#virtual servers
Text
Top cloud communication trends to follow in 2023

#cloud communication#cloud telephony#remote work#scalability#reliability#affordability#virtual servers#unified communication and collaboration (UCC)#AI#automation#5G connectivity#security#UCaaS#end-to-end encryption#multi-factor authentication#productivity#work-life balance#remote meetings#machine learning
0 notes
Text

I certainly didn’t see this being on my 2023 bingo card.
Edit: Ya’ll this meme above isn’t accurate anymore since other messages from the group came out. I made this meme when the first initial message came out.

The meme down below is more correct as to what’s probably happening with Ao3. Also wanted to say that despite the name of group, the people behind it are probably Russians.
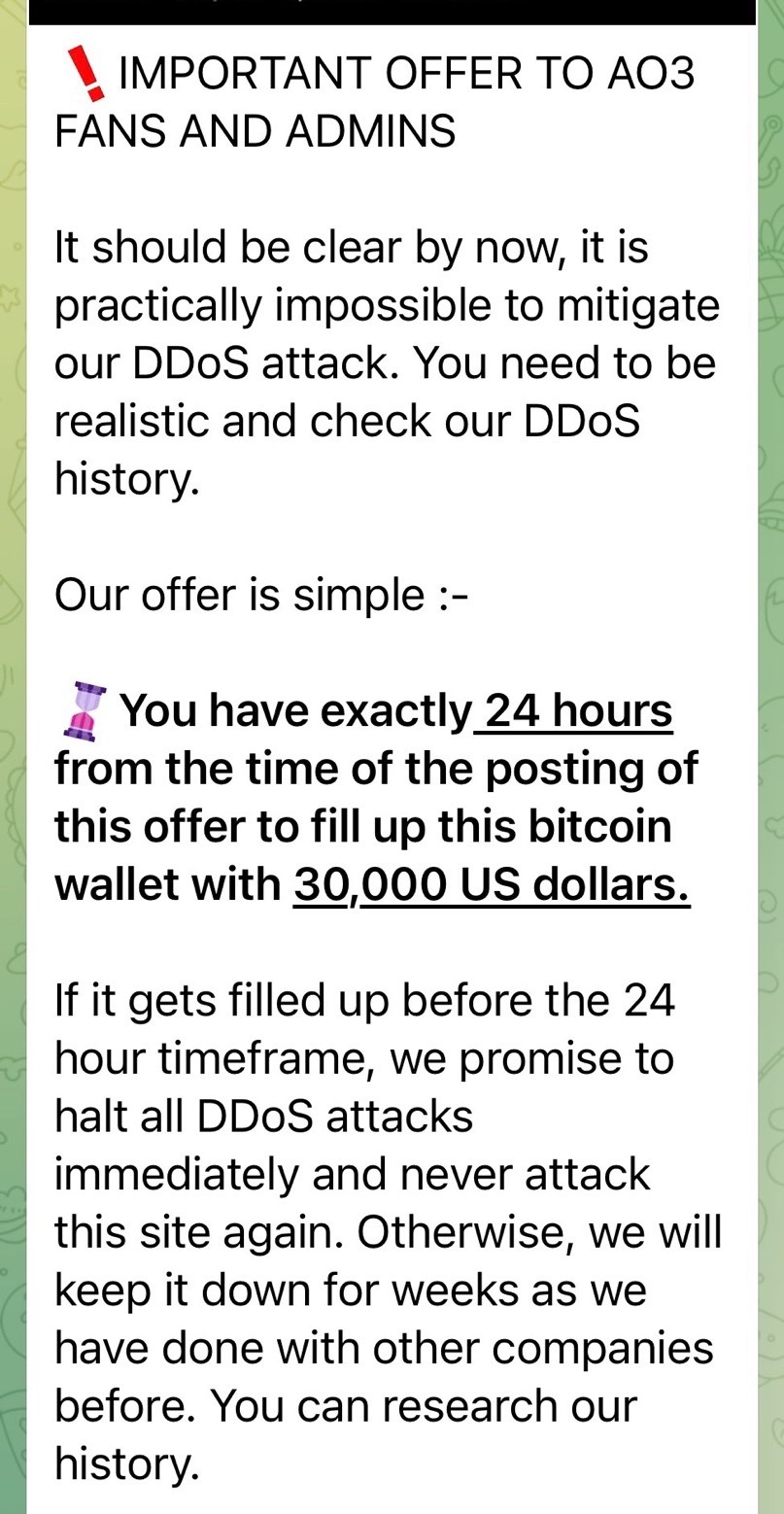
Edit: July 11th, So Ao3 is back! Though the donation link is being attacked now. There’s also a second account on Twitter trying to impersonate Ao3.
#a03#fanfic#fanfiction#supernatural#ao3#hackers#anonymous Sudan#lgbt#ao3 smut#the disgusting smuts were the hackers words#like so what?#you can’t handle our noncon dubcon omegaverse angst mpreg smuts#go read fifty shades of grey then. it’s not our fault you can’t handle us#also the fact they called it disgusting smuts implies that they had to have went to ao3 and read smut on there#Edit: they just released a statement saying they want 30k in US dollars in bitcoin for the ao3 servers#i reblogged that statement twice I believe#and to hold a non profit organization as a virtual hostage?#really#like they’d have better luck holding Wattpad for hostage
1K notes
·
View notes
Text

Death's dance running the Net.
Now available for purchase on INPRNT
#net#netrunner#coding#malware#security#death#dance#skates#web#server#flash#sisters#output#void#lady#hoko#virtual#loop#light#drawing#illustration#digitalart#digitalartwork#digitalsketch#digitalillustration#greed#scifi#90s
93 notes
·
View notes
Text

EN blue women
#hololive#vtuber#virtual youtuber#gawr gura#ouro kronii#nerissa ravencroft#my art#friend in a server im in asked if someone could draw this so i gave it a go
382 notes
·
View notes
Text

Valentin & Mitch | 669/??
━━ ETHEREAL 🌈
#Cyberpunk 2077#Mitch Anderson#Valentin Da Silva#Aldecaldos#OTP: High Voltage#MLM#Screenshot#Virtual Photography#OUGGGHHH#prompted by bb beanie and their lil throwback challenge on The Cyberpunks server#I FEEL LIKE MY VP IS RUSTY ASF LATETLY But I like this one ahgfhhg#The mood has been in Chamble >:O cringe ass fandom would do that to ya#But uwu gotta vibe
59 notes
·
View notes
Text

#whitegirls#18+ blog#18+ content#beautiful#gorgeous#i sell custom content#i sell noods#i sell videos#so hot 🔥🔥🔥#comeplay#tounge#lets play#virtual private servers#virtualpet#bbc#ineedyou#make me cvm
119 notes
·
View notes
Text

NaNoWriMo live write-in (hosted on Discord)
Join our write-in for extra motivation to continue NaNoWriMo or to work on a writing project you have. Get inspired by your fellow writers to get through NaNoWriMo. Writing together has many benefits among greater accountability for your writing schedule and the possibility to get others interested in your story.
You can video stream yourself writing (or not), everyone will be muted, so we can concentrate on writing. We can chat over text and motivate each other through writing sprints. The goal is to have fun writing together, there’s no pressure to finish a piece or reach a certain word count. Remember: It doesn't need to be perfect, it is great because only you can write your story. Important note: Time will be adjusted to find a date and time frame in which most participating writers are available.
Reblog to spread the word. We are a small and supportive writing community and happy to welcome new writers!
Comment on this post to get an invitation link to our fun little Discord server. You will join a safe writing community where you can just chit-chat, bounce ideas off of one another, share and discuss your writing and art, and ramble as much as you want about your WIP. If you want, you can also stream your favourite writing music or participate in games. For further information, read our faq page or send an ask.
We will be your writing family when the world gets too loud.
#wc.event#nanowrimo#writing community#virtual write in#live write in#writeblr#writers on tumblr#nano 2023#writeblr discord server
27 notes
·
View notes
Text
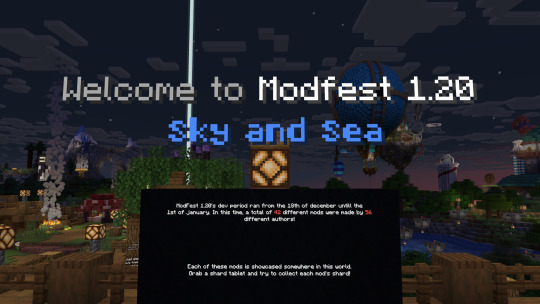
The ModFest 1.20: Sky and Sea Server is Live!
56 mod authors have created 42 mods in a two-week minecraft mod jam - now all available on a world full of curated mod showcase booths and cute collectibles!
Download the pack from modrinth and have fun!
#minecraft server#minecraft#modded minecraft#modding#virtual event#gaming#video games#minecraft build
16 notes
·
View notes
Photo

you have reached the edge of this world
#inanimate insanity#ii mephone5#my art#inspired by when u phase thru an object in a video game and the inside is just. invisible#that and when u hit an invisible wall#anyway lately i've had this concept in my brain of like. what if the consciousness of the dead meeples were stored in a server or smth#and they're jsut vibing in a customizable virtual limbo
109 notes
·
View notes
Text

starting a 70 hour rpg one day before it's online components shut down forever is a very good way to spend your saturday night
#i saw all the news about wii u servers closing and suddenly had an urge#i am not actually going to play it in full because i am sure they'll announce a remaster some day soon#but at least i have this to fall back on#also my wii u still has some bangers...#metroid virtual console titles and WW/TP HD. bring them to switch nintendo#xenoblade#xenoblade chronicles x
12 notes
·
View notes
Text

again, couldn't resist taking a pic of these two sillies who have invaded my life
#project sekai#akito shinonome#toya aoyagi#project sekai akito#project sekai toya#akitoya#i finally found out how to enter a virtual live on jp servers#i kinda expected for them to sing kashika#i am not used to listening to the og version of it since the akito alt cover#now i think the og sounds like a full group cover of akitos alt#anyway LOOK AT MY BABY BOYS#I LOVE THEM SO MUCH AAAA
28 notes
·
View notes
Text
Terrible news. Apparently Jellyfin’s macOS client can’t use their own, in-house version of ffmpeg. As a result, macOS Jellyfin doesn’t support JPEG XL images. I tried compiling an ffmpeg version with JXL enabled, but it still won’t work. Sigh. If anybody knows a workaround/fix, I’d gladly appreciate it. For now, though, I’m thinking about trying a Linux Virtual Machine solution.
#rambles#irl#computer#computers#macos#mac#linux#server#jellyfin#ffmpeg#tech support#jpeg xl#jxl#images#photos#virtual machine#vm#utm#qemu#help
7 notes
·
View notes
Text
I can't fucking believe this entire company, thousands of employees, hundreds of locations, has been completely dead in the water the entire day not a single person has been able to do anything productive for this entire workday. not complaining! just never thought I would see this.
19 notes
·
View notes
Text
(this is a small story of how I came to write my own intrusion detection/prevention framework and why I'm really happy with that decision, don't mind me rambling)
Preface
About two weeks ago I was faced with a pretty annoying problem. Whilst I was going home by train I have noticed that my server at home had been running hot and slowed down a lot. This prompted me to check my nginx logs, the only service that is indirectly available to the public (more on that later), which made me realize that - due to poor access control - someone had been sending me hundreds of thousands of huge DNS requests to my server, most likely testing for vulnerabilities.
I added an iptables rule to drop all traffic from the aforementioned source and redirected remaining traffic to a backup NextDNS instance that I set up previously with the same overrides and custom records that my DNS had to not get any downtime for the service but also allow my server to cool down.
I stopped the DNS service on my server at home and then used the remaining train ride to think. How would I stop this from happening in the future? I pondered multiple possible solutions for this problem, whether to use fail2ban, whether to just add better access control, or to just stick with the NextDNS instance.
I ended up going with a completely different option: making a solution, that's perfectly fit for my server, myself.
My Server Structure
So, I should probably explain how I host and why only nginx is public despite me hosting a bunch of services under the hood.
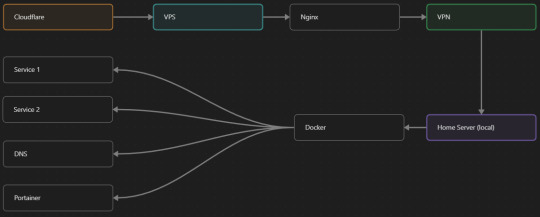
I have a public facing VPS that only allows traffic to nginx. That traffic then gets forwarded through a VPN connection to my home server so that I don't have to have any public facing ports on said home server. The VPS only really acts like the public interface for the home server with access control and logging sprinkled in throughout my configs to get more layers of security. Some Services can only be interacted with through the VPN or a local connection, such that not everything is actually forwarded - only what I need/want to be.
I actually do have fail2ban installed on both my VPS and home server, so why make another piece of software?
Tabarnak - Succeeding at Banning
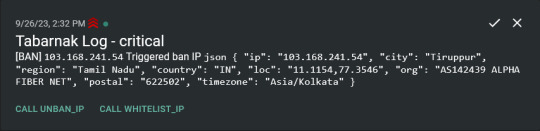
I had a few requirements for what I wanted to do:
Only allow HTTP(S) traffic through Cloudflare
Only allow DNS traffic from given sources; (location filtering, explicit white-/blacklisting);
Webhook support for logging
Should be interactive (e.g. POST /api/ban/{IP})
Detect automated vulnerability scanning
Integration with the AbuseIPDB (for checking and reporting)
As I started working on this, I realized that this would soon become more complex than I had thought at first.
Webhooks for logging
This was probably the easiest requirement to check off my list, I just wrote my own log() function that would call a webhook. Sadly, the rest wouldn't be as easy.
Allowing only Cloudflare traffic
This was still doable, I only needed to add a filter in my nginx config for my domain to only allow Cloudflare IP ranges and disallow the rest. I ended up doing something slightly different. I added a new default nginx config that would just return a 404 on every route and log access to a different file so that I could detect connection attempts that would be made without Cloudflare and handle them in Tabarnak myself.
Integration with AbuseIPDB
Also not yet the hard part, just call AbuseIPDB with the parsed IP and if the abuse confidence score is within a configured threshold, flag the IP, when that happens I receive a notification that asks me whether to whitelist or to ban the IP - I can also do nothing and let everything proceed as it normally would. If the IP gets flagged a configured amount of times, ban the IP unless it has been whitelisted by then.
Location filtering + Whitelist + Blacklist
This is where it starts to get interesting. I had to know where the request comes from due to similarities of location of all the real people that would actually connect to the DNS. I didn't want to outright ban everyone else, as there could be valid requests from other sources. So for every new IP that triggers a callback (this would only be triggered after a certain amount of either flags or requests), I now need to get the location.
I do this by just calling the ipinfo api and checking the supplied location. To not send too many requests I cache results (even though ipinfo should never be called twice for the same IP - same) and save results to a database.
I made my own class that bases from collections.UserDict which when accessed tries to find the entry in memory, if it can't it searches through the DB and returns results. This works for setting, deleting, adding and checking for records.
Flags, AbuseIPDB results, whitelist entries and blacklist entries also get stored in the DB to achieve persistent state even when I restart.
Detection of automated vulnerability scanning
For this, I went through my old nginx logs, looking to find the least amount of paths I need to block to catch the biggest amount of automated vulnerability scan requests. So I did some data science magic and wrote a route blacklist.
It doesn't just end there. Since I know the routes of valid requests that I would be receiving (which are all mentioned in my nginx configs), I could just parse that and match the requested route against that. To achieve this I wrote some really simple regular expressions to extract all location blocks from an nginx config alongside whether that location is absolute (preceded by an =) or relative. After I get the locations I can test the requested route against the valid routes and get back whether the request was made to a valid URL (I can't just look for 404 return codes here, because there are some pages that actually do return a 404 and can return a 404 on purpose).
I also parse the request method from the logs and match the received method against the HTTP standard request methods (which are all methods that services on my server use). That way I can easily catch requests like:
XX.YYY.ZZZ.AA - - [25/Sep/2023:14:52:43 +0200] "145.ll|'|'|SGFjS2VkX0Q0OTkwNjI3|'|'|WIN-JNAPIER0859|'|'|JNapier|'|'|19-02-01|'|'||'|'|Win 7 Professional SP1 x64|'|'|No|'|'|0.7d|'|'|..|'|'|AA==|'|'|112.inf|'|'|SGFjS2VkDQoxOTIuMTY4LjkyLjIyMjo1NTUyDQpEZXNrdG9wDQpjbGllbnRhLmV4ZQ0KRmFsc2UNCkZhbHNlDQpUcnVlDQpGYWxzZQ==12.act|'|'|AA==" 400 150 "-" "-"
I probably over complicated this - by a lot - but I can't go back in time to change what I did.
Interactivity
As I showed and mentioned earlier, I can manually white-/blacklist an IP. This forced me to add threads to my previously single-threaded program. Since I was too stubborn to use websockets (I have a distaste for websockets), I opted for probably the worst option I could've taken. It works like this:
I have a main thread, which does all the log parsing, processing and handling and a side thread which watches a FIFO-file that is created on startup. I can append commands to the FIFO-file which are mapped to the functions they are supposed to call. When the FIFO reader detects a new line, it looks through the map, gets the function and executes it on the supplied IP.
Doing all of this manually would be way too tedious, so I made an API endpoint on my home server that would append the commands to the file on the VPS. That also means, that I had to secure that API endpoint so that I couldn't just be spammed with random requests.
Now that I could interact with Tabarnak through an API, I needed to make this user friendly - even I don't like to curl and sign my requests manually. So I integrated logging to my self-hosted instance of https://ntfy.sh and added action buttons that would send the request for me.
All of this just because I refused to use sockets.
First successes and why I'm happy about this
After not too long, the bans were starting to happen. The traffic to my server decreased and I can finally breathe again.
I may have over complicated this, but I don't mind. This was a really fun experience to write something new and learn more about log parsing and processing.
Tabarnak probably won't last forever and I could replace it with solutions that are way easier to deploy and way more general. But what matters is, that I liked doing it. It was a really fun project - which is why I'm writing this - and I'm glad that I ended up doing this.
Of course I could have just used fail2ban but I never would've been able to write all of the extras that I ended up making (I don't want to take the explanation ad absurdum so just imagine that I added cool stuff) and I never would've learned what I actually did.
So whenever you are faced with a dumb problem and could write something yourself, I think you should at least try. This was a really fun experience and it might be for you as well.
Post Scriptum
First of all, apologies for the English - I'm not a native speaker so I'm sorry if some parts were incorrect or anything like that.
Secondly, I'm sure that there are simpler ways to accomplish what I did here, however this was more about the experience of creating something myself rather than using some pre-made tool that does everything I want to (maybe even better?).
Third, if you actually read until here, thanks for reading - hope it wasn't too boring - have a nice day :)
8 notes
·
View notes
Text




Valentin & Mitch | 645/?? | Lifepath AUs 🌵🌆💻
▶ Lifepath template by @arcandoria 🧡
#Cyberpunk 2077#Mitch Anderson#Valentin Da Silva#Aldecaldos#OTP: High Voltage#MLM#Screenshot#Virtual Photography#Felt like reposting this 😩😩#ngl I'm still ghuezhiughuiez hooked on street kid and corpos AU#Mitch doesnt LOOK LIKE HIMSELF AS A CORPOOOO LOOKATHIM 👁👄👁#I deadass just... swapped his cyebrware for Meredith's and used Vik's hair (I think)#but yeh basically- Street Kid Valentin is a.. Valentinos HAH#and Mitch is a 6th street#Tinos!Valentin sneaking some PTSD pills to 6th!Mitch and often getting caught by others 6th members#and getting beat up cause well they don't like valentinos roaming their streets#but Mitch often runs out of pills and Val doesn't went him to turn psycho#As for their corpos asses- Mitch is a Militech engineer watchin' over trainee Da Silva#who accidently breached into some of their servers's ICE while attempting to upgrade it with some illegal software#AHUGEZHUI Their appearances and lores aren't too developped but 👁👄👁 YEH
54 notes
·
View notes
Text
Not gonna lie y'all I am playing DnD for the first time in a long time and I only know the dm personally (he is a coworker and friend), so... just wish me and my social anxiety luck, I guess. Am nervous, but appreciative that there are other adults who want to be social and silly. This is fine. We are literally about to role-play for 3 hours as a merry band of misfits. Why am I concerned
3 notes
·
View notes