#facebook data leak
Text
More than 400 Malicious Android and iOS Apps Stealing Login Credentials: Report
More than 400 Malicious Android and iOS Apps Stealing Login Credentials: Report
After Meta researchers discovered more than 400 rogue apps across each of their separate app marketplaces, Apple and Google were both made aware of the problem. By using their Facebook accounts, users could log into the aforementioned apps or access their extra features. The user’s credentials were taken after being entered and exploited to grant unauthorised access to the victim’s…

View On WordPress
0 notes
Text



IN THE FALL OF 2020, GIG WORKERS IN VENEZUELA POSTED A SERIES OF images to online forums where they gathered to talk shop. The photos were mundane, if sometimes intimate, household scenes captured from low angles—including some you really wouldn’t want shared on the Internet.
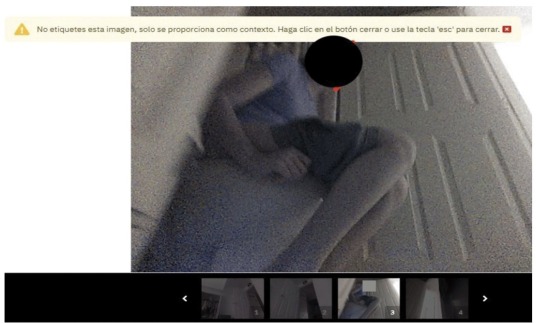
In one particularly revealing shot, a young woman in a lavender T-shirt sits on the toilet, her shorts pulled down to mid-thigh.
The images were not taken by a person, but by development versions of iRobot’s Roomba J7 series robot vacuum. They were then sent to Scale AI, a startup that contracts workers around the world to label audio, photo, and video data used to train artificial intelligence.
They were the sorts of scenes that internet-connected devices regularly capture and send back to the cloud—though usually with stricter storage and access controls. Yet earlier this year, MIT Technology Review obtained 15 screenshots of these private photos, which had been posted to closed social media groups.
The photos vary in type and in sensitivity. The most intimate image we saw was the series of video stills featuring the young woman on the toilet, her face blocked in the lead image but unobscured in the grainy scroll of shots below. In another image, a boy who appears to be eight or nine years old, and whose face is clearly visible, is sprawled on his stomach across a hallway floor. A triangular flop of hair spills across his forehead as he stares, with apparent amusement, at the object recording him from just below eye level.

iRobot—the world’s largest vendor of robotic vacuums, which Amazon recently acquired for $1.7 billion in a pending deal—confirmed that these images were captured by its Roombas in 2020.
Ultimately, though, this set of images represents something bigger than any one individual company’s actions. They speak to the widespread, and growing, practice of sharing potentially sensitive data to train algorithms, as well as the surprising, globe-spanning journey that a single image can take—in this case, from homes in North America, Europe, and Asia to the servers of Massachusetts-based iRobot, from there to San Francisco–based Scale AI, and finally to Scale’s contracted data workers around the world (including, in this instance, Venezuelan gig workers who posted the images to private groups on Facebook, Discord, and elsewhere).
Together, the images reveal a whole data supply chain—and new points where personal information could leak out—that few consumers are even aware of.
(continue reading)
#politics#james baussmann#scale ai#irobot#amazon#roomba#privacy rights#colin angle#privacy#data mining#surveillance state#mass surveillance#surveillance industry#1st amendment#first amendment#1st amendment rights#first amendment rights#ai#artificial intelligence#iot#internet of things
5K notes
·
View notes
Text
The surveillance advertising to financial fraud pipeline

Monday (October 2), I'll be in Boise to host an event with VE Schwab. On October 7–8, I'm in Milan to keynote Wired Nextfest.

Being watched sucks. Of all the parenting mistakes I've made, none haunt me more than the times my daughter caught me watching her while she was learning to do something, discovered she was being observed in a vulnerable moment, and abandoned her attempt:
https://www.theguardian.com/technology/blog/2014/may/09/cybersecurity-begins-with-integrity-not-surveillance
It's hard to be your authentic self while you're under surveillance. For that reason alone, the rise and rise of the surveillance industry – an unholy public-private partnership between cops, spooks, and ad-tech scum – is a plague on humanity and a scourge on the Earth:
https://pluralistic.net/2023/08/16/the-second-best-time-is-now/#the-point-of-a-system-is-what-it-does
But beyond the psychic damage surveillance metes out, there are immediate, concrete ways in which surveillance brings us to harm. Ad-tech follows us into abortion clinics and then sells the info to the cops back home in the forced birth states run by Handmaid's Tale LARPers:
https://pluralistic.net/2022/06/29/no-i-in-uter-us/#egged-on
And even if you have the good fortune to live in a state whose motto isn't "There's no 'I" in uter-US," ad-tech also lets anti-abortion propagandists trick you into visiting fake "clinics" who defraud you into giving birth by running out the clock on terminating your pregnancy:
https://pluralistic.net/2023/06/15/paid-medical-disinformation/#crisis-pregnancy-centers
The commercial surveillance industry fuels SWATting, where sociopaths who don't like your internet opinions or are steamed because you beat them at Call of Duty trick the cops into thinking that there's an "active shooter" at your house, provoking the kind of American policing autoimmune reaction that can get you killed:
https://www.cnn.com/2019/09/14/us/swatting-sentence-casey-viner/index.html
There's just a lot of ways that compiling deep, nonconsensual, population-scale surveillance dossiers can bring safety and financial harm to the unwilling subjects of our experiment in digital spying. The wave of "business email compromises" (the infosec term for impersonating your boss to you and tricking you into cleaning out the company bank accounts)? They start with spear phishing, a phishing attack that uses personal information – bought from commercial sources or ganked from leaks – to craft a virtual Big Store con:
https://www.fbi.gov/how-we-can-help-you/safety-resources/scams-and-safety/common-scams-and-crimes/business-email-compromise
It's not just spear-phishers. There are plenty of financial predators who run petty grifts – stock swindles, identity theft, and other petty cons. These scams depend on commercial surveillance, both to target victims (e.g. buying Facebook ads targeting people struggling with medical debt and worried about losing their homes) and to run the con itself (by getting the information needed to pull of a successful identity theft).
In "Consumer Surveillance and Financial Fraud," a new National Bureau of Academic Research paper, a trio of business-school profs – Bo Bian (UBC), Michaela Pagel (WUSTL) and Huan Tang (Wharton) quantify the commercial surveillance industry's relationship to finance crimes:
https://www.nber.org/papers/w31692
The authors take advantage of a time-series of ZIP-code-accurate fraud complaint data from the Consumer Finance Protection Board, supplemented by complaints from the FTC, along with Apple's rollout of App Tracking Transparency, a change to app-based tracking on Apple mobile devices that turned of third-party commercial surveillance unless users explicitly opted into being spied on. More than 96% of Apple users blocked spying:
https://arstechnica.com/gadgets/2021/05/96-of-us-users-opt-out-of-app-tracking-in-ios-14-5-analytics-find/
In other words, they were able to see, neighborhood by neighborhood, what happened to financial fraud when users were able to block commercial surveillance.
What happened is, fraud plunged. Deprived of the raw material for committing fraud, criminals were substantially hampered in their ability to steal from internet users.
While this is something that security professionals have understood for years, this study puts some empirical spine into the large corpus of qualitative accounts of the surveillance-to-fraud pipeline.
As the authors note in their conclusion, this analysis is timely. Google has just rolled out a new surveillance system, the deceptively named "Privacy Sandbox," that every Chrome user is being opted in to unless they find and untick three separate preference tickboxes. You should find and untick these boxes:
https://www.eff.org/deeplinks/2023/09/how-turn-googles-privacy-sandbox-ad-tracking-and-why-you-should
Google has spun, lied and bullied Privacy Sandbox into existence; whenever this program draws enough fire, they rename it (it used to be called FLoC). But as the Apple example showed, no one wants to be spied on – that's why Google makes you find and untick three boxes to opt out of this new form of surveillance.
There is no consensual basis for mass commercial surveillance. The story that "people don't mind ads so long as they're relevant" is a lie. But even if it was true, it wouldn't be enough, because beyond the harms to being our authentic selves that come from the knowledge that we're being observed, surveillance data is a crucial ingredient for all kinds of crime, harassment, and deception.
We can't rely on companies to spy on us responsibly. Apple may have blocked third-party app spying, but they effect nonconsensual, continuous surveillance of every Apple mobile device user, and lie about it:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
That's why we should ban commercial surveillance. We should outlaw surveillance advertising. Period:
https://www.eff.org/deeplinks/2022/03/ban-online-behavioral-advertising
Contrary to the claims of surveillance profiteers, this wouldn't reduce the income to ad-supported news and other media – it would increase their revenues, by letting them place ads without relying on the surveillance troves assembled by the Google/Meta ad-tech duopoly, who take the majority of ad-revenue:
https://www.eff.org/deeplinks/2023/05/save-news-we-must-ban-surveillance-advertising
We're 30 years into the commercial surveillance pandemic and Congress still hasn't passed a federal privacy law with a private right of action. But other agencies aren't waiting for Congress. The FTC and DoJ Antitrust Divsision have proposed new merger guidelines that allow regulators to consider privacy harms when companies merge:
https://www.regulations.gov/comment/FTC-2023-0043-1569
Think here of how Google devoured Fitbit and claimed massive troves of extremely personal data, much of which was collected because employers required workers to wear biometric trackers to get the best deal on health care:
https://www.eff.org/deeplinks/2020/04/google-fitbit-merger-would-cement-googles-data-empire
Companies can't be trusted to collect, retain or use our personal data wisely. The right "balance" here is to simply ban that collection, without an explicit opt-in. The way this should work is that companies can't collect private data unless users hunt down and untick three "don't spy on me" boxes. After all, that's the standard that Google has set.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/09/29/ban-surveillance-ads/#sucker-funnel

Image:
Cryteria (modified)
https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0
https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#commercial surveillance#surveillance#surveillance advertising#ad-tech#behavioral advertising#ads#privacy#fraud#targeting#ad targeting#scams#scholarship#nber#merger guidelines#ftc#doj
286 notes
·
View notes
Text
FREQUENCY: Episode 3 - A Soldier Boy Story
FREQUENCY: A Soldier Boy Story
EPISODE 3: “Elkwood, TN”
WORD COUNT: 4059
PAIRING: Soldier Boy X Reader
WARNINGS: (NSFW) Drugs, death, and mentions of suicide. Foul language, mentions of sex, or sexual innuendos. Slow burn starts now. (Sorry)
A/N: This story is dark, and covers mature themes. The main character, as well as other major characters, are offensive in nature, and may offend some people. Please peruse with caution, and remember that this is fiction. Reader discretion is advised. Please message me for any questions, comments, or concerns.
Masterlist | Taglist
When Vought had relocated me to Appalachian West Virginia, I didn’t know anyone. I was moved into a wooded mountain home, and watched over by two local park rangers. Both men, both never had been married. They had no idea how to take care of a young girl. But, from fourteen to eighteen, I struck up a bond with both of them that I had never experienced with another human being.
Jim was an older white man, maybe in his late fifties. He’d take me out on his gator and drive me all around the national park. He’d play me John Denver, as he’d smoke a pack of camel crush. He always told me never to smoke. That it was an awful habit he had formed. I told him he wouldn’t ever have to worry about that. I could always taste the pesticides.
I always swore Jim had been gay. He had the quintessential straight man behavior. He shot guns, smoked, watched sports, and enjoyed shitty, cheap beer. But, he was handsome. He was over fifty and had never been married. He isolated himself in the embrace of the forest. He would sit outside on the back porch, and paint the sunset. On holidays I’d ask him why he wasn’t with his family, he told me his job was to watch me, so he couldn’t be. But that wasn’t true. He never liked talking about home. He had no photos up from his childhood. And he never, ever reminisced on simpler times.
Wahkan was cherokee. He was from one of the reservations in East Tennessee. He moved up to West Virginia after getting offered more money to watch the lands up there. He accepted, of course, and funneled most, if not all of his money back to his family. Hell, the only reason he took on the challenge of raising me was so he could take the money from Vought, and send it back over to the res.
I’m always fortunate I was able to go with him to the reservation. I used to sit in the long grass with the other girls my age, and make jewelry from creek rocks, and turkey feathers. The sun would set in the distance, and a crackling fire would billow up into the sky. They’d have buffalo roasting over it. Its hide laid out, and drying in preparation for a warm winter coat.
When I decided to move back to the city after I had turned eighteen, it was a hard goodbye with the both of them. They watched as I got loaded back up into the same black Escalade that dropped me off all those years ago. I had waved goodbye with misty tears in my eyes. I wasn’t much of a crier, but watching them become smaller as the car drove away changed that.
A few months after I had gotten settled, things felt uneasy. I would communicate with some of the girls from the res on Facebook. Wahkan, and John hadn’t been answering me. They said they hadn’t heard from them either. That day I sat outside of Vought tower on a bench, and listened in on crisis management. From the sounds of it, there had been a data leak that was traced back to somewhere a few miles away from the town I used to stay in.
I hopped in my car and drove straight to West Virgina, only stopping for gas. I got there around nightfall. The cabin was dark, and quiet. That wasn’t normal, I had thought. I listened in, hearing one slow heartbeat. Thank god. He must’ve been sleeping. I let out a sigh of relief, and started back to my car— until I smelled it. Fresh, hot blood. My face went white, and my heart sank. I sprinted up to the front of the house, and noticed the door had been left cracked open, a trail of red footprints staining the wood.
I kicked the door open, screaming, seeing if I’d get any response. I flipped the lights to the house on, and looked around until I saw John’s body laying at the start of the kitchen. He was lifeless, and had been for an hour or so. They were just here. I searched frantically for Wahkan, trying to locate the sound of the slowing heartbeat I had heard earlier. My eyes landed on him. He was on the floor next to the couch.
“You shouldn’t be here,” he said. “It’s not safe, if they find you, they’ll kill you.”
I fell to my knees, rushing to his side. I placed my hand over the wound on his stomach, firmly pressing down to stop the bleeding.
“I don’t understand,” I cried. “Where’s the phone? I need to call an ambulance.”
“Too late,” He added, his voice barely above a whisper. “They cut the lines before they left.”
I reached into my pocket, going to pull out my own phone, but he placed his hands on mine, and stopped me.
“No,” he shook his head. “This is my time. It’s alright.”
“This is all my fault.” I said, as I felt hot tears streaming down my face, and neck.
“Don’t make this about you.” He laughed, soft and weak, putting a bloody hand against the side of my face.
“They’ll never get away with this.” I demanded.
He just shook his head, taking a deep breath. His eyelids were getting heavy. He didn’t have much time left.
“Just be…gentle,” He said. “And if you ever need a place to stay…a place that’s safe…a place where you can think of home…the reservation will welcome you with open arms.”
He wiped a tear away with his thumb, as he took his last breath. His body going limp. At least he was at peace.
Driving down the interstate with Uncle Sam by my side, I knew exactly where we would settle ourselves at. Elkwood is a tiny town a little ways from Gatlinburg, nestled at the bed of a beautiful valley. It’s quiet, and everyone knows each other. Like, if someone was throwing a small get together, you best believe the whole town was showing up. Whether it be the people who lived on the res, or just plain mountain folk.
I looked to my side, he was hunched over, my registration from the glove compartment settled in his lap. He’s snorting from a small pile of benzos he made me stop for earlier. He catches my gaze.
“Want some?”
“No thanks.” I chuckle.
“Suit yourself.” He says before diving back into the freshly crushed powder.
I watch him from the corner of my eye as I speed quickly down the highway. His hair, and beard are wild, and disheveled. He looks close to normal though in the sweat suit I gave him. I smile to myself, picturing him in that campy army green uniform. What a fraud, I think. The man was never a real soldier, they might as well have him look like one.
“You’re a pretty good driver for a woman.” He states, wiping off his nose, scooping his powder back into a ziplock bag.
“Thanks…” I say, rolling my eyes. He was much nicer when he wasn’t talking.
“So what's your thing?”
“I’m sorry?”
“Your thing, like, your power, I guess. I don’t fuckin’ know. You said you were a supe, right?”
“Yes, unfortunately.”
“Unfortunately? You must have some shitty power then.”
Some shitty power, I think. Rolling my eyes again.
“I get it,” He says smiling, leaning into me. “They forced it on ya while you were just a baby, huh?”
He reaches down, pulling out a pack of cigarettes. He puts one up to his lips and lights it, inhaling deeply. He blows the air out through parted lips as he continues his conversation.
“Seems like you bastards that had baby V are all just a bunch of freaks.”
I look over at him, raising an eyebrow. Now I know why they wanted to keep this guy fucking sedated.
“Say, what's your name anyway? Can’t go around just calling you a freak bastard.” He chuckles smugly.
“Actually,” I grin. “That is my name.”
He squints his eyes at me, pulling his cigarette away from his lips. He leans back, taking me in.
“Some parents you have calling you Freak Bastard, huh?”
“No,” I say, laughing now. “Just Freak, short for Frequency.”
He holds a finger up, tipping it at me. “Ah, but that's your Supe name, what's your real name?”
My real name. I go to change the subject.
“So, do you want to know my plan? The reason why I’ve rescued you? What I need your help with?”
“I’m gonna be honest with you sweetheart, I don’t usually go by a plan. I just wing it, and it happens to work out in my favor.”
“Right,” I nod. “That's why you ended up back in the ice again, huh?”
He glares at me, I beam right back at him.
“So,” I start. “Over the Summer Vought is throwing this huge party in celebration of Temp V.”
“What the fuck is Temp V?” He asks.
“...Temporary Compound V.” I say blankly.
“Right, I remember the cock sucker talking about that. Wait…When the fucks the Summer? And what the fuck year is it?”
“It's April. And it’s only been a year since they put you back in that chamber.”
He stares off into the distance, a solemn look on his face. I couldn’t even imagine having missed thirty years of life. Being put to sleep at the birth of the computer, and waking back up at the dawn of AI.
My empathy for him is short lived.
“Wait, you’re tellin’ me I got to wait,” He counts on his fingers. “Three fuckin’ months before we do this?”
“That's three months of freedom to you.”
“It's not fuckin' freedom if I’m gonna be on the run from these people finding me for Christs sake! Also, last time I fuckin’ checked, you’re practically holding me hostage!”
I scoff at him. “Oh please, you said earlier you could kill me, then leave at any time.”
“Yeah, well, that’s before you brought up family.”
Fuck. I think. I forgot about that.
I don’t say much else as I stare out at the road ahead of me. I feel my blood pressure going up, my arteries tightening at just the mention of my shitty lie. I’d make a horrible villain, I think. I feel guilty for everything, and everyone. I sigh, reaching down to the radio. I fiddle with it until it reaches a mixed station, classic hits from then and now.
“Well,” I say, pressing my foot harder onto the accelerator. “We can try and catch you up on everything you missed over the past thirty years.”
I turn up the dial as “Wonderwall” sings through the speakers.
We are about two hours from Tennessee now, he's fast asleep in the passenger seat. I got him a cheeseburger earlier, and picked up some hair shears from a dollar store on the same exit. I think he had worn himself out trying to trim his own hair and beard. He gets frustrated easily. I had offered to help, but he insisted on doing it himself.
As the gas pumps in my car, I look down at my phone. There had been no news alerts about a break in, or that Soldier Boy was missing. Vought must be doing a good job with crisis management. Or the CIA simply never let them know. I had no texts from anyone either. See, it isn’t out of the ordinary for me to disappear into the middle of nowhere. In fact, even the likes of Butcher knew I often found myself back home in the South to escape the sounds of the city.
Before I left I remembered to leave my debit and credit cards at home so I wouldn't be tempted to use them. I always kept a significant amount of cash in the safe anyway after years of training. I had turned on auto-payments for my rent, and obviously didn’t cancel any sort of subscription service like Netflix or Spotify. I thought if someone had been on my trail, the first thing they'd check would be my bank records. I made sure to turn off all location tracking on my phone, and decided to keep my VPN on 24/7. That wouldn’t be out of the ordinary to anyone either, again, considering my past in security.
The pump thuds, signifying it's filled up. I grab the handle, and pull the nozzle out. I always have to make sure to cover my nose with my sleeve in these instances. The fumes have made me pass out in the past. Benzene is so pungent that a normal human nose can even smell it if there's just 1 part per million in the surrounding air. I get dizzy just thinking about it.
We get close to Elkwood now, maybe twenty minutes out. I look over to him as he puffs little snores out into the air. His heartbeat is steady, his blood pressure normal in comparison to when I woke him up earlier.
Ever since he trimmed his hair, made himself look more presentable, I found myself not blaming women for being so attracted to him. I mean, he really was a beautiful man…As long as he kept that fuckin’ mouth shut. He has a light dusting of freckles across his nose, which is a stark contrast to his hard exterior. His eyes are a sweet shade of green, one that matches that awful uniform of his.
I pull up to the outskirts of the res, some of the younger kids had ended up building their own homes around this area. I walk up to Ama’s trailer, leaving him back in the car asleep to avoid any unwanted interactions. Before I can knock on the door, she goes to open it. Ama beams at me, as beautiful as ever, pulling me into a tight hug. She's the one I had been keeping in touch with on facebook after all these years.
“Welcome home.” She says smiling.
I smile back. Looking down I notice a small child wrapped around her legs, and a man standing up from the couch.
“You’ve been busy!” I exclaim, waving at the little boy hiding his face behind his mother, giggling.
“I have been,” She gestures to the man behind her. “This is my boyfriend, Asher.”
I put my hand out for a shake. A white guy, I think. I give her a look as he grips onto my hand. She looks back at me, beginning to laugh. I remember all of them always making fun of the Wasichu. Something catches her gaze in the distance. I turn around to see Soldier Boy leaning against the door of my car, lighting a cigarette.
“Who is this?” She asks, walking over to my car to inevitably meet the man I so desperately need to hide. Fuck, I think. What am I going to say about this?
He turns to her as she walks towards him. He puts on a big smile. She opens her arms wide for a hug.
“I’m Ben,” He beams. Ben. I swear his teeth glimmer in the light for a second. “I’ve heard so much about you.”
Bastard. I think. He knows what he's doing.
“It’s nice to meet you, Ben,” Ama wraps her arm around my shoulder as I walk over to the both of them, grinning awkwardly. “She never told me she had a man back home.”
I flush at this. Damn it. He looks down at his feet kicking at a little rock. He acts bashful, like he's been caught doing something naughty.
“What, she didn’t mention little ol’ me?” He asks.
“Nope, not even a peep.” She elbows me in the side.
I scoff at her, gesturing down to the little boy who had followed us over to the car.
“I’m sorry, last time I checked you have a fucking child!”
She leans into my neck, whispering to me through gritted teeth.
“The elders don’t want others to know…” She raises her eyebrows.
Ah. I nod. At least she has an excuse.
“Well,” She says, clapping her hands together. “Let's get you two home!”
She still has her hands wrapped around my shoulders, walking us towards my new abode for the next few months.
“He’s so hot. I didn’t know you were into older guys.” She whispers under her breath.
I elbow her in the side, my face heating up with some color. I could hear him smiling behind me. I wasn’t the only one around here with good hearing anymore.
The trailer is cute, small but cute. It’s painted a gentle powder blue, and the shutters contrast a pale yellow. It has a little porch with two adirondack chairs outfront, as well as a little bench swing hanging questionably from the wooden awning. Ama had made a note to put a bunch of potted flowers on the outside, knowing how much I like the smell of them. It also may have added to the overall aesthetic of the home.
She unlocked the front door for me, and then handed me the key. SB and Asher were behind us talking about something to do with the house. This is dangerous. He knew nothing about anything these days, let alone how to even have a conversation with a modern man. If you were to ask him who the current president was, he wouldn't have an answer. If you were to tell him we have had a black president, he’d probably pass out on the floor.
“Alright,” She says, showing off the place. “This is it.”
It's cute, small, but cute. I can't help but worry about the fact that neither of us will probably be able to stand each other at the end of this, but hey, let's think positively.
“This is the living room, which is obviously attached to the kitchen.” She goes over to the couch, gesturing to it. “Pull out if he ever ends up in the dog house.” She clicks her tongue, winking at him.
The living area has a floral print sectional, and a leather recliner. In the center is an old wooden coffee table, and a big ass TV across from it, mounted to the wall.
“Cable, Netflix, ESPN, you name it.” She adds.
The kitchen has smaller versions of standard appliances, and every sort of pot and pan or baking dish we may need.
“The second eye on that stove doesn't work, so don't even try it. Oh, and unfortunately it is gas. If it really starts to bother you we can get you an electric.”
“Dont worry about it,” I wave my hand to her, brushing it off. “A little methane never hurt anybody.”
She laughs, turning to Asher. “No need for a carbon monoxide detector with this one in the area.”
I look over at SB, he looks thoroughly confused. Standing here now I realize I still never told him the gift compound v gave me. I’m sure he's just utterly bewildered by this point. He looks between Ama and I like we’re fucking crazy.
“Shower, bath, toilet. Don’t flush, and run laundry or do dishes at the same time.”
Bathroom, much like the rest of the house, is small. But again, it has everything we may need, so I can't complain. Also we lucked out with having a washer and dryer on site. The last thing I want is having to drag him to a laundromat.
“And the best part, the bedroom!” She kicks the door open, displaying a very comfortable queen size bed. Only one. I think. Thank god for the pull out couch.
“Drawers line the walls over here under the TV, and there are some more underneath the mattress.”
“Awesome,” I beam. “Really Ama, I can't begin to thank you enough.”
She smiles, pulling me into a big hug.
“We’re so happy you're here.”
She goes up to SB, resting a careful hand on his shoulder, smiling at him tenderly. He nods to her, thanking her as well.
“Alright, I’ll leave you to it. Don’t do anything I wouldn’t, and text me if you need me.”
“Will do.” I say, following her over to the front door, and closing it behind them.
I take a deep breath, pushing my back against the door, sliding down onto the floor. I jolt my head up, pointing at him.
“He didn’t say anything you didn’t know, did he?”
He shrugs, moving over to the sectional and plopping himself down on it.
“So you're telling me I have to stay in this shack with you for three months?” He ignores my question.
I narrow my eyes on him.
“You got anything better to do?”
“Yeah, fleeing the country to sunny Costa Rica.” He counters.
I scoff, standing up, and walking over to the sink. I grab a cup from the cupboard, and pour myself a glass of water from the tap.
“They make it pretty hard these days. Y’know, crossing the border.” I add.
He smiles, a weak, weary expression on his face. He looks down at his hands.
“For the time being, I don’t mind being here. As long as you promise no one is gonna find me.”
“They won’t, and they never will. I told you, once you help me with this, you are free to go. I will get you out of here, family in hand, no problem.”
He stares at me for a moment. It’s silent. He watches me with squinted eyes.
“What's all this about gas stoves? You pyrokinetic?”
I start laughing, in fact, I start laughing really hard. So hard I have to bring a finger up to my eyes to wipe.
He chuckles now too, watching me.
“What?” He says.
“No, I’m sorry. It was just funny, the way that you said it, I mean.”
“So, you are?”
“What?”
“A pyrokinetic.”
“Oh, God no.”
“Then what the fuck is your deal with gas stoves, little girl?” He grills, concerned.
“Okay, first of all, I’m not a little girl. I am an adult.” I gesture down to my obvious adult body.
“Yeah, whatever. You’re at least a hundred years younger than me, so.”
There is silence, until.
“It’s my senses, by the way. Since you’re curious, I mean.” I say suddenly.
“What do you mean?” He asks.
“My five senses, they are all heightened.”
“What, like taste and shit?”
“Yes, taste and shit.” I snort.
“You smell colors or something?” He jokes.
“Sometimes.” I say, shrugging my shoulders. I begin to walk off into the bedroom.
“Wait, what?” He glares at me questionably.
“I’m going to sleep.” I ignore him.
“I’m sorry, did you say you could smell colors?”
“Goodnight, Ben.” I put emphasis on his name, knowing he never told it to me. He grins. I start to close the door, he shouts to me from his spot on the couch.
“Leave the door unlocked, I’ll be in there in a few.”
“Nice try.” I say.
“A queen is plenty big for two!”
“So is that pullout couch.”
He groans as I close the door behind me.
As I fall asleep, I can only hope for the best. As God as my witness, I would never mean to lie about something as big as family. Especially since I don’t even have one to enjoy. I’d do anything for that. At this point though, my game plan would be; get revenge on Vought, face the consequences from him, and inevitably die. That sounds like a dream. I’d go out with a smile knowing my success in Vought slaughter. May he blow me up into a million little pieces.
Masterlist | Episode 4 | Taglist
Taglist:
@Sl33pylilbunny @Lanassmarty @Sydneyyyya @1-800shootmeplease @muhahaha303 @nancymcl @speedyrebelfan @ghh05ttt @agentorange9595 @let-me-luve-you @peachytits @darkdahl @deans-spinster-witch @soggybasementfries @ladysparkles78 @madamthemoo
#soldier boy the boys#soldier boy fanfic#soldier boy#soldier boy x reader#soldier boy smut#soldier boy imagine#the boys fanfic#the boys#homelander smut#homelander x reader#homelander#billy butcher x reader#billy butcher#jensen ackles x reader#jensen ackles
119 notes
·
View notes
Text
Europe is poised to deliver a potentially fatal blow to Facebook's surveillance business model.
Cory Doctorow:
A leak from the European Data Protection Board reveals that the EU's top privacy regulator is about to overrule the Irish Data Protection Commission and declare Facebook's business model illegal, banning surveillance-based ads without explicit consent
189 notes
·
View notes
Text
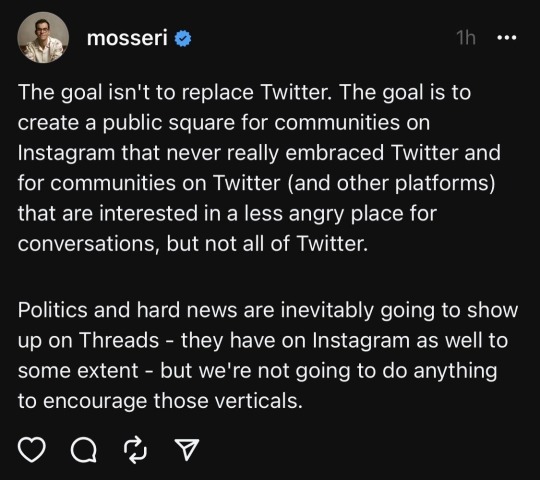
this is one of the lead developers of the new twitter clone, Threads. this is the sort of clean, sanitized, apolitical approach that people have—rightly—criticized a specific fraction of middle class russians for; this is a purged, poptimistic set of interests quite in line with many regimes around the world. and, after all, why would facebook, which leaked data on a massive scale, including to illegal data scraping companies working for political campaigns, not want to encourage "politics and hard news"?
54 notes
·
View notes
Text
I performed a social experiment today, and the results kinda lowkey shocked me:
TW for topics relating to violence, self harm and suicide, bullying/harassment, threats against personal safety, and adjacent topics.
Note: I refer to myself as a “good person” a few times here. I am not in any way suggesting that I am a model for people to follow. I refer to myself as such to show what I think a good person would do.
Idk why it continues to surprise me, but I did a social experiment today and I still find it so weird how outright fucking MEAN people are.
I was simply talking about my likes and dislikes, and I say a few things about a game I like (that gets a lot of hate for no reason). I expected backlash for liking the game, that’s normal and I get that no matter where I say it. Suddenly, I am getting death threats and suicide guilt trips for liking said game. I am told that i should kill myself, I should die, I should never have been born, my parents were right for starving and neglecting me.
Over a game.
The social experiment I performed was to create an overemphasized version of my current life, and to slip up and create loopholes to see if people would find out I was lying. I joked around and tried to copy the behavior of other people, while also subtly attention seeking and dropping hints that I was faking my life. I also did my best to get peoples social media for later purposes.
I was being serious when I was talking about liking the game, and THATS when people snapped. Suddenly they brought up all the evidence of why I was lying and how, which I found odd that they hadn’t before. I played up my argument and pretended to be one of the people that guilt trips and gaslighted others to win the argument to make them react more.
I did expect “kys” jokes and other mean comments. That is what I set out to find. I did NOT expect to be sent death threats, doxxing threats, threats to harm my irl family, etc.
I eventually revealed that it was an experiment, and that I had screen recordings and screenshots of the hate messages and messages proving whose social media belonged to who.
Now, I don’t have social media besides Pinterest, Tumblr, Ao3, and Discord. I purposefully did not ask for or share these things. I made burner Tiktok, Twitter, Snapchat, Facebook, and Instagram accounts, and followed the members with those.
After I revealed the information, I thought it would be a good idea to tell them (jokingly) that I was going to leak the screenshots to their family and friends that followed their socials.
And guess what, they IMMEDIATELY started apologizing and begging me not to. People were even advocating to ban me and erase all message data relating to me (as though that would do anything).
My experiment set out to show how humans, especially younger people ( <22), act when they are behind their online identity. And how they change immediately when they realize that someone they know in real life will find out.
I am not going to send screenshots to their IRLs, nor on and of my socials, as I am not petty and I respect their privacy as minors (and humans) like a good person would and should.
My complaint is just asking why people are so mean? What do they gain? Absolutely nothing. I keep being disappointed for being surprised, over and over again.
Please be a nice person, to anybody who read this long post. I have made huge mistakes in the past, in the same way that this experiment shows.
You do not have to like someone. You do not have to agree with their opinions. But imagine if this wasn’t an experiment. Imagine if a younger person with a little out of the ordinary life joined this group, and got treated this way.
They wouldn’t be prepared for this. This could harm people. This DOES harm people. There are countless, and I mean COUNTLESS news stories about cyber harassment and bullying leading to teen suicide.
Be a good person, both IRL and online. You can and will harm people by your negative actions. I don’t expect you to like everyone. I expect you to be kind and respectful. If they become angry or mean, that does not indicate that you can react harshly.
Cut off your connection. Block them. Report them. We have measures on the internet to essentially get a restraining order on people you don’t like.
Be a good fucking person.
Have a wonderful day/night. I am sorry for the rant.
#social media#social justice#social issues#social psychology#social science#experimental#experimentation#social experiment#science experiments#kindness#rant post#rant xx
14 notes
·
View notes
Note
what extensions do you use?
that depends on which browser profile i'm using d:
in general, i have:
uBlock Origin (trusted adblocker; it can block scripts too; supports custom rules)
Privacy Possum (blocks tracking headers and falsifies tracking data, possibly redundant now between UBO and firefox's own methods)
OVPN (mainly for specific webRTC leak protection and to block accessing certain site w/out my VPN on)
Tridactyl (keyboard navigation ! vim-style keybinds; i can't sing its praises enough)
some profile-specific extensions:
XKit Rewritten (makes tumblr usable lmao)
Facebook Container (apparently no longer needed in some versions of firefox ??)
Bypass Paywalls Clean (no more paywalls for news sites etc.; removed from mozilla store, i've linked the gitlab)
Unpaywall (as above but focused on academic articles; uses legal sources)
Just Delete Me (uses justdeleteme.xyz database; provides a link for deleting your account on the current website and indicates difficulty)
imo extensions are always a tradeoff between privacy (specifically, fingerprint resistance) and convenience. i plan to rework my firefox profiles (again lmao) w/ this in mind, since i don't need Just Delete Me 99% of the time, for example.
for things like cookie management i'd recommend using firefox's own inbuilt settings (again for fingerprinting reasons). i'd love a way to automatically refuse cookie agreements but i'm not installing an extra extension just for that. same w/ the "bypass twitter login" extensions - i can just do that manually via deleting those elements in UBO, or probably set a custom rule to automate it.
#theremustbebetteroptions#DATA_REQUESTS#online privacy#firefox#firefox extensions#adblock#REPO#REPO/SOFTWARE#REPO/SOFTWARE/FIREFOX
92 notes
·
View notes
Text
ALL WOMEN ARE BAD AND HE'RES WHY
Okay, now that I have your attention, important PSA time. Facebook's data will likely be leaked. Their servers are entirely unprotected at the moment, leaving most of the online world's personal data at stake. I have already looked into a few sample data collections, and they have enough data on each person to write a 9/11 research team-level analysis on each person. The number of facebook users in just the last year is considered to be some number I dont know, but I do know that it has over 2000000000 total entries of personal data. Based on the demographic of facebook, we can reasonably assume that most of these people are over 50. Meaning, statistically speaking, if you are reading this, these are your parents and grandparents. These are the people who loved you and raised you. And now, everything about them is going to be free, unencrypted access to the entire internet. So what can you do? Well, not much really. You could try deleting your account, but this just moves the data to an external server. The best thing you can do is set all of your demographic settings to crazy things, such as living in Antarctica and being 120 years old. Ideally, you could also delete all your posts, but this wont be perfect in itself.
#terf#196#r/196#hungryposting#hornyposting#shitpost#psa#news#please#read#no tldr#facebook#twitter#meme#r196#literally 19684
24 notes
·
View notes
Note
The email and phone number associated with my mainstream social media (such as facebook, Twitter and instagram) are being sold under the username I have on those accounts. I can’t figure out how this information got leaked. Was it sold by the social media companies themselves? I am more careful with fandom but now I’m stressed. If you’re mindful about separate emails and usernames, is there any possible scenario in which an employer could still buy info that would lead to an AO3 account?
--
I don't know. It depends on what has had a data breach, what has sold data, and how rigorous you've been about the separation.
21 notes
·
View notes
Text
Robomaus wrote this disquieting vision of a possible future, shared with permission, where the anti-AI art push "wins" that I think any anti-AI folks should take pause over, if only because it's one where nobody wins except the megacorps:
2023-2024: An unknown number of challengers hop on the bandwagon of suing a handful of AI companies publishing open-source (er, relatively) models and software. Their PR campaign is centered around the abuses of closed platforms such as OpenAI, and continued reliance on public technical misunderstandings.
2025: Butterick, Getty, or some unknown challenger wins the lawsuit. Styles are now copyrightable or "infringeable" in some form, and all input has to be licensed before being used in a model that has any potential of being used for profit in any form whatsoever. Research on generative models continues in a handful of European universities where data mining is still legal for purely academic purposes. After additional lobbying, the USCO decision is reversed, allowing for AI-generated works to be copyrighted by the prompter.
2026: Midjourney disappears into the night. Stability AI declares bankruptcy. OpenAI is able to pay their legal fees by a bailout from Elon Musk and Peter Thiel-types after a public shift to "anti-wokeism", but will never live up to the "open" standard or publish any models, or access to them. Emad becomes an angel investor and technical advisor for Drawful (no relation to the game), an AI-generated licensed art startup.
2027: DeviantArt is bought by ArtStation and is now an archive and source for additional ad revenue. If they haven't been already, Midjourney's model-training techniques are leaked. Models are widely shared on pirate sites with names such as www27.notavirus.modelputlocker.ru. Since Automatic1111's webui doesn't actually contain any models, it's left up for research purposes, or easily downloadable. However, most AI research is now moved in house by new divisions of major publishing companies, who are now also lobbying to have access to consumer GPUs restricted.
2028: Drawful and Soundful are now in open beta, if they haven't been already! Now you can make art in the style your favorite artists for only $30 a month; however, any art you prompt, in addition to any derivative work you make from the art you prompt, is owned by the service. Licensing costs extra.
Although they make it easy to train your own model by uploading a folder of your own work, artists get paid a fraction of a cent per generation on these sites, decided by a mixture of nearest-match reverse CLIP search, and a dropdown menu suggesting "popular styles" such as classic Disney, Pixar, and whatever limited-time offer corporate crossover event is currently happening. Signing away your right to be trained on is common practice in the industry. When you sign away your right, you also sign away the rights to all works created by fine-tuning a model on your work. The "most liked" works on the site have a chance to be re-recorded by the artist, with no credit whatsoever to the prompter. After all, they only came up with the idea and happened to like what came out of the AI; anyone can do that.
The scary part of this is, the ideas don't come out of nowhere, according to the author, this is directly based on what happened with Napster, Facebook and Spotify.
Which I think any artists cheering on the idea of applying a Spotify model to AI art should take pause over...
36 notes
·
View notes
Text
This day in history

This Saturday (Nov 4), I'm keynoting the Hackaday Supercon in Pasadena, CA.

#15yrsago The Essential Groucho https://memex.craphound.com/2008/11/03/the-essential-groucho/
#5yrsago Swedish ISP punishes Elsevier for forcing it to block Sci-Hub by also blocking Elsevier https://torrentfreak.com/swedish-isp-protest-site-blocking-by-blocking-rightsholders-website-and-more-181102/
#5yrsago Disneyland’s laundry used “gamification” as an “electronic whip,” leading to worker stress and injuries https://aeon.co/essays/how-employers-have-gamified-work-for-maximum-profit
#5yrsago Facebook blames malicious browser plugins for leak of 81,000 users’ private messages and offer of account data for 120,000,000 users https://www.wired.com/story/hackers-posted-private-facebook-messages/
#5yrsago A human being at Facebook manually approved the idea of targeting ads to users interested in “white genocide” https://theintercept.com/2018/11/02/facebook-ads-white-supremacy-pittsburgh-shooting/
70 notes
·
View notes
Text
BROWSERS, ADBLOCKERS AND OTHER ADDONS
tl;dr: Use LibreWolf and install CleanURLs, or if not, use uBlock Origin and CleanURLs on whatever browser you use.Librewolf : https://librewolf.net/uBlock Origin : https://ublockorigin.com/CleanURLs : https://github.com/ClearURLs/Addon
BROWSERS:
I will not start an argument about the necessity of privacy respecting browsers, I assume if you're reading this rambling of mine about the subject you're at least partially interested in not leaking all your data to the internet. Most browsers you'll encounter are leaky, and they will give your data to 3rd parties, either by poor design or implementation or knowingly and happily for money, but some browsers are just more leaky than others, so your choice of browser matters.
Apart from the ethical issues that uncontrollable data selling raises, online ads, tracking cookies and these tracking methods lead to a slower internet, higher processor and memory requirements, a messy design of webpages, and a plethora of other security issues and opportunities for bad actors ("hackers"). The sheer number of so-called attack vectors that web browsing presents is astounding.
Just to give a brief image of it, visit the site https://privacytests.org/, it will show you a comparison of web browsers on their performance of not leaking stuff to other people. The different tests are performed daily, and the website is rather informative about these tracking methods, attack vectors. Some part may be less important to you (Tor capabilities for example), so not all privacy respecting features are created equal, but this is the closest you'll ever get to an open and easily digestable learning material on browser privacy.
At the time of writing the best option for daily use is LibreWolf, basically a fine-tuned Firefox. It also has a lot of features for advanced users, but is generally easy to use, with built in uBlock Origin, and javascript disabled (which you may want to enable for certain web pages).You may want to know that certain browsers are tracking your movement and build a profile on you without ever visiting any webpage, and this category includes Firefox, and Chromium as well.
ADBLOCKERS:
Most adblockers have long sold their souls to the devil, and they are the ones collecting data on you, and some of them are purposefully not blocking certain ads, go figure. A lot of them are not open source, or not even open on their business pactices. You wouldn't hire a security company to protect your business who has a sketchy and non-transparent working, and who you cannot verify that they are not accepting money from the Chinese Communist Party, would you? The easy answer is to use uBlock Origin, an open source, transparent, free as in freedom software, with a completely transparent working, and verifiable everything. Please note that uBlock and uBlock Origin are not the same adblocker, and the regular uBlock has been bought by - guess what - an advertising company.
CleanURLs: Sometimes when you receive a youtube link, and you click on in, instead of youtube.com/watch?=xxxxxxx you'll get a ten times longer link with fbclid and really long alphanumerical stuff, isn't it weird? Does this link need to be this long to function? Well, the answer is no. It's just one of the tricks how websites track you with even more unnecessary cookies, that try to follow you from site A to site B (for example to figure out which youtube account belongs to which facebook user to make even more targeted ads). You can manually delete all those cross-site tracking stuff from every link you use but it's a tedious, but easily automated task. That's where CleanURLs come in, to do this instead of you. You'll be surprised how many tracking attempts are blocked in a day by this stuff.May these tools bring you a faster and cleaner internet experience.
18 notes
·
View notes
Text
//The Wire//2000Z April 2, 2024//
//ROUTINE//
//BLUF: ISRAELI STRIKE IN DAMASCUS KILLS THREE IRANIAN GENERALS. COLORADO BILL TO GRANT ILLEGALS IDENTITY DOCUMENTS ADVANCES.//
-----BEGIN TEARLINE-----
-International Events-
Syria: Last night Israeli forces struck a building immediately adjacent to the Iranian Embassy in Damascus. The main structure of the Iranian Embassy was partially damaged in the strike, while the building adjacent was demolished, killing three Iranian generals and several other military leaders/advisors. AC: Iran claims the building was a diplomatic wing of their Embassy compound, whereas Israel claims it was a commercial building. Though this detail is extremely important, independent verification is challenging due to the highly dense urban terrain. Of note, the former Canadian Embassy is also next door to the struck compound (Canada having ceased its diplomatic mission in Syria during the war). In any case, this is undoubtedly a strong escalation in an already very tense conflict.
-HomeFront-
USA: Emerging court documents that are part of an anti-trust lawsuit allege that Meta/Facebook not only has access to allegedly encrypted private messages, but also sold users’ private messages to Netflix as part of a data sharing agreement. AC: Though the exact details of these latest allegations are not possibly verifiable without a forensic audit of Facebook’s systems, Facebook was designed from the ground up to be an intelligence collection platform, as overwhelmingly indicated by hundreds of leaks, whistleblower testimonies, and governmental spying scandals over the years.
Colorado: The Colorado Road and Community Safety Act (SB24-182) has passed the Senate judiciary committee and has been forwarded to appropriations. AC: The only function of this three-page bill, despite it’s name, is to allow illegal immigrants to obtain a Colorado driver’s license. The bill as it currently stands also does not require illegals to be residents of Colorado to obtain a driver’s license. Though this seems very common among many states at this point, it is important to remember that Colorado also recently implemented their Automatic Voter Registration system, which automatically registers all persons who obtain a driver’s license to vote.
-----END TEARLINE-----
Analyst Comments: It is unclear as to what potential fine-print is contained in Colorado’s SB24-182 as it pertains to other existing laws. The text of the bill is clear enough, but as almost all laws contradict other laws and the Constitution itself, it’s almost certain that this bill will contradict existing legal precedent on the matter. Common sense would dictate that surely a driver’s license law cannot overrule Constitutional rights. However, in all 50 states citizens are finding out that when the rubber meets the road, the text of a law doesn’t really matter in practice. From an information warfare perspective, the intent is clear. First create the automatic voter registration system, then change the definitions of who the law applies to. Changing definitions and requirements is a classing hallmark of mission-creep, and if passed, it would be prudent to assume that this would at minimum move the goalposts when it comes to voting rights in Colorado.
Analyst: S2A1
//END REPORT//
3 notes
·
View notes
Text
An investigation uncovers a web of influence in the powerful coalition aligned behind the European Commission’s proposal to scan for child sexual abuse material online, a proposal leading experts say puts rights at risk and will introduce new vulnerabilities by undermining encryption.
In early May 2022, days before she launched one of the most contentious legislative proposals Brussels had seen in years, the European Union’s home affairs commissioner, Ylva Johansson, sent a letter to a US organisation co-founded in 2012 by the movie stars Ashton Kutcher and Demi Moore.
The organisation, Thorn, develops artificial intelligence tools to scan for child sexual abuse images online, and Johansson’s proposed regulation is designed to fight the spread of such content on messaging apps.
“We have shared many moments on the journey to this proposal,” the Swedish politician wrote, according to a copy of the letter addressed to Thorn executive director Julie Cordua and which BIRN has seen.
Johansson urged Cordua to continue the campaign to get it passed: “Now I am looking to you to help make sure that this launch is a successful one.”
That campaign faces a major test in October when Johansson’s proposal is put to a vote in the Civil Liberties Committee of the European Parliament. It has already been the subject of heated debate.
The regulation would obligate digital platforms – from Facebook to Telegram, Signal to Snapchat, TikTok to clouds and online gaming websites – to detect and report any trace of child sexual abuse material, CSAM, on their systems and in their users’ private chats.
It would introduce a complex legal architecture reliant on AI tools for detecting images, videos and speech – so-called ‘client-side scanning’ – containing sexual abuse against minors and attempts to groom children.
Welcomed by some child welfare organisations, the regulation has nevertheless been met with alarm from privacy advocates and tech specialists who say it will unleash a massive new surveillance system and threaten the use of end-to-end encryption, currently the ultimate way to secure digital communications from prying eyes.
The EU’s top data protection watchdog, Wojciech Wiewiorowski, warned Johansson about the risks in 2020, when she informed him of her plans.
They amount to “crossing the Rubicon” in terms of the mass surveillance of EU citizens, he said in an interview for this story. It “would fundamentally change the internet and digital communication as we know it.”
Johansson, however, has not blinked. “The privacy advocates sound very loud,” the commissioner said in a speech in November 2021. “But someone must also speak for the children.”
Based on dozens of interviews, leaked documents and insight into the Commission’s internal deliberations, this investigation connects the dots between the key actors bankrolling and organising the advocacy campaign in favour of Johansson’s proposal and their direct links with the commissioner and her cabinet.
It’s a synthesis that granted certain stakeholders, AI firms and advocacy groups – which enjoy significant financial backing – a questionable level of influence over the crafting of EU policy.
The proposed regulation is excessively “influenced by companies pretending to be NGOs but acting more like tech companies”, said Arda Gerkens, former director of Europe’s oldest hotline for reporting online CSAM.
“Groups like Thorn use everything they can to put this legislation forward, not just because they feel that this is the way forward to combat child sexual abuse, but also because they have a commercial interest in doing so.”
If the regulation undermines encryption, it risks introducing new vulnerabilities, critics argue. “Who will benefit from the legislation?” Gerkens asked. “Not the children.”
Privacy assurances ‘deeply misleading’
Star of That ‘70s Show and a host of Hollywood hits, 45-year-old Kutcher resigned as chairman of the Thorn board in mid-September amid uproar over a letter he wrote to a judge in support of convicted rapist and fellow That ‘70s Show actor Danny Masterson, prior to his sentencing.
Up until that moment, however, Kutcher had for years been the very recognisable face of a campaign to rid the Internet of CSAM, a role that involved considerable access to the top brass in Brussels.
Thorn’s declarations to the EU transparency register lists meetings with senior members of the cabinets of top Commission officials with a say in the bloc’s security or digital policy, including Johansson, antitrust czar Margrethe Vestager, Commission Vice-President Margaritis Schinas, and internal market commissioner Thierry Breton.
In November 2020, it was the turn of Commission President Ursula von der Leyen, who was part of a video conference with Kutcher and an organisation registered in the small Dutch town of Lisse – the WeProtect Global Alliance.
Though registered in the EU lobby database as a charity, Thorn sells its AI tools on the market for a profit; since 2018, the US Department of Homeland Security, for example, has purchased software licences from Thorn for a total of $4.3 million.
These tools are used by companies such as Vimeo, Flickr and OpenAI – the creator of chatbot ChatGPT and one of many beneficiaries of Kutcher’s IT investments – and by law enforcement agencies across the globe.
In November 2022, Kutcher and Johansson lined up as key speakers at a summit organised and moderated by then European Parliament Vice President Eva Kaili, who three weeks later was arrested and deposed over an investigation into the ‘Qatargate’ cash-for-lobbying scandal.
In March this year, six months before his resignation amid uproar over his letter of support for Masterson, Kutcher addressed lawmakers in Brussels, seeking to appease concerns about the possible misuse and shortcomings of the existing technology. Technology can scan for suspicious material without violating privacy, he said, a claim that the European Digital Rights association said was “deeply misleading”.
The Commission has been reluctant to detail the relationship between Thorn and Johansson’s cabinet under the EU’s freedom of information mechanism. It refused to disclose Cordua’s emailed response to Johansson’s May 2022 letter or a ‘policy one pager’ Thorn had shared with her cabinet, citing Thorn’s position that “the disclosure of the information contained therein would undermine the organisation’s commercial interest”.
After seven months of communication concerning access to documents and the intervention of the European Ombudsman, in early September the Commission finally released a series of email exchanges between Johansson’s Directorate-General for Migration and Home Affairs and Thorn.
The emails reveal a continuous and close working relationship between the two sides in the months following the roll out of the CSAM proposal, with the Commission repeatedly facilitating Thorn’s access to crucial decision-making venues attended by ministers and representatives of EU member states.
The European Ombudsman is looking into the Commission’s refusal to grant access to a host of other internal documents pertaining to Johansson’s proposal.
FGS Global, a major lobbying firm hired by Thorn and paid at least 600,000 euros in 2022 alone, said Thorn would not comment for this story. Johansson also did not respond to an interview request.
Enter ‘WeProtect Global Alliance’
Among the few traces of Thorn’s activities in the EU’s lobby transparency register is a contribution of 219,000 euros in 2021 to the WeProtect Global Alliance, the organisation that had a video conference with Kutcher and Von der Leyen in late 2020.
WeProtect is the offspring of two governmental initiatives – one co-founded by the Commission and the United States, the other by Britain.
They merged in 2016 and, in April 2020, as momentum built for legislation to CSAM with client-side scanning technology, WeProtect was transformed from a British government-funded entity into a putatively independent ‘foundation’ registered at a residential address in Lisse, on the Dutch North Sea coast.
Its membership includes powerful security agencies, a host of governments, Big Tech managers, NGOs, and one of Johansson’s most senior cabinet officials, Antonio Labrador Jimenez, who heads the Commission’s team tasked with fighting CSAM.
Minutes after the proposed regulation was unveiled in May last year, Labrador Jimenez emailed his Commission colleagues: “The EU does not accept that children cannot be protected and become casualties of policies that put any other values or rights above their protection, whatever these may be.”
He said he was looking forward to “seeing many of you in Brussels during the WeProtect Global Alliance summit” the following month.
Labrador Jimenez officially joined the WeProtect Policy Board in July 2020, after the Commission decided to join and fund it as “the central organisation for coordinating and streamlining global efforts and regulatory improvements” in the fight against CSAM. WeProtect public documents, however, show Labrador Jimenez participating in WeProtect board meetings in December 2019.
Commenting on this story, the Commission said Labrador Jimenez “does not receive any kind of compensation for his participation in the WeProtect Global Alliance Management Board, and performs this function as part of his duties at the Commission”.
Labrador Jimenez’s position on the WeProtect Board, however, raises questions about how the Commission uses its participation in the organisation to promote Johannson’s proposal.
When Labrador Jimenez briefed fellow WeProtect Board members about the proposed regulation in July 2022, notes from the meeting show that “the Board discussed the media strategy of the legislation”.
Labrador Jimenez has also played a central role in drafting and promoting Johansson’s regulation, the same proposal that WeProtect is actively campaigning for with EU funding. And next to him on the board sits Thorn’s Julie Cordua, as well as government officials from the US and Britain [the latter currently pursuing its own Online Safety Bill], Interpol, and United Arab Emirates colonel, Dana Humaid Al Marzouqi, who chairs or participates in numerous international police task forces.
Between 2020 and 2023, Johansson’s Directorate-General awarded almost 1 million euros to WeProtect to organise the June 2022 summit in Brussels, which was dedicated to the fight against CSAM and activities to enhance law enforcement collaboration.
WeProtect did not reply directly to questions concerning its funding arrangements with the Commission or to what extent its advocacy strategies are shaped by the governments and stakeholders sitting on its policy board.
In a statement, it said it is led “by a multi-stakeholder Global Policy Board; members include representatives from countries, international and civil society organisations, and the technology industry.”
The financing
Another member of the WeProtect board alongside Labrador Jimenez is Douglas Griffiths, a former official of the US State Department and currently president of the Geneva-based Oak Foundation, a group of philanthropic organisations around the world providing grants “to make the world a safer, fairer, and more sustainable place to live”.
Oak Foundation has provided WeProtect with “generous support for strategic communications”, according to WeProtect financial statements from 2021.
From Oak Foundation’s annual financial reports, it is clear it has a long-term commitment to aiding NGOs tackling child abuse. It is also funding the closely linked network of civil society organisations and lobby groups promoting Johansson’s proposed regulation, many of which have helped build an umbrella entity called the European Child Sexual Abuse Legislation Advocacy Group, ECLAG.
ECLAG, which launched its website a few weeks after Johansson’s proposal was announced in May 2022, acts as a coordination platform for some of the most active organisations lobbying in favour of the CSAM legislation. Its steering committee includes Thorn and a host of well-known children’s rights organisations such as ECPAT, Eurochild, Missing Children Europe, Internet Watch Foundation, and Terre des Hommes.
Another member is Brave Movement, which came into being in April 2022, a month before’s Johansson’s regulation was rolled out, thanks to a $10.3 million contribution by the Oak Foundation to Together for Girls, a US-based non-profit that fights sexual violence against children.
Oak Foundation has also given to Thorn – $5 million in 2019. In 2020, it gave $250,000 to ECPAT to engage “policy makers to include children’s interests in revisions to the Digital Services Act and on the impact of end-to-end encryption” and a further $100,000 in support of efforts to end “the online child sexual abuse and exploitation of children in the digital space”. The same year it authorised a $990,000 grant to Eurochild, another NGO coalition that campaigns for children’s rights in Brussels.
In 2021, Oak Foundation gave Thorn a further $250,000 to enhance its coordinating role in Brussels with the aim of ensuring “that any legislative solutions and instruments coming from the EU build on and enhance the existing ecosystem of global actors working to protect children online”.
In 2022, the foundation granted ECPAT a three-year funding package of $2.79 million “to ensure that children’s rights are placed at the centre of digital policy processes in the European Union”. The WeProtect Global Alliance received $2.33 million, also for three years, “to bring together governments, the private sector, civil society, and international organisations to develop policies and solutions that protect children from sexual exploitation and abuse online”.
In a response for this story, Oak Foundation said it does not “advocate for proposed legislation nor work on the details of those policy recommendations”.
It did not respond directly to questions concerning the implications of Johansson’s regulation on privacy rights. A spokesperson said the foundation supports organisations that “advocate for new policies, with a specific focus in the EU, US, and UK, where opportunities exist to establish precedent for other governments”.
‘Divide and conquer’
Brave Movement’s internal advocacy documents lay out a comprehensive strategy for utilising the voices of abuse survivors to leverage support for Johansson’s proposal in European capitals and, most importantly, within the European Parliament, while targeting prominent critics.
The organisation has enjoyed considerable access to Johansson. In late April 2022, it hosted the Commissioner in an online ‘Global Survivors Action Summit’ – a rare feat in the Brussels bubble for an organisation that was launched just weeks earlier.
An internal strategy document from November 2022 the same year leaves no doubts about the organisation’s role in rallying support for Johansson’s proposal.
“The main objective of the Brave Movement mobilisation around this proposed legislation is to see it passed and implemented throughout the EU,” it states.
“If this legislation is adopted, it will create a positive precedent for other countries… which we will invite to follow through with similar legislation.”
In April this year, the Brave Movement held an ‘Action Day’ outside the European Parliament, where a group of survivors of online child sexual abuse were gathered “to demand EU leaders be brave and act to protect millions of children at risk from the violence and trauma they faced”.
Johansson joined the photo-op.
Survivors of such abuse are key to the Brave Movement’s strategy of winning over influential MEPs.
“Once the EU Survivors taskforce is established and we are clear on the mobilised survivors, we will establish a list pairing responsible survivors with MEPs – we will ‘divide and conquer’ the MEPs by deploying in priority survivors from MEPs’ countries of origin,” its advocacy strategy reads.
Conservative Spanish MEP Javier Zarzalejos, the lead negotiator on the issue in the parliament, according to the Brave Movement strategy has called for “strong survivors’ mobilisation in key countries like Germany”.
Brave Movement’s links with the Directorate-General for Migration and Home Affairs goes deeper still: its Europe campaign manager, Jessica Airey, worked on communications for the Directorate-General between October 2022 and February 2023, promoting Johansson’s regulation.
According to her LinkedIn profile, Airey worked “closely with the policy team who developed the [child sexual abuse imagery] legislation in D.4 [where Labrador Jimenez works] and partners like Thorn”.
She also “worked horizontally with MEPs, WeProtect Global Alliance, EPCAT”.
Asked about a possible conflict of interest in Airey’s work for Brave Movement on the same legislative file, the European Commission responded that Airey was appointed as a trainee and so no formal permission was required. It did say, however, that “trainees must maintain strict confidentiality regarding all knowledge acquired during training. Unauthorised disclosure of non-public documents or information is strictly prohibited, with this obligation extending beyond the training period.”
Brave Movement said it is “proud of the diverse alliances we have built and the expert team we have recruited, openly, to achieve our strategic goals”, pointing out that last year alone one online safety hotline received 32 million reports of child sexual abuse content.
Brave Movement has enlisted expert support: its advocacy strategy was drafted by UK consultancy firm Future Advocacy, while its ‘toolkit’, which aims to “build a beating drum of support for comprehensive legislation that protects children” in the EU, was drafted with the involvement of Purpose, a consultancy whose European branch is controlled by French Capgemini SE.
Purpose specialises in designing campaigns for UN agencies and global companies, using “public mobilisation and storytelling” to “shift policies and change public narratives”.
Beginning in 2022, the Oak Foundation gave Purpose grants worth $1.9 million to “help make the internet safer for children”.
Since April 2022, Purpose representatives have met regularly with ECLAG – the network of civil society groups and lobbyists – to refine a pan-European communications strategy.
Documents seen by this investigation also show they met with members of Johansson’s team.
A ‘BeBrave Europe Task Force’ meeting in January this year involved the ECLAG steering group, Purpose EU, Justice Initiative and Labrador Jimenez’s unit within the Directorate-General. In 2023 the foundation that launched the Justice Initiative, the Guido Fluri Foundation, received $416,667 from Oak Foundation.
The Commission, according to its own notes of the meeting, “recommended that when speaking with stakeholders of the negotiation, the organisations should not forget to convey a sense of urgency on the need to find an agreement on the legislation this year”.
This coordinated messaging resulted this year in a social media video featuring Johansson, Zarzalejos, and representatives of the organisations behind ECLAG promoting a petition in favour of her regulation.
Disproportionate infringement of rights
Some 200 kilometres north from Brussels, in the Dutch city of Amsterdam, a bright office on the edge of the city’s famous red light district marks the frontline of the fight to identify and remove CSAM in Europe.
‘Offlimits’, previously known as the Online Child Abuse Expertise Agency, or EOKM, is Europe’s oldest hotline for children and adults wanting to report abuse, whether happening behind closed doors or seen on video circulating online.
In 2022, its seven analysts processed 144,000 reports, and 60 per cent concerned illegal content. The hotline sends requests to remove the content to web hosting providers and, if the material is considered particularly serious, to the police and Interpol.
Offlimits director between 2015 and September this year, Arda Gerkens is deeply knowledgeable of EU policy on the matter. Yet unlike the likes of Thorn, she had little luck accessing Johansson.
“I invited her here but she never came,” said Gerkens, a former Socialist Party MP in the Dutch parliament.
“Commissioner Johansson and her staff visited Silicon Valley and big North American companies,” she said. Companies presenting themselves as NGOs but acting more like tech companies have influenced Johansson’s regulation, Gerkens said, arguing that Thorn and groups like it “have a commercial interest”.
Gerkens said that the fight against child abuse must be deeply improved and involve an all-encompassing approach that addresses welfare, education, and the need to protect the privacy of children, along with a “multi-stakeholder approach with the internet sector”.
“Encryption,” she said, “is key to protecting kids as well: predators hack accounts searching for images”.
It’s a position reflected in some of the concerns raised by the Dutch in ongoing negotiations on a compromise text at the EU Council, arguing in favour of a less intrusive approach that protects encrypted communication and addresses only material already identified and designated as CSAM by monitoring groups and authorities.
A Dutch government official, speaking on condition of anonymity, said: “The Netherlands has serious concerns with regard to the current proposals to detect unknown CSAM and address grooming, as current technologies lead to a high number of false positives.”
“The resulting infringement of fundamental rights is not proportionate.”
Self-interest
In June 2022, shortly after the roll out of Johansson’s proposal, Thorn representatives sat down with one of the commissioner’s cabinet staff, Monika Maglione. An internal report of the meeting, obtained for this investigation, notes that Thorn was interested to understand how “bottlenecks in the process that goes from risk assessment to detection order” would be dealt with.
Detection orders are a crucial component of the procedure set out within Johansson’s proposed regulation, determining the number of people to be surveilled and how often.
European Parliament sources say that in technical meetings, Zarzalejos, the rapporteur on the proposal, has argued in favour of detection orders that do not necessarily focus on individuals or groups of suspects, but are calibrated to allow scanning for suspicious content.
This, experts say, would unlock the door to the general monitoring of EU citizens, otherwise known as mass surveillance.
Asked to clarify his position, Zarzalejos’ office responded: “The file is currently being discussed closed-doors among the shadow rapporteurs and we are not making any comments so far”.
In the same meeting with Maglione, Thorn representatives expressed a “willingness to collaborate closely with COM [European Commission] and provide expertise whenever useful, in particular with respect to the creation of the database of indicators to be hosted by the EU Centre” as well as to prepare “communication material on online child sexual abuse”.
The EU Centre to Prevent and Combat Child Sexual Abuse, which would be created under Johansson’s proposal, would play a key role in helping member states and companies implement the legislation; it would also vet and approve scanning technologies, as well as purchase and offer them to small and medium companies.
As a producer of such scanning technologies, a role for Thorn in supporting the capacity building of the EU Centre database would be of significant commercial interest to the company.
Meredith Whittaker, president of Signal Foundation, the US non-for-profit foundation behind the Signal encrypted chat application, says that AI companies that produce scanning systems are effectively promoting themselves as clearing houses and a liability buffer for big tech companies, sensing the market potential.
“The more they frame this as a huge problem in the public discourse and to regulators, the more they incentivise large tech companies to outsource their dealing of the problems to them,” Whittaker said in an interview for this story.
Effectively, such AI firms are offering tech companies a “get out of responsibility free card”, Whittaker said, by telling them, “’You pay us (…) and we will host the hashes, we will maintain the AI system, we will do whatever it is to magically clean up this problem”.
“So it’s very clear that whatever their incorporation status is, that they are self-interested in promoting child exploitation as a problem that happens “online,” and then proposing quick (and profitable) technical solutions as a remedy to what is in reality a deep social and cultural problem. (…) I don’t think governments understand just how expensive and fallible these systems are, that we’re not looking at a one-time cost. We’re looking at hundreds of millions of dollars indefinitely due to the scale that this is being proposed at.”
Lack of scientific input
Johansson has dismissed the idea that the approach she advocates will unleash something new or extreme, telling MEPs last year that it was “totally false to say that with a new regulation there will be new possibilities for detection that don’t exist today”.
But experts question the science behind it.
Matthew Daniel Green, a cryptographer and security technologist at John Hopkins University, said there was an evident lack of scientific input into the crafting of her regulation.
“In the first impact assessment of the EU Commission there was almost no outside scientific input and that’s really amazing since Europe has a terrific scientific infrastructure, with the top researchers in cryptography and computer security all over the world,” Green said.
AI-driven scanning technology, he warned, risks exposing digital platforms to malicious attacks and would undermine encryption.
“If you touch upon built-in encryption models, then you introduce vulnerabilities,” he said. “The idea that we are going to be able to have encrypted conversations like ours is totally incompatible with these scanning automated systems, and that’s by design.”
In a blow to the advocates of AI-driven CSAM scanning, US tech giant Apple said in late August that it is impossible to implement CSAM-scanning while preserving the privacy and security of digital communications. The same month, UK officials privately admitted to tech companies that there is no existing technology able to scan end-to-end encrypted messages without undermining users’ privacy.
According to research by Imperial College academics Ana-Maria Cretu and Shubham Jain, published last May, AI driven Client Side Scanning systems could be quietly tweaked to perform facial recognition on user devices without the user’s knowledge. They warned of more vulnerabilities that have yet to be identified.
“Once this technology is rolled out to billions of devices across the world, you can’t take it back”, they said.
Law enforcement agencies are already considering the possibilities it offers.
In July 2022, the head of Johansson’s Directorate-General, Monique Pariat, visited Europol to discuss the contribution the EU police agency could make to the fight against CSAM, in a meeting attended by Europol executive director Catherine de Bolle.
Europol officials floated the idea of using the proposed EU Centre to scan for more than just CSAM, telling the Commission, “There are other crime areas that would benefit from detection”. According to the minutes, a Commission official “signalled understanding for the additional wishes” but “flagged the need to be realistic in terms of what could be expected, given the many sensitivities around the proposal.”
Ross Anderson, professor of Security Engineering at Cambridge University, said the debate around AI-driven scanning for CSAM has overlooked the potential for manipulation by law enforcement agencies.
“The security and intelligence community have always used issues that scare lawmakers, like children and terrorism, to undermine online privacy,” he said.
“We all know how this works, and come the next terrorist attack, no lawmaker will oppose the extension of scanning from child abuse to serious violent and political crimes.”
8 notes
·
View notes
Text
Online Privacy and Security Tips
I am a firm believer that people should be able to be anonymous and secure online. Over a lifetime of trial and error, I've slowly learned the best ways to protect myself, and I'd like to pass on that knowledge to anyone who wants to hear it.
Last updated Jan 2024 (added note about 1Password checking HIBP for leaked passwords)
Switch to Firefox for your main browser on Windows and Android
Avoid any browser based on the Chromium project (like Microsoft Edge or Google Chrome), as Google has a major conflict of interest that prevents it from truly having users' privacy interests at heart. It makes ~70-80% of its revenue from its highly targeted advertising business, for which it must collect as much information about you as possible. That means that no matter how badly certain parts of Google want to build privacy into the browser, business interests and pressure will always supersede them, or at least force a compromise that still enables some tracking. Firefox is owned and maintained by a non-profit, so it does not have that same conflict, and it shows in the features it builds (and does not build) and the way it treats its users.
I made a list of my favorite Firefox extensions if you want to make your internet experience more pleasant and/or more secure!
Note: on iOS (i.e. iPhones), Firefox' functionality is limited by Apple restrictions and I do not recommend it - using Safari with Extensions like Adguard or 1Blocker is more secure and will give you a better experience. I made a list of my favorite iOS Safari extensions too!
Use a reputable password manager
I suggest 1Password (avoid LastPass and all of the password managers built into browsers, they're not safe). A good password manager increases your online safety by:
Helping you avoid password reuse (a common cause of account hacking)
Generating complex passwords that are difficult to guess or decrypt, and
Allowing you to keep records of all the different sites you have accounts on (so you can quickly change passwords in the event of a breach or delete your accounts on them when they outlive their usefulness)
Delete old accounts you no longer need
If your data has been deleted, no one can steal and leak it if they manage to hack the company.
Sign up for alerts from HaveIBeenPwned (HIBP) to be notified when your data is leaked in a site hacking.
This allows you to quickly change your password, hopefully before anyone is able to decrypt it (if it wasn't stored properly) or use it (if it was easy to guess). If you have reused that password on other sites, be sure to change your password on those sites either.
Note that some leaks don’t actually have any info about what website they were stolen from; if criminals just dump a huge text file onto a hacking forum that has your username and an accompanying password in it, HIBP doesn’t necessarily know what site they hacked to get that info. This is where a password manager like 1Password will come in handy, because 1P can actually use HIBP’s API to check each of your passwords and see if any of them have been leaked before. It will alert you if you need to change a specific password, even if you weren’t aware that site had been hacked.
Note: 1P only sends the first 5 characters of the password hashes to HIBP, not the passwords themselves. You can read more about the feature and how it preserves your privacy here.
Assume all profile pictures on any site are public, and avoid using your face for them if possible
New AI-powered sites like PimEyes can take an image of you, identify your face, and search for it in other, unrelated images around the internet. I searched for myself using a recent image that had never been posted to the internet before, and it immediately identified me in completely separate images I was using as my profile pictures on Facebook and LinkedIn and provided links to my accounts there. In this new AI era, assume anyone who snaps a picture of you can link you to your identity on any website where you have publicly posted your face before. Note: for what it's worth, you can submit an opt-out request to PimEyes if you are worried about someone using it to find your accounts online.
Never post the same (original) image on two accounts that you do want to keep separate
Even a simple reverse image search can allow someone to link your different sites together (i.e. don't post the same vacation photo on both Facebook and Tumblr because anyone can use that to link those sites together. Even if your Facebook or Instagram images are private, a friend of yours could still find the Tumblr you are not comfortable sharing with anyone. Marking your Tumblr as hidden only discourages search engines from indexing it; shady companies can and will ignore that and index it anyway.
7 notes
·
View notes