#cryptology
Text


the freshno nightcrawler
#fresno nightcrawler#fresno nightwalker#fresno alien#cryptid#cryptology#cryptidcore#cryptozoology#art#my artwork#artwork#this is old but i wanted to upload it anyway
39 notes
·
View notes
Text

Source: 9Gag
#cryptid#meme#sarcasm#also not sarcasm#creature#humor#snacking#memes#dad jokes#9gag#cryptids#gremlin things#lol#weird humor#food#cryptology#cheese#gremlin#funny#cryptid things#silly#shitposting#my shitposts
15 notes
·
View notes
Text
Death of a Codebreaker
Trevor Noah is right: we should all have a couple conspiracy theories that we believe in. He's right about a lot of other stuff too, but l need an excuse to post this.
I'm already on the final episode, and I know there's not going to be any definitive answer about what truly happened to Gareth Williams, because I've read just about everything John le Carré has written and I recently finished Mick Herron's Slow Horses book series. Obviously, these feats make me an expert on British Intelligence, even leaving out my extensive knowledge of James Bond (books and films). The point being that if the intelligence services are involved, then you might as well make up your own solution, because that's about as close as you'll get to the truth.
So, by the time I finish the final episode, I hope to have an intriguing, new conspiracy theory to add to my repertoire. . . because one bit of this is straight out of Mick Herron's Joe Country.
#gareth williams#mi6#gchq#british intelligence#british security services#mi5#spy#codebreakers#cryptology#bbc sounds#bbc radio wales#conspiracy theories
5 notes
·
View notes
Text
An Overview of The Nihilist Cipher
Hello! If you're someone interested in ciphers, read ahead to learn a little about one of my long time favorite ciphers, the Nihilist Cipher.
The Nihilist cipher is a polyalphabetic substitution cipher, which basically means it relies on multiple shift ciphers applied to different letters in the text being encoded. If you're familiar with the Vigenère Cipher, Nihilist is pretty similar in a lot of ways.
I'll go through some history of the cipher, how to encode/decode using it, and how to conduct a known plaintext attack on it. I'll also go over how you might approach attacking it without a known plaintext (mainly because I think it's cool), but it won't be the main focus.
History
The Nihilist Cipher was first used by Russian nihilists against Russia's tsarist regime in the late 19th century. It's since been used as a basis for several ciphers with improved security used in WWII, notably the VIC cipher which is essentially an extremely complex hand-encoded cipher that's part of the Nihilist family.
"If [the VIC] cipher were to be given a technical name, it would be known as a 'straddling bipartite monoalphabetic substitution superenciphered by modified double transposition.'"
David Kahn, Number One From Moscow
Usage
Encoding a message requires two things: A key and a Polybius square, known by you and the person you're communicating with. A Polybius square is one of these guys:
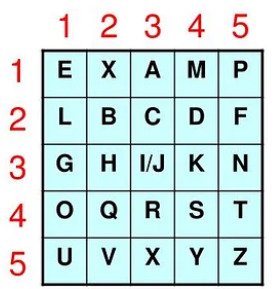
To use the cipher, you must first convert the plaintext into a numeric representation by mapping each letter to a number using the square. The mapping follows a (row, column) scheme, so the letter 'T' in the above square would become '45'. You'll notice that the square is 5x5, meaning there is 1 less square than there are letters in the English alphabet! This is typically solved by either choosing a square to represent 2 letters, differentiated using context by the receiver, or by simply leaving off an unused/infrequently used letter (often Q). It's also common to place a word at the start of the Polybius square, in this case "EXAMPLE" to offset the alphabet and avoid the mappings becoming trivial and obvious to attackers.
After we convert the plaintext to it's numeric representation, that's when the key becomes important. We first encode the key we picked using the Polybius square (i.e. the key MATH would become 14 13 45 32). Then, we repeat the key along the plaintext, and add each plaintext value to the key value to get the ciphertext!
To decode, the receiver must simply repeat the encryption process in reverse: repeating the key across the ciphertext, subtracting the key values, and translating the numeric plaintext back into English text. Because the encryption and decryption processes use the same key, the Nihilist Cipher is considered symmetric.
Known Plaintext Attack
Now we get into the fun part: How can we decode Nihilist encoded text without knowing the key? We will assume we know some ciphertext and the plaintext associated with it. Therefore, our goal is to use what we know to reveal the key, and use the key to decrypt the rest of the cipher. For example, assume we know that the first line of the Bee Movie script, "According to all known laws of aviation", results in the ciphertext "37 66 67 64 35 68 48 53 75 66 57 66 56 84 84 32 57 95 25 84 66 73 36 86 45 65 94 55 37 88 48 85 54".
Since the ciphertext is simply the result of adding the key to the plaintext, to find the key we only need to do the reverse and subtract the plaintext from the ciphertext!
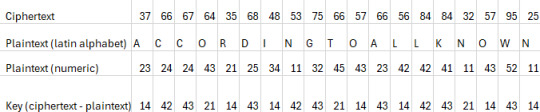
Even with only this short segment, we can see the repeating key is "14 42 43 21 14 43". Now we can repeat this key across the whole message and decrypt the Bee Movie script into numeric encoded plaintext.
At this point, you might be realizing where the next challenge lies. Unless you happen to be in a situation where you don't know the key yet somehow do know the Polybius square, this alone doesn't tell us very much! Since we've essentially converted our original problem into a simple substitution cipher, this is where we employ frequency analysis to figure out which number maps to which letter in the Polybius square. If you're up for a challenge you can do this manually, or use an online tool to analyze the frequency of each number and compare it to how often each letter of the English alphabet appears in typical text. Eventually, you'll be able to decode the Polybius square as the square below.
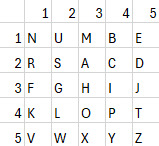
Ironically, the first snippet of The Bee Movie which we knew the plaintext of includes no 'E's, which are the most frequent letter in the English language, but letter frequencies of the full text would end up being much closer to the expected letter proportions.
Congratulations! You've now completed a plaintext attack on the Nihilist cipher and can sit down with a cup of tea for a bit of light reading .

Ciphertext-Only Attack
Now maybe that was too easy for you. Maybe you're a pro cipher-cracker, and you want to decode the Nihilist cipher without some "plaintext crutch". Here's how you can try to approach it! This method will need a large amount of ciphertext available, and relies on statistical analysis, plus some exploitation of the cipher's design to crack it.
The majority of this attack follows the same approach as a statistical attack on the Vigenère cipher. First you determine the key length by testing various key lengths, splitting the text up into groups that would be encoded with the same key, and computing the index of coincidence, which will be high (close to 0.068, the index of coincidence of English text) when the guessed key length is correct.
At this point, if this were the Vigenère cipher, we would have to go on to analyze the mutual index of coincidence between groups of ciphertext characters with the same key shifted by various amounts, but flaws in the Nihilist encoding system mean there's a good chance we can identify the key without this step!
Because of the way the Polybius square is set up, and the lack of modular arithmetic in the encoding method, every key letter value has exactly 25 possible ciphertext numbers that can result from that key. By comparing the ciphertext values encoded with the same shift, we can quickly identify or at least significantly narrow down the shift used to obtain those values! There are even a few cipher text values that immediately reveal what key was used to generate that cipher text (For example, a cipher text value of 30 can only be obtained using key=15). For a full list of possible ciphertext values generated by each key, check out this document I put together.
And that's it!
You are now a certified expert in all things Nihilist cipher. Go forth and use your new skill responsibly, leaving behind cryptic messages everywhere you go.
Happy decoding!

Sources:
https://www.cia.gov/resources/csi/static/Number-One-From-Moscow.pdf
https://en.wikipedia.org/wiki/VIC_cipher
https://cyberw1ng.medium.com/nihilist-cipher-an-in-depth-look-at-the-cryptographic-technique-2023-b05b83551957
https://courses.cs.washington.edu/courses/cse163/20wi/files/lectures/L04/bee-movie.txt
4 notes
·
View notes
Text
"Bismark Omit leafage buck bank."
2 notes
·
View notes
Text
I need you guys help because I am going crazy, a little while back I went through and I solved the substitution cipher in Dipper and Mabel’s Guide to Mystery and Non Stop Fun, literally just by guessing until it worked, but apparently there is an actual decoder somewhere in the book and I’ve gone through it countless times to try and find it and Googled it over and over with no luck, if any of you know where to find it I will be so happy, please help
#gravity falls#journal 3#gravity falls dipper#dipper pines#mabel pines#cryptology#bill cipher#cipher
7 notes
·
View notes
Text
just realized some people don’t know this:
cryptology is NOT the same as cryptozoology
Cryptology is the science of codes and ciphers
cryptozoology is the study of animals whose existence or survival is unproven, or the study of cryptids
I just searched cryptology because its my current obsession and stumbled upon lots of cryptid pictures and art, so I figured I should try and educate the masses
3 notes
·
View notes
Photo

https://archive.org/details/contemporary-cryptology-d.-catalino-et-al.-birkhauser-2005-ww/mode/2up
As the title implies, our aim in the course and in this text is to treat selected topics of the subject of contemporary cryptology, structured in five quite inde- pendent but related themes: Efficient distributed computation modulo a shared secret, multiparty computation, modern cryptography, provable security for pub- lic key schemes, and efficient and secure public-key cryptosystems. The beauty and multidisciplinarity of this topic motivated the interest of the participants, to whom we are very much indebted for their helpful contributions.
Thanks are due to the Centre de Recerca Matematica for organising and sponsoring the Advanced Course, to the CRM administrative staff for smoothly working out innumerable details, and to Paz Morillo for the mathematical organ- isation of the course and for making it such a pleasant experience. Special thanks go to all the participants of the course for their interest in the event and for their many comments on the material.
2 notes
·
View notes
Text
Codes, cyphers, and the National Cryptologic Museum
Codes, cyphers, and the National Cryptologic Museum
Located at the edge of Fort Meade, Maryland, in an old, nondescript motel, is the National Cryptologic Museum. Admission is free, and with that admission you can explore how the worlds of communications, mathematics, and security intersect in cryptology.
Photos from the National Cryptologic Museum
Hebern Electric Code machine, built around 1918, was one of the first U.S. developed modern coding…

View On WordPress
#American Civil War#codes#cold war#communications intelligence#cryptology#cyphers#fort meade#korean war#national security agency#NSA#vietnam war#world war i#world war II
2 notes
·
View notes
Text
#1 Memo: Gravitationsfeldanomalie in der 3. Etage
15/12/22
Seit einigen Tagen beobachten wir außerordentliche Raumkrümmung im Korridor der 3. Etage. Dies ist der erste paranormale Zwischenfall in unseren Räumlichkeiten und unsere Mitarbeitenden sind verständlicherweise in freudiger Erregung. Zwischen dem Aufenthaltsraum der Cryptozoolog*innen und der Feuerschutztür zum Büro der Paranormalen Informatik wölbt sich der Raum in einer ungewöhnlichen Form, bisher konnte mindestens ein Looping festgestellt werden.
Zwei Mitarbeitende der Cryptozoologie verbrachten den Morgen damit, mit einem Glas antiker Oliven aus dem Gemeinschaftskühlschrank das Gravitationsfeld auszutesten. Auf dem Hosenboden an Decke und Boden geheftet gelang es ihnen, sich quer durch den Raum vibrierende Oliven zuzuschieben.
Es gilt weiterhin rauszufinden, ob die Oliven durch die veränderte Gravitation vibrierten, oder ob es sich bei diesem Glas um semi-bewusste bakterielle oder hefige Lebensformen handelt, die den jahrelangen Kälteschock im Kühlschrank überlebten und verzweifelt und zitternd erwachten. Sicherheitshalber wurden die Oliven wieder an ihren Platz im zweiten Kühlfach gebracht, nachdem das Experiment abgeschlossen war.
Die zwei Cryptozoolog*innen beschrieben nach ihrer Rückkehr ins Büro aufsteigende Gefühle von Trauer und Zerstörungswut, und der Erkenntnis, dass das Universum absolut rechtlos und ohne Moral fungiere. Die beiden humanoiden Organismen stehen bis auf weiteres unter Beobachtung; zumindest bis sie aufhören, ihre Hände unter den kochenden Strahl unserer Kaffeemaschinen zu halten.
Wir raten bis auf weiteres allen Mitarbeitenden des Ministeriums für paranormale Angelegenheiten ab, den Korridor in Etage 3 zu nutzen. Allen Informatiker*innen, die bis auf weiteres hinter der Feuerschutztür verbarrikadiert sind wünschen wir alles Gute für die Zukunft!
2 notes
·
View notes
Text
you’ve heard of not safe for W0RK
but have you heard of not safe for wendigos ?
#asking the real questions#shitposting#not safe for wendigos#not safe fw#cryptids#wendigo#sorry I needed to get that one off my chest#creature#monster#wendigos#cryptology#monsters#memes#horror#lol#dark humor#funny#weird humor#weird#spooky#paranormal#cryptid#creatures#my shitposts
9 notes
·
View notes
Text
Women Cryptologists of World War II (U.S. 2022)
Women Cryptologists of World War II (U.S. 2022)
Posted on November 1, 2021 by VSC
Announced November 1, 2022:
This stamp honors all of the women cryptologists of World War II. One of the conflict’s best-kept secrets, their service played an inestimable role in the Allied victory. The stamp art features an image from a World War II–era WAVES recruitment poster with an overlay of characters from the “Purple” code. In the pane selvage,…

View On WordPress
2 notes
·
View notes
Text
Day X. Awii Errkjiti

Summary: Sqctxi’w ghvoocez uckbzxi xlevu alrqnia’ fiviix lbyp wazgjiti
Written for Day X of @flufftober !
#gravity falls#dipper pines#pacifica northwest#dipcifica#flufftober#flufftober 2022#cryptology#cryptograms
2 notes
·
View notes
Photo

Hey guys, check out our latest video- Binance Leading Web3 Fundings | Law enforcement inquiring surging for Coinbase | DIMO launches mainnet | 13% Americans holding crypto 🔰Credits to the original news content sources- 1- Binance Labs Leads Funding Round For Web3 Project- https://bitcoinist.com/binance-leads-funding-web3-project/ 2- Coinbase report shows dramatic increase in law enforcement enquiries worldwide- https://cointelegraph.com/news/coinbase-report-shows-dramatic-increase-in-law-enforcement-enquiries-worldwide 3- Decentralized automotive insight network DIMO launches mainnet- https://www.theblock.co/post/193837/decentralized-automotive-insight-network-dimo-launches-mainnet 4- 13% of Americans have now held crypto: JPMorgan research- https://cointelegraph.com/news/13-of-americans-have-now-held-crypto-jpmorgan-research ———————————————————————————————————————————————— 🔰If you Want to get 100 USDT, Register on the world's biggest crypto exchange- Binance and deposit more than $50 into your account. We'll both get a 100 USDT cashback voucher! 👉 https://bit.ly/bobinance #️⃣ Let's connect on Social Media:🌎 : 👍All links here (IG, Twitter, etc) - https://linktr.ee/cryptoikonmedia 📼 Also Streaming on Theta: https://www.theta.tv/cryptoikonmedia 💼 Business Inquiries: [email protected] 😎 Common username on all other major platform: @cryptoikonmedia 🔰About us: Crypto Ikon Media is a full-service Interactive #Crypto Media Agency. We provide 360-Degree Digital Branding & Marketing services to (Crypto, Defi, NFT, Web3, Metaverse & Blockchain) projects and companies. ———————————————————————————————————————————————— Disclaimer: Our content is not financial advice, legal advice or tax advice in any way, shape or form. Please do your own research. DM for credit or removal request (no copyright intended) ©️ All rights and credits reserved to the respective owner(s) . . . . . . #cryptocommunity #vechain #cryptoassets #criptotrading #tokenization #exchanges #blockchaingames #cryptokitties #ethereumproject #blockchaindevelopment #blockchainsolutions #earncrypto #airdropalert #cryptology #zilliqa #cryptogram #ftse #mainnet #instabitcoin #blockchain (at Delhi, India) https://www.instagram.com/p/CmHgeQbI3d5/?igshid=NGJjMDIxMWI=
#crypto#cryptocommunity#vechain#cryptoassets#criptotrading#tokenization#exchanges#blockchaingames#cryptokitties#ethereumproject#blockchaindevelopment#blockchainsolutions#earncrypto#airdropalert#cryptology#zilliqa#cryptogram#ftse#mainnet#instabitcoin#blockchain
1 note
·
View note
Text
just watched a video on the voynich manuscript (book from the 1400s written in an unknown language/code that has yet to be solved) and now i really really really really really wanna write a zine in my code & leave it in the hills for someone to find
#in a box probably#i have secret code that’s technically a substitution cipher but has gotten increasingly complex over the years#i don’t even know what i’d write it’s just b fun to see if someone could crack it#cryptology#ciphers#code cracking#voynich manuscript#secret code#zine
1 note
·
View note