Footstamp
2113_Kona Island independence group reduced cropping
Involved in etc. For details, see 67721 data
In June 2118, the decision was made to dismantle the unit, and in the same month, the whereabouts of the unit commander and training staff went missing.
In October 2118, independent activity was confirmed, and it was completely destroyed. To this day, it is said that its range has expanded to include Japan, Northern Russia, and the Russian Federation. Tonami is said to have been the general manager since the company's founding.
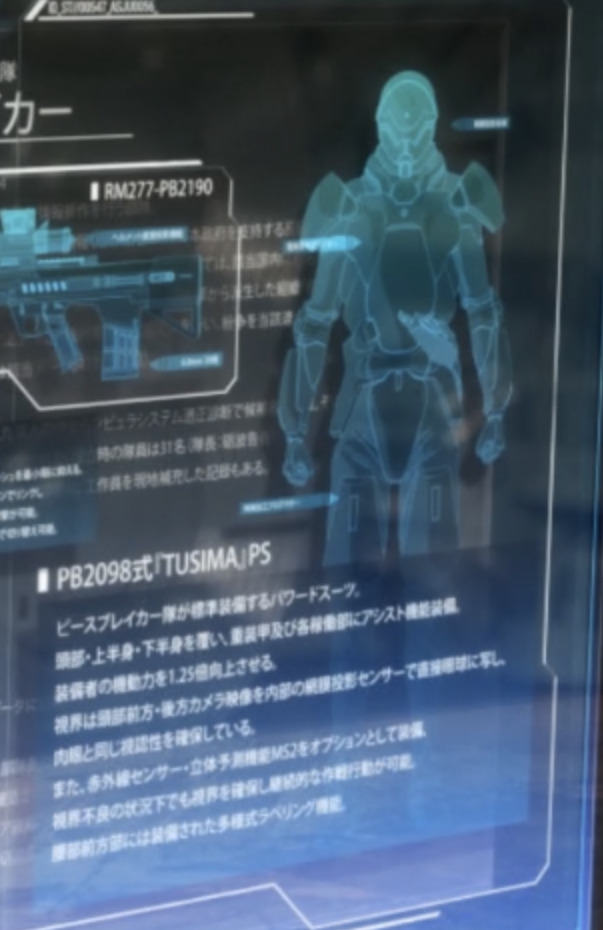
■ PB2098 type TUSIMA PS (Peacebreaker Armor)
A powered suit that is standard equipment for the Peace Breaker Corps. It covers the head, upper body, and lower body, and is equipped with heavy armor and assist functions in each part.
Increases the wearer's mobility by 1.25 times.
Visibility is ensured by using cameras in front and behind the head to project images directly onto the eyes using internal scale projection sensors.
It is also equipped with an infrared sensor and 3D prediction function MS2 as an option.
It is possible to carry out operations without securing visibility even under conditions of poor visibility.
Multi-type labeling function installed on the front of the waist
***
Sibyl itself is promoting conflicts to expand itself, and then denying asylum to the refugees which is why they're confined to Dejima/Kyushu. Sibyl lets MFA do the dirty work and it's obvious that Sibyl just turns a blind eye to this because it benefits their colonisation approach.
I wonder what Kogami's thoughts will be when he comes to realise that his "democratisation" in Siam Reap (Psycho Pass Movie) was just a part of Sibyl's grand plan. Also Kona Island? Didn't Rutaganda and his mercenaries live on an island? The knowledge that Sibyl would let the world suffer, after having seen the true effects of it in his journey abroad and that probably every person he met or lost on his journey (including the people that Tenzing lost) was suffering due to Sibyl's duplicity. In Case 3 Novel, Frederica is investigating the Peacebreakers in Tibet-Himalaya and Garcia by extension.
Honestly, Kogami Shinya seeing the horrors of war, trying to help people and then returning to become a cog in the System is a tragic enough ending for me. I guess this was the meaning of that painting in that room. (The Abyss, I assume?)

Anyhow, I'm on my fourth rewatch (first time with subs so thank god I can follow the dialogues), and Sibyl has a knack of grinding my gears (pun intended), I've come to despise the System as much as Kogami.
I'll delve into a proper review later, for now just accept my ramblings. I have 10,000 thoughts on Akane too, who in this movie punched me right in the heart, honestly I don't know how Akane-chan is so strong. I admire her grit.
51 notes
·
View notes
Text
Why TERFs are Fascists
2500 words that will explain the modern online fascist ecosystem and convince any honest reader that "gender critical" ideology is a major element of how it works (average reading time: 8.3 minutes).
The ways people use social media are very different and because of this I've seen that many comrades involved in building the UK working-class movement are very distanced from a solid understanding of the shape of political discourse online, in the spaces in which a majority of public political discourse now takes place. Even though there are many vocal comrades and union members present in online spaces like twitter or facebook, there is an entire other vastly complex and deeply interconnected space of political discourse that occurs online, where the power and influence that corporate interests wield is nigh inconceivable and keenly felt at all times.


The recent mid-life crisis of elon musk is the perfect beginner course in understanding this through:
The ways that capitalist oligarchs and mega-corporations compete for power and influence as though they were playing a board game;
The present consequences of the cult of infamy that creates internet celebrity and which developed from previous ideas of celebrity via the "mass-democratisation" (or "mass data-exploitation of alienated working class demographics") of the internet and social media sites especially;
At the same time, the ways in which this infamy-culture is directly related to the subservience of mainstream news-media to capitalist ideology via advertising on screens in every pocket and home (in other words we sell our data - i.e. agency - to be used by some of the worst people on the planet to manipulate us in return for advertised access to the public forum - see the Cambridge Analytica scandal for the consequences of this) and the profit motive that algorithmically determines content: in fact the thing that has most rapidly driven change in advertising is the technological improvement of those algorithms to be as efficient at exploitation as possible at all times. Notably this method incentivises a system that makes no distinction between a video of a hate crime and a trending comedy video. See Twitter Main Character Of The Day for other examples.
Now those algorithms are so powerful that they determine the shape of the absolute majority of all political discussion, and are at the same time driven by a content ideology that emerged from the perfect evil marriage-in-triplicate of:
The "media age" Commodification of The Means of Communication (news, social media & the colonisation of the public forum);
The Commodification of Art and Cultural Expression (art becomes content via colonisation of and alienation from community and natural surroundings);
The Cult of the Individual (which desires infamy above all else, favouring the ultra-wealthy and the most extreme).
The relationship between stochastic terrorism and data-driven online existence is obvious: within this evil soup of capitalist ideology, which values power over everything, the means of communication (social media) is a tool to appropriate content (alienated art, labour and identity) that can be manipulated (remember all that stolen data!) as efficiently as possible, and the result is the Culture War, in which fascism thrives.
Just as they always have, capitalist interests create breeding grounds for fascism, here making content as polarizing as possible because it drives engagement and makes numbers go up - the goal is to do this constantly and exponentially for infinity and all time...
Fascist grooming is a fantastic tool towards achieving this goal. Not only does it divide the working class and thus make it easier to exploit and reduce the threat of revolution, you can also look at the current Elon Musk example to see how he is attempting to colonise the means of communication that structure modern stochastic terrorism for personal benefit.

"Shadowbanning" conspiracy-theorist Elon Musk may be hemmoraghing money and destroying everything he touches, but he receives cultural capital with the worst people online in exchange. Is it worth it? He's doing it anyway. The rapist and human trafficker Andrew Tate (whom Musk had an executive hand in unbanning from Twitter along with some of the other most prominent alt-right and conspiracy theory figureheads on the internet like Laura Loomer, Roger Stone and David Icke) getting arrested by Romanian authorities after being publicly humiliated by Greta Thunberg and accidentally revealing his hidden location via pizza box was breaking news despite a vast majority of non-online people who received this news having never previously heard of Andrew Tate. Thunberg's comeback currently ranks as the 4th most liked tweet of all time.
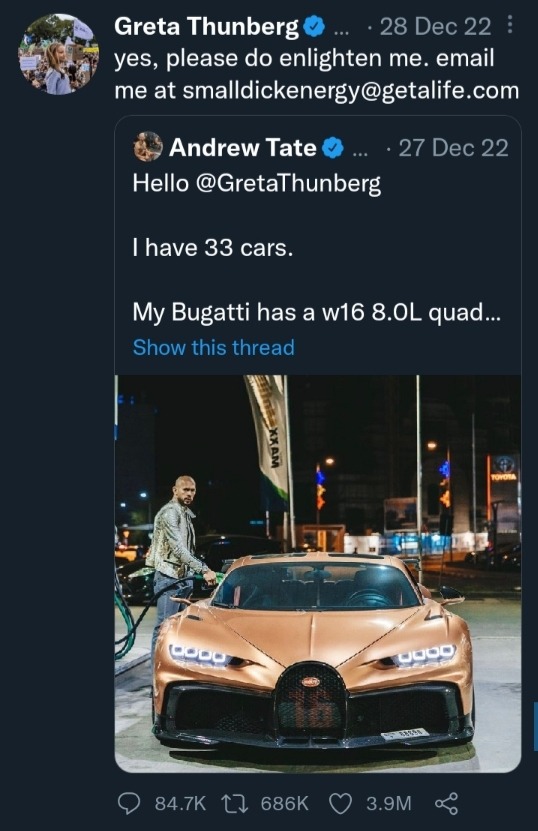
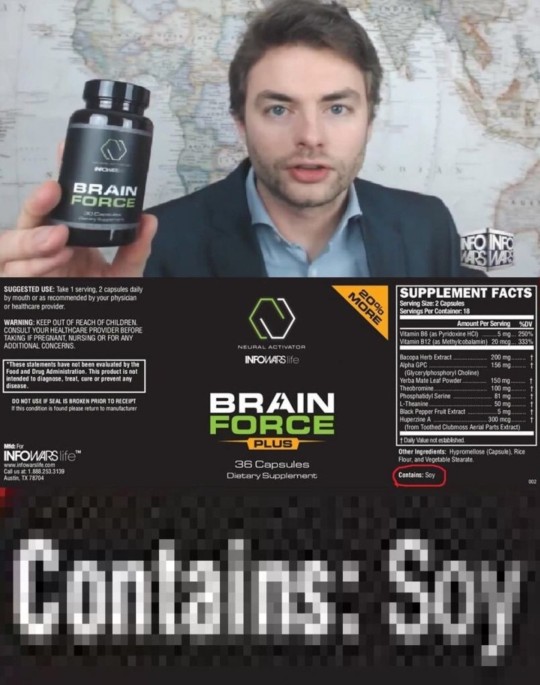
Andrew Tate is a recent leading figure in the misogynist Mens Rights sphere, which has historically been one of the leading recruitment tools across all social media for the stochastic terrorist network that is figure-headed by a coalition of conservative grifters (charlatan cult leaders, conmen selling soy-containing anti-soy conspiracy theory protein shakes, frauds who radicalise a fascist-friendly cult to scam a delusional and easy to manipulate captive audience) and mainstream right-wing political figures.
The TERF (trans exclusionary radical feminist fascist) movement is a direct mirror to this fascist recruitment program and functions in an incredibly similar way. It may seem to the uninformed that it has come from independent grass roots because it claims to be based on valid concerns of real working class people, but this is a myth as false as everything else you can expect to hear from TERFs: it is funded and nurtured by the exact same evil marriage of right-wing political groups and capitalists that foster the alt-right movement.
The TERF ideology (or "gender critical" movement - though this is a deliberate misnomer in the exact fashion of "national socialism", as it is the violent enforcement of the patriarchal systems of oppression which form the false gender binary that is the explicit goal of the TERF ideology) is widely and obviously fascist, and it is observably false to claim that it is not so: it is artifically bred in the same algorithmically-controlled shallow waters that feed the network of conspiracy theories, cults, and the alt-right, which we would most accurately recognise as the stochastic terrorist network of modern fascism.
All online "culture war" (in other terms the majority of political discussion, polarised by the callously evil profit-motivated design of the medium through which it is communicated to drive engagement and sell ads) is dependent on the existence of this ecosystem, and you only need to look at the following widely available details to see this:
The established political powers that are acting to enforce gender-&-bodily-autonomy-based authoritarianism are simultaneously enacting trans genocide and attacking abortion rights with support from terfs, the alt right and other conservative hate groups;
The deep connections in the shared community spaces of the alt-right and TERF movements;
The Q-anon far-right cultist attempted coup in the US and the constant onslaught of semi-organised terrorist violence that is the result of this network;
The pro-fascist credentials and confused political ideologies (mainly the increasingly conspiracy-fuelled fascist dog-whistling of self identified "anti-woke" conservatives and libertarians) of anyone who is a major figure in the discourse surrounding these movements (elon musk, libsoftiktok chaya raichik, lauren boebert, matt gaetz who as of typing held the deciding vote in electing the now US house speaker Kevin McCarthy, marjorie taylor-green, ian miles cheong, tucker carlson, alex jones, andrew tate, joe rogan, ben shapiro, j.k. rowling, maya forstater, piers morgan, nigel farage, etc.);
The previous major political waves made by the reach of these groups (brexit, trans and abortion rights abuses in the US, the conspiracy-fuelled attempted coup in the US, anti-vaxxers and their influence on global covid responses, mass shootings and fascist terrorist attacks, etc.);
The strategic choice of culture war topics to exploit the algorithm & spread fascist propaganda to seed new recruits who will move up the pyramid of stochastic terrorism (and get scammed along the way, as most prominent exponents of fascist ideology are also hardcore grifters, see the overlap with crypto-bros & NFTs) through the incredibly powerful reach of tik-tok, twitter, instagram, facebook & youtube to all demographics of the working class including children;
The fact that terf ideology makes up a significant percentage of current prominent alt-right discourse in the culture war, and that both terfs and the rest of the online right always perform solidarity for one another when they rally against cross-over culture war topics like cancel culture;
A predominantly white, middle-class & conservative "feminist" group that is aggressively anti-intersectional, preferring instead to act against other oppressed groups in solidarity with the misogynist, vocally anti-feminist "mens rights" chanting alt-right is more accurately described as a patriarchal white supremacist group that seeks emancipation for none and is indistinguishable from other conservative groups who act on behalf of patriarchy.
For further proof, watch as I accurately predict that the most active layer of the stochastic pyramid of fascists will crawl out in droves to support J.K. Rowling when the new Harry Potter game releases next month (which includes a slave class of non-human people who love being slaves actually - you even have some of their severed heads on display in your dorm - and in which you fight against a conspiracy of anti-semitic Jewish-coded greedy evil goblins, in a game whose previous lead developer has a youtube channel where he produced lengthy propaganda for alt-right culture war topics) by abusing queer people and women on the internet. Watch as they relish in discovering tedious ways in which they can use this opportunity to spread misinformation & propaganda to fuel the culture war by attacking the left and any and all "wokeists" (the boogeyman group of anyone who speaks or acts in support of any and all oppressed people, including existing as one of these people, especially used to dog-whistle against POC) and know that J.K. Rowling is well aware of the kind of stochastic terrorism she promotes and considers her royalties an endorsement of her ideology. She is the single biggest, most influential terf.
--------
In conclusion, it is absolutely incorrect to ever make the claim that the anti-trans movement is not a fascist movement, as it is a significant element of the online modern fascist ecosystem and has not simply emerged from nowhere but instead is a consequence of many obvious factors (not least of which is the development of modern alt-right conspiracy theories), and this movement is another face of the same monster that first came to major online prominence in the form of gamergate - which itself was a development of the "edgy" and extremely racist, ableist, queerphobic and misogynist culture of 2000s & early 2010s internet and social media.
For many queer people, the sheer act of existing in online spaces is a survival of (and therefore an education in) the consequences of these ideologies, which are labelled online in a variety of ways that all fall under the broad category of the alt-right (i.e. modern online fascist) umbrella and whose names all invoke clouds of connotations with violent authoritarianism, fascism and oppression, for instance: incels -> blackpill -> MRAs -> gamergate -> pizzagate -> Qanon -> flat-earthers -> covid denial -> anti-vaxxers -> "groomer" slurs & anti-trans CSA conspiracies. It is easily possible to find multiple recent terrorist attacks that clearly evidence the direct connections between all of these categories. TERFs are just another group in this cloud of shared characteristics.
This venn diagram (at the centre of which is an explicitly and vocally fascist ideology) is not quite a circle, if only because it must have on-ramps for recruitment: the "gender critical" movement is one of these, and it has proved its potential to be an incredibly effective tool for the spread of fascist ideology and stochastic terror, which is a major reason why "the trans debate" is a constant repeat target of the culture war's ire. The relatively small size of trans communities, their very online presence, the role of patriarchal gender oppression in conservative ideology (and the weakening of LGBTQ solidarity as a consequence of the partial capitalist colonialisation of lgbtq communities and the subsequent alienation of queer youth from their many socialist elders) make trans people as perfect a scapegoat for the fascists of today as they have been for the fascists of the past.
This fascist ideology has shown its hand and the only strategy that has the potential to defeat it is an intersectional revolutionary movement of the working class. It would be a dangerous oversight not to learn these lessons that demonstrate why we must put every effort into organising the rise of working class movements in an intersectional way: from strikes to climate protests to the fights for the rights of refugees, indigenous peoples, queer and trans people, POC and racially oppressed communities, all women, disabled people and all other oppressed peoples of the world (ultimately encompassing the entire global working class): we must connect each of these movements in solidarity with one another.
Just as the enemy is a hateful supremacist ideology that seeks to divide and genocide all of us degenerates (speaking in solidarity as an autistic cis man with the nazi diagnosis "aspergers" - so in retrospect those fascists may have even elected not to murder me for being the wrong kind of retard while today's fascist death cultists distort my hypothetical existence into a ritual weapon to aid the spread of plague, what joy) the fight for all of our rights is the fight against one enemy with many different faces for many different people. It is clear that only mass scale, militant, revolutionary anti-capitalist & anti-fascist solidarity will see any of us freed from its influence. The only way to achieve this is to organise, enact tangible and effective solidarity and bring with it the reasons that allow you to acknowledge that it is your fight too.
To do this effectively, I suggest joining your local revolutionary socialist organisation and attending both pickets and protests. Trans and refugee voices are crucial in the UK (hi from terf island) right now, and the place they can have the most influence is the place that has the most potential to destroy capitalism and build revolution: the picket line.
--------
Thanks for reading, and please do get in touch with your local revolutionary socialist organisation (just search for revolutionary socialist groups in your area) & if they're worth your time they'll have a clear and easily accessible manifesto that can tell you if they're for you and what they stand for.
They will be very glad to have you, eager to share educational resources and happy to find a way for you to get involved that best suits you. Go with a friend and say you want to do some activism but don't know where to begin - it's the truth and the only way to learn. They will be involved in solidarity for strikes and protests, and they will be democratic and actively intersectional: if you go to an upcoming protest or happen to stop by a picket at the right time you will find them there!
Good luck getting involved: if you are in the UK and want advice on how to go about it please message me, unless this post really goes off, in which case I'm expecting I'll catch some heat. I will do my best to point you in the direction you want to go but here is a good start from an organisation I only have positive experiences of working with:
Unite the working class
Intersectional solidarity forever
Terfs fuck around and find out why ✊ means solidarity
67 notes
·
View notes
Text
Anticipating the future of malicious open-source packages: next gen insights
New Post has been published on https://thedigitalinsider.com/anticipating-the-future-of-malicious-open-source-packages-next-gen-insights/
Anticipating the future of malicious open-source packages: next gen insights


Ori Abramovsky is the Head of Data Science of the Developer-First group at Check Point, where he leads the development and application of machine learning models to the source code domain. With extensive experience in various machine learning types, Ori specializes in bringing AI applications to life. He is committed to bridging the gap between theory and real-world application and is passionate about harnessing the power of AI to solve complex business challenges.
In this thoughtful and incisive interview, Check Point’s Developer-First Head of Data Science, Ori Abramovsky discusses malicious open-source packages. While malicious open-source packages aren’t new, their popularity among hackers is increasing. Discover attack vectors, how malicious packages conceal their intent, and risk mitigation measures. The best prevention measure is…Read the interview to find out.
What kinds of trends are you seeing in relation to malicious open-source packages?
The main trend we’re seeing relates to the increasing sophistication and prevalence of malicious open-source packages. While registries are implementing stricter measures, such as PyPI’s recent mandate for users to adopt two-factor authentication, the advances of Large Language Models (LLMs) pose significant challenges to safeguarding against such threats. Previously, hackers needed substantial expertise in order to create malicious packages. Now, all they need is access to LLMs and to find the right prompts for them. The barriers to entry have significantly decreased.
While LLMs democratise knowledge, they also make it much easier to distribute malicious techniques. As a result, it’s fair to assume that we should anticipate an increasing volume of sophisticated attacks. Moreover, we’re already in the middle of that shift, seeing these attacks extending beyond traditional domains like NPM and PyPI, manifesting in various forms such as malicious VSCode extensions and compromised Hugging Face models. To sum it up, the accessibility of LLMs empowers malicious actors, indicating a need for heightened vigilance across all open-source domains. Exciting yet challenging times lie ahead, necessitating preparedness.
Are there specific attack types that are most popular among hackers, and if so, what are they?
Malicious open-source packages can be applied based on the stage of infection: install (as part of the install process), first use (once the package has been imported), and runtime (infection is hidden as part of some functionality and will be activated once the user will use that functionality). Install and first use attacks typically employ simpler techniques; prioritizing volume over complexity, aiming to remain undetected long enough to infect users (assuming that some users will mistakenly install them). In contrast, runtime attacks are typically more sophisticated, with hackers investing efforts in concealing their malicious intent. As a result, the attacks are harder to detect, but come with a pricier tag. They last longer and therefore have higher chances of becoming a zero-day affecting more users.
Malicious packages employ diverse methods to conceal their intent, ranging from manipulating package structures (the simpler ones will commonly include only the malicious code, the more sophisticated ones can even be an exact copy of a legit package), to employing various obfuscation techniques (from classic methods such as base64 encoding, to more advanced techniques, such as steganography). The downside of using such concealment methods can make them susceptible to detection, as many Yara detection rules specifically target these signs of obfuscation. Given the emergence of Large Language Models (LLMs), hackers have greater access to advanced techniques for hiding malicious intent and we should expect to see more sophisticated and innovative concealment methods in the future.
Hackers tend to exploit opportunities where hacking is easier or more likely, with studies indicating a preference for targeting dynamic installation flows in registries like PyPI and NPM due to their simplicity in generating attacks. While research suggests a higher prevalence of such attacks in source code languages with dynamic installation flows, the accessibility of LLMs facilitates the adaptation of these attacks to new platforms, potentially leading hackers to explore less visible domains for their malicious activities.
How can organisations mitigate the risk associated with malicious open-source packages? How can CISOs ensure protection/prevention?
The foremost strategy for organisations to mitigate the risk posed by malicious open-source packages is through education. One should not use open-source code without properly knowing its origins. Ignorance in this realm does not lead to bliss. Therefore, implementing practices such as double-checking the authenticity of packages before installation is crucial. Looking into aspects like the accuracy of package descriptions, their reputation, community engagement (such as stars and user feedback), the quality of documentation in the associated GitHub repository, and its track record of reliability is also critical. By paying attention to these details, organisations can significantly reduce the likelihood of falling victim to malicious packages.
The fundamental challenge lies in addressing the ignorance regarding the risks associated with open-source software. Many users fail to recognize the potential threats and consequently, are prone to exploring and installing new packages without adequate scrutiny. Therefore, it is incumbent upon Chief Information Security Officers (CISOs) to actively participate in the decision-making process regarding the selection and usage of open-source packages within their organisations.
Despite best efforts, mistakes can still occur. To bolster defences, organisations should implement complementary protection services designed to monitor and verify the integrity of packages being installed. These measures serve as an additional layer of defence, helping to detect and mitigate potential threats in real-time.
What role does threat intelligence play in identifying and mitigating risks related to open-source packages?
Traditionally, threat intelligence has played a crucial role in identifying and mitigating risks associated with open-source packages. Dark web forums and other underground channels were primary sources for discussing and sharing malicious code snippets. This allowed security professionals to monitor and defend against these snippets using straightforward Yara rules. Additionally, threat intelligence facilitated the identification of suspicious package owners and related GitHub repositories, aiding in the early detection of potential threats. While effective for simpler cases of malicious code, this approach may struggle to keep pace with the evolving sophistication of attacks, particularly in light of advancements like Large Language Models (LLMs).
These days, with the rise of LLMs, it’s reasonable to expect hackers to innovate new methods through which to conduct malicious activity, prioritizing novel techniques over rehashing old samples that are easily identifiable by Yara rules. Consequently, while threat intelligence remains valuable, it should be supplemented with more advanced analysis techniques to thoroughly assess the integrity of open-source packages. This combined approach ensures a comprehensive defence against emerging threats, especially within less-monitored ecosystems, where traditional threat intelligence may be less effective.
What to anticipate in the future?
The emergence of Large Language Models (LLMs) is revolutionising every aspect of the software world, including the malicious domain. From the perspective of hackers, this development’s immediate implication equates to more complicated malicious attacks, more diverse attacks and more attacks, in general (leveraging LLMs to optimise strategies). Looking forward, we should anticipate hackers trying to target the LLMs themselves, using techniques like prompt injection or by trying to attack the LLM agents. New types and domains of malicious attacks are probably about to emerge.
Looking at the malicious open-source packages domain in general, a place we should probably start watching is Github. Historically, malicious campaigns have targeted open-source registries such as PyPI and NPM, with auxiliary support from platforms like GitHub, Dropbox, and Pastebin for hosting malicious components or publishing exploited data pieces. However, as these registries adopt more stringent security measures and become increasingly monitored, hackers are likely to seek out new “dark spots” such as extensions, marketplaces, and GitHub itself. Consequently, malicious code has the potential to infiltrate EVERY open-source component we utilise, necessitating vigilance and proactive measures to safeguard against such threats.
#Accessibility#ai#Analysis#applications#approach#attention#authentication#Business#challenge#Check Point#CISOs#code#Community#complexity#comprehensive#Dark#Dark web#data#data privacy#data protection#data science#details#detection#Developer#development#documentation#domains#double#dropbox#Ecosystems
3 notes
·
View notes
Text
The Empowering Role of AI in Fostering Creativity and Coexisting with Traditional Artists
Artificial Intelligence has rapidly become an integral part of our daily lives, revolutionizing various industries and transforming how we interact with technology. While some fear that AI may replace human creativity and traditional artistry, this blog post aims to explore how AI actually enhances and empowers the creative landscape for both the average person and traditional artists alike.
1. Demystifying AI's Role:
AI, in its current state, is a powerful tool that complements human creativity rather than replacing it. AI algorithms can process vast amounts of data, identify patterns, and generate content. This capability presents exciting possibilities for fostering creativity, particularly for individuals who may not have formal training or access to expensive tools.
2. Democratisation of Artistic Expression:
The advent of AI-powered tools has democratized artistic expression by making creative platforms more accessible and user-friendly. As a result, the average person can experiment with various art forms, such as painting, music composition, and storytelling, without significant barriers to entry.
3. AI as a Collaborative Partner:
AI's role as a collaborative partner enables artists to augment their skills and envision new possibilities. AI-generated suggestions, prompts, or compositions can inspire artists, pushing the boundaries of their imagination and encouraging them to explore uncharted territories.
4. Enhanced Efficiency and Productivity:
AI streamlines mundane tasks, such as data analysis, research, or repetitive design work, freeing up artists' time to focus on more meaningful and expressive aspects of their craft. This increased efficiency allows artists to delve deeper into their creativity and produce more thoughtful, original works.
5. Preservation and Revival of Artistic Traditions:
AI can play a pivotal role in preserving and reviving traditional artistic techniques. By digitizing historical artworks and sharing valuable knowledge, AI can aid in passing down cultural heritage and artistic traditions to future generations.
6. Embracing Hybrid Creativity:
The future of creativity is likely to be characterized by hybrid collaborations between humans and AI. Artists can harness AI tools to create novel combinations of media, blending traditional craftsmanship with AI-generated elements, resulting in entirely new art forms.
Conclusion:
AI is not a threat to traditional artists; instead, it opens doors to a world of endless creative possibilities. By empowering the average person with accessible tools and supporting artists with efficiency and inspiration, AI fosters a vibrant and diverse creative society. The coexistence of AI and traditional artists promises an exciting future where human imagination and AI ingenuity merge to enrich our artistic landscape. Embracing AI as a creative ally will be the key to unlocking a new era of artistic expression and innovation.
2 notes
·
View notes
Text
Zomato introduces open food trends data analysis platform to aid restaurant partners
It has been introduced with "an aim to support both current and budding restaurant partners in taking a data-driven approach towards decision making", the company said.

NEW DELHI: Online food delivery firm Zomato Ltd on Friday introduced an open data analysis platform for food trends aimed to help its restaurant partners in taking a data-driven approach on prices, dishes and location.
Zomato Food Trends is an open platform accessible to the general public free of charge and it will “provide insights by analysing data from millions of transactions across hundreds of cities in India”, the company said in a statement.
“Restaurant partners can use these insights to customise their strategies and undertake data-driven decisions to accelerate and amplify their success,” it added.
It has been introduced with “an aim to support both current and budding restaurant partners in taking a data-driven approach towards decision making”, the company said.
The food trends platform allows its restaurant partners to view demand and supply gaps that have been zoomed in to a locality level, price distribution and demand trends for different dishes or cuisines, and demand-supply comparison for multiple dishes or cuisines.
“Restaurants can use these insights to make decisions on prices, dishes, locations, etc,” it added.
In a blog post, the company said, “Our aim is to democratise aggregated data insights “ levelling the playing field, particularly for smaller restaurants, to ensure they can make informed and evidence-based decisions.
“The restaurant industry in India has changed remarkably in recent years to meet the dynamic needs of the market and evolving consumer preferences, the company said adding, the country’s food entrepreneur possesses a strong ability to spot trends, identify market need gaps, and innovate to fill those gaps.
Zomato Food Trends is a way to support both current and budding restaurant partners in their endeavours,” it added.
4 notes
·
View notes
Text
Social Media Platforms as Ideal Public Spheres
Three traits cornerstone Habermas' notion of an ideal public sphere; "unlimited access to information, equal and protected participation, and the absence of institutional influence” (Flinchum, Kruse & Norris 2018). There is debate on whether social media platforms align with these requirements.
Arguments For:
Social media is an interactive space which empowers communication amongst active participants. Social media has democratised media content production, enabling equal participation by providing users with the tools necessary to independently broadcast their voice. This redistribution of power has established a media space where communication is on a peer-to-peer level rather than one-to-many (Flinchum, Kruse & Norris 2018). This has empowered individuals to engage in discourse publicly.
The reliance on traditional media gatekeepers has been removed by social media platforms. The equal contribution of the public to the media landscape has decreased the influence of institutions (Flinchum, Kruse & Norris 2018). Moreover, unlike traditional media, there are no gatekeepers on social media platforms which permit or deny the posting of content. This fulfils the requirement of a space absent of institutional influence.
Users also have unlimited access to all information available on social media platforms (Flinchum, Kruse & Norris 2018).
Whilst social media fundamentally meets the requirements of a public sphere, its ideality is inhibited by multiple factors.
Arguments Against:
Unlimited access to information
Users are segregated into niche online communities and are not exposed to the unlimited information available on social media. Algorithms analyse user data to predict and present content which aligns with an individual’s interests. Users are repeatedly exposed to media which affirms pre-existing viewpoints, forming a filter bubble (Belavadi et. al 2020). The online community is separated into smaller ideologically homophilic circles, constructing echo chambers of opinion (Belavadi et. al 2020). Automated content personalisation ultimately limits information access by sheltering users from exposure to opposing viewpoints.
Equal and protected participation
The exclusion of individuals from social media often arises as a consequence of the digital divide, which refers to the discrepancies which prevent certain groups' equal use of online spaces. Primary factors are the lack of access to the required technology, such as a stable internet connection and personal devices, and one's degree of competence with these technologies (James 2021). As individuals have varying access and competence which limits them in different ways, social media is not a space in which all individuals can equally participate.
Users are not protected when participating in discourse on social media. As mentioned in the Flinchum, Kruse & Norris reading; surveillance on social media can result in online activity impacting users’ life offline. This is reflected by the offline consequences faced by NBA player Kyrie Irving’s career after posting a link to an antisemetic film on Twitter in 2022 (Ganguli & Sopan 2022). Irving received an eight-game suspension by the Brooklyn Nets, and Nike terminated his contract 11 months prior to its official expiration (Doston & Vera 2022; Ganguli & Sopan 2022). Exemplified by Irving’s financial and reputational damage; users are held accountable offline for content shared on social media. Users may alter or limit their online presence to not reflect their views and reduce the risk of offline consequences.
The following video discusses the incident further and highlights the damage to Irving's reputation.
youtube
Source: Good Morning America 2022
Government surveillance is also an issue for protected participation on social media. This is exemplified by Douyin, the predecessor of TikTok launched for the Chinese market. The Chinese Communist Party (CCP) monitors online activity and enforces strict internet censorship restrictions (Gamso 2021). Government surveillance prevents protected participation as Douyin users must limit their online expression, particularly on political issues, to avoid legal prosecution.
The following video briefly explains the CCP's internet censorship practices.
youtube
Source: South China Morning Post 2020
Absence of institutional influence
The commodification of user information breaches the requirement of a space free from institutional influence. Data is collected by platform owners and offered as targeted marketing to external organisations. Meta Inc., parent company of Facebook and Instagram, generated $116.6b USD in revenue in 2022 primarily from promotion (Meta Inc. 2022). Platforms themselves benefit economically from their existence, profiting from the data generated by users’ self expression. Thus, social media is not free from economic institutional influence.
Attainability of the Ideal Public Sphere
The reading acknowledges doubts on the attainability of the public sphere outside of theory (Flinchum, Kruse & Norris 2018). Equal participation of all individuals requires the removal of all barriers which often stem from prominent sociocultural and economic issues in society (Flinchum, Kruse & Norris 2018). Thus, the ideal public sphere theorised by Habermas may be unattainable in both the digital and physical space.
Reference List
Belavadi, P, Burbach, L, Calero Valdez, A, Nakayama, J, Plettenberg, N & Ziefle, M 2020, 'User Behavior and Awareness of Filter Bubbles in Social Media', in V G Duffy (ed), Digital Human Modeling and Applications in Health, Safety, Ergonomics and Risk Management. Human Communication, Organization and Work, Springer International Publishing, SpringerLink, pp. 81-92.
Dotson, K & Vera, A 2022, Kyrie Irving returns to the Brooklyn Nets after serving 8-game suspension, CNN, viewed 2 March 2023, <https://edition.cnn.com/2022/11/20/us/kyrie-irving-return-brooklyn-nets/index.html >.
Flinchum, J R, Kruse, L M, Norris, D R 2018, 'Social Media as a Public Sphere? Politics on Social Media', The Sociological Quarterly, vol. 59, no. 1, pp. 62-84.
Gamso, J 2021, 'Is China exporting media censorship? China’s rise, media freedoms, and democracy', European journal of international relations, vol. 27, no. 3, pp. 858-883.
Ganguli, T & Sopan, D 2022, What to Know About Irving’s Antisemitic Movie Post and the Fallout, New York Times, viewed 2 March 2023, <https://www.nytimes.com/article/kyrie-irving-antisemitic.html>.
Good Morning America, 2022, Kyrie Irving causes controversy by sharing anti-Semitic film, viewed 10 March 2023, <Kyrie Irving causes controversy by sharing anti-Semitic film>.
James, J 2021, New perspectives on current development policy : COVID-19, the digital divide, and state internet regulation, Springer International Publishing AG, p.23-35.
Meta Inc., 2022, Meta Reports Fourth Quarter and Full Year 2022 Results, Meta Investor Relations, viewed 10 March 2023, <https://s21.q4cdn.com/399680738/files/doc_financials/2022/q4/Meta-12.31.2022-Exhibit-99.1-FINAL.pdf>.South China Morning Post 2020, How China censors the internet, viewed 11 March 2023, <How China censors the internet>
3 notes
·
View notes
Text
Imperial Lates
Upon experiencing my first Imperial late event, here are a few things that I learnt:
- My first lecture focused on precision polymer particles by Professor Rachel O’riley. Although typically such nanoparticles are governed by the ratio of hydrophobic and hydrophilic components for self assembly, here; the focus was on crystallisation driven self assembly (CDSA) which overrides this mechanism. DMA seeds are used as the original seeds on which the polymer begins to form through a process known as living polymerisation growth for greater control that leads to platelet like structures. Studying the complexity of assembly was important on exploring how polymer length, composition and chemistry can be altered to rationally tune nanoparticle shape and in turn it’s properties. Novel applications include directing biological interactions, such as cellular uptake, intracellular trafficking and immune response or the ability to modulate hydrogel mechanical and adhesion properties when used as fillers for antimicrobial and tissue engineering purposes.
- The second talk event was lead by Dr Catherine Kibirige on treating HIV in rural African communities. HIV is particularly difficult to treat and has to be rather suppressed because of it’s elusion from the immune system. Using a continually shifting shield of glycans, it prevent antibodies from detecting and attacking. It also replicates rapidly using reverse transcriptase to develop a pool of diverse HIV strains - called quasi-species - whilst attacking helper T-cells that orchestrate the immune system’s cell signalling. Finally it has a long incubation period and is slow to reveal (typically 5-10 years), where by that point it may have shredded the victims immune system. There are campaigns that have been developed, notably the ongoing UN led campaign of 95-95-95; where 95% people with HIV know their status, then 95% are receiving their treatment and 95% have suppressed their viral load by 2030. Suppression is the best we have at the current moment with no vaccine, with the Undetectable= Untransmittable campaign (U=U), sexual transmissions of HIV can be stopped by lowering the viral load in blood whilst on effective treatment. Dr Kibirige has been a part of the HIVQuant project that is a HIV-1 kit (working on portable solar or battery driven cyclers) that provides a treatment monitoring solution for resource-constrained settings, especially in Africa to minimise monthly hourly trips to district hospitals to meet the 2030 95-95-95 UN target.
- Vera. AI was the final project that grasped my attention as AI is largely underrepresented in the field of healthcare. Being a hyper-personalised digital platform that focuses on gynaecological, hormonal health management and patient education, this AI tools aims to break women’s health taboos in communicating their medical needs. Focusing on improving patient’s ability to understand and learn, Vera.AI improves patient-doctor communication. This is a project still in it’s early stages but with incorporating ChatGPT in the future, it has colossal potential to democratise women’s health medical data.
#medicine#drugs#drug experiments#imperial college london#AI#HIV#chatgpt#nanoparticles#polymers#self help#university#u=u#95-95-95#united nations#immune system#Imperial lates#learning#womens health
5 notes
·
View notes
Text
Why must modern education embrace technology?
The way schools acknowledge the significance of technology in education, it is evident that the future of
school education in India is improving sustainably. Possessing strong knowledge of modern technologies, software and apps and their usability
can enable teachers to educate children better. Technology and its accessibility can help
teachers stay ahead of the curve and enhance the impact of learning.
Greater accessibility of educational resources and flexibility come with educational
digitisation, among other benefits. No matter what the level of expertise a teacher has in their field of knowledge, there is always an abundance of information undiscovered on the planet. Every teacher can't know everything, which is where technology comes to aid-
allowing us access to an unlimited pool of knowledge. It is also well-known that laptops
or desktops might not be commonly available in every family, but allowing students to access
modern software and tools in a classroom environment will enable them to encounter its
enormous opportunities and explore its applications.
Technology can assist with quality learning plans by personalising them based on
individual learning abilities, aptitude, age, etc. Custom learning software and
applications can offer personalised teaching experiences to help students learn at a rate that
aligns with their knowledge and development. Teachers can find it more flexible and seamless to
guide students to achieve their best potential. It becomes increasingly helpful to apply various
technological resources like visuals and video materials while explaining concepts in the
classrooms.
The requirements for the modern workforce’s digital skills are rising, and integrating
technology in education is the pathway to preparing our present younger generation for the future labour
market. Today’s young generation is exclusively digital by all means, and they can perceive
and process information faster when taught using tech-integrated learning models. With such
a tech-enabled curriculum, lessons are far more interactive and immersive, and students have
significantly better tools to explore thier creative abilities and design thinking skills.
Digitisation is making quality learning accessible globally to democratise education. Today,
even the most reputable universities are offering distance learning programs and digital
learning courses to enable studies universally accessible through e-learning tools and reduce
the access gap in the education sector. The conventional teaching methods consist of some
limitations for both teachers and students in several ways. But Blockchain in education made
it possible to store data, process feedback on each learner’s performance, and use this data to
help evaluate their progress.
Tools such as Virtual Reality have changed the landscape of classroom learning. A student
can be transported immediately into the scientific world to learn concepts by understanding
thier core. For example, a student can see how different organs work and retain the
understanding far longer with the help of VR. Similarly, they will gain conceptual clarity on
how each element contributes to motion and force in Physics. Virtual reality tools can make
learning exciting by exposing students to the infinite world of science and its
theories.
Technology allows us to store a vast amount of information that can help students to prepare
for exams with more resources. Students can
get all the test materials, competitive exam updates, study plans, and interactive lessons and easily
exchange information with peers. The tiresome process of finding previous years’ papers will
now be replaced with finding all the information online from different sources.
10X International school in Bangalore, has a new technology-integrated education concept that
provides the IB curriculum designed with a unique combination of human and artificial
intelligence. Just into a month of operations, the school already has made a bee-line of interested applicants, which is not surprising given the inclination towards technology that the millennial possess. Owing to the rapid technological advancements around the globe; and the s
obsolescence of jobs, 10X brings technology to the forefront of education and prepares
students to be equipped with the necessary skills to sustain and thrive in the future.
2 notes
·
View notes
Text
Insights to automation — should businesses close the loop?
A continuous cycle of insights to automation is the big trend in SaaS, but what are the pitfalls to following the crowd? Technology Magazine finds out

The partnership between ServiceNow and Celonis underlines a market trend plotted by acquisitions such as ProcessGold by UiPath, Signavio by SAP, myInvenio by IBM, and Lana Labs by Appian, as well as partnerships like ABBYY Timeline and Blue Prism. But what do these moves tell us about the trend, according to the leading research and advisory company, Forrester, of ‘closing the loop from insights to integration’?
Speaking on the partnership, Forrester asks if competitors to ServiceNow in the automation platform market will shy away from partnering with Celonis based on the depth of the relationship, and questions if the partnership is “a precursor to an acquisition”, like many before it?
Issues with closing the loop
According to Forrester, “organisations run the risk of tying process optimisation to automation and, even more concerning, to a particular vendor’s automation solution.”
Rob Koplowitz, VP Principal Analyst at Forrester, says that their data indicates that 76% of process optimisation efforts are in service of driving some form of end-to-end automation. As Koplowitz states, “including relevant stakeholders like customer experience professionals, governance, risk and compliance pros, etc. could provide critical insight as to when automation is not the right approach.”
In Koplowitz’s mind, there’s two schools of thought at play: “By creating a tighter link between insight through tools like process and task mining, re-engineering through modelling and documentation and execution through tools like DPA, RPA and low-code, we can streamline insight to automation execution and drive greater agility”.
Koplowitz believes this goal should be considered alongside a parallel approach that overly separates process optimisation from a prescribed automation approach, saying “if a vendor provides customers with a vertical stack, it’s likely that their automation tools will be the solution. If you sell hammers, everything looks like a nail.”
Tying process optimisation to automation
Bruce Mazza, Senior Vice President of Technology Alliances, Blue Prism, insists that it is all about balance, saying: “The best outcomes are possible when organisations find balance between automating existing processes, process re-engineering and optimisation across people, process, and digital workers.”
He added: “Tying process optimisation to automation is important to increase business outcomes including speed, efficiency, cost, and risk reduction. Insight starts by finding hidden bottlenecks and compliance risks at the system level and uncovering user behaviour. Technologies such as process and task mining help democratise insights and baseline the ‘as-is’ process in complex organisations. These insights help bring process excellence business analysts and automation CoEs together to solve problems.”
According to Mazza, “smart enterprises are using these insights to prioritise which processes are best to optimise and automate, then monitor and optimise the end-to-end performance to respond in real-time to remediate new bottlenecks. Without deeper insights, the wrong process variations may be automated, or rework may be required.”
Mazza goes on to add that “insights must be coordinated across many vendor’s systems in an open ecosystem approach including RPA, BPM, systems of record and engagement, and legacy systems. If the insights are limited to only a few systems, or can’t feed the wide array of intelligent automation tools companies use, the business outcomes will be limited.”.
Malcolm Ross — VP, Product Strategy & Deputy CTO at Appian, uses a real-world analogy to describe the process problem: “Take a checkout queue at a traditional retail store as a sample process problem: if the queues are too long when a new product launches or during the holiday busy season, there are a number of ways to mitigate this, such as hiring more clerks, distributing checkouts across the store, or varying the product release days. These are all solutions achieved through process optimisation.
“But, treating this solely as a process problem can prevent sight of the bigger picture and opportunity to change operations or even the business model. Instead of being a process problem, the queue is really a customer experience issue and it could lead to poor customer satisfaction if the wait time is too long. Another way to solve it would be to eliminate the checkout queue altogether and instead, enable staff with mobile devices and distribute them throughout the store to serve customers,” he added.
Analysis and constant review vital to unlocking benefits
Russell Lawrie, commercial director at EAS, a consultancy specialising in robotic automation processes and a UiPath Partner, believes that fully understanding the process and pain points is vital in looking at automation:
“Too often automation is identified as an answer to a particular process or issue without considering the practical and financial improvements of automation across the whole business,” he said.
Echoing Blue Prism, Lawrie says that organisations should “look at the people and ask what their tasks and roles are; learn what processes are undertaken and the issues they present; and know what the print volume is because paper is intrinsic to how a business operates.”
He further added that businesses should “then analyse other aspects such as what applications are being used, time being taken on particular tasks and even the volume of keystrokes required to carry out those tasks. Having this knowledge will show where automation can be of benefit and what solution and software will give the greatest efficiency gains. Don’t forget the right training is also vital for those using the system, otherwise value and benefits will soon be lost.”
Chris Huff, Chief Strategy Officer at Kofax, a California-based intelligent automation software provider, states bias as a potentially a huge issue: “Executives often call for transformation teams, often small and concentrated, to automate business processes based on that particular team’s insights. Any bias on the automation team can have major implications to future business, since automation teams tend to automate, implement and forget. As time passes, people move on to other jobs, yet the automation in all its bias remains.”
Huff says Kofax are thinking of future consequences, insisting they “must institute a continuous process review governance model that minimises early bias from automation efforts while providing oversight and review of automated business processes — so that they evolve as the business and macro environment changes. If not, we risk building modern digital business models today that have the potential to become legacy anchors to the business of the future.”
Vendor lock-in undesirable
Richard Rabin, Head of Process Intelligence at ABBYY, believes that organisations today are not necessarily looking for an all-in-one platform that promises to deliver everything for their intelligent automation, he said: “While they may want best-in-breed solutions and the ability to quickly plug them into existing solutions — as well as the convenience of an all-in-one platform, with process insights easily discoverable on the next platform upgrade — what they really want is to use the best solutions on the market without being tied to one vendor. Organisations need to be careful of standardising on an all-in-one automation and process mining solution if it locks them into an inferior solution. In fact, easy interoperability between automation and mining is better than full integration because it leaves open more options as far as finding the right insights.”
Malcolm Ross of Appian added that “using an integrated automation solution is useful to simplify and speed up deployment of an application. But it is not essential for a company to buy into any one vendor’s solution entirely, although having one software subscription for all automation needs allows organisations to have more control over the lifecycle of the technology, better security, as well as commitment from the vendor for long term maintenance and compatibility. Many organisations also use Appian with other existing automation solutions, such as RPA, process mining, and AI that we can integrate with easily.
Credits: Alex Tuck
Date: March 31, 2022
Source: https://technologymagazine.com/data-and-data-analytics/insights-to-automation-should-businesses-close-the-loop
2 notes
·
View notes
Text
Data Sharing Agreements: A Comprehensive Guide
In today’s interconnected digital world, data has become the lifeblood of businesses, governments, and organizations across the globe. With the increasing reliance on data-driven decision-making, the concept of data sharing agreements has gained prominence. This article dives deep into the intricacies of data sharing agreements, their importance, key considerations, and benefits.
Table of…

View On WordPress
0 notes
Text
Unlocking the Potential of Speech Recognition Dataset: A Key to Advancing AI Speech Technology
In the realm of artificial intelligence (AI), speech recognition has emerged as a transformative technology, enabling machines to understand and interpret human speech with remarkable accuracy. At the heart of this technological revolution lies the availability and quality of speech recognition datasets, which serve as the building blocks for training robust and efficient speech recognition models.
A speech recognition dataset is a curated collection of audio recordings paired with their corresponding transcriptions or labels. These datasets are essential for training machine learning models to recognize and comprehend spoken language across various accents, dialects, and environmental conditions. The quality and diversity of these datasets directly impact the performance and generalisation capabilities of speech recognition systems.
The importance of high-quality speech recognition datasets cannot be overstated. They facilitate the development of more accurate and robust speech recognition models by providing ample training data for machine learning algorithms. Moreover, they enable researchers and developers to address challenges such as speaker variability, background noise, and linguistic nuances, thus enhancing the overall performance of speech recognition systems.
One of the key challenges in building speech recognition datasets is the acquisition of diverse and representative audio data. This often involves recording a large number of speakers from different demographic backgrounds, geographic regions, and language proficiency levels. Additionally, the audio recordings must capture a wide range of speaking styles, contexts, and environmental conditions to ensure the robustness and versatility of the dataset.
Another crucial aspect of speech recognition datasets is the accuracy and consistency of the transcriptions or labels. Manual transcription of audio data is a labor-intensive process that requires linguistic expertise and meticulous attention to detail. To ensure the reliability of the dataset, transcriptions must be verified and validated by multiple annotators to minimise errors and inconsistencies.
The availability of open-source speech recognition datasets has played a significant role in advancing research and innovation in the field of AI speech technology. Projects such as the LibriSpeech dataset, CommonVoice dataset, and Google's Speech Commands dataset have provided researchers and developers with access to large-scale, annotated audio datasets, fostering collaboration and accelerating progress in speech recognition research.
Furthermore, initiatives aimed at crowdsourcing speech data, such as Mozilla's Common Voice project, have democratised the process of dataset creation by enabling volunteers from around the world to contribute their voice recordings. This approach not only helps to diversify the dataset but also empowers individuals to participate in the development of AI technologies that directly impact their lives.
In conclusion, speech recognition datasets are indispensable assets in the development of AI speech technology. By providing access to high-quality, diverse, and representative audio data, these datasets enable researchers and developers to train more accurate and robust speech recognition models. As AI continues to reshape the way we interact with technology, the role of speech recognition datasets will remain paramount in driving innovation and progress in this dynamic field.

0 notes
Text
Online Marketplaces and Luxury Brands: The Digital Communication Challenge
“Unlike the fragmented universe of drivers, rental accommodation, beauty products or food delivery, there are not many luxury brands that really matter.”
The Financial Times wrote earlier in the year that the democratic nature of online shopping platforms dilutes the prestige and premium of luxury items. Being able to shop Nike in the same browser you’re shopping Burberry undermines the heritage and value of the brand, they argued.
However, E-commerce platforms have democratised access to luxury goods. And while the traditional understanding of exclusivity and brand experience are challenged, there are ways to ensure the sartorial themes of luxury fashion, namely craftsmanship and affluence, are maintained.
Cosette is an Australian-owned online luxury handbag and accessory retailer that sells from over 20 high-end fashion brands. Like many retailers, Cosette operates an interconnected digital landscape. Website, social media, newsletters, campaign lookbooks, seasonal trends, affiliate marketing and content, as well as the option to shop in store at the Cosette shopfront at The Rocks, defines our presence in industry.
Like luxury brands themselves, Cosette prioritises personalisation and a clearly defined brand experience. With nine years in market, our direct sales have allowed us to gather and utilise customer data to create a curated and in-demand edit of luxury brands. Cosette’s collection feels bespoke, and we are committed to ongoing review and refinement of our buying, so customers can rely on us to offer find them their most-wanted pieces. This level of customisation strengthens our relationship with consumers, and is a standard framework of our online store.
Being selective with the brands we offer, carefully curating our brand image and creating ‘exclusivity’ of our own, results in a customer experience that is communicated precisely as intended.



0 notes
Text
Mixtral 8x22B sets new benchmark for open models
New Post has been published on https://thedigitalinsider.com/mixtral-8x22b-sets-new-benchmark-for-open-models/
Mixtral 8x22B sets new benchmark for open models
.pp-multiple-authors-boxes-wrapper display:none;
img width:100%;
Mistral AI has released Mixtral 8x22B, which sets a new benchmark for open source models in performance and efficiency. The model boasts robust multilingual capabilities and superior mathematical and coding prowess.
Mixtral 8x22B operates as a Sparse Mixture-of-Experts (SMoE) model, utilising just 39 billion of its 141 billion parameters when active.
Beyond its efficiency, the Mixtral 8x22B boasts fluency in multiple major languages including English, French, Italian, German, and Spanish. Its adeptness extends into technical domains with strong mathematical and coding capabilities. Notably, the model supports native function calling paired with a ‘constrained output mode,’ facilitating large-scale application development and tech upgrades.
Mixtral 8x22B Instruct is out. It significantly outperforms existing open models, and only uses 39B active parameters (making it significantly faster than 70B models during inference). 1/n pic.twitter.com/EbDLMHcBOq
— Guillaume Lample (@GuillaumeLample) April 17, 2024
With a substantial 64K tokens context window, Mixtral 8x22B ensures precise information recall from voluminous documents, further appealing to enterprise-level utilisation where handling extensive data sets is routine.
In line with fostering a collaborative and innovative AI research environment, Mistral AI has released Mixtral 8x22B under the Apache 2.0 license. This highly permissive open-source license ensures no-restriction usage and enables widespread adoption.
Statistically, Mixtral 8x22B outclasses many existing models. In head-to-head comparisons on standard industry benchmarks – ranging from common sense, reasoning, to subject-specific knowledge – Mistral’s new innovation excels. Figures released by Mistral AI illustrate that Mixtral 8x22B significantly outperforms LLaMA 2 70B model in varied linguistic contexts across critical reasoning and knowledge benchmarks:
Furthermore, in the arenas of coding and maths, Mixtral continues its dominance among open models. Updated results show an impressive performance improvement in mathematical benchmarks, following the release of an instructed version of the model:
Prospective users and developers are urged to explore Mixtral 8x22B on La Plateforme, Mistral AI’s interactive platform. Here, they can engage directly with the model.
In an era where AI’s role is ever-expanding, Mixtral 8x22B’s blend of high performance, efficiency, and open accessibility marks a significant milestone in the democratisation of advanced AI tools.
(Photo by Joshua Golde)
See also: SAS aims to make AI accessible regardless of skill set with packaged AI models
Want to learn more about AI and big data from industry leaders? Check out AI & Big Data Expo taking place in Amsterdam, California, and London. The comprehensive event is co-located with other leading events including BlockX, Digital Transformation Week, and Cyber Security & Cloud Expo.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.
Tags: 8x22b, ai, artificial intelligence, development, mistral ai, mixtral, Model, open source
#2024#8x22b#Accessibility#ai#ai & big data expo#AI models#ai news#ai tools#amp#Apache#application development#Articles#artificial#Artificial Intelligence#background#benchmark#benchmarks#Big Data#billion#Cloud#coding#collaborative#Companies#comprehensive#cutting#cyber#cyber security#data#developers#development
0 notes
Text
The Impact of E-Learning Videos on Education
In the rapidly evolving landscape of education, traditional learning methods are being augmented and, in some cases, replaced by innovative technologies that enhance engagement, accessibility, and effectiveness, including e-learning video production . E-learning videos have emerged as a powerful medium, revolutionising the way students learn and educators teach. In this blog, we delve into the profound impact of e-learning videos on education and explore how they are reshaping the future of learning. E-learning videos have the unique ability to captivate learners’ attention and deliver complex concepts in an easily digestible format. Through dynamic visuals, animations, and interactive elements, these videos bring learning to life, making it more engaging and memorable for students of all ages. By incorporating multimedia components such as graphics, simulations, and real-life examples, e-learning videos cater to diverse learning styles, ensuring that every student has the opportunity to grasp and retain information effectively. Moreover, e-learning videos break down geographical barriers and provide access to quality education regardless of location. With the proliferation of online learning platforms and mobile devices, students can now access educational content anytime, anywhere, allowing for flexible learning opportunities that accommodate individual schedules and preferences. This increased accessibility democratises education, empowering learners from diverse backgrounds to pursue their academic goals and unlock their full potential. One of the most significant advantages of e-learning videos is their capacity to deliver personalised learning experiences tailored to each student’s unique needs and learning pace. Through adaptive learning technologies and data-driven insights, educators can customise content delivery, assessments, and feedback to address individual strengths, weaknesses, and learning objectives. By providing targeted interventions and adaptive support mechanisms, e-learning videos enable students to progress at their own pace, fostering a deeper understanding of concepts and promoting mastery-based learning. Contrary to the misconception that online learning is isolating, e-learning videos promote collaboration and social interaction among students through various interactive features and collaborative activities. Virtual classrooms, discussion forums, and group projects facilitate peer-to-peer learning, knowledge sharing, and collaborative problem-solving, fostering a sense of community and camaraderie among learners. Additionally, social learning platforms enable students to connect with peers, mentors, and subject matter experts, creating a supportive learning ecosystem where individuals can learn from each other’s experiences, perspectives, and insights. For educators, e-learning videos serve as valuable tools that enhance instructional delivery, streamline content creation, and facilitate assessment and feedback processes. With user-friendly authoring tools and intuitive learning management systems (LMS), educators can design and develop interactive e-learning videos that align with curriculum objectives, instructional goals, and learner outcomes. Furthermore, e-learning videos enable educators to experiment with innovative teaching methodologies, such as flipped classrooms, blended learning models, and gamified learning experiences, thereby expanding pedagogical possibilities and fostering creativity in the classroom. In conclusion, the impact of e-learning videos on education is undeniable, revolutionising the way students learn, educators teach, and knowledge is disseminated. From enhancing engagement and accessibility to facilitating personalised learning experiences and fostering collaboration, e-learning videos have the power to transform education and empower learners worldwide. At Shot Blast Media, we are committed to supporting the advancement of education through high-quality e-learning video production services . Whether you’re an educational institution, corporate training provider, or e-learning platform, we partner with you to create engaging, impactful, and immersive e-learning videos that inspire learning and drive results. Contact the Shot Blast Media team today to learn more about how we can help you harness the power of e-learning videos to transform education and empower learners worldwide. Our friendly team are always happy to help. +44 (0)113 288 3245 | [email protected] Your Industrial Story Starts Here Press the button. Make the call. Transform your media. +44 (0)113 288 3245 [email protected] Contact Us
0 notes